AWS Shared Responsibility Model
Overview
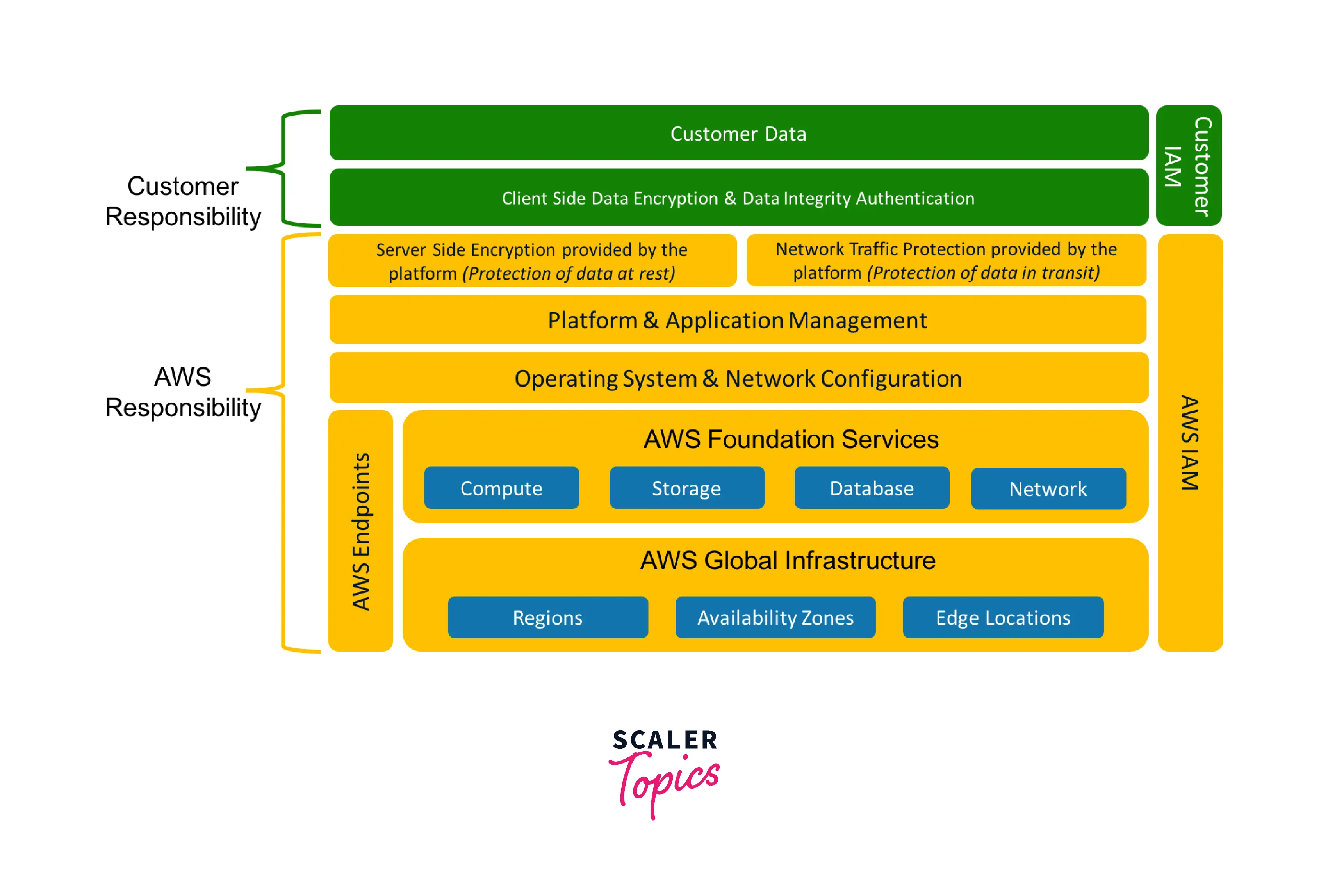
Security and compliance are shared obligations between AWS and the customer. The operational burden on the customer may be minimized due to this shared approach of the AWS Shared Responsibility Model, with AWS managing the host operating system, the virtualization layer, and even the physical security of the premises where the service is located. The client is responsible for administering the guest operating system, including updates and security patches, as well as other relevant application software, and establishing the security group firewall provided by AWS. AWS is in charge of the infrastructure that supports every service the AWS Cloud offers. This infrastructure consists of the data centers, networking, hardware, and software required to provide AWS Cloud services.
What is Shared Responsibility Model and How Does It Work?
The shared responsibility model proposed by AWS is a scheme for allocating duties between AWS and a Customer. This means IN the cloud; security is not just the responsibility of the cloud service provider (CSP) for a business. Instead, the security OF the cloud-based deployment is a shared responsibility between the cloud provider and the cloud client, and the cloud provider's shared responsibility model explains the duties of each side.
The infrastructure that powers all of the services provided by the AWS Cloud is under the control of AWS. The facilities, networking, hardware, and software used to run AWS Cloud services make up this infrastructure.
The AWS Cloud services a client chooses will define the extent of the customer's obligation. The quantity of setup work the client must complete as part of their security obligations is determined by this.
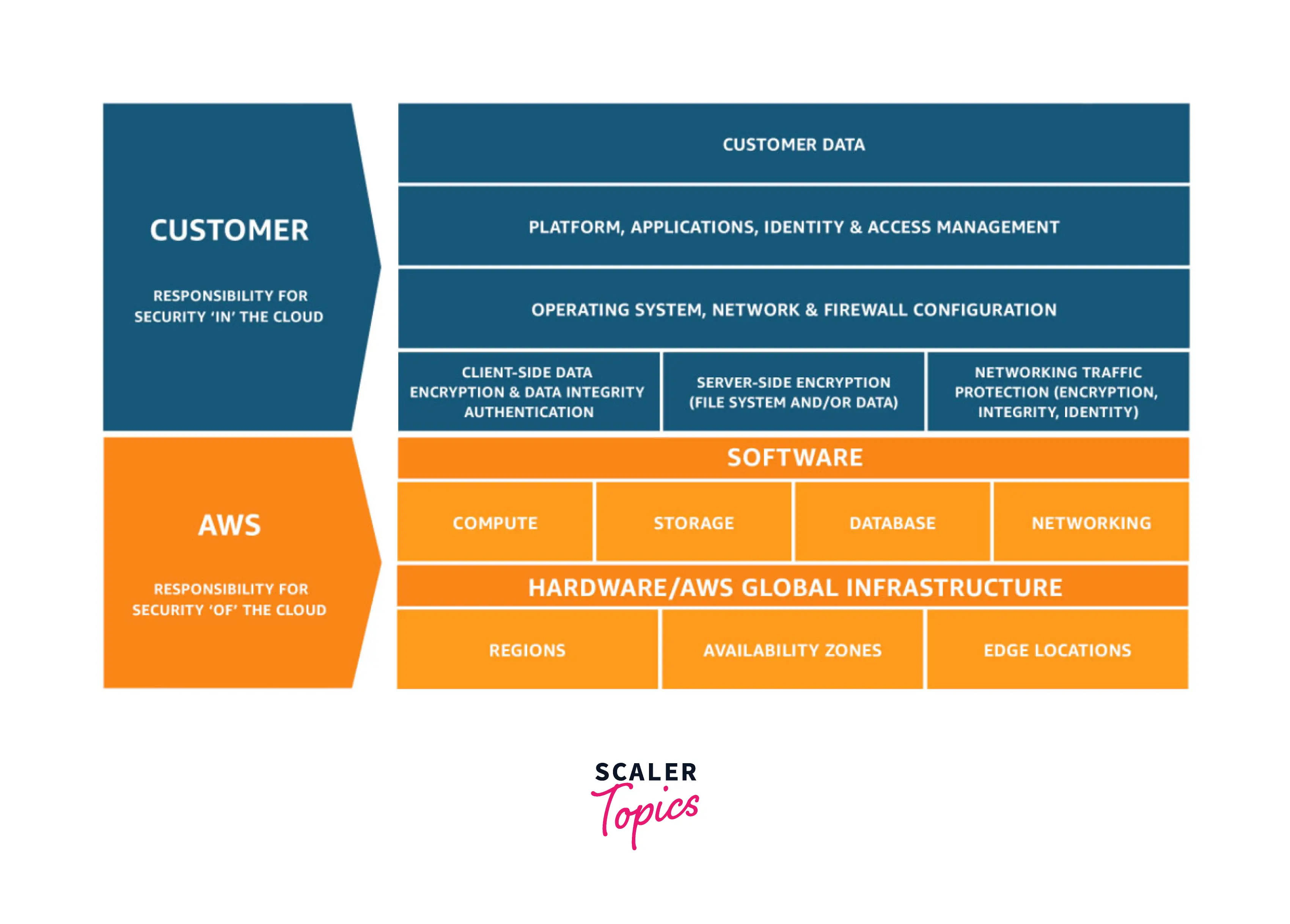
Security IN the cloud : This usually consists of the data that is uploaded/added by the customer. This data can be things like names for the resources that are being created, the files that belong to the customer which they upload .The customer is responsible for managing the data that he/she uploads. Next, coming to the types of configurations(Network and Firewall)that are chosen to maintain security is again something that the customer is held responsible for. Let's say if a user creates an EC2 instance, they themselves are responsible for the type of configurations that they are doing and are also responsible for the management of the Operating System that is being used on the created EC2 instance. Here, the management tasks can be looking after updates and security patches and configuration tasks can be things like creating rules on the security firewall to avoid malicious user access.
Security OF the cloud : In this case, AWS takes the sole responsibility of keeping the customer created infrastructure secure. Here, "Infrastructure" are things like the compute,storage,software and networking based resources that runs on AWS.
Levels of Abstraction in Cloud
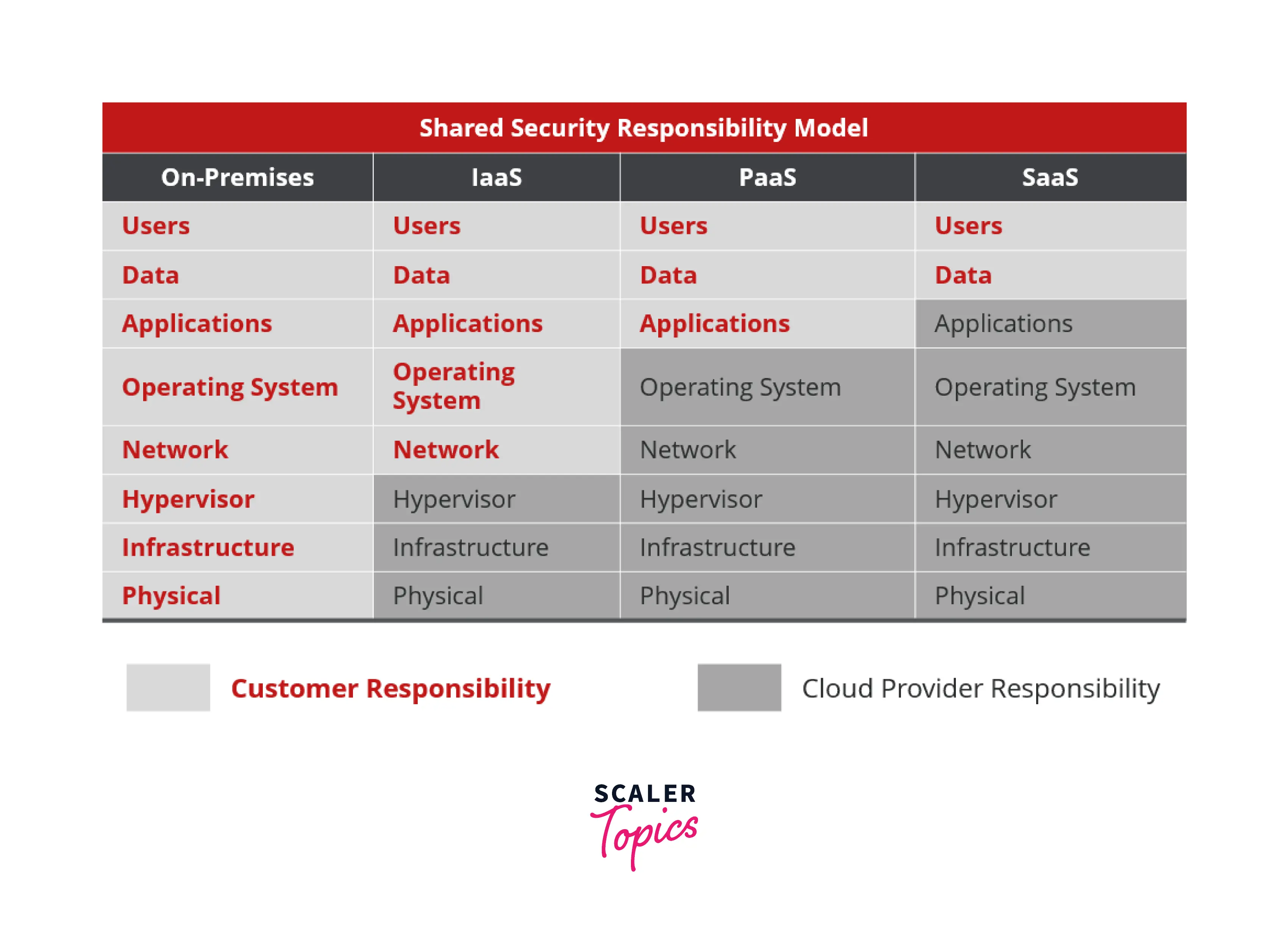
There might not always be a common set of security responsibilities. Every circumstance can need a different level of security and responsibility. Degrees of abstraction are, thus, the area that pertains to such obligations. The terms "levels of abstraction" refer to PaaS (Platform as a Service), IaaS (Infrastructure as a Service), and SaaS (Software as a Service).
- Infrastructure as a Service (IaaS)-The most basic level of abstraction is Infrastructure as a service. IaaS allows cloud suppliers to make their data centers' servers, storage, networks, hardware, and virtualization available to consumers. Although the user has much power, they also bear more security responsibility . For example, if a user creates an EC2 instance, it is their responsibility to set up a security group to avoid access on certain ports. Therefore, here the user has the highest amount of responsibility to protect his EC2 instance.
- Platform as a Service (PaaS) - The subsequent abstraction level enables users to create and consume apps. The cloud vendor also offers a platform for developing, deploying, and managing applications under PaaS, apart from the Infrastructure.
- Software as a Service (SaaS)-The cloud vendor hosts applications under SaaS to make them accessible to end-users or clients. Organizations no longer need to host programs in their own private data centers, thanks to SaaS. RDS ( Relational Database Service) that provides a fully working relational DB service like SQL is an example of SaaS in AWS. Now coming to an example out of AWS, Adobe Photoshop is a SaaS that people use to edit their pictures.
What is AWS Shared Responsibility Model?
Responsibility of AWS
The Infrastructure that powers all of AWS's services must be kept secure. In other words, the components from the host operating system and virtualization layer down to the physical layer where the service is implemented are controlled, used, and managed by AWS.
Responsibility of a Customer
The client is responsible depending on the AWS service utilized and the settings required to protect it. In other words, guests' operating systems, security updates, and application software must be managed by customers. Additionally, users must set up the security measures supplied by AWS, such as security groups, network access control, and IAM (Identity and Access Management).
Responsibility Differences
In addition to the infrastructure requirements of AWS, the user must supply their own control implementation in order to use AWS services:
- IT controls: AWS helps customers manage the burden of security measures including encryption, firewall upkeep, and deployments of IT controls in order to ensure proper adherence to AWS security regulations. AWS and its clients frequently share IT operations.
- Configuration management: While the client is responsible for configuring their own guest operating systems, databases, and software applications, AWS handles the configuration of its infrastructure equipment.
- AWS trains its personnel, but clients must also train their staff.
Types of AWS Shared Responsibility Model
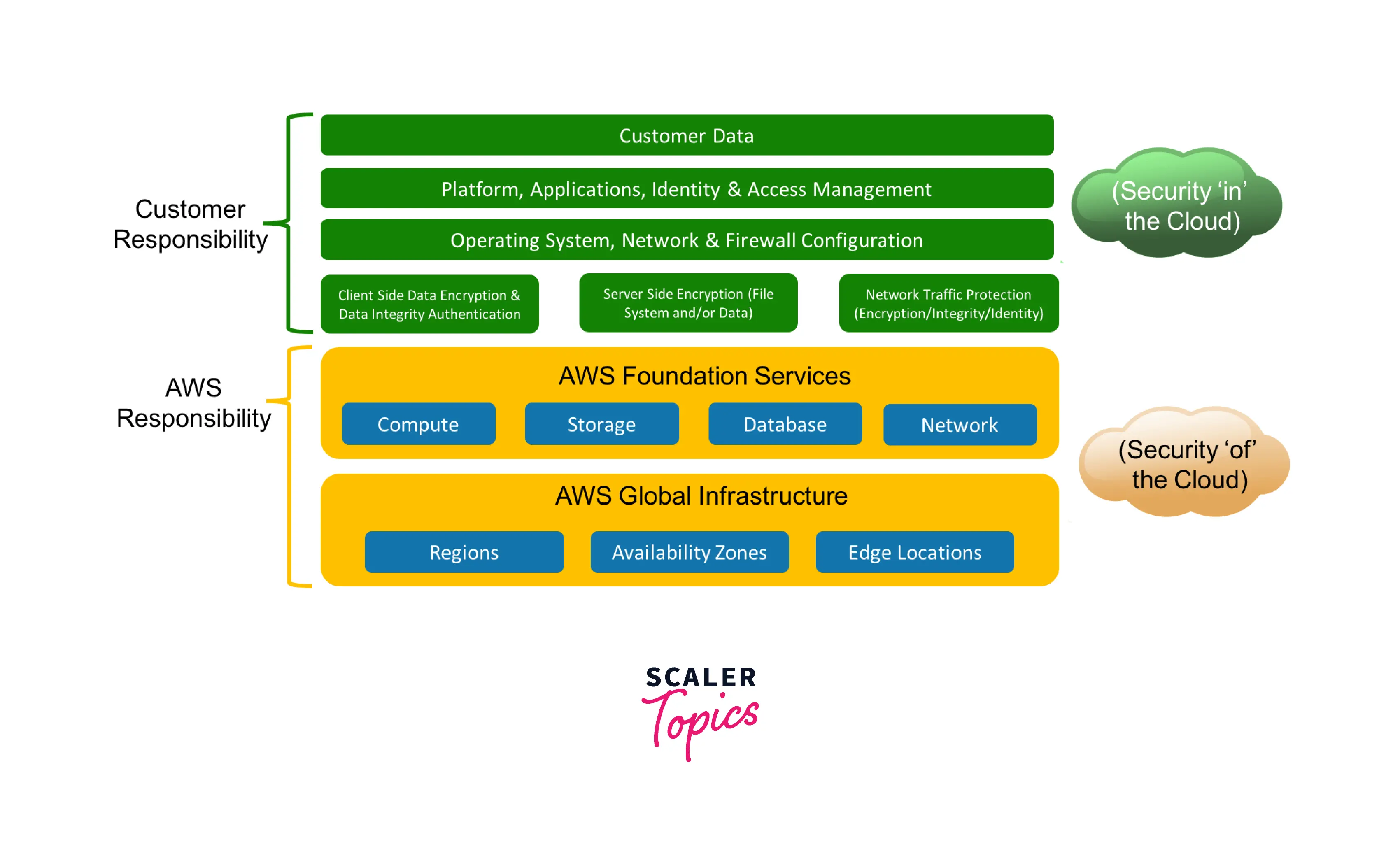
AWS Shared Responsibility for Infrastructure Services
- AWS is in charge of the security of the cloud. This includes the underpinnings of their compute, storage, database, and network services and its global infrastructure components, including regions, availability zones, and edge locations. Your client data is stored in data centers owned and controlled by AWS.
- This includes physical access to all hardware and networking parts and other data center amenities like generators, UPS systems, power distribution units (PDUs), computer room air conditioning (CRAC) units, and fire suppression systems. This physical access entry and control is the foundation for several security compliance procedures previously discussed. In essence, AWS is in charge of the elements that make up the cloud, and any data "inside" the cloud is your responsibility.
- You are in charge of what gets into the cloud since AWS is responsible for securing and maintaining the fundamental cloud infrastructure. This includes operating system security, network security, firewall setup, client and server-side encryption, network traffic protection, application security, and identity and access management.
- How much of this additional protection you choose to use is entirely up to you. Your choice can be affected by the nature of your business or by regulations currently in place. It's important to remember that even while AWS provides a number of reliable security measures, AWS is not in charge of deciding how and when to use them.
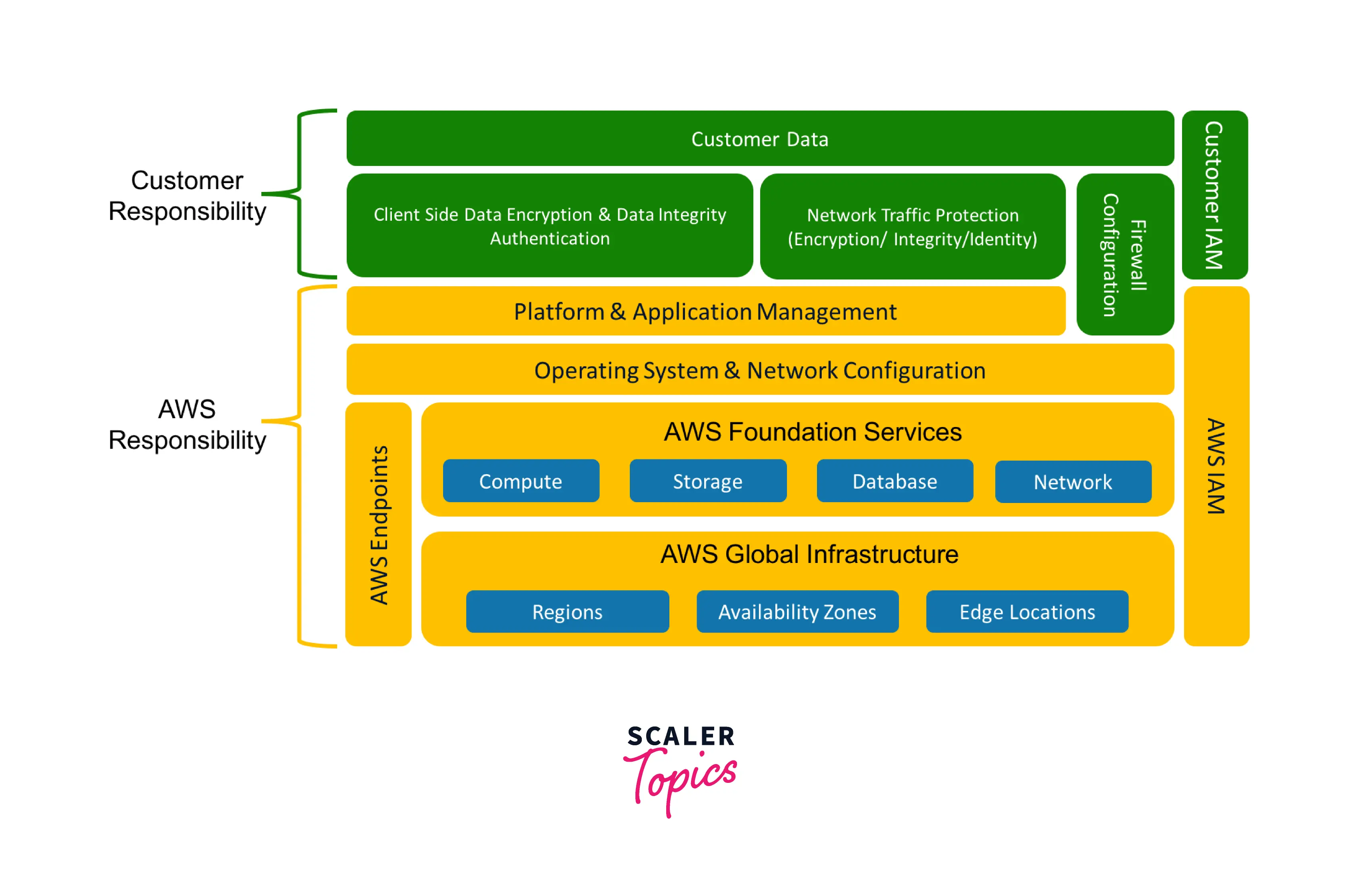
AWS Shared Responsibility for Container Services
- The consumer, in this instance, doesn't control their platform or operating system. A cloud customer's level of security responsibility is lower under this model than in the Infrastructure services. Their operating system is now out of sight and out of their hands. Therefore AWS is now in charge of it. According to this paradigm, the customer is principally in charge of firewall setting and adequately safeguarding their data (i.e., using encryption and access management).
- The administration of any operating system, system, or network configuration, as well as platform and application management, has been transferred to AWS and is no longer our duty as the client. In comparison to services dependent on Infrastructure, there is a significant distinction.
- Not all accountability has changed, though. You should be aware that platform and application management level integration does not affect firewall setup, which is still the end user's responsibility. For instance, you would be in charge of configuring and deploying security groups for Amazon RDS, the relational database service provided by AWS.
AWS Shared Responsibility for Abstract Services
- The security of the offered service must be appropriately configured, which is essentially the customer's responsibility. For instance, if a client sets up DynamoDB with user credentials that are simple to guess, they would be liable for any data breach.
- AWS will manage Network Traffic protection using the system that secures any information moving over the AWS network. You are also in charge of using IAM tools to apply the proper permissions at the platform level (S3 Bucket rules) and the IAM user/group level.
- The degree of control and accountability goes more toward AWS than the client as we move through these models.
Conclusion
- In this article, we learned that the AWS-proposed Shared Responsibility model is a system for dividing obligations between AWS and a Customer. In the cloud, both the consumer and the cloud service provider are accountable for security.
- There are three Levels of Abstraction in cloud computing: PaaS (Platform as a Service), IaaS (Infrastructure as a Service), and SaaS (Software as a Service)., were then examined.
- After that, we discussed AWS and a customer's responsibilities in this approach before comparing and contrasting them.
- Additionally, we spoke about the various AWS Shared Responsibility Models. 1) Shared Responsibility for Infrastructure Services 2) Shared Responsibility for Container Services 3) Shared Responsibility for Abstract Services.
