AWS Session Manager
Overview
Session Manager is an AWS Systems Manager's completely managed feature that allows users to control the AWS EC2 instance using an interactive one-click web-based shell or the AWS Command Line Interface. It enables secure instance administration without the requirement to open incoming ports, manage the bastion host, or handle keys. It simplifies compliance with business rules that need regulated accessibility to instances, stringent security procedures, and a fully auditable log containing instances' access details, all the while giving end-users a simple one-click cross-platform accessibility to their EC2 instance.
What is AWS Session Manager?
AWS Session Manager is a Systems Manager feature that is fully managed. Users may handle the AWS EC2 instance, edge device, and on-premise server and VMs using Session Manager.
Session Manager enables safe and fully transparent node administration even without the requirement for inbound port opening, bastion host maintenance, or SSH key management. Session Manager further enables users to conform with corporation regulations requiring regulated availability to manage nodes, extensive security standards, and a fully auditable log containing node access details.
Architecture
The figure below depicts how various Systems Manager features operate on your resources. The diagram does not include all of the capabilities. Following the diagram, each of the mentioned interactions is discussed.
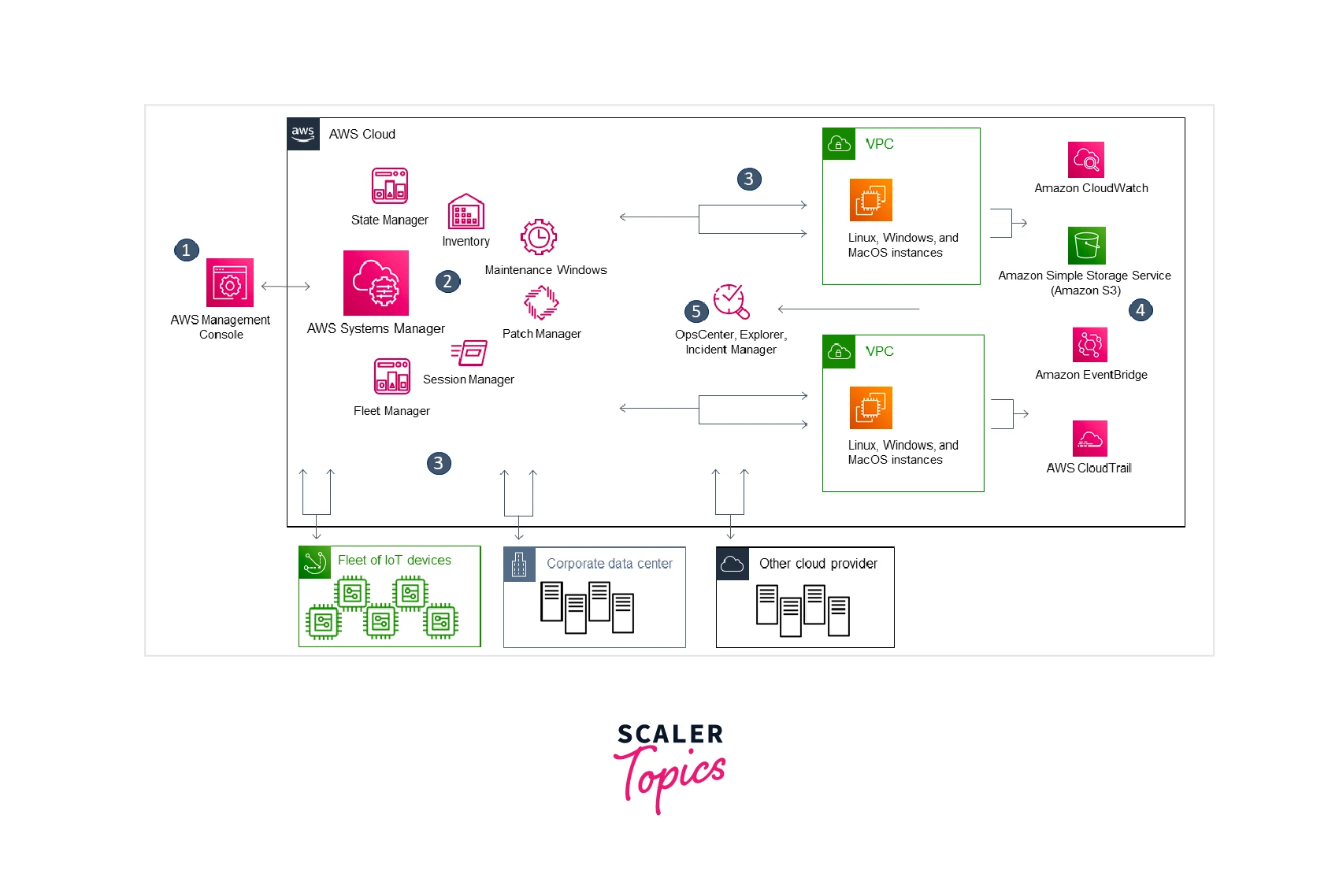
-
Access Systems Manager – Use one of the available options for accessing Systems Manager.
-
Choose a Systems Manager Capability – Determine which capability can help you perform the action you want to perform on your resources. The diagram shows only a few of the capabilities that IT administrators and DevOps personnel use to manage their applications and resources.
-
Verification and Processing – Systems Manager verifies that your AWS Identity and Access Management (IAM) user, group, or role has permission to perform the action you specified. If the target of your action is a managed node, the Systems Manager Agent (SSM Agent) running on the node acts.
-
Reporting - The status of the Systems Manager, SSM Agent, and other AWS services that executed an action on the Systems Manager's behalf is reported. If enabled, Systems Manager can provide status information to other AWS services.
-
Systems Manager operations management capabilities - When enabled, Operations Manager has capabilities such as Explorer, OpsCenter, and Incident Manager to aggregate operations data or produce artifacts in reaction to events or issues with your resources.
Prerequisites
-
Deployment of the Systems Manager Agent: A Systems Manager Agent (SSM) agent must be deployed in each EC2 instance or on-premise system having Administrator privileges.
-
Internet Connection: The SSM agent requires communication with the AWS API, which takes place over regular HTTPS ports. Because the agent always initiates contact, any inbound rules are unnecessary.
-
Systems Manager IAM configuration: Systems Manager Agent (SSM) necessitates the assignment of an instance profile role to each EC2 instance. In addition, for a hybrid cloud environment, an IAM services role is required.
How Does It Work?
-
IAM roles and policies are used to authenticate admin users.
-
If authentication is successful, the AWS Management Console or AWS CLI can access the Session Manager (requires Session Manager CLI plugin).
-
Each EC2 instance's agent connects to the Systems Manager endpoints and executes the command on the instances.
-
Any action taken by the Session Manager is recorded on CloudTrail. Session outputs can optionally be sent to CloudWatch logs and/or S3 buckets (Exception port-forwarding action logs will not be pushed to CloudWatch logs and S3 buckets).
Main Features of AWS Session Manager
-
Compatibility with Linux, macOS, and Windows Server-controlled node: Users may create a secure connection to the on-premises server, VMs, edge devices, and AWS EC2 instances using Session Manager.
-
Session Manager functions are accessible via the console, CLI, and SDK: The following are some ways in which you can interact with Session Manager:
- Either admins or end-users have access to all Session Manager features through the AWS Systems Manager dashboard. The Systems Manager dashboard may be used to carry out any task connected to the session.
- Users may connect to EC2 instances to which they have access, using the AWS EC2 dashboard.
- Users can access Session Manager features using the AWS CLI. By using AWS CLI, users can establish a session, see a catalog of the session, and stop a session completely.
- Session Manager SDK contains libraries and example codes that app developers may utilize to create front-end apps that use Session Manager to access managed nodes, like bespoke shells or self-service portals for internal purposes.
- To use the Session Manager APIs, clients, and programmers may include Session Manager in any client-side tools or automated workflow. even create their unique solution.
-
IAM access management: Users may control the employees within the company who can start a session to managed node as well as which node users can access, by using IAM policies. Users can also grant the controlled nodes momentary access. For instance, one could wish to grant production server access to the on-call engineers during the production cycle.
-
Supports logging and audit capabilities: By connection with such a variety of different AWS services, Session Manager gives users choices for auditing and tracking session history in the AWS account.
-
Customized shell profile: Users have choices to set settings for sessions while using Session Manager. With the help of these editable profiles, users may specify choices for the shell, environment variable, active folders, and the execution of several commands upon session startup.
-
Support for customer-key data encryption: Users may set up Session Manager to stream to a CloudWatch Log group or encrypt all sessions data log you transmit to the AWS S3 bucket. Additionally, users may set up Session Manager to further encrypt the information sent during the session between client computers and the managed node.
-
Compatibility of a managed node without the public IP address using AWS PrivateLink: Furthermore, to better safeguard the session, users may configure VPC Endpoint with Systems Manager utilizing AWS PrivateLink. The network communication among the managed node, Systems Manager, and AWS EC2 is restricted to an AWS network using AWS PrivateLink.
-
Tunneling : You may tunnel communication, including HTTPS or customized protocols, between local ports on a client computer and a remote port on managed nodes during a session by using Session-type AWS Systems Manager documents.
-
Interactive instructions: To control whatever clients may do on managed nodes, develop any Session-type SSM documents which use a session to execute a single instruction dynamically.
Who Should Use AWS Session Manager?
-
Anyone who uses AWS and desires to improve its security and auditing posture, reduce operating costs by consolidating access controls on the managed node, and limit incoming node access.
-
Restrict incoming ports on a managed node or permit connection to managed node without public IP addresses if you wish to observe and access logs of activities on the managed node.
-
Users who require a single answer for managed Linux, macOS, and Windows Servers nodes and administrators who wish to give and deny access from a single site.
-
Clients that wish to establish a one-click connection to the managed nodes using the AWS CLI or a browser without needing to supply a Key.
AWS Session Manager Use Cases
Automation
-
Develop infrastructure self-services automated runbook.
-
Create AMI from AWS Marketplace or customized AMIs with the help of Automated, an AWS Systems Manager feature, by utilizing an open Systems Manager document (SSM document) or by designing custom processes.
-
Create a custom Automated runbook or use the AWS-UpdateLinuxAmi and AWS-UpdateWindowsAmi Automation runbook to create and maintain AMI.
Inventory
- Utilize AWS Config and Inventory, a feature of AWS Systems Manager, to track the changes made to the app's setup over time.
Restoration Windows
- Establish a timetable for highly destabilizing operations like software installs, driver updates, and OS patching on the node.
Stores parameter
-
To handle global setup centrally, utilize the AWS Systems Manager's Parameters Store feature.
-
AWS KMS is utilized by AWS Systems Manager Parameters Store.
-
Use the Parameters Store arguments to access AWS Secret Manager's secrets.
Patch Manager
-
To push deploy fixes at volume and improve fleet-compliant monitoring throughout the node, employ Patch Manager, a feature of AWS Systems Manager.
-
Connect Patch Manager to AWS Security Hub to track the patch state of the fleet from a security perspective and get notifications whenever a node in the fleet is not in compliance.
Execute the command
-
Use the EC2 Command Line to scalably manage instances without SSH access.
-
Use AWS CloudTrail to audit each API call performed by or on behalf of Run Commands, an AWS Systems Manager feature.
-
Passwords, configuration, or other sensitive information that is structured in plaintext shouldn't be included while sending a command with Run Commands. The account's Systems Manager APIs activity is recorded in an AWS S3 bucket designated for the AWS CloudTrail log. That implies that the unencrypted contents of those secrets are visible to every client having accessibility to the S3 buckets. To protect sensitive information used in the Systems Manager processes, experts advise establishing and utilizing the SecureString parameter.
-
To execute stage command operations, utilize Run Command's target and rate control capabilities.
-
Use AWS IAM rules to grant Run Command (and any other Systems Manager features) fine-grained access privileges.
Session Manager
-
Use AWS CloudTrail to examine session activities in the AWS accounts.
-
Use AWS CloudWatch Logs or S3 to record session information in the AWS accounts.
-
Manage user access to instances throughout a session.
-
Limit who can execute instructions during a session.
-
Activate or deactivate the administrative permission for the SSM-user accounts.
State Manager
-
Use the pre-configured AWS-UpdateSSMAgent file at least once a month to update SSM Agents.
-
Utilizing AWS-InstallPowerShellModule, we can publish the PowerShell or DSC modules to AWS S3.
-
Configure the applications group for the node using tags. Select the target node rather than supplying specific node IDs through the Target argument.
-
Use Systems Manager to quickly fix issues identified by AWS Inspector.
-
Publish the SSM documents with the rest of the business and utilize a centralized configuration repository.
Management node
- For Systems Manager to function, specific time references are necessary. The node's time and day may not match the signature date of the API calls if they are not properly specified. This could result in mistakes or insufficient functioning. Nodes with incorrect time settings, for instance, do not feature in the listings of a managed node.
How to Set up AWS Session Manager?
Follow the steps in this section to use AWS Systems Manager's Session Manager and link to the managed nodes in the account.
Step 1: Fulfill all criteria for Session Manager
Check that your environment matches the following prerequisites before using Session Manager.
1. Supported operating system
Session Manager may connect to Amazon Elastic Compute Cloud (Amazon EC2) instances as well as servers or virtual machines (VMs) in your hybrid environment using the advanced instances tier.
Session Manager is compatible with the following operating systems:
- Linux: Session Manager supports all Linux versions supported by AWS Systems Manager.
- macOS: Session Manager supports all macOS versions supported by AWS Systems Manager.
- Windows: Session Manager is compatible with Windows Server 2012 and Windows Server 2022.
2. SSM Agent
-
AWS Systems Manager SSM Agent version 2.3.68.0 or later must be installed on the managed nodes to which you want to connect via Session Manager.
-
To encrypt session data using a key created in AWS Key Management Service (AWS KMS), SSM Agent version 2.3.539.0 or later must be installed on the managed node.
-
To use shell profiles in a session, the managed node must have SSM Agent version 3.0.161.0 or later installed.
-
To begin Session Manager port forwarding or SSH session, the managed node must have SSM Agent version 3.0.222.0 or later installed.
-
To stream session data via Amazon CloudWatch Logs, the managed node must have SSM Agent version 3.0.284.0 or later installed.
3. Connectivity to endpoints
The managed nodes to which you connect must also enable outbound HTTPS (port 443) communication to the following endpoints:
- ec2messages.region.amazonaws.com
- ssm.region.amazonaws.com
- ssmmessages.region.amazonaws.com
4. AWS CLI
If you start your sessions using the AWS Command Line Interface (AWS CLI) rather than the AWS Systems Manager console or the Amazon EC2 panel, you must have version 1.16.12 or later of the CLI installed on your local workstation.
To verify the version, use: aws --version.
5. Turn on the advanced-instances tier (hybrid environments)
To use Session Manager to connect to on-premises computers, you must enable the advanced instances tier in the AWS account and the AWS region where you construct hybrid activations to register on-premise machines as managed instances. The advanced instances tier comes at a cost.
6. Verify IAM service role permissions (hybrid environments)
To connect with Systems Manager API activities, hybrid instances employ the AWS IAM service role defined in the hybrid activation. This service role must have the permissions necessary to connect to your on-premise computers using Session Manager. The needed rights for Session Manager are already granted if your service role has the AWS managed policy AmazonSSMManagedInstanceCore.
If you discover that the service role lacks the necessary rights, you must deregister the managed instance and re-register it with a new hybrid activation that employs an IAM service role with the necessary permissions.
Step 2: Verify or create an IAM role with access to the Session Manager
AWS Systems Manager does not have access to do operations on your instances by default. You must use AWS IAM to allow access. An instance profile provides permissions for Amazon EC2 instances. You can add an IAM instance profile to a newly created Amazon EC2 instance or a previously launched instance.
Permissions are supplied for on-premise servers or virtual machines by the IAM service role associated with the hybrid activation used to register your on-premise machine with Systems Manager.
To allow Session Manager operations to be done on your instances in certain scenarios, execute one of the following:
-
Incorporate Session Manager permissions into a bespoke IAM role: To add permissions for Session Manager to an existing IAM role that doesn't rely on the AWS-provided default policy AmazonSSMManagedInstanceCore, follow the steps in Adding Session Manager permissions to an existing IAM role.
-
Create a custom IAM role with Session Manager permissions only: To create an IAM role that contains permissions only for Session Manager actions, follow the steps in Create a custom IAM role for Session Manager.
-
Create and use a new IAM role with permissions for all Systems Manager actions: To create an IAM role for Systems Manager managed instances that use a default policy supplied by AWS to grant all Systems Manager permissions, follow the steps in Create an IAM instance profile for Systems Manager.
Step 3: Control user session access to managed nodes
AWS Systems Manager Session Manager enables you to give and revoke user access to managed nodes from a single location. You may govern which managed nodes individual users or groups can connect to as well as which Session Manager API activities they can execute on the managed nodes, using IAM policies.
About Session ID ARN formats
Session ID variables are used in IAM rules for Session Manager access. Session IDs are used to manage access in session Amazon Resource Names (ARNs).
The following is the format for session ARNs:
arn:aws:ssm:region-id:account-id:session/session-id
For example:
arn:aws:ssm:us-east-2:123456789012:session/JohnDoe-1a2b3c4d5eEXAMPLE
To provide permissions for Session Manager activities, you may utilize AWS's default IAM rules, one for end users and one for administrators. You may also design bespoke IAM policies for specific requirements.
Step 4: Setup session preference
An AWS IAM administrator user can do the following tasks:
-
Enable "Run As" for Linux controlled nodes. This allows sessions to be started with the credentials of a specified operating system user rather than the credentials of a system-generated ssm-user account that Session Manager creates on a managed node.
-
Configure Session Manager to utilize AWS KMS key encryption to safeguard data exchanged between client computers and managed nodes.
-
Set up Session Manager to produce and deliver session history logs to an S3 bucket or a CloudWatch Logs log group. The log data that has been saved may then be utilized to audit or report on the session connections established on your managed nodes and the commands that have been performed on them throughout the sessions.
-
Set the session timeout. You may use this parameter to indicate when a session should be terminated after a period of inactivity.
-
Set up Session Manager to utilize a customizable shell profile. These customizable profiles enable you to establish session preferences such as shell preferences, environment variables, working directories, and running multiple commands when a session is launched.
Step 5: (Optional) Restrict access to commands in a session
Step 6: (Optional) Create a VPC endpoint for Session Manager using AWS PrivateLink
Step 7: (Optional) Enable or disable administrator permission for the SSM-user accounts
Step 8: (Optional) Use Session Manager to allow and control SSH connections permission
Benefits and Limitations of AWS Session Manager
Benefits
IAM rules for central access management to managed node
Accessibility to the managed node may be granted and revoked by admins in a single location. Users may regulate whether specific people or groups within the company have accessibility to managed nodes and Session Manager with a simple IAM policy.
There's no need to handle bastion host or SSH key, nor open inbound ports
The risk of entities issuing malicious or unauthorized instructions on the managed node grows significantly if the incoming SSH port and remote PowerShell port are left open. Session Manager frees users from handling SSH key and certificate, bastion host, and jump box by allowing users to stop those inbound ports, which enhances the security posture.
Accessibility to the managed node with a single click from the terminal and CLI
Users may launch a session with a single click using the AWS EC2 console or the AWS Systems Manager console. Users may launch a session that executes a single instruction or a series of instructions using the AWS CLI. The connection time is significantly decreased since IAM policy, rather than SSH key or other procedures, is used to grant access to the managed node.
Access to managed node and AWS EC2 instances in hybrid and cloud settings
Inside a hybrid cloud environment, users may link to a non-EC2 node such as an on-premises server, authorized edge device, and VMs offered by the other cloud services in addition to AWS EC2 instances.
Advanced Instance Tier
Users should first enable the advanced-instance tier to use Session Manager to link to non-EC2 nodes. The advanced-instance tier has a fee associated with it. Nevertheless, employing Session Manager to access EC2 instances is free of cost.
Port Forwarding
Every port on the managed nodes can be redirected to the client's local ports. Afterward, we can access any server application which is executing within the nodes by connecting to the local ports.
Compatibility for Windows, Linux, and macOS across all platforms
With just one utility, Session Manager offers compatibility with Windows, Linux, and macOS. For instance, users are not required to establish an RDP connection to access managed Windows server nodes or SSH connections to access managed Linux and macOS nodes.
Audit and logging for sessions
Users may be required to produce a record of connecting to the managed node and the command that has been executed against them to satisfy the operations or security needs of the business. Additionally, you may be notified whenever a client in the company initiates or terminates a session.
Connectivity with the following AWS resources enables log and audit functionality:
- AWS CloudTrail : AWS CloudTrail logs info regarding requests to the Session Manager API in the AWS accounts and stores log data in the AWS S3 bucket you choose. All of the account's CloudTrail logs are stored in a single bucket.
- AWS S3 : To test and debug, users may decide to store session logs in an AWS S3 bucket of their choosing. With the AWS KMS key, logs may be delivered to the AWS S3 bucket either with or without encryption.
- Logs from AWS CloudWatch: Users may track, save, and retrieve system logs across multiple AWS resources using CloudWatch Log. For the sake of troubleshooting and monitoring, users can transmit session logs to a CloudWatch Logs log group. With a KMS key, logs may be delivered to the log groups either with or without encryption.
- AWS EventBridge and SNS : With EventBridge, users can make rules to monitor changes to the AWS services that define and get alerts when they occur. Whenever a client begins or finishes a session, they can write rules to identify it. Users can then get notified of this using AWS SNS (for instance, by text message or email).
Limitations
-
AWS Session Manager does not support file transfers.
-
Windows does not enable RDP and does not have the "Run As" functionality. Port forwarding could be used in its place.
-
Session Manager needs the sophisticated on-premise instances tier but is interoperable with the on-premises systems (payment required).
-
The majority of the ssh-compatible utilities are not enabled by Session Manager because it is not a native SSH service.
AWS Session Manager vs AWS SSH
| AWS Session Manager | AWS SSH | |
|---|---|---|
| 1. | Users can control AWS EC2 instances, on-premises instances, and virtual machines using Session Manager. | The secure connection between the system and an EC2 instance is made possible through the network protocol known as SSH, or Secure Shell. Through the command line, you'll be able to manage the EC2 instances. |
| 2. | Install the SSM Agent. Session Manager will be able to handle all active EC2 instances, thanks to the SSM agents. The SSM agents must be installed on all on-premise servers. | A running instance of EC2 must be located in a public subnet. On AWS, it is part of the free tier. |
| 3. | Activate the EC2AccessForSSM IAM role offered by AWS. This permits access to the EC2 instances via the Session Manager. | The instances demand the following configuration settings: SSH access via security groups - It will employ the TCP protocol on port 22. Possession of a key pair - Create a key pair and transfer that to the local computer. |
Conclusion
-
AWS Systems Manager is a secure end-to-end solution for hybrid cloud environments that allows safe and secure operations at scale. It serves as the operations center for your AWS apps and resources.
-
A steady stream of session data logs is sent to Amazon CloudWatch Logs. When streaming session data, details such as the commands a user has executed in a session, the ID of the user who performed the commands, and timestamps are provided.
-
Users may begin a session with a single click using the AWS EC2 interface or the AWS Systems Manager console. Users may initiate a session that runs a single instruction or a sequence of instructions using AWS CLI.
-
If you want to monitor and track the activities on the managed node, restrict incoming ports or allow connections to the managed node without a public IP address.
-
By utilizing IAM policies, users may govern which nodes the employees can access as well as on which nodes they can initiate sessions. Users can also provide temporary access to restricted nodes.
