AWS VPN
Overview
AWS Virtual Private Network (AWS VPN) establishes a private and encrypted connection between your network (or) device and the AWS Cloud. Users can use a client to connect to new AWS services (or) to expand their present on-premises network into a VPC.
What is Virtual Private Network (VPN)?
A Virtual Private Network (VPN) is a method that establishes a secure virtual tunnel to allow communication between two remote sites using public, unreliable network infrastructure. The security of data communication over this tunnel is achieved through encryption between the origin and the destination, removing the danger of information interception during transmission.
A VPN establishes a safe, encrypted connection over an insecure network, such as the public internet. A VPN connection uses common public infrastructure while ensuring anonymity via security mechanisms and tunneling technologies.
What is AWS VPN?
AWS Virtual Private Network securely connects your on-premises networks, distant offices, client devices, and the AWS global network. AWS VPN comprises two services: AWSSite-to-Site VPN and AWS Client VPN, both of which deliver a highly available, managed, and elastic cloud VPN` solution to secure your network traffic.
AWS Site-to-Site VPN establishes secure connections between your network and Amazon Virtual Private Clouds (or) AWS Transit Gateways. AWS Client VPN links your users to AWS (or) on-premises resources via a VPN software client to manage remote access.
Components of AWS VPN
The essential ideas for VPN are as follows:
- AWS VPN connection
A secure link between your on-premises hardware and your VPCs.
- AWS VPN tunnel
An encrypted channel over which data may transit from the client network to AWS. Each VPN connection comprises two tunnels that may be used concurrently for maximum availability.
- Client gateway
An AWS resource that provides information about your customer to the AWS gateway gadget.
- Customer gateway device
A hardware (or) software component on your end of the Site-to-Site AWS VPN connection.
- Target gateway
The VPN endpoint on the Amazon side of the Site-to-Site AWS VPN connection.
- Virtual private gateway
The AWS VPN endpoint on the Amazon side of your Site-to-Site VPN connection that can join to a single VPC is known as a virtual private gateway.
- Transit gateway:
A transit hub that can be used to connect several VPCs and on-premises networks, as well as serve as an aanAWS VPN endpoint for the Amazon side of a Site-to-Site VPN connection.
Types of AWS VPN
AWS VPN is made up of two services: AWS Site-to-Site VPN and AWS Client VPN.
AWS Site-to-Site VPN connects your on-premises network (or) branch office site to your Amazon Virtual Private Cloud (Amazon VPC). AWS Client VPN links your users to AWS (or) on-premises resources via a VPN software client to manage remote access.
AWS Client VPN
With the help of the managed client-based AWS VPN service, AWS Client VPN allows safe access to both on-premises and AWS resources. The elastic, fully-managed `AWS Client VPN service dynamically scales up (or) down in response to user demand. You don't have to maintain (or) install hardware (or) software-based solutions and try to predict how many distant users to support at once because it is a cloud AWS VPN service.
The following are the essential elements required to use AWS Client VPN.
- Client VPN Endpoint:
A Client VPN endpoint is created and configured in AWS by your Client VPN administrator. When establishing an AWS VPN connection, your administrator decides which networks and resources you can access.
- VPN Client Application
The software program you use to connect to the Client VPN endpoint and create a secure VPN connection.
- Client VPN endpoint configuration file
An endpoint configuration file that your Client VPN administrator has given you. The file contains data about the Client VPN endpoint and the certificates necessary to create an AWS VPN connection. This file is loaded into the VPN client program of your choice.
How Does It Works?
Your remote workforce uses AWS VPN to securely access resources on both AWS and on-premises networks.
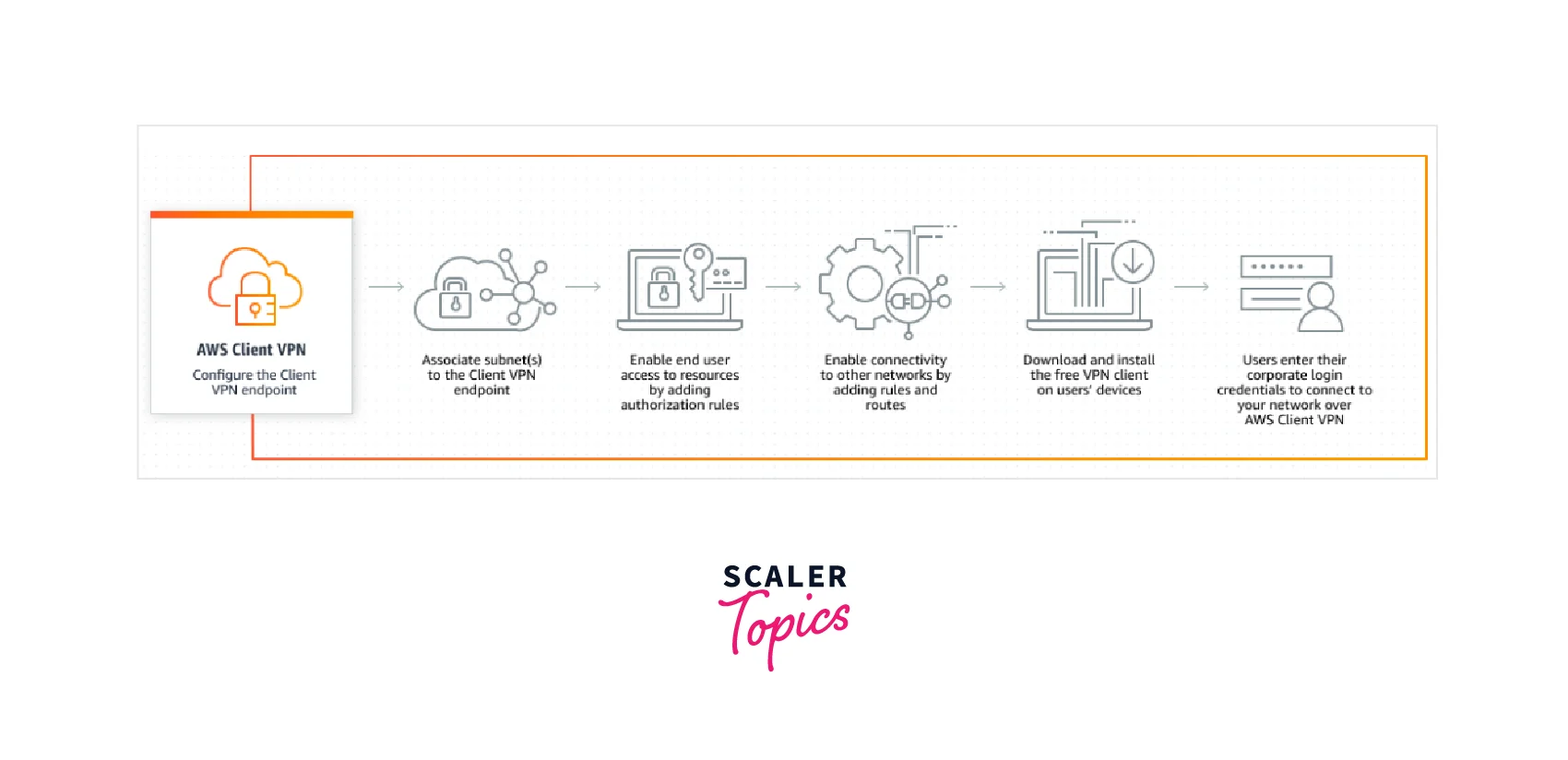
Administrators and clients are the two user personas that interact with the AWS Client VPN endpoint.
The administrator is in charge of installing and configuring the service. This includes building the Client VPN endpoint, associating it with the target network, defining the authorization rules, and adding new routes (if required). Following the installation and setup of the Client AWS VPN endpoint, the administrator downloads the Client VPN endpoint configuration file and distributes it to the customers that want access.
The final user is referred to as the client. This is the individual who establishes an AWS VPN session by connecting to the Client VPN endpoint. The AWS VPN session is established by the customer from their local computer or mobile device by utilizing an OpenVPN-based VPN client program. They can safely access the resources in the VPC where the related subnet is located after they have created the AWS VPN connection. If the necessary route and authorization rules are defined, they can also access other AWS resources, an on-premises network, or other clients.
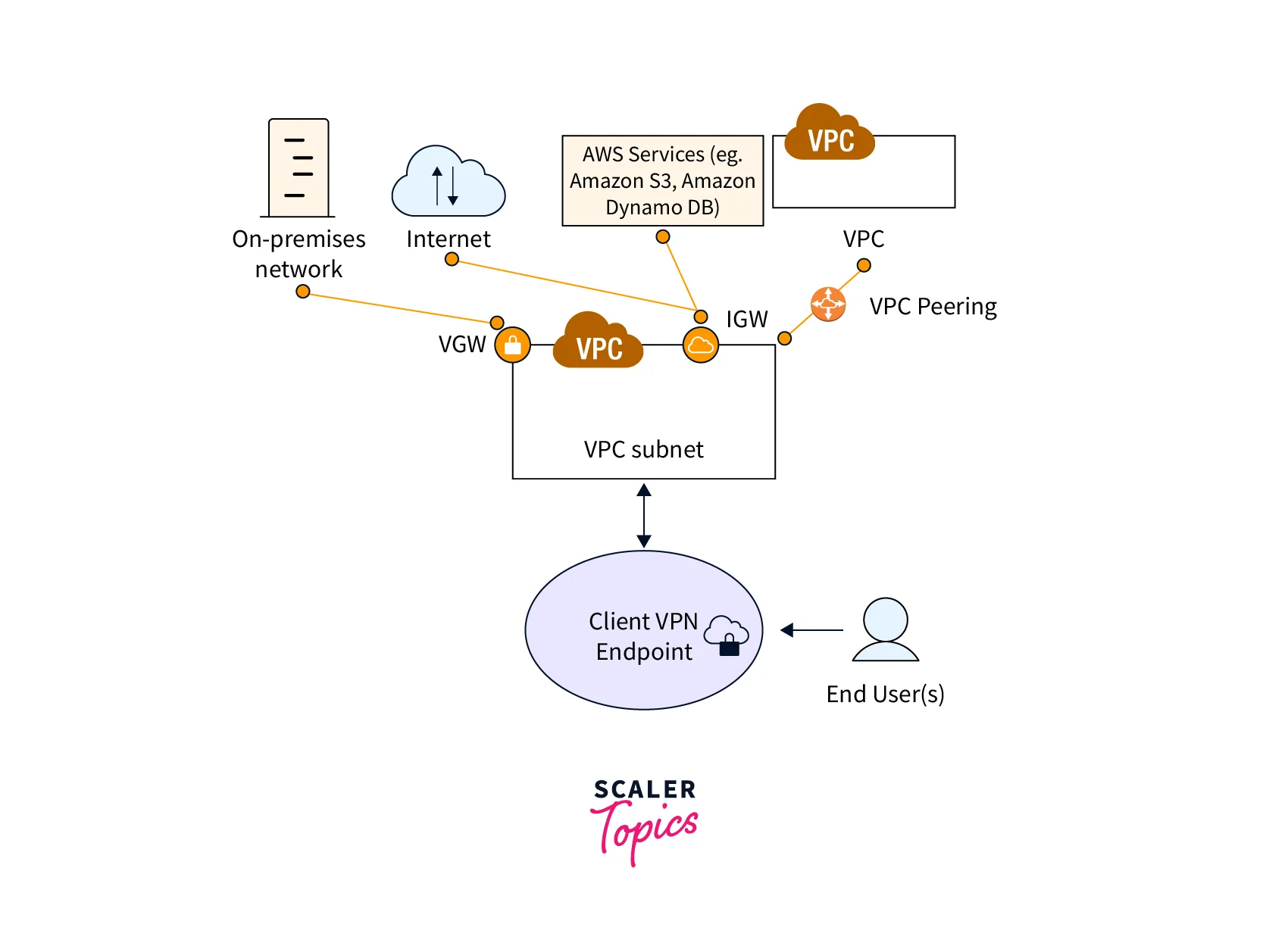
The diagram below depicts the fundamental Client VPN architecture.
Features
Authentication
AWS Client VPN will use either Active Directory (or) Certificates to authenticate. AWS VPN interacts with AWS Directory Services, which connects to your on-premises Active Directory, eliminating the need to copy data from your current Active Directory to the cloud. Certificate-based Authentication with Client VPN interfaces with AWS VPN Certificate Manager to simplify certificate provisioning, management, and deployment.
Authorization
AWS Client VPN supports network-based authorization, which allows you to set access control rules that restrict access to certain networks based on `Active Directory groups.
Secure Connectivity
AWS Client VPN uses the secure TLS VPN (Transport Layer Security VPN) tunnel protocol to encrypt communication. Users can access all AWS and on-premises resources over a single VPN tunnel that finishes at each Client AWS VPN endpoint.
Connection Management
Amazon CloudWatch Logs are used to tormentor, store, and access log files from AWS Client VPN connection logs. The corresponding log data was retrieved from CloudWatch Logs. While maintaining control over who has access to your network, you can simply monitor, do a forensics investigation, and terminate individual connections.
Compatibility
The AWS VPN service is intended to connect devices to your network. It allows you to select an OpenVPN-based client, allowing workers to use whatever device they want, including Windows, Mac, iOS, Android, and Linux computers.
Service Management
Because it is an AAWS-managed service, it alleviates the administrative effort of establishing and operating a third-party remote access VPN solution.
High Flexibility and Availability
It grows automatically based on the number of users connected to your AWS and on-premises resources.
Granular Control
It allows you to define network-based access rules to apply bespoke security controls. These rules can be defined at the Active Directory group level. Access control can also be implemented using security groups.
Simpleness of Usage
It allows you to access both AWS and on-premises resources using a single VPN channel.
Manageability
It allows you to see connection logs, which include information about client connection attempts. You may also manage active client connections, including the option to disconnect them.
In-Depth Integration
It is compatible with existing AWS services such as AWS Directory Service and Amazon VPC.
Use Cases
Rapidly Expanded Remote Access
Unexpected occurrences may necessitate that many of your staff work remotely. This causes an increase in `AWS VPN connections and traffic, which might impact performance and availability for your users. AWS Client VPN is elastic, scaling up automatically to meet peak demand. It scales back down when the surge has gone to avoid paying for wasted capacity.
Accessing Applications during Migration
AWS Client VPN gives customers safe access to apps on and off the cloud. This is useful during cloud migrations when applications are moved from on-premises to the cloud. Users do not need to modify how they access their apps during (or) after migration using AWS VPN.
Connection with Authentication and MDM systems.
When using the AWS-provided OpenVPN Client software, AWS Client VPN supports Authentication with Microsoft Active Directory via AWS Directory Services, Certificate-based Authentication, and Federated Authentication via SAML-2.0. AWS VPN integrates with Mobile Device Management (MDM) solutions to reject devices that violate your regulations.
Securely Integrating Devices
Using certificate-based Authentication, establish encrypted connections between IoT devices and Amazon Virtual Private Cloud (VPC) services.
Pricing
-
In AWS VPN, you are charged for the number of active client connections per hour and the number of linked subnets using Client VPN per hour.
-
Billing begins after the subnet connection is established, and each partial hour utilized is charged at the hourly rate.
-
The next stage is to connect customers to the AWS VPN endpoint, after which they are charged a second cost per hour dependent on the number of active clients connected to the Client VPC endpoint. Any customer connection that lasts shorter than an hour is also pro-rated.
AWS Client VPN pricing example:
You set up an AWS Client VPN endpoint and assign it to a single subnet. Then, you establish ten Client VPN connections to your AWS VPN endpoint. These links are live for one hour.
AWS Client VPN endpoint hourly charge:
For a particular AWS Region, the AWS Client VPN endpoint hourly fee is KaTeX parse error: Expected 'EOF', got ' ' at position 138: …nection fees is ̲0.50 per hour. AWS Client VPN total costs $0.60 per hour in this instance.
AWS Site-to-Site VPN
The AWS Site-to-Site VPN service establishes a secure link between your data center (or) branch office and your AWS cloud services. For globally distributed applications, the Accelerated Site-to-Site AWS VPN option, which integrates with AWS Global Accelerator, provides even higher performance.
How Does It Works?
A Site-to-Site VPN connection offers two VPN tunnels between a virtual private gateway or a transit gateway on the AWS side, and a customer gateway (which represents a VPN device) on the remote (on-premises) side.
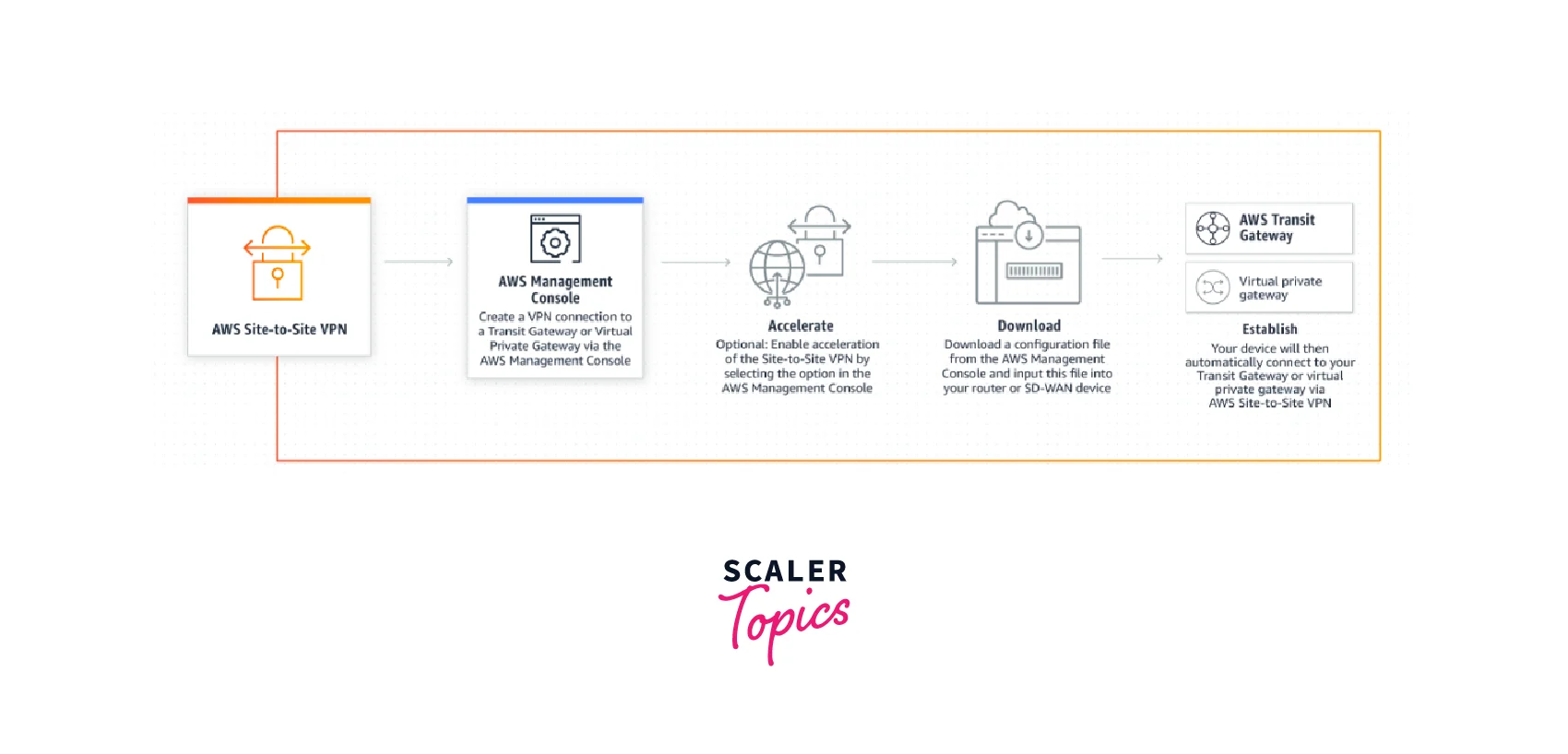
Contents required for the AWS Site-to-Site VPN connection include the:
- Virtual private gateway The AWS VPN concentrator on the Amazon side of the Site-to-Site VPN connection is known as a virtual private gateway. You set up a virtual private gateway and link it to the VPC where you wish to establish the Site-to-Site AWS VPN connection.
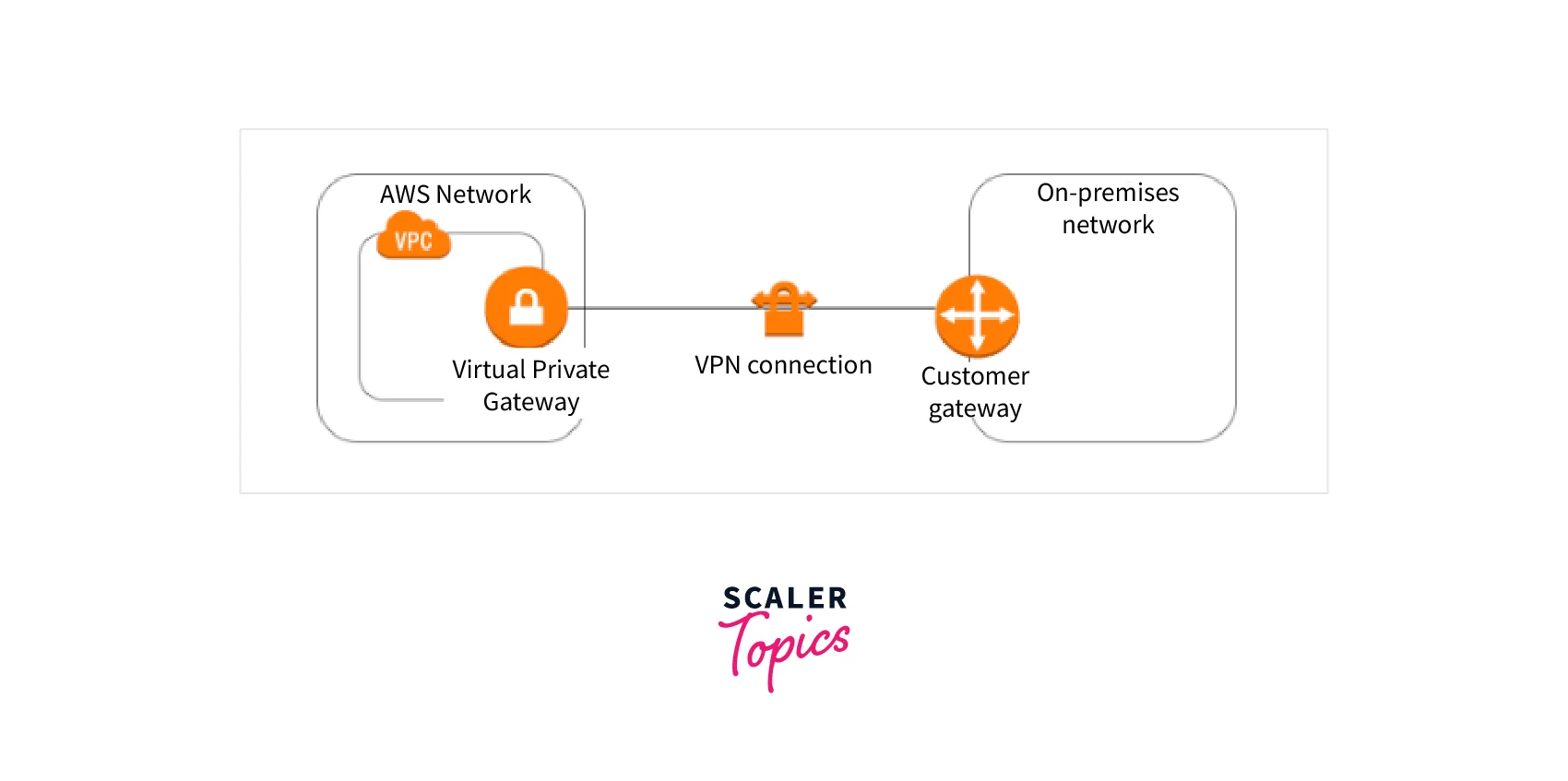
You can define the private Autonomous System Number (ASN) for the Amazon side of the gateway when you construct a virtual private gateway. If no ASN is specified, the virtual private gateway is established using the default ASN. If no ASN is specified, the virtual private gateway is established using the default ASN.
- Gateway for transit A transit gateway is a transit hub that connects your virtual private clouds (VPC) and on-premises networks. A Site-to-Site AWS VPN connection can be created as an attachment on a transit gateway.
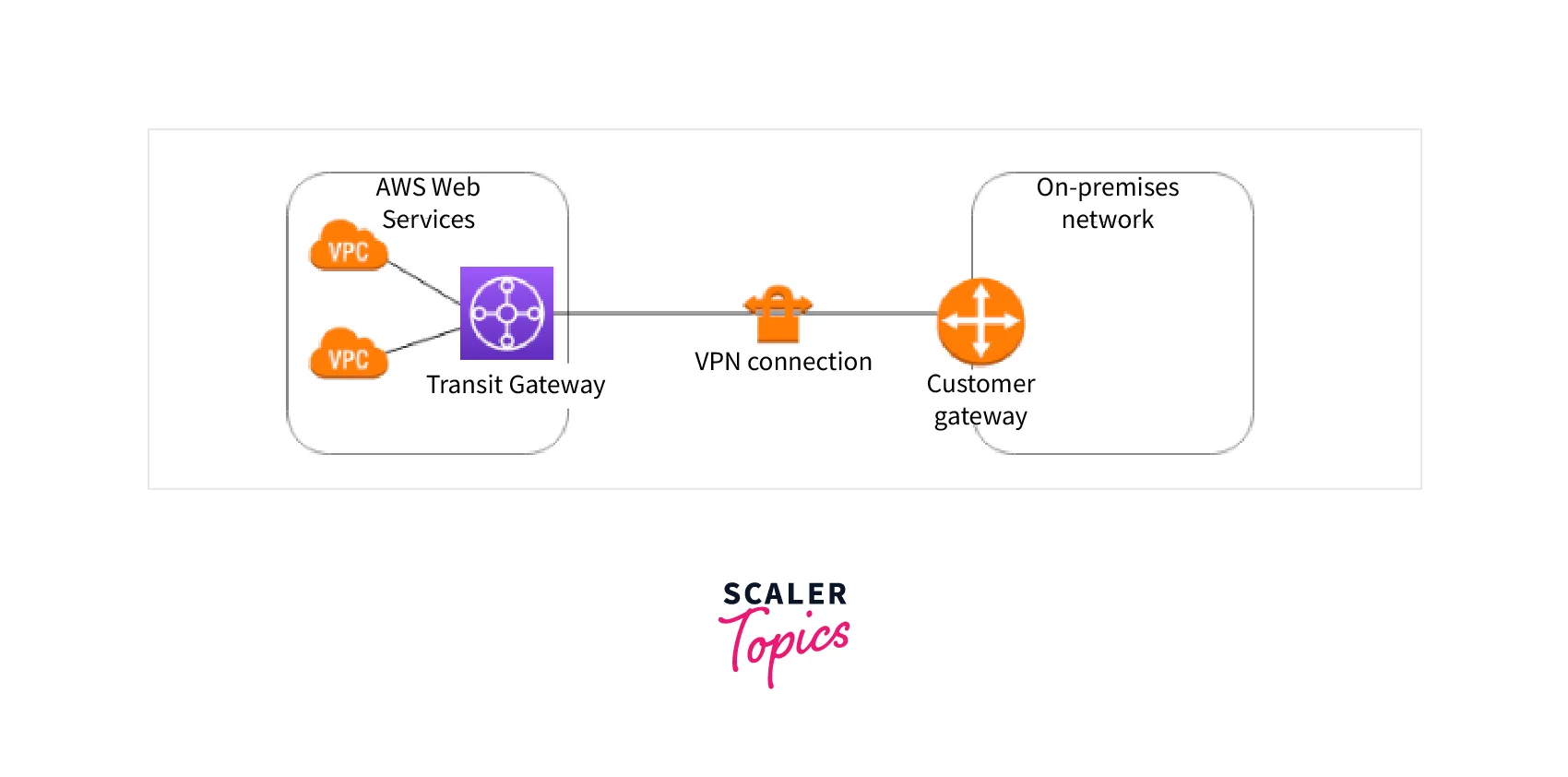
- Client gateway device On your side of the Site-to-Site AWS VPN connection, a client gateway device is a physical hardware or software program. You set up the device to use the Site-to-Site VPN connection.
- Customer interface A customer gateway is an AWS VPN resource that represents a customer gateway device in your on-premises network. AWS receives information about your device when you create a customer gateway.
Features
Site-to-Site AWS VPN Acceleration
When you connect an on-premises site to the AWS cloud, Accelerated Site-to-Site AWS VPN will route your VPN traffic to the AWS edge location nearest to you. Accelerated VPN boosts the speed of your Site-to-Site` VPN connections by shortening the distance over which data is transferred over the internet and instead using the AWS global fiber network's stability and performance.
Connectivity that is secure
AWS Client VPN employs OpenVPN, which negotiates data channel settings via a TLS encrypted control channel. The data channel is SSL-based, but additional safeguards are added.
High accessibility You can construct failover and CloudHub solutions with AWS Site-to-Site AWS VPN and AWS Direct Connect. CloudHub allows your distant sites to interact with one another and the VPC. It runs on a straightforward hub-and-spoke topology that may be used with or without a VPC. Customers with many branch offices and existing internet connections that want to construct a convenient, possibly low-cost hub-and-spoke architecture for main or backup communication between these remote locations may consider this concept.
Customization Options for tunnel setup offered by Site-to-Site AWS VPN include the inner tunnel IP address, pre-shared key, and Border Gateway Protocol Autonomous System Number (BGP ASN). You may set up additional secure VPN tunnels in this manner to boost the bandwidth for your apps.
Traversal of Network Address Translation (NAT)
Thanks to AWS Site-to-Site VPN's NAT Traversal apps, you may utilize private IP addresses behind routers on private networks with a single public IP address facing the internet.
AWS VPN Private IP
Site-to-site VPN connections may be deployed using private IP addresses (DX) with Direct Connect. This functionality allows you to encrypt DX communication between your on-premises network and AWS without using public IP addresses, resulting in greater security and network privacy`.
Monitoring
Site-to-Site AWS VPN may send metrics to CloudWatch, giving you more visibility and control. CloudWatch also allows you to transmit your custom metrics and add data points in any sequence and at your desired pace. You may obtain statistics on those data points as an ordered collection of time-series data.
Use Cases
Migration of Applications
Moving apps to the cloud is simpler with a Site-to-Site AWS VPN connection between your network and the AWS cloud. Without altering how your users use these apps, you may effortlessly relocate your IT resources and `host Amazon VPCs inside your company firewall.
Hidden transmission between various sites
Site-to-Site AWS VPN connections are used for secure communication between distant sites.
Pricing
-
Each hour your AWS VPN connection is provisioned and accessible results in a fee. Data transport from Amazon EC2 to the internet incurs a fee.
-
When you establish an accelerated AWS VPN connection, we create and manage two accelerators on your behalf. Each accelerator carries a data transfer fee and an hourly rate.
-
If you establish an AWS Site-to-Site VPN connection to your Amazon VPC, you are invoiced for each AWS VPN connection hour that the VPN connection is established and accessible; partial AWS VPN connection use is billed as a full hour. Charges for ordinary AWS data transmission apply to all data sent through the AWS VPN connection.
Site-to-Site VPN pricing example:
User set up an AWS Site-to-Site VPN connection to your Amazon VPC. The connection is valid for 30 days and is available 24 hours a day. This connection allows you to transmit 1,000 GB in and 500 GB out.
AWS Site-to-Site VPN connection price: AWS Site-to-Site VPN charges an hourly fee while connections are active. The price for the Region can be 36.00 per month. Data transfer out fee: The first 100 GB are free, therefore you pay 36.00 per month. Site-to-Site AWS VPN total costs $72.00 per month.
VPN CloudHub
Using the AWS VPN CloudHub, which builds on the AWS-managed VPN alternatives previously discussed, you may securely interact between two sites. You can use the AWS VPN CloudHub with (or) without a VPC, thanks to its straightforward hub-and-spoke architecture. Use this method if you have many branch offices and active internet connections and wish to construct a handy, potentially affordable hub-and-spoke architecture for primary or backup communication between these remote locations.
The following diagram shows the AWS VPN CloudHub architecture, with dashed lines representing network traffic routed over AWS VPN connections between distant sites.
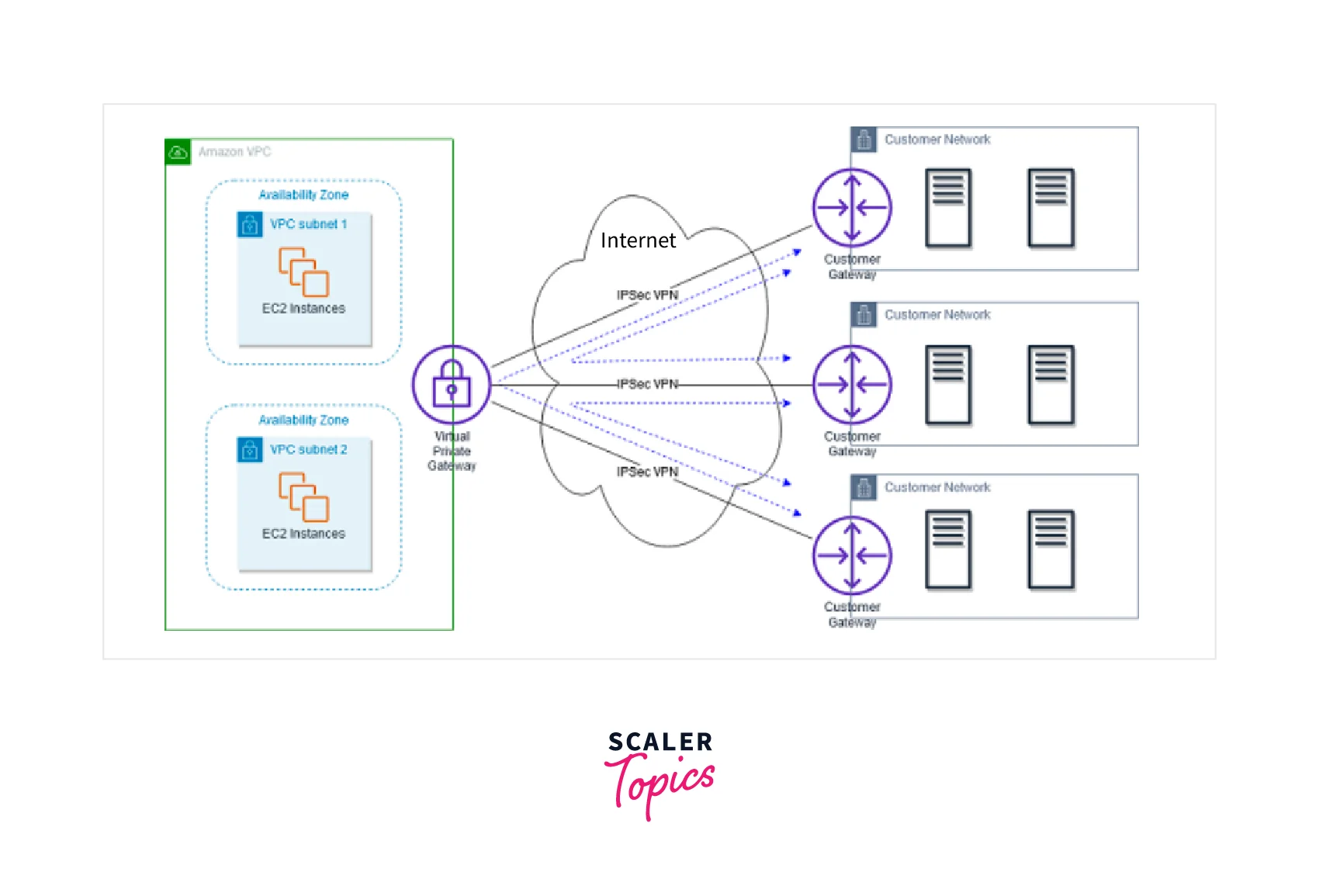
Multiple client gateways connected to an Amazon VPC virtual private gateway utilizing different BGP autonomous system numbers are used by AWS VPN CloudHub (ASNs). Over their VPN connections, your gateways broadcast the proper routes. Each BGP peer receives and broadcasts these routing advertisements for each site to send data to and receive data from the other sites. Each spoke's distant network prefixes need to have distinct ASNs, and the sites can't have IP ranges that overlap.
To set up the CloudHub: Building several client gateways, each with a unique public IP address and ASN, is feasible. Each client gateway and a shared virtual private gateway can establish an AWS VPN connection. Each AWS VPN connection has to promote its unique BGP routes. Network statements are used in the AWS VPN configuration files for the VPN connection to do this.
Benefits of AWS VPN
-
The deployment setups are carried out easily by using step-by-step installation wizards, thanks to connections made over the AWS VPN. Users' access is made as easy as feasible by entering the login and password in the browser.
-
Additionally, they enable straightforward control and Monitoring by the solution's administrators, even without extensive networking expertise. To satisfy the needs of SMBs, they also provide simpler license and support options, which reduce costs.
-
Protection from hacking data, systems, and websites via remote access, where the answer is also available.
-
The transmission of private data over the internet without danger of data theft or espionage.
-
Identify users who `access systems and data, centralized control over the system, and have information access rights (with the appropriate AWS VPN key management platform).
-
Defending your internal network's most critical servers and workstations from harmful employee and outsider assaults (by adopting an encryption solution).
-
Protection of automated machine and sensor production cycles in an industrial setting (with the adoption of an encryption solution).
Difference between AWS VPN and AWS Direct Connect
1. Network and Connection:
The performance of the AWS VPN can reach 4 Gbps or less compared to Direct Connect. Direct Connect offers performance ranging from 50 Mbps to 100 Gbps.
While the network in AWS Direct Connect is stable and offers a constant experience, the network in AWS VPN is connected to shared and public networks, which causes bandwidth and latency to change.
2. Pricing:
An AWS VPN is less expensive than AWS Direct Connect.
AWS Direct Connect does not offer a VPN option based on connection hours.
3. Security:
Your communication is not automatically encrypted in transit when using AWS Direct Connect. The client network and AWS link are secured via Site-to-Site AWS VPN.
AWS Direct Connect is the primary option for businesses that want stronger security requirements since it offers higher security. Because the communication is carried over the public Internet network rather than a private dedicated network, AWS VPN raises greater security issues.
4. Establishing time
VPN is recommended for businesses new to using AWS Cloud since it is simpler to set up and install than AWS Direct Connect.
AWS Direct Connect can be used by businesses that want more security and consistent network performance. Installation needs a skilled staff, and setup is more difficult than AWS VPN.
5. Link Aggregation Group
Link aggregation groups may be used in Direct Connect to combine several connections into one and efficiently manage the connection.
VPN does not employ link aggregation groups, and numerous connections into the network are not possible. As a result, the connections are not efficiently handled.
6. Routing Options:
Because routing is not a primary problem in Direct Connect, no different routing choices are supplied.
Dynamic and static routing options are offered, allowing the network and the user to access flexible routing setups.
7. Availability
Direct Connect is always available since it does not rely on public networks or internet connections. As a result, it is not essential to supply several data centers in different places.
The availability of a VPN connection is increased by making two geographically separated data centers accessible so that the VPN connection is not disrupted.
Conclusion
-
AWS VPN comprises two services: AWS Site-to-Site VPN and AWS Client VPN, both of which deliver a highly available, managed, and elastic cloud VPN solution to secure your network traffic.
-
AWS Client VPN supports network-based authorization, which allows you to set access control rules that restrict access to certain networks based on Active Directory groups.
-
AWS Client VPN is elastic, scaling up automatically to meet peak demand. It scales back down when the surge has gone to avoid paying for wasted capacity.
-
Accelerated AWS VPN boosts the speed of your Site-to-Site AWS VPN connections by shortening the distance over which data is transferred over the internet and instead using the AWS global fiber network's stability and performance.
-
A Site-to-Site AWS VPN connection between your network and the AWS cloud makes moving programs to the cloud easier. You can easily transfer your IT resources and run Amazon VPCs within your corporate firewall without changing the permissions of the users.
-
AWS Direct Connect is the primary option for businesses that want stronger security requirements since it offers higher security.
