AWS Cloud Security
Overview
A concept of shared responsibility is offered by the AWS cloud. Your company is in charge of protecting its data and workloads, while AWS controls cloud security for its infrastructure. To assist you in putting your company's security policy into practice, Amazon offers various security services and capabilities, such as encryption, key management, and identity and access management (IAM).
Introduction to AWS Cloud Security
Amazon Web Services (AWS) is a renowned cloud service provider that offers several security measures. This essay will go through the security features that make AWS a safe cloud platform. AWS Security refers to a set of attributes, technologies, or features that make Amazon Web Services (AWS) a secure public cloud service provider. The demand for greater cloud security has grown along with the uptake of cloud services.
The best part about AWS cloud security is that it not only safeguards data, especially PII (personally identifiable information) like SSNs, bank account numbers, passport numbers, and so forth but also applications that access the data. Even the infrastructure (such as servers) on which apps are executed is safeguarded by cloud security. It is worthy of note that the way security is delivered depends on the cloud service provider being used and the cloud security options they offer.
AWS Cloud security is similar to that of on-premises data centers but without the facility and hardware maintenance costs. When you use the cloud, you don't have to worry about managing physical servers or storage devices. Instead, you monitor and protect the flow of data into and out of your cloud resources with software-based security tools.
Standards and regulations for compliance are another crucial part of security, as a slip-up here could cost your company money. The infrastructure of Amazon has received certification for practically all international compliance standards. The workloads you deploy on Amazon won't necessarily be compliant, though. You must be aware of your compliance obligations and implement the necessary security and privacy measures using the tools supplied by Amazon.
The AWS Cloud allows you to scale and innovate while keeping your environment secure and only paying for the services you use. As a result, you'll be able to acquire the security you require at a lower cost than you would with on-premises security.
As an AWS customer, you gain access to all of AWS' best practices in terms of policy, architecture, and operational processes, which were developed to meet the needs of our most security-conscious customers. Get the security controls, flexibility, and agility you need.
A shared responsibility model is supported by the AWS Cloud. You are in charge of cloud security, and AWS will handle it. This implies that, just like in an on-site data center, you maintain control over the security measures you put in place to protect your content, platform, applications, systems, and networks.
Numerous tools and features will be available to you, helping you achieve your security goals. AWS provides tools and services for network security, configuration management, access control, and data encryption.
Finally, accredited organizations from various countries and sectors regularly review and certify AWS environments. In the AWS environment, you can use automated tools for reporting on privileged access and asset inventory.
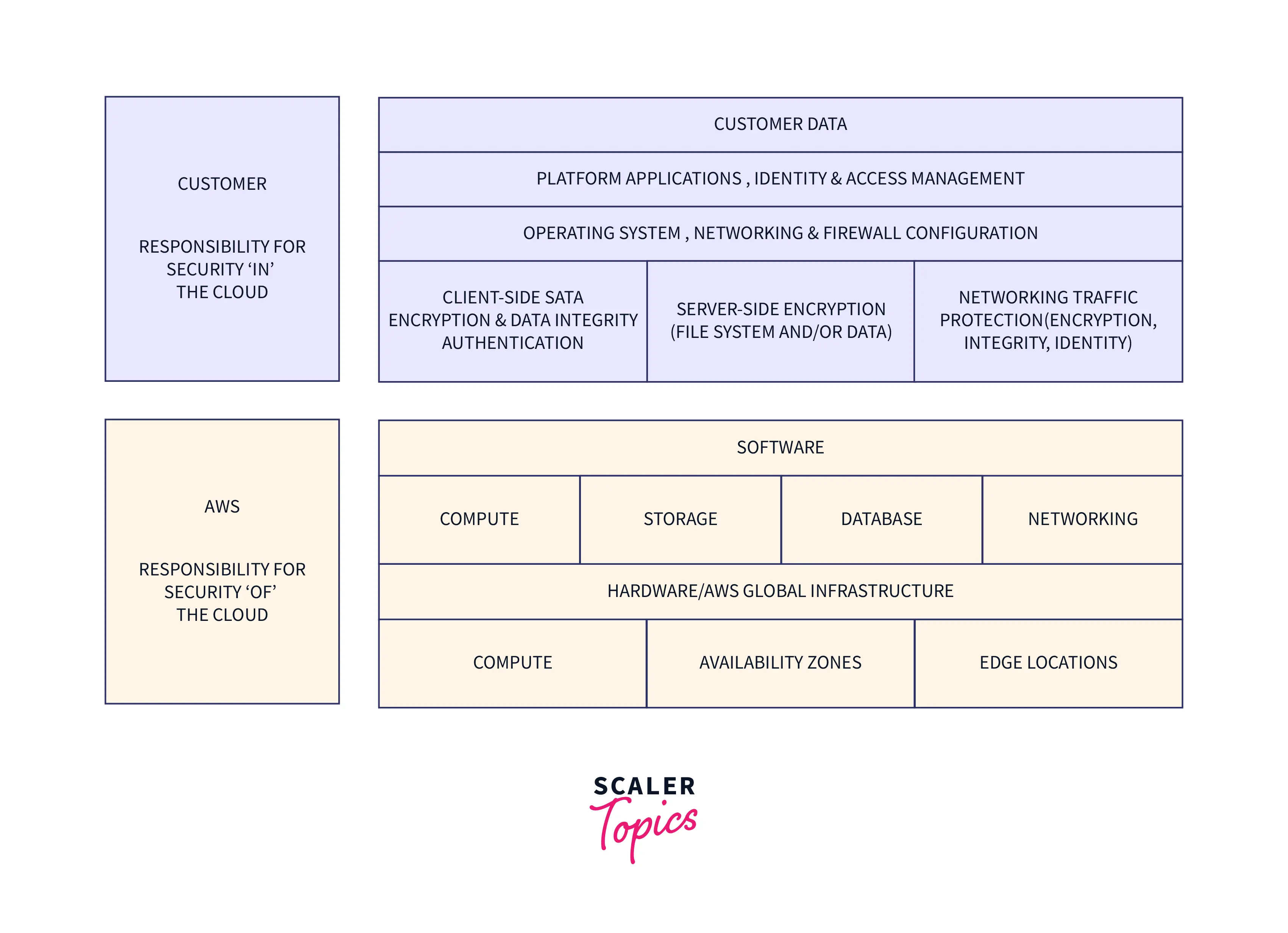
AWS Shared Security Model
Despite offering a secure infrastructure with built-in tools, firewalls, encryption, private connections, and cross-service Transport Layer Security (TLS), Amazon Web Services (AWS) only takes responsibility for the infrastructure layer and, as with managed services, the service layer as well. Operating systems, apps, networks, and third-party integrations are all the responsibility of the client. Although AWS offers features and tools that help customers meet their security obligations, it is up to the customer to configure them.
The AWS shared responsibility model is a concept of dividing responsibilities between AWS and a Customer.
- The Customer is you.
- AWS's responsibilities are the security of the cloud.
- Customer responsibilities are security in the cloud.
Responsibility of AWS
The security of the cloud is the responsibility of AWS. All infrastructure layers are managed by AWS.
Infrastructure layers include, among others:
- Data warehouses
- Software and hardware
- Virtualization
- Networking
Responsibility of a Customer
Every decision customers make in the AWS Cloud is subject to customer responsibility for security. You (the customer) have total control over your material. AWS services, software, and data access are managed by the customer.
Responsibility Differences:
| AWS | Customer (you) |
|---|---|
| Edge locations | Networking traffic protection |
| Availability zones | Server-side encryption |
| Regions | Client-side data encryption |
| AWS global infrastructure | Operating systems configuration |
| Hardware | Network configuration |
| Networking | Firewall configuration |
| Database | Platform management |
| Storage | Applications management |
| Compute | Identity management |
| Software | Access management |
Other AWS Security Services
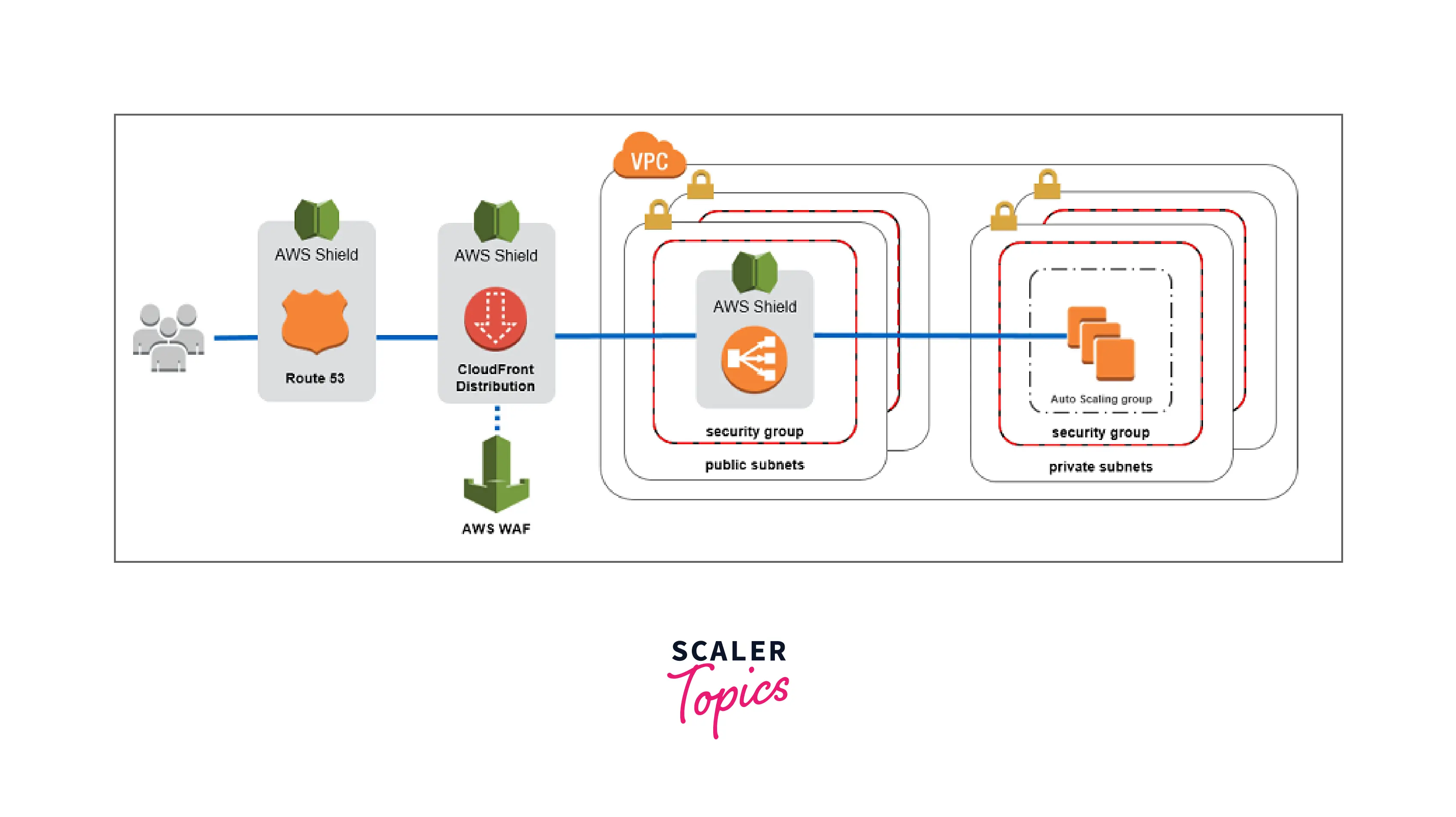
- AWS Shield: This is a managed DDoS (or Distributed Denial of Service) protection service that safeguards web applications running on AWS.There’s AWS Shield Standard which is always-on, using techniques to detect malicious traffic and AWS Shield Advanced which provides enhanced detection. On the AWS Management Console, look under Security, Identity & Compliance for AWS Shield.
- AWS WAF (Web Application Firewall): This protection service offers a firewall that guards against common attacks like SQL injection and cross-site scripting by inspecting the data being provided to your application. Through Cloud Front, WAF may safeguard websites that are not hosted by AWS. When requests are denied, CloudFront can be set up to show a specific error page. (A firewall is a security mechanism that guards who can access our websites and applications by monitoring and controlling incoming and outgoing network traffic based on pre-established rules).
- Identity and Access Management(IAM): We can control who has access to our AWS account, services, and even applications that are running in our account using this AWS service. IAM is a worldwide service that is readily accessible everywhere. Security concepts under this option include:
- IAM User: To represent the person or service that communicates with the services and apps running in your AWS account, you build an entity on the platform. AWS users have usernames and access credentials (a console password on the access key which includes an access key ID and secret access key).
- IAM Group: This is a group of IAM users that facilitates administering a user group based on permissions.
- IAM Role: This identity has a set of privileges or permissions that are not connected to a particular IAM User or IAM Group.
- IAM Policy: A policy, which can be associated with users, groups, and roles, is a mechanism to specify permissions at the granular level. AWS has a pre-defined list of policies, but you can also use JSON to design your unique policies.
It's intriguing to learn that AWS can assist you in maintaining control over your data's location, accessibility, and resource usage at any given time. This is just one of the numerous advantages of using an Amazon security solution, which is truly great. Kindly check the AWS Security page for further details.
Features of AWS Security
-
Security of AWS Infrastructure: To assist you in securing your data and controlling network access, AWS provides a range of security tools and services. For instance, network firewalls built with Amazon VPC let you create personal networks and control access to your instances or applications. Customers can manage encryption in transit across all AWS services using TLS. There are connectivity options available, including private or dedicated connections from your place of business or on-premises environment.
App and content delivery strategies can make use of layer 3 or layer 4 DDoS mitigation technologies as well as layer 7 DDoS mitigation technologies. All network traffic between AWS-secured facilities, both regionally and globally, is automatically encrypted.
-
Encryption: Elastic Block Store (EBS), Simple Storage Service (S3), Relational Database Service (RDS), and Redshift all come with built-in encryption from Amazon. Server-Side Encryption (SSE) with Amazon S3-Managed Keys (SSE-S3), SSE with AWS KMS-Managed Keys (SSE-KMS), or SSE utilizing Customer-Provided Encryption Keys are all options for essential independent control offered by the AWS Key Management Service (KMS) (SSE-C).
-
Monitoring and Logging: AWS CloudTrail monitors the AWS cloud environment including any API calls or console actions. Amazon CloudWatch provides standardized log data from all Amazon services, and Amazon GuardDuty can identify malicious or unauthorized activities by analyzing logs in real time.
-
Multiple Accounts: Customers may set up and manage their environments more quickly by using AWS Control Tower to handle numerous accounts and teams.
-
Cloud Security Governance: An organization can achieve its business objectives by using cloud security governance, a management strategy that enables effective and efficient security management and operations in the cloud environment.
It explains how to apply policies using the AWS cloud computing platform. The first step in creating a strong security culture is your choices regarding technology and governance. Everyone must be responsible for security, so make sure your platform, automation, and analytics make it simpler. AWS computing infrastructures are periodically evaluated, and certifications are given in various nations and industry sectors by accrediting agencies.
-
Application Security in Cloud Platform: Businesses may protect the data and applications they deploy in AWS cloud environments with the help of a set of policies, practices, and controls included in it. To secure the commercial value of your apps, you must first detect any vulnerabilities established throughout the software development process. You may discover, prioritize, and address application vulnerabilities and risks related to open-source or third-party code with the help of the AWS Marketplace solutions. Make use of MFA and other approaches. Then, to prevent unauthorized access to resources, the AWS Network and Application Protection services provide equally configurable options for traffic inspection and filtering. With fine-grained security, it safeguards you at the host, network, and application levels.
-
Identity and Access Control: For setting up, implementing, and monitoring user access controls and gaining access to the Amazon Console, service APIs, and cloud resources. AWS Identity and Access Management (IAM) defines user accounts and roles. Through AWS Multi-Factor Authentication and AWS Single Sign On, Amazon offers secure login (SSO).
AWS Compliance
AWS Cloud Compliance enables you to comprehend AWS's comprehensive procedures for maintaining cloud security and data protection. Compliance duties will be shared as systems are created on top of AWS Cloud infrastructure. AWS Compliance enablers extend traditional programs by connecting governance-focused, audit-friendly service characteristics with applicable compliance or audit standards. Customers can use this to set up and administer an AWS security control environment.
Shared security and compliance responsibilities exist between SAWS and the customer. This shared architecture can help reduce the operational load for the customer because AWS operates, manages, and controls every component, from the host operating system and virtualization layer down to the physical security of the buildings where the service is provided.
The client is in charge of configuring the security group firewall offered by AWS and the guest operating system (including updates and security patches). Because their responsibilities vary based on their services, how well they've been integrated into their IT infrastructure, and the rules and regulations that apply, customers should carefully consider the services they choose. Due to this shared duty, the deployment can be flexible and under customer control.
This distinction of responsibility is usually referred to as Security of the Cloud versus Security in the cloud, as indicated in the chart below.
The IT infrastructure of AWS is created and maintained in line with several IT security standards and best security practices. AWS participates in the following assurance programs, which are listed below in brief:
AWS SOC Compliance
For customers and auditors, AWS offers System and Organization Control (SOC) reports that are created by unaffiliated third parties. These are produced for clients by AWS Artifact and consist of:
- AWS SOC 1 Report.
- AWS SOC 2 Security, Availability & Confidentiality Report.
- AWS SOC 2 Security, Availability & Confidentiality Report, which only covers Amazon DocumentDB.
- AWS SOC 2 Privacy Type I Report
- The AWS SOC 3 Security, Availability & Confidentiality Report
AWS HIPAA
Because cloud service providers are not certified explicitly under HIPAA, AWS harmonizes HIPAA risk management criteria with FedRAMP and NIST 800-53 standards. How to harmonize NIST 800-53 with the HIPAA Security Rules is laid out in NIST paper SP 800-66.
PCI Compliance
The most rigorous certification available, PCI DSS Level 1 Service Provider, is followed by Amazon Web Services (AWS). Coalfire Systems Inc., an impartial Qualified Security Assessor, has evaluated it (QSA). The AWS Artifact site offers access to the PCI DSS Attestation of Compliance (AOC) and Responsibility Summary.
GDPR Compliance
The General Data Protection Regulation of the European Union is adhered to by AWS services (GDPR). However, a GDPR-compliant architecture does not ensure compliance because clouds use shared responsibility. To maintain compliance throughout their ecosystems, users can make advantage of the tools supplied by AWS. The specific functionalities that AWS offers to satisfy GDPR are as follows:
- Access control—limiting unauthorized people and service roles' access to resources.
- Logging and monitoring ensure visibility and supply information for audits.
- Data on AWS is encrypted by default, and there are several key management methods available.
Other Compliance Standards and Certifications
Additional compliance standards and certifications covered by AWS include:
- Global benchmarks—such as CSA, PSI DSS Level-1, SOC 1, 2, & 3, and ISO9001, 27001, 27017, & 27018
- North American benchmarks—including those published by the CJIS, FedRAMP, the US Department of Defense, FISMA, ITAR, Canada’s PIPEDA, and more
- In Asia—Japan’s FinTech, NISC, and FISC, Australia’s IRAP, Singapore’s MTCS Tier 3, Korea’s M-ISMS, and more
- In Europe—the UK’s G-Cloud and CYber Essentials Plan, France’s ASIP HDS, Germany’s C5, and more.
AWS Security Best Practices
You can apply the following best practices to improve security for AWS workloads.
- Encrypt Data: AES-256 bit encryption is used by the built-in encryption capabilities of AWS. Although free, AWS service-managed keys only offer server-side encryption. Customers can use an AWS-defined Customer Master Key (CMK), which AWS exchanges on an annual basis, or build their independent encryption infrastructure using the paid-for AWS Key Management Service (KWS).
- Backing Up Systems and Data: Use the 3-2-1 backup rule (3 copies, 2 locations, 1 of them on a different physical location—different service or area) while backing up your cloud systems and data. Make sure one of the two backups is stored on a cloud service other than AWS.
- Limit AWS Security Groups: Only necessary ports should remain open, and network administrators should offer access through security groups. To automate the configuration of Virtual Private Cloud (VPC) security groups, use AWS Config and AWS Firewall Manager. You may find out which networks your VPC networks are currently permitted to access using the Network Reachability rules package, which is included with Amazon Inspector.
- Secure Access to Cloud Resources: You can provide various users with different levels of access to cloud resources and APIs using Amazon IAM. Using the principle of least privilege, you should build policies based on roles rather than individual users. Create password guidelines that forbid the usage of flimsy and reused passwords.
- Centralize CloudTrail Logs: AWS CloudTrail logs should be written and encrypted to an S3 bucket to avoid deletion. Connect your logs to AWS services or Security Information and Event Management (SIEM) tools that provide centralized analysis. Logs from your Amazon deployment can be centrally located in the same log repository.
Some AWS Security Mistakes to Avoid
- Failing to Set Authentication: Make sure all critical AWS resources are, at the very least, authenticated; protocols should be in place to make sure nobody forgets to secure resources. Use strong password policies and multi-factor authentication (MFA) wherever possible for any accounts or service roles that require access to private information or the Amazon console.
- Unrestricted Outbound Traffic: To avoid data exfiltration after a security breach or in the event of an unintentional loss, outbound access should be prohibited. Instead of using 0.0.0.0/0, enter specified IP addresses or address ranges to stop your resources from connecting to IPv4 addresses that are not under your control.
- Hard-coding Secrets: Temporary AWS credentials are frequently provided using AWS IAM roles. Use ASW Secrets Manager to rotate, maintain, and retrieve database credentials, API keys, and other secrets for longer-lasting credentials. Sensitive data does not need to be hard-coded because these may be obtained via the Secrets Manager API.
- AWS Cloud Misconfiguration: Solutions for Cloud Security Posture Management (CSPM) ensure that cloud services, including the numerous EC2 security configurations, are set up correctly. Utilizing CSPM tools, you may continuously check the health of cloud setups, locating misconfigurations and other security vulnerabilities and automatically fixing them.
- Misconfigured S3 Buckets: Numerous data leaks are caused by improperly configured S3 buckets. An object storage service is S3. Each bucket in which data is kept has customizable access rights. Buckets are private by default, allowing only accounts with express authorization to access them. However, buckets can be set up to be accessible to anyone with an internet connection, which is frequently the case. Buckets are typically made publicly accessible because users find it handy to get around access limits. However, occasionally this is a genuine mistake.
Benefits and Limitations of AWS Security
Benefits of AWS Security
Scale Securely with Superior Visibility and Control
With AWS, you have complete control over your data's location, accessibility, and the resources your company is using at any given time. Wherever your information is housed, fine-grained identity and access restrictions along with continuous monitoring for near real-time security information ensure that the correct resources always have the right access.
Automate and Reduce Risk with Deeply Integrated Services
By minimizing human setup errors and allowing your team more time to concentrate on other duties that are crucial to your company's success, automating security tasks on AWS enables you to be more secure. To make it simpler for your security team to collaborate closely with developer and operations teams to write and deliver code more quickly and securely, choose from a wide range of tightly integrated solutions that can be combined to automate jobs creatively.
Build to the Highest Standards for Data Security and Privacy
AWS is careful to protect your privacy. Building on the most secure global infrastructure is possible with AWS, and you always retain ownership of your data, including the right to encrypt, relocate, and govern retention. Before leaving our secure facilities, all data moving across the AWS global network that connects our data centers and regions is automatically encrypted at the physical layer. There are additional encryption layers, such as all VPC cross-region peering traffic and TLS connections between customers or services.
Largest Ecosystem of Security Partners and Solutions
Utilize security technologies and consulting services from well-known solution providers you already know and trust to extend the benefits of AWS. We have carefully chosen service providers with a wealth of experience and a track record of success in achieving cloud adoption at every level, from initial migration to continued day-to-day management.
Get the Most Thorough Security and Compliance Measures
AWS frequently receives third-party validation for hundreds of international compliance criteria that we continuously monitor to support your compliance efforts. This will enable you to meet security and compliance standards for the financial, retail, healthcare, government, and other sectors.
Limitations of AWS Security
- New instances can adopt the group by default – potential unintentional security compromise
- Data loss through exfiltration attacks is made possible.
- Enables external security attacks e.g. port scans, DoS, and brute force password attempts.
- Difficult to manage, maintain, and audit.
- Enables internal security attacks e.g. packet sniffers and OS credential dumping.
- No alerting of a suspicious activity or unintentional security risks.
- Additional costs are dedicated to tech support which makes it costlier.
- Issues like downtime, backup issue, and privacy issue can take place.
- Teleporting this technology is not yet possible.
Conclusion
- In this article, we learned about what is AWS Cloud Security and how AWS Cloud security is similar to that of on-premises data centers but without the facility and hardware maintenance costs.
- We also learned about other AWS Security services like AWS Shield, AWS WAF, and Identity and Access Management(IAM). We got to know.
- This protection service offers a firewall that guards against common attacks and critical features of AWS Security.
- It included Security of AWS Infrastructure, Monitoring and Logging, and Cloud Governance.
- This article also taught about AWS Shared Security Model and AWS Compliance.
- In the end, we learned about various benefits of AWS Security, like building high-security data standards.
- This article also explained some of the crucial disadvantages of AWS Security, like data loss through exfiltration attacks made possible by this.
