AWS VPC Endpoint
Overview
AWS introduced VPC Endpoints in 2015. VPC endpoints are the features associated with the AWS VPC services. Before AWS VPC endpoints, all traffic between AWS resources was routed through the public internet. This main problem is solved by VPC endpoints. VPC endpoints help customers route traffic between AWS resources such as EC2, ECS, EKS, lambda, etc., and AWS services such as S3, DynamoDB, API Gateway, SQS, etc. within the VPC region. It is a private connection powered by AWS PrivateLink.
Introduction to VPC Endpoint
Before learning about the VPC endpoints, we should know two things.
What is VPC?
VPC stands for Virtual Private Cloud.
- AWS VPC provides virtual data centres as a service to all customers.
- A single VPC contains all the necessary components required to build the data centre. In reality, it is a data centre but resides in some other location. The maintenance and availability of the data centre will be taken care of by AWS. As a customer, we should pay only for the resources we are using or provisioning.
- The basic components of VPC include Subnet, Internet Gateway, Nat Gateway, and Route table.
- AWS resources such as EC2, RDS, ECS, and EKS will be provisioned using those networking components of the VPC.
VPC is the regional service.
What is an Endpoint?
- Endpoints are end devices that act as entry points to the networking layer.
Now, coming back to AWS VPC Endpoints
Customers can use AWS VPC endpoints to route resource traffic between AWS resources and AWS Services within their VPC rather than out to the internet. Let me explain with an example.
Imagine the below scenario:
Customers have one EC2 instance and one S3 bucket. Both the Ec2 instance and S3 bucket reside in the ap-south-1 region (Mumbai ) region.
If customers request something like GetObject or ListObject from the EC2 instance CLI to the S3 bucket,
The traffic flow will be:
EC2 instance --> AWS VPC --> Public Internet --> AWS Service
If we enabled the VPC endpoints for the Service S3, then the traffic flow will be
EC2 Instance--> AWS VPC--> AWS VPC Endpoint --> AWS Service
Thus, a private connection is established between the EC2 and S3 using the AWS VPC Endpoint.
Types of VPC Endpoints (in detail)
In AWS, there are three types of VPC endpoints. They are
- Gateway Endpoints
- Interface Endpoints (Private Link)
- GWLB Endpoints (Gateway Load Balancer)
Interface Endpoints
- Customers can use VPC Interface endpoints to connect to over 130 AWS Services and over 1300 AWS third-party partners who also provide connectivity services.
- Interface endpoints are built on this technology, called PrivateLink.
- Interface endpoints are associated with the availability zone.
Gateway Endpoints
- It is only used for accessing the DynamoDB and S3 services.
- In this endpoint, we can mention the users or roles of an IAM.
- Those IAM entities can access the S3 and DynamoDB resources using the VPC endpoint link.
Gateway Load Balancer Endpoints
- Customers can deploy virtual appliances as Gateway Load Balancer endpoints in the network layer. Here, the network layer refers to the AWS VPC.
- The virtual appliance will act as a firewall, intrusion detection system, or traffic filter for the entire VPC.
S3 VPC Endpoints Strategy
The S3 service will be supported by both interface and gateway endpoints. However, knowing when to use interface endpoints and gateway points plays an important role in a well-architected framework.
When Should We Use Interface Endpoints?
If the customer focuses on any one of the following, they can proceed with interface endpoints for S3.
Access Pattern:
Customers can choose interface endpoints that provide a private connection between the customer application and the AWS S3 bucket if the application is deployed in EC2, ECS, or EKS.
VPC Endpoint Architecture:
Large-scale applications and multiple VPC architectures should consider using VPC endpoints to protect the network layer from exposure to the public internet.
Since VPC endpoints integrated with a VPN connection will support multi-regions, customers should consider VPC endpoints for complex architectures.
Bandwidth Consideration:
Data transfer between the EC2 resource and S3 depends on the instance's bandwidth. Usually, interface endpoints are configured with 10 GBps. If the traffic exceeds this limit, the interface endpoints will scale automatically to meet the demand.
Since bandwidth is high, customers can expect low latency when compared to the public internet connection.
When Should We Use Gateway Endpoints?
Gateway endpoints are provided at no cost, but interface endpoint costs are based on an hourly basis. If the customer's application mainly uses the AWS S3 service for most of the application requests and the data is not sensitive, then the customer should consider using gateway endpoints.
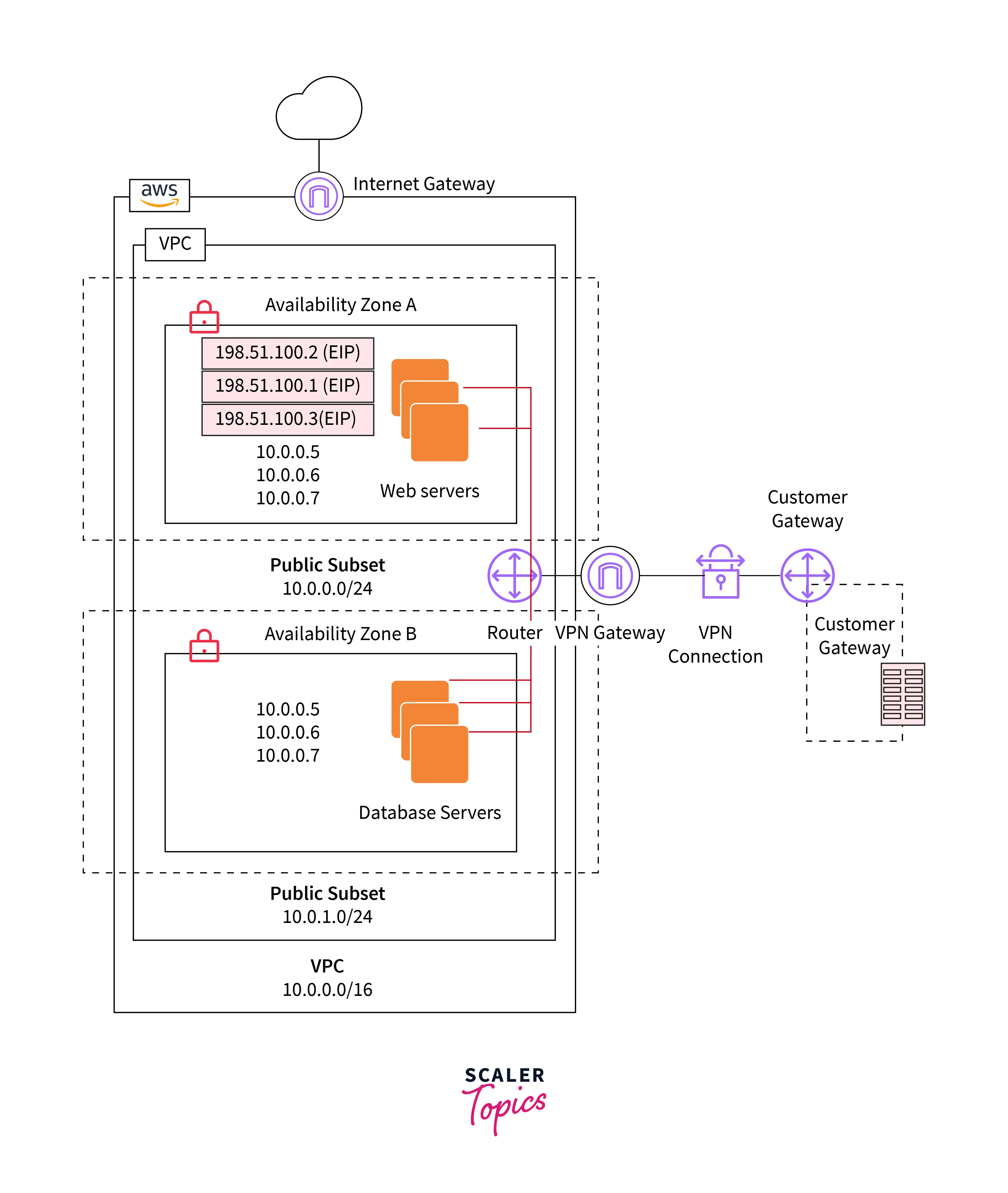
Architecture of VPC
Essentially, every VPC includes four components:
- Subnet
- Route Table
- Internet Gateway
- NAT Gateway
The subnet will be classified into two types:
Public Subnet:
- If the subnet route table is associated with the internet gateway, then the subnet is known as the public subnet
Private Subnet:
- If the subnet route table is associated with a NAT gateway, then the subnet is known as a private subnet.
Route Table:
The route table consists of the route list associated with the subnet.
VPC Endpoints:
- VPC endpoints reside within the region. But the interface VPC endpoint will be created in every availability zone chosen by the customer while creating
- If the customer selects two subnets in the same availability zone, then interface VPC endpoints will be created in two availability zones.
- The security group is also associated with VPC endpoints for an extra layer of security to restrict access at the VPC endpoint level.
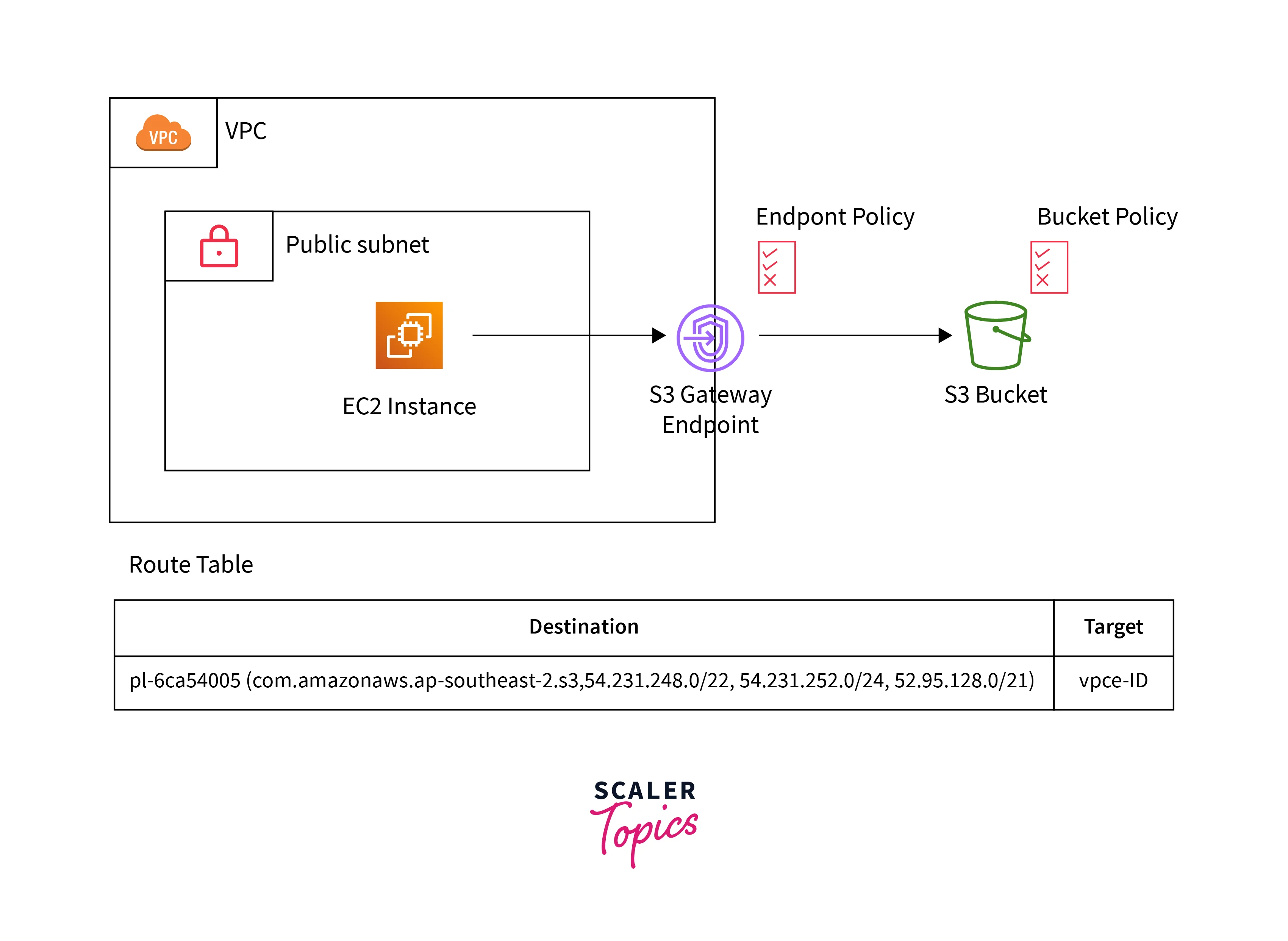
With VPC Endpoints
- As you can see in the below image, the traffic or HTTPS request initiated from the EC2 instance will reach the S3 Gateway VPC endpoint. Then it will route the traffic or request to the S3 bucket, and vice versa.
The private connection between the AWS resources and AWS services has been established.
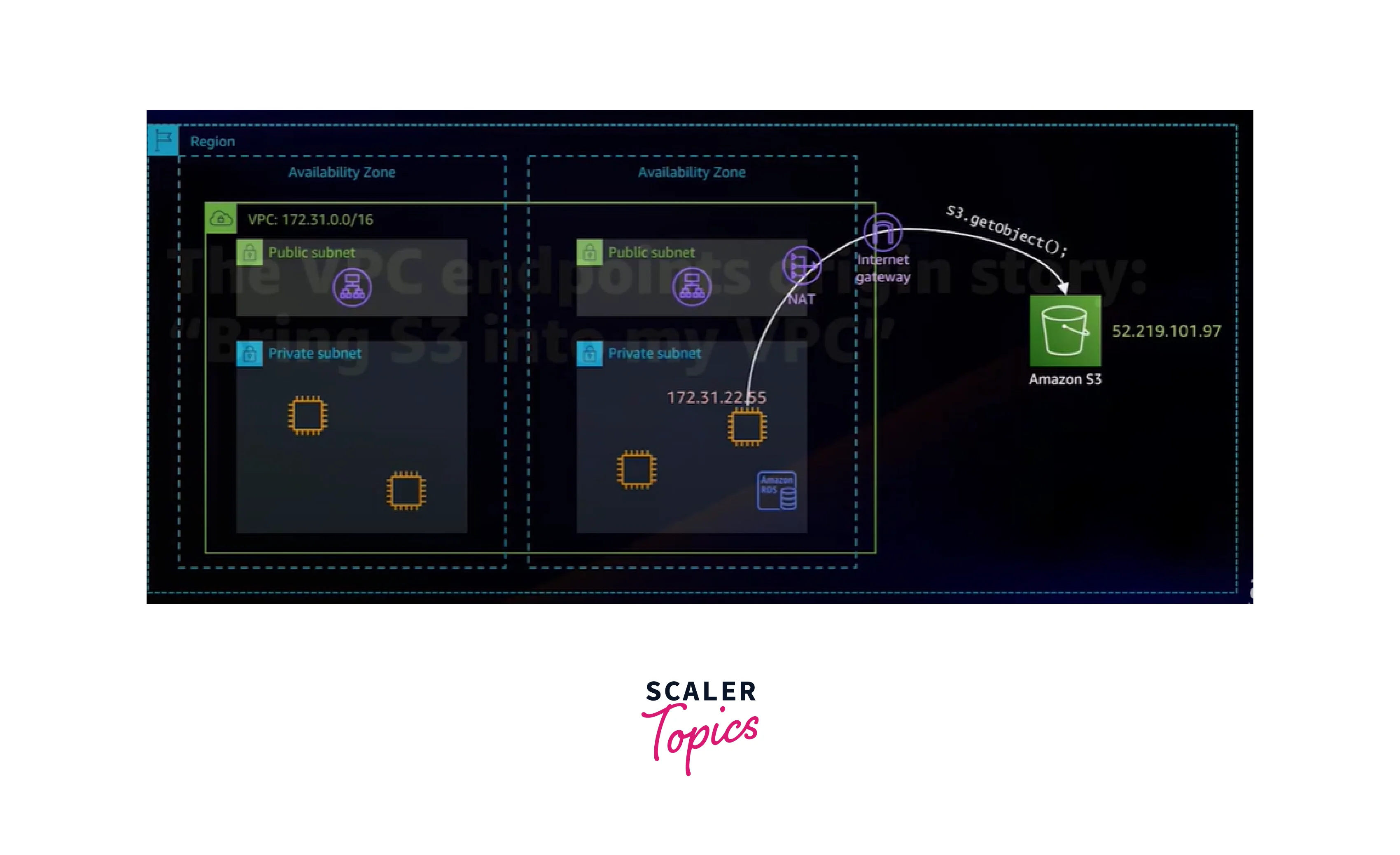
Without VPC Endpoints
- In this image, the VPC endpoint components are not there. So when the request is initiated from the EC2 instance, it will route through the public internet and then reach the AWS Services.
Benefits and Limitations of VPC Endpoints
- AWS VPC endpoints are one of the features associated with the AWS VPC. It is generally available for all AWS customers across the world.
- AWS VPC endpoints come with an endpoint policy. It is an identity access management resource policy that does not override a user-based policy or service-specific policy like the S3 bucket policy.
- It is a separate policy on the endpoint itself to control access to the AWS services via these endpoints. Here, the traffic will route between AWS resources and services.
- Enabling VPC endpoints helps customers reduce latency between AWS resources and services.
- The pricing of AWS VPC endpoints is very low. In other words, a single VPC endpoint will cost an average of $10 per month.
- VPC endpoints also act as one of the security layers for the customer infrastructure.
- VPC endpoints between the regions are not directly possible. To achieve that, we need to provision a VPC peering connection between two VPCs in different regions.
- We need to rely on AWS since there are no tools provided by AWS for internal troubleshooting between the VPC and VPC endpoints generally.
How to Create and Delete VPC Endpoint Registration?
Creation Of VPC Endpoint:
1. Go to the AWS VPC Console and select Endpoints in the left navigation pane. Then select the Create Endpoint button.
2. Enter the below name: S3-endpoint and choose AWS Service as the service category.
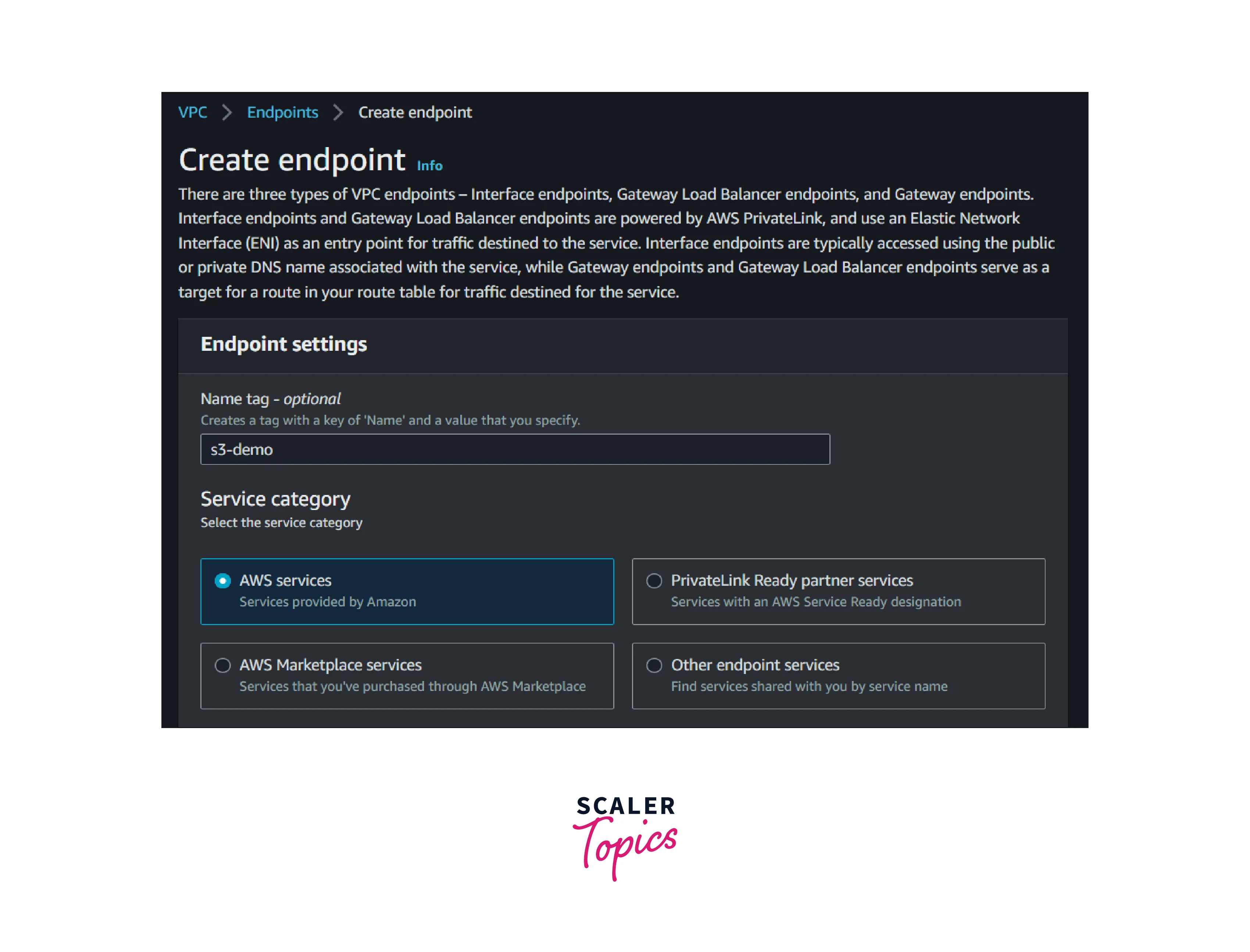
3. Select the service type as S3 and choose the interface endpoints.
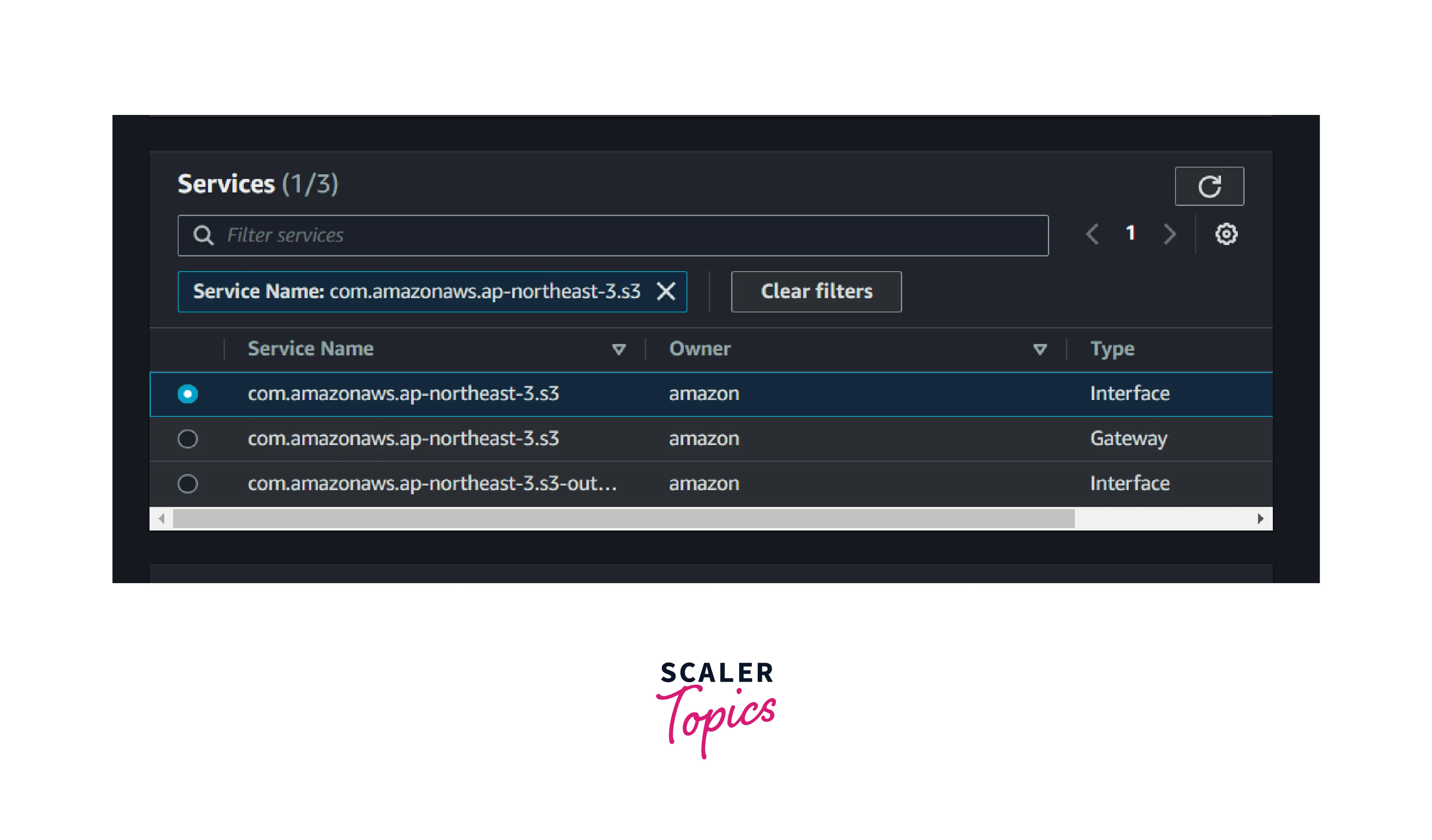
4. Select the desired VPC and subnets.
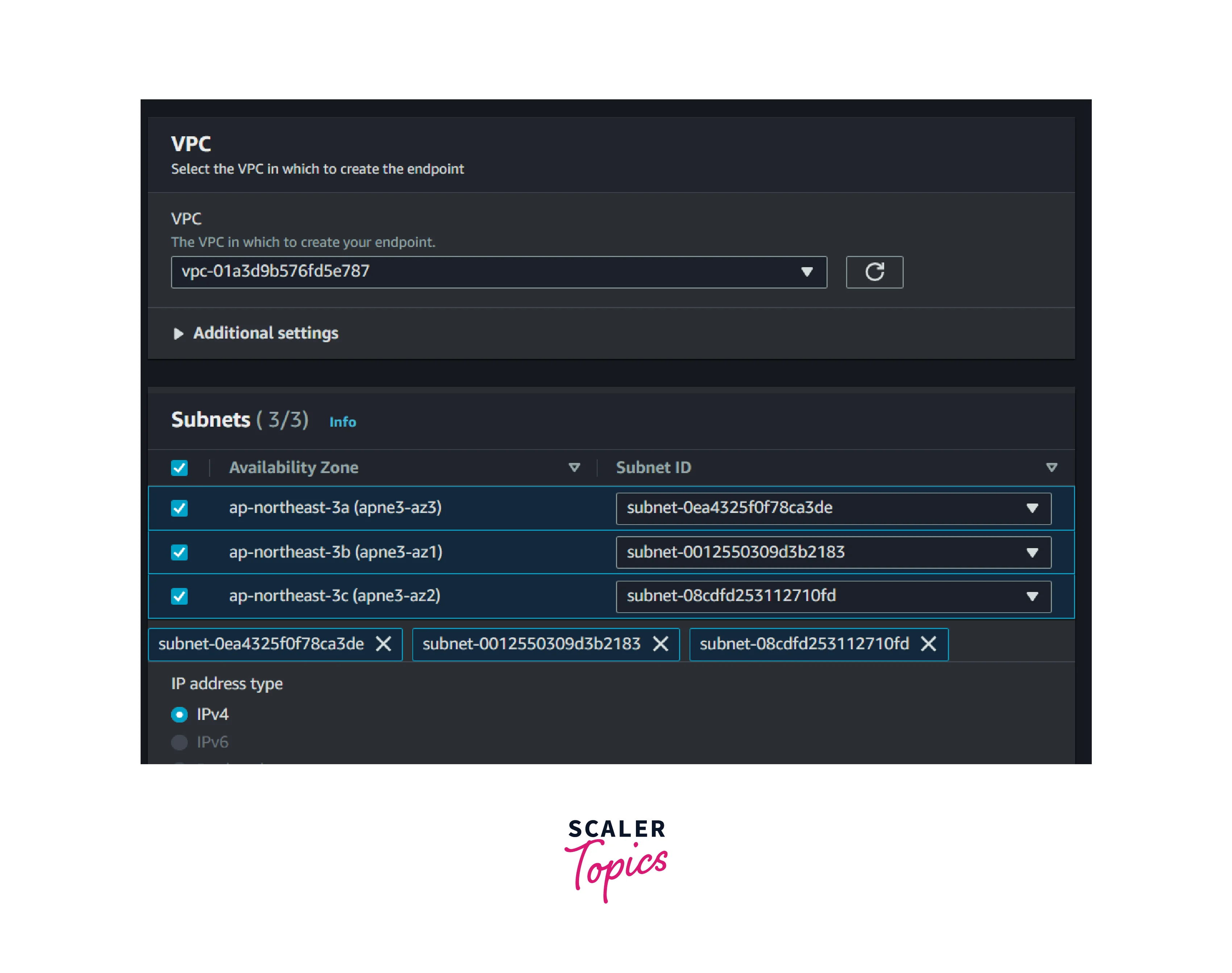
5. Select the Default security group and click Create Endpoints.we can also change the security group rules after the creation if required.
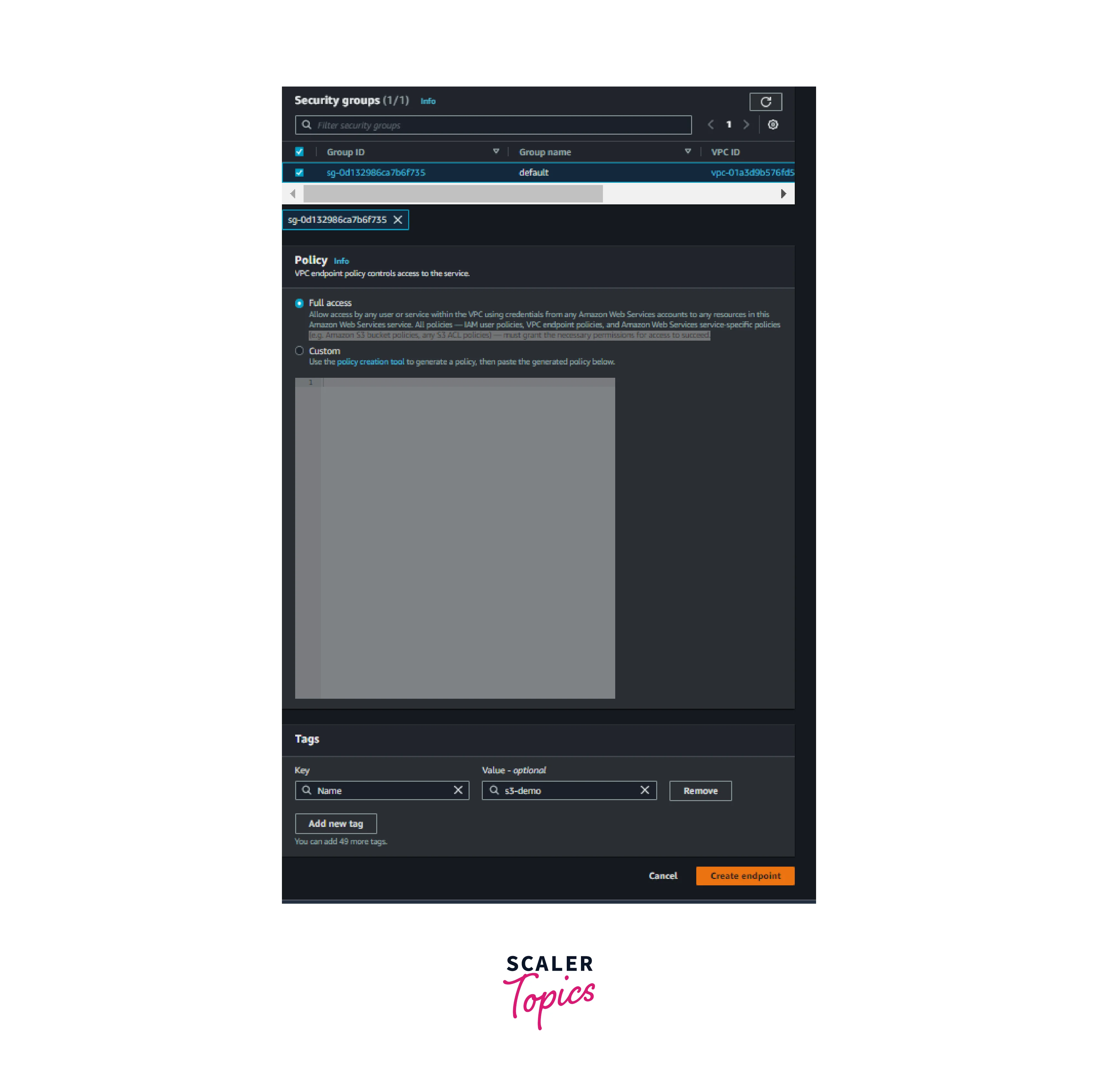
Note: Interface endpoints are subject to the availability zone.
It will take some minutes for it to become provisioned and available.
After a few minutes, the AWS Interface VPC endpoints for S3 are available for use.
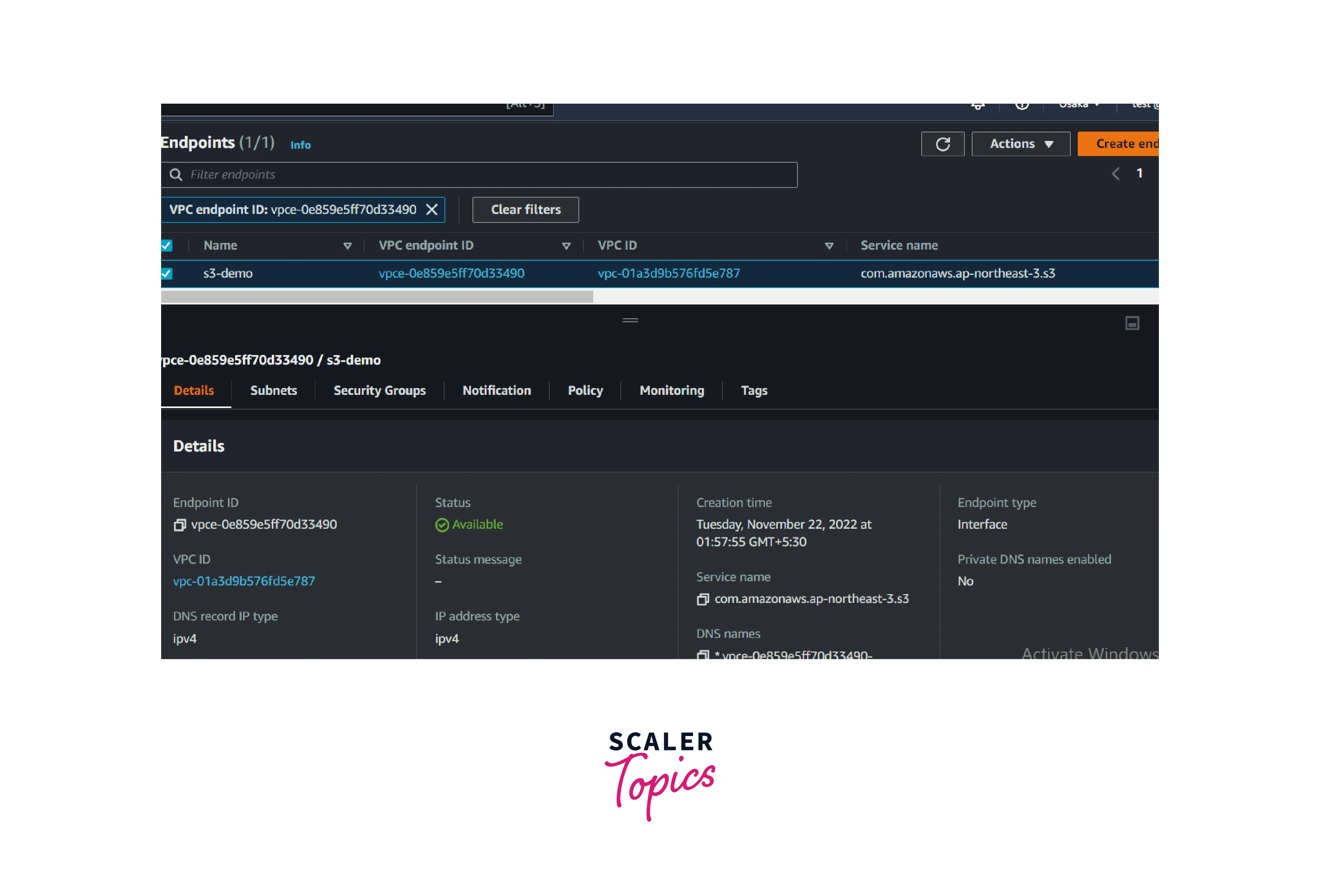
Deletion Of VPC Endpoint:
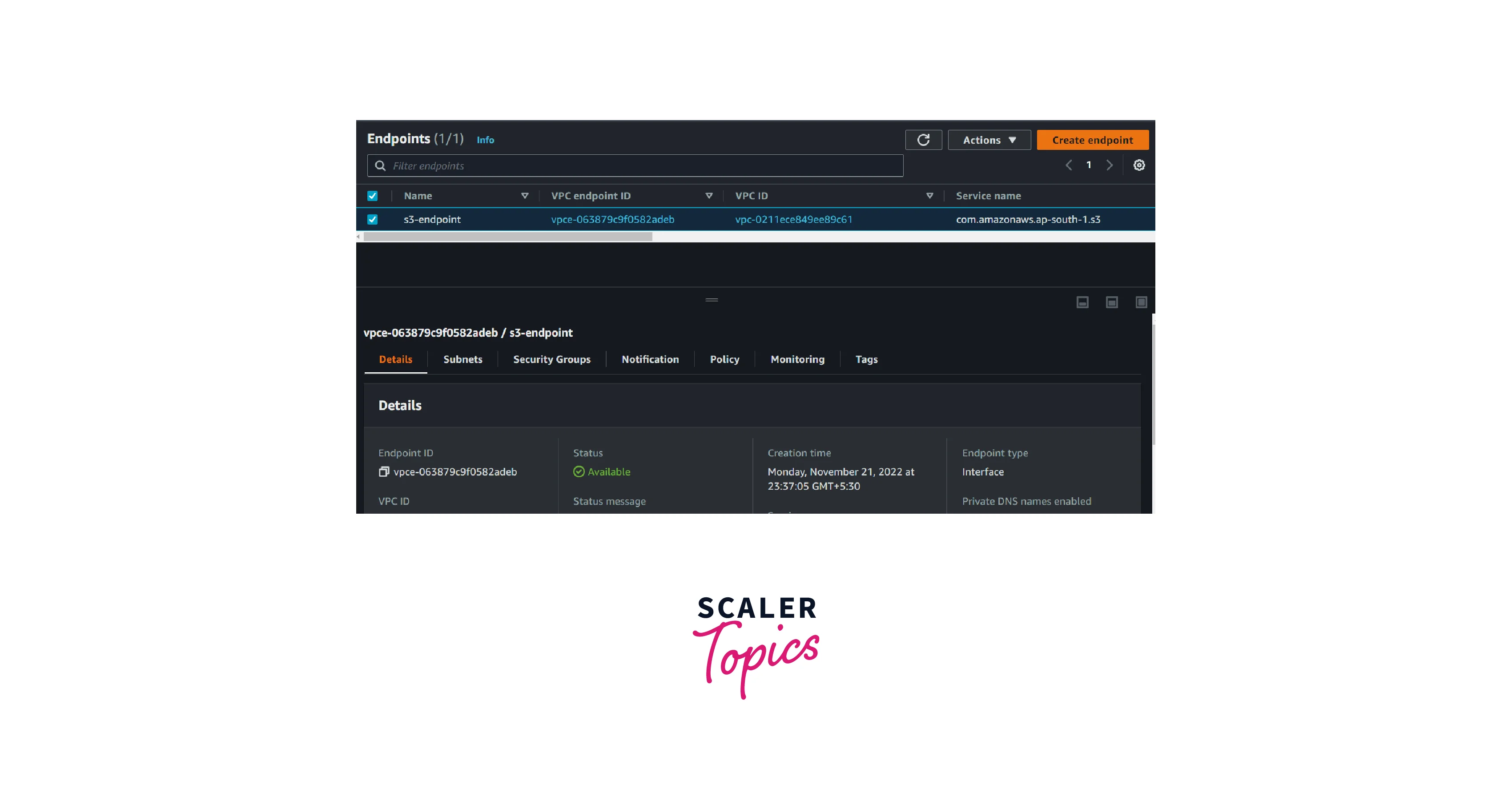
- Go to the AWS VPC Console and select the endpoint in the left navigation pane. Then Select the VPC endpoint that you want to delete and click Action.
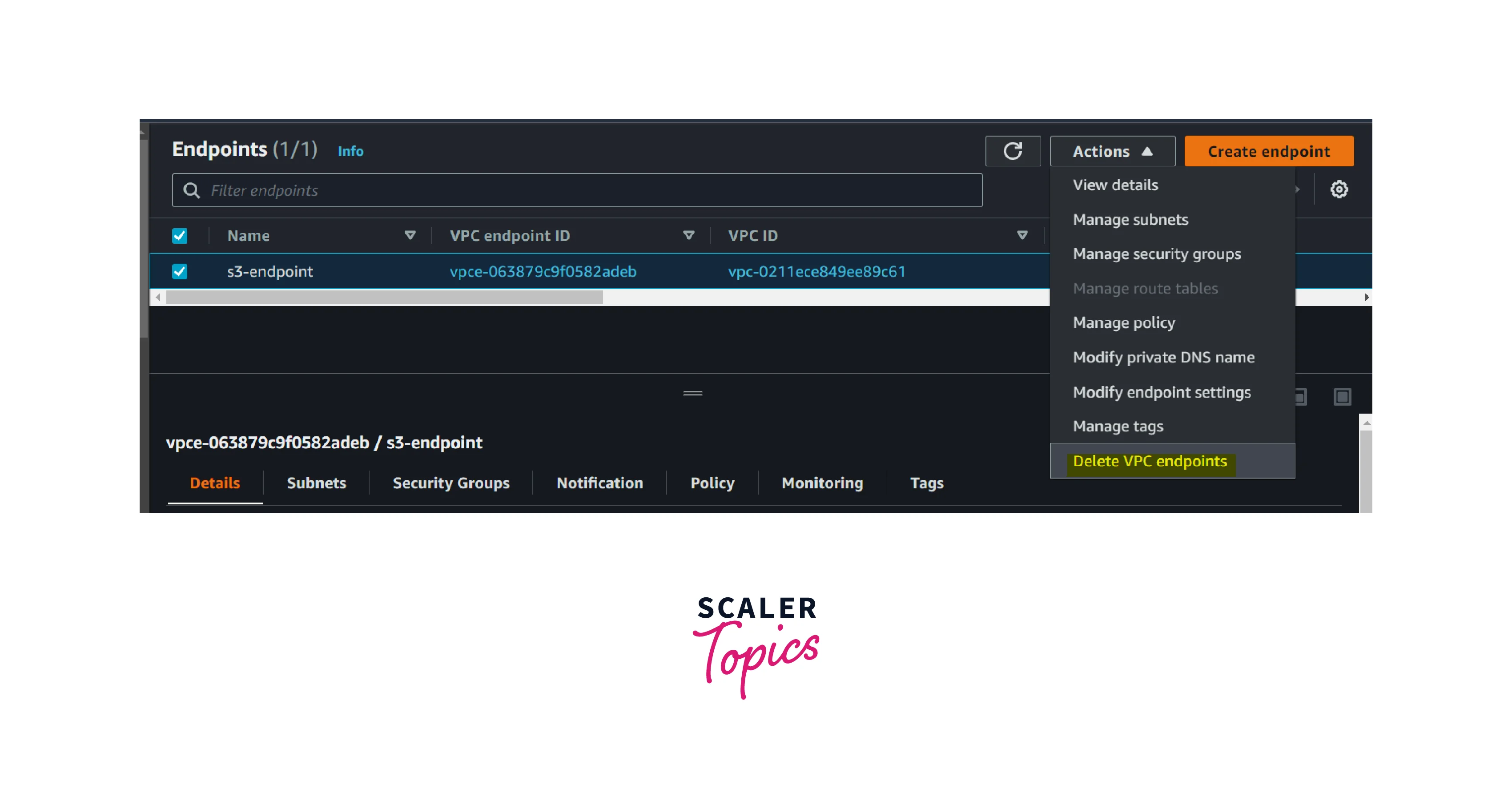
- Click the Delete VPC endpoints button to delete the AWS VPC endpoint.
VPC Endpoints vs VPC Peering Connections
| AWS VPC Endpoint | AWS VPC Peering |
|---|---|
| It provides a connection between AWS Resource and AWS Services | It establishes communication between AWS VPC in the same region |
| Dedicated connection towards VPC endpoints from on-premises is possible through Direct Connect and Site to site VPN within a region. | It will be used as a fallback for the Direct Connect service |
| VPC Endpoints are horizontally scaled and managed by AWS | Virtual Private Gateway is managed by AWS where are customer Gateway’s end devices will be managed by the Customer's end |
| It applies to AWS Services | It applies to AWS VPC |
| The latency between the AWS resource and Service will be less | The latency between the AWS VPC and the customer data centre is based on internet bandwidth and customer end devices. |
Conclusion
- AWS VPC endpoints provide the private connection between AWS resources and AWS services within the VPC.
- AWS VPC Endpoints act as one of the security layers in the AWS Cloud infrastructure.
- AWS VPC endpoints are horizontally scaled and managed by AWS.
- There are three types of AWS VPC endpoints. Customers can opt for anyone based on their business use case.
- AWS VPC endpoints help customers reduce latency and security risks.
- Using VPC peering, customers can establish a connection between different VPCs and different VPC endpoints in the same region.
- Customers can leverage VPC endpoints to establish communication between the services deployed in AWS compute resources.
