AWS PrivateLink
Overview
AWS PrivateLink enables private communication between VPCs, AWS services, and your on-premises networks without exposing your traffic to the public Internet. AWS PrivateLink makes it simple to link services across accounts and VPCs, simplifying your network design dramatically. You don't need to use an internet gateway, NAT device, public IP address, AWS Direct Connect connection, or an AWS Site-to-Site VPN connection to enable communication with the service from your private subnets. The specific websites, services, and API endpoints that may be accessed from your VPC are therefore under your control.
What is AWS PrivateLink?
With the help of the highly available and scalable AWS PrivateLink technology, you can securely link your VPC to services as though it were your VPC itself. To enable communication with the service from your private subnets, you do not need to employ an internet gateway, NAT device, public IP address, AWS Direct Connect connection, or an AWS Site-to-Site VPN connection. As a result, you have control over the particular websites, services, and API endpoints that can be accessed from your VPC.
With AWS PrivateLink, you can connect to a number of AWS services, endpoint services (services hosted by other AWS accounts), and supported AWS Marketplace partner services using private IP addresses in your VPC. The interface endpoints are created inside your VPC using IP addresses and elastic network interfaces from your VPC's subnets. In order to manage endpoint access, VPC Security Groups may be used. Interfaces powered by PrivateLink VPC endpoints connect you to solutions offered in the AWS marketplace and services hosted by AWS Partners.
Your virtual network appliances or customized traffic inspection algorithms will have the same degree of security and performance thanks to AWS PrivateLink, which powers Gateway Load Balancer endpoints.
How Does It Work?
Your VPCs can be securely connected to supported AWS services via PrivateLink AWS, including your own AWS service, services hosted by other AWS accounts, and services from third parties on the AWS Marketplace. You no longer need an Internet gateway, NAT device, public IP address, or VPN connection to communicate with the service because communication between your VPC and any of these services does not leave the Amazon network.
To use PrivateLink AWS, establish an interface VPC endpoint for a service in your VPC. A private IP address in your subnet creates an Elastic Network Interface (ENI), which serves as a gateway for traffic going to the service. Endpoints for the Amazon PrivateLink service will appear in your VPCs as ENIs with private IPs. Between approved AWS services, services hosted by other AWS accounts, and supported AWS Marketplace services, PrivateLink offers secure communication. You do not require an internet gateway, NAT device, AWS Direct Connect connection, or AWS Site-to-Site VPN connection in order to communicate with the service.
Create a VPC endpoint in your VPC, give it a service name, and a subnet to access PrivateLink. As a result, an elastic network interface is created in the subnet that acts as a point of entry for traffic going to the service. You are free to create your own VPC endpoint service using PrivateLink AWS and make it accessible to other AWS customers.
Where/How can You Use an AWS PrivateLink
You can build VPC endpoints to link resources in your VPC to AWS PrivateLink-compatible services. By using AWS PrivateLink, you can develop your own VPC endpoint service that will give other AWS users access to your offering.
The VPC on the left in the accompanying diagram includes three interface VPC endpoints and a number of EC2 instances in a private subnet. An AWS service is connected to the topmost VPC endpoint. Connecting to a service hosted by another AWS account is what the middle VPC endpoint does (a VPC endpoint service). Connected to an AWS Marketplace partner service is the lowest VPC endpoint.
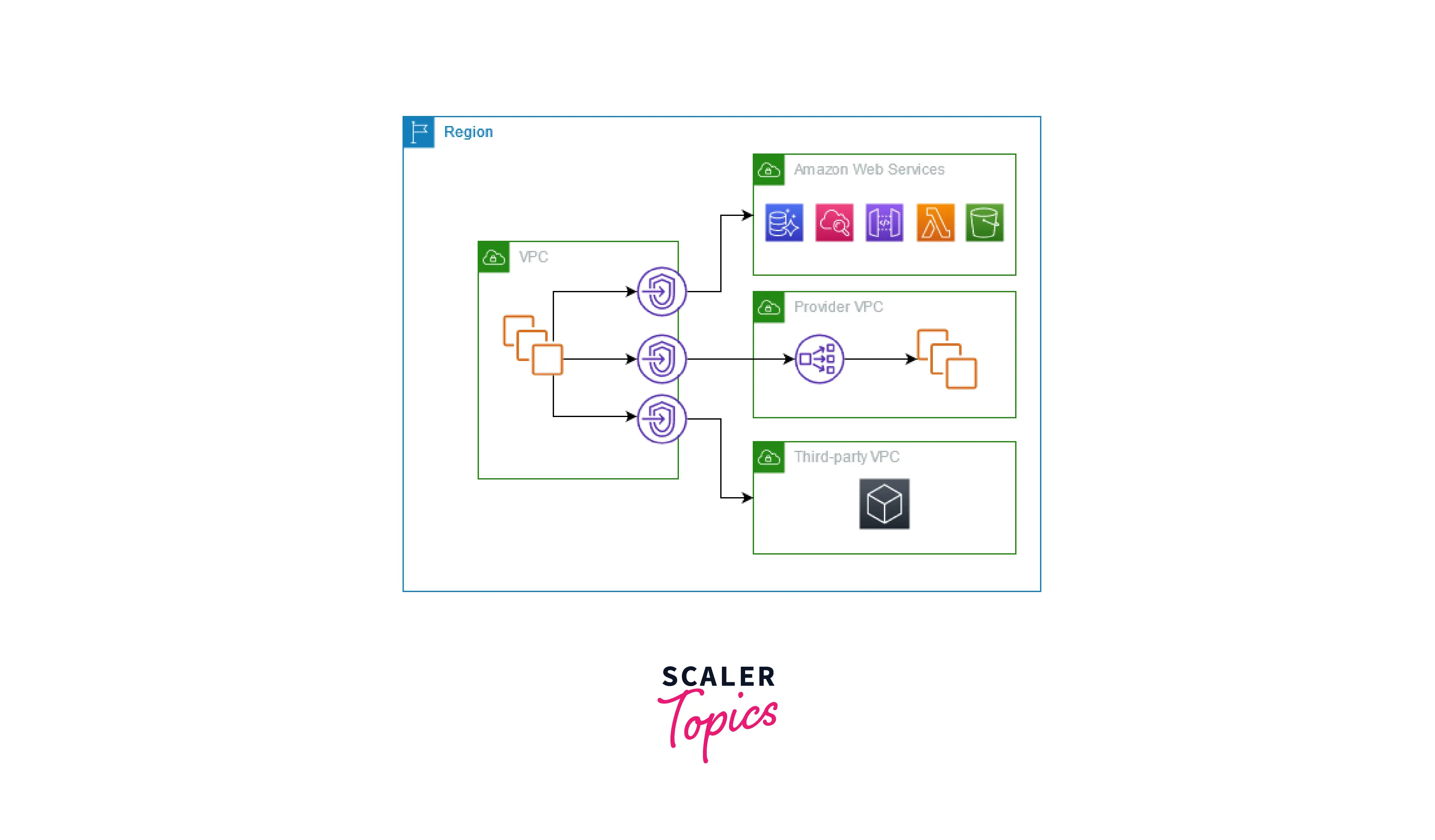
Utilize AWS PrivateLink to Connect your VPC to Services
Between virtual private clouds (VPC), supported AWS services, services hosted by other AWS accounts, and supported AWS Marketplace services, AWS PrivateLink creates a secure connection. The service can be reached without the usage of an internet gateway, NAT device, AWS Direct Connect connection, or AWS Site-to-Site VPN connection.
Create a VPC endpoint in your VPC with the service's name and a subnet specified if you want to use AWS PrivateLink. Due to the creation of an elastic network interface in the subnet, traffic directed at the service can enter the network through this interface.
You can develop your own VPC endpoint service supported by AWS PrivateLink and make it possible for other AWS users to use it.
AWS PrivateLink Concepts
A virtual private cloud (VPC), which is a conceptually isolated virtual network, can be created using Amazon VPC. In your VPC, you can start up AWS resources. You can enable connections between resources inside and outside of your VPC. For instance, you may add an internet gateway to the VPC to enable internet access or a VPN connection to enable on-premises network access.
When using AWS PrivateLink, it's crucial to comprehend the ideas listed below.
Architecture Diagram
An explanation of how AWS PrivateLink functions at a high level is shown in the diagram below. To connect to endpoint services hosted by service providers, service consumers construct interface VPC endpoints.
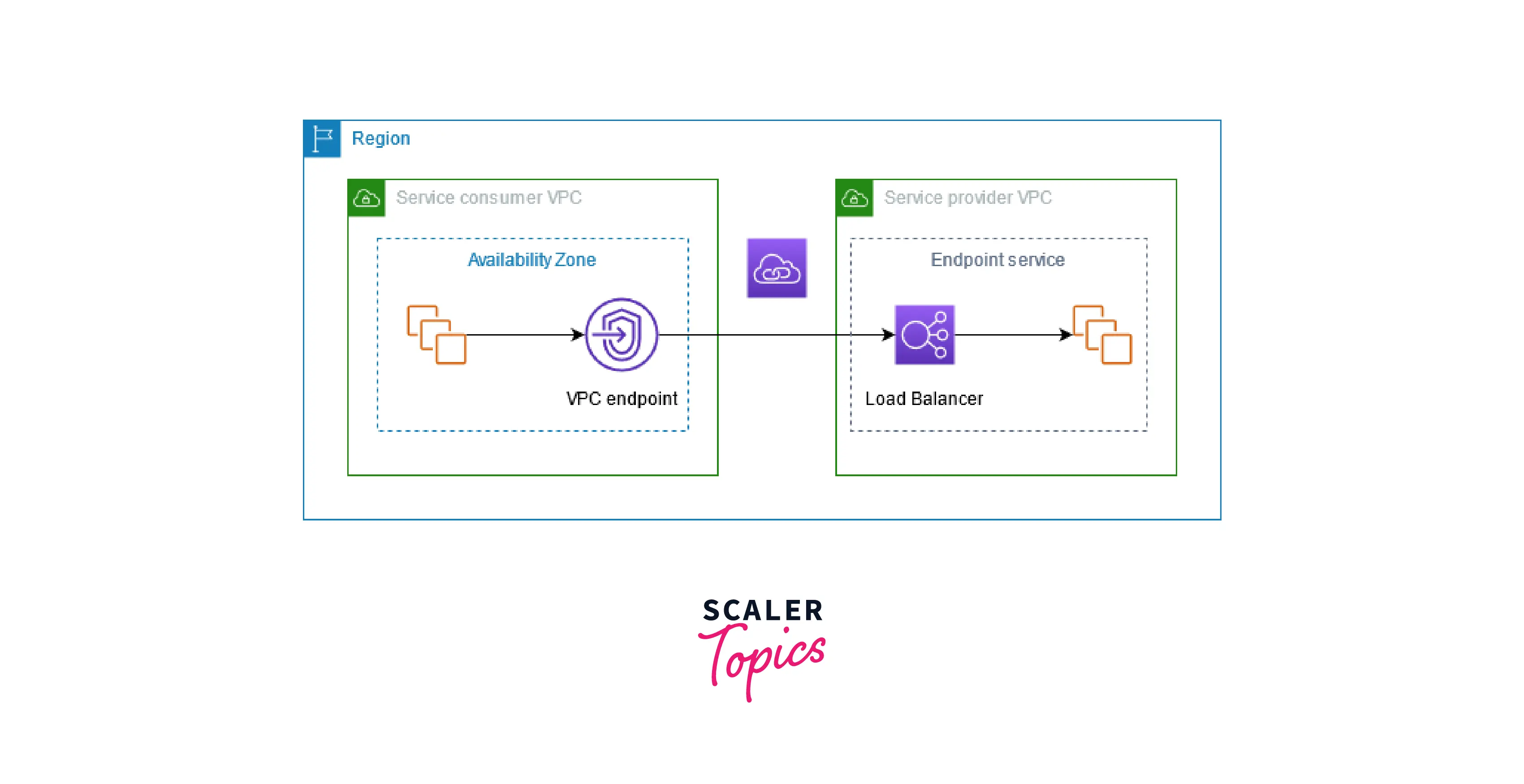
Service Providers
The person who provides a service is its owner. AWS Partners and other AWS accounts are examples of service providers. Service providers can use on-premises servers or AWS resources like EC2 instances to host their services.
Endpoint Services
To make their service accessible in a Region, a service provider develops an endpoint service. A load balancer must be specified when a service provider creates an endpoint service. Consumers of your service submit requests, which the load balancer sends to your service.
Your endpoint service is by default not accessible to service users. You must add permissions to your endpoint service that permit only certain AWS principals (AWS accounts, IAM users, and IAM roles) to connect.
Service Names
A service name is used to identify each endpoint service. When constructing a VPC endpoint, the service's name must be specified by the service consumer. The service names for AWS services are searchable by service consumers. Consumers of services must be informed of the names of the services offered by service providers.
Service States
An endpoint service could be in any of the following states:
- Pending - It is currently creating the endpoint service.
- Available - The endpoint service is accessible.
- Failed - An error occurred while creating the endpoint service.
- Deleting - The endpoint service was deleted by the service provider and is currently being deleted.
- Deleted - Endpoint service has been deleted.
Service Consumers
A service's consumer is the one who uses the service. Customers of the service have the option of using on-premises servers or AWS resources, such as EC2 instances, to access endpoint services.
VPC Endpoints
The person who uses a service is referred to as the consumer. Customers of the service have the choice of accessing endpoint services through on-premises servers or AWS resources, such as EC2 instances.
- Interface - To transmit traffic to endpoint services that use a Network Load Balancer to distribute traffic, create an interface endpoint. DNS is utilized to resolve traffic that is headed for the endpoint service.
- Gateway - Create a gateway endpoint to use private IP addresses to deliver traffic to Amazon S3 or DynamoDB. You direct traffic from your VPC to the gateway endpoint using route tables. AWS PrivateLink is not enabled on gateway endpoints.
- GatewayLoadBalancer - To transmit traffic to a fleet of virtual appliances using private IP addresses, create a Gateway Load Balancer endpoint. Using route tables, you direct traffic from your VPC to the Gateway Load Balancer endpoint. The virtual appliances receive traffic distribution via the gateway load balancer, which scales to meet demand.
Endpoint Network Interfaces
It is a network interface that the requester controls and serves as a gateway for traffic going to an endpoint service. We create an endpoint network interface in each subnet you choose when you create a VPC endpoint.
If a VPC endpoint supports IPv4, the network interfaces of that endpoint have IPv4 addresses. A VPC endpoint's network interfaces have IPv6 addresses if IPv6 is supported by the endpoint. The IPv6 address of an endpoint network interface cannot be accessed online. Take note that denyAllIgwTraffic will be activated on a network interface with an IPv6 address.
Endpoint Policies
You can connect an IAM resource policy to a VPC endpoint as a VPC endpoint policy. It chooses which principals are allowed to access the endpoint service via the VPC endpoint. The default VPC endpoint policy permits every action taken on every resource by every principal over the VPC endpoint.
Endpoint States
A connection request is sent to the endpoint service when a VPC endpoint is created. The request may be approved or denied by the service provider. The VPC endpoint can be used by the service consumer once it enters the Available state if the service provider approves the request.
A VPC endpoint could be in any of the attainable states listed below:
- PendingAcceptance - The request for a connection is pending. In the case of manually accepted requests, this is the starting state.
- Available - The VPC endpoint is accessible.
- Pending - The connection request was approved by the service provider. In the event that requests are automatically accepted, this is the starting state. If the service consumer alters the VPC endpoint, the VPC endpoint returns to the original state.
- Rejected - The connection request was turned down by the service provider. Even when a connection is made accessible for usage, the service provider has the right to deny it.
- Failed - The VPC endpoint could not be made available.
- Expired - Request for a connection has expired.
Private Hosted Zones
A hosted zone contains DNS entries that describe the traffic routing for a domain or subdomain. The routing of internet traffic is determined by the records for a public hosted zone. The traffic routing in your VPCs is determined by the records for a private hosted zone. You can set up split-horizon DNS with Route 53 by utilizing the same domain name for both a public website and an endpoint service supported by AWS PrivateLink.
Features of AWS PrivateLink
- Service Usage Via Amazon PrivateLink: Establish an interface VPC endpoint for service outside your VPC to leverage Amazon PrivateLink. Doing this creates an elastic network interface with a private IP address in your subnet and acts as a gateway for traffic going to the service.
- Using Amazon PrivateLink to Share your Services: You can build your own endpoint service (powered by Amazon PrivateLink) and provide other Amazon Web Services users access to it.
- Integration with AWS Marketplace: AWS Marketplace and PrivateLink can be connected with a quick search of the services provided by AWS PrivateLink. In order to make it simpler to tell which services are linked to your endpoint, services that are available through the AWS Marketplace are supported with vanity DNS domains.
- Accessing your On-Premises Applications Privately: The capability for private connectivity using AWS Direct Connect provided by Interface VPC endpoints enables applications running on your premises to connect to these services across the Amazon private network.
AWS PrivateLink Use Cases
- Access AWS Services Safely: Connect to AWS services from your VPC and on-premises locations to securely and privately move important data. You can establish a private, secure, and scalable connection between your VPC and AWS services and SaaS applications using AWS PrivateLink. You are protected against unsolicited contact from the service provider because service connections can only be started by you.
- Maintain Adherence to Regulations: You can retain compliance with rules such as HIPAA, EU/US Privacy Shield, and PCI by banning the transmission of sensitive data, such as customer records, via the Internet. Customers in the government, healthcare, and financial services sectors in particular need to be aware of this. Traffic between AWS resources, VPCs, and external services is kept on the Amazon network, which is subject to strict security and compliance regulations.
- Switch to a Hybrid Cloud: Using AWS Direct Connect or AWS VPN, on-premises applications can connect to service endpoints in an Amazon VPC, redirecting traffic to AWS services through AWS PrivateLink while keeping all network traffic inside the Amazon network. SaaS organizations can now provide services that appear to be hosted on a private network thanks to AWS PrivateLink.These services can be securely accessed from both the cloud and on-site locations in a highly available and scalable manner using AWS Direct Connect and AWS VPN.
- Provide SaaS Services Through APN: Services provided by AWS Partners are housed on a private network yet are safely accessible from the cloud and on-site.
AWS PrivateLink Pricing
To provide private connectivity to a service that is either owned by AWS or by a customer or partner of AWS, you can construct AWS PrivateLink endpoints. Regardless of how connected to the service your VPC endpoint is, you will be charged for each hour it remains provisioned in each Availability Zone. Gigabytes handled through the VPC endpoint are subject to data processing fees, independent of the origin or destination of the traffic. Each consumed partial VPC endpoint-hour is invoiced as a complete hour.
Interface endpoints and Gateway Load Balancer Endpoints are the two types of AWS PrivateLink endpoints available for use. The following are the rates that apply depending on the type of endpoint you use:
Interface Endpoint pricing
Accessing services like AWS services, internal application services, or SaaS services that are being run outside of your VPC can be done secretly and securely via interface endpoints.
| Data Processed per month in an AWS Region | Pricing per GB of Data Processed ($) |
|---|---|
| First 1 PB | $0.01 |
| Next 4 PB | $0.006 |
| Anything over 5 PB | $0.004 |
Gateway Load Balancer Endpoint Pricing
Gateway load balancer endpoints can be used to covertly and securely inject network and security services running outside of your VPC into your traffic flow, including firewalls, intrusion detection and prevention systems, monitoring, analytics, and other services.
Benefits of AWS PrivateLink
The following are some advantages of using AWS PrivateLink:-
- Secure Traffic: Your VPCs can be securely and scalably connected to AWS services using AWS PrivateLink. Due to the fact that AWS PrivateLink traffic does not go over the open Internet, it is less susceptible to threats like distributed denial-of-service attacks and brute force attacks. To make your services seem as though they were hosted on your private network, you can use private IP connectivity.
- Streamline Network Administration: The linking of services across multiple accounts and Amazon VPCs does not need the use of firewall rules, path definitions, or route tables. You don't need to configure an Internet gateway, connect to a VPC peering network, or manage VPC Classless Inter-Domain Routing in your VPC (CIDRs). AWS PrivateLink streamlines your network design, making it simpler to manage your worldwide network.
- Improve Cloud Migration Speed: Traditional on-premises applications can more easily be migrated to cloud-hosted SaaS services thanks to AWS PrivateLink. You can move your data and make use of extra cloud services to ensure that your traffic is secure because your data isn't exposed to the Internet, where it can be hacked. You can no longer choose between using a service and disclosing sensitive information online. You may get the most recent regulations to help clients stay compliant on our website for AWS Compliance Programs.
- Automation Capability: You may build an even more user-friendly, straightforward PrivateLink workspace by automating your infrastructure and configuration management using a Terraform Provider supporting SaaS, like the one from Databricks.
FAQs
Q: What Exactly is AWS PrivateLink?
A: You can use private IP addresses in your VPC to connect to some AWS services, endpoint services (services hosted by other AWS accounts), and supported AWS Marketplace partner services.
Q: What is the Console?
A: To access and use GuardDuty, use the console, a browser-based user interface.
Q: What Are the Benefits of AWS Privatelink?
A: The advantages of AWS Privatelink are as follows: It speeds up your transfer to the cloud, encrypts your traffic, and makes network administration simple.
Q: What are the Benefits of Using a VPC Endpoint with AWS PrivateLink?
A: End users might gain several ways from VPC endpoints' secure access to a particular service.
- With no requirement for an Internet gateway, NAT gateway, VPN connection, or VPC peering connection, VPC endpoints offer access to a particular service, lowering the dangers of exposing your resources to the Internet or other external networks.
- The risks associated with exposing your traffic to the Internet are decreased because your traffic stays within Amazon's private network.
- You can limit access through a VPC endpoint to particular individuals, actions, and resources when using VPC endpoints to access Amazon services.
Q: How Do I Discover Which Services Are Available Today?
A: With the help of the VPC console or the AWS CLI/SDK, you can look up services that are offered. After that, you can use a VPC endpoint to request access to a service.
Conclusion
- In this article we learned about what is AWS PrivateLink. You can use private IP addresses in your VPC to connect to some AWS services, endpoint services (services hosted by other AWS accounts), and supported AWS Marketplace partner services.
- This article also explained some of the key features of AWS PrivateLink. It also explained how efficiently we can integrate AWS PrivateLink with AWS MarketPlace.
- To use PrivateLink AWS, you need to establish an interface VPC endpoint for a service in your VPC.
- It furthers the primary concepts involved in AWS PrivateLink. It covered the Architecture Diagram, Service Providers, and different Service Customers of AWS PrivateLink.
- We also learned some of the use cases of AWS PrivateLink. It explained how securely we can handle AWS with AWS PrivateLink.
- We went through the pricing of AWS PrivateLink. It explained Interface endpoints and Gateway Load Balancer Endpoints are the two types of AWS PrivateLink endpoints available for use.
