Application security group in Azure
Overview
Azure Application Security Groups (ASG) are a vital part of Azure's network security. These groups allow you to categorize virtual machines (VMs) based on their roles, functions, or security requirements. ASGs work at the application level, giving you detailed control over how data moves and security rules. This makes it easier to manage rules, creates smaller, secure sections in your network, and focuses on protecting specific applications. ASGs seamlessly integrate with other Azure services, enhancing security for Azure resources. They are essential for securing complex, multi-tier applications, ensuring data flows are application-specific, and reducing the attack surface in your Azure environment.
What is ASG?
ASGs operate at the application layer (Layer 7) of the OSI model, enabling application-centric security. This means that instead of relying on traditional IP or port-based controls, ASGs allow you to define security policies based on the applications running on your VMs. This application-awareness is particularly valuable for securing complex, multi-tier applications where different parts of the application have unique security needs.
Azure Application Security Groups (ASG) are a fundamental element of network security within Microsoft Azure. They provide a flexible and dynamic way to organize and secure virtual machines (VMs) based on their roles, functions, or specific security requirements.
The primary purpose of ASG is to simplify the management of security rules. Instead of creating rules for individual VMs, rules are defined for ASGs. VMs that share similar security requirements are grouped into these ASGs, and the same security policies apply to all VMs within the group. This not only streamlines administrative tasks but also ensures that security policies are consistent across all related resources.
ASG supports micro-segmentation, a security strategy that divides a network into smaller, isolated segments. By reducing the attack surface and limiting lateral movement of threats, micro-segmentation significantly enhances network security. Dynamic membership capabilities allow VMs to be added to or removed from ASGs based on their roles or functions, adapting to the evolving needs of your infrastructure.
ASGs also seamlessly integrate with other Azure services, providing a comprehensive approach to security. They enhance the visibility of network traffic, simplify security policy management, and ensure that only necessary and authorized traffic is allowed between VMs.
Key Points About ASG
Azure Application Security Groups (ASG) are a crucial component of network security in Azure environments. Here are some key points in more detail:
-
Micro-Segmentation for Enhanced Security: ASG enables micro-segmentation, allowing you to group virtual machines (VMs) based on their roles and functions. This fine-grained control limits lateral movement of threats and reduces the attack surface, significantly enhancing security.
-
Application-Centric Approach: ASG works at Layer 7 (the application layer) and is great for securing complex apps with different security needs. It's like having tailored security for each part of a multi-tier application.
-
Simplified Policy Management: ASG offers centralized policy management. Security rules are defined at the ASG level, simplifying the enforcement of consistent policies across multiple VMs. This not only reduces complexity but also ensures policy consistency.
-
Efficient Grouping of VMs: VMs with similar security needs are grouped together within ASGs. This grouping makes it easier to manage security policies for resources that share common security requirements, such as a specific application tier.
-
Enhanced Visibility: ASG provides improved visibility into network traffic and security. You can monitor and control communication at the application layer, which is especially valuable for understanding how applications interact.
-
Rule-Based Traffic Control: ASG rules allow you to specify which traffic is allowed or denied between ASGs. This fine-grained control over network access is efficient and contributes to better network security.
-
Dynamic Membership: VMs can be dynamically added to or removed from ASGs based on their roles or functions. This dynamic membership makes it easy to adapt security policies as your infrastructure evolves.
-
Reduced Complexity: ASG simplifies security groupings by focusing on the application layer. This makes security policies more manageable and less prone to errors compared to traditional IP or port-based controls.
-
Scalability: ASG can scale to meet the security needs of growing organizations. It can be used for small deployments and large, complex applications, providing flexibility as your network expands.
-
Multi-Tier Application Security: ASG is particularly valuable for securing multi-tier applications where different layers have distinct security requirements. This helps maintain the integrity of the entire application.
-
Application-Aware Security: ASG enforces security policies that are application-aware. This level of awareness is critical for comprehensive network protection, especially in complex, modern application environments.
Creating a New Security Application Group
Creating a new Security Application Group (ASG) in Azure is a straightforward process that allows you to group virtual machines (VMs) based on their roles, functions, or security requirements. Here's a step-by-step guide to creating a new ASG:
Step 1: Sign in to the Azure Portal
- Go to https://portal.azure.com and sign in with your Azure account.
Step 2: Navigate to "Security Application Groups"
- In the Azure Portal, click on the "All services" option in the left-hand menu or use the search bar to find "Application Security Groups."
Step 3: Create a New ASG
- In the "Application Security Groups" section, click on "Add" to create a new ASG.
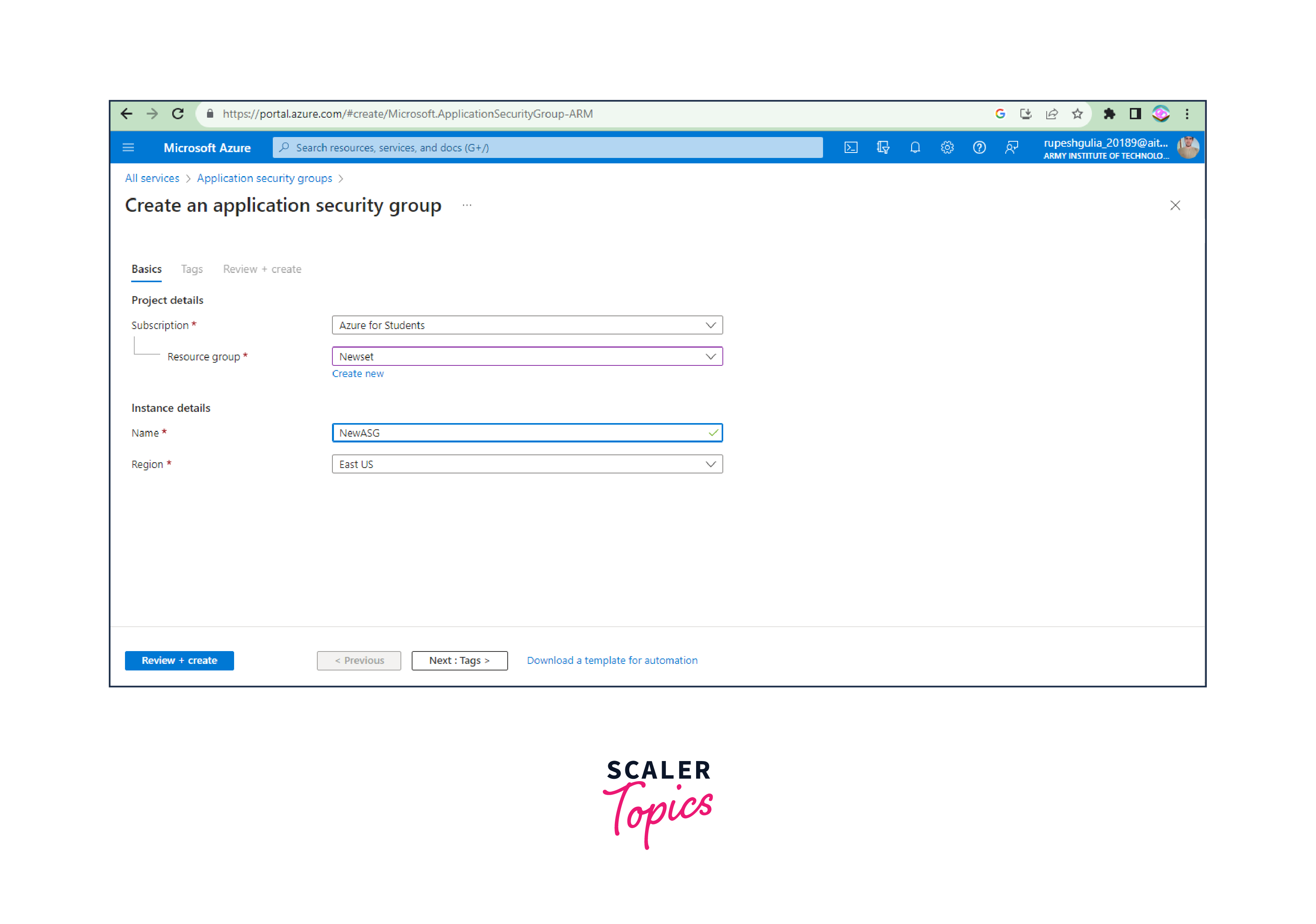
Step 4: Configure ASG Settings
- Fill in the required details for the new ASG:
- Name: Provide a unique name for your ASG.
- Subscription: Choose the Azure subscription in which you want to create the ASG.
- Resource group: Select an existing resource group or create a new one to contain the ASG.
- Region: Choose the Azure region for your ASG.
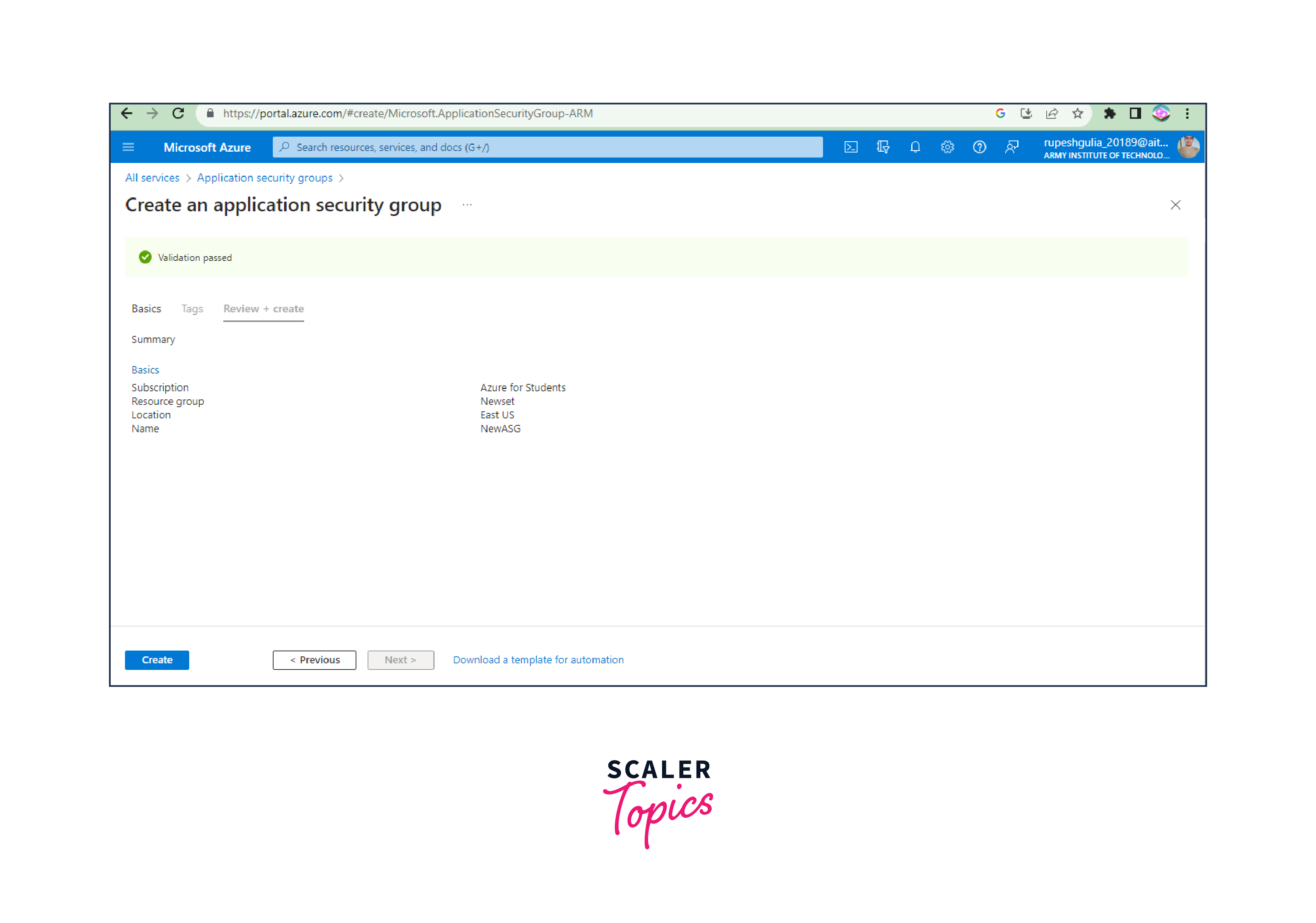
Step 5: Review and Create
- After configuring the ASG settings, review your choices to ensure they are accurate.
- Click "Create" to create the new Security Application Group.
Step 6: Add Virtual Machines to the ASG
- Once the ASG is created, you can add VMs to it. To do this, navigate to the "Virtual machines" section in the Azure Portal.
- Select the VM you want to add to the ASG and go to its settings.
- In the settings, find the "Application security groups" section, and select the ASG you created earlier.
Step 7: Configure Security Rules
- After adding VMs to the ASG, you can configure security rules for the group. These rules define which traffic is allowed or denied for VMs within the ASG.
- Navigate to the "Network security groups" section in the Azure Portal, find the NSG associated with the ASG, and configure security rules as needed.
Step 8: Review and Test
- After setting up the ASG and security rules, review your configurations and perform testing to ensure that the security policies are correctly applied to the grouped VMs.
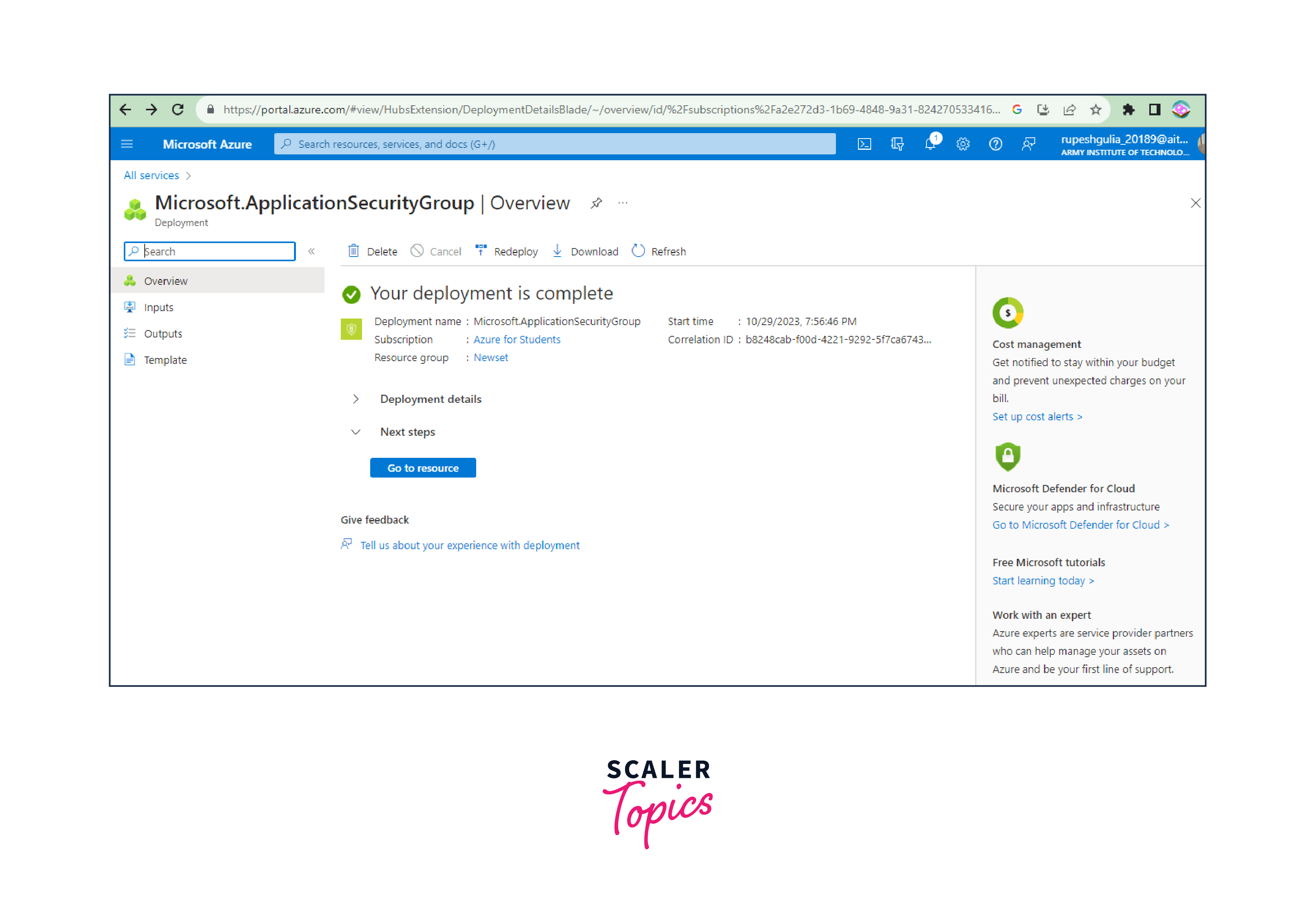
Creating a Security Application Group in Azure provides you with a powerful tool for managing security policies at the application layer, simplifying security rule management, and enhancing network security within your Azure environment.
Benefits of Using ASG
Using Application Security Groups (ASGs) in your Azure environment offers a multitude of advantages that contribute to a more secure and manageable network infrastructure. Here's a more detailed explanation of these benefits:
-
Streamlined Rule Management: ASGs simplify the complex task of managing security rules. Rather than defining rules for individual virtual machines (VMs), you can categorize VMs into logical groups and apply rules at the group level. This greatly reduces the number of rules to manage and minimizes the potential for rule conflicts.
-
Granular Control: ASGs operate at the application layer, providing you with granular control over how network traffic is allowed or restricted. This means you can specify which applications can communicate with one another and under what conditions, enhancing the precision of your security measures.
-
Micro-Segmentation: Micro-segmentation is a key feature of ASGs. It enables you to create isolated security perimeters within your network. By isolating different parts of your infrastructure, you limit the scope of potential security breaches. If one segment is compromised, the impact is contained.
-
Application-Centric Security: Traditional security focuses on IP addresses and ports. ASGs take a different approach by concentrating on applications. This aligns security with the actual needs of your applications and helps protect the most critical components of your network.
-
Enhanced Network Security: By effectively organizing VMs into groups and controlling traffic at the application layer, ASGs contribute to an overall more secure network environment. This reduces the attack surface, making it harder for malicious actors to exploit vulnerabilities.
-
Consistency in Policies: Policies defined at the ASG level are consistently applied to all VMs within the group. This ensures that security measures are uniform and eliminates the risk of inconsistencies or misconfigurations that might occur when managing rules individually.
-
Integration with Azure Services: ASGs are fully integrated with other Azure services. This means that they play a pivotal role in the security of your Azure resources, providing comprehensive network security and complementing other security measures such as firewalls and intrusion detection systems.
-
Dynamic Membership: ASGs support dynamic membership, allowing VMs to be added or removed from groups as needed based on their roles or functions. This adaptability ensures that security policies always align with the evolving requirements of your infrastructure.
-
Customization: ASGs are highly customizable, meaning you can tailor security policies to meet the specific needs of your organization. This includes aligning security with various compliance standards and regulations relevant to your industry.
-
Centralized Management: Centralized management is a key feature of ASGs, enabling security teams to define and enforce security policies from a single, unified point. This streamlines operational efficiency and ensures that security measures are consistently implemented.
-
Optimized Response: In the unfortunate event of a security incident, ASGs can be used to trigger automated responses. For example, they can isolate compromised systems from the network or block traffic that exhibits malicious behavior in real-time, minimizing the impact of security breaches.
In conclusion, the benefits of using ASGs in your Azure environment are extensive. They range from simplifying rule management and offering granular control to supporting micro-segmentation and ensuring that security policies are closely aligned with the unique needs of your applications. ASGs contribute to a more secure, efficient, and responsive network security strategy.
Azure NSG vs. ASG
Here's a comparison between Azure Network Security Groups (NSG) and Azure Application Security Groups (ASG) in tabular form:
| Aspect | Network Security Group (NSG) | Application Security Group (ASG) |
|---|---|---|
| Purpose | Controls inbound and outbound traffic at the network layer (Layer 3 and 4). | Provides security grouping for application-level firewall rules and micro-segmentation. |
| Layer of Operation | Operates at the network layer (Layer 3 and 4). | Operates at the application layer (Layer 7). |
| Rule Type | Contains rules for IP addresses, port ranges, and protocols. | Contains rules for application-level communication, allowing grouping of VMs for security policies. |
| IP and Port Rules | Define rules based on IP addresses, port ranges, and protocols. | Define rules based on application-specific endpoints or service tags. |
| Inbound and Outbound Rules | Supports both inbound and outbound rules. | Supports both inbound and outbound rules. |
| Priority | Rules have priority values (lowest to highest) for processing. Lower priority rules are evaluated first. | Rules have priority values (lowest to highest) for processing. Lower priority rules are evaluated first. |
| Security Policies | Typically used for perimeter security and controlling network traffic between subnets and the internet. | Used for micro-segmentation within subnets and controlling traffic between application components. |
| Use Cases | Useful for creating network-level access controls, e.g., allowing or blocking specific traffic to VMs. | Ideal for creating fine-grained security policies at the application layer, especially in complex, multi-tier applications. |
| VM Association | Rules are associated directly with VM network interfaces or subnet resources. | VMs are associated with security groups, and rules are created for these groups. |
| Network Scope | Applies to the entire VNet or subnet where the NSG is associated. | Applies to specific VMs or applications grouped in security groups. |
| Granularity | Offers network-level granularity for controlling traffic. | Provides application-level granularity for controlling communication between VMs. |
Both NSGs and ASGs serve different purposes and can be used in conjunction to achieve comprehensive security in Azure environments, with NSGs focusing on network-level security and ASGs providing fine-grained application-level security.
Conclusion
- ASGs provide granular control over network traffic by grouping virtual machines (VMs) based on their roles or functions within an application. This enables organizations to implement precise security policies.
- ASGs enable micro-segmentation, dividing a network into smaller, isolated segments. This ensures that only necessary communication occurs between VMs, reducing the attack surface.
- ASGs simplify rule management by allowing administrators to define security policies at the application level rather than specifying individual VMs. This reduces complexity and makes security policies more maintainable.
- By controlling traffic at the application layer (Layer 7), ASGs add an extra layer of security to the network, complementing network security groups (NSGs) that operate at the network layer (Layer 3 and 4).
- ASGs facilitate compliance with security and regulatory requirements by enabling organizations to enforce strict access controls and segmentation within their applications.
- ASGs can scale to accommodate growing application environments, making them suitable for organizations of all sizes.
- ASGs seamlessly integrate with other Azure security services, such as Network Security Groups (NSGs) and Azure Firewall, providing a comprehensive security solution.
