Access Matrix in OS
Overview
An access matrix in operating system is used to define each process’s rights for each object executing in the domain. It helps in the protection of a system and specifies the permissions/rights for every process executing in the domain. The access matrix in os is represented as a two-dimensional matrix.
What is Access Matrix in Operating Systems?
Access Matrix is a security model of the protective state of a computer system. For each object, the permissions for every process executing in the domain are specified using an access matrix.
Access matrix in os is shown as a two-dimensional matrix, where the columns of the matrix represent objects, while the rows represent domains. Each matrix cell represents a specific set of access rights that are granted to processes of the domain this indicates that each entry access (i, j) specifies the set of actions that a process executing in domain Di may invoke on object Oj. The access matrix implements policy decisions and these policy decisions involve which rights should be included in the (i, j)th entry like reading, writing, and executing. (This policy is usually decided by the operating system).
Implementation of Access Matrix in OS
As already discussed, the access matrix in the operating system likely occupies a significant amount of memory and is very sparse. Therefore, it is storage inefficient to directly implement an access matrix for access control. The access matrix can be subdivided into rows or columns to reduce the inefficiency. To increase efficiency, the columns, and rows can be collapsed by deleting null values. Four widely used access matrix implementations can be formed using these decomposition methods:
- Global Table
- Capability Lists for Domains
- Access Lists for Objects
- Lock and key Method
Various Methods Used to Implement the Access Matrix in OS
Some widely used methods for implementing the access matrix in os are as follows:
1. Global Table
The global table is the most basic and simple implementation of the access matrix in the operating system which consists of a set of an ordered triple <domain , object, right-set>. When an operation M is being executed on an object Oj within domain Di, the global table searches for a triple <Domain(Di), Object(Oj), right-set(Rk)> where M € Rk. If the triple is present, the operation can proceed to continue, or else a condition of an exception is thrown. There are various drawbacks to this implementation, the main drawback of global table implementation is that because the table is sometimes too large, it cannot be stored in the main memory, that's why input and output are required additionally.
2. Access Lists
In the Access Lists method, the access matrix in os is divided into columns (Column wise decomposition). When an operation M is being executed on an object Oj within domain Di, We search for an entry <Domain(Di), right-set(Rk)> with M € Rk in the access list for object Oj.If the triple is present, the operation can proceed to continue, or else we check the initial set. If M is included in the default set, access is allowed; otherwise, access is denied, and an exception is raised.
3. Capability Lists
In the access matrix in the operating system, Capability Lists is a collection of objects and the operations that can be performed on them. The object here is specified by a physical name called capability. In this method, we can associate each row with its domain instead of connecting the columns of the access matrix to the objects as an access list.
A capability list is itself a protected object maintained by OS and accessed by the user indirectly.
4. Lock-Key Mechanism
It is a comparison between capability lists and access lists. Every domain has a distinct bit pattern called keys, and every object has a distinct bit pattern called locks. Only if a domain's key matches one of the locks of the object, A process can access it.
In simple words, When a process running in a specific domain (Di) try to access an object (Oj) then the key of that Di must match with the lock of that Oj, then only an object can be accessed. The operating system should handle the keys and locks in such a way that any unauthorized access should not be allowed on them.
Examples
Consider the below example for a better understanding of implementing an access matrix in the operating system.
Now, let's take an example when there are four files having the following access rights (files f1, f2, f3, and f4) and three domains (D1, D2, D3)
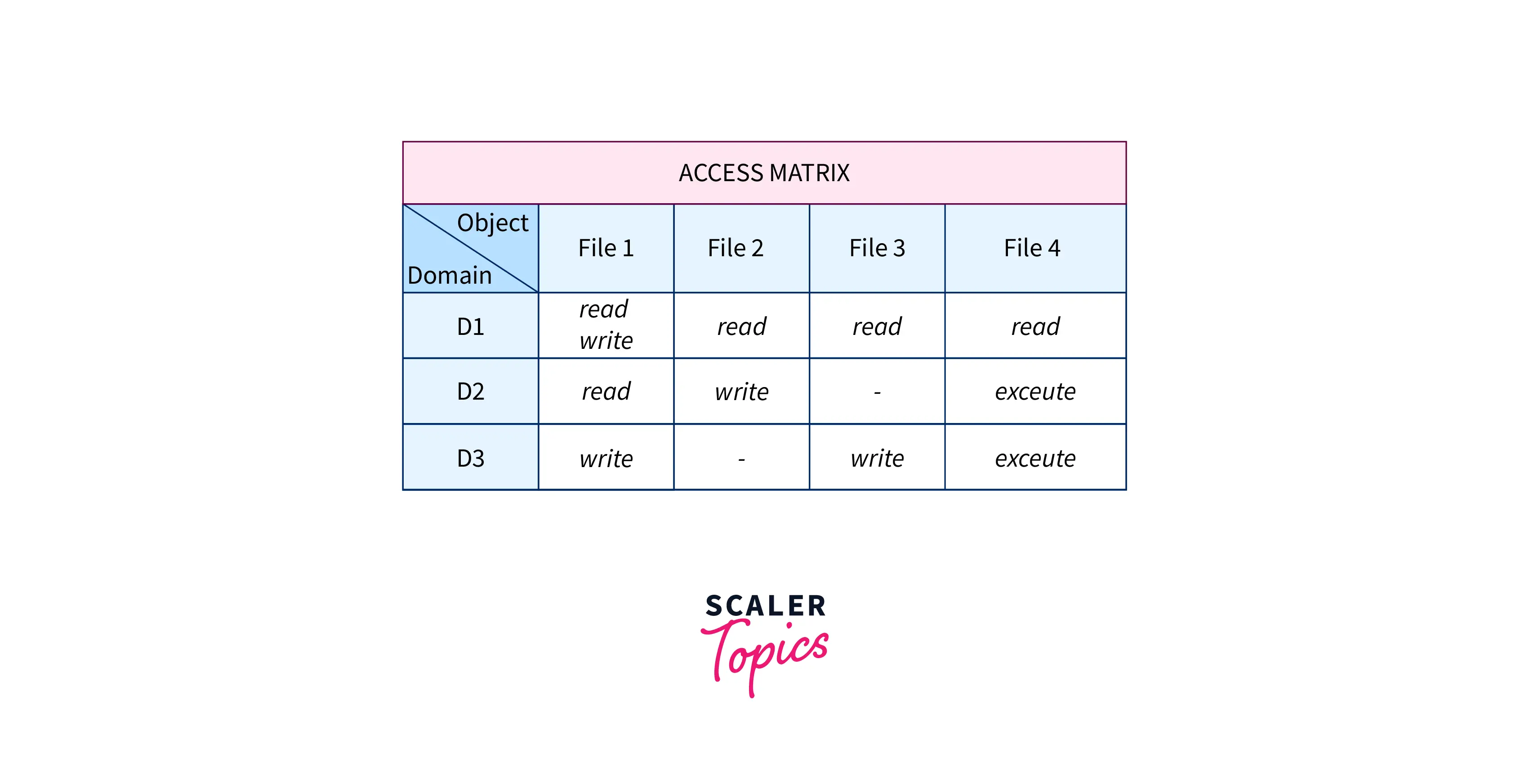
The access matrix, as seen in the figure above, here represents the set of access rights as:
- Any file can be read by a process running in the D1 domain and can only be written into f1.
- A process in D2 domain has access to read f1, write to f2, and execute f4.
- D3 processes in the domain can write to f1 and 3 and can execute f4.
The contents of the access-matrix entries are normally decided by the users. The access matrix's Oj column is added when a user creates a new object, Oj, with the proper initialization entries as provided by the creator. Processes should be able to switch between different domains.
An access matrix can be used to specify and implement both static and dynamic access rights. When a process switches between different domains, it's similar to when we do a (domain switch) operation on an object (the domain). The table below demonstrates the possibility of domain switches from the D1 domain to D2, D2 to D3, and D2 to D1.
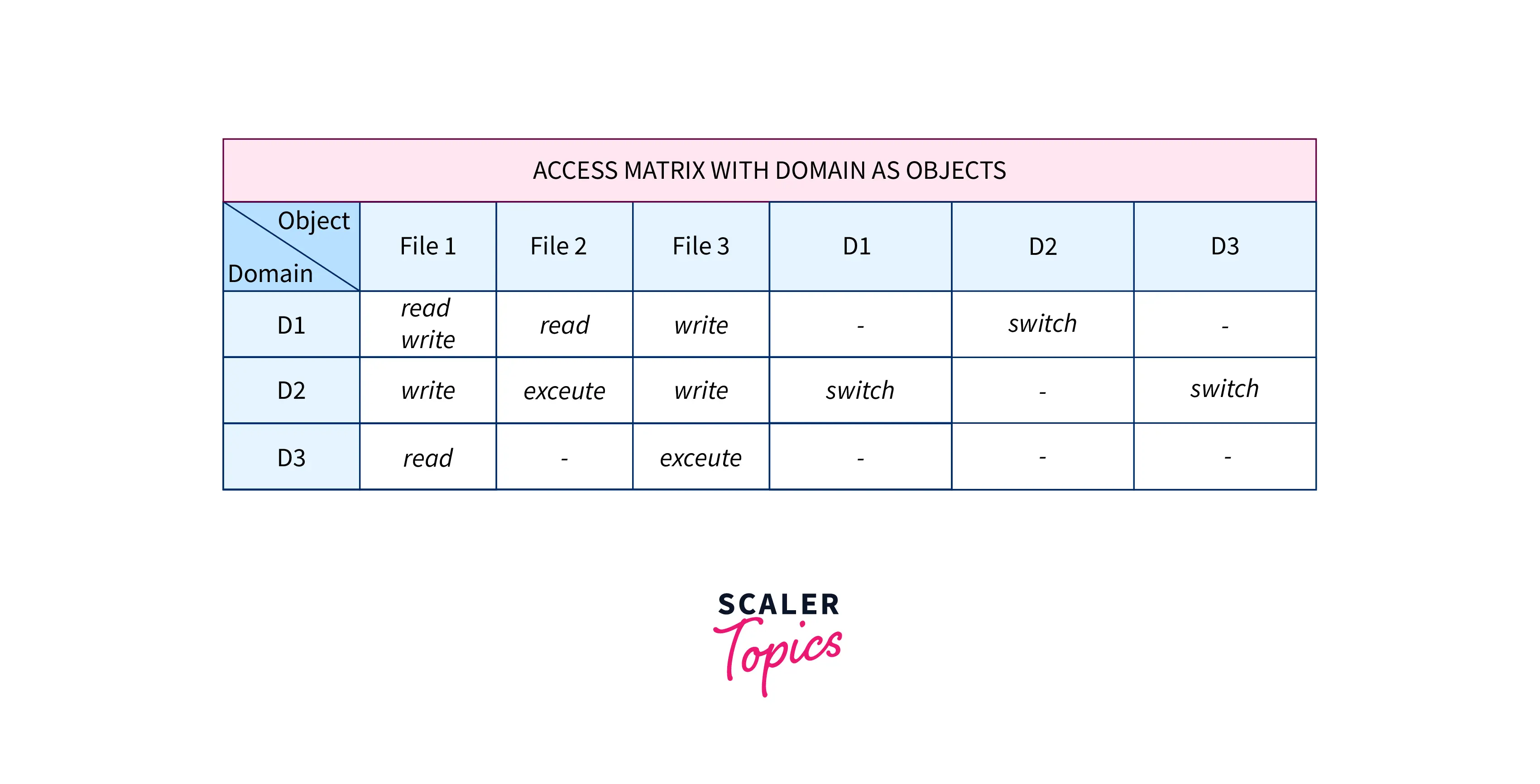
An asterisk (*) appended to the access right indicates the capability of copying an access right from one domain to another of the access matrix. The access right may only be copied within the column (i.e., for the object) for which it is defined by the copyright.
Conclusion
- An access matrix in os is used to define each process’s rights for each object executing in the domain.
- An access matrix in an operating system helps in the protection of a system and is represented by a two-dimensional matrix.
- We have also discussed the implementation of the access matrix in os with some methods in detail with the help of examples.
- Domain switching can easily be supported by simply “switch” access to other domains using an access matrix.
- Global table is not widely used as it has a drawback, due to several objects existing in the system table size increases, and additional I/O is required.
