Azure Network Security
Azure Network Security provides comprehensive protection for your cloud resources. It includes features like Azure Firewall, Network Security Groups, and Virtual Network Service Endpoints to control inbound and outbound traffic. It offers DDoS protection, threat intelligence, and VPN gateways for secure connectivity. Azure Security Center helps monitor and respond to threats. With a robust set of tools, it safeguards your virtual networks, applications, and data from cyber threats while ensuring compliance and seamless network connectivity.
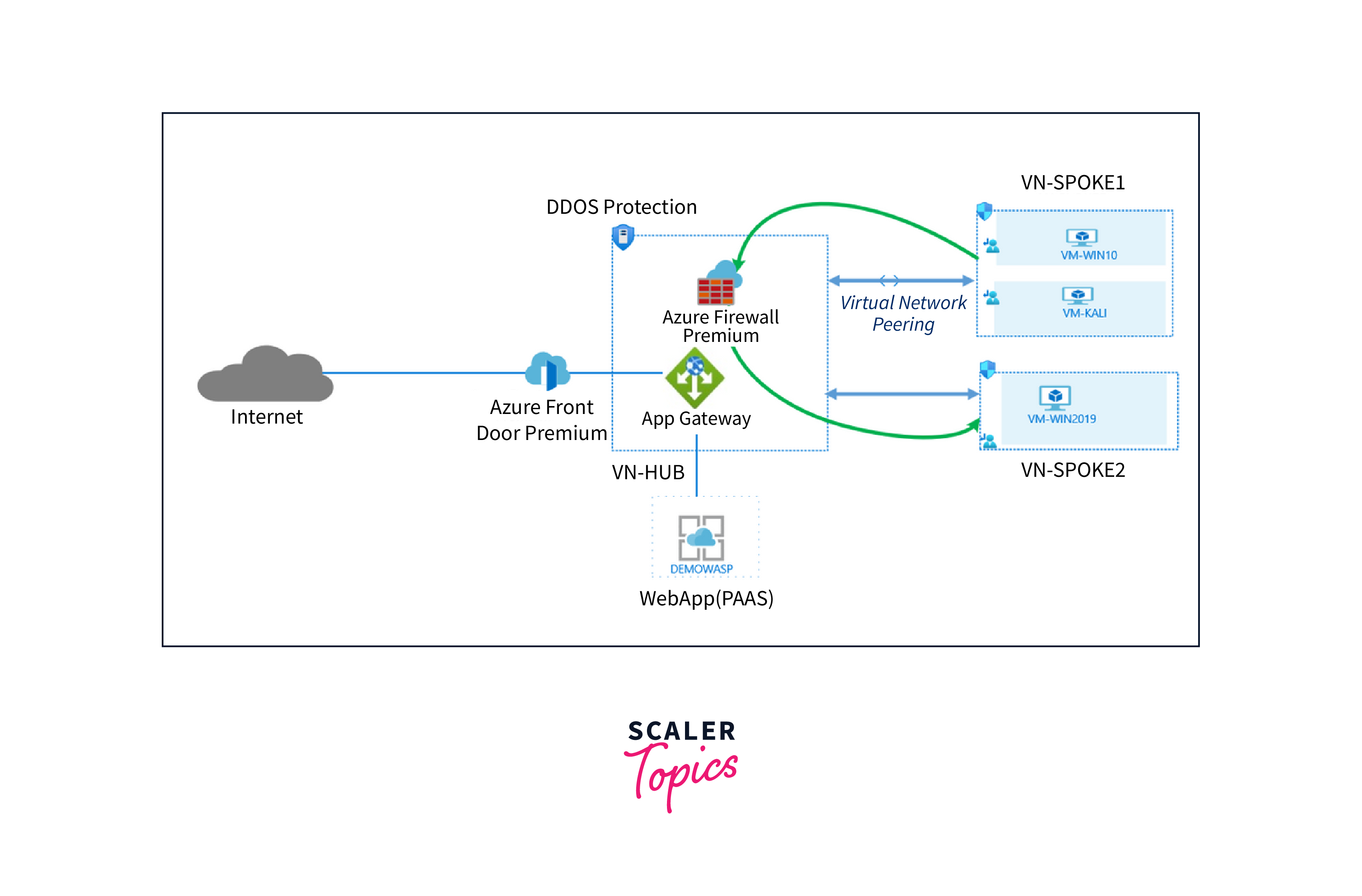
Azure Network Security is a crucial component of Microsoft's Azure cloud platform, designed to provide robust and comprehensive protection for your cloud-based resources. As organizations increasingly migrate their workloads to the cloud, security becomes paramount, and Azure Network Security offers a suite of tools and services to address these concerns.
Azure Network Security encompasses several key features, such as Azure Firewall, which acts as a perimeter security solution, controlling inbound and outbound traffic and providing high-level security for applications and data. Network Security Groups allow fine-grained control over network traffic and segmentation, ensuring only authorized communication occurs.
Azure Security Center complements these services by providing a centralized hub for monitoring, threat detection, and incident response, helping organizations maintain a strong security posture while ensuring regulatory compliance. Whether you're running virtual networks, applications, or databases, Azure Network Security empowers you to protect your digital assets in the Azure cloud environment.
Azure networking
Azure Networking is a critical component of Microsoft's Azure cloud platform, offering a suite of services and features to create, manage, and secure network infrastructure in the cloud. It plays a pivotal role in ensuring seamless connectivity, scalability, and robust security for cloud-based applications and services. Here's an in-depth overview of Azure Networking:
- Virtual Networks (VNets): Azure VNets are the cornerstone of network architecture. They provide a virtual representation of a network within Azure, allowing organizations to isolate their resources and control their IP address ranges, subnets, and network settings. VNets can be peered to create a unified network or connected to on-premises networks through VPN or Azure ExpressRoute.
- Azure Firewall: Azure Firewall is a fully managed, cloud-native firewall service that safeguards applications and data by controlling both inbound and outbound traffic. It offers features like network and application layer filtering, threat intelligence, and support for high availability.
- Network Security Groups (NSGs): NSGs are stateful, rules-based firewalls that help control network traffic within VNets or subnets. You can define rules to allow or deny specific traffic based on source, destination, and service, ensuring network security.
- Load Balancers: Azure Load Balancers distribute incoming network traffic across multiple virtual machines, enhancing the availability and scalability of applications. There are two types: Azure Application Gateway, which focuses on web applications, and Azure Standard Load Balancer for various workloads.
- Virtual Network Peering: This allows the connection of VNets within the same region or across regions, enabling private and efficient communication between resources in different VNets.
- ExpressRoute: Azure ExpressRoute offers dedicated, private connections between on-premises data centers and Azure, bypassing the public internet. It ensures reliable, high-performance connectivity, making it suitable for data-intensive workloads and data residency requirements.
- Azure VPN Gateway: It allows the creation of site-to-site or point-to-site VPN connections, extending on-premises networks to Azure for secure and encrypted access to resources in the cloud.
- DDoS Protection: Azure provides robust protection against Distributed Denial of Service (DDoS) attacks through Azure DDoS Protection Standard, which includes mitigation of attacks in real-time.
- Virtual WAN: Virtual WAN simplifies and optimizes connectivity for branch offices and remote locations to Azure, offering a software-defined approach to networking and improving performance, security, and manageability.
- Azure Network Watcher: This service provides monitoring, diagnostics, and insights into network performance, helping administrators troubleshoot issues, visualize network topology, and ensure the health of their network infrastructure.
Network access control
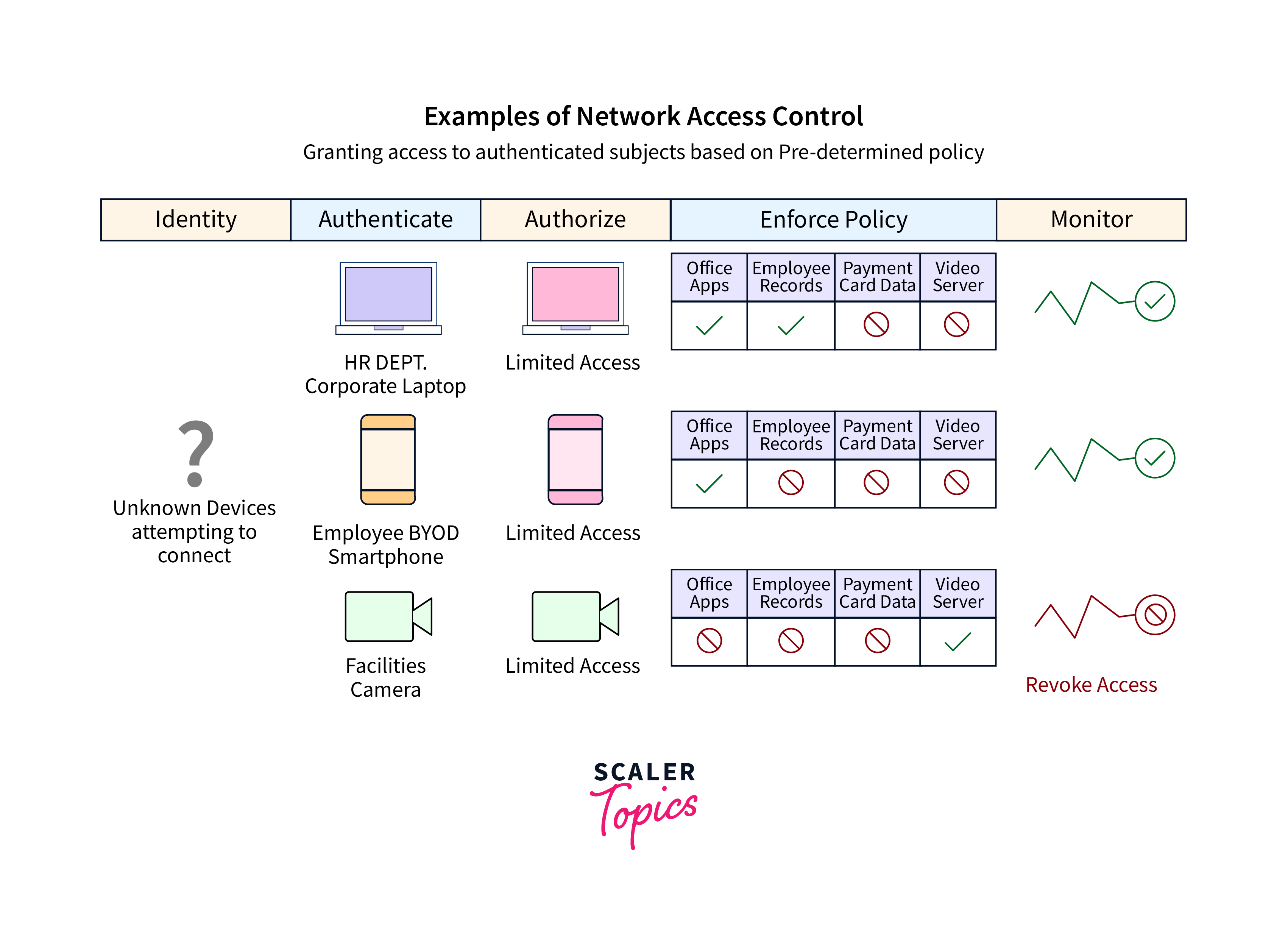
Network Access Control (NAC) is a critical security technology that organizations use to manage and enforce policies for controlling access to their network infrastructure. It provides a robust framework for ensuring that only authorized users and devices can connect to a network, while also safeguarding against unauthorized access and potential security threats. Here's a more detailed overview of NAC:
- Authentication and Authorization: NAC begins with user and device authentication. Users must prove their identity using methods such as usernames, passwords, multi-factor authentication, or digital certificates. Authorization determines the level of network access granted to authenticated users based on their roles, responsibilities, and the principle of least privilege.
- Endpoint Security Assessment: NAC solutions often conduct endpoint security checks to ensure that devices connecting to the network meet predefined security requirements. This can include verifying the presence of up-to-date antivirus software, current OS patches, correct firewall settings, and other security configurations. Non-compliant devices may be placed in a quarantine network or granted limited access until they meet the security requirements.
- Network Segmentation: NAC can enforce network segmentation by isolating devices into separate virtual LANs (VLANs) or micro-segments. This reduces lateral movement in case of a breach and restricts access based on device type or user role.
- Continuous Monitoring: NAC solutions continuously monitor network traffic and the status of connected devices. They can identify anomalies or unauthorized activities and trigger alerts or automated actions if suspicious behavior is detected.
- Guest Access: NAC can provide controlled and isolated access for guest users or devices, ensuring that guests don't have the same level of access as internal users, reducing the risk to network security.
- Integration with Identity and Access Management (IAM): NAC solutions often integrate with IAM systems to streamline user provisioning, authentication, and role-based access control.
- Enforcement of Security Policies: NAC enforces security policies through predefined rules and policies that dictate access rights, acceptable use, and security requirements. These policies can be tailored to different user groups or device types.
- Remediation: When non-compliant devices are identified, NAC can initiate remediation processes. This might involve pushing security updates, patches, or configuration changes to bring the device into compliance.
- Compliance Reporting: NAC solutions provide reporting and auditing capabilities, helping organizations maintain a record of who accessed the network, when, and what activities they performed. This is essential for regulatory compliance and internal security audits.
- Scalability and Flexibility: NAC solutions must be scalable to accommodate the increasing number of devices and users on modern networks. They should also be flexible enough to adapt to changing security requirements and evolving threat landscapes.
Azure Firewall
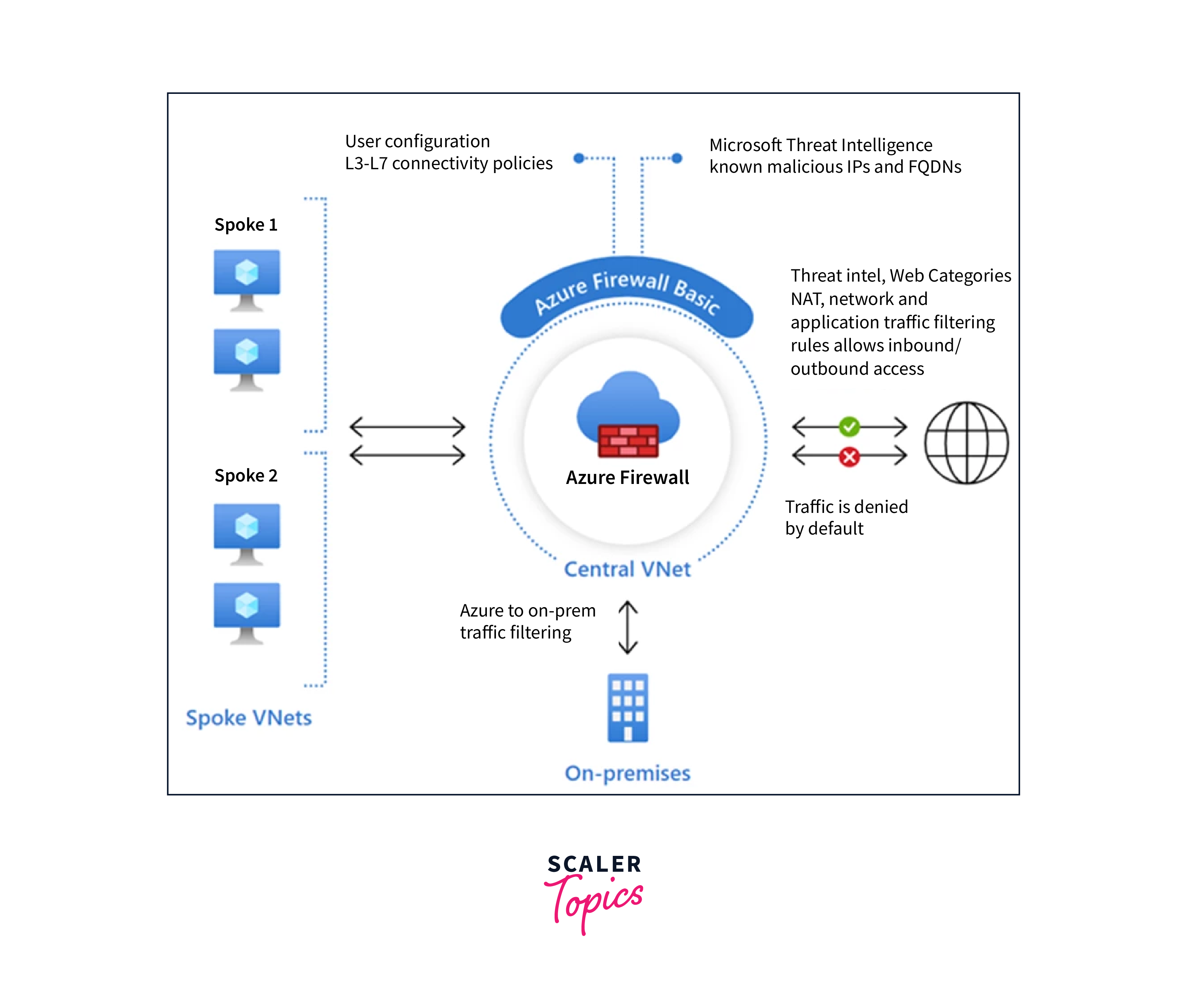
Azure Firewall is a cloud-native, fully managed firewall service offered by Microsoft Azure, providing robust security for your cloud-based applications and data. It serves as a critical perimeter security solution, protecting your virtual networks from unauthorized access and cyber threats. Here's a comprehensive overview of Azure Firewall:
- Perimeter Defense: Azure Firewall is strategically placed at the perimeter of your virtual network, controlling and monitoring all incoming and outgoing traffic. This ensures that only legitimate and authorized traffic is allowed while keeping malicious threats at bay.
- Stateful Inspection: As a stateful firewall, it analyzes network traffic not just based on individual packets, but also in the context of established connections. This allows it to make informed decisions about whether to permit or deny traffic, enhancing security.
- Application and Network Rules: Azure Firewall offers the flexibility to define both application and network-level rules. Application rules provide granular control over specific applications or services, while network rules allow control based on IP addresses, ports, and protocols.
- Threat Intelligence: It integrates with Microsoft's threat intelligence feed, which is regularly updated to block known malicious IP addresses and domains. This proactive approach helps prevent threats from reaching your resources.
- Logging and Monitoring: Azure Firewall provides detailed logging and reporting capabilities. Logs can be integrated with Azure Monitor, Azure Security Center, or third-party SIEM solutions, allowing you to monitor network activity, detect and respond to security incidents, and maintain compliance.
- High Availability: It's designed for high availability and can be configured in active-active or active-standby mode, ensuring uninterrupted service even during failures.
- Integration with Azure Services: Azure Firewall seamlessly integrates with other Azure services, simplifying the enforcement of security policies and the protection of resources across your Azure environment.
- Auto-Scaling: Azure Firewall can automatically scale to handle varying traffic loads, ensuring optimal performance and availability.
- Centralized Management: You can manage Azure Firewall centrally through Azure Firewall Policy, making it easier to enforce consistent security policies across multiple virtual networks and subscriptions.
Secure remote access and cross-premises connectivity
Secure remote access and cross-premises connectivity are critical components in today's increasingly distributed and cloud-driven work environments. These technologies enable organizations to facilitate secure communication and access between remote users, branch offices, and cloud resources.
Secure Remote Access:
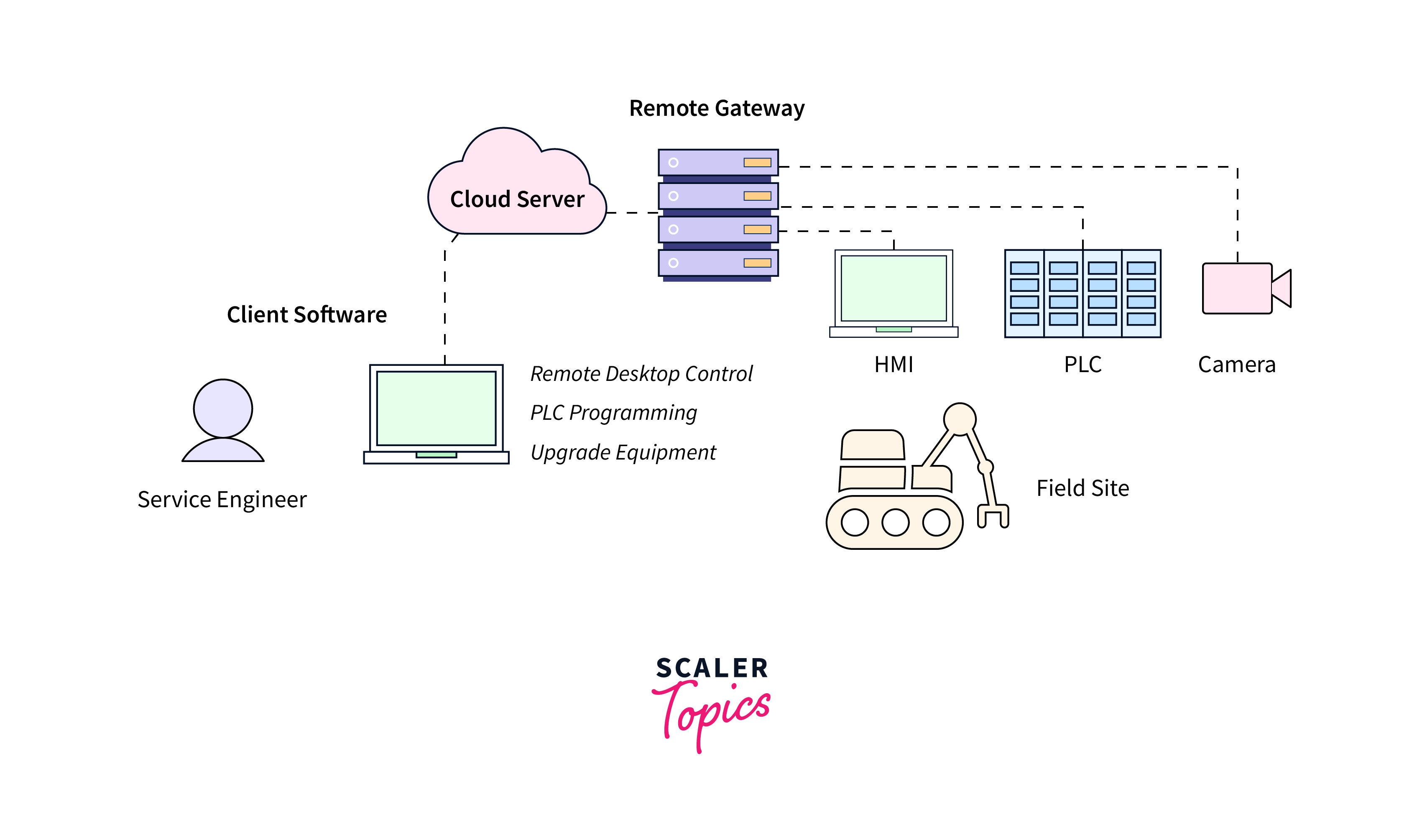
Secure remote access allows authorized users to connect to a network or specific resources from outside the traditional office environment while maintaining data privacy and security. Key technologies and practices include:
- Virtual Private Network (VPN): VPNs create an encrypted tunnel over the internet, ensuring data privacy and security while enabling remote users to access the corporate network. There are various types of VPNs, including site-to-site and client-to-site VPNs.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password, a temporary code from a mobile app, or a fingerprint scan.
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS): These cryptographic protocols ensure secure data transfer between remote users' devices and corporate resources over the internet, commonly used for secure web access (HTTPS).
- Remote Desktop Services (RDS): RDS technology allows remote users to access and control a desktop or application running on a server, enhancing productivity while maintaining security.
Cross-Premises Connectivity:

Cross-premises connectivity refers to the establishment of secure and efficient communication channels between an organization's on-premises network and cloud-based resources or remote branch offices. Key technologies and solutions include:
- Azure Virtual Network and VPN Gateway: Microsoft Azure offers Azure Virtual Network and VPN Gateway services, which allow organizations to create a secure, site-to-site VPN connection between their on-premises network and Azure resources. This enables a seamless and secure extension of the corporate network into the cloud.
- ExpressRoute: Azure ExpressRoute offers a dedicated, private connection between on-premises data centers and Azure data centers, bypassing the public internet to ensure a highly reliable, low-latency connection.
- SD-WAN (Software-Defined Wide Area Network): SD-WAN technology optimizes network traffic and ensures secure communication between branch offices, data centers, and the cloud. It offers centralized management, dynamic path selection, and enhanced security.
- Direct Connect: For organizations using Amazon Web Services (AWS), AWS Direct Connect establishes dedicated network connections between on-premises data centers and AWS regions, ensuring predictable network performance.
Availability
Availability, in the context of information technology and cloud services, refers to the degree to which a system, application, or service is accessible and operational when needed. It is a critical aspect of ensuring that technology resources are reliable and dependable, and it is typically measured in terms of uptime.
High availability is achieved through various strategies and technologies, including redundancy, failover mechanisms, and load balancing. Key considerations include:
- Redundancy: Redundancy involves having backup components or systems in place. For example, in a high-availability server setup, multiple servers can replicate data and services. If one server fails, another can seamlessly take over, minimizing downtime.
- Failover: Failover mechanisms ensure that when a primary system or component becomes unavailable, traffic and operations are automatically switched to a secondary, operational system. This minimizes disruptions and maintains service availability.
- Load Balancing: Load balancers distribute incoming network traffic across multiple servers or resources to ensure that no single component becomes overloaded. This optimizes resource utilization and enhances availability by preventing server overload.
- Disaster Recovery: Availability also includes disaster recovery planning, which involves offsite backups, data replication, and recovery procedures in case of catastrophic events, such as natural disasters or large-scale system failures.
- Monitoring and Management: Continuous monitoring of system health, performance, and security is crucial for maintaining availability. Automated management and alerting systems can quickly respond to issues to minimize downtime.
Name resolution
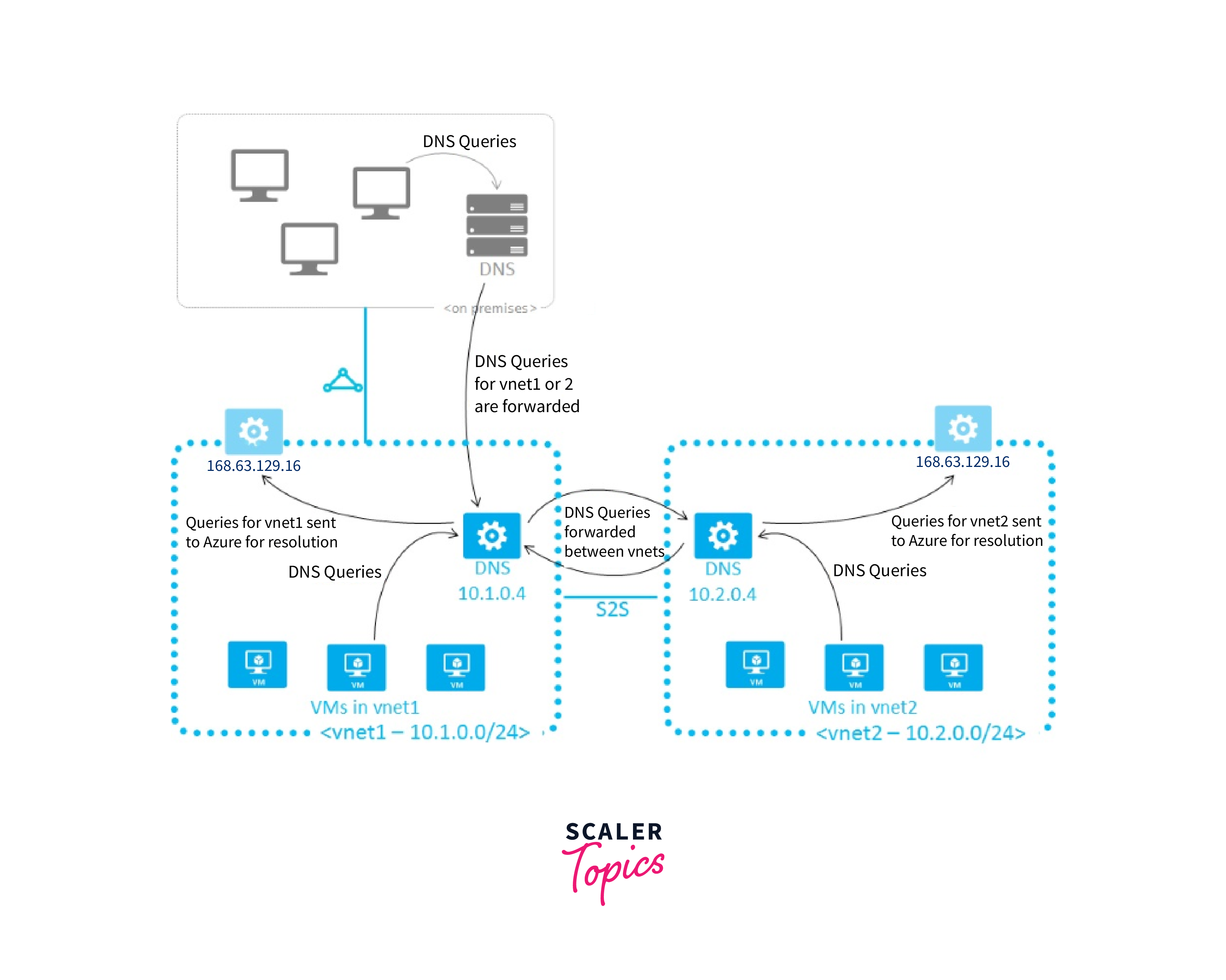
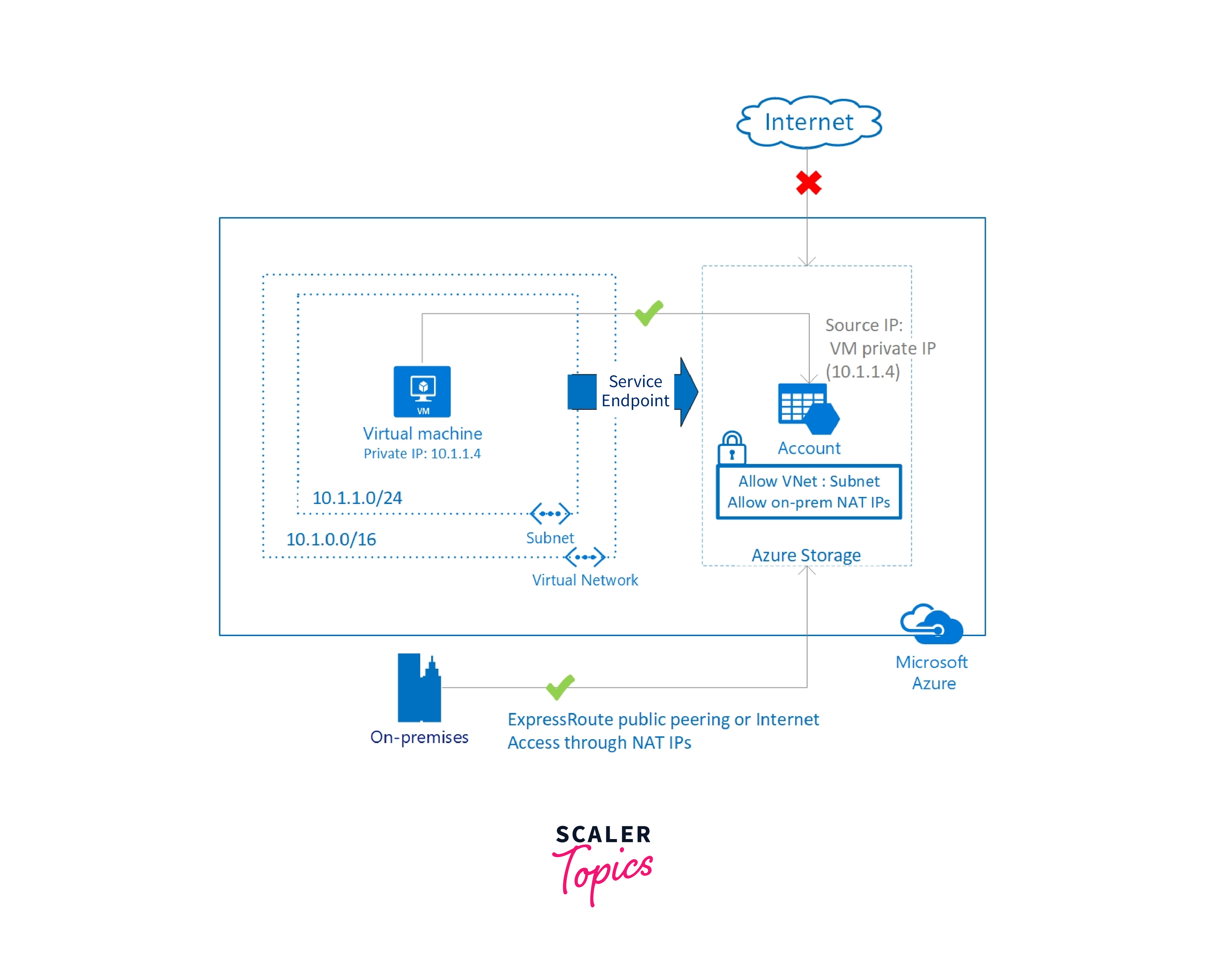
In the context of Azure Network Security, name resolution refers to the process of translating domain names to their corresponding IP addresses within the Azure cloud environment. This translation is crucial for proper communication and security enforcement. Here's how name resolution works in Azure Network Security:
- Azure DNS: Azure offers its Domain Name System (DNS) service, known as Azure DNS. This service allows you to host your domain names within Azure and manage DNS records associated with those domains. It plays a central role in name resolution within the Azure ecosystem.
- Name-to-IP Resolution: When resources, such as virtual machines or applications, need to communicate with each other, they often rely on DNS to resolve the names of other resources to their respective IP addresses. Azure DNS enables these resources to look up the IP addresses associated with domain names used within the Azure cloud environment.
- Security Policies: Azure Network Security services, like Azure Firewall or Network Security Groups (NSGs), can be configured to allow or deny traffic based on domain names. This is especially valuable for applying security policies, content filtering, and controlling communication between resources based on fully qualified domain names (FQDNs).
- Logging and Monitoring: Name resolution activities and DNS traffic can be logged and monitored to detect suspicious or unauthorized network activity. This is essential for identifying potential security threats or misconfigurations.
- Private DNS Zones: Azure allows you to create private DNS zones for internal domain names, enabling secure and efficient name resolution within your virtual network, even without exposing these domain names to the public internet.
Perimeter network architecture
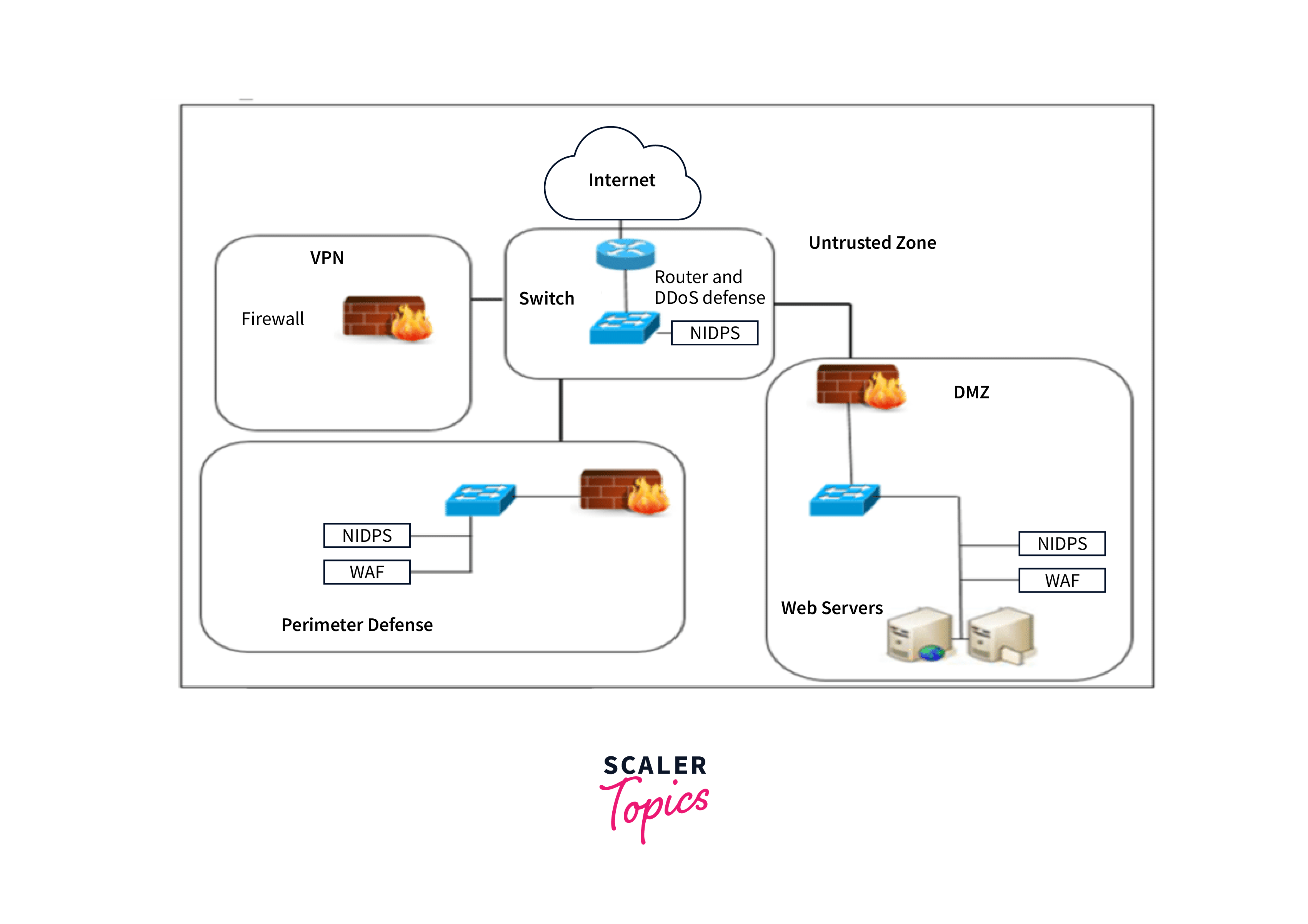
A perimeter network architecture, also known as a demilitarized zone (DMZ), is a network design strategy that establishes a secure buffer zone between an organization's internal network and the external, untrusted network, typically the internet. The primary purpose of a perimeter network is to enhance security by segregating and inspecting traffic before it reaches the internal network. Here's an overview in 250 words:
Key Components of Perimeter Network Architecture:
- Firewalls: Perimeter networks are protected by one or more firewalls. These security devices enforce access control policies and filter incoming and outgoing traffic. Firewalls can be configured to permit or deny traffic based on specific rules.
- Proxy Servers: Proxy servers act as intermediaries between internal users and external services. They can enhance security by caching web content, filtering content, and providing an additional layer of protection against threats.
- Intrusion Detection and Prevention Systems (IDPS): IDPS tools are often deployed within the perimeter network to monitor traffic for suspicious activity or known attack patterns. They can identify and block potential threats.
- Web Application Firewalls (WAF): A WAF is designed to protect web applications from a variety of security threats, including cross-site scripting (XSS), SQL injection, and other application-layer attacks. It's particularly important for protecting web services and applications.
- Mail and Message Filtering: Perimeter networks often include email gateways and message filtering systems to block spam, malware, and other threats before they enter the internal network.
- Virtual Private Network (VPN) Gateways: VPN gateways in the perimeter network enable secure remote access for employees and partners while keeping internal network resources isolated.
Use Cases:
- Enhanced Security: Perimeter networks provide an additional layer of security that inspects and filters traffic before it reaches the internal network, reducing the risk of attacks and breaches.
- Public Services: They can host publicly accessible services, such as web servers, without exposing the internal network. This is important for protecting sensitive data and resources.
- Segregation: Perimeter networks allow organizations to segment their network traffic, isolating internal network resources from potentially risky external traffic.
- Compliance: Many regulatory requirements necessitate the use of a DMZ to protect sensitive data and comply with security standards.
Azure DDoS protection

Azure DDoS (Distributed Denial of Service) Protection is a comprehensive service provided by Microsoft Azure to safeguard cloud resources from the damaging effects of DDoS attacks. DDoS attacks are malicious attempts to overwhelm a target's network or applications with a flood of traffic, making them inaccessible to users. Here's an overview of Azure DDoS Protection in 250 words:
Key Features:
- Traffic Scrubbing: Azure DDoS Protection automatically detects and mitigates DDoS attacks by scrubbing incoming traffic at Azure's global network before it reaches your resources. This process filters out malicious traffic, ensuring that legitimate traffic can reach your services without interruption.
- Protection Tiers: Azure offers two protection tiers: Basic and Standard. Azure DDoS Protection Basic is automatically enabled for all Azure services at no extra cost. Azure DDoS Protection Standard provides more advanced and customizable protection, making it suitable for mission-critical applications.
- Customization: With Azure DDoS Protection Standard, you can create custom protection policies to tailor the service to your specific needs. This allows you to adjust protection thresholds and enable specific DDoS mitigation policies to protect your applications.
- Anomaly Detection: Azure DDoS Protection uses machine learning algorithms to monitor traffic patterns and detect anomalies that could indicate a DDoS attack. When anomalies are detected, mitigation measures are triggered automatically.
- Traffic Analytics: Detailed traffic analytics and reporting help you understand the traffic patterns and potential threats. You can use this data to fine-tune your security policies and improve your overall security posture.
Use Cases:
- Protecting Critical Applications: Azure DDoS Protection is crucial for protecting critical web applications, APIs, and services against DDoS attacks that could disrupt business operations and affect user experience.
- Ensuring High Availability: By mitigating DDoS attacks, Azure DDoS Protection ensures high availability and continuous access to Azure resources, preventing costly downtime.
- Regulatory Compliance: Azure DDoS Protection helps organizations meet compliance requirements, as many regulations mandate the implementation of DDoS protection measures.
- Safeguarding Data: Protecting against DDoS attacks is an essential aspect of safeguarding sensitive data and maintaining the integrity of cloud-based assets.
Azure Front Door
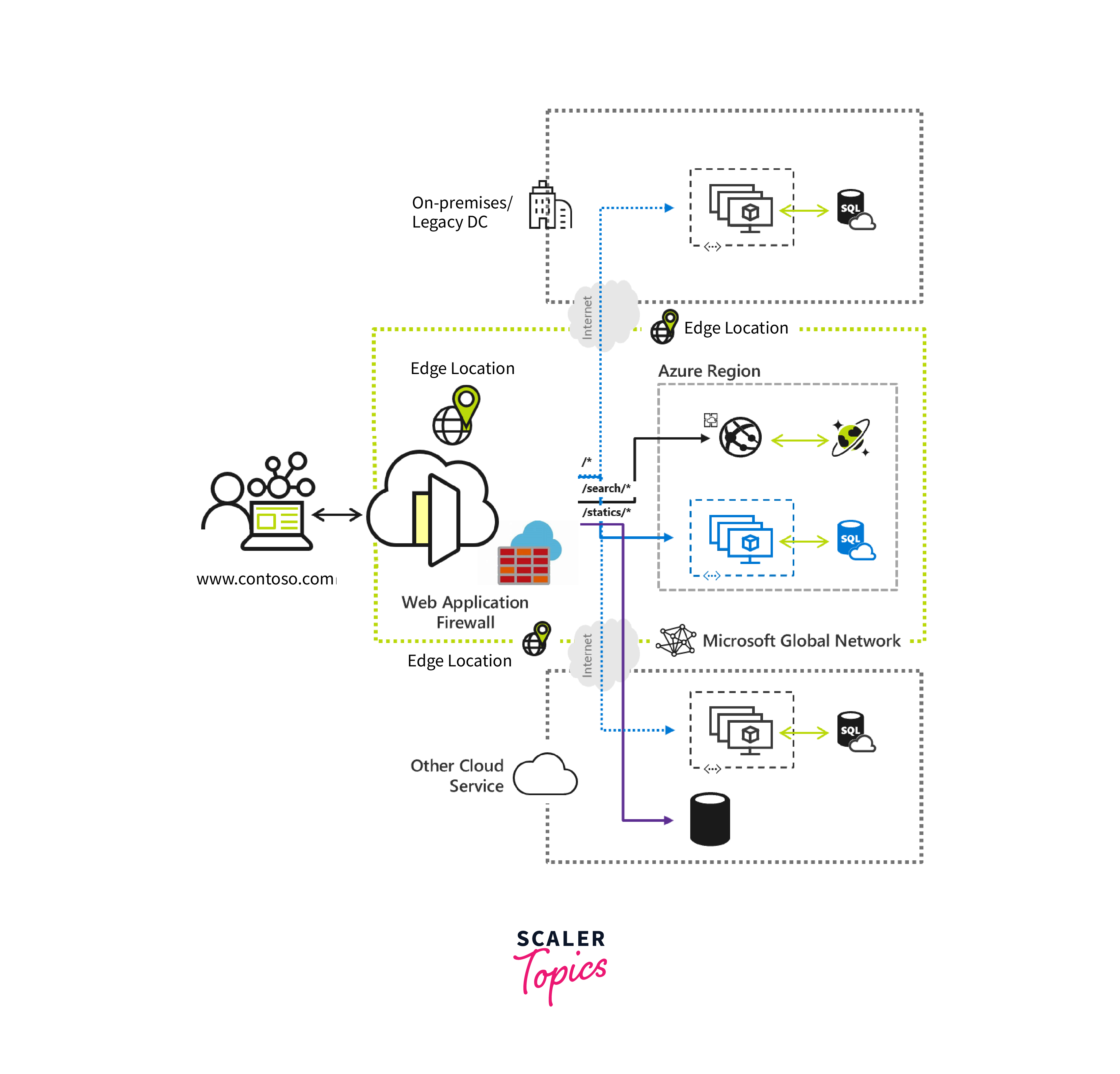
Azure Front Door is a content delivery and global application acceleration platform provided by Microsoft Azure. It acts as a secure entry point to your web applications and services, offering a range of capabilities to improve performance, availability, and security.
Key Features:
- Global Load Balancing: Azure Front Door routes incoming traffic to the closest and healthiest backend server or instance, optimizing the user experience by reducing latency and improving response times.
- Web Application Firewall (WAF): Front Door integrates with Azure Web Application Firewall, providing enhanced security by filtering and blocking malicious traffic, protecting against web application attacks, and ensuring data privacy.
- SSL Offloading: Front Door offloads Secure Sockets Layer (SSL) encryption and decryption, reducing the processing load on backend servers and improving overall performance.
- Content Caching: Front Door caches content at edge locations, reducing the load on origin servers and accelerating content delivery to end-users.
- Traffic Analytics: Front Door offers detailed traffic analytics and reporting, helping you gain insights into user behavior, diagnose issues, and make data-driven decisions to optimize application performance.
- Custom Rules: You can define custom routing and load-balancing rules based on factors like HTTP headers and URL paths, enabling fine-grained control over how traffic is directed to backend resources.
Use Cases:
- Global Scale Applications: Azure Front Door is ideal for applications that require global scale, ensuring that users are directed to the closest and most responsive application instance, regardless of their geographic location.
- Web Acceleration: It accelerates web applications and content delivery by caching frequently accessed content at edge locations, reducing latency and improving load times.
- Security: With integrated Azure Web Application Firewall, it protects against malicious traffic, mitigates DDoS attacks, and helps secure applications and services.
- High Availability: Front Door offers failover and redundancy, ensuring high availability and minimizing downtime for critical applications and services.
- Content Management: It's suitable for delivering dynamic content, APIs, and multimedia content efficiently, even during traffic spikes.
Azure Traffic manager
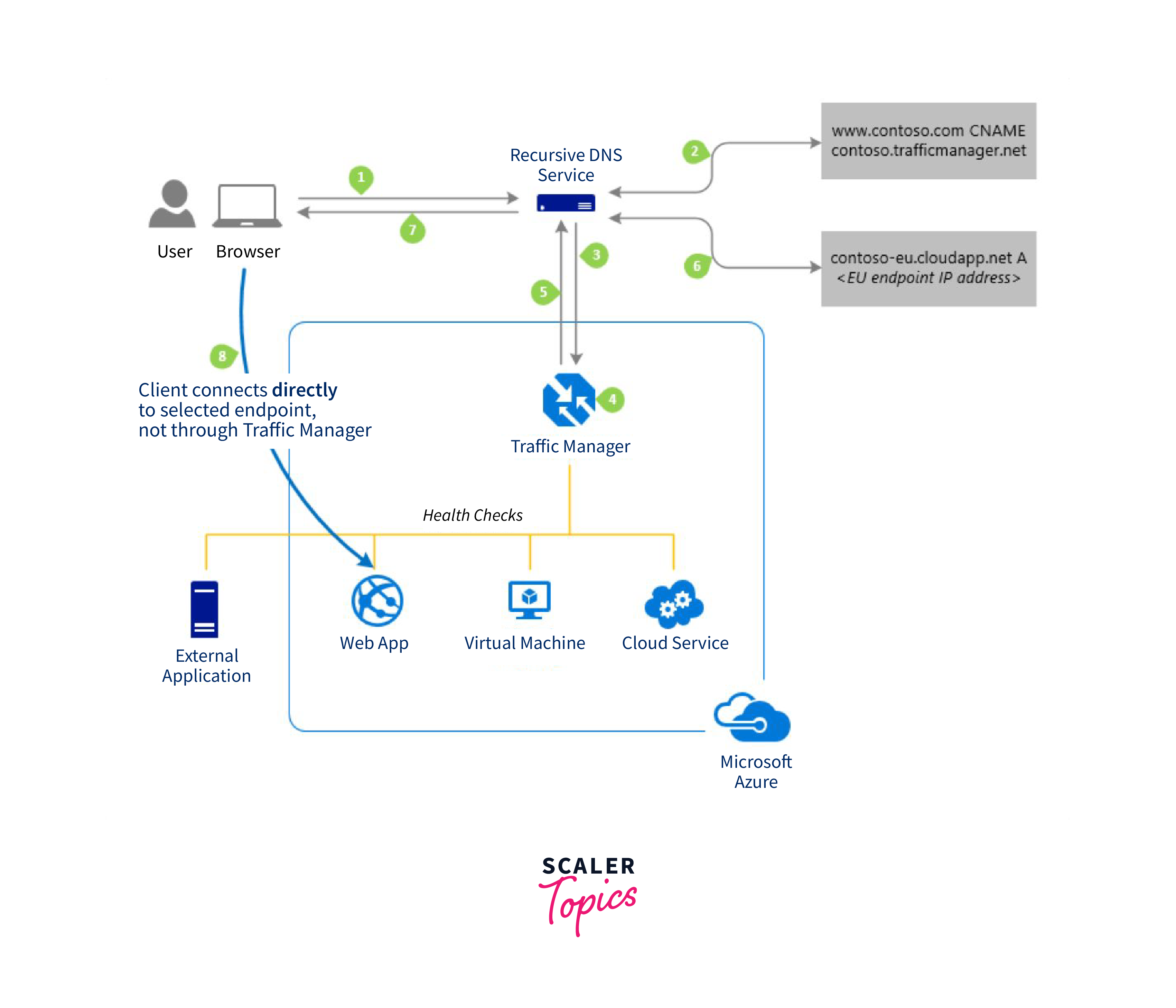
Azure Traffic Manager is a global Domain Name System (DNS) load balancer provided by Microsoft Azure. It enables you to distribute user traffic across multiple Azure datacenters, ensuring high availability, improved application performance, and fault tolerance. Here's an overview in 250 words:
Key Features:
- DNS-Based Traffic Routing: Azure Traffic Manager uses DNS to direct client requests to the most appropriate endpoint based on routing methods you define. This allows for flexible traffic distribution across multiple endpoints, such as Azure regions or external services.
- Multiple Routing Methods: It offers various routing methods, including Priority, Weighted, Performance, Geographic, and Subnet. These methods enable you to control how traffic is distributed based on specific requirements, such as prioritizing certain datacenters or routing users to the nearest endpoint for optimal performance.
- Geographic Load Balancing: With Geographic routing, you can direct users to the closest datacenter, improving response times and providing a localized experience.
- Failover Support: Azure Traffic Manager monitors the health of your endpoints, automatically routing traffic away from unhealthy endpoints to ensure high availability.
- Endpoint Monitoring: It allows you to configure health probes for each endpoint, checking their availability and responsiveness. If an endpoint fails these probes, traffic is automatically redirected to healthy endpoints.
- Global Scale: Azure Traffic Manager operates at a global scale, making it suitable for serving applications and services to a geographically distributed user base.
Use Cases:
- High Availability: Azure Traffic Manager improves service availability by directing users to the most responsive and healthy endpoint, ensuring uninterrupted service access.
- Load Balancing: It helps distribute incoming traffic across multiple Azure resources, datacenters, or endpoints to optimize resource utilization and prevent overloading.
- Disaster Recovery: Traffic Manager can be used to route traffic to a secondary datacenter in the event of a disaster or regional outage, ensuring business continuity.
- Content Delivery: It's valuable for content delivery networks (CDNs) and media streaming services, optimizing content delivery by routing users to the nearest content source.
- Global Expansion: Azure Traffic Manager supports expansion to new geographic regions and facilitates the deployment of applications with a global presence.
Monitoring and threat detection
Monitoring and threat detection in the context of Azure Network Security are essential components of maintaining a secure and well-protected cloud environment. Azure provides several tools and services to help organizations detect and respond to security threats effectively:
- Azure Monitor: Azure Monitor is a comprehensive monitoring and telemetry service that collects and analyzes data from various Azure resources, including virtual machines, networking, and security services. It offers insights into network performance, resource health, and security-related events.
- Azure Security Center: This centralized security management system provides advanced threat protection across all Azure services. It continuously monitors for security threats, misconfigurations, and vulnerabilities and offers recommendations for remediation.
- Log Analytics: Part of Azure Monitor, Log Analytics collects and analyzes data from various sources, helping organizations gain insights into network traffic, security events, and resource activities. It's crucial for proactive threat detection.
- Azure Firewall Logs: Azure Firewall generates logs that can be integrated with Azure Monitor and Log Analytics to monitor network traffic, identify malicious activities, and ensure compliance.
- Azure Network Watcher: This tool provides network-level monitoring and diagnostics, allowing for the detection of network anomalies, security group rule violations, and traffic flow analysis.
- Azure DDoS Protection: It offers real-time monitoring and mitigation of Distributed Denial of Service (DDoS) attacks, protecting against threats that could disrupt network services.
- Threat Intelligence: Azure Security Center incorporates threat intelligence feeds to stay up-to-date on the latest cybersecurity threats and vulnerabilities.
Conclusion
- Azure includes robust identity and access management tools, such as Azure Active Directory, for securing user authentication and authorization.
- Organizations can establish secure remote access to Azure resources using technologies like Virtual Private Networks (VPNs) and DirectConnect.
- Azure enables secure connections between on-premises networks and cloud resources, ensuring data flows safely.
- DNS-based name resolution is essential for routing traffic and ensuring security within Azure.
- Azure Front Door and Traffic Manager services optimize application performance and availability, routing traffic efficiently and securing content delivery.
- Azure provides tools like Azure Monitor and Azure Security Center for continuous monitoring, anomaly detection, and threat response.
- Azure Network Security forms a comprehensive framework for safeguarding Azure resources, making it suitable for a wide range of organizations and use cases.
