AWS Audit Manager
Overview
AWS Audit Manager is a cloud service that automates the collection of evidence so that we can continuously audit AWS usage. We can use aws audit manager to assess the effectiveness of our controls, Streamline compliance, and manage risk. The objective of audit management is to organize, streamline, and simplify the auditing process. Traditionally, an audit manager was a professional who supervised company audits. Today, the term is increasingly applied to software services that fulfill similar functions.
Introduction
- AWS Audit Manager is a tool in the Security category of a tech stack.
- Automates the collection of evidence for procedures, policies, and activities, along with the creation of audit reports.
- AWS Audit Manager is a cloud service by Amazon Web Services that helps you regularly audit your AWS usage in order to simplify risk management and compliance with industry standards and regulations.
- It automates evidence collection to reduce the "all hands on deck" manual effort that is typically required for audits and enables you to scale your audit capability in the cloud as your business expands.
AWS Audit manager software facilitates the collection and organization of audit evidence. Also, it monitors the process of gathering evidence so that stakeholders can monitor progress and prioritize audit-related tasks. Typically, the software is aware of the processes and procedures a business must implement to comply with various regulatory requirements, and as a result, it provides a framework for guiding evidence collection.
How Does it Work?
As an AWS service, Audit Manager automates the collection of evidence, such as your cloud service usage, configurations, event logs, and other findings. Instead of spending weeks manually sorting through controls, the AWS Audit Manager service automatically maps your resources to predefined and custom compliance frameworks.
- The built-in frameworks simplify the translation of system evidence into audit-ready assessment reports and simplifies the evaluation of the controls' effective operation (policies, procedures, and operations).
- Similarly, the Ready-to-use frameworks from the AWS Audit Manager assist users in mapping the use of AWS assets to the applicable guidelines or industry standards, Payment Card Industry Data Security Standard (PCI DSS), GDPR, and such as CIS AWS Foundations.
-
As the auditor moves away from physically gathering, examining, and monitoring evidence to answer any questions, the AWS audit manager enables its users to implement an automated and dependable intelligence and use collection system.
-
It offers a straightforward method for tracking the authority of the proof chain, encourages the coordination of efforts for cooperation, and facilitates the monitoring of proof security and trustworthiness.
Audit Manager can also be used to continuously evaluate your internal risk assessment and ensure its consistency.
Concepts and Terminologies of AWS Audit Manager
-
Assessments: A framework, which consists of controls, serves as the basis for an evaluation. Depending on business requirements, users can design an evaluation using either a standard framework or a custom framework. In standard frameworks, pre-built control sets facilitate compliance with a particular standard or regulation. An assessment has two states:
- Active - currently collecting evidence.
- Inactive - stops collecting evidence.
-
Assessment Reports: A completed document resulting from an AWS Audit Manager evaluation, an assessment report is also known as an audit report. These reports provide a synopsis of the pertinent evidence collected for the audit. They direct users to the appropriate folders containing evidence. It also includes links to PDF files containing evidence. The evaluation reports are placed in an S3 bucket.
-
Audit: A financial audit is an impartial evaluation of a company's assets, operations, or financial integrity. An audit of information technology (IT) evaluates the controls of an organization's information systems. The objective of an IT audit is to determine whether information systems protect assets, operate efficiently, and preserve data integrity.
-
Framework Library: Specifies the controls and data source mappings for a particular compliance regulation or standard. By submitting a share request, a recipient can create assessments using your custom framework.
- Custom Frameworks - AWS frameworks that you have created.
- Standard Frameworks – AWS frameworks that are pre-built.
-
Delegations: This enables you to delegate a control set for review and validation of evidence to a subject matter expert. Audit owners ask the delegates to review the evidence associated with a control set.
- Delegate
- Audit owner
-
Compliance Standard: A compliance standard is a set of structured instructions that define how an organization adheres to established standards, specifications, or laws. PCI DSS and HIPAA are two examples.
-
Compliance Regulation: A law, rule, or other directive issued by a government agency to regulate behavior constitutes a compliance regulation. GDPR is a perfect example.
-
Control Library:
- Custom Controls - Allows you to specify the data sources from which you wish to collect evidence. Customized controls that you have created.
- Standard Controls - Predefined AWS controls. Any standard control can be customized to meet your specific needs. Standard controls cannot be deleted.
-
Evidence: Evidence is a document containing the information required to demonstrate compliance with a control's requirements. Two examples of proof are a user-initiated modification activity and a system configuration snapshot. there are two sorts of evidence:
- Automated Evidence — The evidence automatically collected by AWS Audit Manager is referred to as automated evidence.
- Manual Evidence — This is evidence that can be uploaded manually as a supporting document to AWS Audit Manager.
Features Of AWS Audit Manager
AWS Audit Manager was packed with features. Audit Manager provides prebuilt frameworks with controls that are complete customization of frameworks and controls, aligned to common industry standards and laws, and automated collection and organization of evidence from users' AWS consumption in accordance with each control requirement.
- Continuous auditing and compliance.
- Frameworks and controls.
- Internal risk assessments.
- Evidence collection from multiple sources.
- Workflow for delegation.
- Prebuilt frameworks.
- Audit ready reports.
- Transition from manual to automated evidence collection.
AWS Audit Manager Use Cases
- Deploy Internal Risk Assessments: Customize a pre-built framework from scratch, and then initiate an evaluation that will automatically collect evidence.
- Continually Audit To Assess Compliance: Collect evidence automatically, monitor your compliance posture, and proactively minimize threats by refining your controls.
- Transition From Manual To Automated Evidence Collection: Automated evidence collection eliminates the need to collect, assess, and manage evidence.
AWS Audit Manager Monitoring
- Collects log data from AWS CloudTrail and generate evidence of user activity from processed logs.
- You can capture snapshots of your resource security posture by generating reports:
- Add findings to AWS Config.
- Results of security checks retrieved directly from the AWS Security Hub.
- Audit Manager contains a License Manager framework to aid in audit preparation.
- The following services can help you in preparing for your audit:
- AWS License Manager framework.
- The framework of AWS Control Tower Guardrails.
- Using Amazon SNS, you can notify a user whenever one of the following events occurs:
- A control set is assigned for review by the audit owner.
- The owner of the audit has completed reviewing a control set.
- The delegate provides the audit owner with a set of controls that have been submitted.
Security in AWS Audit Manager
Cloud security is a top priority at AWS. Customers of AWS have access to data centers and network topologies designed to meet the requirements of the most security-conscious businesses. Under the shared responsibility model, this is referred to as cloud security or cloud-based security.
- Cloud Security - AWS is responsible for protecting the infrastructure used to run AWS services in the AWS Cloud. AWS also provides services that can be utilised securely. Third-party auditors examine and certify the effectiveness of our security as part of the AWS Compliance Programs.
- Cloud-Based Security – Users' responsibilities are determined by the AWS service they utilize. Other factors, such as the sensitivity of the data, the company's requirements, and applicable laws and regulations, are also the responsibility of the users.
Data Protection in AWS Audit Manager
Establishing individual user accounts with the AWS IAM (Identity and Access Management) and Protecting AWS account credentials are advised for data security. Consequently, every user is only granted the permissions that are required to fulfill their job responsibilities. It is recommended to protect the data using the following techniques:
- Use the AWS encryption solutions and all of AWS's fundamental security settings.
- AWS CloudTrail is capable of logging API and user activity.
- Use SSL to communicate with the AWS resources. TLS version 1.2 or more updated is recommended.
- Use multi-factor authentication (MFA) with each account.
- Use the most advanced security services like Amazon Macie, that also helps discover and protect sensitive Amazon S3 data.
When creating assessments, custom controls, custom frameworks, or delegation comments, AWS Audit Manager clients should not include sensitive identifying information in free-form fields. Customer data is stored for up to a year on AWS Audit Manager's fast storage. By default, user data will be deleted one year after collection.
Key Management
It supports both AWS-owned keys and client-managed keys for encrypting all the Audit Manager resources (assessment reports, assessments, evidence, controls, and frameworks are stored in Amazon S3 buckets in our account).
Encryption at Rest
AWS Audit Manager uses server-side encryption with AWS-managed keys to secure all of its data storage and logs. Data is encrypted using either a customer-managed key or an AWS-owned key, depending on the user's preferences.
AWS Audit Manager encrypts the content with an AWS-owned key if the user does not supply a customer-managed key. Audit Manager encrypts all DynamoDB and Amazon S3 service metadata with an AWS-owned key.
Encryption in Transit
AWS Audit Manager offers secure and confidential endpoints for encrypting the data in transit. Using secure and private endpoints, AWS can ensure the authenticity of API queries to the Audit Manager.
AWS Audit Manager Pricing
Users are charged based on the number of resource assessments performed and assessment reports stored in Amazon S3. Each assessment of a resource generates a single piece of evidence.
Three different types of evidence are there:
- Snapshot of a resource configuration.
- User activity.
- Compliance check result.
- AWS Free Tier: AWS Audit Manager provides a free tier for new users. The complimentary tier will expire two calendar months following the initial subscription. The free tier includes 35,000 resource assessments per month for two calendar months.
- Pricing is based on the region, Per 1,000 Audit Manager resource assessments per account per region.
- Additional Charges: The charges shown on the Amazon S3 section of the AWS invoice. Our prices do not include applicable duties and taxes, including the sales tax and VAT unless otherwise specified.
Amazon Audit Manager allows users to store and generate audit-ready assessment reports containing a summary document and folders of supporting evidence in the AWS S3 buckets. We incur standard Amazon S3 storage fees to store all objects in the bucket, like retrieving and storing assessment report data in S3.
How Does AWS Audit Manager Streamline Compliance Audits?
AWS Audit Manager is a service that automates compliance evidence collection. The organization notifies the AWS Audit Manager of applicable controls. Amazon Audit Manager retrieves relevant information from other services, such as AWS CloudTrail, AWS Config, and AWS Security Hub. This information is converted into a format that is fully transparent and it serves as evidence of the control's implementation.
Audit Evidence Access Controls
Audit evidence is private, and access must be managed and controlled. AWS Audit Manager, as you might expect, integrates with AWS Identity and Access Management (IAM), a solution that businesses with AWS-based infrastructure already employ. The Audit Manager can segregate individual assessments so that only authorized individuals and groups can access them.
Simplified Audit Workflows
The collection of evidence can be complex and difficult to manage. It is simple to make errors that lengthen and increase the cost of audits. Auditees are relieved of a significant burden by automatic data collection. Because AWS Audit Manager is deeply integrated into the AWS platform, the software gathers the majority of evidence without requiring human intervention.
Automatic Evidence Collection
AWS Audit Manager supports multiple automated data sources with different data collection frequencies:
- Amazon CloudTrail is used for user activity tracking. Data collection is continuous.
- AWS API calls collect daily, weekly, or monthly snapshots of resource configuration data from AWS resources.
- AWS Security Hub provides security check snapshots. According to Security Hub check schedules, data is collected.
- AWS Config provides resource security snapshots. The collection of data is triggered by an AWS Config rule.
AWS Audit Manager Frameworks
Each framework provides audit control groups and mappings to AWS resources and data. AWS offers pre-built compliance frameworks for a variety of standards, including:
- Health Insurance Portability and Accountability Act (HIPAA)
- FedRAMP Moderate Baseline
- General Data Protection Regulation (GDPR)
- SOC 2
- PCI DSS V3.2.1
- ISO/IEC 27001:2013 Annex A
Users can create custom frameworks in addition to pre-built frameworks. These enable organizations to deploy AWS Audit Manager assessments no pre-built option is there. In addition, they can create assessments and collect evidence to meet other business requirements, such as internal audits.
Continuous Compliance
Continuous compliance is one of the greatest benefits of automated evidence collection. Manual evidence collection is typically periodic. The gathering of evidence for "the big audit" is an expensive procedure that is not repeated until the next audit period.
Continuous compliance can be maintained with the help of automated evidence gathering. It makes sense to keep audit evidence up-to-date as evidence collection becomes much simpler. Because the evidence is always current, it is possible to maintain continuous compliance, and when a new audit is required, there are significantly fewer costs associated with evidence collection.
Getting Started with AWS Audit Manager
Setting Up Audit Manager
- Go to the AWS Management Console.
- Sign in with the credentials of your IAM identity.
- Click on Set up AWS Audit Manager.
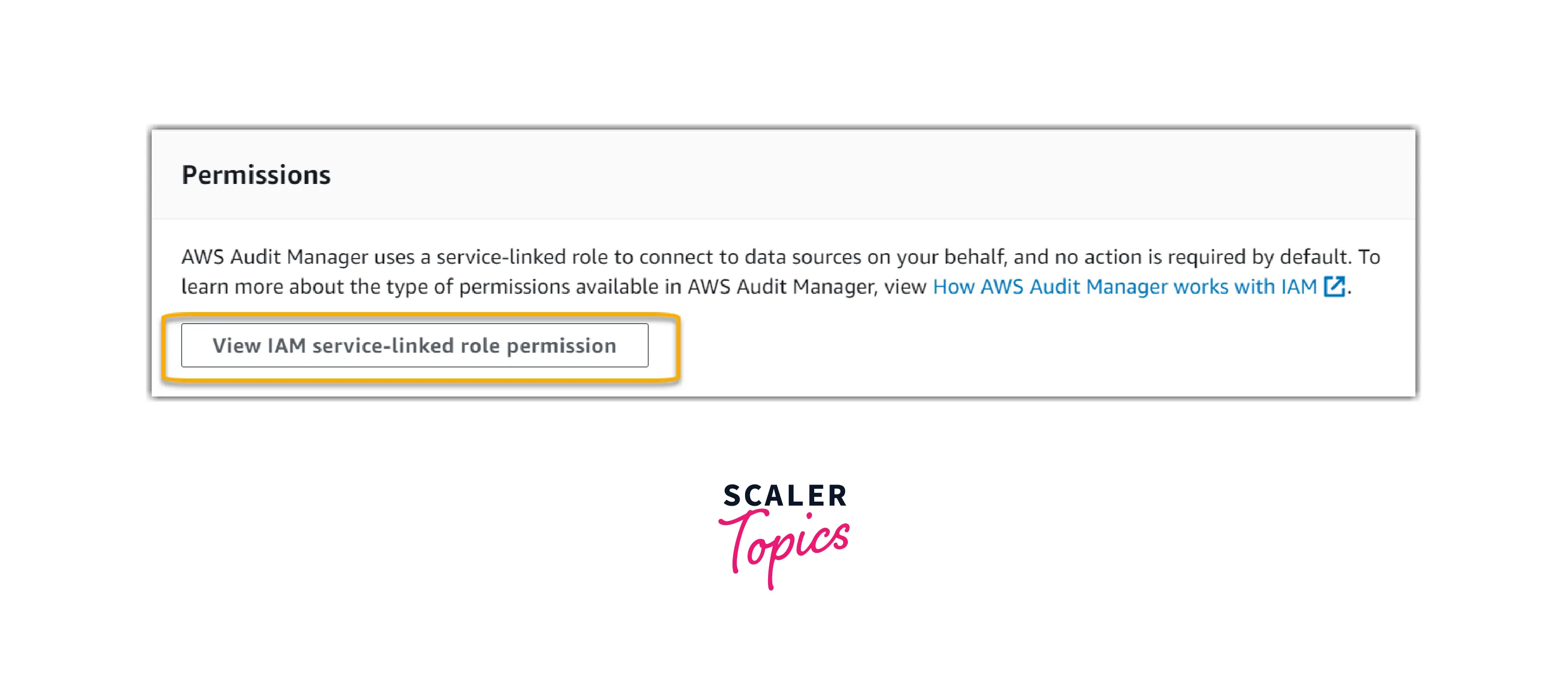
- There is no action required under Permissions. Audit Manager connects to data sources on your behalf utilizing a service-linked role. By selecting the View IAM service-linked role permission, you can review the service-linked role.
- Under Data encryption, the default option specifies that Audit Manager will generate and manage an AWS KMS key for storing your data securely.
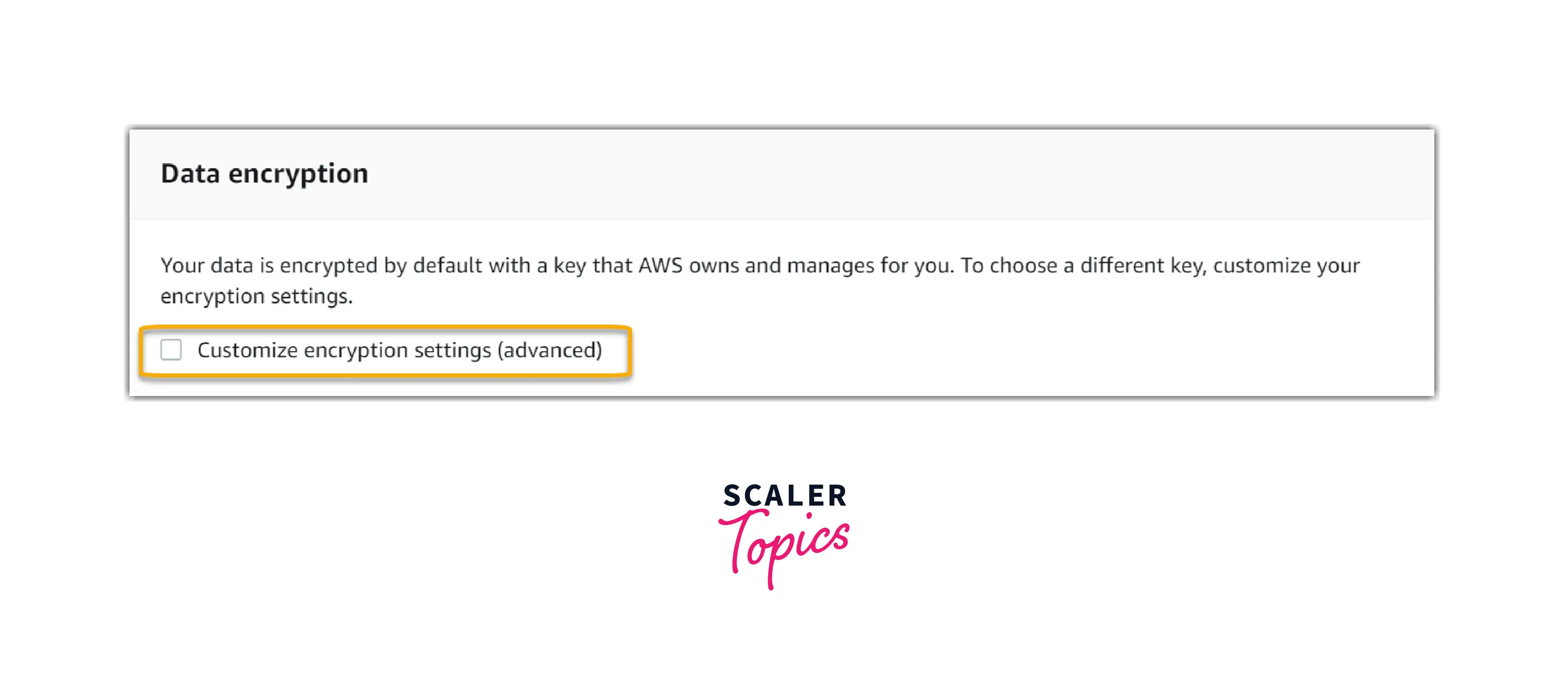
Select the checkbox next to Customize encryption settings if you wish to use your own customer-managed key to encrypt data using Audit Manager (advanced). Then, you can select an existing KMS key or generate a new one.
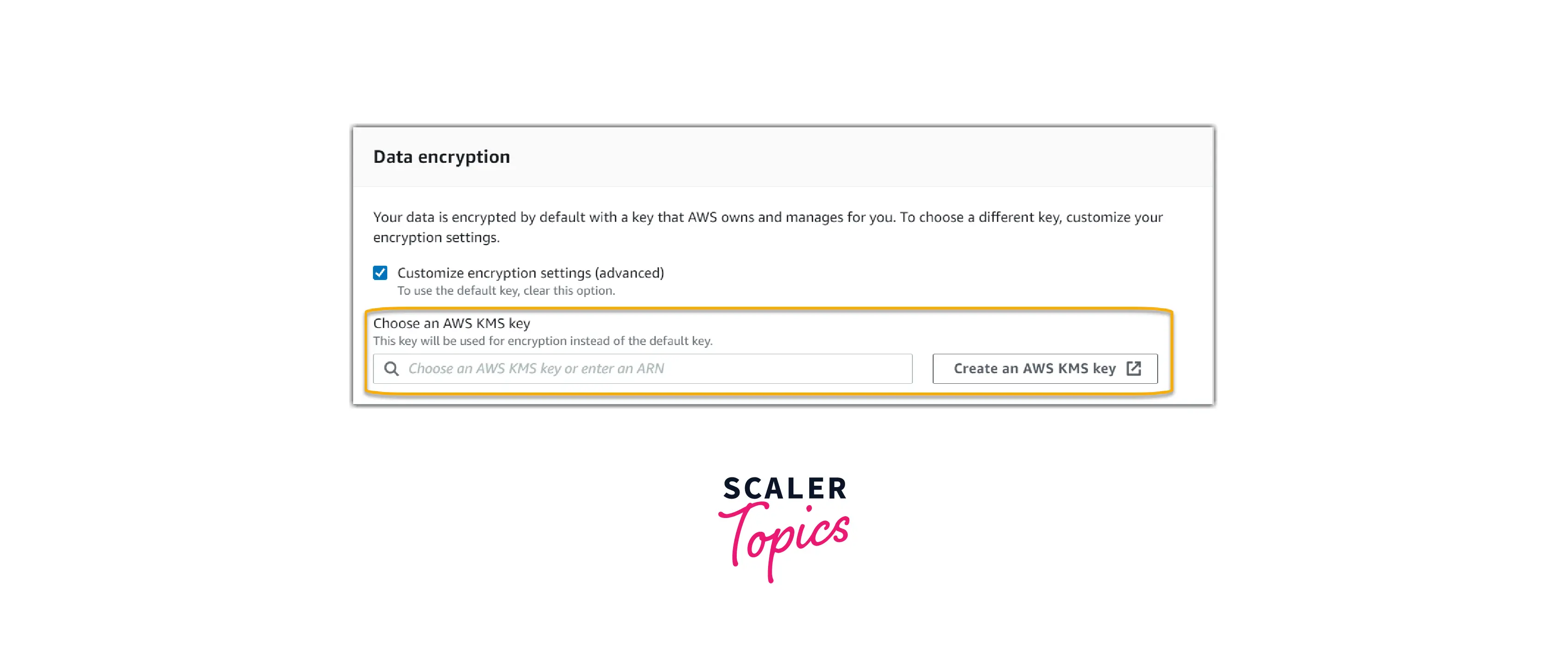
- (Optional) You can specify a delegated administrator account under Delegated administrator - optional if you want Audit Manager to conduct assessments for multiple accounts. Enable and configure AWS Organizations for use with Audit Manager for further information and recommendations.
- (Optional) We recommend that you enable AWS Config under AWS Config – optional for the best service. This permits the Audit Manager to produce evidence utilizing AWS Config rules. See Enable and configure AWS Config for use with Audit Manager for instructions and recommended settings.

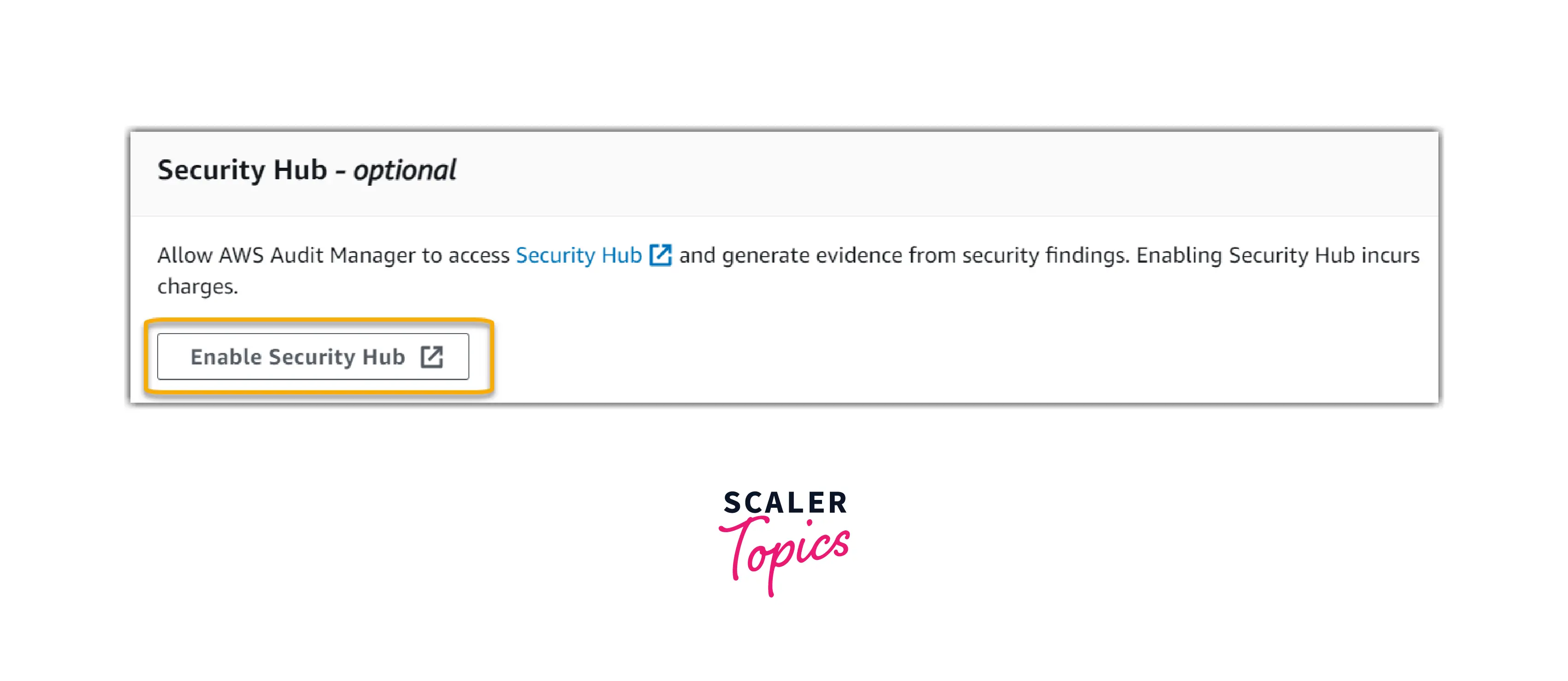
- (Optional) We recommend that you enable Security Hub under Security Hub - optional for the best experience. This permits the Audit Manager to produce evidence utilizing Security Hub checks. Enable and configure the AWS Security Hub for use with Audit Manager for instructions and recommended settings.
- Click on Complete setup to finish the setup process.
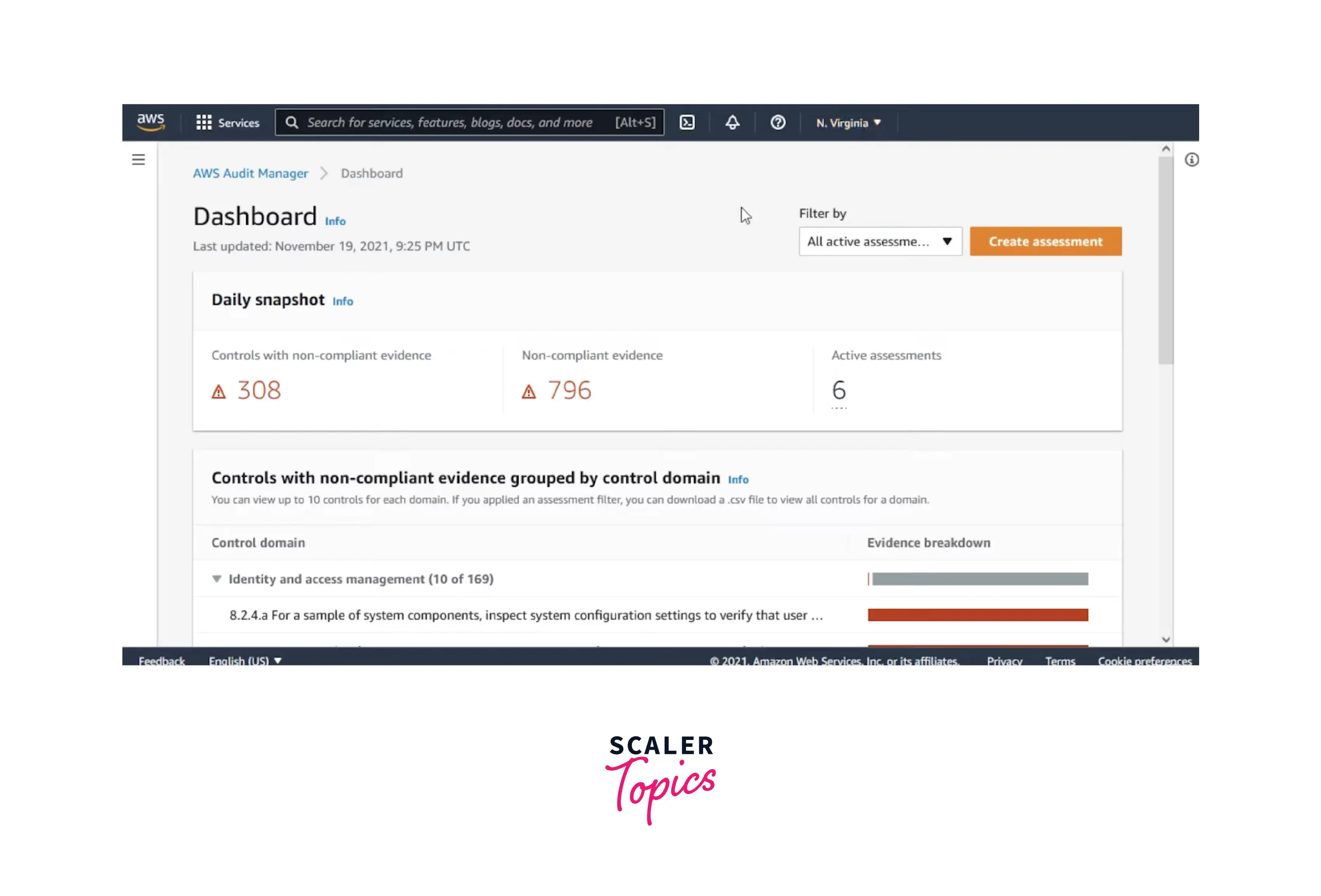
- Learn How To Monitor Active Assessments - View analytics data and identify evidence of noncompliance. Explore the dashboard documentation >>
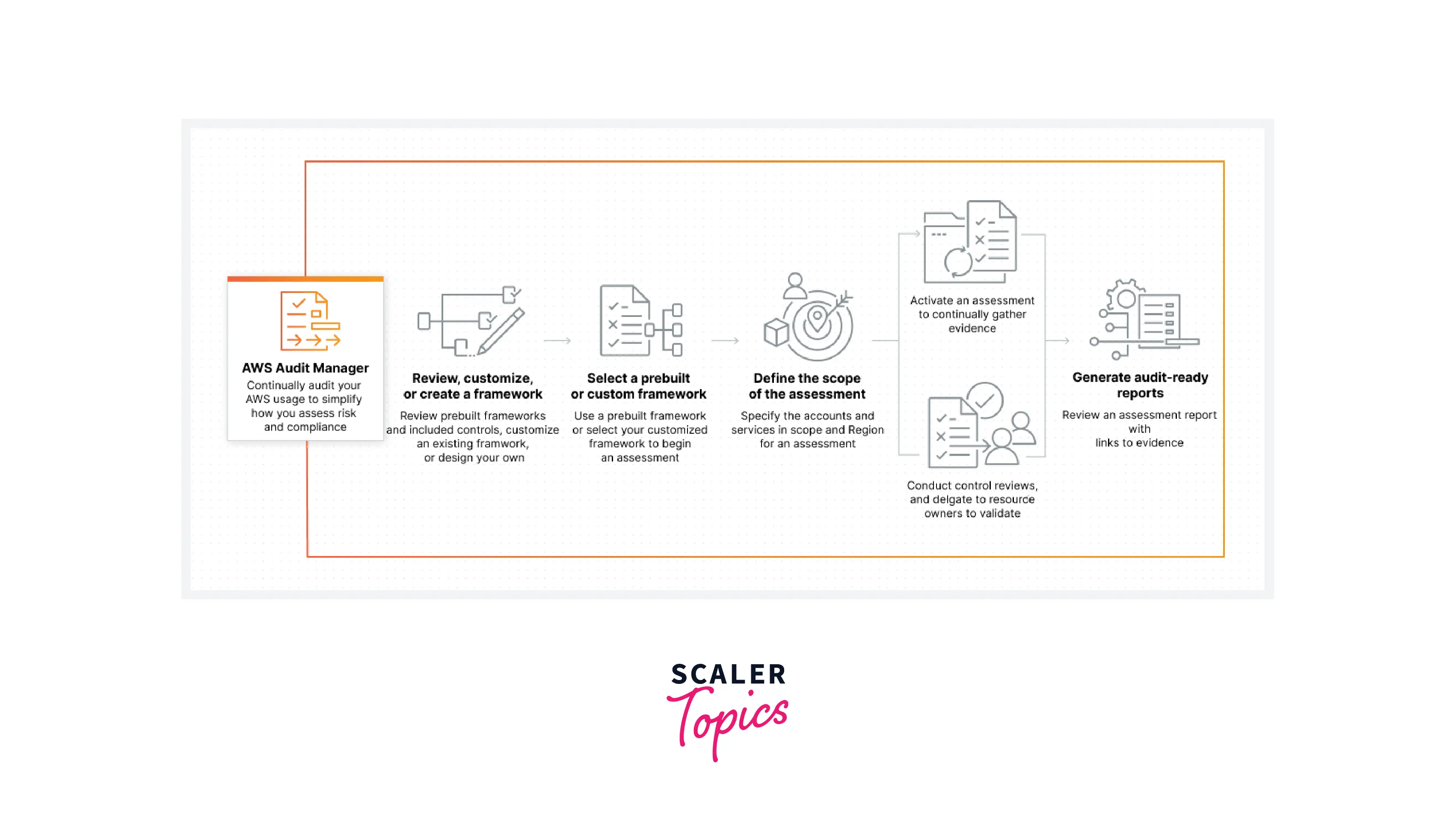
1. Review, Customize, or Create a Framework: Go to the AWS Management Console and select the AWS Audit Manager option. Review predefined frameworks and included controls, modify an existing framework, or define your own framework.
2. Select a Prebuilt Framework or Custom framework: Use the pre-built framework or your own customized framework to start an assessment.
3. Define the Scope and Activate Your Assessment: Specify the services/accounts in a region, and activate the assessment to continuously gather evidence.
- Explore Audit Manager - Upload evidence collected manually for your hybrid environment. Read the user guide >>
1. Creating an Assessment (Audience: Audit owners)
2. Reviewing a Control Set (Audience: Delegates)
- Contact an Expert - Learn more about how to audit the AWS service usage. Contact us >>
Customizing AWS Audit Manager
Prerequisites
- Set up AWS Audit Manager. Configure an assessment report destination in the Amazon Audit Manager settings via the AWS Audit Manager console. Make a new folder for evidence within the bucket, followed by a directory. AWS Audit Manager will then store our assessment reports in this Amazon S3 bucket (for example, s3:/s3-customauditmanagerframework—/evidences/).
- Create an IAM user with Audit owner permissions. We can use the AWS Audit Manager Administrator Access policy as a starting point for this lab, but we should restrict these permissions as required.
Create a Custom Control
We'll configure a custom control consisting of three data sources. Each data source gathers evidence in accordance with the evaluation of a particular AWS Config rule.
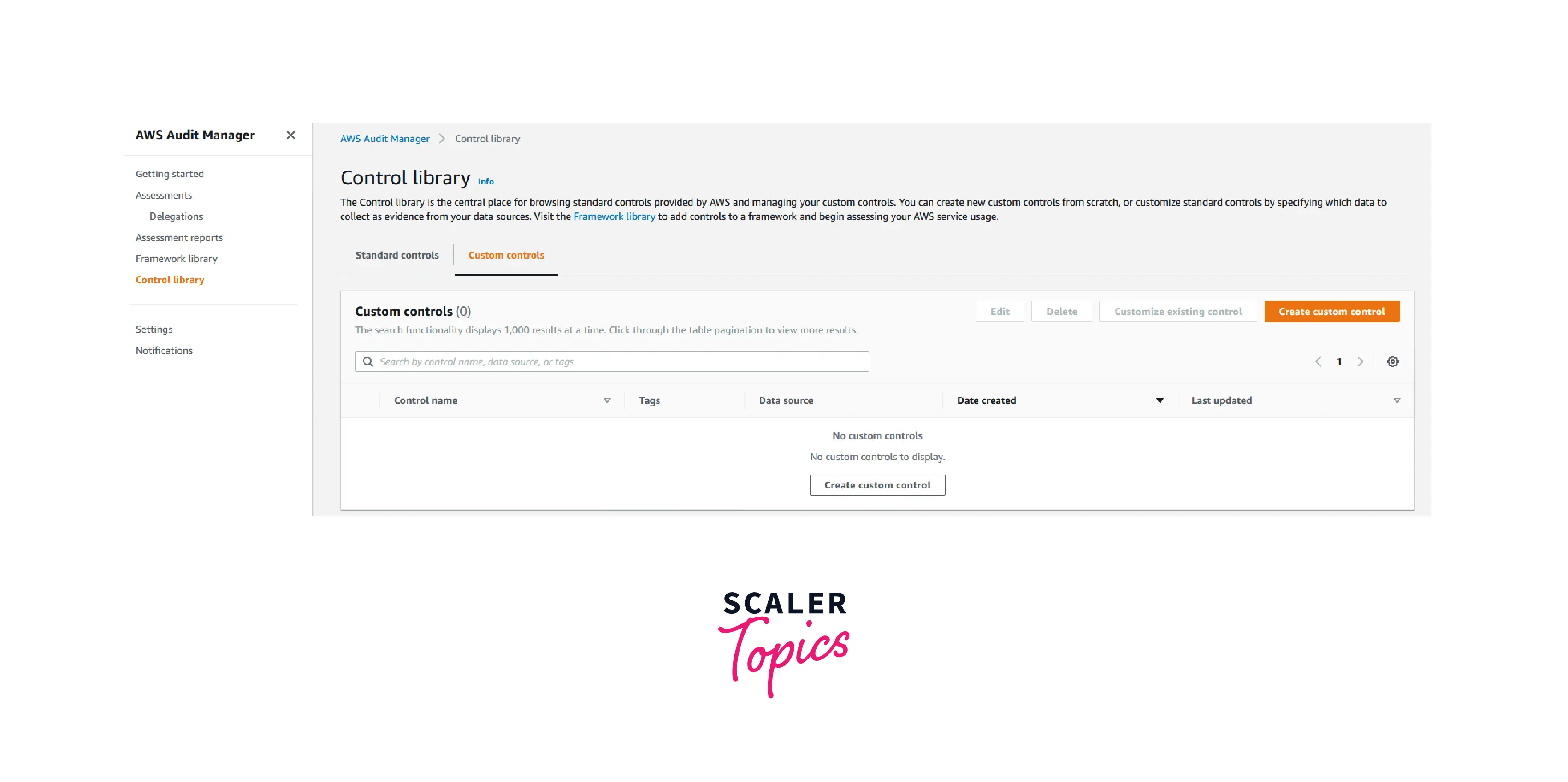
- In the Amazon Audit Manager console, select Control library from the navigation pane on the left side, followed by Create custom control.
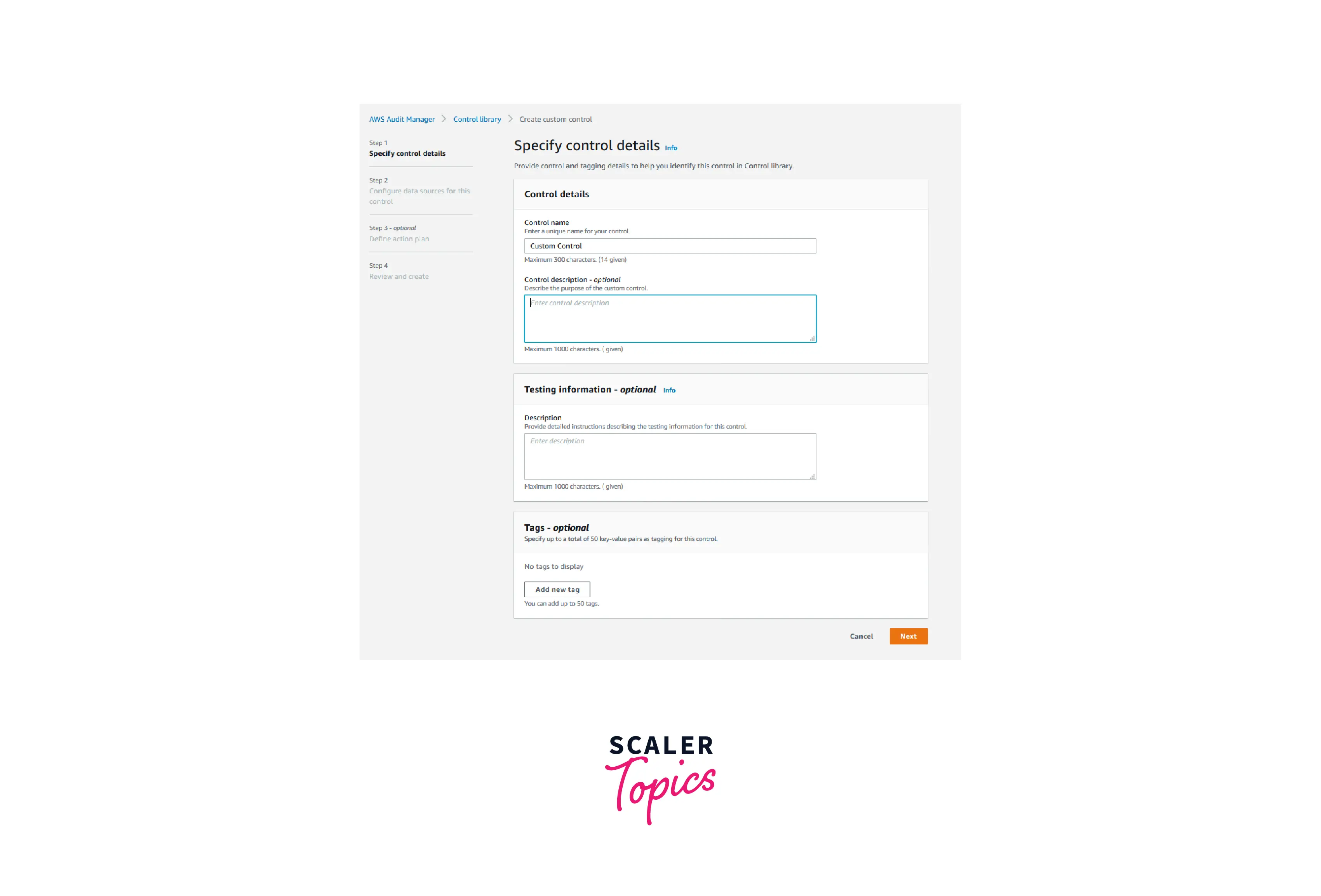
- Enter a name (such as Custom Control) and an optional description under Control name, then click Next.
- In the next step, select Automated evidence within the Select an evidence collection method field. Choose Compliance checks for resource configurations from AWS Config in Select an evidence type by mapping to a data source and choose CLOUD_TRAIL_ENCRYPTION_ENABLED within Specify an AWS Config Rule. To add the data source, select Add data source.
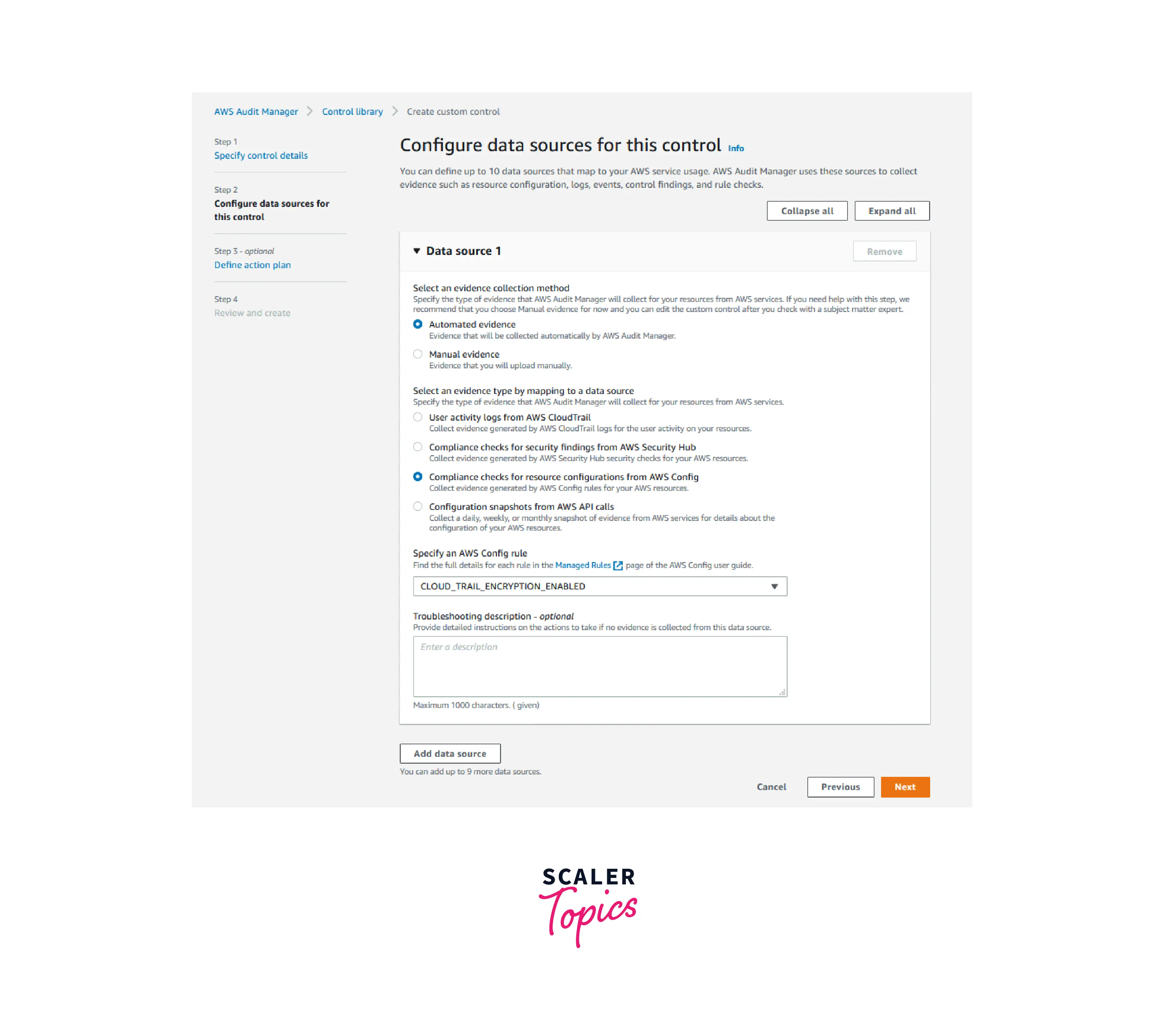
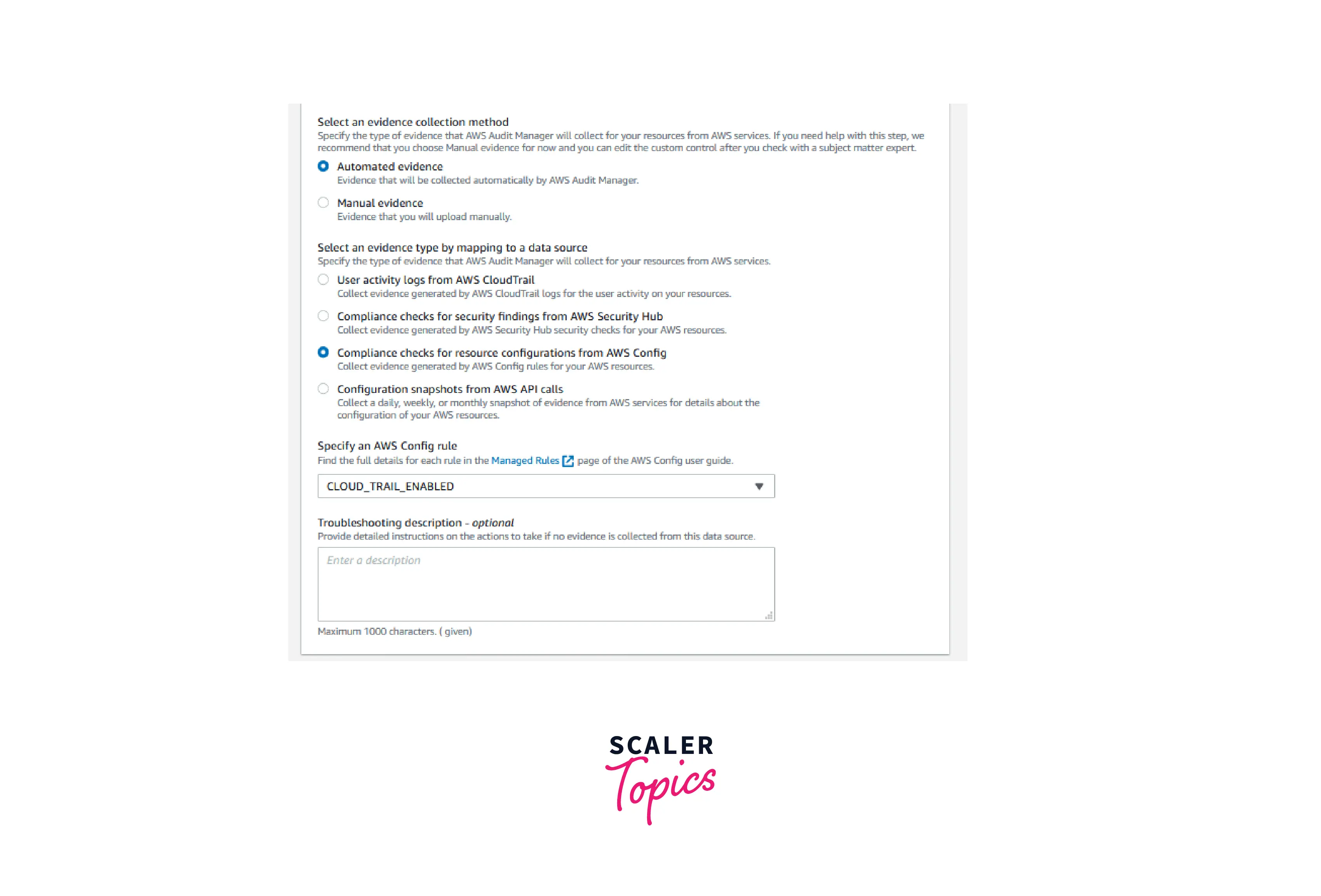
- Add further data sources. Follow the instructions in Step 3 to locate additional data sources. Add the AWS Config Rules CLOUD_TRAIL_ENABLED and S3_ACCOUNT_LEVEL_PUBLIC_ACCESS_BLOCKS as data sources. Choose Next.
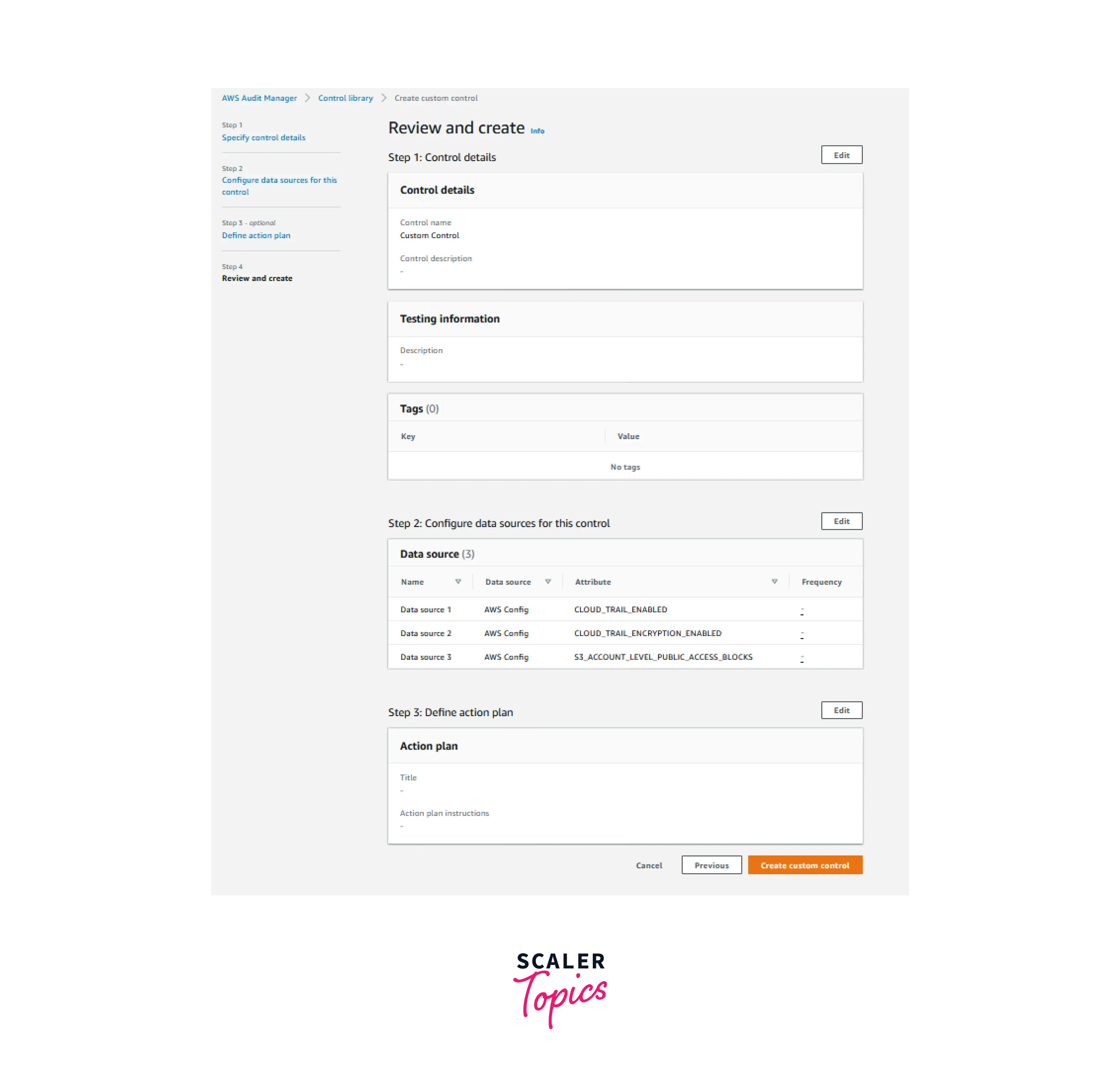
- Skip defining the action plan on the Review and create screen and select Create custom control instead.
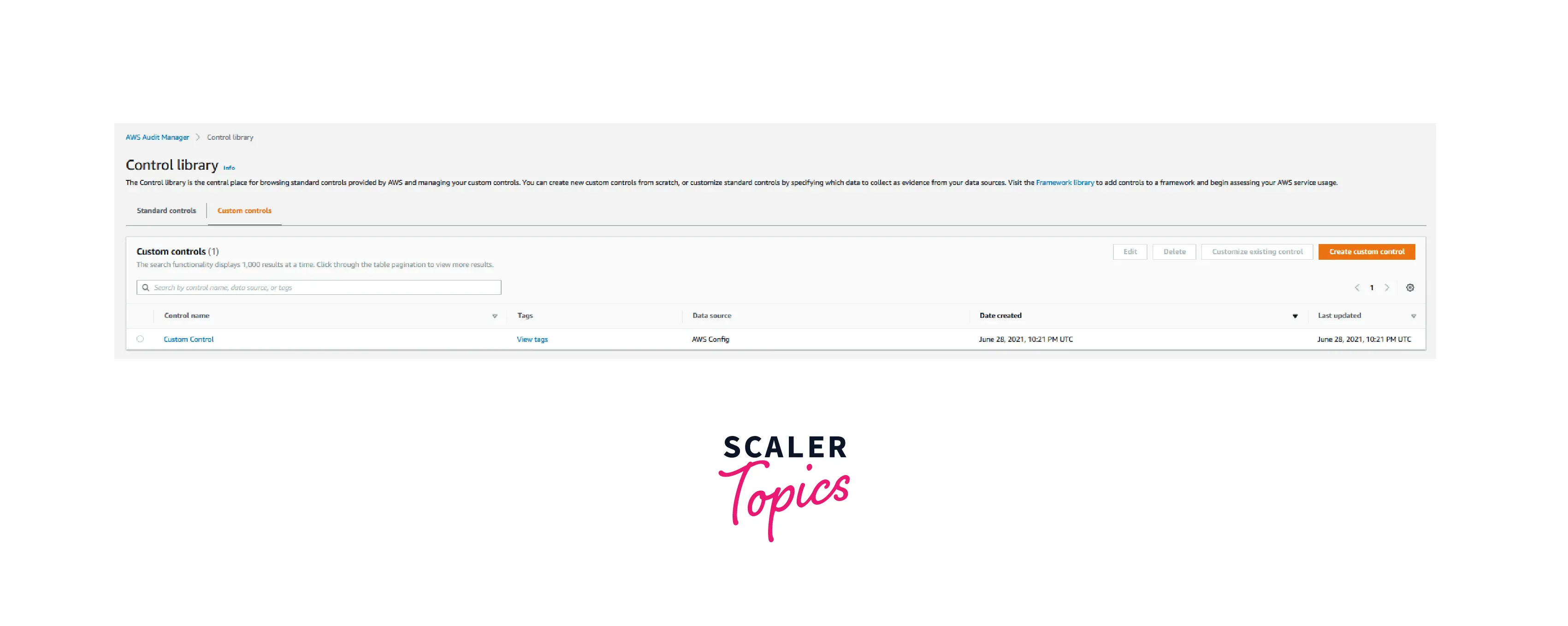
- The Custom control displayed in the Control library is represented in the figure below:
Create a Custom Framework
Custom frameworks enable you to organise controls into control sets according to your specific needs. Using the custom control you created in the previous section, follow these steps to create a custom framework.
- Select Framework library from the left panel, and then select Create custom framework.

- In the Specify framework details field, enter the framework's name (for example, Record Custom Control). Select Next after entering an optional compliance type and description.
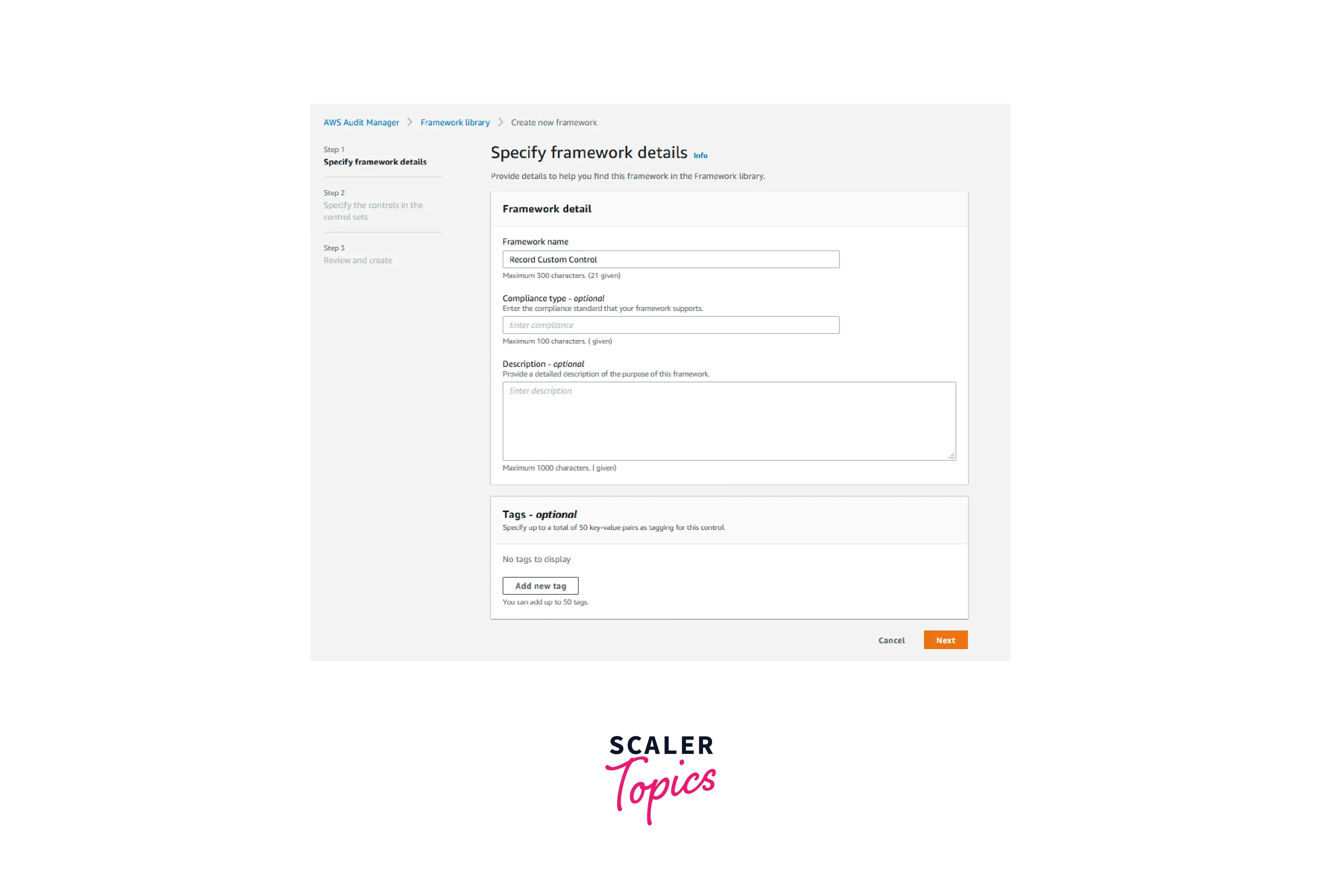
- Provide a name for the control set in Specify the controls in the control set and below the Control set name (for example, Custom Control Set). Select Custom controls and then Add to control set under Select control type. The custom control that you previously created should appear under Selected controls.
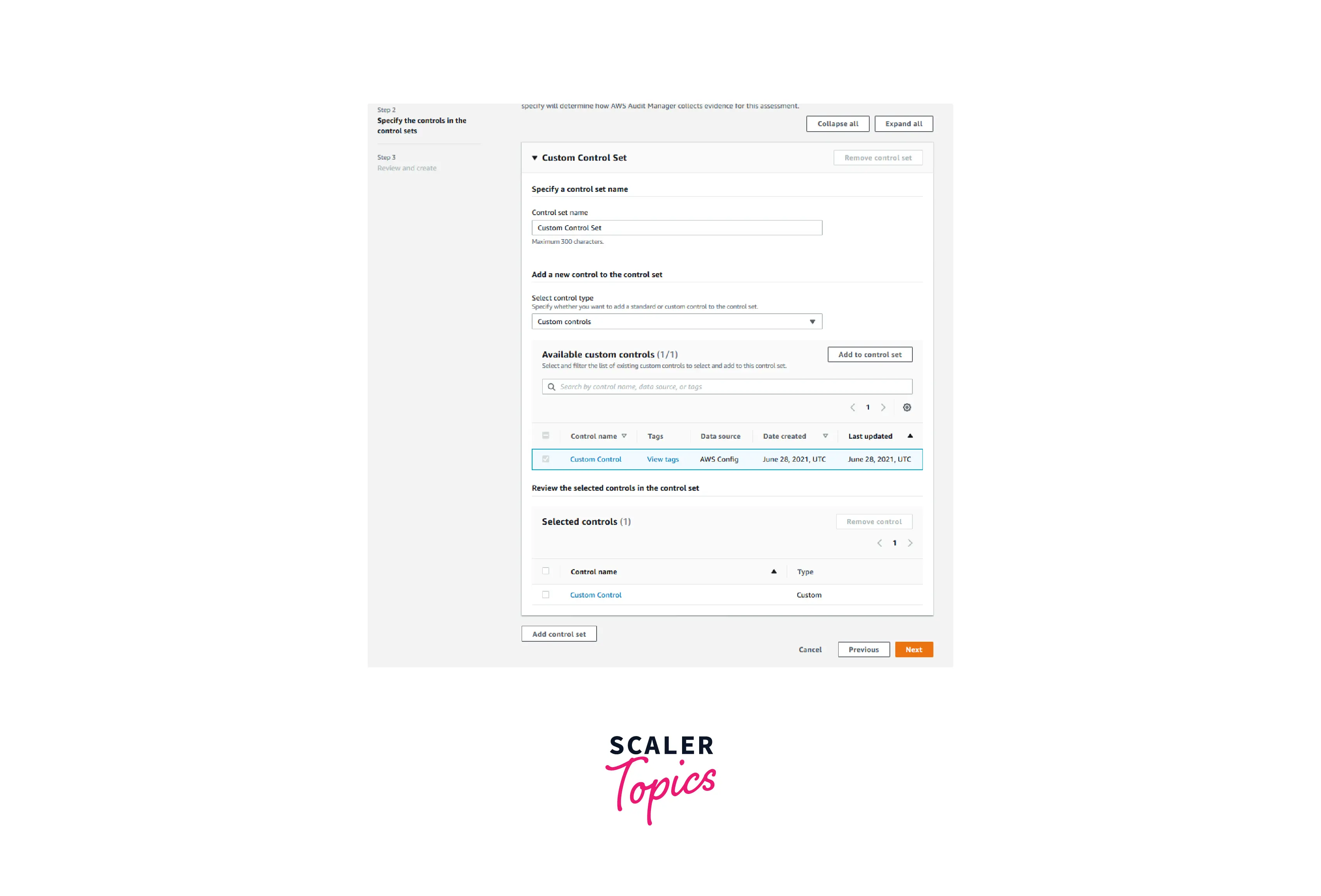
- Select Create custom framework from the Review and create screen.
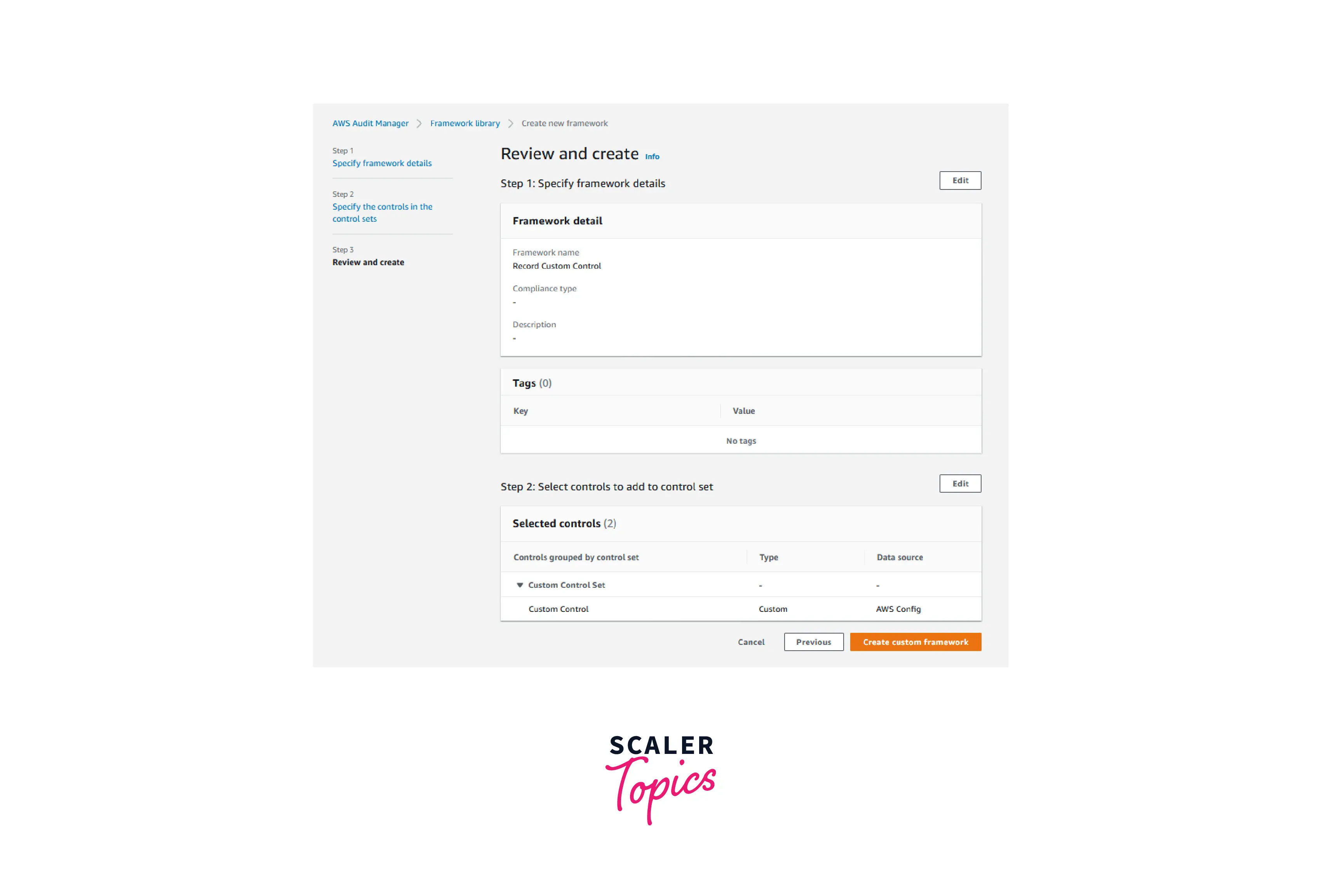
The below image shows the custom framework that consists of the custom control which we had previously configured.
Create a Custom Assessment
An Audit Manager assessment is an AWS Audit Manager framework implementation. It gathers the evidence associated with the AWS Config Rules you created, converts it into an auditor-friendly format, and attaches it to the framework's custom control.
- Select Assessments from the left navigation pane, then click Create assessment.
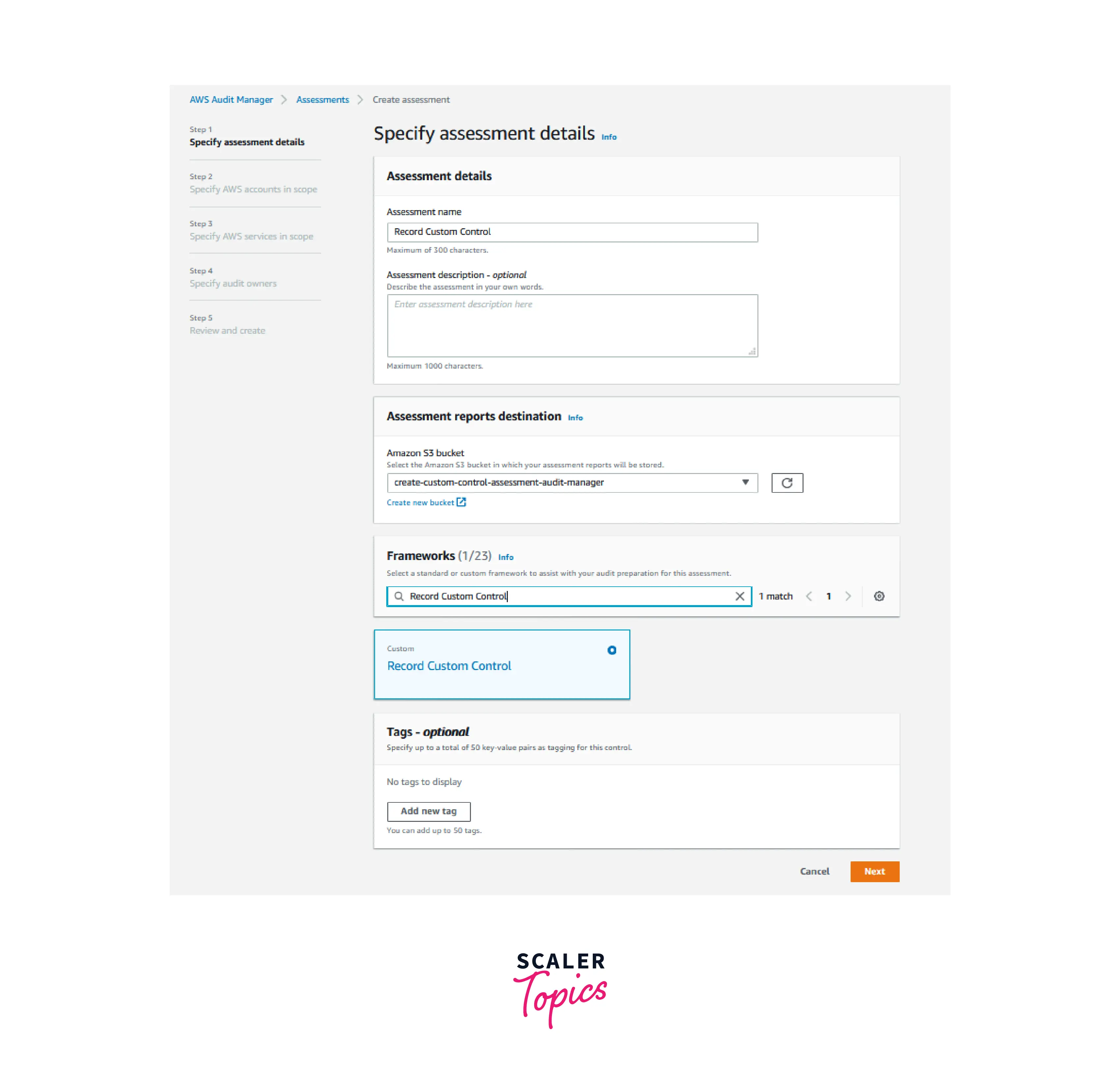
- Under Assessment Details in Specify assessment details, fill any name (such as Record Custom Control). In the Assessments report destination field, select the Amazon S3 bucket from the prerequisites section of Step 5. Select the Record Custom Control under Frameworks, then click Next.
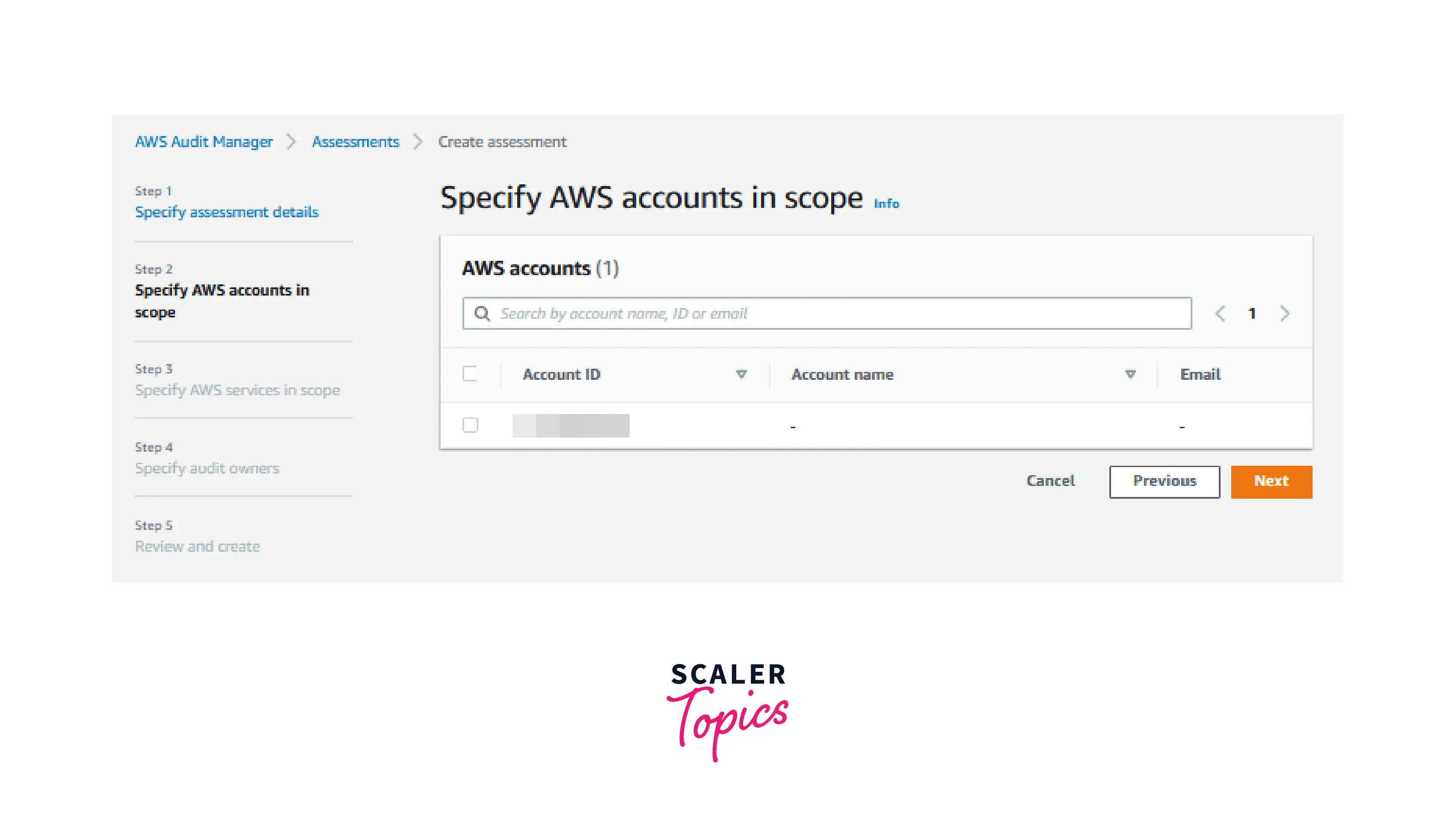
- Select the account in scope for the assessment in Edit AWS accounts in scope and then click Next.
 )
)
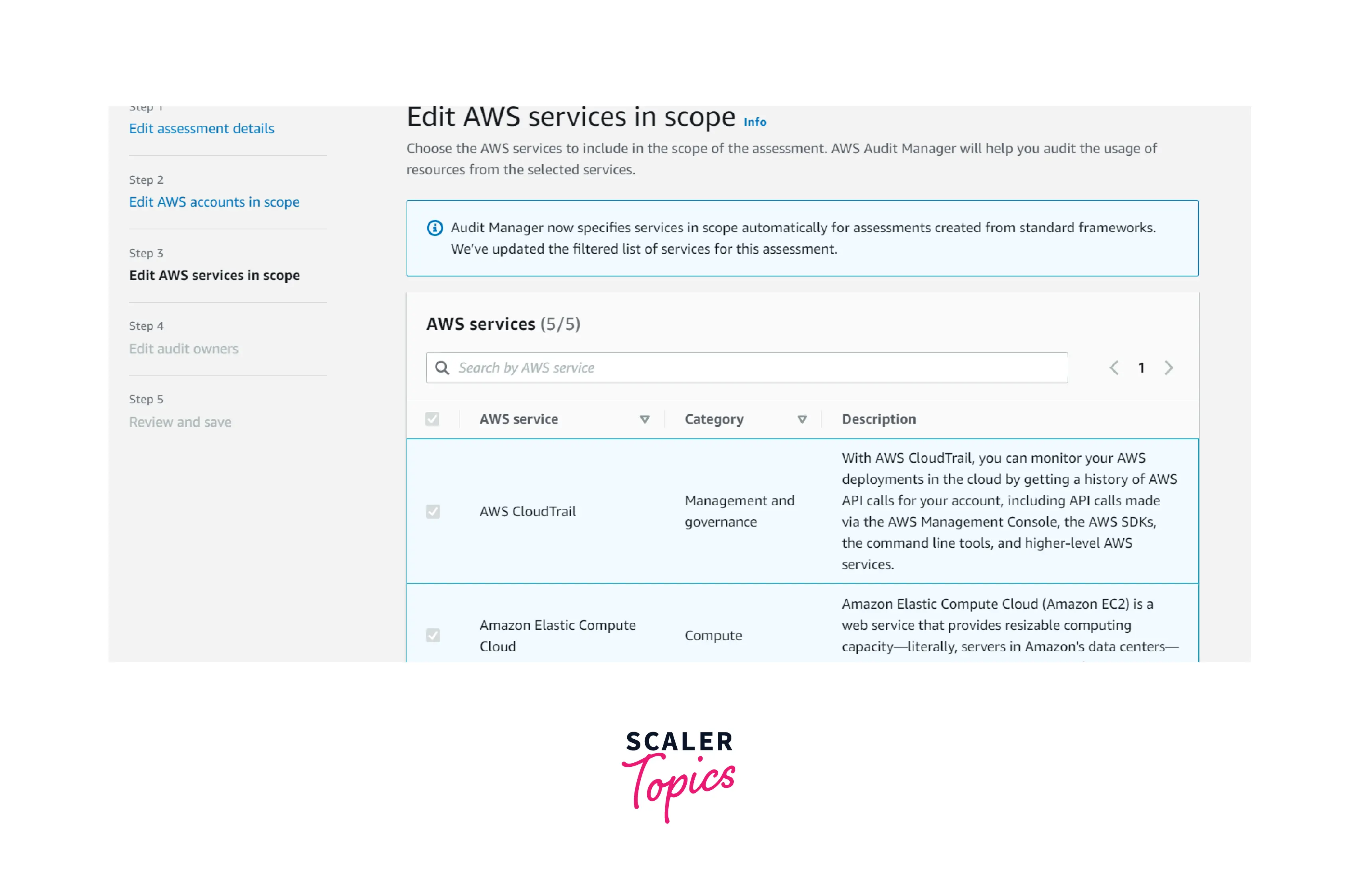
- Select all AWS services automatically detected by Audit Manager and then click Next under AWS services.
- Select the Audit owner user you created in Step 4 in the prerequisites section under Specify audit owners, and then click Next.
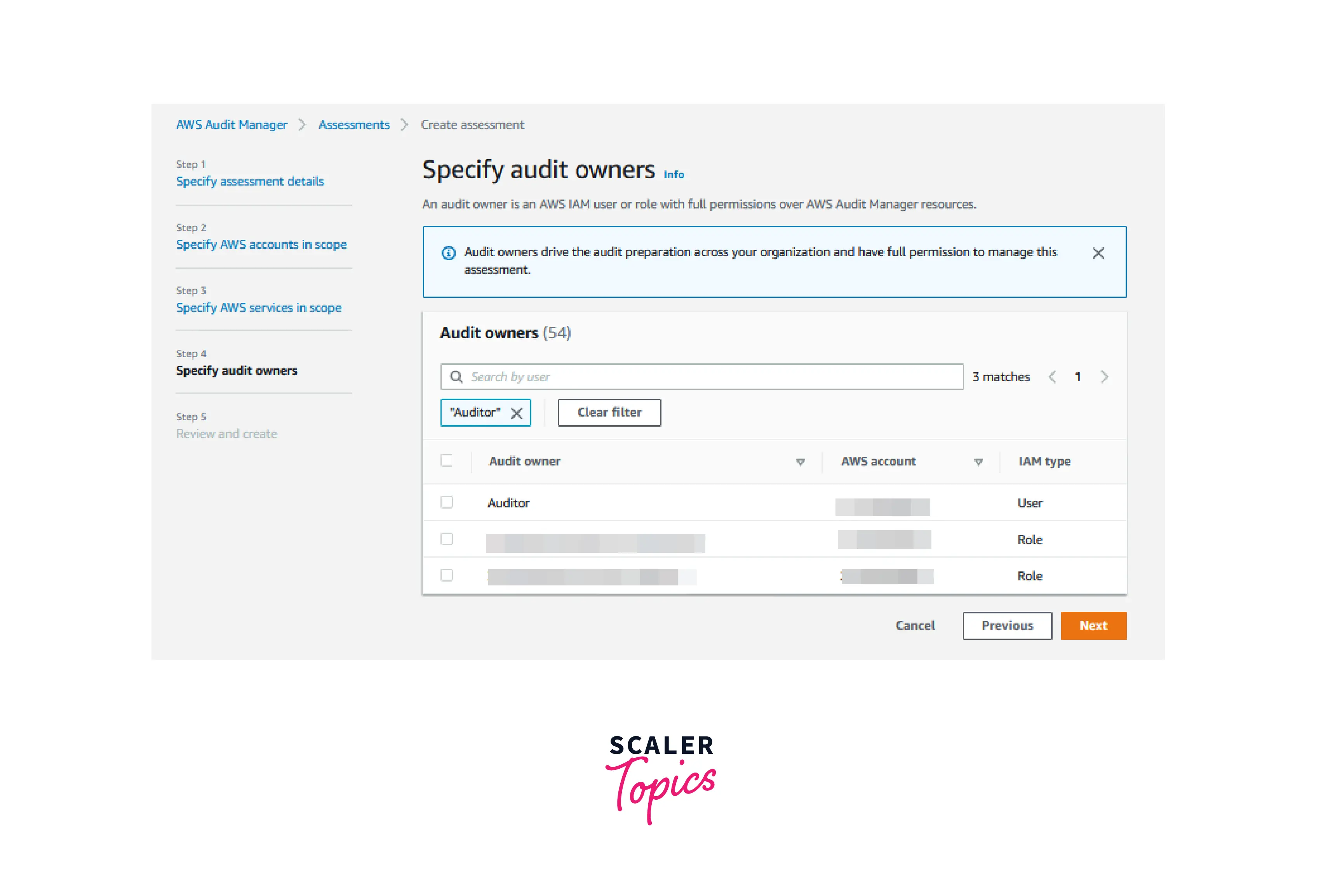
- Select Create assessment on the Review and create page.
Cleanup
Follow the steps to delete the custom framework, and then delete the Audit Manager-created custom controls.
Benefits and Limitations of AWS Audit Manager
Benefits of AWS Audit Manager
- Ensure Evidence Integrity: AWS Audit Manager stores evidence in a secure location where it is unmodified.
- Create Reports for Auditors: We can generate assessment reports that summarise the relevant evidence gathered for our audit.
- Support Cross-Team Collaboration: We can delegate control sets to subject matter experts who can evaluate related evidence, and provide.
- Customized Frameworks: We can create our own frameworks with standard or custom controls to meet our specific internal audit requirements.
- Get Started Quickly: We can choose from a gallery of prebuilt frameworks that support a variety of compliance standards and regulations, and then initiate the automated collection of evidence to audit the usage of our AWS services.
Limitations of AWS Audit Manager
AWS Audit Manager is a valuable tool for companies that host their infrastructure and services on AWS. It performs admirably within its limited capabilities. But it is not a complete audit automation solution. Moreover, no audit automation tool can complete an audit, evaluate compliance, and generate a credible audit report. Other limitations include:
- Lack of direct communication with auditors.
- Limited capabilities in project management.
- Evidence collection is limited to AWS and the data sources supported by the platform.
AWS Audit Manager Alternatives & Comparisons
OpenSSL

It is an extensive toolkit for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. It is also a cryptography library for general usage.
Authy

We make the highest rated Two-Factor Authentication mobile app for consumers, a Rest API for developers, and a robust authentication platform for enterprises.
Ensighten

Ensighten is an all-inclusive website security company that provides compliance, enforcement, and client-side protection against data loss, ad injection, and intrusion.
AWS Amplify

A JavaScript library for front-end and mobile developers who are constructing cloud-enabled applications. The library is a declarative interface for multiple categories of operations, making it easier to incorporate common tasks into your application. The default implementation is compatible with Amazon Web Services (AWS) resources but is open and pluggable for use with other cloud services that wish to provide an implementation or custom backends.
Let's Encrypt

It is a non-profit organization that provides a free, automated, and open certificate authority (ISRG).
Conclusion
- AWS Audit Manager is a service that automates the collection of evidence so that we can continuously audit AWS usage.
- AWS Audit Manager is a tool in the Security category of a tech stack. It helps managers and third-party auditors manage applied for control reviews during audits.
- Depending on business requirements, users can design an evaluation using either a standard framework or a custom framework.
- Evidence is a document containing the information required to demonstrate compliance with a control’s requirements.
- Cloud security is a top priority at AWS, customers have access to data centers and network topologies designed to meet the requirements of the most security-conscious businesses.
- We can create our own frameworks with standard or custom controls to meet our specific internal audit requirements.
- AWS Audit Manager is a valuable tool for companies that host their infrastructure and services on AWS. It performs admirably within its limited capabilities.
