AWS Organizations
Overview
Anyone can create AWS accounts and spin-up resources. Suppose we have multiple AWS accounts, each account for a different domain or project. How can we manage all the AWS accounts in one place ?
The answer is AWS Organizations. AWS Organization is a centrally managed AWS service that lets us add and manage multiple AWS accounts and simplifies the billing experience.
Introduction to AWS Organizations and its Working
Many AWS customers are managing multiple AWS accounts as they have scaled up their use of AWS for a wide variety of reasons, such as a different domain, project, research, auditing, etc.
It is a hectic and time-consuming job for AWS customers to manage billing, governance, and auditing for each account separately.
In 2017, AWS introduced the AWS Organization service to help customers mitigate this problem.
AWS Organizations helps the customer to simplify multiple account management experience. It also offers policy-based management for multiple accounts. Customers can create one group under the organization and add multiple accounts to that group. Then we can apply policies to that group that centrally controls the use of AWS Services at the API level across the added multiple accounts.
For example, we can create a group of accounts that are used for production resources and apply a policy to that group that limits which AWS service APIs (Application programming interface) those accounts can use.
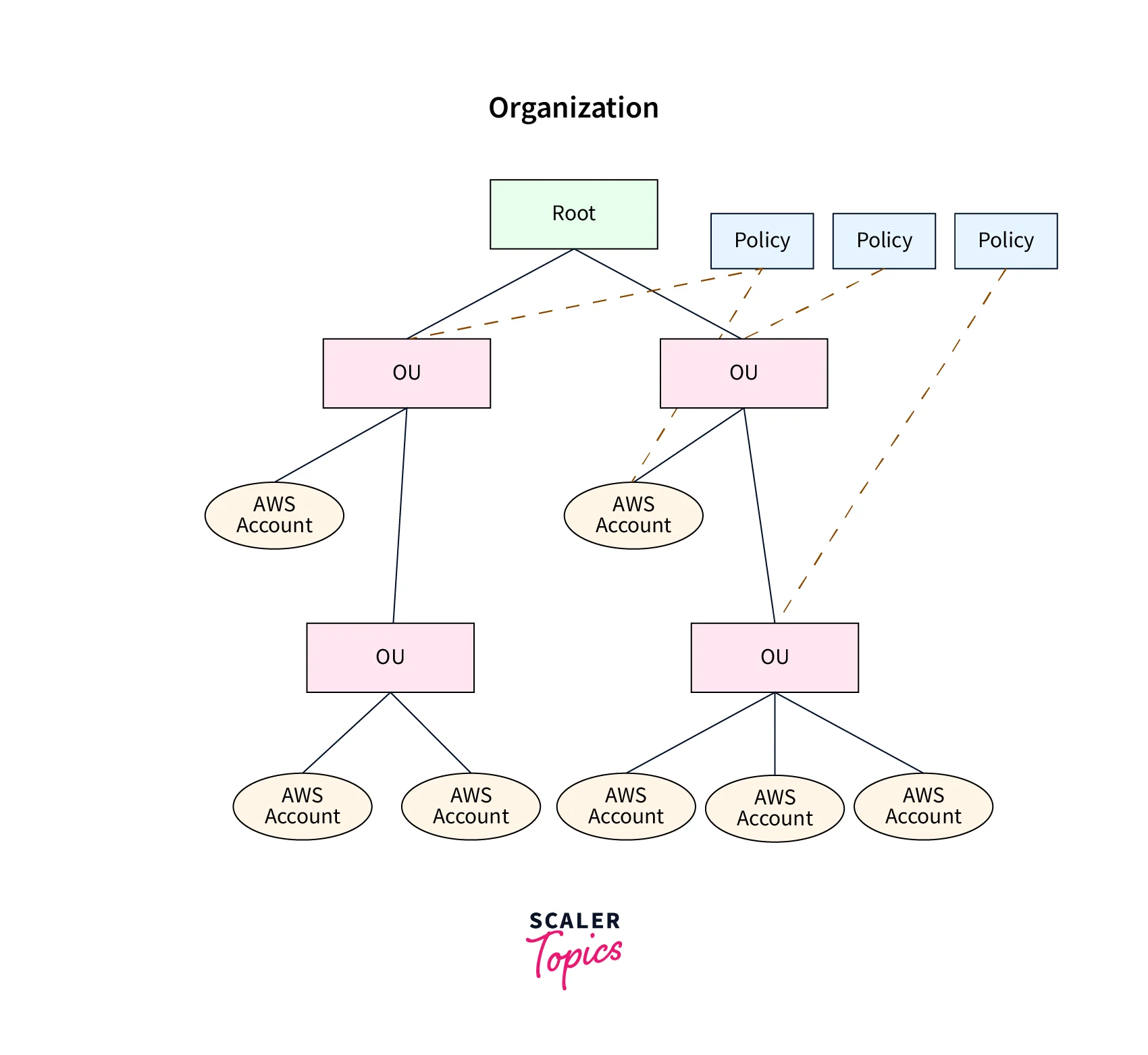
Working of AWS Organization :
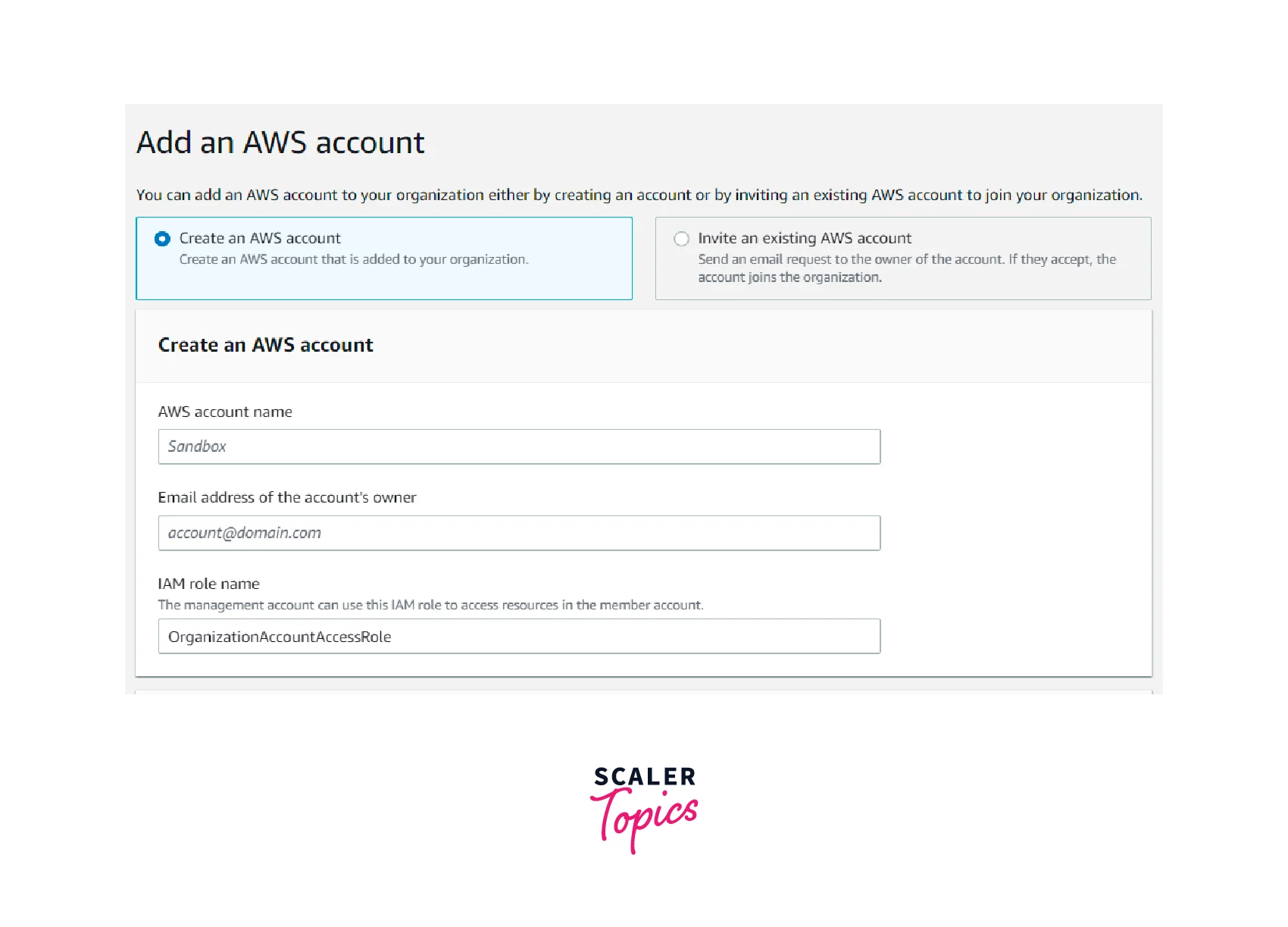
We have two options to add an AWS account to Organizations, which is later called an AWS member account.
-
Option - 1 :
We can create a new AWS account with the email address from the AWS Organization console and send an invitation to add it to the AWS organization -
Option - 2 :
We send an invitation to the existing AWS account. The AWS account will accept the invitation and become a member of that AWS organization.
We can add or remove the AWS member account as per our business needs.
AWS Organizations Key Concepts
Before diving deep into the AWS Organization, we should be familiar with the below-mentioned key concept which is associated with the AWS organization
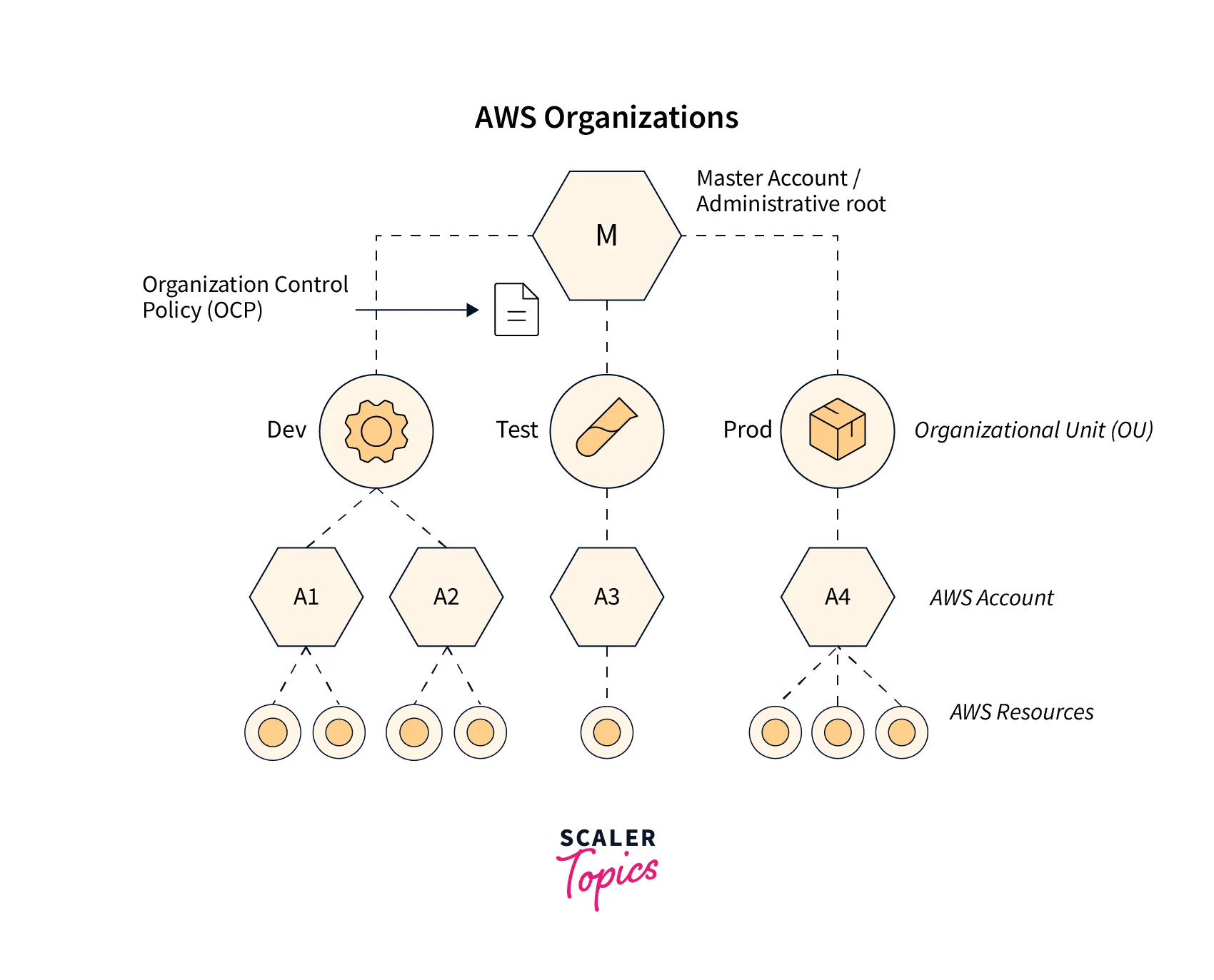
Root :
This is the parent Organization Unit for all the AWS accounts or other organizational units within the AWS Organization. It is often called the organizational root.
AWS Management Account :
Every account has its own AWS Management Account. Before starting work on the AWS Organization, we need to verify the root user's email address for the AWS Management Account.
AWS Member Account :
We can either create a new AWS account or invite an existing AWS account. Both accounts will be considered member accounts once they have accepted the invitation from AWS Organizations.
Organization Unit :
The organization unit (OU) acts as a container for AWS member accounts within a root. Organization Units contain member accounts or nested OUs.
Available feature sets :
There are two features available for the AWS Management account in the AWS Organization.
- All features enabled.
- Consolidated billing
- All features enabled :
All features will be enabled by default for the AWS Management account. If AWS management accounts would like to control the other AWS member accounts, then the AWS member accounts should acknowledge and approve the request. - Consolidated billing :
This feature will provide consolidated billing for all the member accounts within the organization in the AWS management account's billing console.
Enables all features in an AWS Organization :
- This feature set enables the use of organization policies that can restrict the services and actions that can be performed within each member account.
- Until we enable all features, we have access to consolidated billing only.
- By enabling all features, we can perform advanced account administration features that AWS Organization supports.
Service control policies :
Service control policies are similar to IAM policies. We can attach it to three levels.
- Root account
- OU account
- AWS Member account
Since the AWS Organization follows a hierarchy model, if we apply Service Control Policy (SCP) to the root level, then the policy will be inherited by all the AWS Member accounts within the AWS Organizational root.
If we apply the service control policy to the Organization unit, all the AWS member accounts mapped under the Organization unit will inherit the policy.
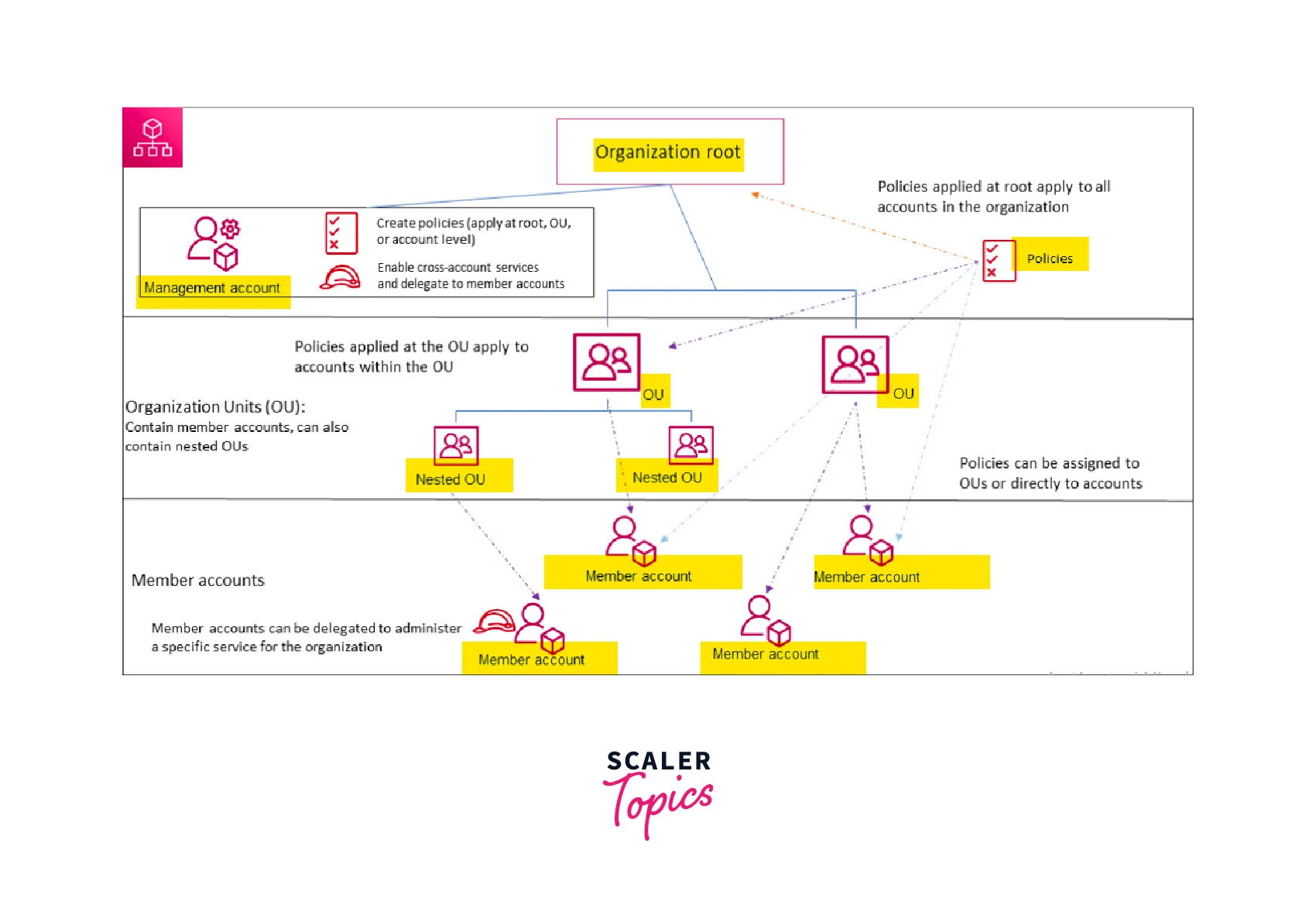
Service Control Policies
- An AWS Service Control Policy is used to manage permissions across the members' accounts mapped under the particular organization.
- The Service Control Policy that we attach, will even override the permissions of the administrators of member accounts or organizational units in the AWS Organization.
- The management account can use service control policies to limit or restrict access for the member account's users and roles, increasing the level of granularity.
- The Service Control Policy follows the same format as an IAM policy with Allow or Deny parameters.
Consideration for Using Service Control Policies
- The AWS Management account where the AWS organization is created enables all features by default.
- To use service control policies, the AWS member account should enable all features.
- Once the member accounts are acknowledged and approved, we can attach the Service Control Policy to the Organization Unit or AWS member account.
- Service control policies can be enabled or disabled only by the AWS management account.
Resource Groups
An AWS resource group is used to group our AWS resources under a single entity. Using resource groups, we can centrally apply changes such as patch updates or tagging to our resources such as EC2, RDS, etc.
What is Tag Policy ?
Tag policies help customers standardize tags on all tagged resources across AWS Organizations. We can use tag policies to define tag keys (including how they should be capitalized) and their allowed values.
Tag policy in the resource group :
- We can create a tag policy and attach it to the AWS organization root, AWS member account, or organization unit in the AWS Organization console.
- If we attach the tag policy to the root, all the AWS member accounts or organization units mapped under the organization root will inherit the tag policy.
- Every resource should use tags in their AWS resource for compliance requirements.
- We can easily find the list of compliant and non-compliant resources in the AWS resource group tag policies console.
Features of AWS Organizations
Define and manage your organization :
- We can create a new AWS account or add an existing AWS account to an AWS Organization.
- We can create a new organization unit and add or remove the existing AWS member account from the organization unit.
Centrally manage billing and costs :
- Using the AWS Management account, we will be able to view the resource usage such as EC2, RDS, Lambda, etc for all the member accounts and track the service cost using the AWS Cost Explorer service. This helps us to optimize our resource usage in a single window for all the member accounts.
Audit your environment for compliance :
- Using AWS CloudTrail, AWS management can create a log group where we will receive the logs of all activity of AWS accounts under the AWS Organization. This configuration cannot be modified by an AWS member account.
- Using AWS Backup, you can enforce backups for certain critical environment workloads for specific member accounts or all member accounts by applying an AWS Service Control Policy.
- Using AWS Config, we can define recommended configuration settings to follow for all the member accounts under the AWS Organization.
Share resources across accounts :
- Using Resource Access Manager, we can share resources across our AWS Account within the AWS Organization.
- Using AWS License Manager, we centrally agree to use software licenses, which will reduce the overhead of software license management.
- Through the AWS Service Catalog, we can also share the catalog of IT products and services such as EC2 instances, storage volumes, networking components, packaged AWS Marketplace products, etc.
Control access and permissions :
- Using AWS IAM Identity Center (successor to AWS Single Sign On (SSO)), we can delegate and customize user or role permission to access our AWS accounts and resources using the Active Directory.
- We can also apply service control policies to IAM users or AWS member accounts or Organization Units to control access to AWS services, resources, and regions within an AWS organization.
Protect and monitor your accounts :
- AWS Organizations helps the security team to access AWS accounts with centrally managed tools. AWS GuardDuty also detects threats across our AWS Organization if we provide read-only security access to all the member accounts.
Use Cases of AWS Organizations
There are lots of use cases that will apply to AWS Organization. Here, we discuss the four most commonly used use cases by AWS customers.
Separate Environment for Workloads.
For example, suppose we have one AWS account for a production environment, one for the development environment, and one for the testing environment. Using an AWS Organization, we can delegate permission across the three environments and centrally manage all the AWS environments under one AWS organization.
Separate Business Unit
Most customers use AWS Organization for managing different business units or Domain Units.
For example :
- A company consists of many units, such as an HR unit, an Infra unit, a DevOps unit, a security unit, etc.
- We can create an account or invite an account for each unit and centrally manage them under the AWS organization.
- This helps with a higher level of granularity and resource ownership for all the divisions within the company.
National or State Compliance
Every country or state mandates financial or bank sector companies to comply with their policies. Using AWS Organization, we can achieve compliance standards for all the member accounts without the hassle by using Service Control Policies and AWS CloudTrail.
Consolidated Billing
Using the AWS Management Console, we will get a consolidated bill for all the member accounts mapped under the organization.
Benefits of AWS Organizations
- We can use a group alias rather than an individual email address as the account's (member or management AWS account's) email address.
- We can create and implement AWS tagging standards across the member accounts under the AWS organization.
- We can also leverage compliance monitoring scripts to monitor all the member accounts.
- The AWS multi-account strategy for business can be easily managed by the AWS Organization console.
- AWS Organization provides Consolidated Billing which helps customers to optimize and reduce costs for their AWS resources.
How to Create an AWS Organizational Unit ?
By default, our AWS Management account will come under root (organizational root).
Now, we are going to create one new organization unit and move the AWS Management account from the organization root to the newly created Organization unit.
-
Step - 1 :
Go to the AWS management console and enter AWS Organizations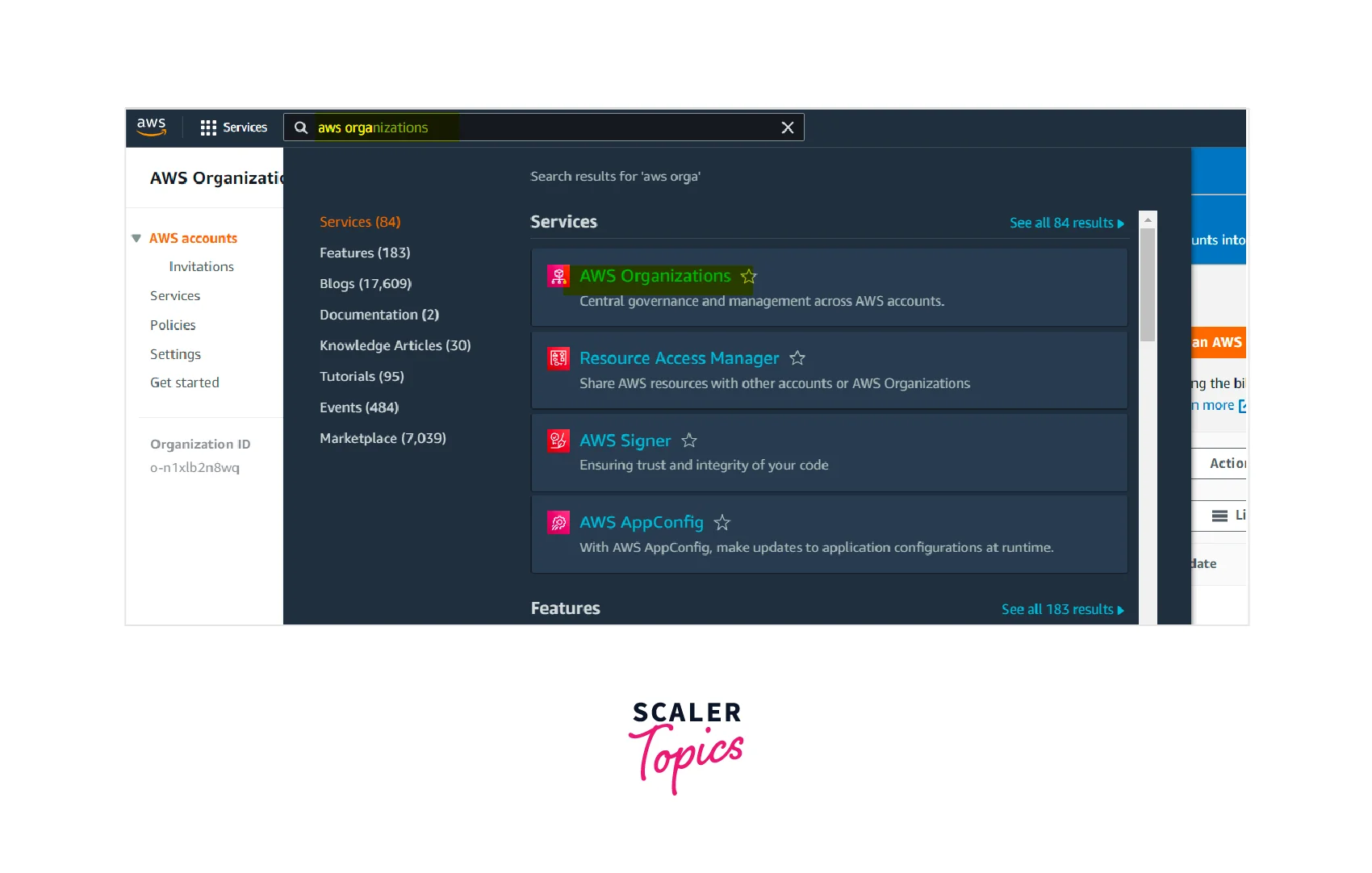
-
Step - 2 :
On the left side of the AWS Organization console, click AWS accounts in the navigation pane.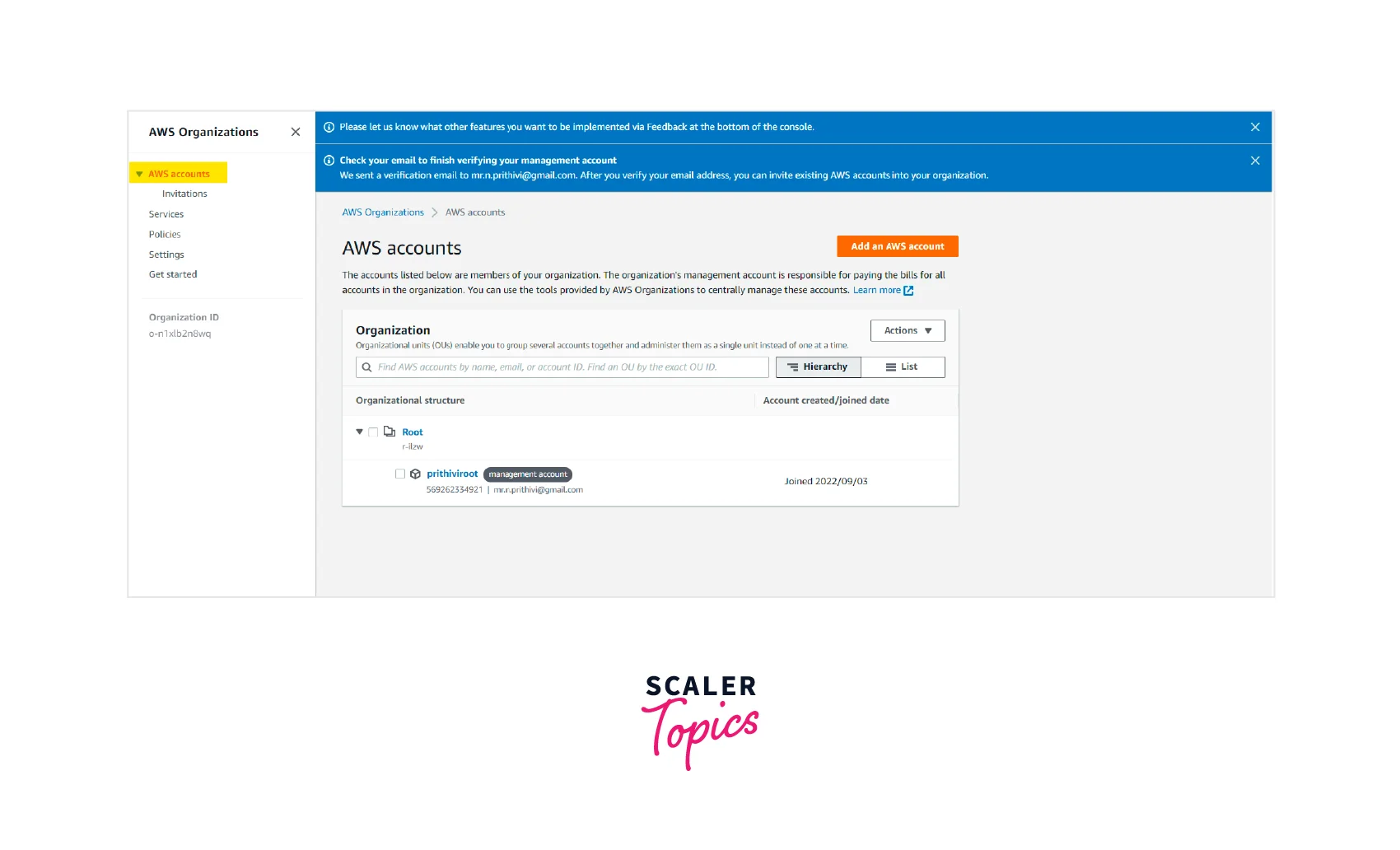
-
Step - 3 :
You can see that the AWS Management account is nested under the root (organization root).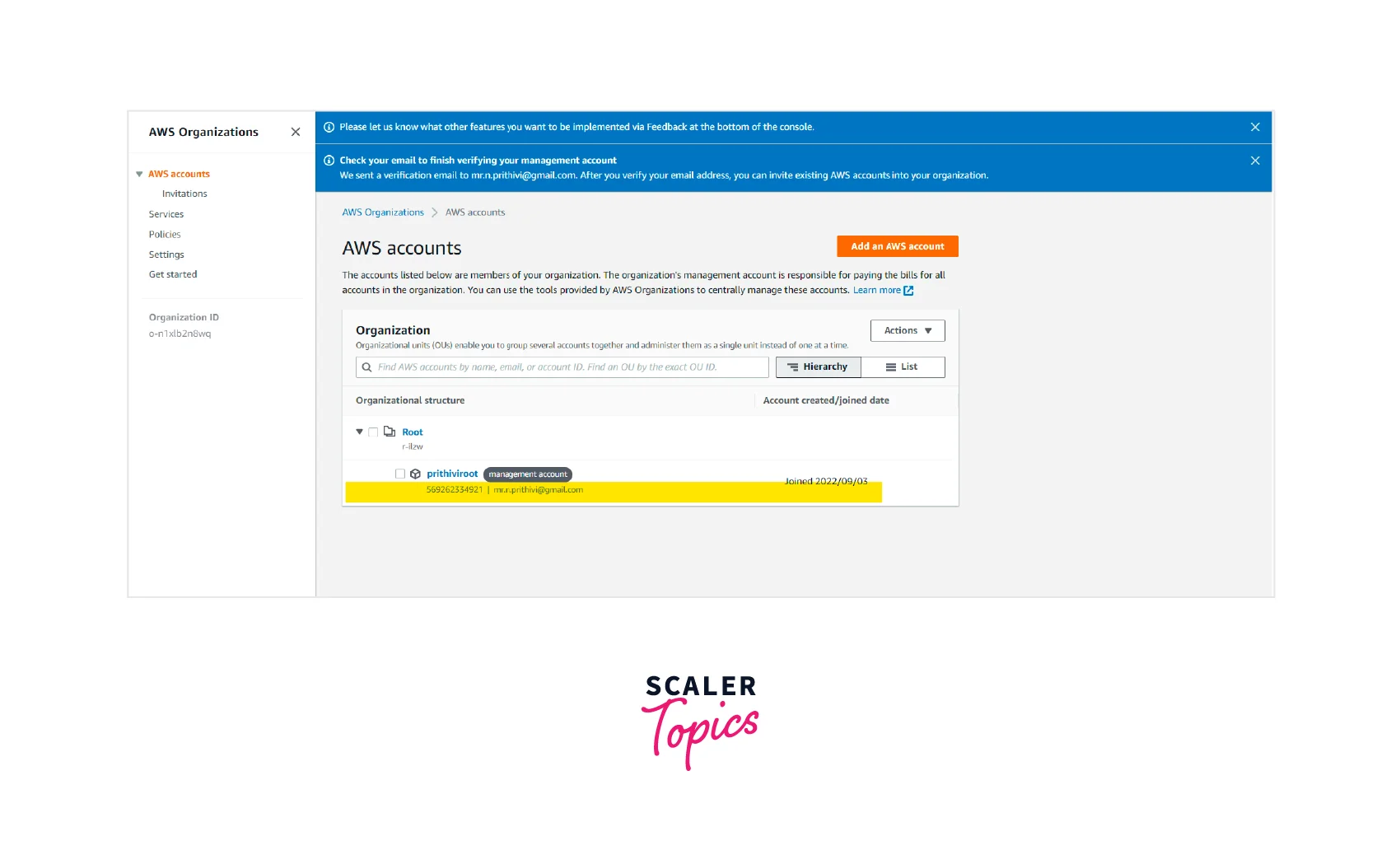
-
Step - 4 :
Click the Root checkbox and select Actions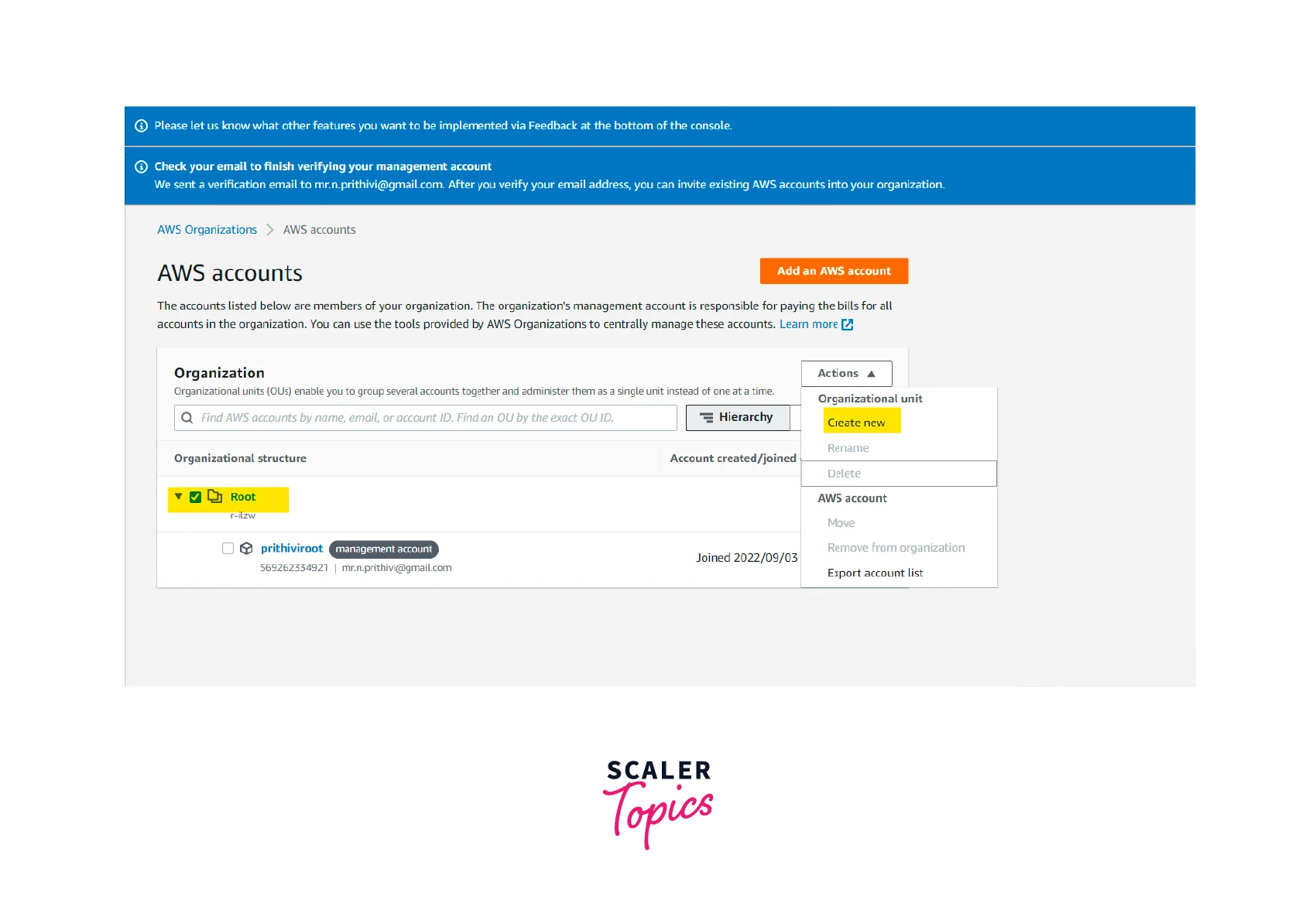
-
Step - 5 :
Click Create new under the organization unit heading and enter the organization unit name.Organization Unit Name : parent-account
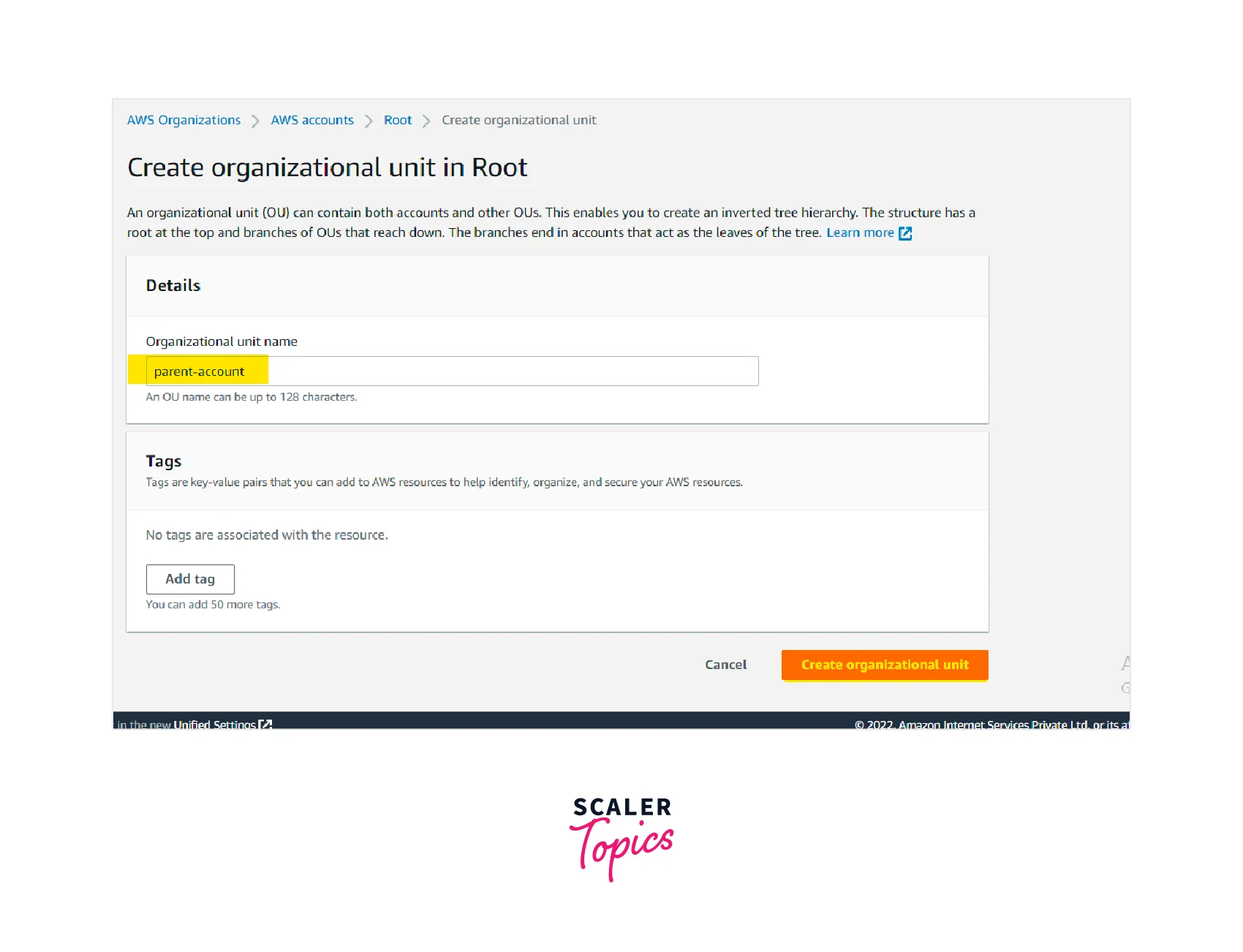
Now we can see that a new organization unit parent-account is created.
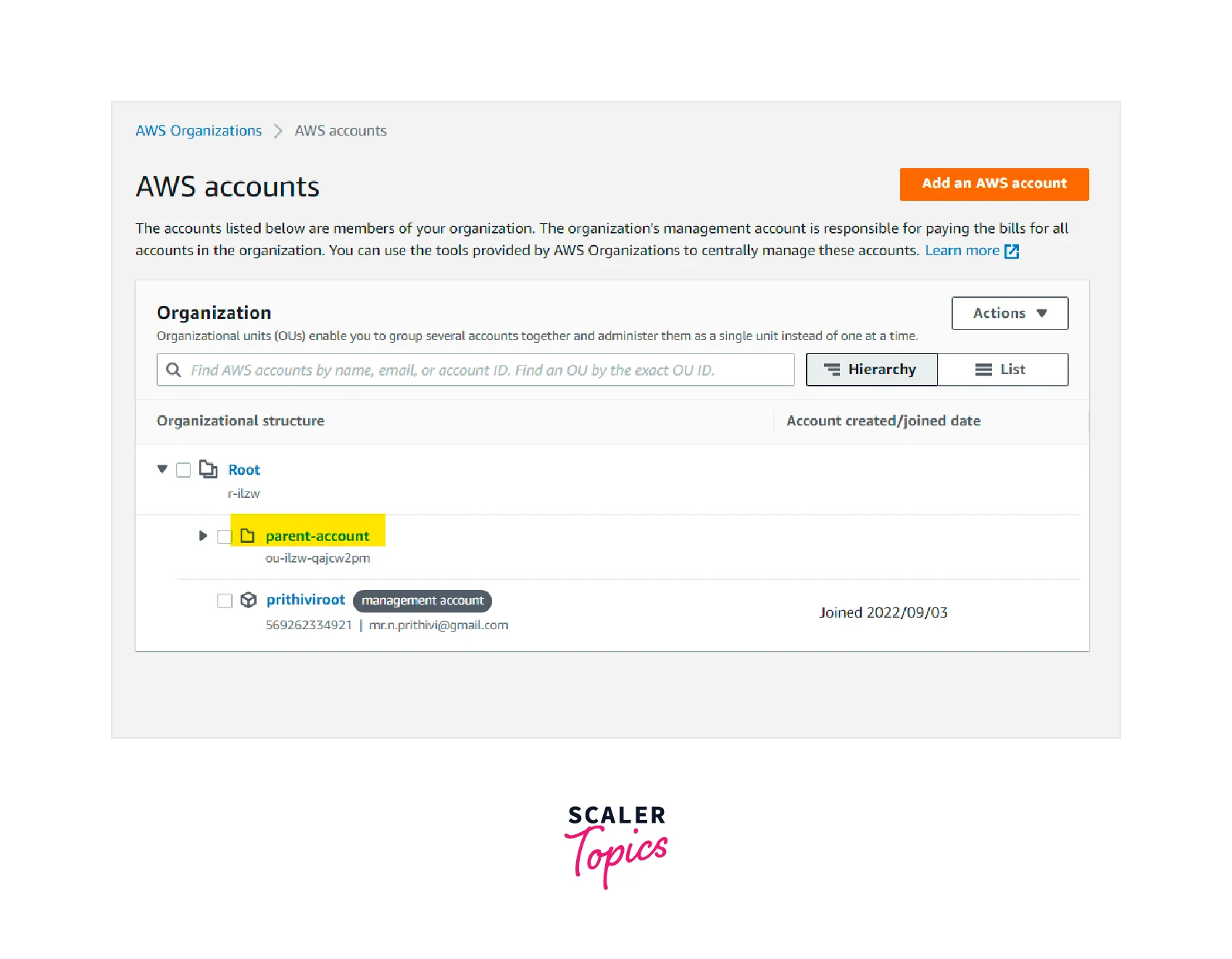
-
Step - 6 :
Click Action and select Move after selecting the checkbox of AWS Management account.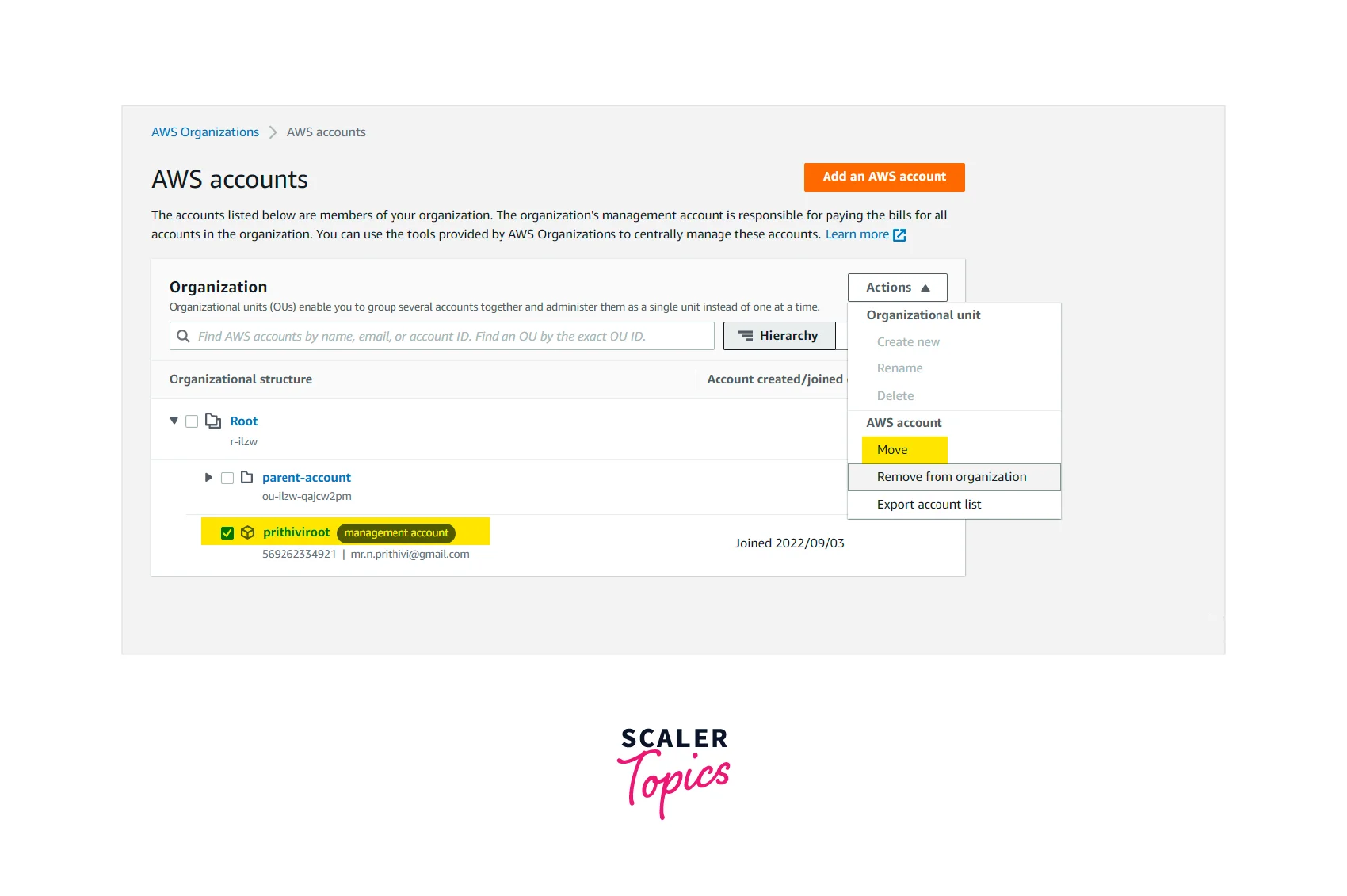
-
Step - 7 :
Select the checkbox of the newly created organizational unit and click the Move AWS account button.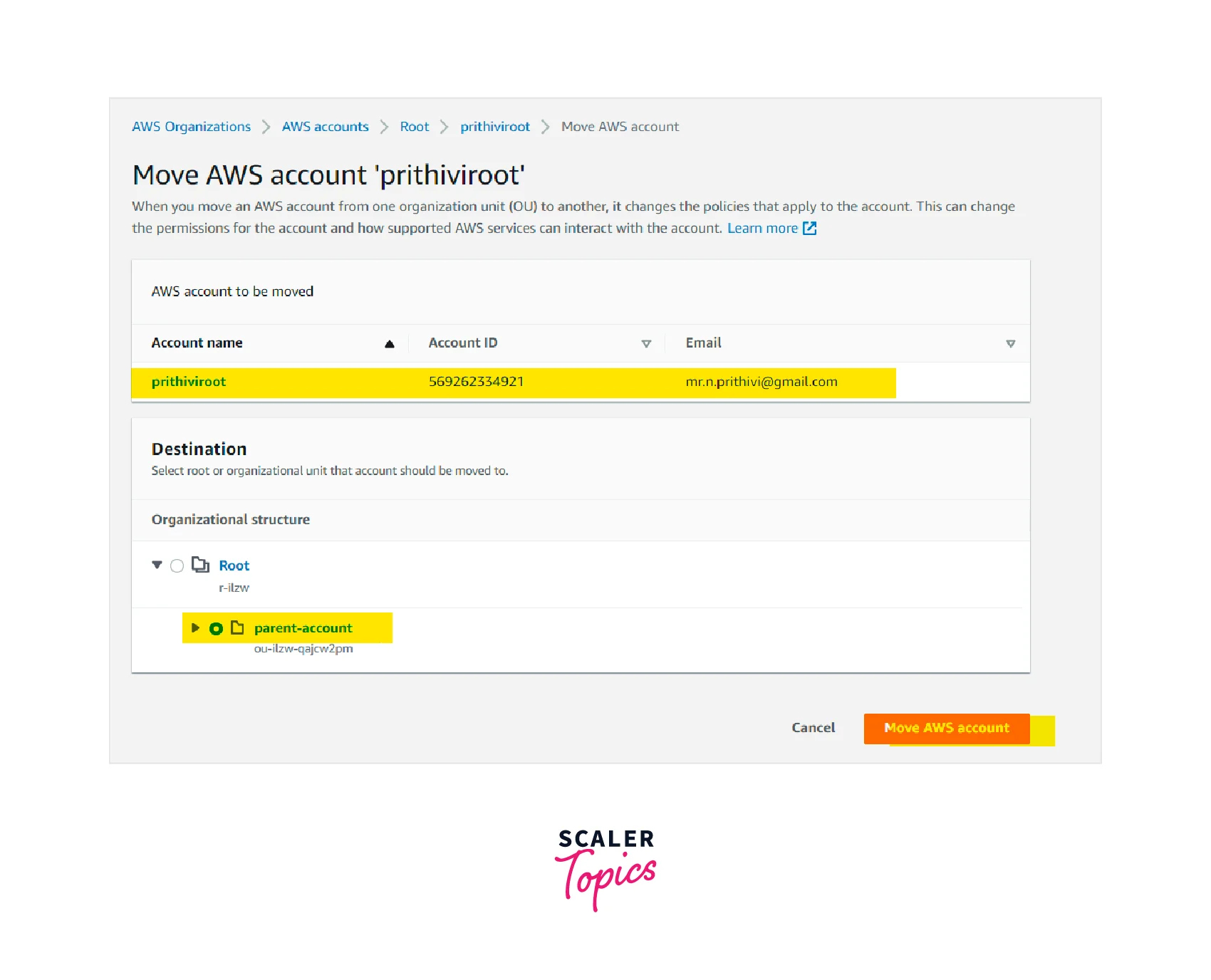
-
Step - 8 :
Now, we can see that the AWS management account is moved from the organization root to the newly created Organization unit.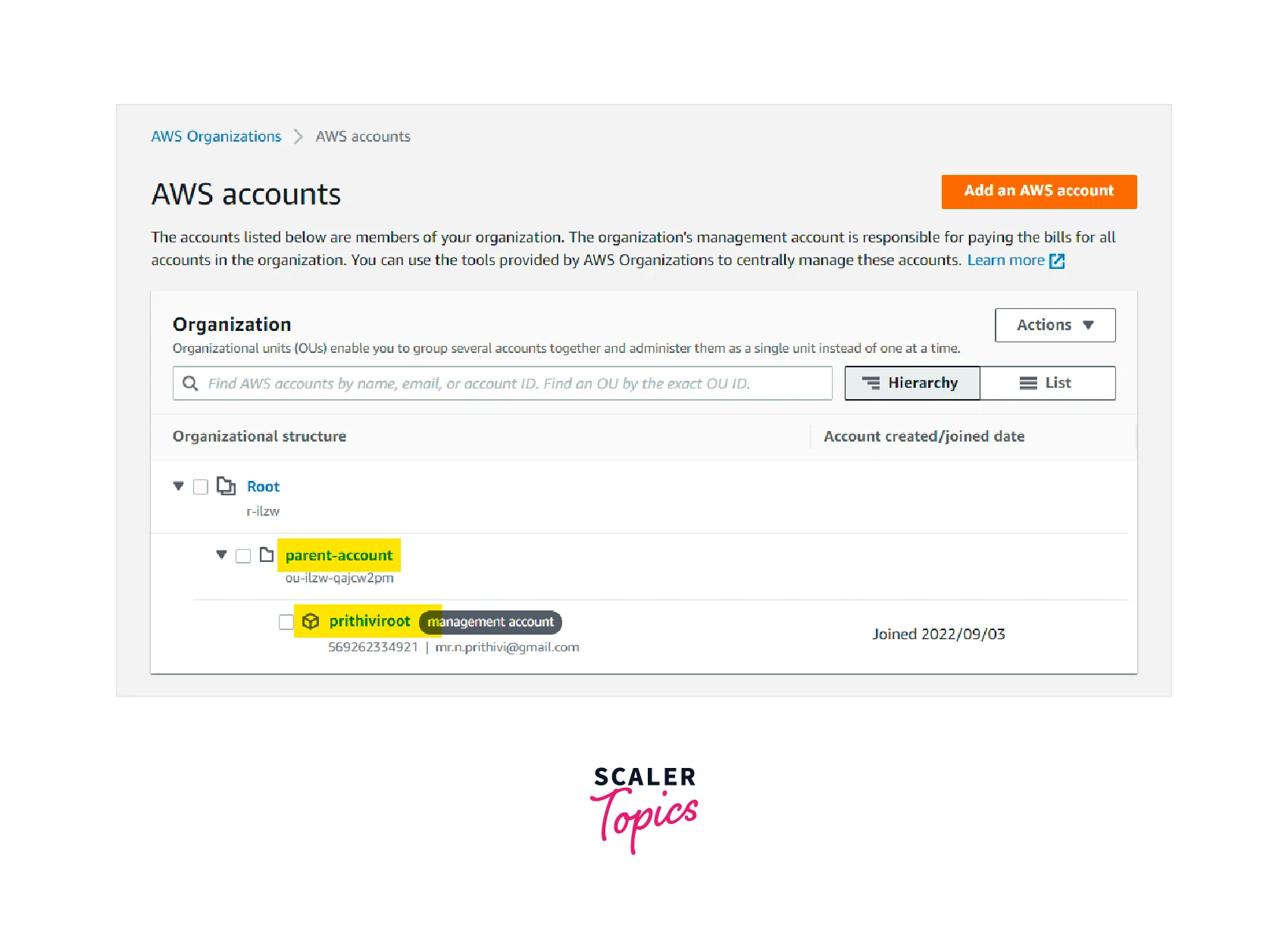
AWS Organizations Pricing and Quotas
There is no cost for using AWS Organization. We just have to pay for the resources we have used across the member accounts, such as EC2, S3, RDS, and so on.
Quotas
An AWS Management account can manage up to ten accounts by default. We need to use AWS Service Quotas services to increase the service quota for managing more than ten AWS member accounts.
| Quota Name | AWS Default value | Adjustable by AWS Service Quotas |
|---|---|---|
| Maximum number of accounts | 10 | Yes |
| Number of roots in an organization | 1 | No |
| Number of OUs in an organization | 1000 | No |
| Number of policies of each type in an organization | 100 per policy type | No |
| Enable all features request expiration | 90 Days | No |
| Handshake expiration | 30 Days | |
| No | ||
| Member accounts you can concurrently close | 3 | No |
| Member accounts you can concurrently create | 5 | No |
| Minimum age for removal of created accounts | 7 Days | No |
| Number of invitation attempts you can perform in 24 hours | 20 | No |
| OU maximum nesting in a root | 5 | No |
| OUs in an organization | 1000 | No |
| Policies in an organization | 1000 | No |
| Roots in an organization | 1000 | No |
| Service control policies per account | 5 | No |
| Service control policies per OUs | 5 | No |
| Service control policies per root | 5 | No |
| Service control policy document size | 5 KB | No |
Conclusion
- AWS Organizations service helps manage multiple AWS accounts and govern multiple environments in one place.
- AWS Organizations provides the underlying infrastructure and capabilities to build and manage multi-account environments.
- AWS customers can centrally provision accounts and resources using AWS Organization Service control policies.
- Using AWS Organizations, customers can secure and audit their environment for compliance requirements.
- Customers can also share resources and control access to accounts, regions, and services.
- AWS Organizations helps to optimize costs and consolidate billing by enabling all features across the AWS member accounts.
- All AWS customers have access to AWS Organizations at no extra cost.
