NACL ( Network Access Control Lists )
Overview
Amazon NACL ( Network Access Control List) is a security measure used by the Amazon Web Services stack. By supplying a firewall, Network Access Control List aids in securing the VPCs and subnets. It assists in providing a security layer that regulates and effectively manages the traffic that circulates within the subnets.
What are Network Access Control Lists?
A network access control list (ACL) permits or prohibits particular inbound or outgoing traffic at the subnet level. To give one more layer of security to your VPC, you can either use the default network ACL or establish a custom network ACL with rules that are identical to the rules for your security groups.
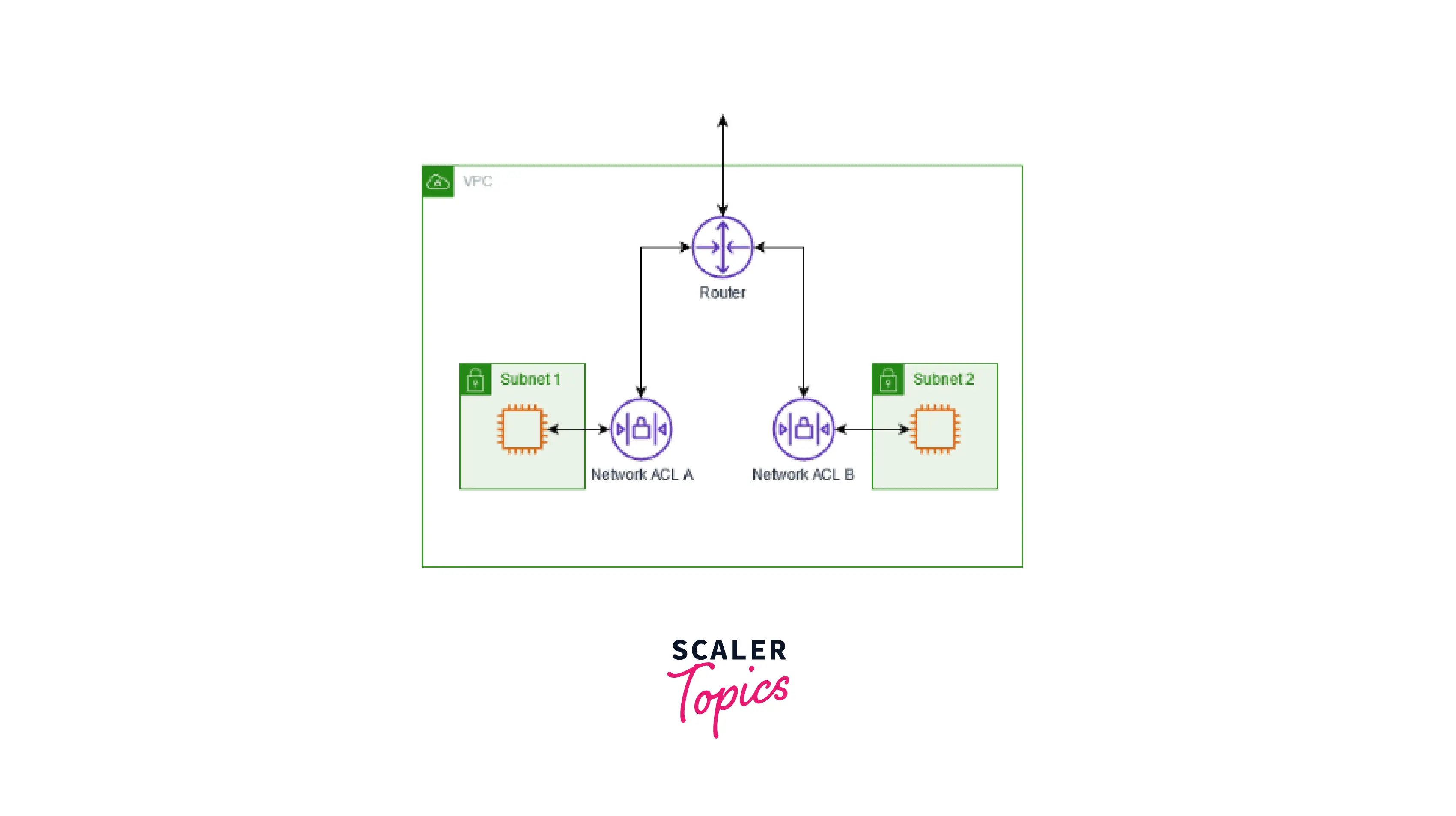
The diagram that follows demonstrates a VPC with two subnets. A network ACL exists for each subnet. The router routes the traffic to its destination when it enters the VPC (for instance, from a peering VPC, VPN connection, or the internet). Traffic heading towards subnet one is permitted to enter subnet one, and traffic heading outside of subnet one is allowed to depart subnet 1, according to network ACL A. Like ACL A, network ACL B controls which traffic can enter and exit subnet 2.
Components of Network Access Control List
Network Access Control List entries are made up of several distinct parts that describe how the Network Access Control List handles various traffic kinds. Here are a few instances of typical Network Access Control List elements:
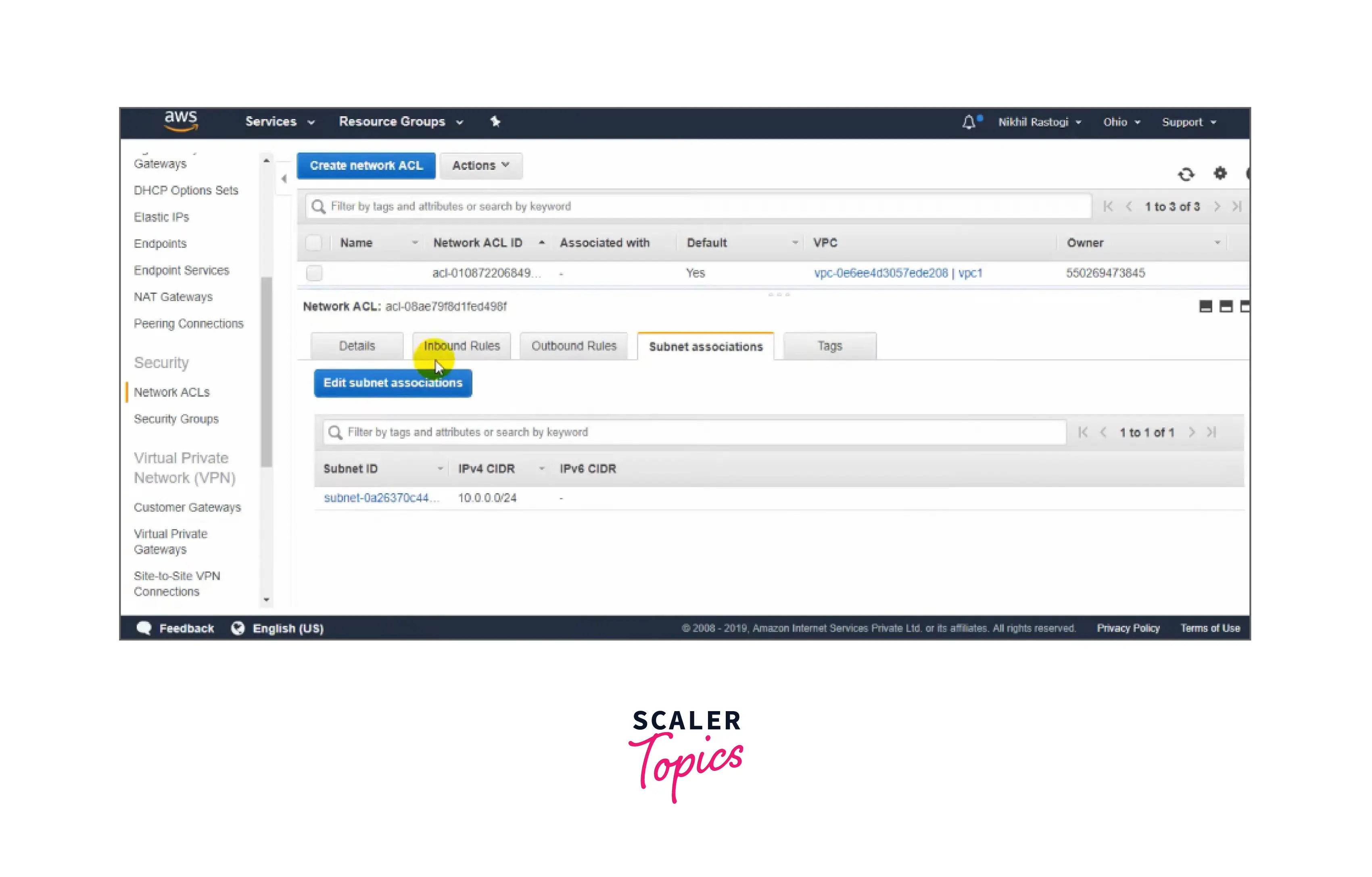
In the above image, you can see the information related to Network Access Control List(NACL) such as name, Network ACL ID, associated VPC, and owner.
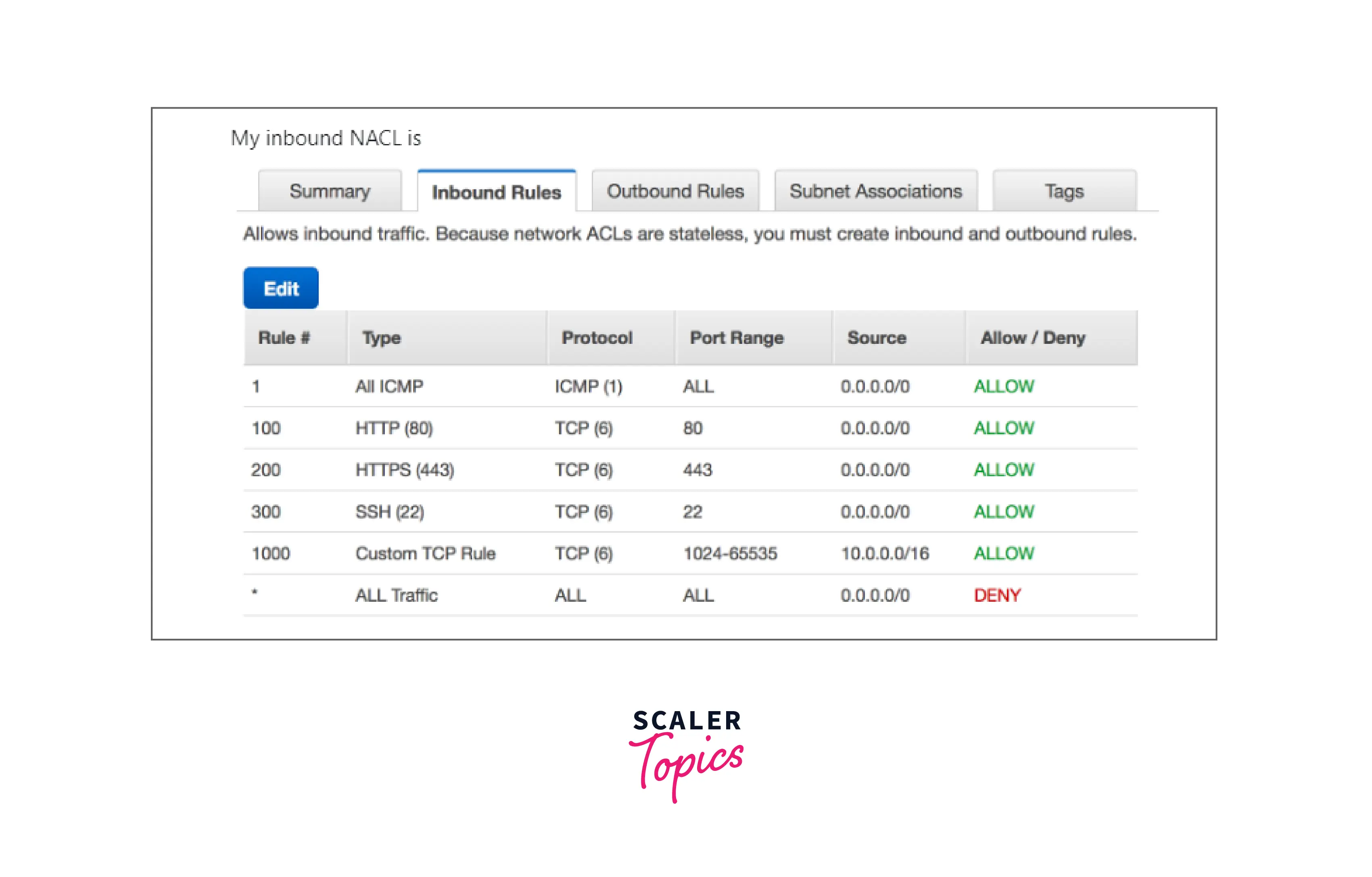
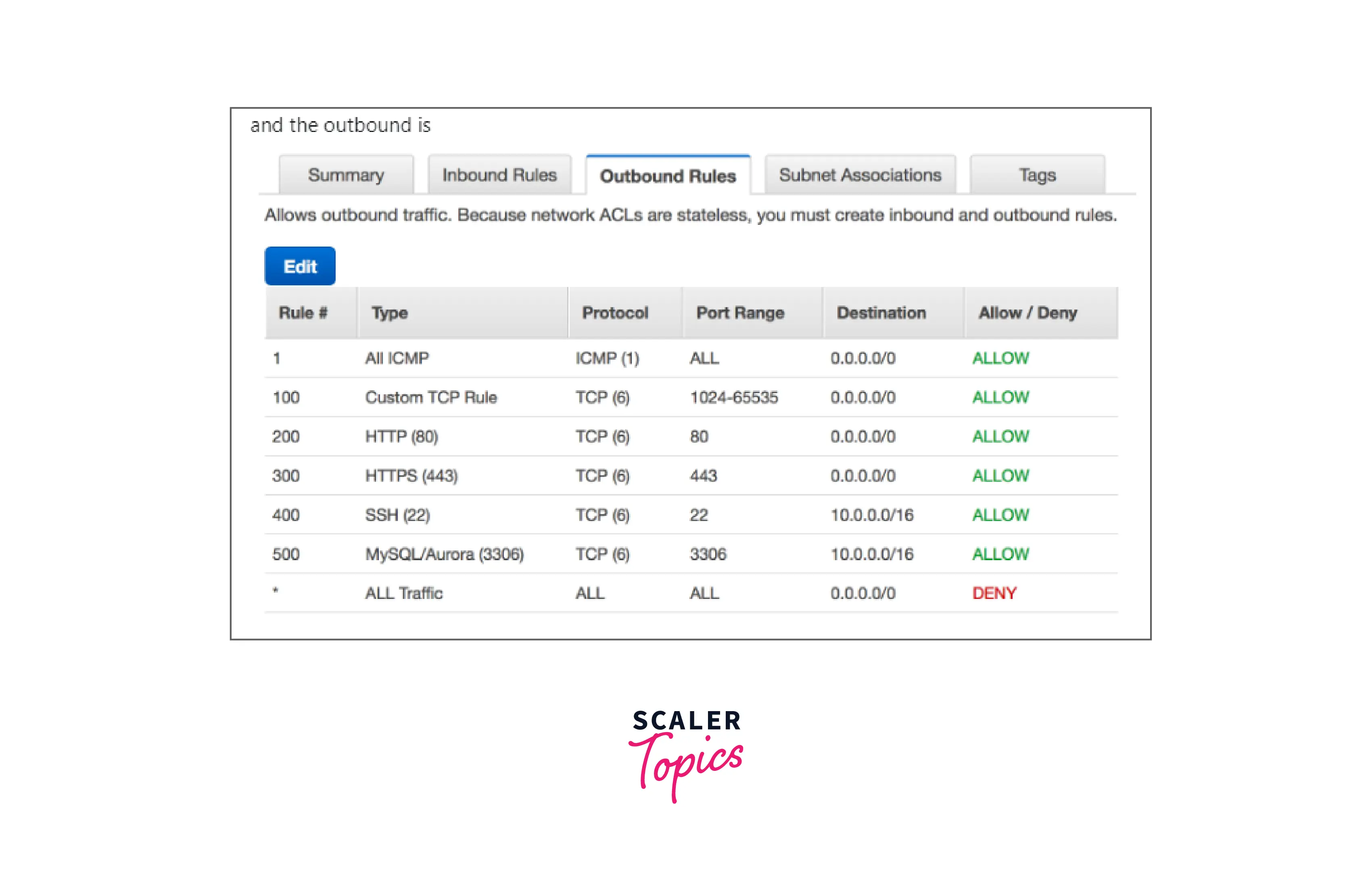
You can easily refer to the above images for the below-mentioned points:
Network Access Control List's name: This uses a name rather than a number to identify an ACL as shown in the above image. Some ACLs permit both letters and numbers.
Rule Number: The rule with the lowest number is examined first. Any higher-numbered rule that might conflict with a rule that matches traffic is ignored.
Type: The nature of the transmission, like SSH, HTTPS, HTTP, ALL ICMP, etc. Additionally, you may pick a specific range (or) all traffic.
Protocol: Any protocol with a standard number can be specified for example ICMP, TCP, etc. You can select any or all of the ICMP types and codes if you choose ICMP as the protocol.
Port Range: The traffic's listening port or set of ports. For example 80 for HTTP traffic, 443 for HTTPS, 3306 for MySQL/Aurora, etc.
Source: The origin of the traffic (CIDR range) is shown in the inbound image above.
Destination: The location where the traffic is headed (CIDR range) as shown in the outbound image above.
Benefits
-
When a website has to be visited, the user's request must land on the correct port and the website server must access the database(having data stored), and after extracting the necessary information, the website server must respond to the user.
-
The default Network Access Control List for ipv4 traffic is already present in the VPC. Constructing a custom Network Access Control List and linking it to a subnet is possible. The default setting for this modified Network Access Control List is to block all incoming and outgoing IPv4 traffic. It has to follow a set of rules to respond in a particular way to requests.
-
While more than one subnet can be bound simultaneously with a single Network Access Control List, only one subnet can be attached simultaneously with a single Network Access Control List.
-
A network access control list facilitates user identification. ACLs guarantee that authorized users and traffic can only access a system.
-
Compared to alternative technologies that serve the same purpose, Network Access Control Lists provide performance benefits. Access control lists don't affect routing device performance since they are configured directly on the forwarding hardware of the device. In contrast, a stateful inspection firewall is a different piece of software that could result in performance reduction. Additionally, managing network traffic makes networks more effective.
-
Network Access Control Lists can give network managers more granular control over user and traffic permissions at various network nodes. They assist in regulating traffic moving between internal networks and access to network endpoints.
Network Access Control List Basics
The following are the fundamentals of network ACLs that you should be aware of:
-
A customizable default network ACL is automatically included with your VPC. It permits all incoming and outgoing IPv4 traffic by default and IPv6 traffic if necessary.
-
A custom network ACL can be built and paired with a subnet. Each custom network ACL blocks all incoming and outgoing traffic by default until you add rules.
-
A network ACL has to be connected to each subnet in your VPC. A subnet is automatically linked to the default network ACL if you don't specifically link it to another network ACL.
-
A network ACL can be connected to several subnets. A subnet, however, may only be connected to one network ACL at once. The prior association is eliminated when you link a network ACL to a subnet.
-
Network ACL includes both incoming(inbound) and outgoing(outbound) rules. Any rule has the authority to allow or prohibit traffic. Each rule is assigned a number between 1 and 32766. We analyze the regulations in order, beginning with the rule with the lowest number while deciding whether to authorize or prohibit transportation. If the traffic follows a rule, the rule is applied, and no more rules are considered. To make it easy to add more rules later, we recommend beginning by creating rules in increments (for instance, increments of 10 or 100).
-
Rather than looking at how traffic is routed within a subnet, we assess the network ACL rules when traffic enters and exits the subnet.
-
Network ACLs are stateless; therefore, replies to permitted inbound traffic must adhere to the outgoing traffic rules (and vice versa).
-
Both the number of rules per network ACL and the number of network ACLs per VPC have limitations (also known as limits).
Network Access Control List Rules
The default network ACL can add or remove additional rules, and new network ACLs can be made for your VPC. Changes you make to a network ACL's ruleset are immediately reflected in all connected subnets.
The components of a network ACL rule are as follows:
-
The Rule Number: The rule with the lowest number is examined first. Any higher-numbered rule that might conflict with a rule that matches traffic is ignored.
-
Type: The nature of the transmission, like SSH. Additionally, you may pick a specific range or all traffic.
-
Procedure: Any protocol that has a standard protocol number can be specified. Go to Protocol Numbers for further details. You can choose any or all of the ICMP types and codes if you choose ICMP as the protocol.
-
Port selection: The traffic's listening port or set of ports. 80, for HTTP traffic, as an example.
-
Source: The traffic's origin (CIDR range) in the inbound block.
-
Destination: The traffic's final destination (CIDR range) in the outbound block.
-
Accept/Deny: Whether to allow (or) block the requested traffic.
The CIDR range is immediately changed to its canonical form when a rule is added through a command-line tool or the Amazon EC2 API. For instance, if you provide the CIDR range 100.68.0.18/18, we will construct a rule with the CIDR range 100.68.0.0/18.
Default Network Access Control List
The default network ACL is set to allow all traffic into and out of the subnets to which it is assigned. Each network ACL additionally includes a rule with an asterisk as the rule number. This rule ensures that a packet is refused if it does not match any of the other numbered rules, provided "DENY" is declared for the asterisk rule. To explain above mentioned points an example is included below which will clear your understanding further.
The following is an example default network ACL for an IPv4-only VPC.
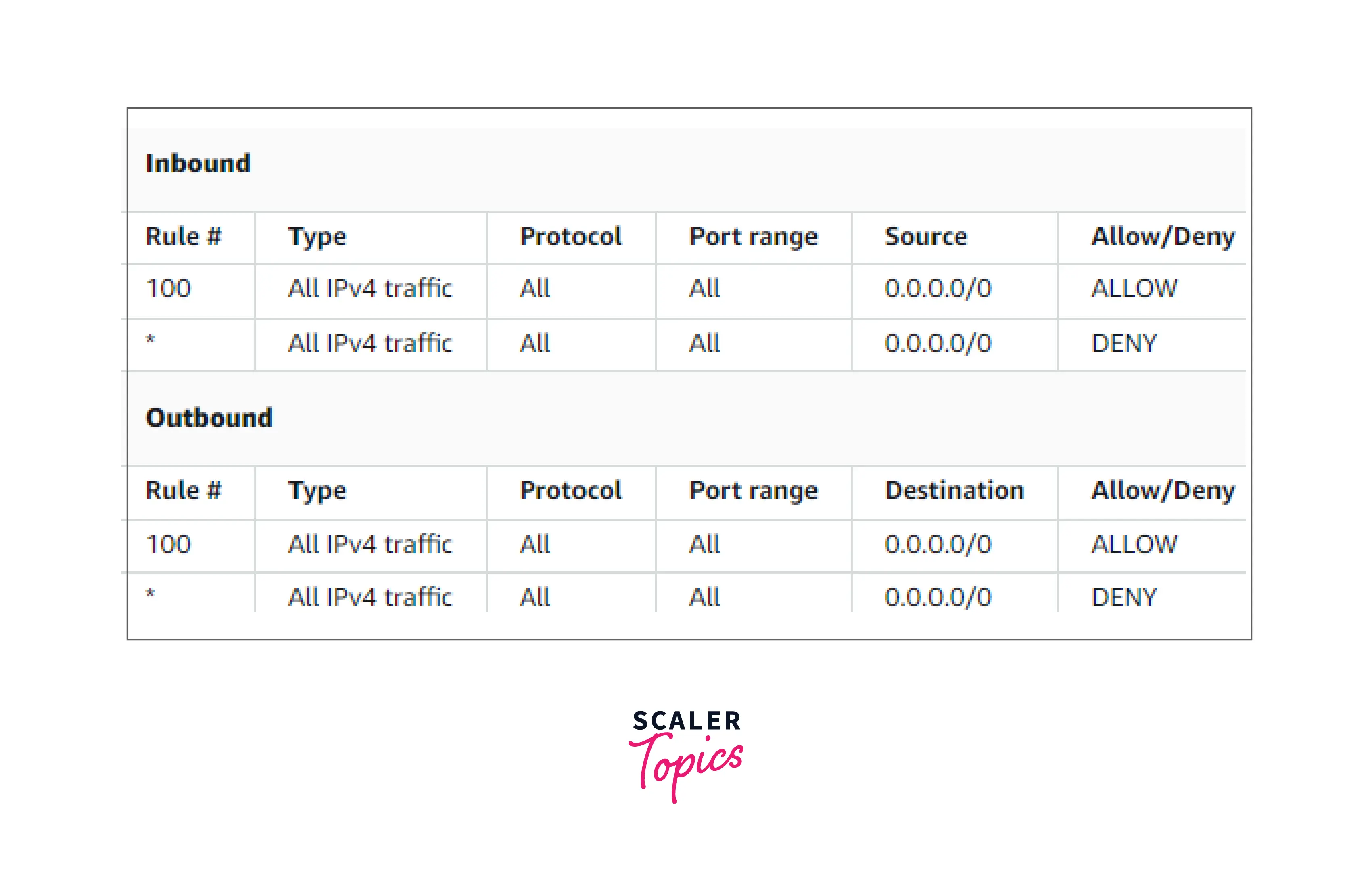
For example, suppose we are having packet having the rule number 150 for the below inbound block, then that packet will be searched if it can be sent to the network or not, and the comparison will be done with each Rule# (as shown above).
Firstly comparison with rule number 100 happens, if it does not match, parse the next rule. In the example above we reach the * rule eventually and here this rule rejects the packet since it doesn't fit any of the rules and there is a "DENY" specified in Allow/Deny column.
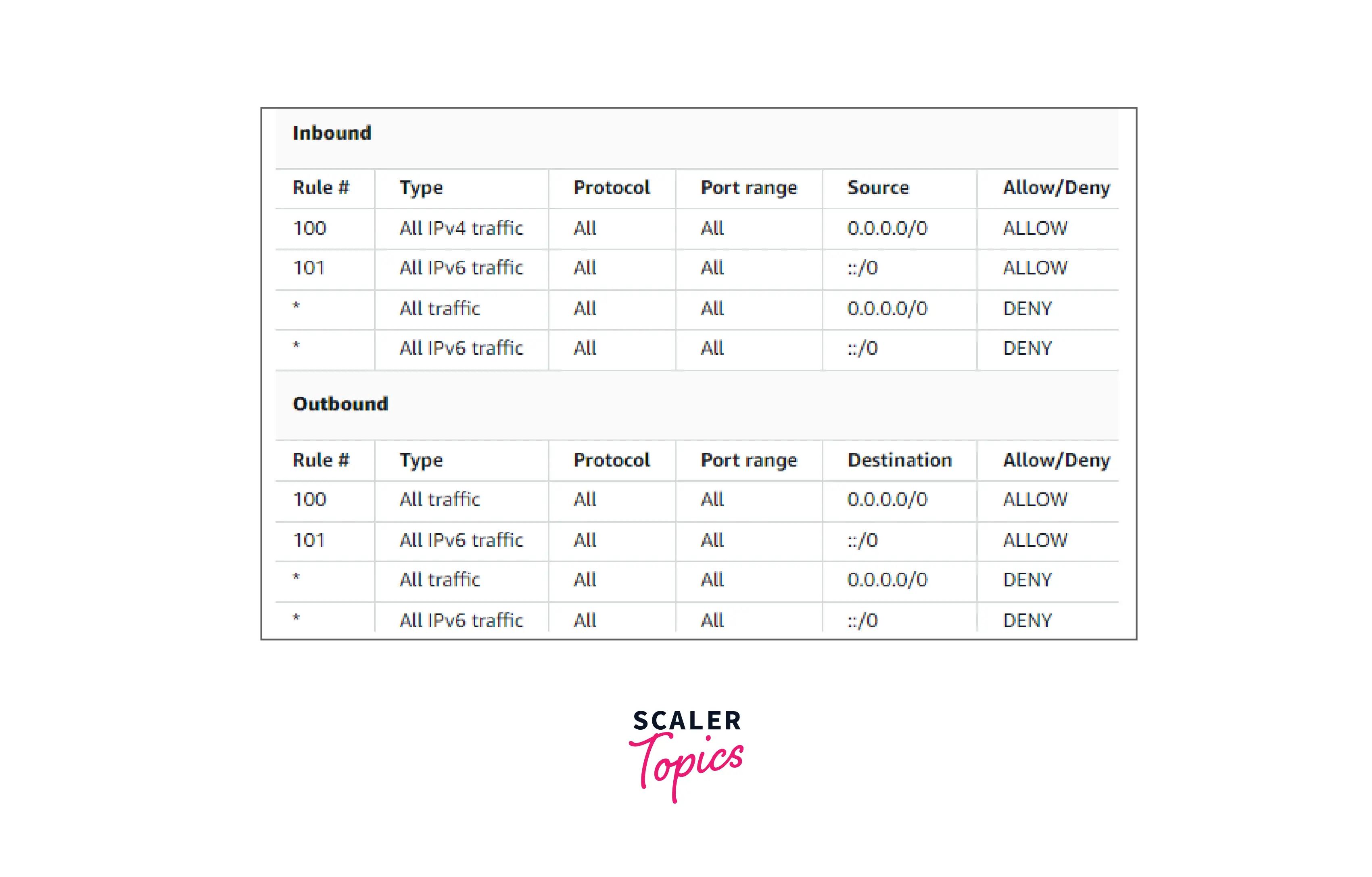
When you construct a VPC with an IPv6 CIDR block or associate an IPv6 CIDR block with an existing VPC, we add rules that allow all IPv6 traffic to flow into and out of your subnet. We also add rules with asterisk rule numbers, which ensure that a packet is denied if it does not fit any of the other numbered rules by specifying a "DENY". These regulations cannot be changed or removed.
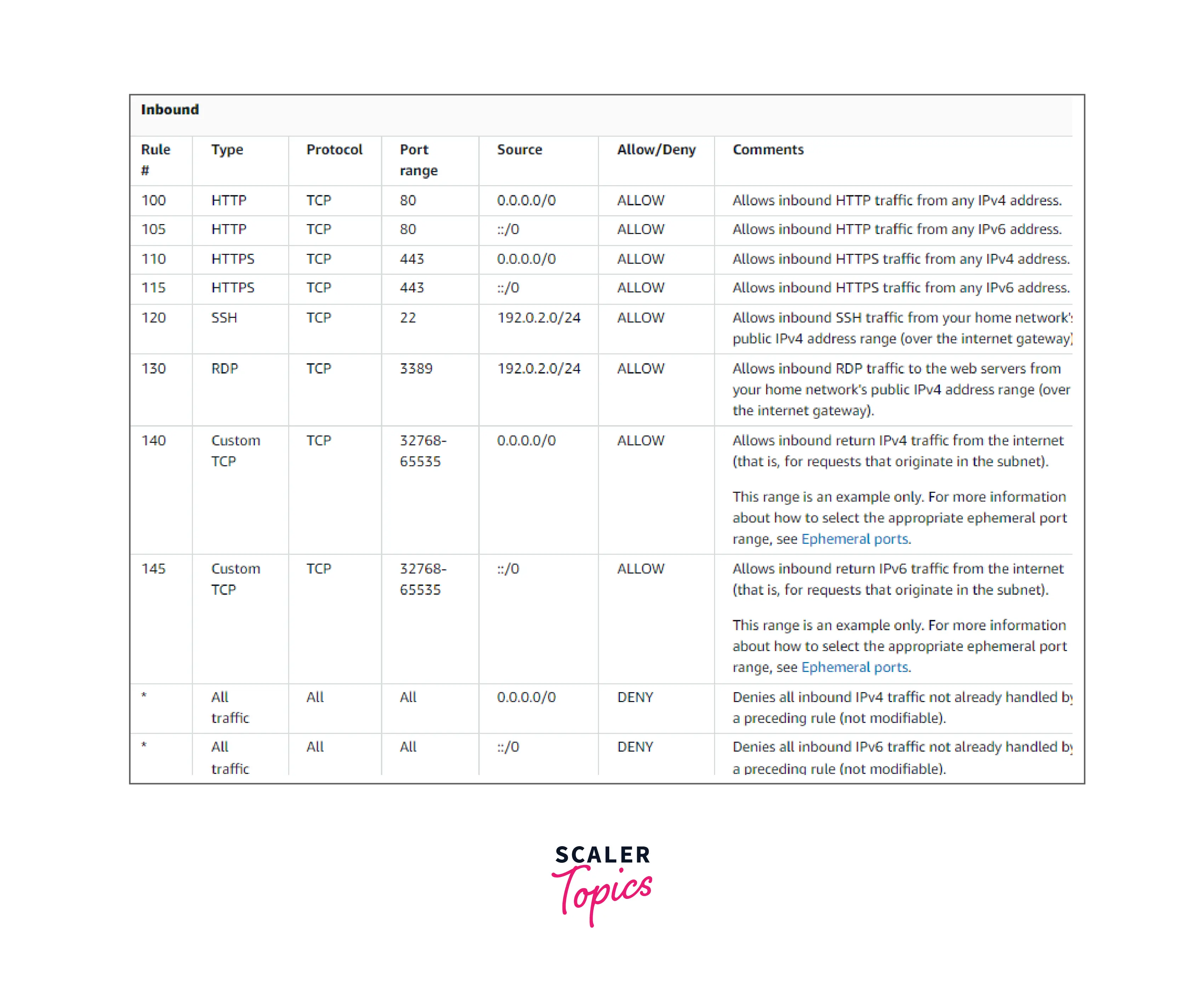
Custom Network Access Control List
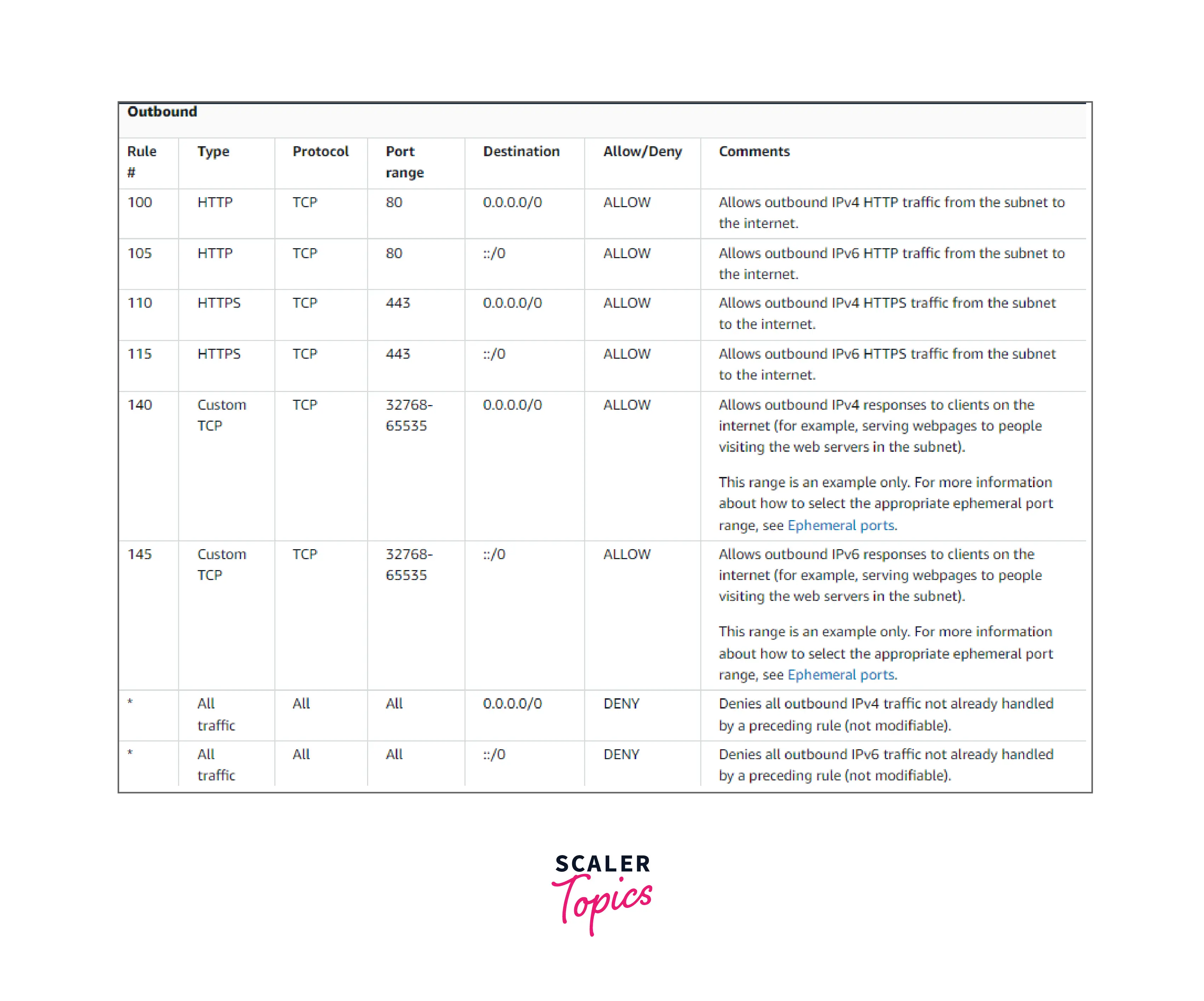
A sample custom network ACL for a VPC that only supports IPv4 is shown in the following table. It has guidelines that permit HTTP and HTTPS transmission (inbound rules 100 and 110). An associated outbound rule allows replies to that inbound traffic (outbound rule 140, which covers ephemeral ports 32768-65535). See Ephemeral ports for further details on choosing the suitable ephemeral port range.
Additionally, the network ACL has inbound rules that let RDP and SSH traffic into the subnet. Responses are allowed to depart the subnet thanks to the outbound rule 120.
Outbound rules (100 and 110) in the network ACL let HTTP and HTTPS traffic leave the subnet. An equivalent incoming rule allows replies to that outgoing traffic (inbound rule 140, which covers ephemeral ports 32768-65535).
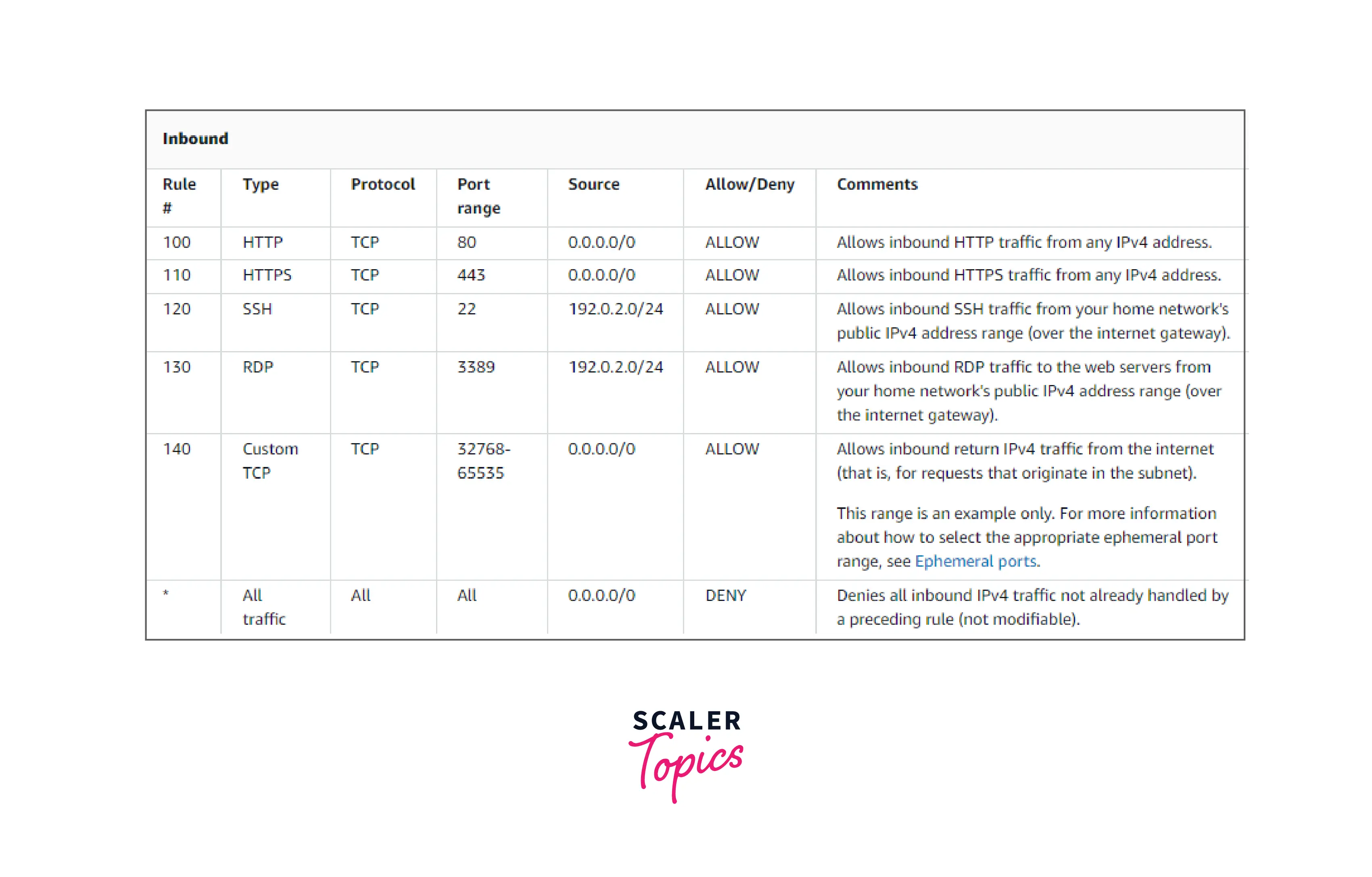
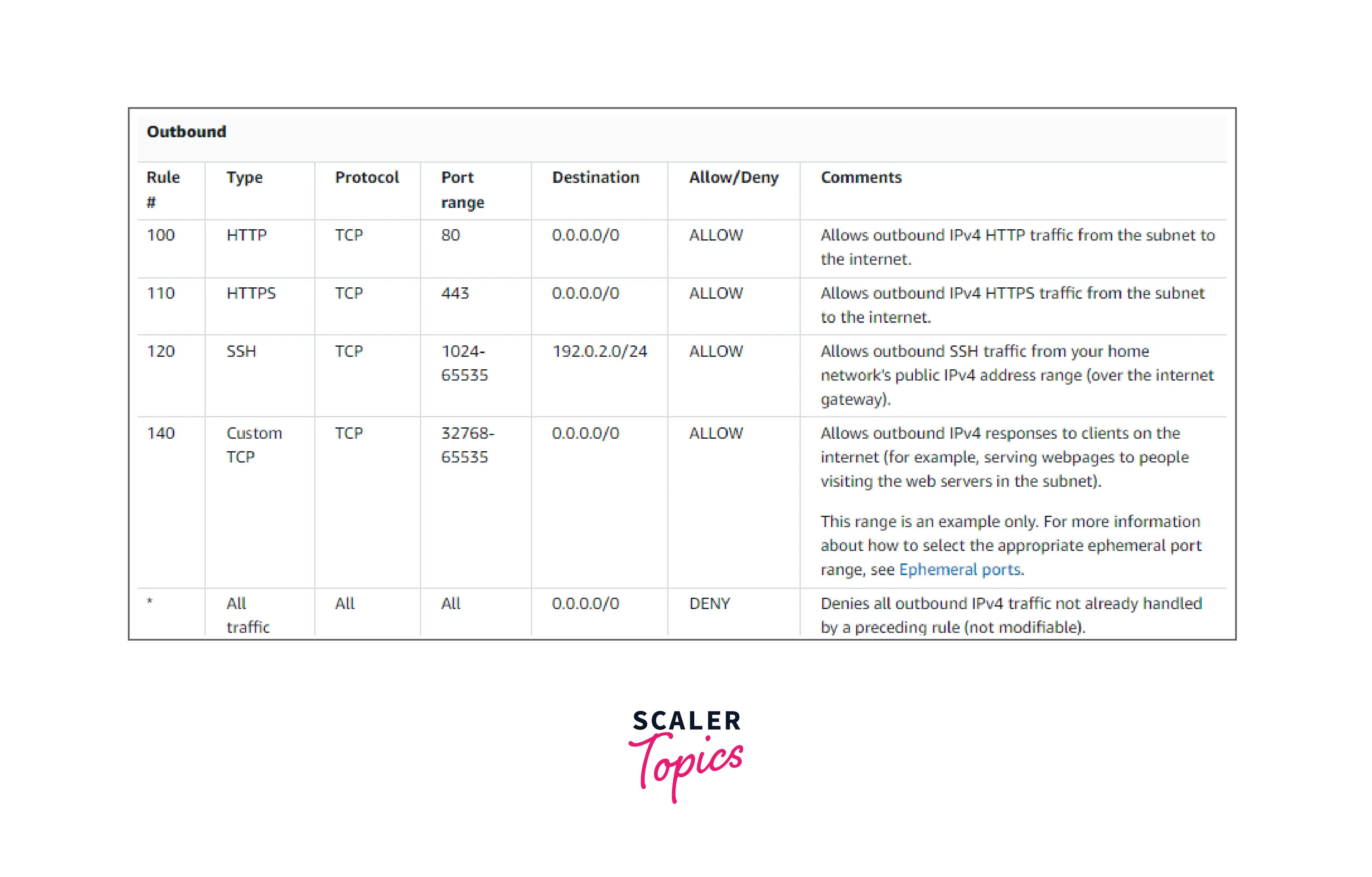
As a packet enters the subnet, we assess it using the inbound ACL rules that the subnet is connected to (starting at the top of the list of rules and moving to the bottom). The assessment proceeds if the packet is intended for the HTTPS port (443). The package does not comply with the initial rule examined rule 100. The packet can enter the subnet since it matches the second rule 110.
The * rule eventually rejects the packet after comparison with all rules since "DENY" is specified in Allow/Deny column and was intended for port 139, which doesn't match any of the rules.
If you need to open a lot of ports but also want to deny some of the ports in the range, you might want to add a deny rule. Just be sure to position the deny rule before the rule that permits a variety of port traffic in the table.
Your use case determines whether you add allow rules. For DNS resolution, you may add a rule that permits outbound TCP and UDP access on port 53. Make sure there is a corresponding incoming or outbound rule that allows response traffic for each rule you create.
An identical example of a custom network ACL for a VPC with an associated IPv6 CIDR block is shown in the following table. Rules for all IPv6 HTTP and HTTPS traffic are included in this network ACL. In this instance, additional rules were put between the IPv4 traffic rules already in place. After the IPv4 rules, you may also add the rules as higher number rules. Since IPv4 and IPv6 traffic is distinct from one another, none of the IPv4 traffic regulations apply to IPv6 traffic.
Be mindful of how resources you generate using other AWS services may be impacted if you build a custom network ACL.
Your load balancer won't be able to do health checks on the instances if the subnet for your backend instances has a network ACL with a deny rule applied for all traffic with a source of either 0.0.0.0/0 or the subnet's CIDR.
Difference between Security Groups and NACL (Network Access Control List)
-
Scope: Network ACLs are linked to the subnet, whereas security groups are linked to an instance. Because network ACLs are applicable at the subnet level, each instance in the subnet that has a related Network Access Control List will abide by its restrictions. Security groups are an exception to this rule; security groups must be expressly allocated to an instance. This indicates that the rule is applied to all instances inside the subnet group. You have to manually assign a security group to the instances when using the Security group.
-
State: Security groups are stateful. This means that any modifications made to an incoming rule will be reflected in the outgoing rule. For example, if you accept an entering port 80, the outbound port 80 will be opened immediately. Network ACLs are stateless. This means that any changes made to an incoming rule will not be carried over to the outgoing rule. For example, if you accept incoming traffic on port 80, and want to have outbound traffic from port 80 as well, then you have to apply the rule manually in the outbound rules.
-
Rules; Security group only accepts allowed rules (by default, all rules are denied). You cannot, for instance, prevent a specific IP address from creating a connection. Allow and deny rules are supported by Network ACL. You might forbid a specific IP address from establishing a connection using refuse rules. Disallow connections from IP address 123.201.57.39 to EC2 Instances.
-
Rule process order: Specifically, security groups assess all of its rules before permitting traffic, whereas NACLs evaluate them in numerical order, from top to bottom.
-
Defense order: For inbound/ingress traffic, Network ACL serves as the primary layer of security while Security groups serve as the second layer of security. Security group serves as the first line of security, while Network ACL is the second line of protection for outgoing traffic.
-
Rule Destination: CIDR, IP, and security group destinations are permitted under security group rules. Only CIDR is permitted as a destination under network ACL rules.
Conclusion
-
The VPC already has the default Network Access Control List for IPv4 traffic. It is possible to create a custom Network Access Control List and attach it to a subnet. The modified Network Access Control List's default configuration is to ban all incoming and outgoing IPv4 traffic.
-
In numerical sequence from top to bottom, in Network Access Control Lists, security groups evaluate each rule in their system before permitting traffic.
-
Each instance in the subnet that has a relevant Network Access Control List will abide by its constraints. Network ACLs are applied at the subnet level.
-
Multiple subnets can be linked to a network ACL. However, a subnet can only be concurrently linked to one network ACL. When you associate a Network ACL with a subnet, the previous association is removed.
-
Network ACLs are stateless. This means that any changes made to an incoming rule will not be carried over to the outgoing rule. For example, if you accept incoming traffic on port 80, and want to have outbound traffic from port 80 as well, then you have to apply the rule manually in the outbound rules.
