What is AWS GuardDuty?
Overview
Amazon GuardDuty is a threat detection service provided by AWS. A cybersecurity technique called threat detection continually scans a system for harmful activity and produces warnings and security events. Teams can keep an eye on AWS resources and receive alerts and updates about possible dangers by using GuardDuty.
In order to safeguard the infrastructure and AWS cloud resources, security teams respond to these warnings and take preventative measures. This article outlines the AWS GuardDuty, its working and deep dives into its benefits and why it is needed?
What is AWS GuardDuty?
Consider yourself a security guard employed by a bank. It goes without saying that you would be vigilant and on the lookout for any unusual activity.
Similarly, GuardDuty acts as a security guard to the AWS account. It is a locally based intelligent threat detection service that monitors your AWS account for suspicious and unusual activities by looking at AWS CloudTrail event logs, VPC flow logs, and DNS logs. Then, it analyses log data in search of abnormalities and known malicious sources, including IP addresses and URLs, by comparing it to numerous security and threat detection feeds.
Working of AWS GuardDuty
To lower risk, Amazon GuardDuty continuously and intelligently detects threats to your AWS accounts, workloads, and data stored in Amazon S3.
It functions simply as a security service that monitors everything occurring in your account at the infrastructure level and notifies you of any suspicious activity. GuardDuty looks for three different kinds of threats:
- Compromised situations: GuardDuty can identify any odd increases in network traffic as well as resources that have been taken over, including EC2 instances that have been taken over by an external IP address.
- Reconnaissance: When an attacker does reconnaissance, they learn about the network. An attacker utilizes reconnaissance to communicate with the network's open ports, active services, etc. to gather information without actively using the network. GuardDuty detects behavior that can indicate snooping, such as unblocked port probing from a known malicious IP, VPC port scanning, and strange API activity.
- Insecure accounts: Common behaviors that point to an account penetration, such as API requests from odd places, modifications that erode the account's password policy, and API calls from known malicious IPs, are recognized by GuardDuty.
Three severity levels—low, medium, and high—are used by the service to classify its warnings.
- Threats with low intensity have generally been stopped without endangering resources.
- Threats of a medium intensity suggest questionable behaviour. This may involve a surge in traffic to domains with a connection to bitcoin, which may indicate cryptocurrency mining.
- Threats with a high intensity of severity point to a compromised resource and should be remedied right away.
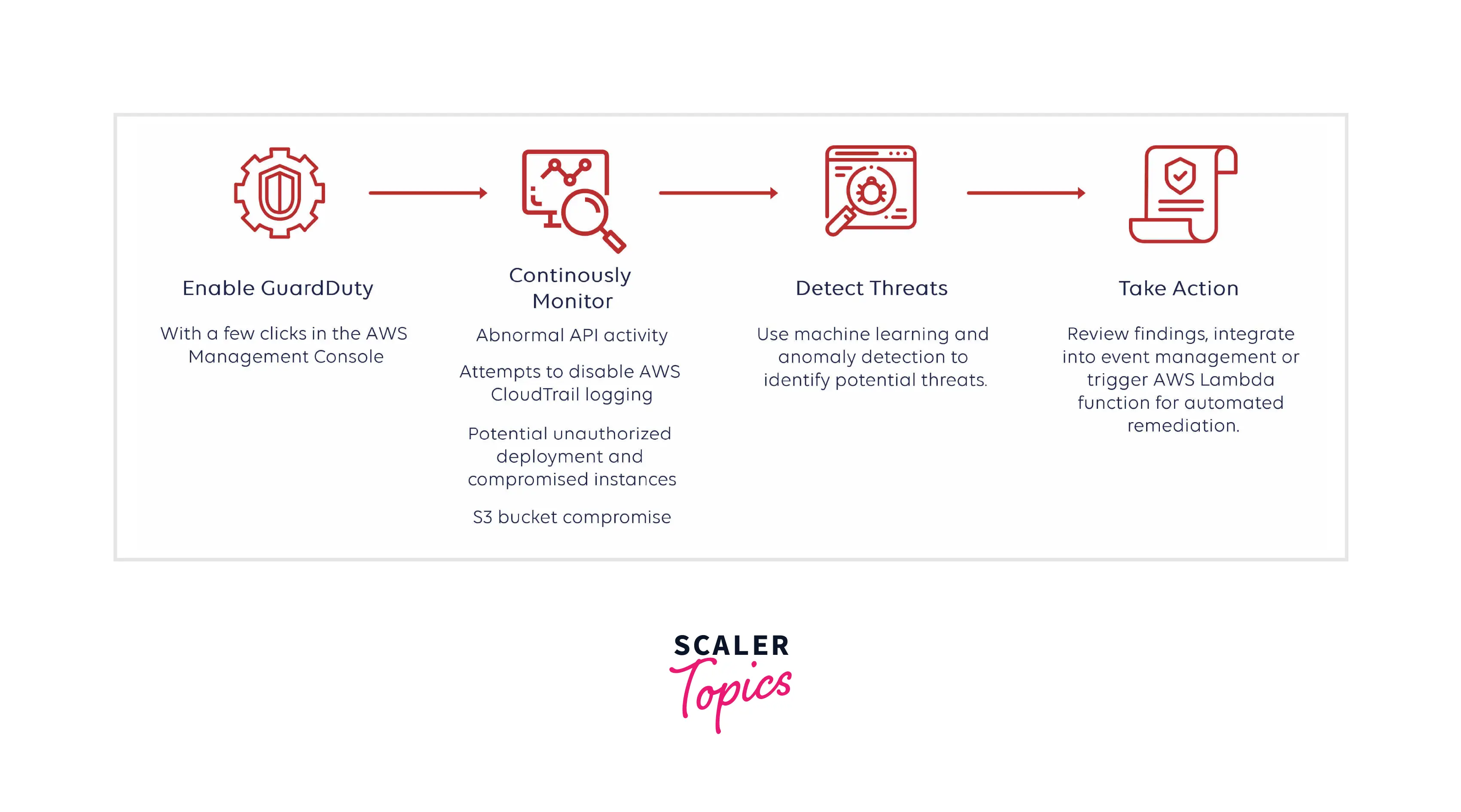
Advantages Of AWS GuardDuty
- The key advantage of the GuardDuty is that it is an active service monitoring and identifying abnormalities throughout your environment with the added benefit of having it driven by machine learning and leveraging various threat detection feeds, looking for any communications with un-trusted and hostile sources.
- Amazon GuardDuty not only finds threats but also makes it simple to automate your response, speeding up cleanup and recovery. GuardDuty utilizes Amazon CloudWatch events and Amazon Lambda to automate remedial steps. The security results from GuardDuty are instructive and useful for security operations. Details about the compromised resource and information about the attacker, such as IP address and location, are included in the results.
- You may enable GuardDuty across all of your existing and new accounts, thanks to Amazon GuardDuty's multi-account functionality. For simpler management, your security team may combine all of your company's results from many accounts under a single GuardDuty administrator account. It is simple to connect with an existing corporate event management system because the aggregated results are readily accessible through CloudWatch Events.
GuardDuty Findings
When GuardDuty notices unusual and possibly harmful activity in your AWS environment, it produces findings. These may be seen via the GuardDuty Console, CLI, or API operations.
The summary of a finding includes:
- Finding type: A succinct, accessible discussion of the potential security problem in finding this type.
- Security level: A finding's severity level is classified as either high, medium, or low.
- Region: The AWS region where the discovery was made.
- Count: The number of times GuardDuty produced the discovery following the activation of GuardDuty on your AWS account.
- Account ID: The account's ID in AWS where the behaviour occurred that caused GuardDuty to produce this discovery.
- Resource ID: This is the ID of the AWS resource that was used in the activity that caused GuardDuty to produce this discovery.
- Threat list name: This is the name of the threat list that contains the domain or IP address that was used in the action that caused GuardDuty to produce the discovery.
- Last seen: The time at which the action occurred that caused GuardDuty to produce this discovery (your local timezone if examined through the console, and UTC if checked through the CLI or API) is known as the last seen.
The Resources Affected component of a finding includes:
- Resource role is often set to Target due to the possibility of the impacted resource being the target of an attack.
- The resource's kind impacted is known as its resource type. Either AccessKey or Instance is the value here.
- The ID of the EC2 instance participating in the behaviour that caused GuardDuty to produce the discovery is known as the instance ID.
- Port is the connection's port number that was in use during the activity that caused GuardDuty to produce the discovery.
- Access key ID: This is the access key ID of the user whose action caused GuardDuty to produce the finding.
- Primary ID: This is the principal ID of the user whose action caused GuardDuty to produce the discovery.
- User type refers to the user's behavior during the activity that caused GuardDuty to produce the finding.
- User name of the user who participated in the action that caused GuardDuty to produce the finding.
The Action section of a finding contains the following:
- An example of an action is the finding activity type. One of the following four values: NETWORK CONNECTION, AWS API CALL, PORT PROBE, or DNS REQUEST, can represent this value.
- API: This is the name of the API action that GuardDuty used to create this discovery.
- Service name: The name of the AWS service (GuardDuty) that produced the discovery is given as the service name.
- Connection direction refers to the direction of the network connection that was seen during the activity that caused GuardDuty to produce the finding. There are three possible values: INBOUND, OUTBOUND, and UNKNOWN.
- The GuardDuty Protocol is the network connection protocol that GuardDuty saw in the behaviour that caused it to make the discovery.
The Actor portion of a finding includes:
- Location: The IP address engaged in the action that caused GuardDuty to produce the finding has location data.
- Information about the IP address's ISP organization that was involved in the action that caused GuardDuty to produce the conclusion.
- IP address: The IP address that participated in the behavior that caused GuardDuty to produce the finding.
- Port: This is the port used by the activity that caused GuardDuty to produce the discovery.
- Domain: The domain where the incident occurred that caused GuardDuty to provide the finding.
The Details portion of a discovery contains the following information:
- ThreatPurpose: This attribute specifies the main goal of a threat or possible assault. These values are possible:
- Backdoor: This shows that the assault has infiltrated an AWS resource and is able to connect to its home command and control (C&C) server to obtain additional instructions for harmful behaviour.
- Behavior: This value shows that GuardDuty has identified activity or activity patterns that deviate from the predefined baseline for a certain AWS resource.
- Cryptocurrency: This number shows that GuardDuty has found software connected to cryptocurrency.
- Pentesting is the deliberate use of AWS resources by owners or their authorised representatives to test AWS services for flaws such as open security groups or too liberal access keys.
- Persistence: It denotes the presence of a principal in your AWS environment who is acting differently from expected behaviour. Such a principal is not known to have updated the network configuration settings, the policies, or the rights related to AWS users or resources in the past.
- Policy: It denotes that your AWS account is acting in a manner that is contrary to advised security best practises.
- PrivilegeEscalation: This value alerts you to a particular principal's activity in your AWS environment that may be a sign of a privilege escalation assault.
- Recon: This value denotes the presence of a reconnaissance assault that is scoping for security holes in your AWS environment by probing ports, listing users, listing database tables, etc.
- ResourceConsumption: This number shows that a principal in your AWS environment is acting differently from expected behaviour. For example, such a principal has never previously started any EC2 instances.
- Stealth: This value denotes an assault that is aggressively attempting to cover its traces and its actions.
- Trojan: This result indicates that a harmful assault is utilising Trojan malware, which operate secretly. This software can occasionally appear to be a trustworthy application. Users occasionally, unintentionally launch this programme. Other times, this programme could be made to run automatically by taking advantage of a flaw.
- UnauthorizedAccess: This value denotes that GuardDuty has identified unauthorised users as the source of suspicious behaviour or a pattern of suspicious activity.
- ResourceTypeAffected: It identifies the specific AWS resource that this discovery indicates might be the target of an attack. GuardDuty findings can only identify EC2 instances, principals, and credentials as impacted resources.
- ThreatFamilyName: This identifies the type of threat or potentially harmful behaviour that GuardDuty is detecting in general.
- ThreatFamilyVariant: Identifies the particular ThreatFamily variation that GuardDuty is identifying. Attackers frequently create new varieties by significantly altering the attack's functioning.
- Artifact: It refers to a particular resource that belongs to an attack tool.
Trusted IP Lists and Threat Lists
- IP addresses that you have whitelisted for safe connectivity with your AWS infrastructure and apps make up trusted IP lists. For IP addresses in trusted IP lists, GuardDuty does not provide results.
- You are only permitted to have one uploaded trustworthy IP list per AWS account and per region at any time.
- Threat lists include IP addresses that are known to be dangerous. According to threat lists, GuardDuty generates findings. You can have up to six threat lists uploaded at once per AWS account and per region.
Use Cases Of AWS Guard Duty
- Learn about stolen passwords, unexpected Amazon S3 data access, API requests from known malicious IP addresses.
- Receive information about security event findings, including context, metadata, and details about impacted resources, and leverage the GuardDuty console interface with Amazon Detective to ascertain their root cause. Detective is a service that aids in the analysis and investigation of the underlying reasons for security alerts or other suspicious behaviour.
- Examine files in the Amazon Elastic Block Store (EBS), the AWS block storage system, for malware that could be causing odd behaviour in instances and container workloads operating on the Amazon EC2 platform.
- Utilizing the AWS Security Hub and Amazon EventBridge interfaces, and send discoveries to your chosen operational tools.
AWS GuardDuty Pricing
The fee for each service depends on the location you are utilising the service in. You can visit GuardDuty's AWS pricing page for a complete list of each region. You may use Amazon GuardDuty for free for the first 30 days after enabling it for the first time. You can also see how much Amazon GuardDuty would have cost you for those 30 days to help you estimate your payment if you decide to keep using the service. Charges for GuardDuty are as follows:
- Analysis of CloudTrail management events by AWS: GuardDuty monitors CloudTrail management events continually. Control plane, another name for management events, provides details on management actions taken on resources in your AWS account.
- **Analysis of DNS query logs and VPC flow logs: GuardDuty regularly examines DNS query logs and VPC flow logs.
- Analysis of authenticated CloudTrail S3 data events: When the GuardDuty S3 Protection feature is on, GuardDuty continuously examines authenticated CloudTrail S3 data events, keeping track of access and activity in all of your Amazon S3 buckets.
- Analysis of the Amazon EKS audit logs: When the GuardDuty Kubernetes Protection feature is turned on, GuardDuty continually examines the audit logs from Amazon EKS and minimises expenses by only processing the events required for security analysis.
- Data that has been associated to an Amazon Elastic Compute Cloud(EC2) instance or container workload having behaviour suspected to be malicious will have a duplicate of its Amazon Elastic Block Store (EBS) volumes analysed for malware when the GuardDuty Malware Protection feature is activated.
AWS GuardDuty VS Inspector
Before we begin the comparison, let's define Amazon Inspector. Amazon Inspector is a vulnerability management service that continuously scans your AWS workloads for vulnerabilities.
While Amazon GuardDuty helps you analyse your overall AWS account for possible risks, Amazon Inspector offers security audits of the settings and configurations of your applications.
When deploying your apps, you may set up Inspector first, and then soon after that, GuardDuty, to get warnings on potential dangers.
For Inspector, it's important to keep in mind that at the moment, only EC2 is covered when we talk about applications. You can install an Inspector agent to have it evaluate a wider variety of settings. In Inspector, evaluations are based on "rules" that let you know if you are following security best practices.
Conclusion
- In the article, we learnt about several of the capabilities of Amazon GuardDuty threat detection services.
- AWS GuardDuty is a smart service for threat detection. It examines billions of events from your AWS accounts' AWS CloudTrail (AWS user and API activity), Amazon VPC Flow Logs (data on network traffic), and DNS Logs (name query patterns).
- It employs machine learning to identify threats and its simple user interface enables people of any skill level to quickly diagnose security problems.
- It's also simple to deploy and has extensive connectivity with many AWS services.
