Microsoft Azure Sentinel
In the modern digital realm, securing organizations is critical. Microsoft Azure Sentinel is a cloud-based Security Information and Event Management (SIEM) solution that leverages AI and Machine Learning to combat security threats. This advanced system analyzes vast data from multiple sources in real-time, enabling swift identification and resolution of potential risks. Integrated with Microsoft's ecosystem, Azure Sentinel enhances security operations through scalable, real-time data analysis and automated threat response. It's designed to cater to organizations of varying sizes, ensuring heightened security through efficient detection and management of emerging cybersecurity challenges.
What is Azure Sentinel?

Azure Sentinel is a cloud-based Security Information and Event Management (SIEM) service by Microsoft. It empowers organizations to monitor and respond to security threats across their entire enterprise. By aggregating data from various sources like devices, applications, and services, Sentinel provides a comprehensive view of an organization's security posture. Leveraging advanced AI and machine learning, it can detect and analyze anomalies, suspicious activities, and known threats in real-time.
Azure Sentinel facilitates intelligent incident response by automating actions and orchestrating workflows to address security incidents swiftly. Its integrated and customizable dashboards enable security analysts to gain insights and make informed decisions effectively. As a cloud-native solution, Azure Sentinel ensures scalability and easy integration with other Microsoft and third-party services. This makes it an essential tool for enhancing the security posture of modern enterprises and safeguarding their digital assets against a rapidly evolving threat landscape.
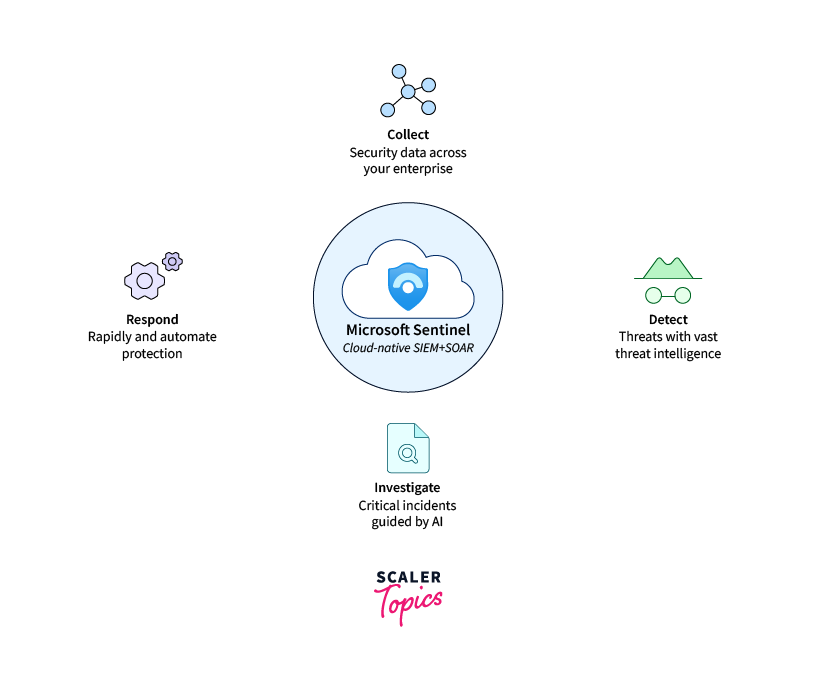
Features of Azure Sentinel
Some Key features of Microsoft Sentinel are as follows:
- Customizable Dashboards: The service offers interactive and customizable dashboards that provide security analysts with actionable insights and visualizations to monitor security incidents effectively.
- Automated Response: Azure Sentinel enables automated incident response, allowing security teams to define playbooks that orchestrate actions when specific security events occur, saving time and minimizing human error.
- Threat Intelligence: It integrates with Microsoft Threat Intelligence and other third-party threat intelligence sources, enhancing its ability to identify and mitigate emerging threats.
- Scalability: Being a cloud-native service, Azure Sentinel scales effortlessly to accommodate growing data volumes and business requirements.
- Integration: It seamlessly integrates with the broader Microsoft ecosystem and third-party security tools, fostering a unified security approach.
- Compliance and Governance: Azure Sentinel helps organizations meet regulatory compliance requirements by offering built-in compliance reports and supporting audit processes.
- Incident Management: The service provides a central repository to manage and track security incidents, streamlining incident response and investigation.
- Threat Hunting: With its advanced query capabilities, analysts can perform ad-hoc investigations and conduct proactive threat hunting to identify hidden threats and potential vulnerabilities.
How Azure Sentinel Works
Azure Sentinel is a cloud-based Security Information and Event Management (SIEM) service offered by Microsoft. It collects and analyzes data from various sources like servers, devices, applications, and cloud resources, providing a unified view of an organization's security posture.
The process starts with data ingestion, where logs and security events are gathered from connected sources. This data is then enriched and normalized to facilitate analysis. Azure Sentinel employs AI-driven analytics to detect and investigate security threats, identifying patterns and anomalies.
Incident response is streamlined with automated playbooks that execute predefined actions upon detecting specific threats. Customized dashboards and reports offer real-time visibility into security incidents and provide actionable insights for further investigation and mitigation.
Azure Sentinel leverages the power of Microsoft's cloud infrastructure, making it highly scalable, cost-effective, and efficient in rapidly detecting and responding to security threats, enhancing overall organizational cybersecurity posture.
Key Components & Key Points
Connect to All Data
Connect to all Data is a key feature of Azure Sentinel, allowing the platform to ingest and analyze data from diverse sources like servers, devices, applications, and cloud resources. This capability ensures comprehensive security monitoring and threat detection, enhancing the effectiveness of the SIEM service.
Workbooks
Workbooks are a key feature of Azure Sentinel, providing customizable data visualizations and interactive analytics. Security teams can create and share dashboards, charts, and graphs, enabling real-time insights into security incidents, facilitating quick decision-making, and enhancing the overall monitoring and response capabilities of the SIEM service.
Analytics
Analytics in Microsoft Azure Sentinel, utilizing AI-driven machine learning algorithms to detect and investigate security threats. It helps identify patterns, anomalies, and suspicious activities within data, enabling security teams to proactively respond to potential threats, enhancing the platform's effectiveness in safeguarding the organization's digital assets.
Security Automation and Orchestration
Security Automation and Orchestration is a key feature of Azure Sentinel that streamlines incident response processes. It allows security teams to create automated playbooks with predefined actions to execute upon detecting specific threats. This capability reduces manual effort, accelerates response time, and ensures consistent and efficient incident handling. By automating repetitive tasks, organizations can improve their overall security posture and effectively mitigate security incidents in a timely manner.
Investigation
Investigation is a key point of Azure Sentinel, offering intuitive tools to explore and analyze security incidents. It allows security analysts to delve into data, perform queries, and pivot on relevant information, enabling thorough investigations to understand the scope and impact of potential security threats.
Hunting
Hunting is a key component of Azure Sentinel, enabling proactive threat detection. Security teams can perform targeted searches and use custom queries to uncover hidden threats and potential security risks. This capability empowers organizations to stay ahead of emerging threats and strengthen their overall cybersecurity defenses.
Community
Community in Microsoft Sentinel or Azure Sentinel, referring to the active user community and open-source contributions. Users can share and access custom queries, playbooks, and workbooks, fostering collaboration, knowledge-sharing, and collective improvement of the platform's capabilities to bolster threat detection and incident response efficiency.
Azure Sentinel Solutions
Why choose Microsoft Azure Sentinel Solutions
Here are some key points on Why choose Microsoft Azure Sentinel Solutions:
- Scalable and robust cloud infrastructure for handling large volumes of security data.
- Native integration with Microsoft services like Office 365 and Azure AD for seamless data correlation.
- AI-driven analytics and machine learning for proactive threat detection.
- Security automation and orchestration for streamlined incident response.
- Thriving user community for collaborative knowledge sharing.
- Customizable workbooks for interactive data visualization and analytics.
- Continuous updates and improvements from Microsoft's extensive security expertise.
- Cost-effective pricing models tailored to organizational needs.
- Centralized security monitoring and management across on-premises and cloud environments.
- Compliance with industry standards and regulations for enhanced data protection.
Types of Azure Sentinel Solutions
- Pre-Built Connectors: Azure Sentinel provides pre-built connectors to various data sources, including Microsoft services like Office 365, Azure Active Directory, and Azure Security Center, as well as third-party solutions such as firewalls and antivirus systems.
- Analytics Rules: Azure Sentinel includes pre-configured analytics rules that detect common security threats and anomalies. These rules cover areas such as malware detection, account compromise, and suspicious network activities.
- Playbooks: Playbooks are pre-defined workflows that automate incident response processes. Azure Sentinel offers a range of built-in playbooks and allows customization to suit specific organizational requirements.
- Workbooks: Workbooks provide customizable visualizations and analytics dashboards to monitor and investigate security incidents. Azure Sentinel offers a set of pre-built workbooks, and users can create their own tailored to their needs.
- Threat Intelligence: Azure Sentinel integrates with various threat intelligence platforms, providing access to up-to-date threat feeds and enabling proactive threat detection and response.
- Community Contributions: The Azure Sentinel community shares custom queries, playbooks, and workbooks, providing a rich library of community-driven solutions and expertise.
Normalization and the Azure Sentinel Information Model (ASIM)
Normalization: In the context of Azure Sentinel, normalization refers to the process of standardizing and transforming incoming security data from various sources into a consistent format. Different devices and applications generate logs in their own unique structures, making it challenging to analyze and correlate data effectively. Normalization normalizes this data, converting it into a common format, which simplifies data analysis and allows for more efficient detection of patterns and anomalies.
Azure Sentinel Information Model (ASIM): ASIM is a data schema used by Azure Sentinel to define the structure and organization of normalized data. It provides a unified and standardized way to store security-related information, ensuring consistent representation of data from disparate sources. ASIM enables security analysts to create custom queries and perform advanced analytics on normalized data, facilitating faster and more accurate threat detection, investigation, and response.
Components of the Azure Sentinel Information Model (ASIM)
- Normalized Schemas: These encompass predefined event types that serve as a foundation when constructing unified capabilities. Each schema specifies the event's fields, a standardized column naming convention, and a consistent format for field values. They provide a common structure for organizing and interpreting data.
- Entities: Represent objects within the system, such as users, hosts, applications, or IP addresses. They provide context and structure to the data.
- Relationships: Define connections and associations between entities, facilitating a comprehensive understanding of the environment and potential security dependencies.
- Fields: Capture specific attributes or properties of entities, allowing detailed information to be extracted and analyzed.
- Log Analytics Tables: ASIM utilizes these tables to store and manage normalized data after undergoing the parsing and normalization process.
- Parsers: Parsers are essential components responsible for interpreting and extracting meaningful information from raw logs generated by various sources. They convert diverse log formats into a consistent and standardized structure for further analysis.
- Detection Rules: Leverage the normalized data to perform threat detection and analysis, helping identify security incidents and potential risks.
- Queries: Support custom queries to retrieve and analyze data, empowering advanced investigation and threat hunting capabilities.
Microsoft Azure Sentinel Tutorial
To begin using Azure Sentinel, follow these steps:
- Access the Azure portal and locate the search bar.
- Search for Azure Sentinel or Microsoft Sentinel using the portal's search bar.
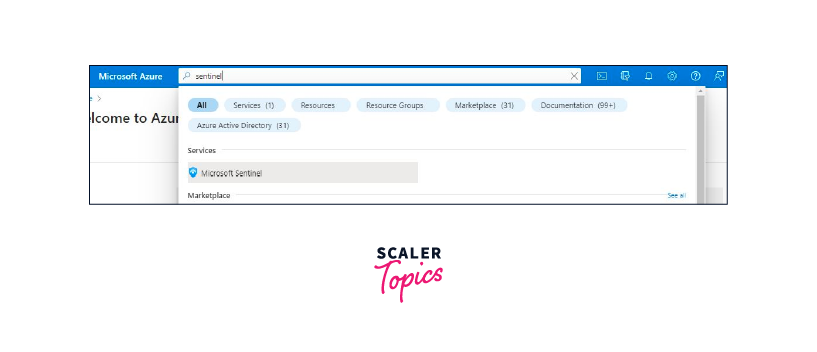
- Create a new Sentinel by navigating to the Create tab and clicking on it.
- Proceed to create a new workspace.
- Fill in the necessary details for the workspace, including the resource group you wish to connect to.
- If the resource group is not available, create a new one.
- Enter the desired instance name and select the region. Click on the Review + Create button.
- Review the information you've provided and click on Create to initiate the creation process.
- Wait for a minute or two for the instance to be created.
- Once the process is complete, you will see the name of your instance displayed below.
- Click on the instance you have created to access the Overview tab.
- In the Overview tab, you can observe the functioning of your created instance.
- Navigate to the News & Guides section by clicking on it.
- Within this section, you can add data collectors to your instance.
- Click on Connect to proceed.
- This will display a list of available data connectors.
- Select any data connector from the list to view its details on the right side.
- If the data connector meets your requirements, you can proceed by purchasing its API.
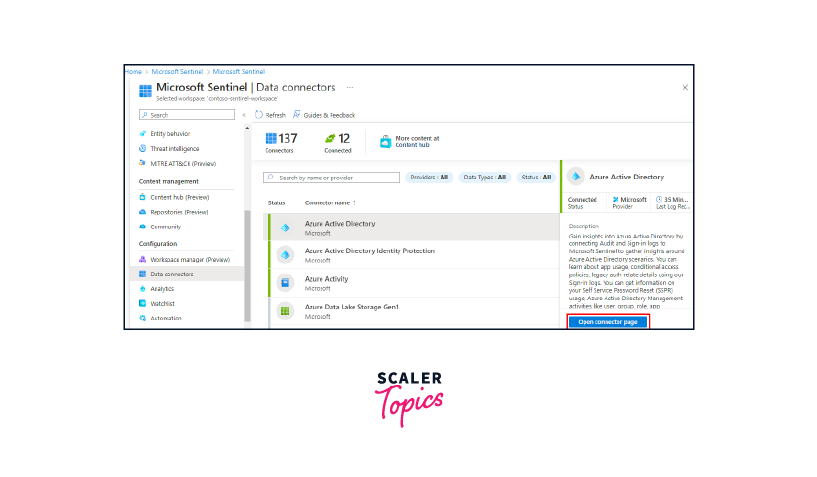
- The Workbooks tab allows you to save templates for workbooks.
- Within this tab, you will find a variety of notebooks from which you can choose.

Conclusion
- Azure Sentinel is a cloud-based SIEM service by Microsoft for intelligent security analytics and threat detection.
- Customizable Dashboards, Automated Response, Threat Intelligence, Scalability, Integration, Compliance and Governance, Incident Management, Threat Hunting, etc are some Features of Microsoft Sentinel.
- Connect to all Data, Workbooks, Analytics, Security Automation and Orchestration, Investigation, Hunting, Community are some key components of Microsoft Sentinel.
- Azure Sentinel Solutions are pre-built, customizable resources that enhance threat detection and security analytics within the Azure Sentinel platform.
- Azure Sentinel Information Model (ASIM) defines the structure and organization of normalized security data for analysis and correlation.
