IAM Elements in AWS
Overview
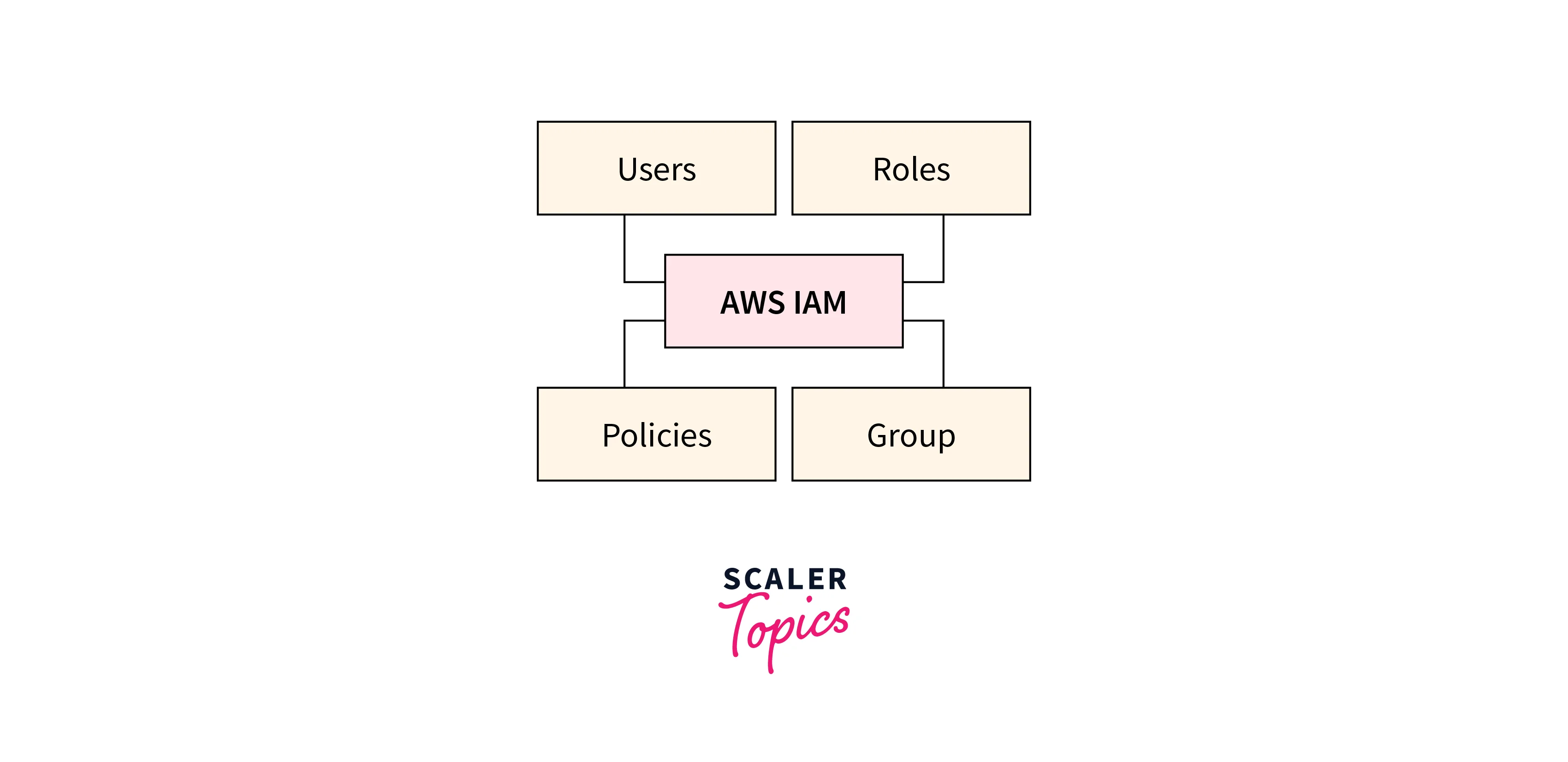
AWS Identity and Access Management (IAM) controls access to AWS services and resources. It consists of users, groups, roles, policies, and permissions. Users are entities with unique credentials, while groups organize users for collective permission management. Roles define permissions for entities both within and outside AWS accounts. Policies are JSON documents outlining permissions, attached to users, groups, or roles. IAM ensures security by regulating who can access resources and what actions they can perform, facilitating granular control over AWS services, minimizing security risks, and allowing scalable, secure management of users' access within the AWS ecosystem.
What are IAM Elements in AWS?

IAM elements are the fundamental components and concepts within IAM that enable you to manage access to your AWS environment.
Users
IAM users in AWS are fundamental entities representing individuals, applications, or services interacting with AWS resources. Each user has distinct credentials—username/password or access keys—enabling access to the AWS Management Console or programmatic interaction via APIs. Users are pivotal in access control, where permissions are assigned through policies defining allowable actions on specific AWS resources. This granularity allows adherence to security best practices, like implementing Multi-Factor Authentication (MFA) and following the principle of least privilege. User lifecycle management involves creation, modification, and deletion as organizational needs evolve.
Users can assume roles to integrate with other AWS services temporarily, facilitating tasks or resource access. For Example, "Sameer" is an IAM user with rights to manage S3 buckets and limited access to EC2 instances.
Groups
In AWS IAM Elements, Groups are collections of IAM users, simplifying permission management by allowing bulk assignment of policies. They serve as a way to organize users with similar responsibilities or access requirements into logical units. By associating policies with groups, permissions can be efficiently granted or revoked across multiple users simultaneously. This streamlines administration, ensuring consistent access controls for users within the same functional or departmental role.
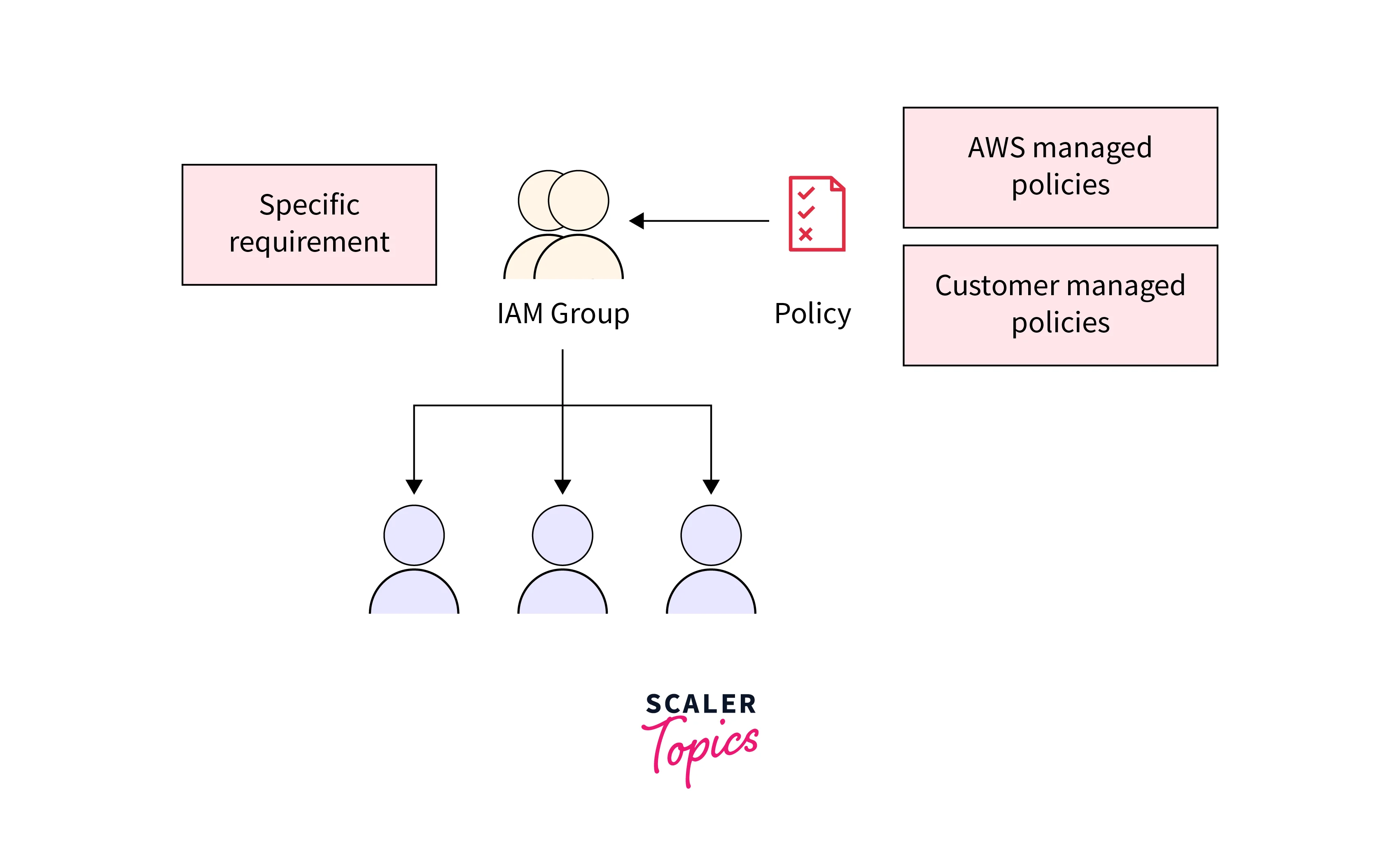
Groups don't have their own credentials; they inherit permissions from the policies attached to them. This abstraction minimizes redundancy, as changes made to group policies reflect in all associated users' permissions. Groups enhance security by enforcing the principle of least privilege, granting users only the necessary access for their roles. For example, the "Developers" group might have access to EC2 instances and limited rights to manage S3 buckets.
Roles
In AWS IAM, Roles are pivotal elements designed for interaction between AWS services and applications with other AWS resources. Unlike users, roles are not directly associated with specific individuals or entities; instead, they are intended for temporary use by automated systems. Roles offer a secure and versatile mechanism for delegated permissions, widely employed by services such as EC2 instances and Lambda functions. When a service assumes a role, it gains temporary access to specified resources, ensuring accountability and traceability.
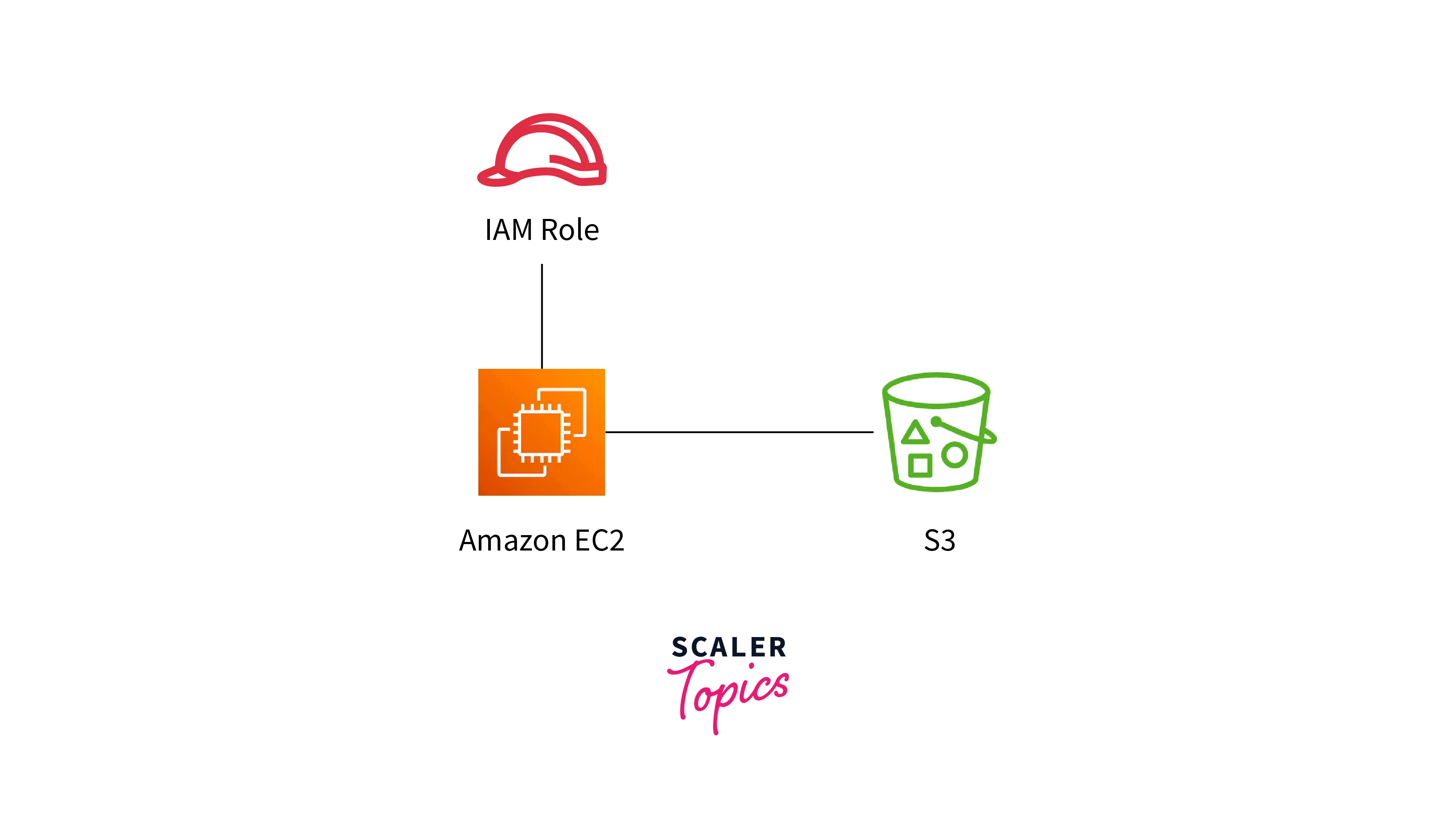
Roles play a crucial role in enabling fine-grained access control and adhering to the principle of least privilege. They facilitate secure delegation of permissions, allowing services to perform necessary tasks without the constraints of permanent identity associations, thereby enhancing flexibility, security, and governance within the AWS environment. For example, "DataAnalystRole" grants read-only access to S3 buckets and permits running specific queries within an RDS database, ensuring controlled data analysis.
Policies
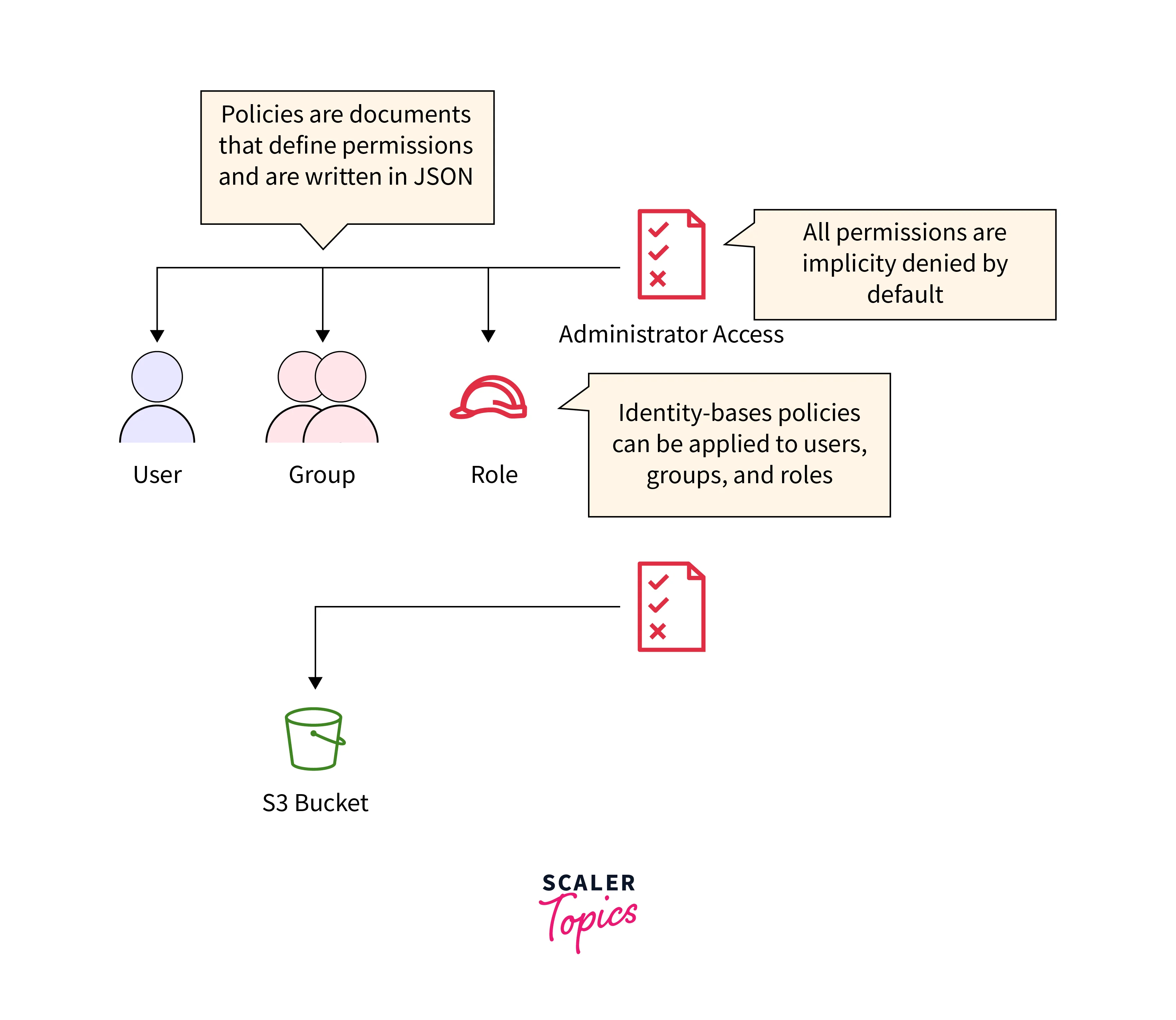
In AWS IAM, policies are crucial elements defining permissions and access controls for users, groups, and roles. These JSON-based documents outline rules specifying what actions are permitted or denied on specific AWS resources. Policies can be attached to IAM identities, allowing precise definition of allowed actions, resources, and conditions for access. They encompass statements that articulate permissions, including actions (such as read, write, or modify), resources (like S3 buckets or EC2 instances), and optional conditions (like IP addresses or time of access).
Policies enable the implementation of the principle of least privilege, ensuring that entities have only the necessary permissions for their tasks, bolstering security and compliance. This policy grants permission to perform the s3:GetObject action on all objects within the "example-bucket" S3 bucket (arn:aws:s3:::example-bucket/*)
IAM Processes
IAM (Identity and Access Management) processes are crucial for managing and controlling access to resources within an organization's digital environment.
Authentication
- Authentication within IAM processes involves verifying a user's identity to grant access to systems or resources.
- It's the crucial step where individuals prove they are who they claim to be.
- Various methods ensure this verification, including passwords, biometrics (like fingerprints or facial recognition), tokens, or smart cards.
- Multi-factor authentication (MFA) combines two or more authentication factors for heightened security.
- The process involves validating the provided credentials against stored or generated data, ensuring their accuracy before permitting access.
- Robust authentication mechanisms thwart unauthorized access attempts, enhancing system security.
- Continual advancements in technology, such as adaptive authentication, analyze multiple factors like location, device, and behavior to dynamically adjust security measures.
- Authentication, a cornerstone of IAM, safeguards sensitive information and resources while enabling legitimate users to access essential systems efficiently.
Authorization
- Authorization within IAM processes dictates the permissions and level of access granted to authenticated users.
- Once a user's identity is confirmed through authentication, authorization determines what resources, data, or actions they can access or perform within a system or application.
- This process involves defining user roles, groups, or individual entitlements and associating them with specific permissions or restrictions.
- Access control lists (ACLs), role-based access control (RBAC), attribute-based access control (ABAC), or other mechanisms are employed to enforce these authorizations.
- Authorization ensures that users only have access to the resources required for their roles while preventing unauthorized access to sensitive data or critical systems.
- Continuous monitoring and periodic reviews of authorization settings are essential to maintain security, compliance, and alignment with evolving organizational needs within the IAM framework.
Identity Lifecycle Management
- Identity Lifecycle Management (ILM) in IAM processes involves the comprehensive management of user identities throughout their entire lifecycle within an organization.
- This encompasses the creation, modification, and deactivation of user accounts, aligning access with their evolving roles and responsibilities.
- During onboarding, ILM ensures the provisioning of appropriate access rights.
- Throughout an individual's tenure, it facilitates updates and adjustments to permissions based on changing roles or requirements.
- When employees depart, ILM oversees the deprovisioning process, promptly revoking access to prevent security risks.
- Automation plays a key role in streamlining these processes, improving efficiency, and reducing the risk of human error.
- Effective ILM contributes to security, compliance, and operational efficiency, making it a crucial component of IAM strategies for organizations managing access to digital resources.
User Management
In Amazon Web Services (AWS), Identity and Access Management (IAM) governs User Management, enabling the control and management of user access to AWS resources. Within AWS IAM, User Management involves several key aspects:
- User Creation and Deletion:
IAM allows the creation of individual users or groups, each with unique credentials and permissions tailored to specific roles or tasks. Admins can swiftly create, modify, or delete user accounts as needed. - Permission Assignment:
Users are granted permissions via policies. These policies define what actions they can perform on AWS resources. Permissions can be granular, allowing precise control over resource access. - Multi-factor Authentication (MFA):
IAM supports MFA, adding an extra layer of security by requiring users to present an additional form of verification, such as a code from a mobile device, along with their password. - Password Policies:
Administrators can set and enforce password policies to ensure strong, regularly updated passwords for user accounts, bolstering security measures. - Access Keys and Credentials:
IAM manages access keys for programmatic access to AWS services, allowing automation and interaction with AWS resources through APIs securely.
IAM Best Practices
Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) in AWS IAM is a core best practice that advocates granting users only the minimum permissions required to perform their tasks. It ensures that users have precisely the necessary access rights and no more, minimizing the potential impact of security breaches or human errors. By following PoLP, AWS IAM assigns permissions at a granular level, tailoring access to specific job roles or functions.
Regularly reviewing and refining these permissions helps to align access with evolving responsibilities, reducing the risk of unauthorized actions or data breaches. Implementing PoLP enhances security by limiting the scope of potential damage from compromised accounts, reducing attack surfaces, and enabling better control over AWS resources, ensuring a more robust and secure environment.
Multi-Factor Authentication (MFA) Authentication Methods
Multi-Factor Authentication (MFA) is a crucial best practice within AWS Identity and Access Management (IAM) that adds an extra layer of security beyond passwords. AWS encourages MFA as a standard authentication method for user accounts. It requires users to present at least two forms of verification before accessing AWS resources, typically combining something they know (like a password) with something they have (such as a mobile device or hardware token).
By implementing MFA in AWS IAM, it significantly reduces the risk of unauthorized access, even if passwords are compromised. AWS supports various MFA methods like virtual MFA devices, hardware MFA tokens, or SMS-based authentication, allowing users flexibility in choosing their preferred authentication mechanism. Enforcing MFA across user accounts strengthens security measures, aligning with industry best practices and bolstering protection against unauthorized access attempts within the AWS environment.
Regular Auditing
Regular auditing in AWS IAM is a fundamental best practice that involves systematically reviewing and analyzing user permissions, access logs, and configurations within an AWS environment. This process ensures compliance adherence, identifies security gaps, and detects any unauthorized or suspicious activities. Auditing involves scrutinizing access controls, IAM policies, and user activities to verify that permissions align with the Principle of Least Privilege and comply with organizational standards and regulations.
By routinely examining IAM configurations and access logs, organizations can proactively address vulnerabilities, prevent unauthorized access, and respond swiftly to potential security incidents. This practice enhances the overall security posture, aids in risk mitigation, supports compliance requirements, and fosters a proactive security approach, enabling organizations to maintain a robust and secure AWS environment.
Conclusion
- AWS IAM elements include users, groups, roles, policies, ACLs, MFA, Identity Providers, STS, credential reports, access analyzer, and best practices analyzer, managing access and permissions within AWS.
- IAM Users are entities with unique credentials within AWS, allowing individuals to interact with AWS services, each having defined permissions and access to resources.
- IAM Groups in AWS are collections of users sharing similar permissions. They simplify access management by allowing policies to be applied collectively to multiple users.
- IAM Roles in AWS grant temporary permissions for users, services, or resources, defining access to specific AWS resources without needing permanent credentials.
- IAM Policies in AWS define permissions, allowing or denying actions on specific AWS resources. They're attached to users, groups, or roles, controlling access within the AWS environment.
- Authentication in AWS IAM verifies user identities using credentials like passwords or keys, ensuring access to AWS services aligns with authorized users.
- Authorization in AWS IAM controls user access to AWS resources by applying policies defining what actions are permitted or denied based on defined permissions and roles.
- Identity Lifecycle Management in AWS IAM involves managing user identities throughout their entire tenure, covering creation, modification, and deactivation to align access with evolving roles and requirements.
- IAM best practices in AWS involve implementing least privilege, using MFA, regularly auditing permissions, creating and managing roles, and employing strong policies for secure access management.
