ALOHA in Computer Network
Overview
The term Aloha in computer network means hello. Aloha is a data-link layer multiple access protocols that describes how multiple terminals can access the medium without interfering or conflicting. Norman Abramson and his associates developed it in the 1970s at the University of Hawaii. Each node or station in ALOHA transmits a frame without attempting to determine whether the transmission channel is idle or busy. If the channel is idle, the frames will be successfully transmitted. If two frames try to occupy the channel at the same time, they will collide and be discarded. These stations may opt to retransmit the corrupted frames until successful transmission occurs.
Introduction to Multiple Access Protocol
Multiple Access Protocols operate in the Medium Access Control sublayer (MAC sublayer) of the OSI(Open Systems Interconnection) model. These protocols enable several nodes or users to share a network channel. In general, Multiple Access Protocols are the set of protocols whose objective is to optimize the transmission line, avoid crosstalks and minimize the collisions in the channel.
When a sender and receiver share a dedicated link for data packet transmission, data link control is sufficient to handle the channel. Assume there is no specific path for two devices to communicate or transmit data. In that scenario, numerous stations access the channel and broadcast data over it at the same time. It may result in collisions and crosstalk. As a result, the multiple access technique is essential to limit collisions and eliminate channel crosstalk.
To understand the concept of Multiple Access Protocols more meaningfully, consider a scenario of a classroom full of students. When a teacher asks a question, all of the students (small channels) in the class begin addressing the question at the same time (transferring the data simultaneously). Since all students reply at the same moment, data is overlapping or lost. As a result, it is the job of a teacher (multiple access protocol) to control the students and force them to give one answer.
Let's look at the types of various Multiple Access Protocols.
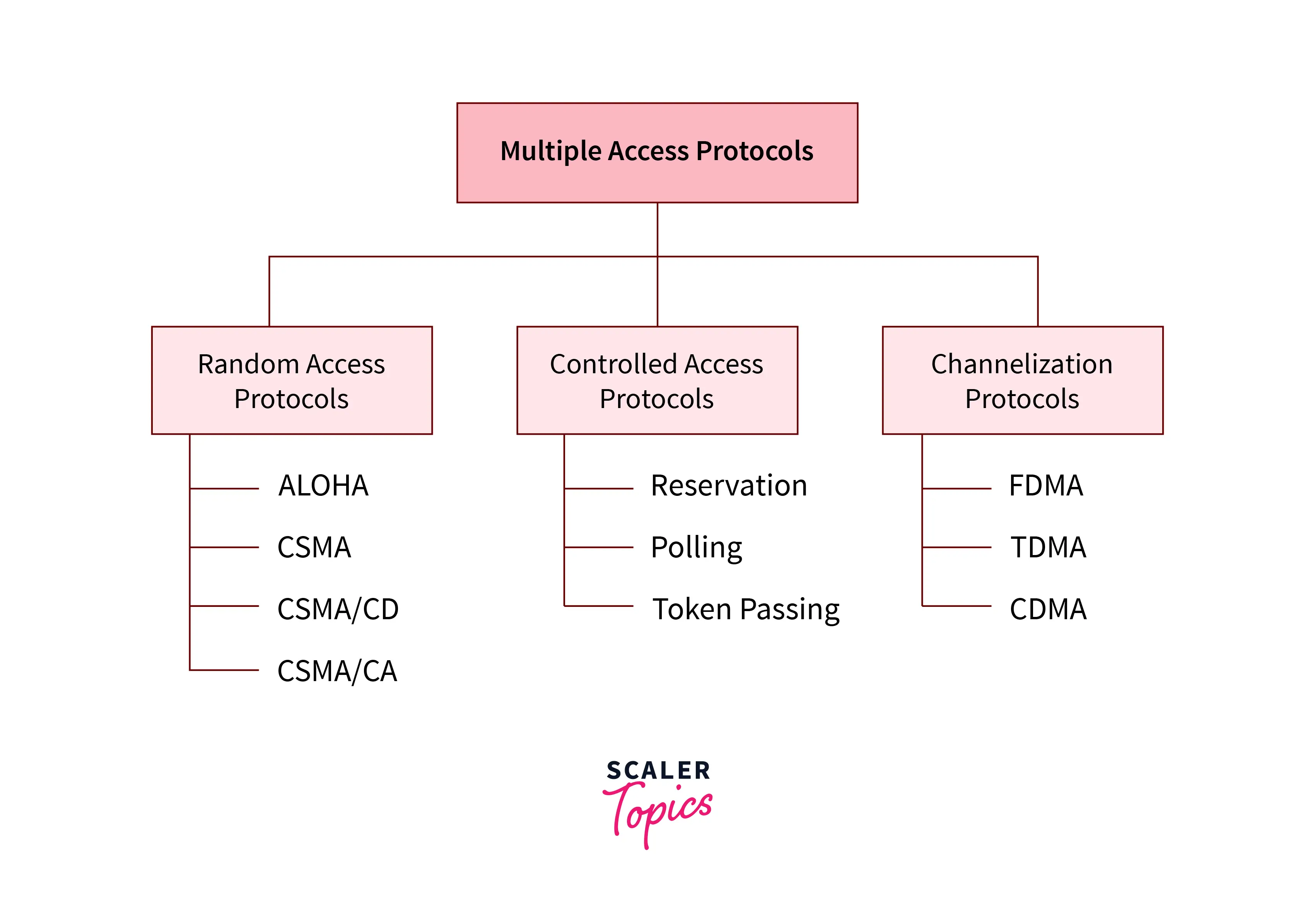
Random Access Protocols
In this protocol, each station has equal priority when it comes to sending data over a channel. One or more stations in a random access protocol cannot rely on another station, nor can one station control another. Each station broadcasts the data frame depending on the channel's status (idle or busy). A collision or conflict may occur if more than one station transmits data over the same channel. Data frame packets may be lost or altered due to the collision. As a result, it is not received by the receiving end.
Controlled Access Protocols
It is a technique for minimizing data frame collisions on a shared channel. Each station interacts and decides to send a data frame by a specific station that is approved by all other stations in the controlled access protocol. This means that until all other stations are not approved, a single station cannot deliver data frames. Reservation, polling, and token passing are the three methods of controlled access.
Channelization Protocols
A channelization system allows many stations to split the entire useable bandwidth in a shared channel based on their time, distance, and codes. It can access all stations simultaneously to send data frames to the channel. FDMA(Frequency Division Multiple Access), TDMA(Time Division Multiple Access), and CDMA(Code Division Multiple Access) are some of the methods of channelization protocols.
What is ALOHA in Computer Network?
ALOHA is a multiple-access protocol that allows data to be transmitted via a shared network channel. It functions in the open systems interconnection (OSI) model's medium access control sublayer (MAC sublayer). Several data streams from multiple nodes are transmitted across a multi-point transmission channel using this protocol. It was developed by Norman Abramson and his associates in the 1970s at the University of Hawaii.
Each node or station in ALOHA transmits a frame without attempting to determine whether the transmission channel is idle or busy. If the channel is idle, the frames will be successfully transmitted. If two frames try to occupy the channel at the same time, they will collide and be discarded. These stations may opt to retransmit the corrupted frames until successful transmission occurs.
Rules of ALOHA in Computer Network
- At any time, any station can transmit data to a channel.
- Collisions and data frames may be lost during data transmission over multiple stations.
- There is no need for carrier sensing.
- Aloha has no collision detection because the acknowledgment of the frames exists.
- It necessitates data retransmission after a random amount of time.
Types of ALOHA in Computer Network
The two protocols of Aloha in computer networks are:
- Pure Aloha
- Slotted Aloha
Pure Aloha
We employ Pure Aloha whenever data is available for transmission over a channel at stations. In pure Aloha, if each station transmits data to a channel without determining if the channel is idle or not, a collision may occur, and the data frame may be lost. When any station sends a data frame to a channel, the pure Aloha waits for the receiver's acknowledgment. If the receiver's acknowledgment is not received within the given time, the station waits for a random amount of time, known as the backoff time (Tb). Furthermore, the station may believe the frame has been lost or destroyed. As a result, it retransmits the frame until all of the data is properly delivered to the receiver.

Four stations (an unreasonable example) compete with one another for access to the shared channel. The diagram demonstrates that each station sends two frames for a total of eight frames on the shared medium. Due to several frames competing for the same shared channel, some of these frames collide. The picture above reveals that just two frames survive: frame 1.1 from station 1 and frame 3.2 from station 3. Even if one bit from one frame coexists on the channel with one bit from another frame, a collision occurs, and both are destroyed.
Vulnerable Time for Pure Aloha
We assume that the stations send fixed-length frames, which takes Tt time( Transmission Time) to transmit the frames completely. The diagram given below shows the vulnerable time for station A. The Vulnerable time for any station must be twice the transmission time because to stop the collision of frames, we must make sure that no other station starts its transmission between Tt time before and Tt time after the transmitting station.
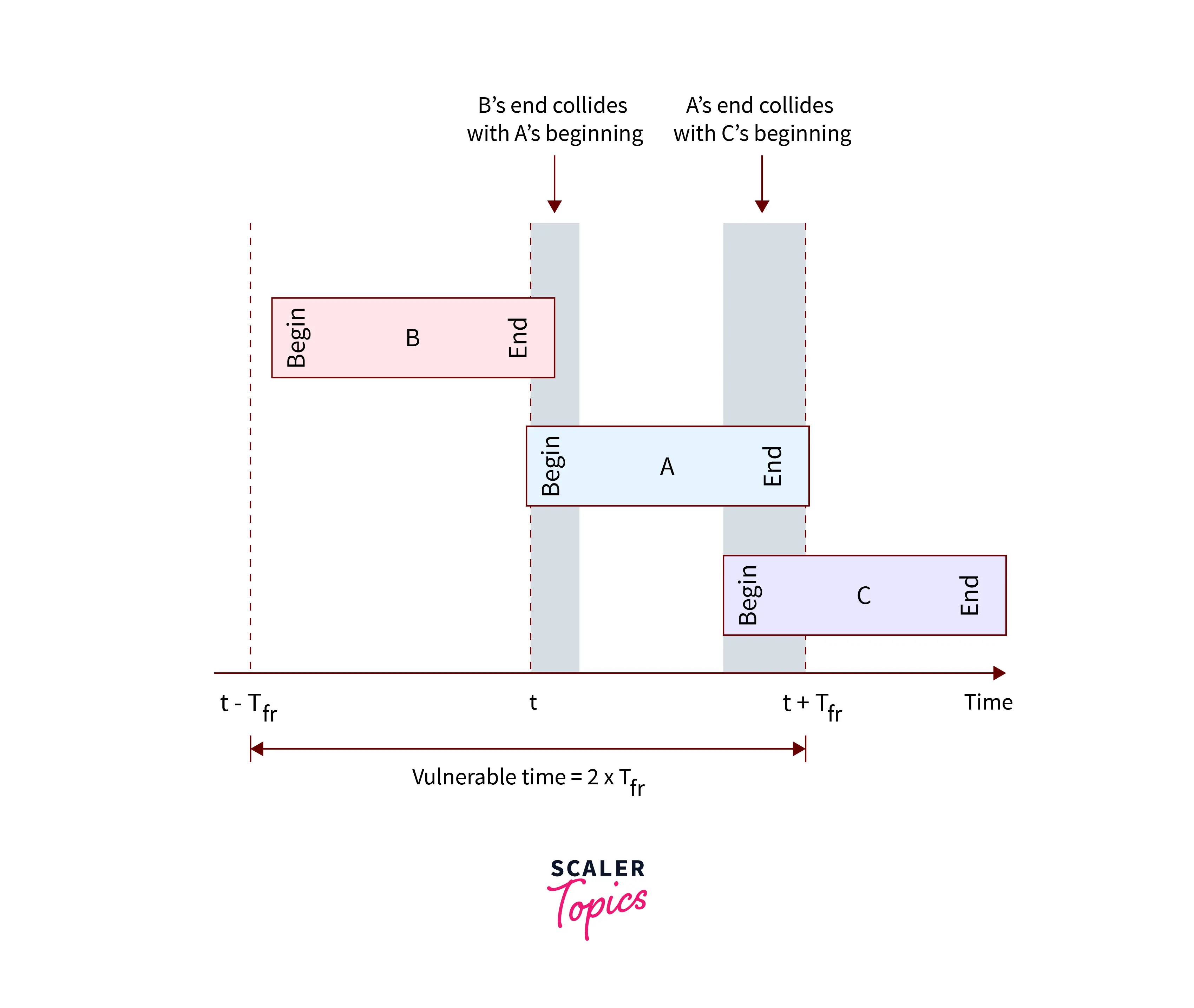
At the time t, Station A sends a frame. Assume station B has previously transmitted a frame between and . As a result, the frames from station A and station B collide. The end of B's frame intersects with the start of A's frame. Assume, on the other hand, that station C sends a frame between and . There is a collision between frames from stations A and C here. The start of the C's frame intersects with the conclusion of A's frame.
Where,
is a Vulnerable Time for Pure Aloha, is the Transmission Time of the station.
Note:- The Transmission Time or propagation time is the total time taken by the station to transmit the message completely. It is calculated by:
| Transmission Time() = Message lengthBandwidth of the Channel |
|---|
Throughput of Pure Aloha
Suppose G is the average number of frames created by the system during a single-frame transmission period. Then it may be demonstrated that the average number of successful ALOHA transmissions is given by S.
The value of S will be maxed if . So the Smax is 0.184. In other words, if one-half a frame is generated during one frame transmission time, 18.4 percent of these frames will reach their destination successfully.
The efficiency of Pure Aloha is 18.4%.
Slotted Aloha
Pure Aloha has a very high chance of hitting a frame, hence the slotted Aloha is intended to outperform its efficiency. In slotted Aloha, the shared channel is split into fixed time intervals called slots. As a result, if a station wants to send a frame to a shared channel, it can only do so at the start of the slot, and only one frame can be sent to each slot. Additionally, the station must wait until the beginning of the slot for the subsequent transmission if it is unable to transfer data at the beginning of the slot. However, sending a frame at the start of two or more station time slots still carries the risk of a collision.
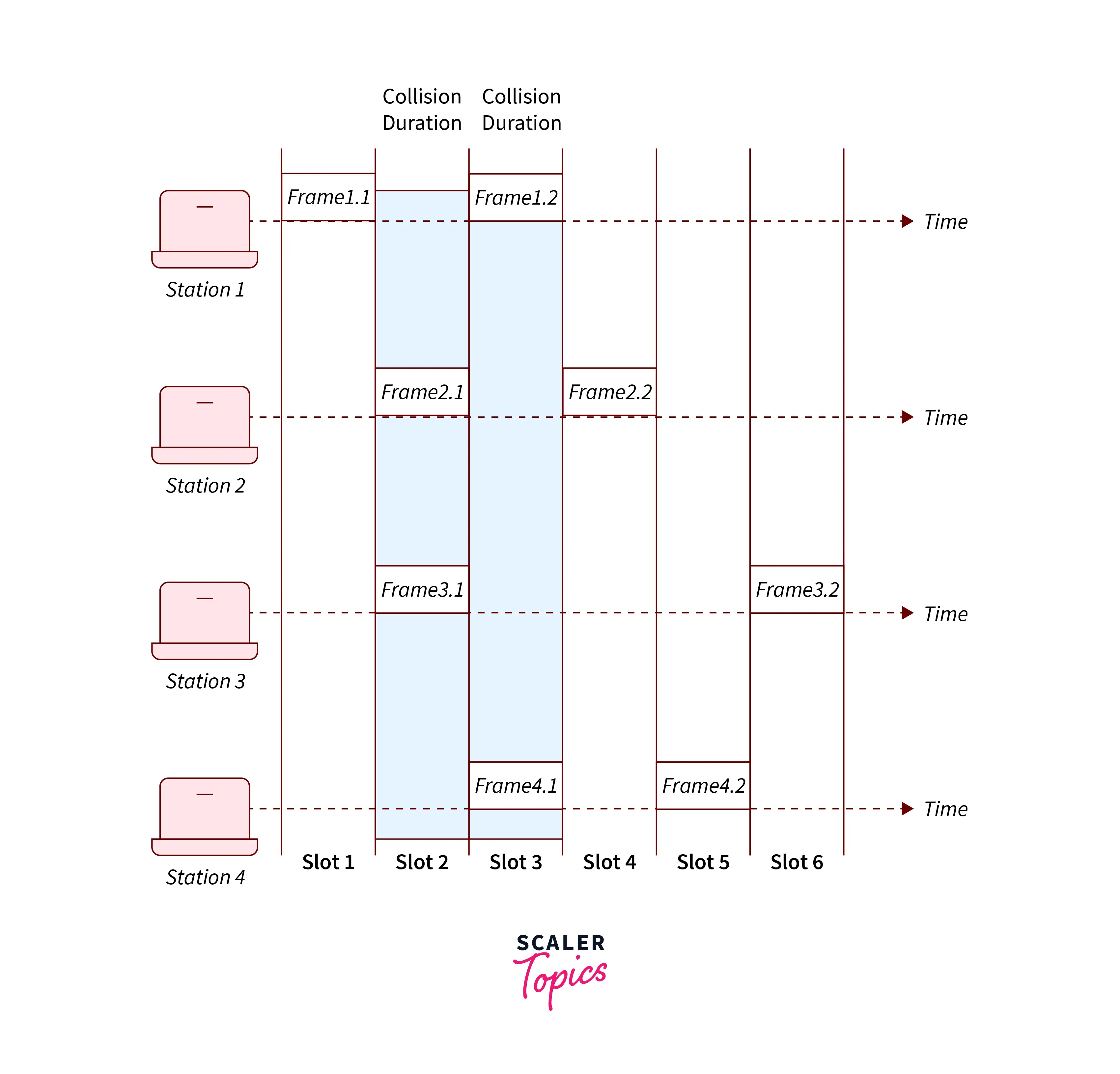
The figure shows how the channel is divided into slots. A station can start its transmission only at the start of the slot. So the only possible condition for collision is if two or more stations start transmission in the same slot. This condition is shown in Frame 1.2 of Station 1 and Frame 4.1 of Station 4.
Vulnerable Time for Slotted Aloha
The Vulnerable Time in the case of Slotted Aloha is equal to the transmission time of the station. It is because we bound the transmission of stations with the slots. The figure given below shows the Vulnerable time for Slotted Aloha.

Where,
is a Vulnerable Time for Slotted Aloha, is the Transmission Time of the station.
Throughput of Slotted Aloha
Suppose G is the average number of frames created by the system during a single-frame transmission period. Then it may be demonstrated that the average number of successful ALOHA transmissions is given by S.
The value of S will be max if . So the Smax is 0.368. In other words, 36.8 percent of these frames will reach their destination successfully if a frame is generated during one frame transmission time.
The efficiency of Slotted Aloha is 36.8%.
Protocol Flow Chart for ALOHA
The figure given below is the flow chart of the Aloha Protocol and describes the working of Aloha.
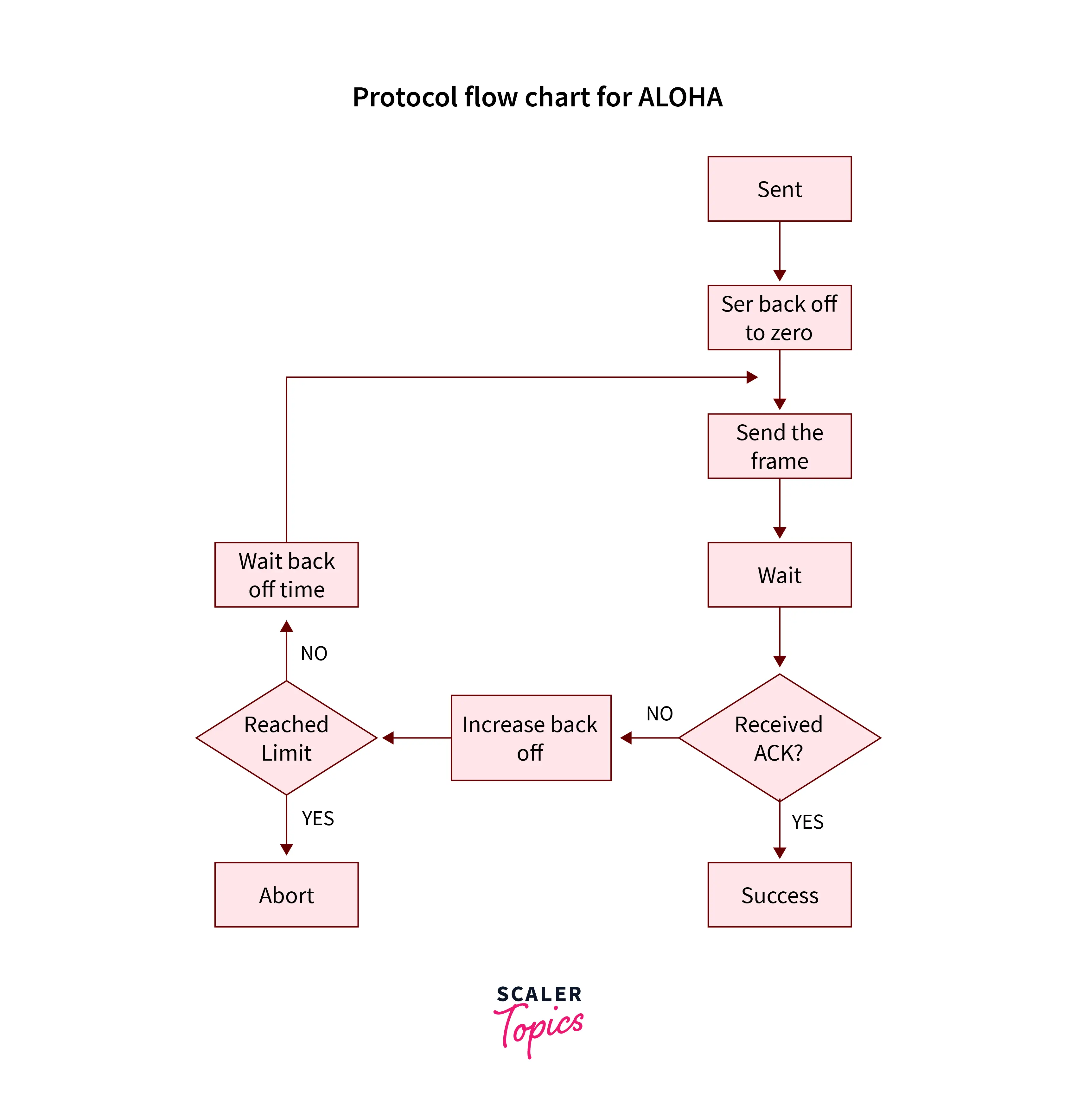
Explanation
- A station having data to transmit will start its transmission.
- It waits for some random time (depending on the type of Aloha Protocol). For example, it is in the case of Pure Aloha.
- If the acknowledgment is received, then the transmission is successful.
- If no acknowledgment is received, it means a collision has occurred. Then the station uses a backoff strategy to retransmit the packet again.
- After various iterations, the station aborts the transmission if there is no acknowledgment.
Differences between Pure and Slotted ALOHA
| Pure Aloha | Slotted Aloha |
|---|---|
| Any station can start transmission at any time. | Any station is allowed to start transmission only at the beginning of the slot. |
| Time is continuous and not globally synchronized. | Time is discrete and globally synchronized. |
| Vulnerable Time is equal to twice the transmission time of the station. | Vulnerable time is equal to the transmission time and given by: |
| The average number of successful ALOHA transmissions in the case of Pure Aloha is given by: | The average number of successful ALOHA transmissions in the case of Slotted Aloha is given by: |
| The maximum efficiency is 18.4%. | The maximum efficiency is 36.8%. |
| The chance of collision is high. | The chance of collision is relatively less as compared to Pure Aloha. |
Dive into the world of networking principles with our Free Computer Networking course. Join today and acquire the skills to create secure and scalable network infrastructures.
Conclusion
- The term Aloha in computer network means hello. Aloha is a data-link layer multiple access protocol that describes how multiple terminals can access the medium without interfering or conflicting.
- Aloha in computer networks is a random access protocol.
- Norman Abramson and his associates developed it in the 1970s at the University of Hawaii.
- Multiple Access Protocols are the set of protocols whose objective is to optimize the transmission line, avoid crosstalks, and minimize the collisions in the channel.
- There are two types of Aloha:
- Pure Aloha
- Slotted Aloha
- In Pure Aloha in computer network:
- Vulnerable Time is equal to twice the transmission time.
- Efficiency is 18.4%.
- The average number of successful ALOHA transmissions is given by .
- In Slotted Aloha:
- Vulnerable Time is equal to the transmission time.
- Efficiency is 36.8%.
- The average number of successful ALOHA transmissions is given by .
- The number of collisions is relatively less in Slotted Aloha than in Pure Aloha.
