AWS Service Control Policy (AWS SCP)
Overview
AWS Service Control Policy works with the AWS Organization Service. AWS Service Control Policy enables customers to grant granular access to all AWS organization member accounts. Service control policies, or AWS SCPs, are represented in JSON just like IAM policies. AWS SCPs can be attached only to the AWS Organization level. Customers can apply SCPs to only member accounts in an organization. They have no effect on users or roles in the AWS management account.
What is AWS SCP (Service Control Policy)?
AWS Organization is one of the AWS Services. It is used to manage multiple AWS accounts in a single AWS account. It was also used to create a new AWS account. There are two types of accounts represented in the AWS organization. They are
- Management account
- Member Account
- The management account is the AWS account where the AWS Organization is enabled.
- A member account is the AWS account that is invited to add resources to the AWS Management account.
- Now back to the service control policy, A service control policy is like an IAM policy with JSON syntax. It offers central control over the maximum available permission for all the member AWS accounts.
- SCP takes effect on member accounts only, not on management accounts.
- AWS SCP is not enough to take action by the IAM user or role in the member account within an organization. The administrator of the member account still attaches permissions or policies for the IAM user or role to perform the action.
- Then the permissions of the logical intersection between the SCP policy and the IAM policy are evaluated; if there is no deny in the SCP policy, the IAM user or role is able to perform the respective action.
Testing Effects of SCPs
- AWS strongly recommends that you don't attach SCPs to the root of your organization without thoroughly testing the impact that the policy has on accounts.
- Instead, create an OU that you can move your accounts into one at a time, or at least in small numbers, to ensure that you don't inadvertently lock users out of key services.
Maximum Size of SCPs
AWS SCPs are also represented in JSON like IAM policy.
| Description | Limit |
|---|---|
| Maximum SCPs attached to root | 5 |
| Maximum SCPs attached per Organizational unit | 5 |
| Maximum SCps attached per account | 5 |
| Maximum size per SCPs document | 5120 Bytes |
Note: Every entity must have at least one SCPs attached to it all the time.
Inheritance of SCPs in the OU Hierarchy
Consider the below example
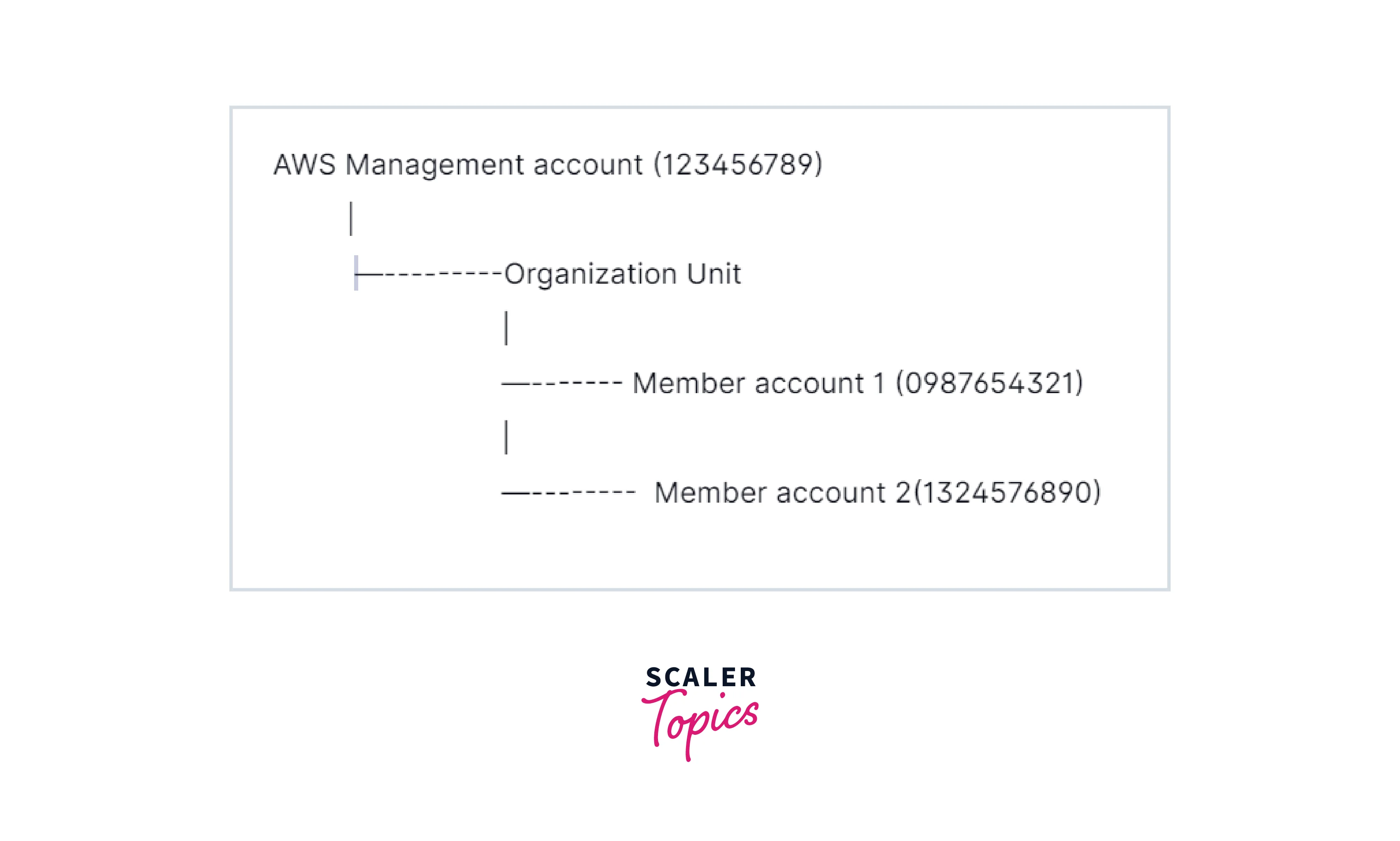
We can attach the SCP at the root level or organizational unit level or member account level.
If we attach the SCP at the organizational unit level, the member account associated with the Organizational unit will inherit the Service control policy
If we apply the SCPs at the root level, all the aws member accounts and organization units will inherit the Service control policy.
So, it is important for the customer to attach the SCP at the right level to inherit the permission across organization and member accounts.
SCPs Effects On Permissions
What are the entities the SCP can affect?
- SCPs will affect the IAM user and roles in the AWS member account.
- SCP will not affect the IAM users and roles in the management account.
- Scps will not affect IAM users and roles outside of the organization. i.e., if the requestor is not a member of an AWS organization or does not have an AWS member account, SCPs will not affect the permission or usage of those resources.
Example
Consider the below scenario:
There are two AWS accounts, namely Account A and Account B. There is one AWS Organization. Under this organization, Account A is the member account. There is one SCP attached to the Account A member account stating that IAM users in Account A will only access S3 resources. In the S3 resources, access for Account B is allowed in the bucket policy.
- Now, if the Account B IAM user tries to access the S3 resources, he/she will be able to get them.
- Because Account B is not part of the AWS organization, SCP won’t control the AWS account outside the organization.
- In Account A resources, i.e S3, there is the necessary permission for account B. So SCPs can’t affect resource-based policy directly.
Using Access Data To Improve SCPs
- Customers can use the AWS CLI, AWS API, or AWS Management Console to view the service whose data was last accessed for an AWS Organization entity or policy.
- The data consists of information about IAM users and roles in an AWS Organization account.
Tasks And Entities Not Restricted By AWS SCPs
The following tasks cannot be completed in an AWS organization by enforcing or utilizing service control policies.
Task on Management Account
- AWS management account actions performed and executed
- Make trusted signer functionality available for CloudFront private content.
- Task performed by the root user
- Register for the Enterprise Support Plan.
- Changes between the AWS Support Plan
- To set up reverse DNS on the Lightsail server and EC2 instances
Task on an AWS Account was Created Before September 15, 2017
- If the AWS accounts were previously created, AWS recommends that you do not rely on AWS SCP to limit permissions and restrict operations.
- Customers cannot change the root user's multi-factor authentication settings.
- The x.509 keys can't create, update, or delete for the root user.
- Customers cannot change the root user's password.
- Customers cannot create, update, or delete root access keys.
- If the AWS accounts are created after September 15, 2017, AWS SCP will prevent the root user of the member accounts from executing the action as well.
Task on AWS-Related Service
- Alexa Top Sites
- Alexa Web Information Service
- Amazon Mechanical Turk
- Amazon Product Marketing API
Creating, Updating, and Deleting SCPs
Create an AWS SCP
- Go to the AWS Organization console and select the Services in the left navigation pane
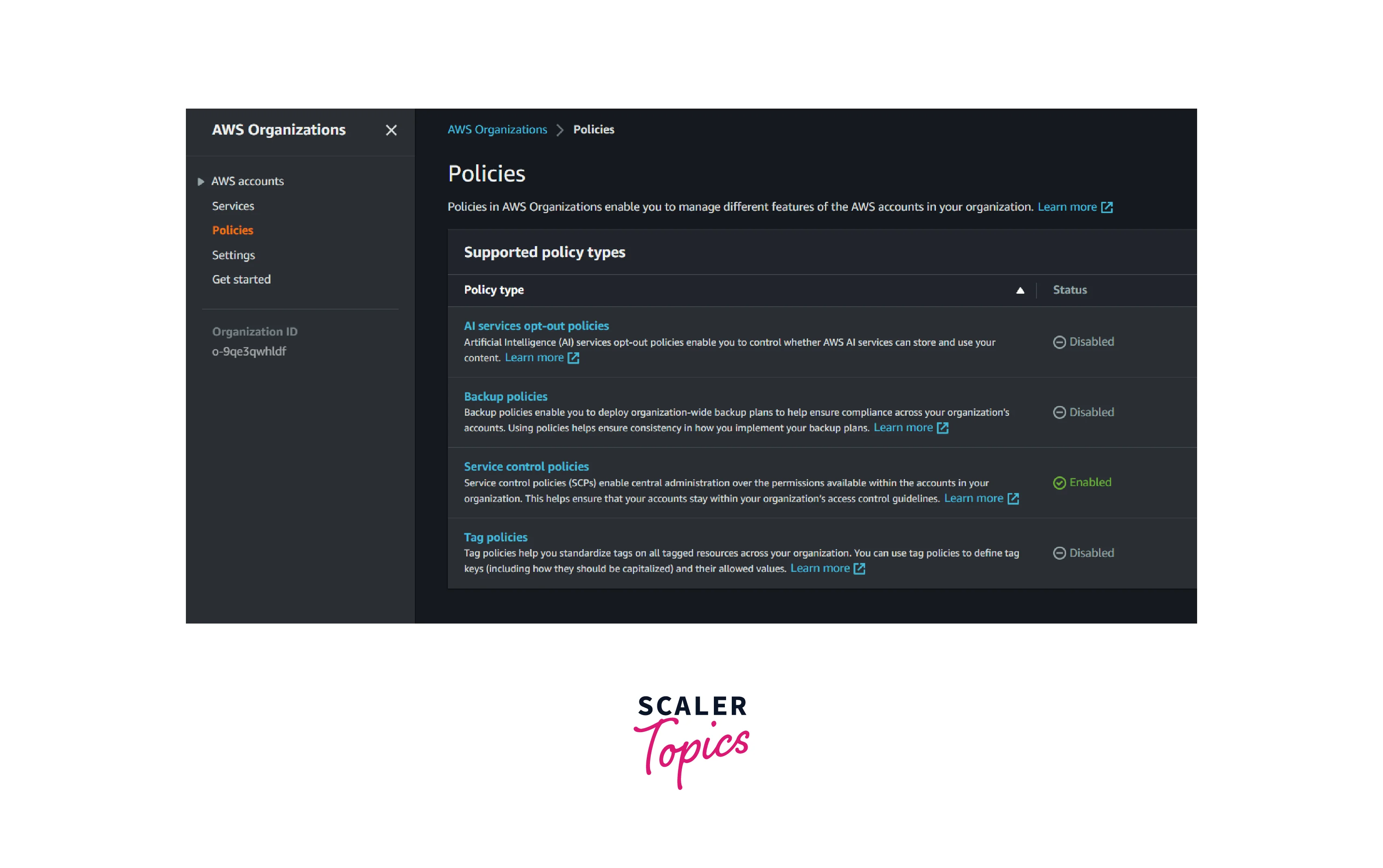
- Select the Service control policies and Click create policy
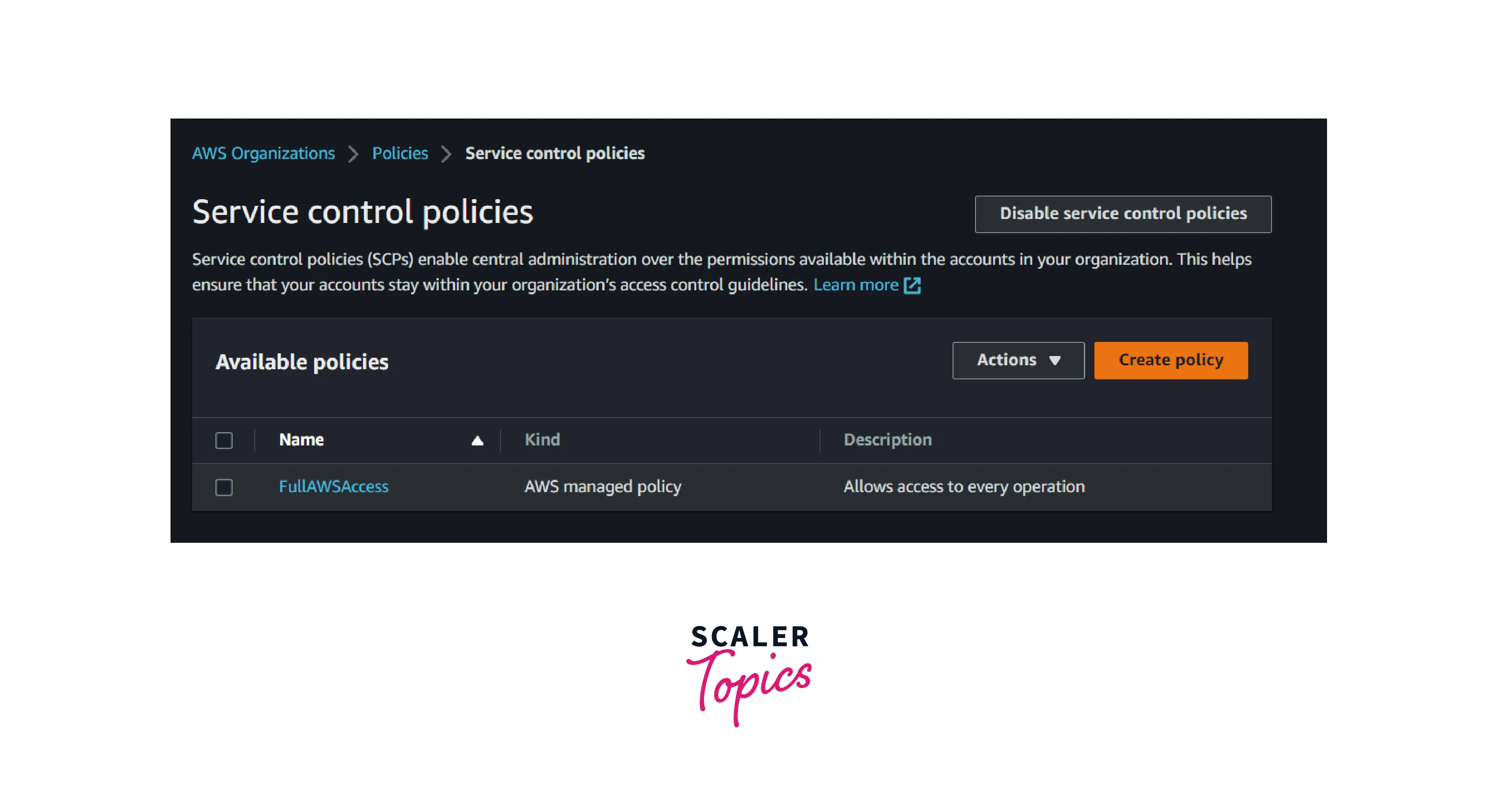
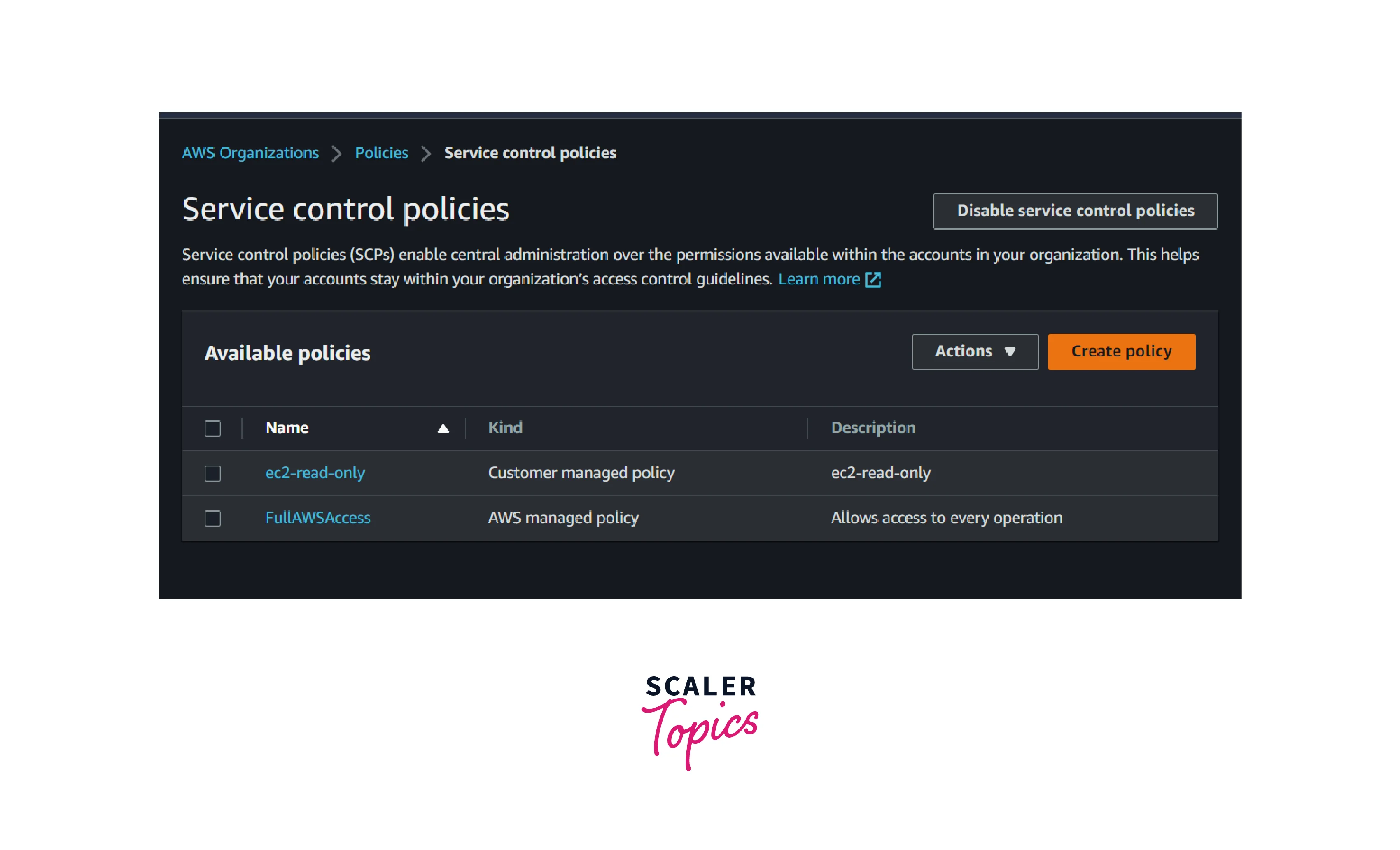
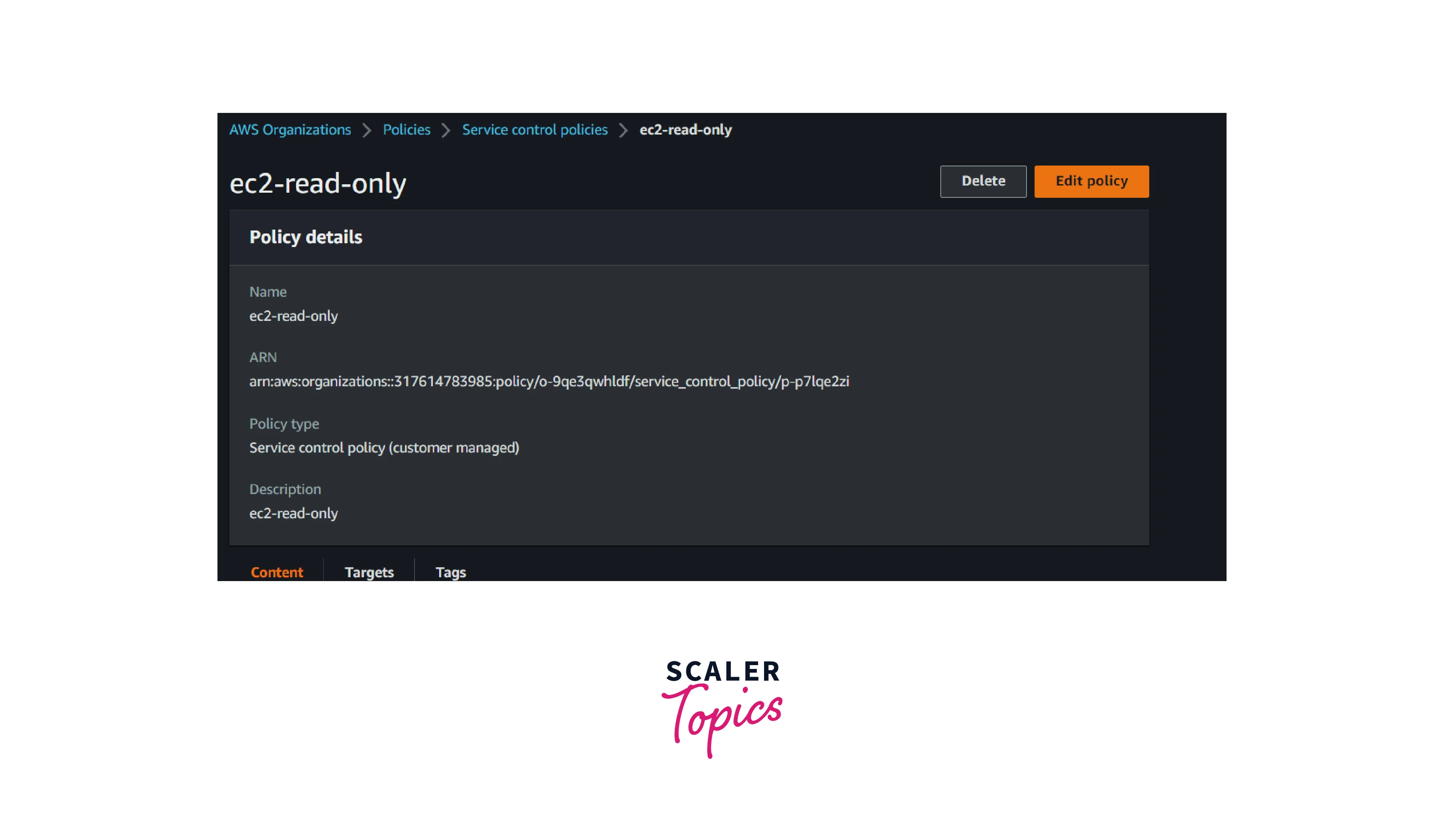
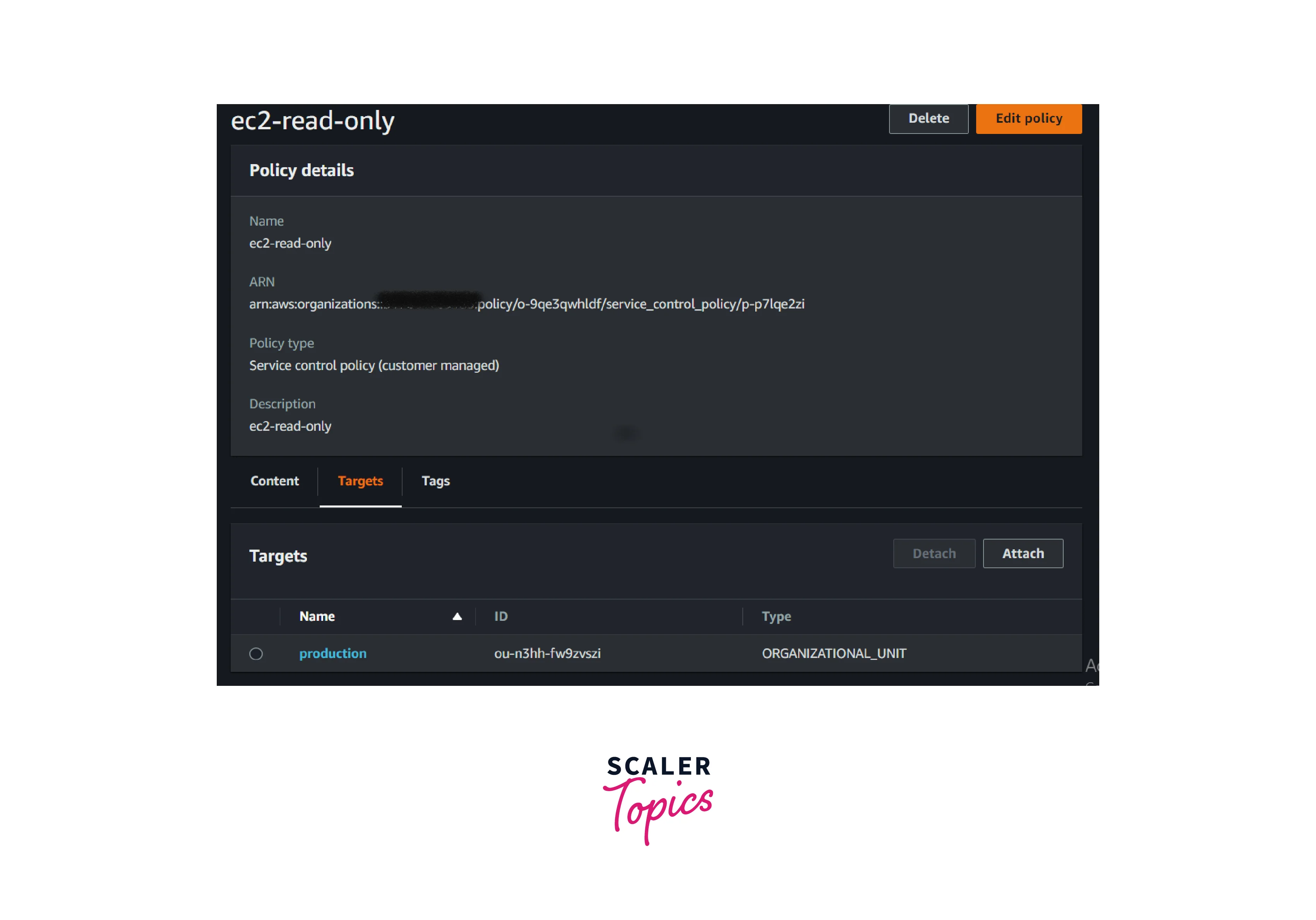
- Enter the name as ec2-read-only and paste the below JSON and click the save the button
- The above policy will allow the IAM identities to read the EC2 resources. If any IAM role or users try to stop or start the instance, they will get an error stating that the particular action is not authorized.
Update an AWS SCP
- Click the created SCP and select the Edit Policy
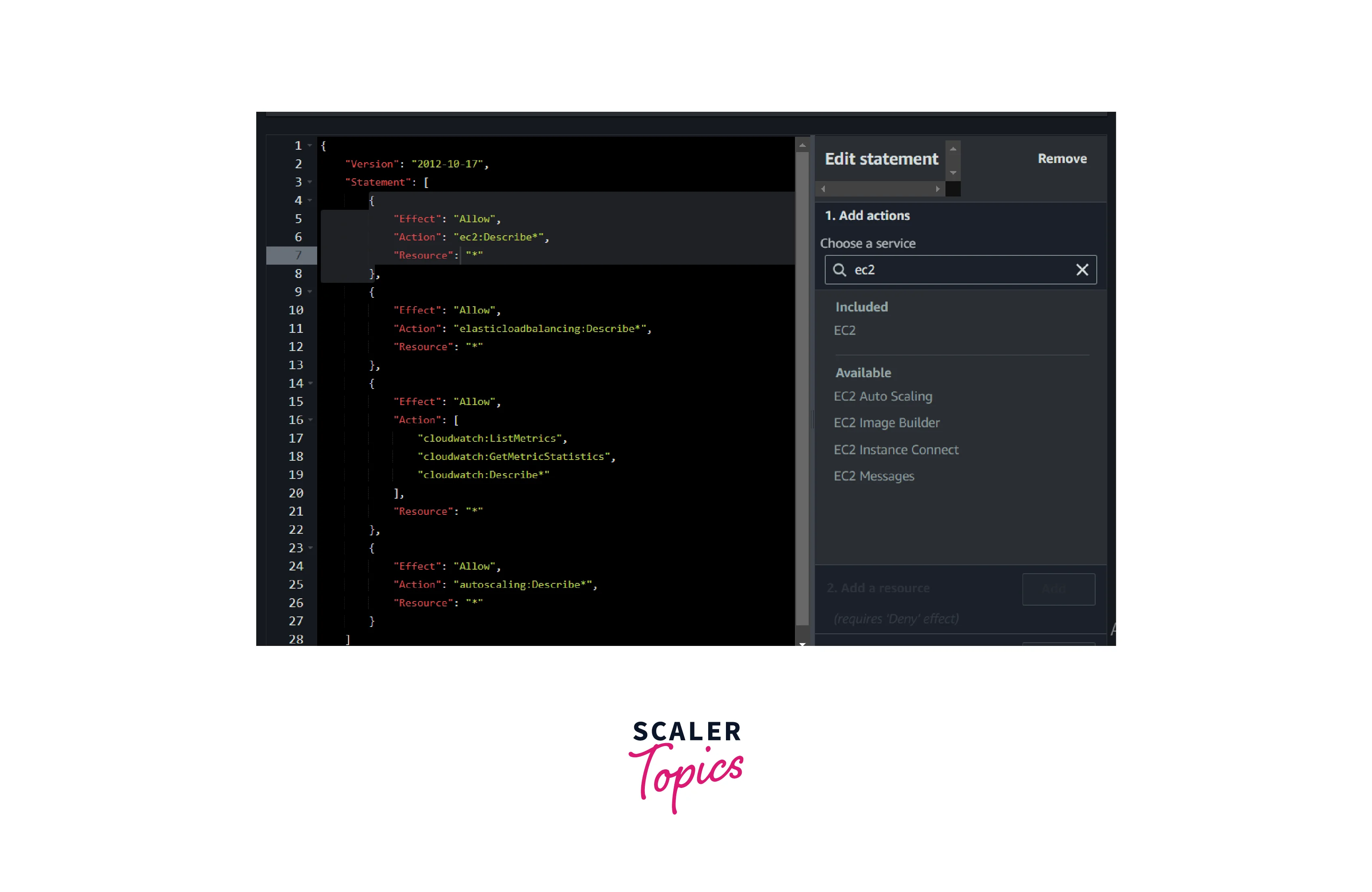
- Select EC2 and select all actions; it will add the below statement to the existing policy.
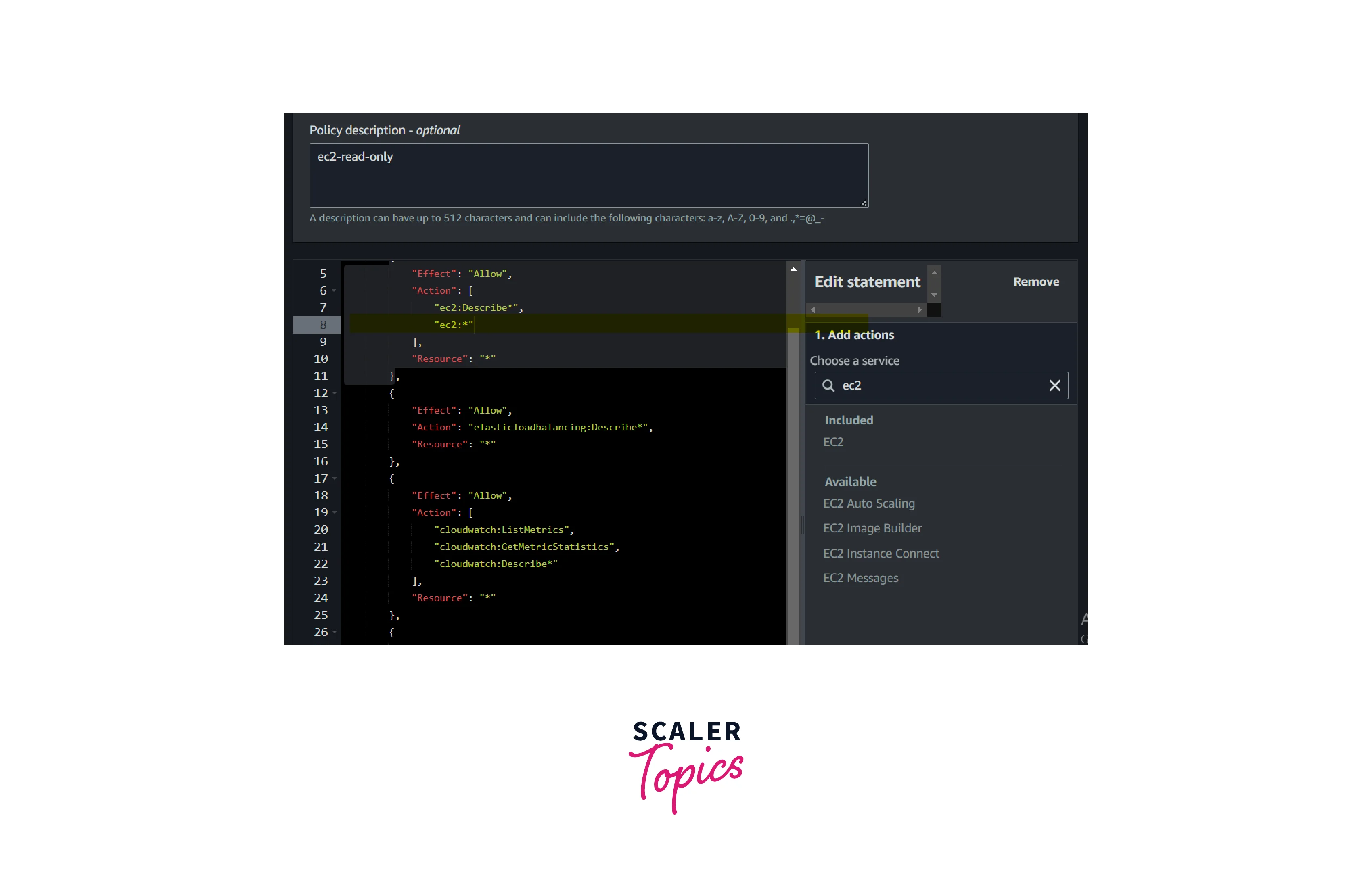
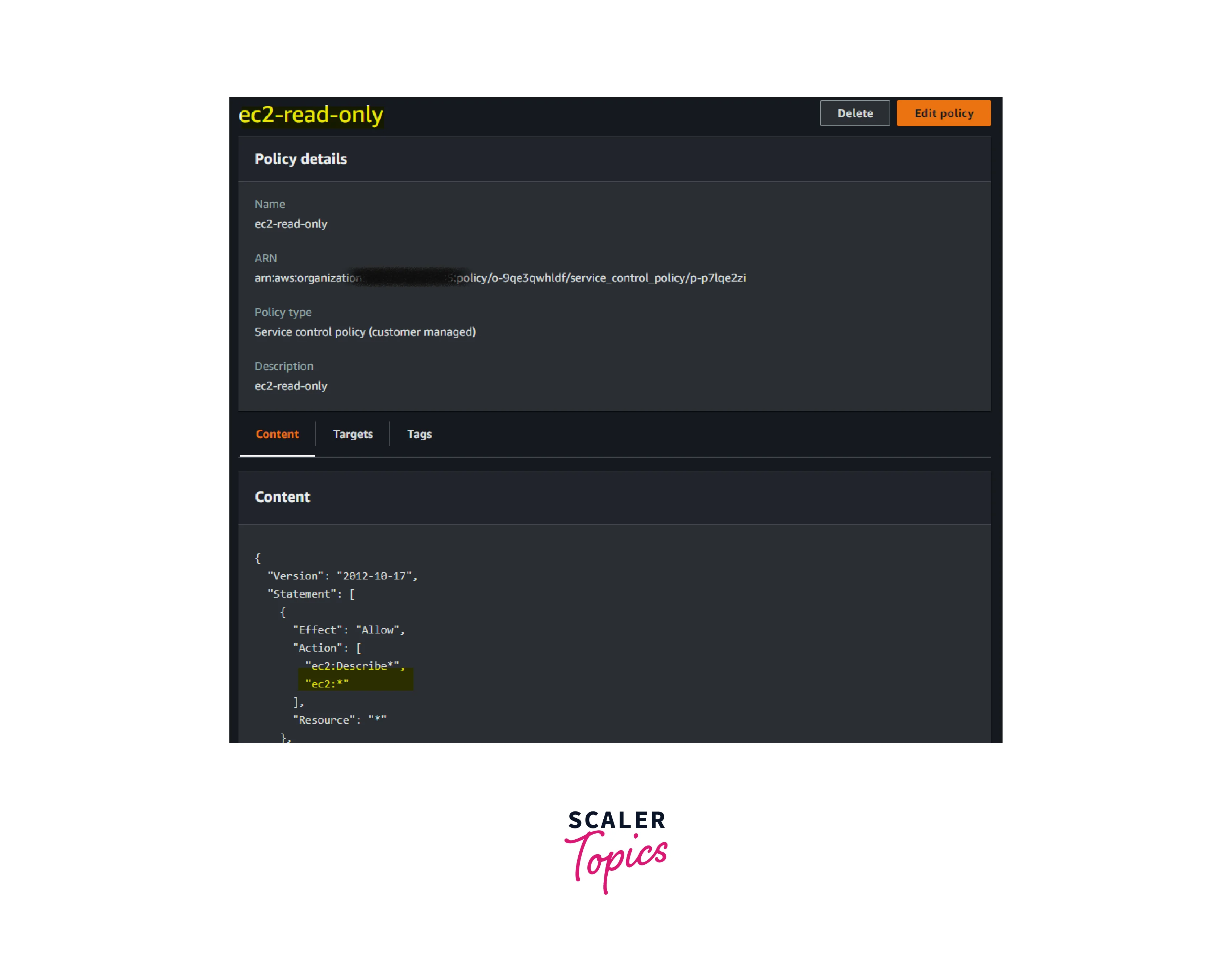
- Now the policy is to have full access to AWS EC2 resources.
- Review the policy and save it.
Delete an AWS SCP
- Select the AWS SCP that you wish to delete and select the action button.
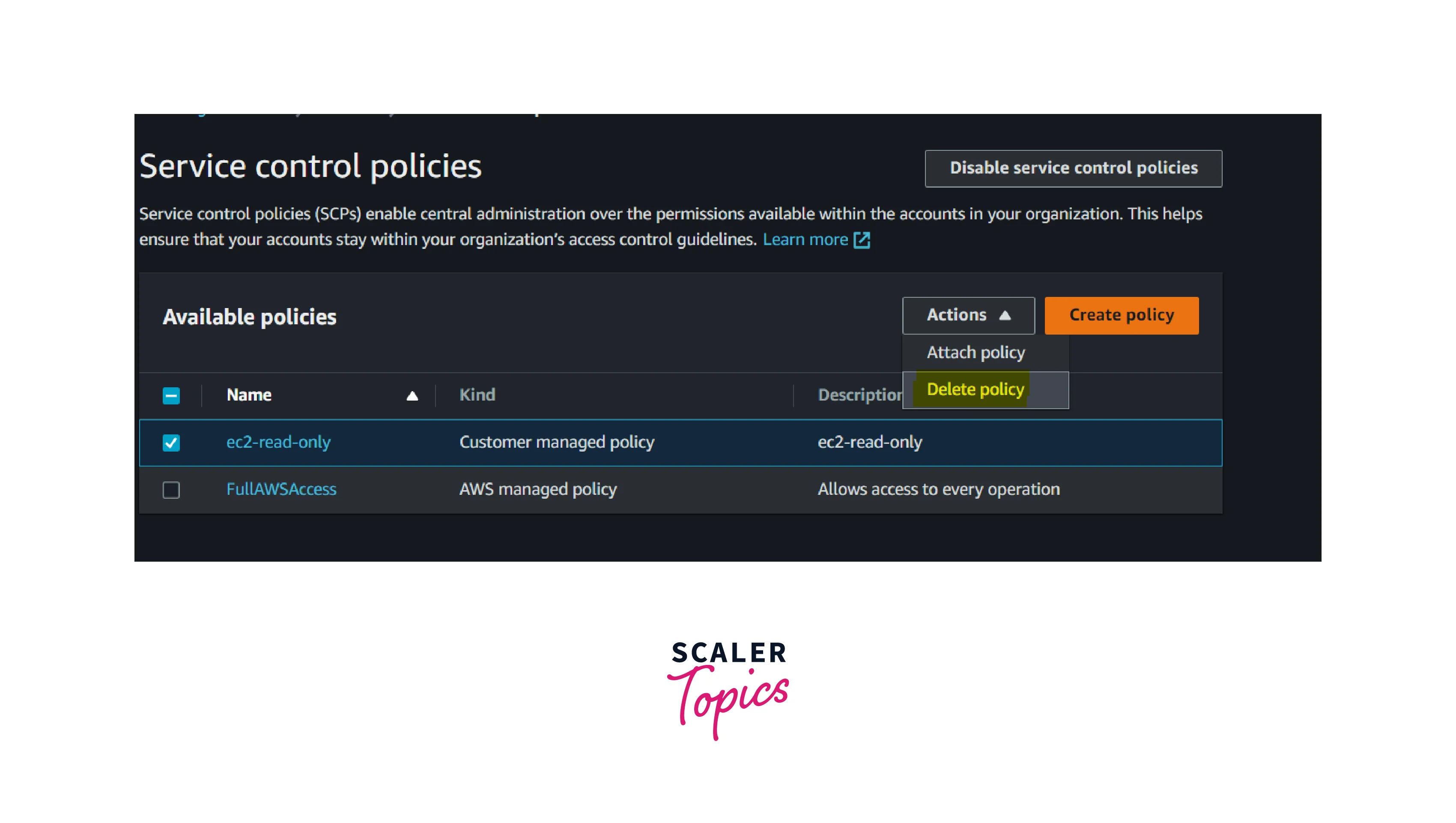
- To delete the policy, click the delete policy button.
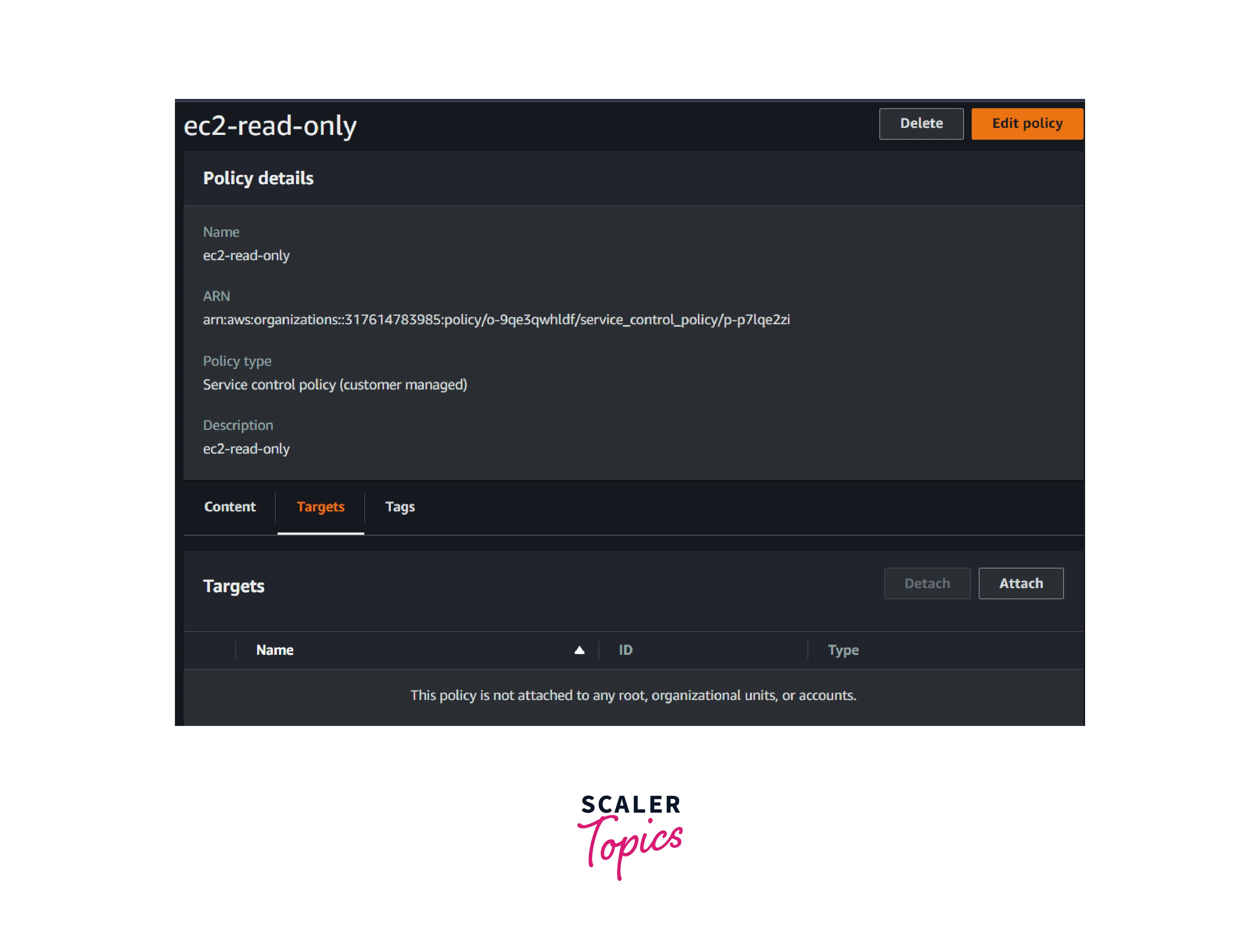
Attaching And Detaching SCPs
- Go to the AWS Organization and select the AWS Service Control Policy.
- Select the Target tab. We can attach or detach the SCP to or from the AWS member account or Organization unit.
- Select the AWS OU or AWS Member account (if applicable) and select attach a policy
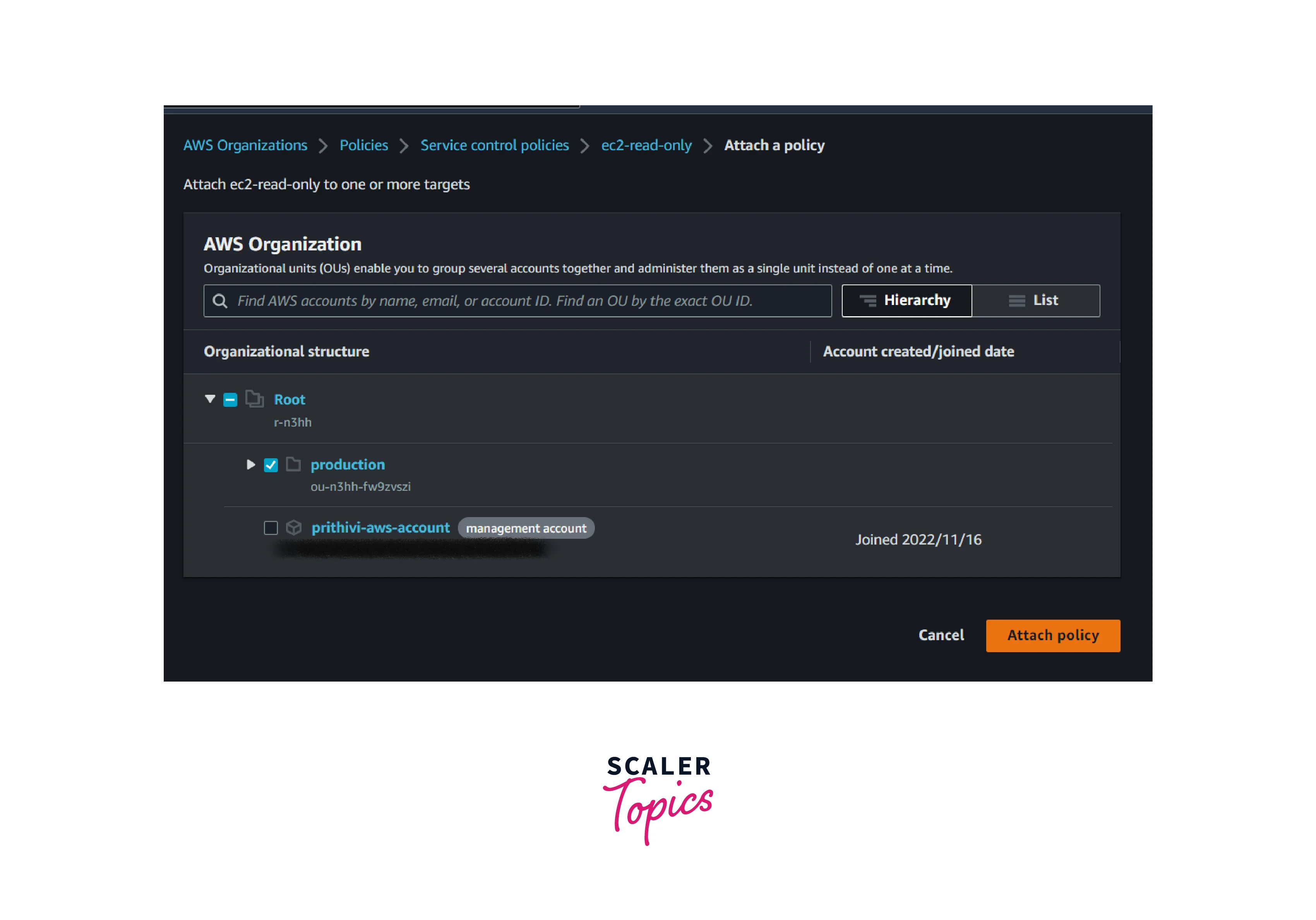
- Select Attach or detach as per the requirements. The same process will be followed for detaching the policy.
Strategies For Using SCPs
We can use SCP in two ways: They are
-
Use SCP as Deny List
-
Use SCP as Allow List
1. Use SCP As Deny List
By default, all the actions will be denied permission. We need to choose which actions and resources are not prohibited.
The above policy prevents Dynamodb from performing any actions. if this service control policy is attached to the AWS account.
Then the IAM user with DynamoDB full access will not be able to access the DynamoDB resources.
Because AWS SCP supersedes the IAM policy.
2. Use SCP As Allow List
By default, all actions are prohibited; we must select which actions and resources are permitted.
The above policy allows all actions for EC2 and CloudWatch services and resources.
- The IAM user or role with an IAM policy providing EC2 and cloud watch access will be able to access the service in the member account.
- Even if the permissions are provided in the service control policies, we still need to attach the IAM policy to the IAM entities within the AWS account or AWS Member account, and then only will it work.
- Similarly, customers can limit the permissions of the IAM identities at the organization level or account within the organization using AWS service control policies.
SCP Syntax
AWS Service control policy and IAM policy is using the similar JSON syntax
JSON - JavaScript Object Notation
Certain elements have certain actions. They are
| No. | Elements | Supported Actions |
|---|---|---|
| 1 | Version | Allow, Deny |
| 2 | Statement | Allow, Deny |
| 3 | Statement ID (SID) | Allow, Deny |
| 4 | Effect | Allow, Deny |
| 5 | Action | Allow, Deny |
| 6 | NotAction | Deny |
| 7 | Resource | Deny |
| 8 | Condition | Deny |
Version Element
Every version must start with version and its value will be 2012-10-17
"Version": "2012-10-17",
Statement Element
SCP consists of statement elements in the policy. customers will be able to have only one statement per SCP Policy.
In the below policy, we could see that the policy contains only one statement, within that statement relevant elements are allowed or denied.
Example 1
Example 2
Statement ID Element
Statement ID or SID is an optional identifier, we can use in the SCP syntax for our general purpose of identification.
There will be no effect if we won’t use the SID in the policy.
Effect Element
Statement element will contain either allow effect or deny effect in the SCP policy
ALLOW Effect
In the above policy, users in the account will be able to access the S3 resources.
DENY Effect
In the above policy, if the user tries to launch an instance and the instance type is not m5.large, the user will not be able to launch the EC2 instance.
The service control policy will deny the permission
Note: In addition to the SCP, IAM Users should have the necessary IAM policy associated with them
Action Element
Action elements describe what actions are allowed or denied by the policy.
If the action contains “*”. It will represent all actions.
The permission for the actions will be determined by the Effect allow or deny statement.
NotAction Element
NotAction element is rarely used in the SCP policy. It helps to ignore a particular action while mentioning the group's actions.
In the above example, we could see all the resources in the us-west-1 region are denied except IAM.
NotAction elements are used in this kind of limited restriction usage.
Resource Element
Resource element represents the resources of the particular service.
For example, In s3 service, we can mention the resources as their bucket or object or both.
If we put “*” in the resource statement, it will take effect to allow or deny all the principle
In the above example, the role named “role-to-deny” is denied for the action mentioned the action element
Condition Element
Condition elements support deny action only.
The above policies restrict any actions outside of the ap-south-1 region except for the listed actions
Why You Should Use AWS Service Control Policies (SCPs)?
- AWS organization is the single solution for customers who have multiple AWS accounts and want to control all AWS account resource access from a single location.
- In an AWS organization, we can control the member AWS accounts using the service control policy.
- If customers want to delegate access to the specified region or service, they can implement SCP across all the AWS accounts in the AWS Organization console.
- In this kind of scenario, SCP will help customers provide granular permissions to the AWS organizational unit and its member accounts.
- AWS SCP also helps the AWS account prevent security posture risks for the AWS account.
Scenario
Consider the following scenario: the organization has one management account and three member accounts.
One management account: the master account
Member Account 1 : Production Member Account 2 : Non-production Member Account 3 : auditing
- We can use SCP to ensure that IAM identities auditing member accounts (Account 3) do not have access to production accounts (Member account 1) or non-production accounts (Member account 2).
- By doing so, we can limit access to our account.
AWS SCP Examples And Implementation
In this demo, we are going to restrict S3 service to all the IAM entities.
First, we create an S3-deny-policy and attach it to the OU or the member account.
- Go to the AWS Organization console and select Policy and click create policy
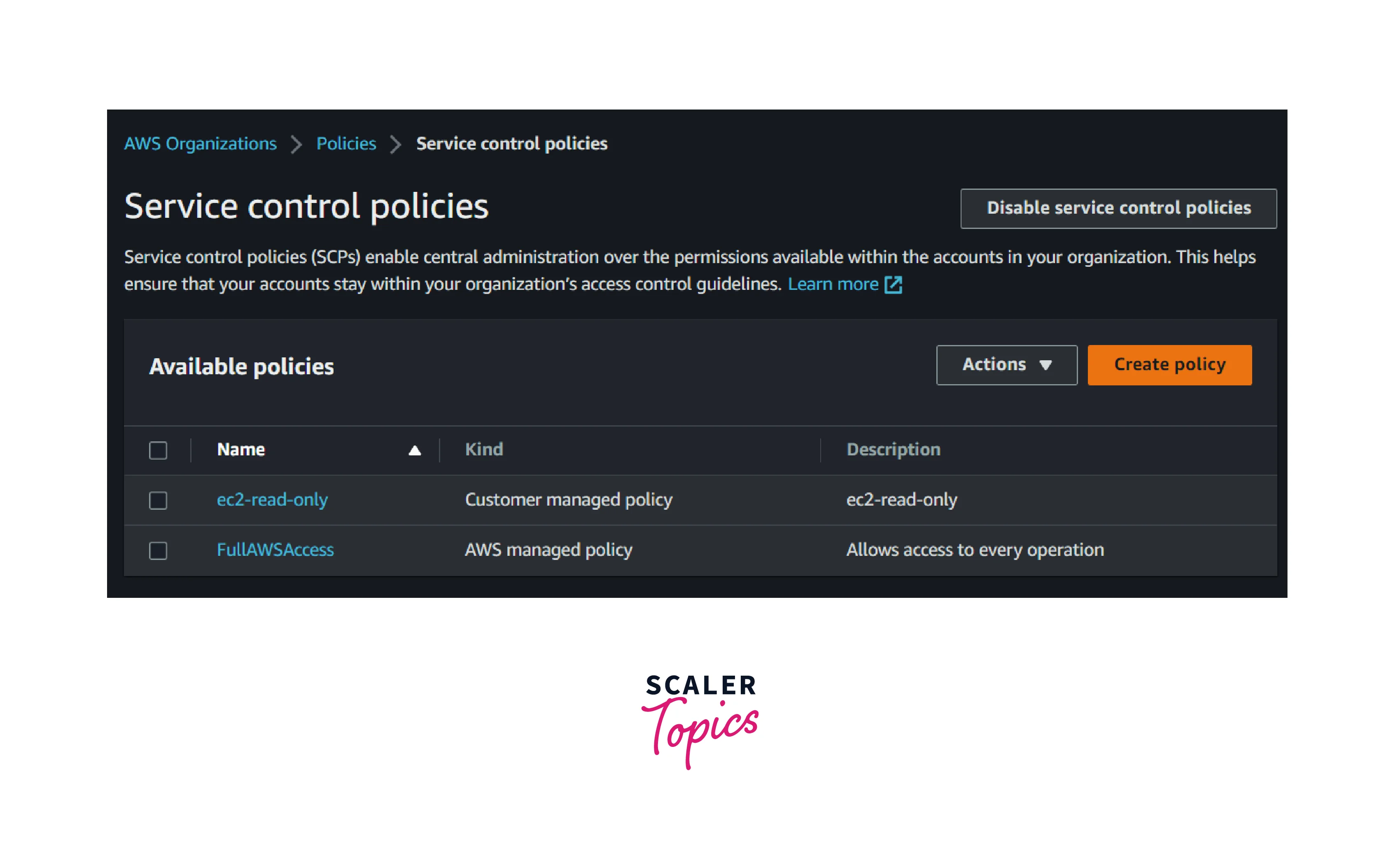
- Enter the policy name and description as S3-deny-policy
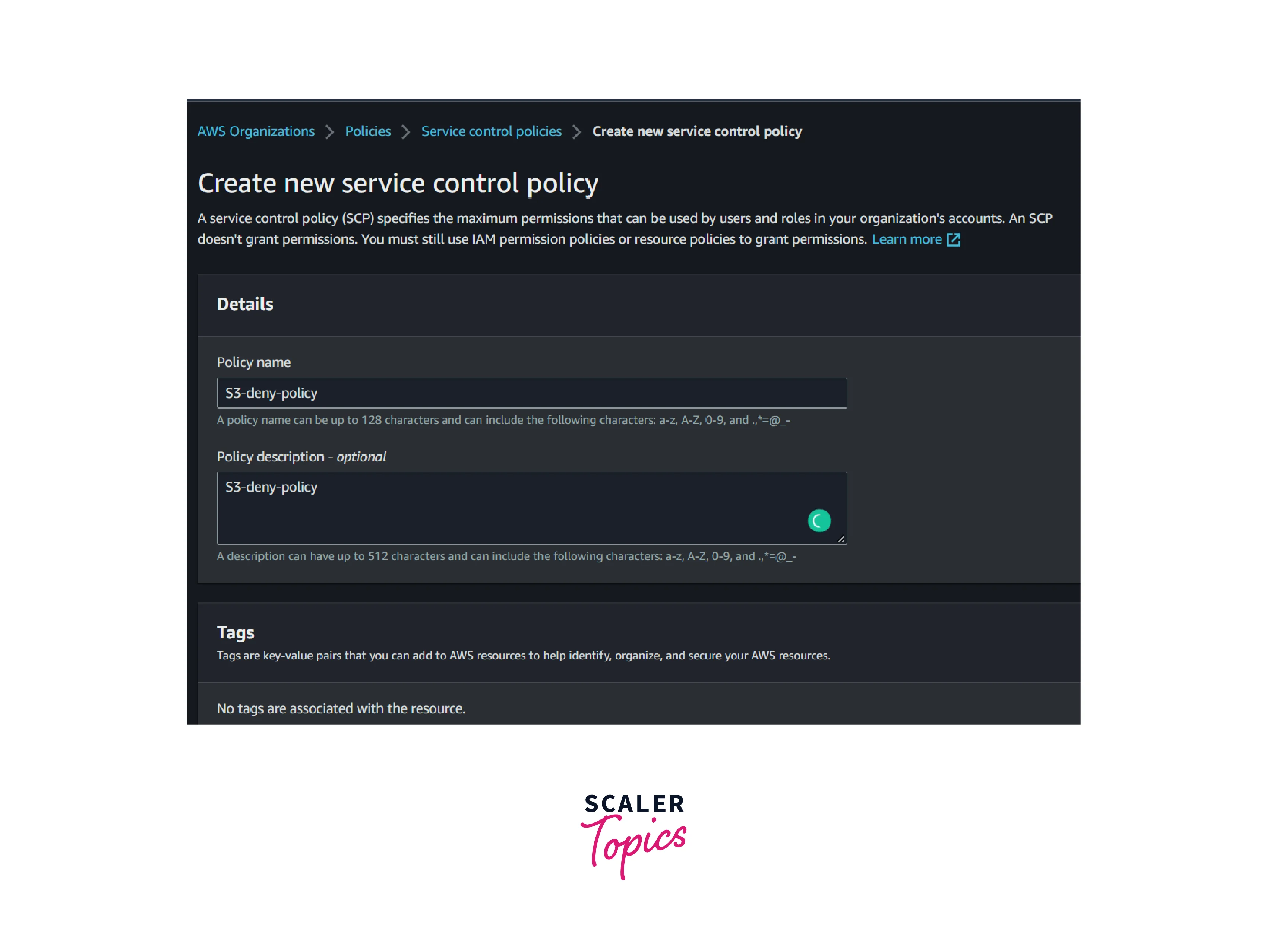
- Copy and paste the below-mentioned JSON policy or modify it as per the policy mentioned below in the console. Then click create policy
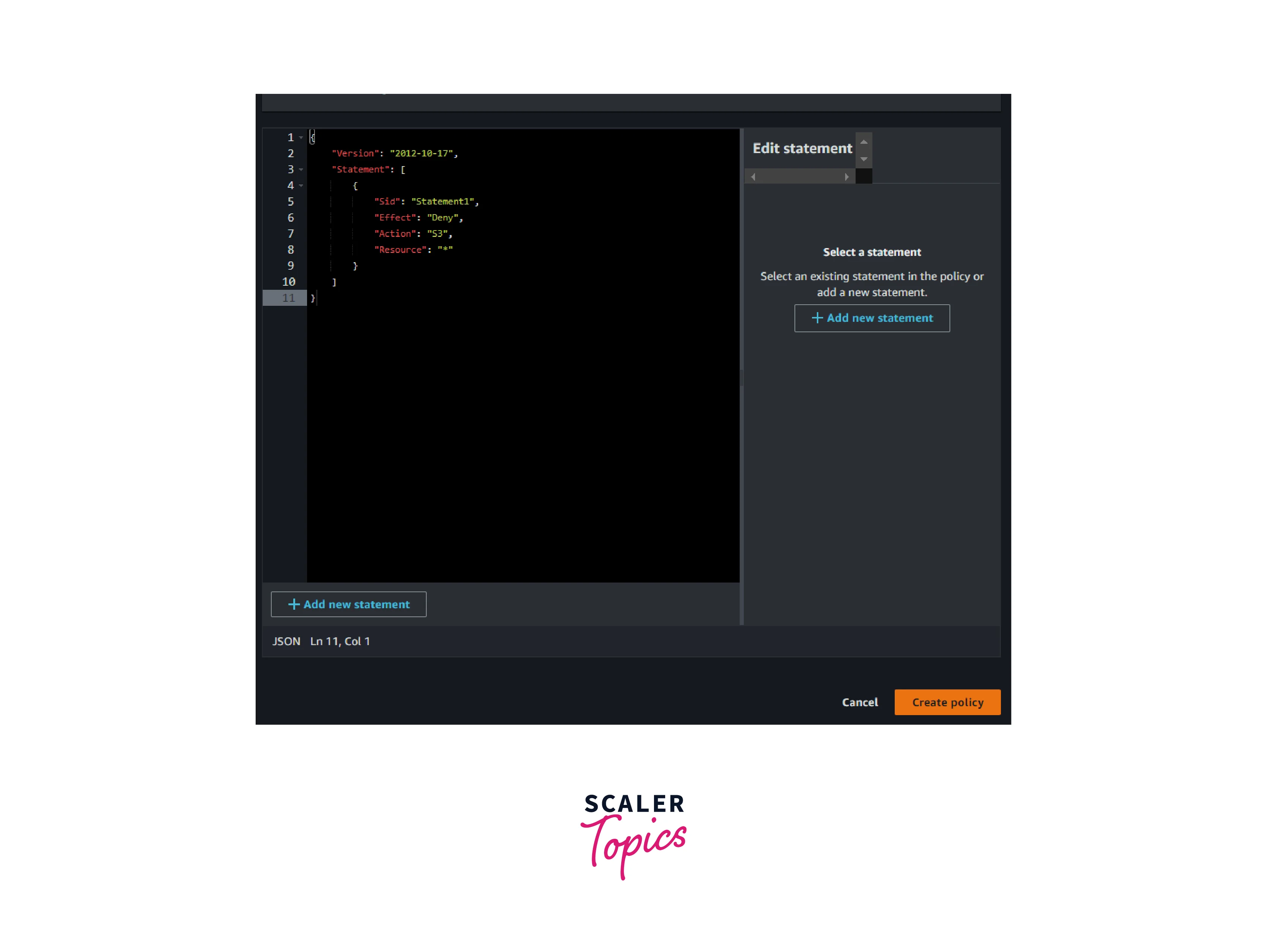
- Select the created policy and choose Attach Policy option showing under the Action menu
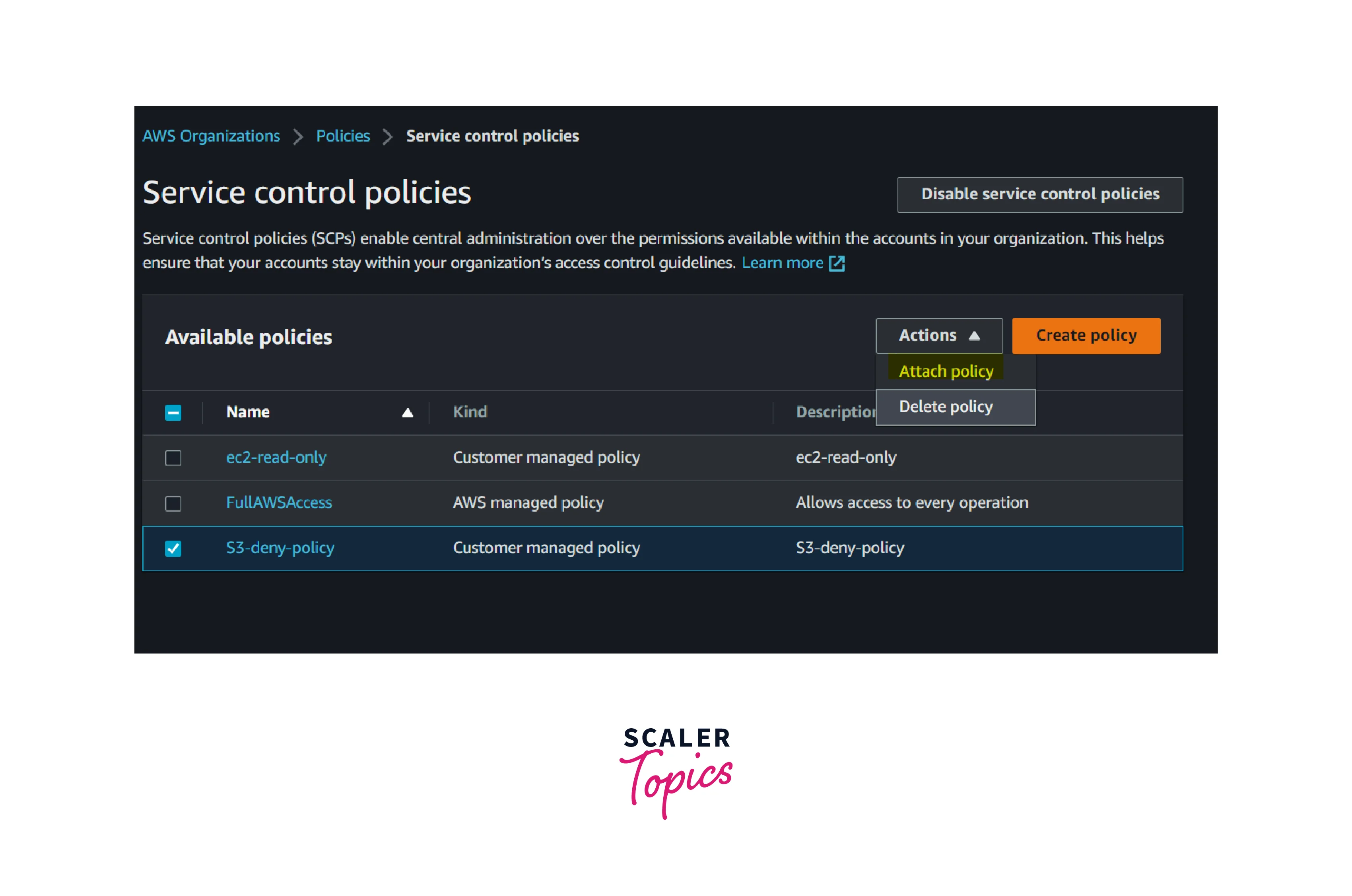
- Select the organization unit you wish to apply the policy and Attach it.
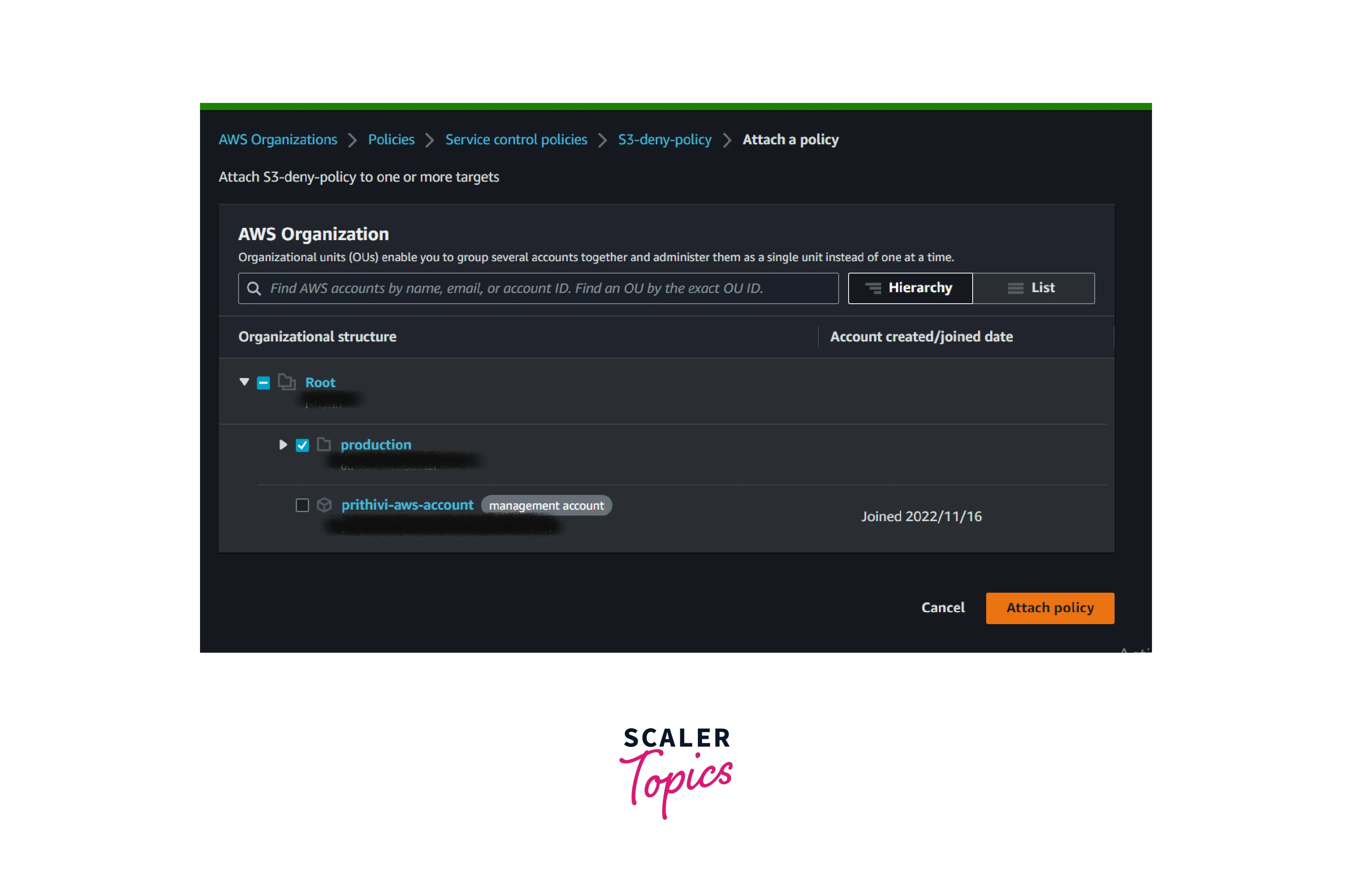
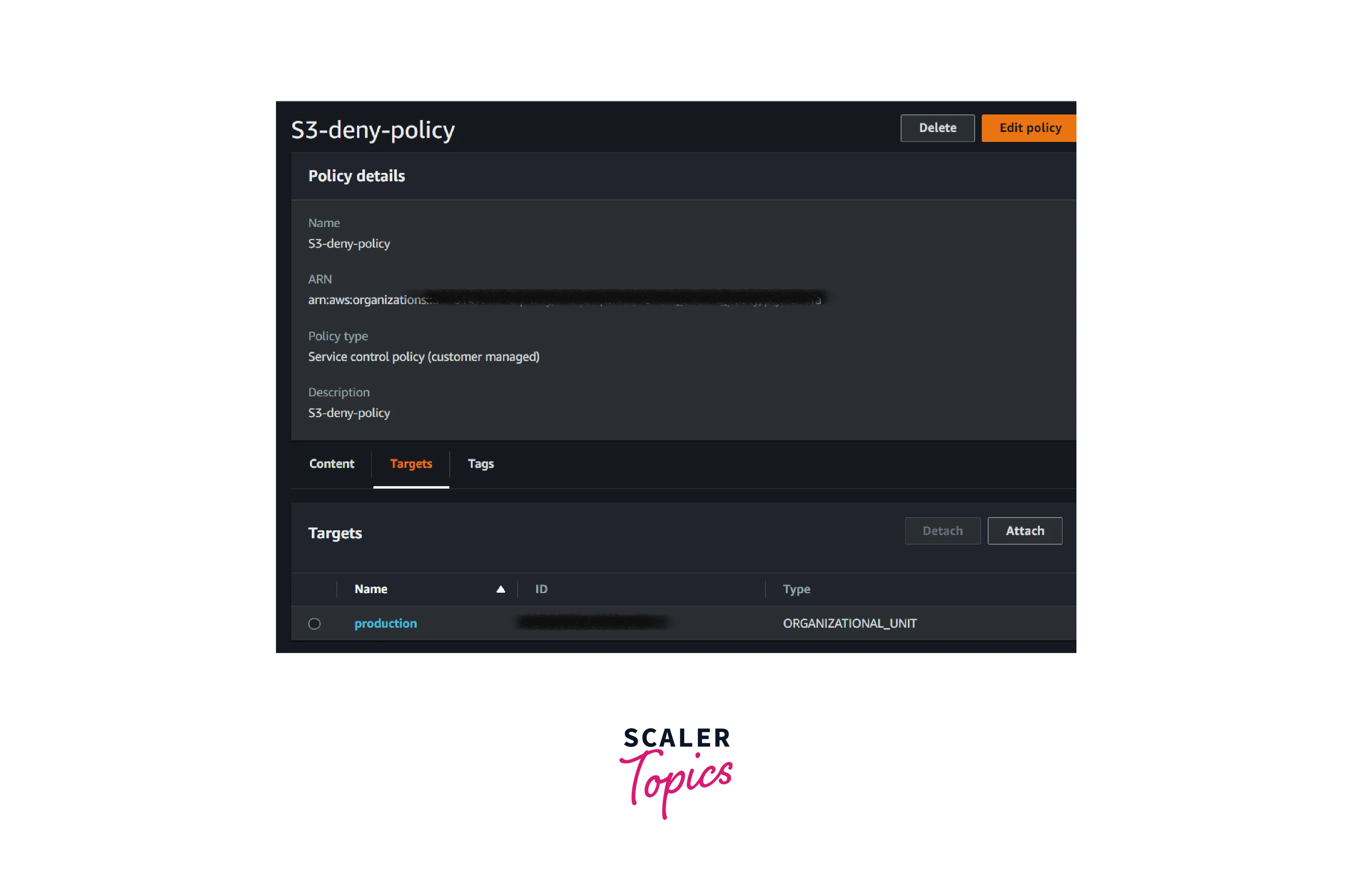
- Now, we can see that the newly created policy has been attached to the production organizational unit.
How To Test An AWS SCP?
Now log into the AWS member account using the IAM user or role
Here AWS member account refers to the AWS account mapped under the production organization unit where S3-deny-policy SCP is attached.
Once logged into the AWS account, try to read the S3 buckets from the console, you will get no buckets or it will through some error like below
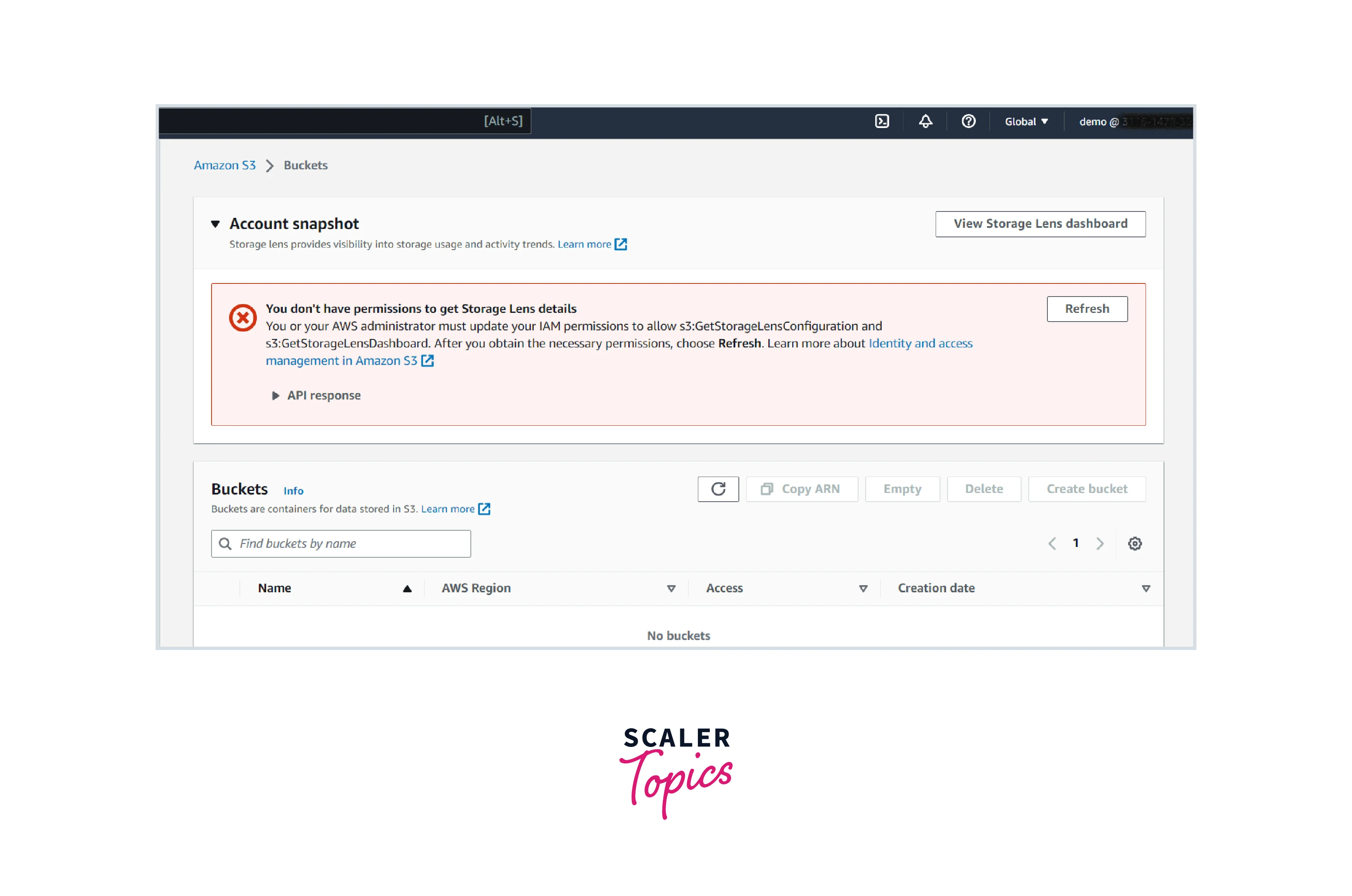
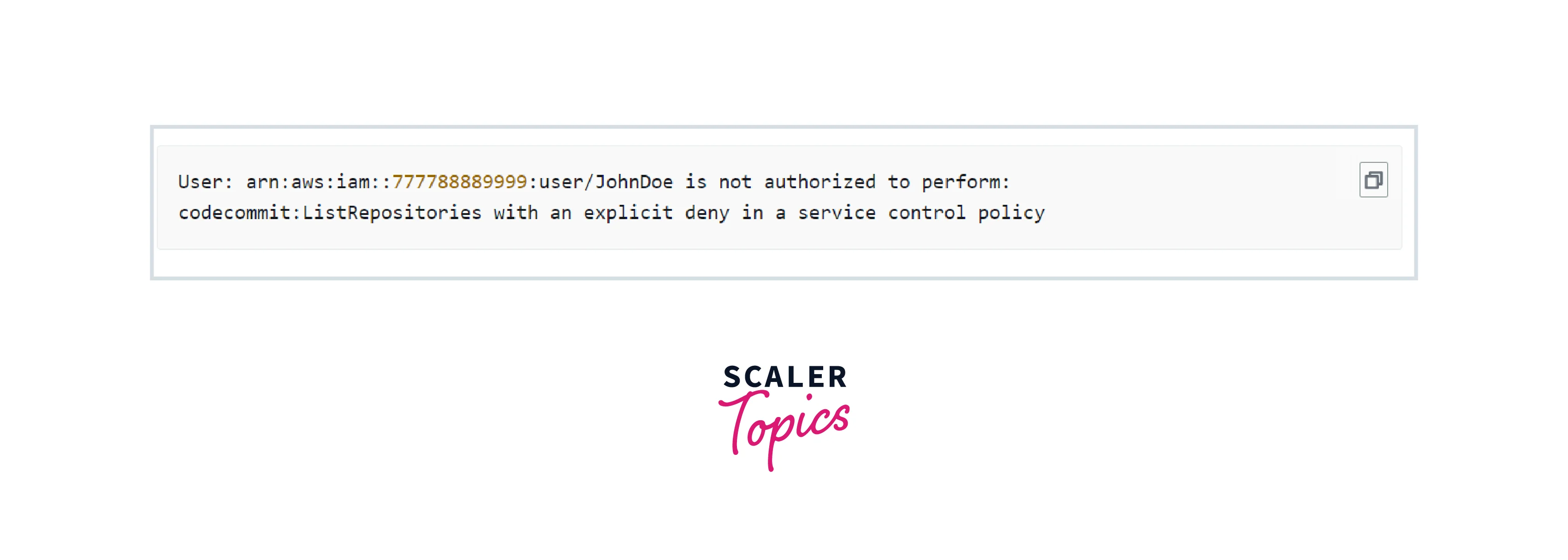
The reason for the error is that in the above step, we added the S3-deny-policy which deny all the IAM entity within the AWS account to access the S3 bucket.
This is how a customer can control the resources of the member account using AWS SCP under AWS Organization.
AWS SCP Best Practices
Some of the AWS suggested Service control policy best practices are mentioned below
Allow Only Approved Services
- If the IAM user or role is concerned with a particular service, then customers should provide access to that particular service only. By doing so, we achieve granular permission for the IAM identities
Deny Root User Access
- The root user will be able to make changes to the member account by itself even if the SCP is enforced in it. so it is advisable to restrict the root user access by enforcing the SCP Policy in the Organizational Unit.
Region Enforcement
- If the customer is using only one region or two regions, then they can implement SCP to disable the other region for the member accounts.
- If one member account is using one region and another member account is using another region, we can create SCP individually and attach it to the member account directly.
Deny The Ability To Leave Organization
- If the member account has access to leave the organization, it will have its own set of rules to operate and risk the entire organization against the security
- To avoid this from happening, customers are suggested to implement the SCP to the member account or organizational unit level.
- By attaching the SCP, the member account won’t be able to leave the organization without management account permission. Customers can have entire control over their organization.
Deny The Ability To Disable Tools such as GuardDuty, Cloudtrail, etc
- We should implement the SCP to restrict the member accounts to meddle with the monitoring and auditing tools such as Guard Duty and Cloudtrails. Example Policy
For more details about AWS SCP best practices. Kindly refer to the link below.
Reference: AWS SCP Examples
Service Control Policies (SCP) vs IAM Policies
| No. | Service Control Policy | IAM Policy |
|---|---|---|
| 1 | A service control policy is associated with the member AWS account within the organization | IAM policy associated with IAM identities such as IAM user, role, or groups |
| 2 | It allows deny or allow the individual AWS account within the organization or Group of member accounts under an organizational unit | It allows deny or allows the AWS service via API action |
| 3 | AWS SCP takes precedence over IAM policy if there is deny in the principle | IAM policy and SCP policy will be evaluated before executing the API Call. |
| 4 | AWS SCP provides fine-grained permission to a single AWS account or multiple AWS accounts under an Organizational unit or entire organization members' account | IAM policy provides fine-grained permission to the IAM identities within the AWS account |
| 5 | The maximum size of the AWS SCP policy is 5120 bytes | The maximum size of the AWS IAM policy is 6144 characters |
Conclusion
- AWS Service Control Policy works with AWS Organization Service when multiple AWS accounts are associated.
- AWS SCPs enables customers to apply for fine-grained permission across all AWS accounts in a single console.
- The AWS SCPs can be attached to the organization at the root level, OU level, and member account level.
- There is no cost for using the AWS service control policies in an AWS organization. By enabling SCP, another layer of security was added for accessing the member accounts.
- AWS SCP helps customers achieve the least granular access to their AWS accounts.
