AWS Network Firewall
Overview
The managed network firewall service for VPC is called AWS Network Firewall (NF). It makes it possible to quickly deploy and manage web filtering, IPS, and IDS and a stateful inspection to safeguard VPCs. Network Firewall adapts automatically to traffic volume, ensuring high availability without requiring extra security infrastructure investment.
What is AWS Network Firewall?
A managed solution called AWS Network Firewall provides all Amazon Virtual Private Clouds (VPCs) with the immediate network security they require. Its goal is to detect and stop infiltration. There is no need to deploy or manage any infrastructure because this service is simple to start up and scales automatically with network demand. We can use a network firewall to filter traffic at the edge of our VPC, including traffic to and from internet gateways, VPN connections, and AWS Direct Connect. It supports Suricata-compatible rules and leverages the open-source intrusion detection system (IPS) for a stateful inspection.
Our Amazon VPC traffic can be monitored and secured in the following ways using the AWS network firewall :
- Only route traffic through accessible AWS service domains or endpoints with specific IP addresses, like Amazon S3.
- It is possible to restrict the kinds of domain names that can be visited from our applications by using custom lists of known dangerous domains.
- On the traffic coming into or going out of our VPC, deep packet inspection can be done.
- Stateful protocols allow for the detection of filter protocols, such as HTTPS, regardless of the port being utilized.
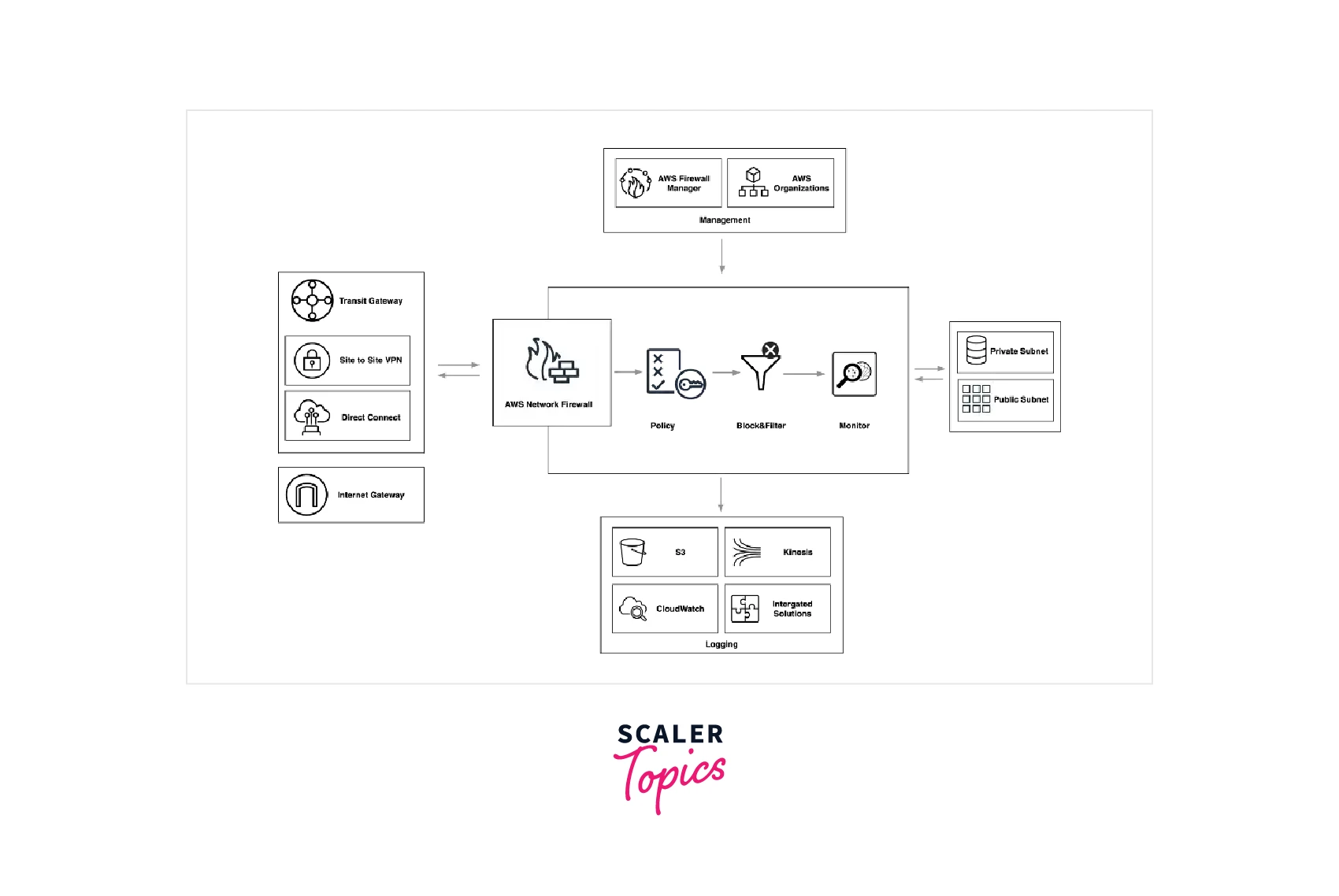
We may create firewall rules that offer us precise control over network traffic using the adaptable rule engine of AWS Network Firewall. Additionally, we can enable interfaces with managed intelligence feeds obtained by AWS partners and import rules that have previously been created in open-source rule standards. AWS network firewall works with AWS Firewall Manager to generate policies based on AWS Network Firewall rules and then implement them centrally across all of our VPCs.
How Does It Work?
The simplest configuration for AWS resources is shown in the figure below.
Later, a more thorough explanation will be provided.
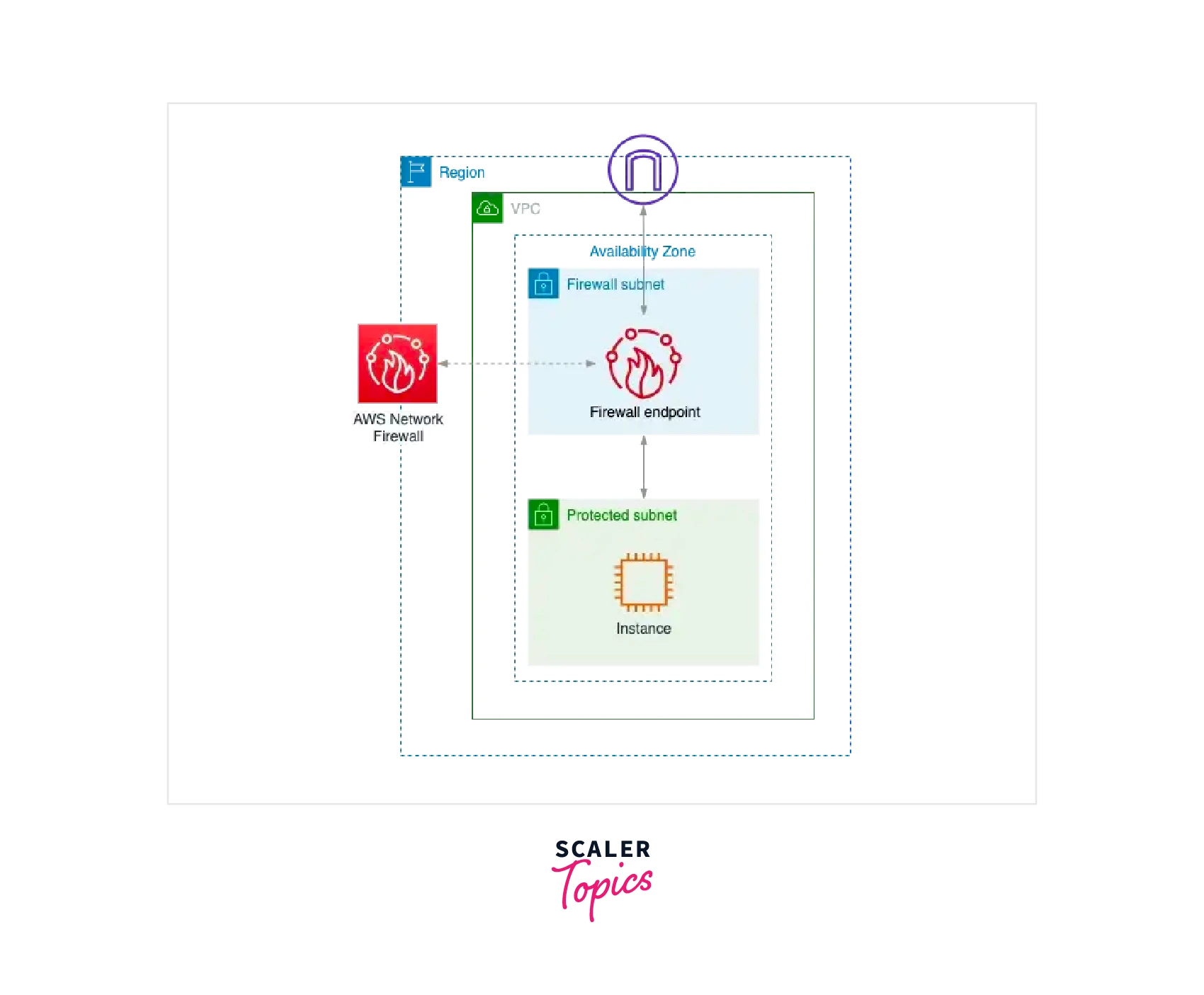
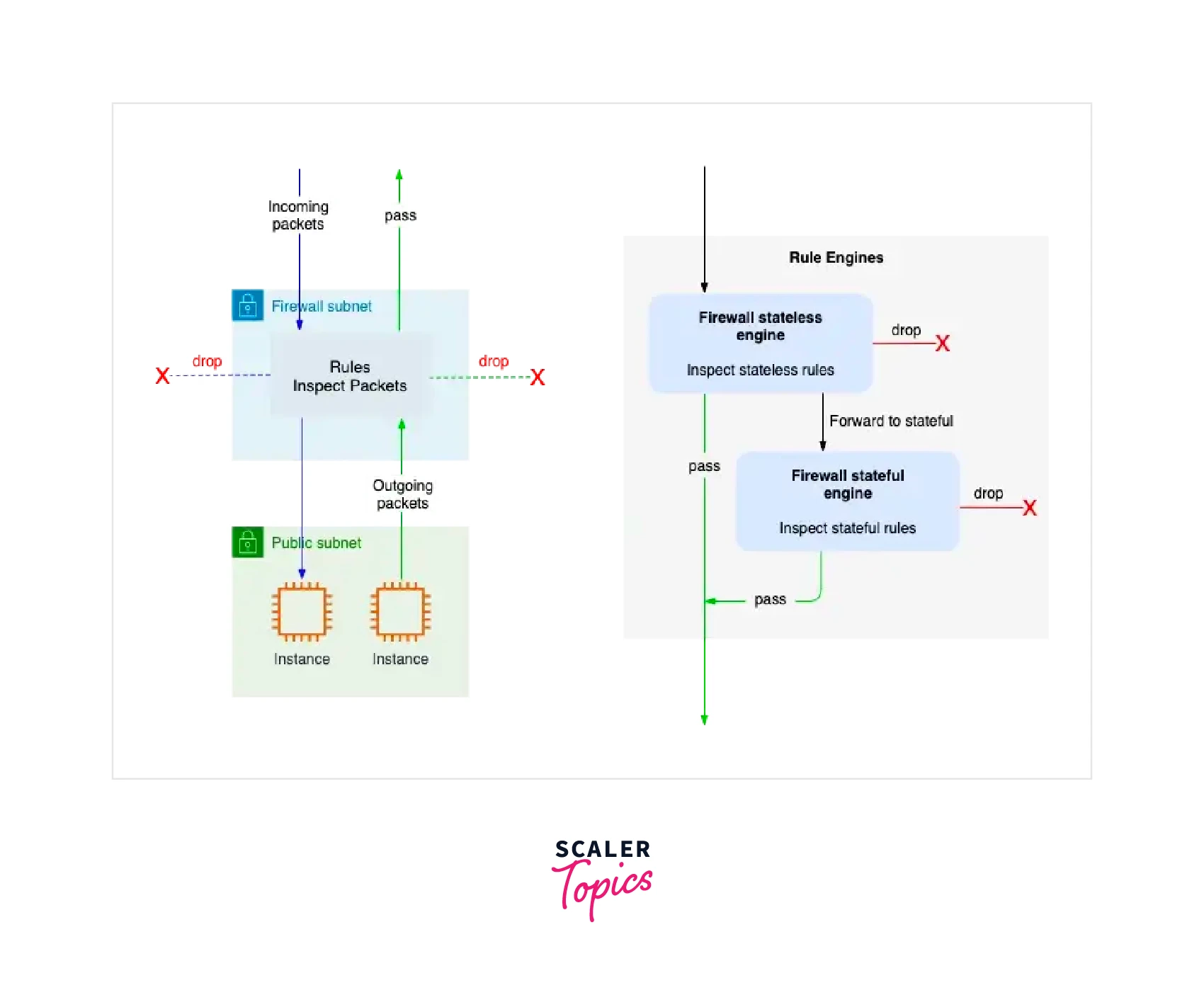
The logical diagram is depicted on the left side, and The rule engine packet flow is shown on the right side.
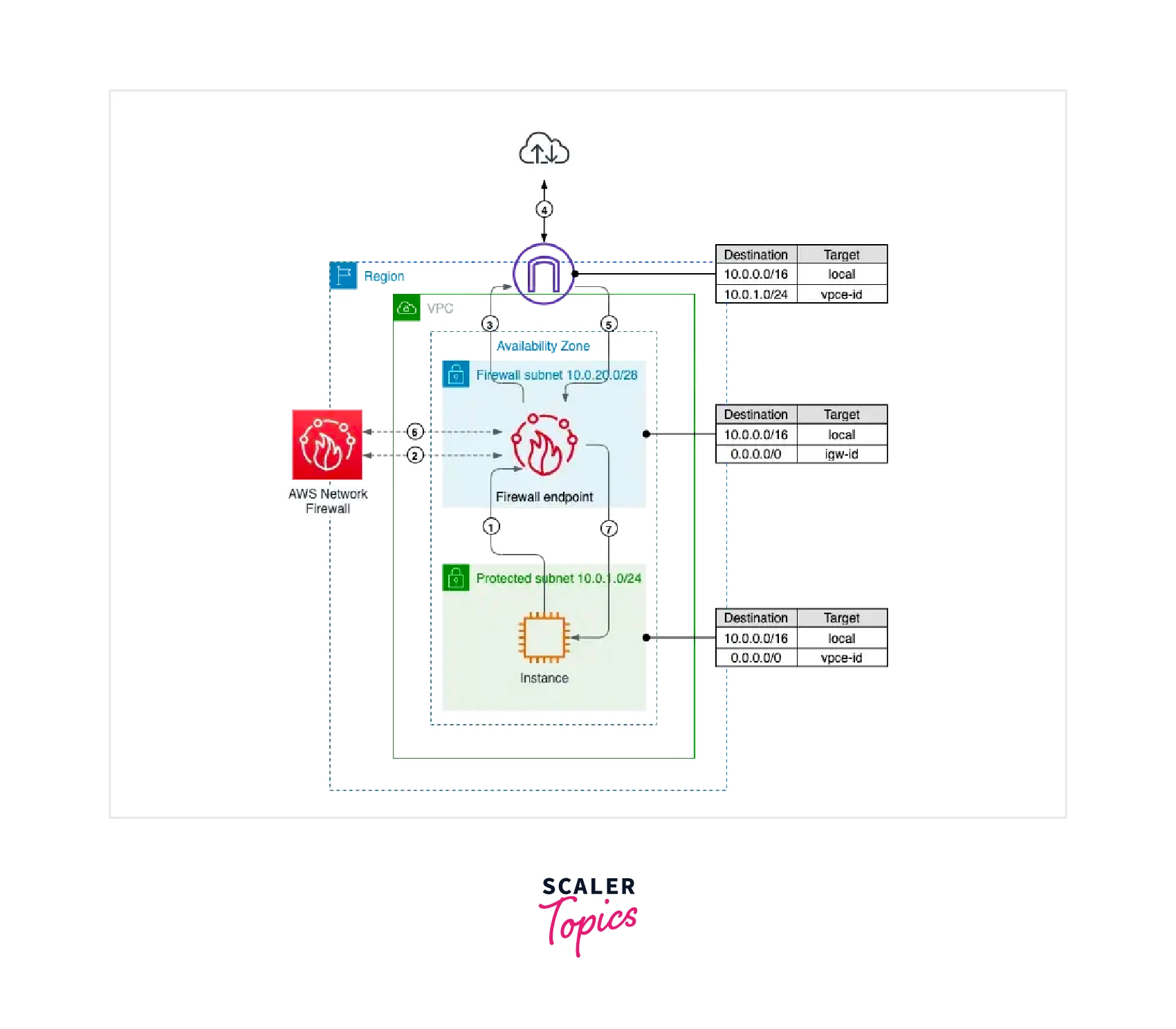
- Traffic should be routed equally to the Network Firewall endpoint so that the logic supplied by NF can be applied to the traffic-filtering logic.
- Identical to the PrivateLink VPC interface endpoint is this firewall endpoint. The main distinction is that it can be a target in a routing table. An NF endpoint is installed in a VPC's dedicated subnet (Firewall subnet).
- The firewall subnet is either public or private, based on the user application and deployment model. Allocate a subnet for each AZ in high reliability and multi-AZ installations.
- Each firewall subnet would have access to the firewall endpoint after NF is deployed. Similar to an interface endpoint, a firewall endpoint appears in the VPC route table target selection as vpce-id.
- Routing tables need to be set up as per the below figure to check any inbound or outbound traffic by NF.
Features of AWS Network Firewall
The following is a discussion of the AWS Network Firewall's features :
- Automatic Scaling and High Availability :
Redundancies are included in the AWS Network Firewall to guarantee that every traffic is continuously analyzed and tracked. A 99.99% uptime guarantee is included in the service level agreement for AWS Network Firewall. According to the volume of traffic, it automatically adjusts our firewall bandwidth up or down to maintain consistent, predictable performance and cut expenses. - Dependable Firewall :
For removing packets based on the source location or protocol type, this feature considers the environment of traffic flows. The stateful firewall's match criteria, which include a match setting for traffic direction, are the same as those for stateless inspection features offered by AWS Network Firewall. Using the adaptable rule engine of AWS Network Firewall, we can create firewall rules based on source/destination IP, source/destination port, and protocol. - Web Filtration :
For unencrypted web traffic, AWS Network Firewall enables outbound and inbound web filtering. For encrypted online traffic, Server Name Indication (SNI) is used to prohibit access to particular websites. It can also analyze fully qualified domain names in addition (FQDN). - Prevention of Intrusion :
The intrusion prevention system (IPS) of AWS Network Firewall offers active traffic flow inspection together with continuous network and application layer security against brute-force and vulnerability-based assaults. The signature-based detection engine may identify threat signatures based on characteristics like byte sequences and packet abnormalities. - Alert and Flow Logs :
Alert logs are rule-specific and offer further information about the rule that was activated as well as the session that did so. Flow logs, which contain one line per the direction of traffic flow, offer state information about all traffic flows flowing through the firewall. - Visibility and Centralised Administration :
Using the AWS Firewall Manager, we can centrally deploy and manage security settings for all of our services, VPCs, and accounts in AWS Organizations. To expand enforcement consistently and hierarchically, AWS Firewall Manager bundles AWS Network Firewall rules groups into policies that we may apply across our infrastructure. - Management and Customization of Rules :
Customers can execute Suricata-compatible rules that are sourced either internally, from in-house custom rule creation, or externally, from third-party suppliers or open-source platforms, using AWS Network Firewall. - a Diverse Ecosystem of Partners:
As AWS Network Firewall interfaces with AWS Partners, it can export logs to analytics tools and link with central third-party policy orchestration. AWS Network Firewall logs and security event data can be provided to outside analytics programs like Security Information and Event Management (SIEM) software for more visibility.
Why AWS Network Firewall?
- High Availability Managed Infrastructure :
The infrastructure of the AWS Network Firewall is managed by AWS, and it scales automatically with our network activity. We do not need to monitor our network security infrastructure because it can accommodate a large number of connections. - Flexible Defence Through Granular Command :
To safeguard particular workloads, the AWS Network Firewall provides a sophisticated rules engine that supports hundreds of custom rules. These rules are created in popular open-source rule formats and can be based on IP, port, protocol, domain, and pattern matching. - Uniform Administration of Policies Across VPCs and Accounts :
Together with AWS Firewall Manager, AWS Network Firewall offers centrally controlled security policies for all active accounts and VPCs. We may make sure that newly generated accounts and VPCs automatically enforce mandatory security standards. Additionally, it offers real-time information from Amazon CloudWatch for monitoring firewall activities.
AWS Network Firewall Deployment Models
Distributed AWS Network Firewall Deployment Model
- For the NF put into each VPC under the distributed deployment paradigm, protection is needed. Through VPC isolation, each VPC is independently safeguarded, and the blast radius is decreased.
- There is no requirement for any VPC to be connected to another VPC. Every AWS Network Firewall has the option of having a unique firewall policy or sharing a policy across many firewalls using reusable rule groups.
- This makes it possible to operate each AWS Network Firewall separately, lowering the risk of misconfiguration and limiting the damage.
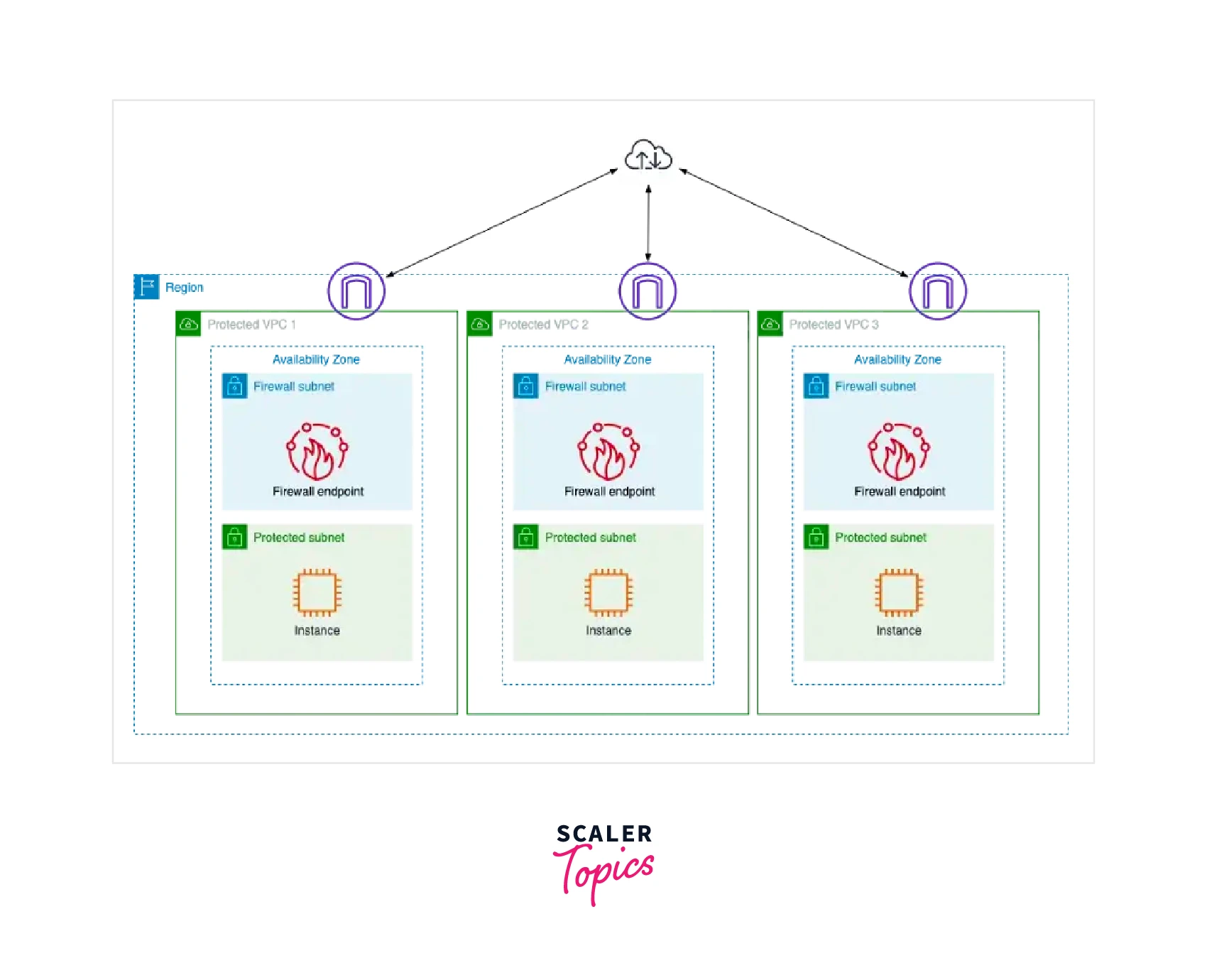
Centralized AWS Network Firewall Deployment Model
- For East-West (VPC-to-VPC) and/or North-South (internet egress and/or on-premises) traffic, AWS Network Firewall is deployed into a central VPC.
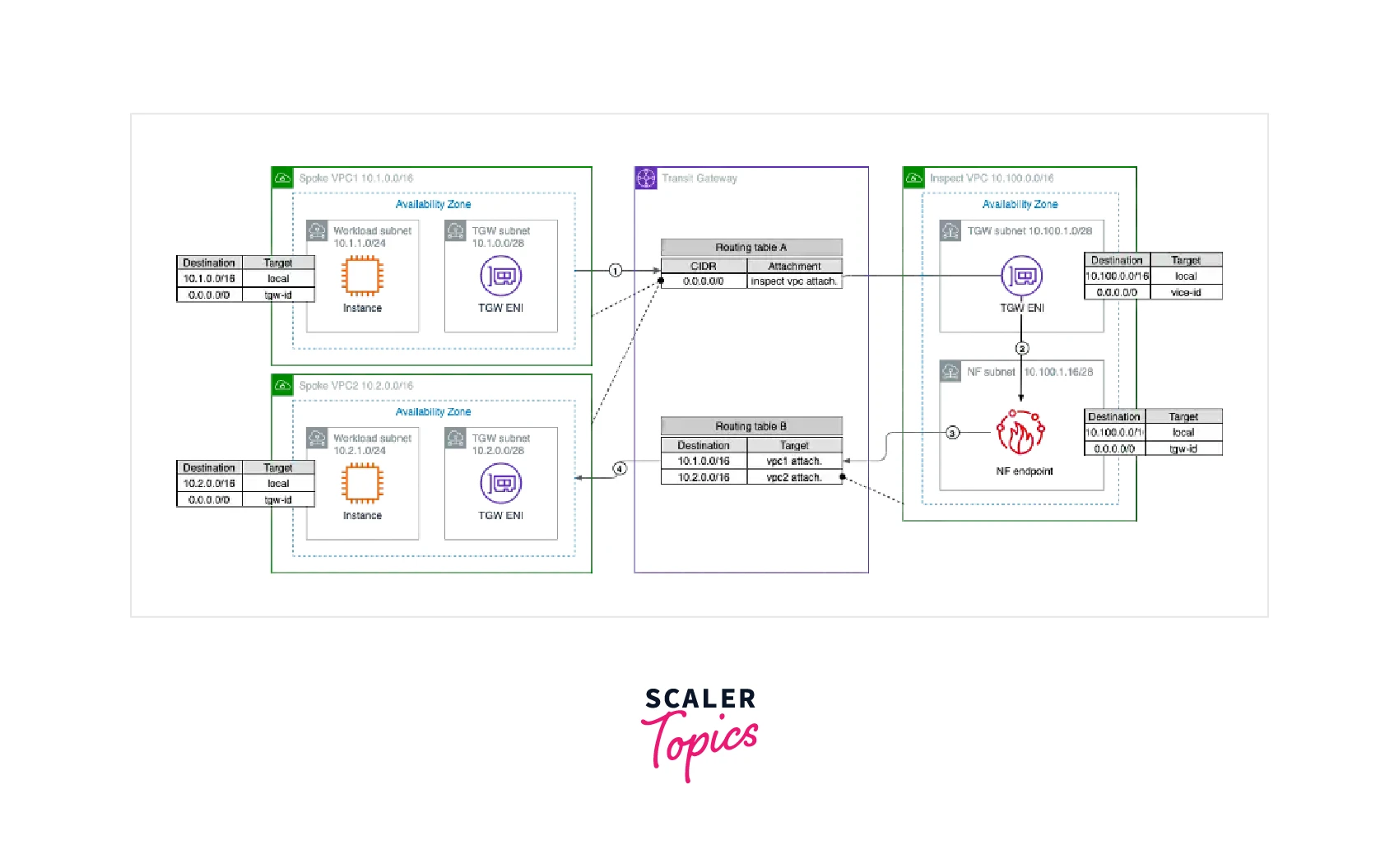
Combined AWS Network Firewall Deployment Model
- The model will be explored in the scenario of Internet traffic. In other words, Internet-facing services must be reachable via the Internet, and the intended use of NF is to inspect the aforementioned traffic.
- Various potential architectures may be used for this (an example is a single centralized Ingress VPC for Internet ingress traffic).
- Combination Model : dispersed for some traffic flows and VPCs and centralized for others.
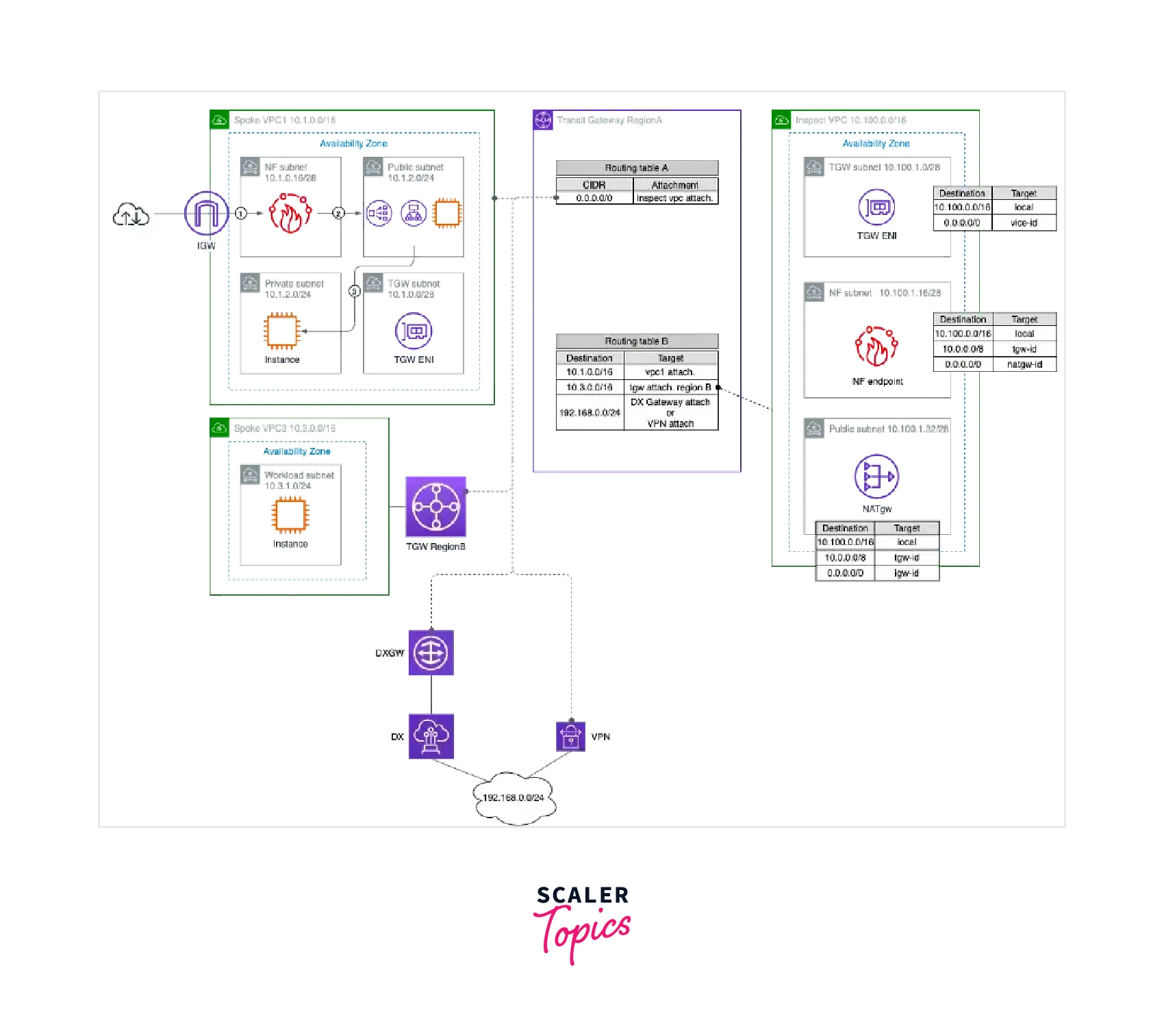
AWS Network Firewall Use Cases
- Examine the Traffic Between VPCs :
Utilizing the AWS Network Firewall, monitor and manage traffic between VPCs to logically divide networks that house critical applications from those that house line-of-business workloads. - Obstruct Outgoing Traffic :
Utilize the AWS Network Firewall to implement outbound traffic screening to stop data loss, aid in compliance, and stop communications from known malware. - Stop Intrusive Inbound Internet Traffic :
Utilizing the AWS Network Firewall, examine active network flow utilizing features like a stateful inspection, protocol identification, and more. - Encrypting VPN and AWS Direct Connect Traffic :
Your on-premises infrastructures and client devices can use AWS Transit Gateway to send secure Direct Connect and VPN traffic.
AWS Network Firewall Pricing
Each firewall endpoint's fee for the service is set at an hourly cost. The traffic processed by our firewall endpoint, which is priced by the gigabyte, must also be paid for. Gigabytes handled through the firewall endpoint are charged, independent of the origin or destination of the traffic. For all data transported across the AWS Network Firewall, we additionally pay standard AWS data transfer fees.
Pricing for NAT Gateways - If we decide to set up a NAT gateway in our AWS account together with a network firewall, the processing per GB and use hours fees for the firewall are matched one-to-one with the fees for the NAT gateway.
| Resource Type | Price – Commercial Regions |
|---|---|
| Network Firewall Endpoint | $0.395/hr |
| Network Firewall Traffic Processing | $0.065/GB |
| NAT gateway Pricing | For every hour and GB charged for Network Firewall endpoints, use one hour and one GB of NAT gateway at no extra cost. |
To Know More About the Pricing of the AWS Network Firewall, Please Visit This Link.
Getting Started with AWS Network Firewall
Step - 1 : Create Rule Groups
To Establish a Stateless Rule Group :
- Visit link to access the Amazon VPC console while logged in to the AWS Management Console.
- Select Network Firewall rule groups from the Network Firewall drop-down menu in the navigation pane.
- Select Create rule group.
- Select Stateless rule group under Rule group type on the Create rule group page.
- Type the rule group's desired name here. Later in the tutorial, when you add the ruling group to your firewall policy, you'll use the name to recognize it. After you create a rule group, its name cannot be changed.
- Enter 10 for Capacity.
- To establish a stateless rule that blocks all packets from the source IP address CIDR range 192.0.2.0/24, use the following rule specifications:
-
Keep a priority of 10.
-
Maintain the All setting for the protocol.
-
Type 192.0.2.0/24 as the source address.
-
Maintain Any as the source port.
-
Set Any as the destination address.
-
Select Drop as the action.
-
Select Add rule. Your rule has been added to the list of rules.
-
To Establish a Stateful Rule Group :
- Select Stateful rule group under Rule group type on the Create rule group page.
- The stateful rule group's name should be entered.
- Enter 10 for Capacity.
- Import Suricata compatible rules is the stateful rule group configuration option to select. The Suricata-compliant IPS rules entry form displays. The following Suricata rule should be copied and pasted into the text field. This rule disables TLS for a certain target domain :
Step - 2 : Create a Firewall Policy
To Set Up a Firewall Policy :
-
Select Create firewall policy from the Firewall policies page.
-
Give the firewall policy the name you want to use. When you link the policy to your firewall later in the tutorial, you'll use the name to recognize it. After you create a firewall policy, you cannot modify its name.
-
To access the Add rule groups page for the firewall policy, select Next.
-
Select Add rule groups from the Stateless rule groups section, then check the box next to the stateless rule group you created earlier. Decide on Adding rule groupings. The capacity counter for the firewall policy displays the capacity used by adding this rule group next to the firewall's maximum capacity at the bottom of the page.
-
Select Add rule groups from the Stateful rule groups section, then check the box next to the stateful rule group you created in the previous step. Decide on Adding rule groupings.
-
To move through the tagging choice and to the Review and create the page, select Next twice. To get back to the relevant page in the firewall policy creation wizard, select Edit for any section from this page.
-
To create a firewall policy, select Create firewall policy.
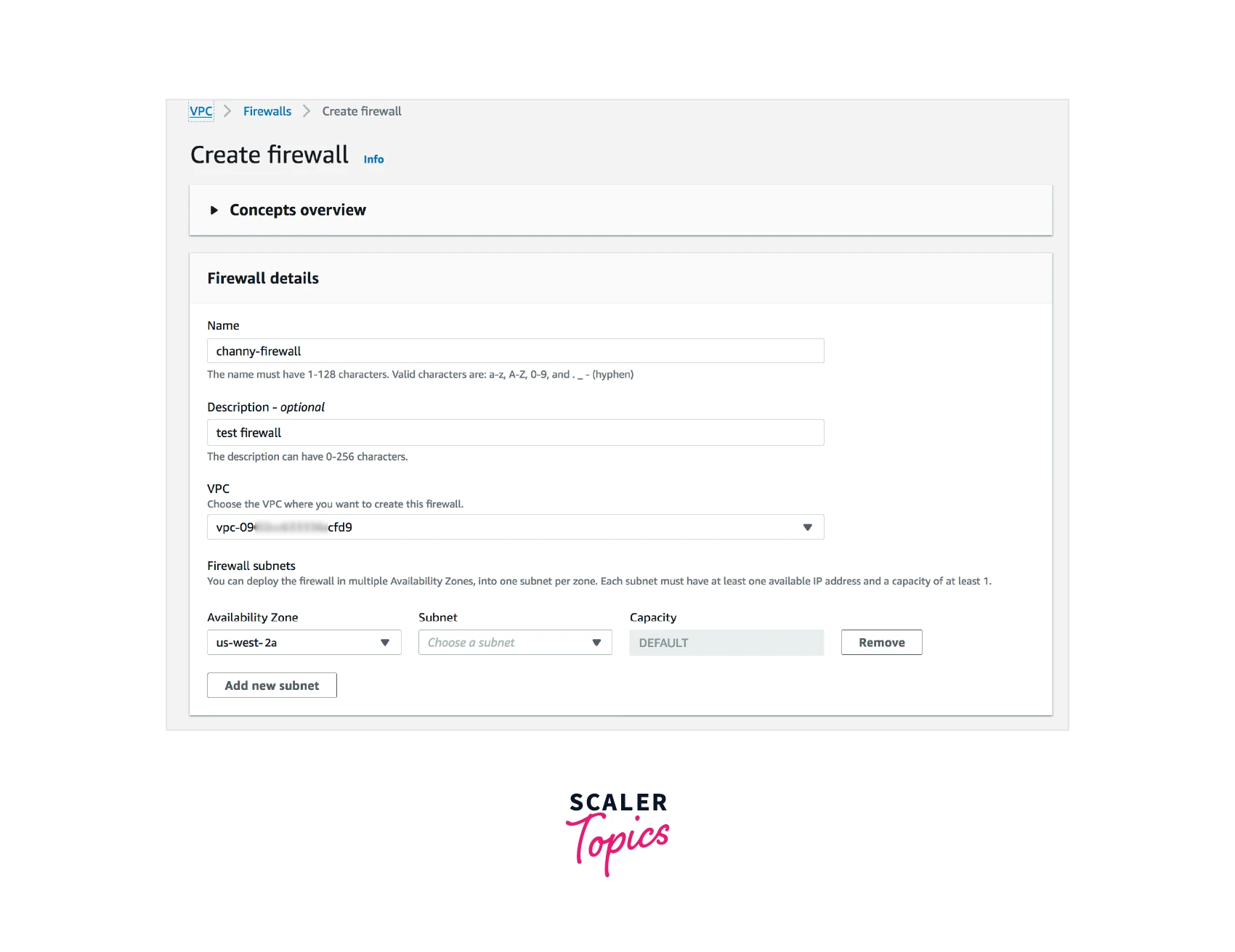
Step - 3 : Create a Firewall
-
Select Create firewall.
-
Enter the name you'd like to use to refer to this firewall under Name. After you create a firewall, you cannot modify its name.
-
Go to the menu and choose your VPC for VPC.
-
Select the firewall subnet and availability zone that you mentioned in the "Before you start" section.
-
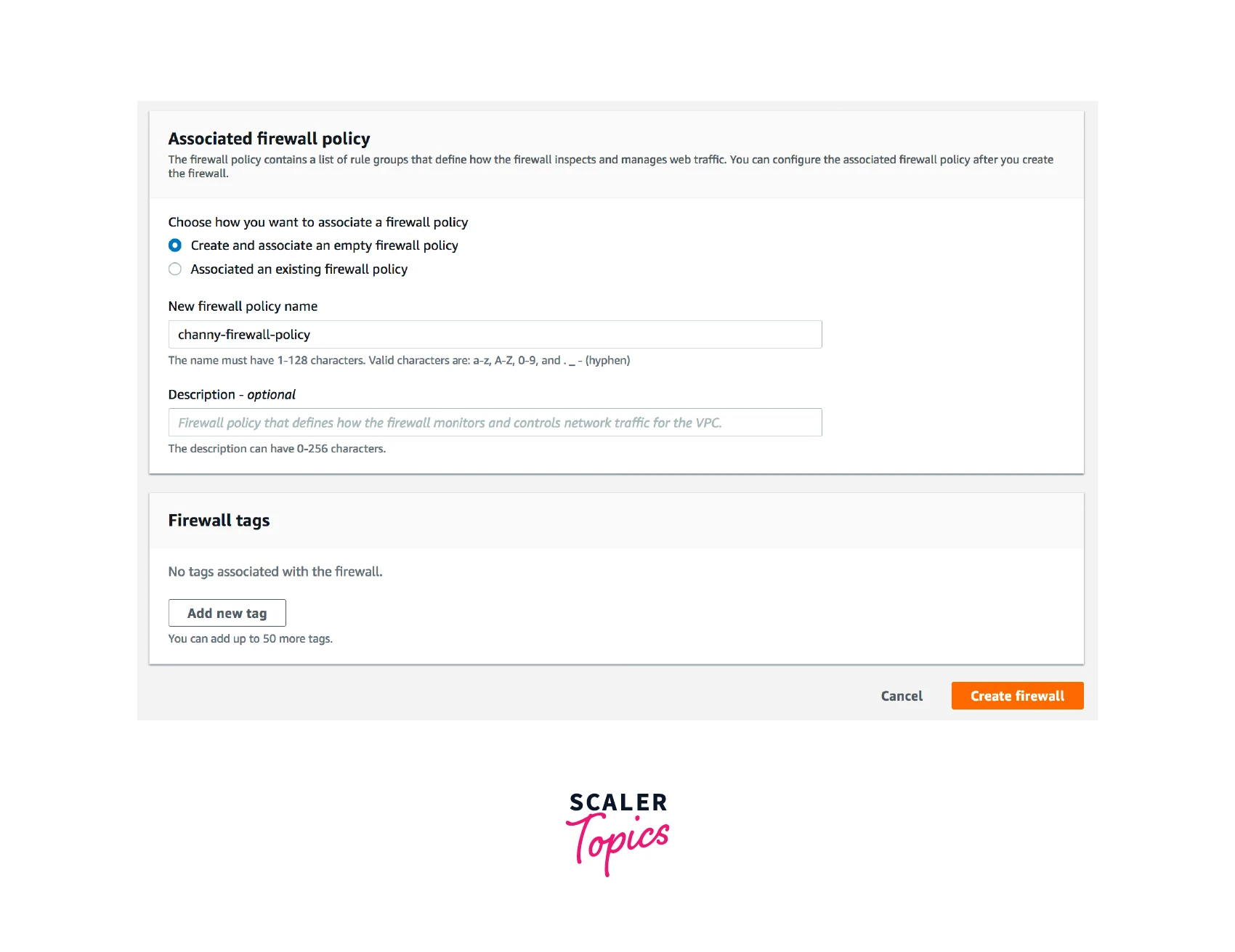
Select the firewall policy you created in the previous phase by selecting Associate an existing firewall policy under Associated firewall policy.
-
Select Create firewall.
Step - 4 : Remove the Firewall and Clean Up Your Resources
To Delete the Network Firewall Resources :
- Choose the firewall you built for the instruction from the Firewalls tab.
- Select Delete, then submit your request.
- Select Firewall policies from the Network Firewall drop-down menu in the navigation pane.
- Choose the firewall rule you made for the instruction on the Firewall policies page.
- Select Delete, then submit your request.
- Select Network Firewall rule groups from the Network Firewall drop-down menu in the navigation pane.
- Choose Delete after selecting the name of the rule groups you generated for the tutorial on the Rule group page.
Conclusion
- In this article, we learned about AWS Network Firewall. For your virtual private cloud (VPC), which you made using Amazon Virtual Private Cloud, there is a stateful, managed network firewall and attack detection and prevention service called AWS Network Firewall (Amazon VPC).
- The main advantages of using AWS Network Firewall are that we can centrally control security policies and do not have to construct and manage the network security architecture ourselves. We can also create unique firewall rules.
- AWS Network Firewall allows us to control security for both an organization and many accounts, so we can use it to handle security across several AWS accounts.
- The inspection of encrypted communication is not supported by the AWS Network Firewall.
- Each firewall endpoint’s fee for the service is set at an hourly cost. The traffic processed by our firewall endpoint, which is priced by the gigabyte, must also be paid for.
