Azure Advanced Threat Protection
Overview
Azure Advanced Threat Protection (Azure ATP) is a security solution designed to safeguard your organization's digital infrastructure against advanced cyber threats. Leveraging cutting-edge technology and AI-driven analytics, Azure ATP provides a robust defense against malicious activities, helping you stay one step ahead of cyber adversaries. In this article, we will explore the key components of Azure ATP, along with its features and how it secures your cloud infrastructure.
Microsoft Entra ID Protection
Microsoft Entra ID Protection is a feature within the Microsoft Entra ID P2 edition, that offers a comprehensive view of risk detections and potential vulnerabilities that can impact your organization's identities. Leveraging existing Microsoft Entra anomaly-detection capabilities, available through Microsoft Entra Anomalous Activity Reports, this feature introduces new risk detection types capable of identifying real-time anomalies.
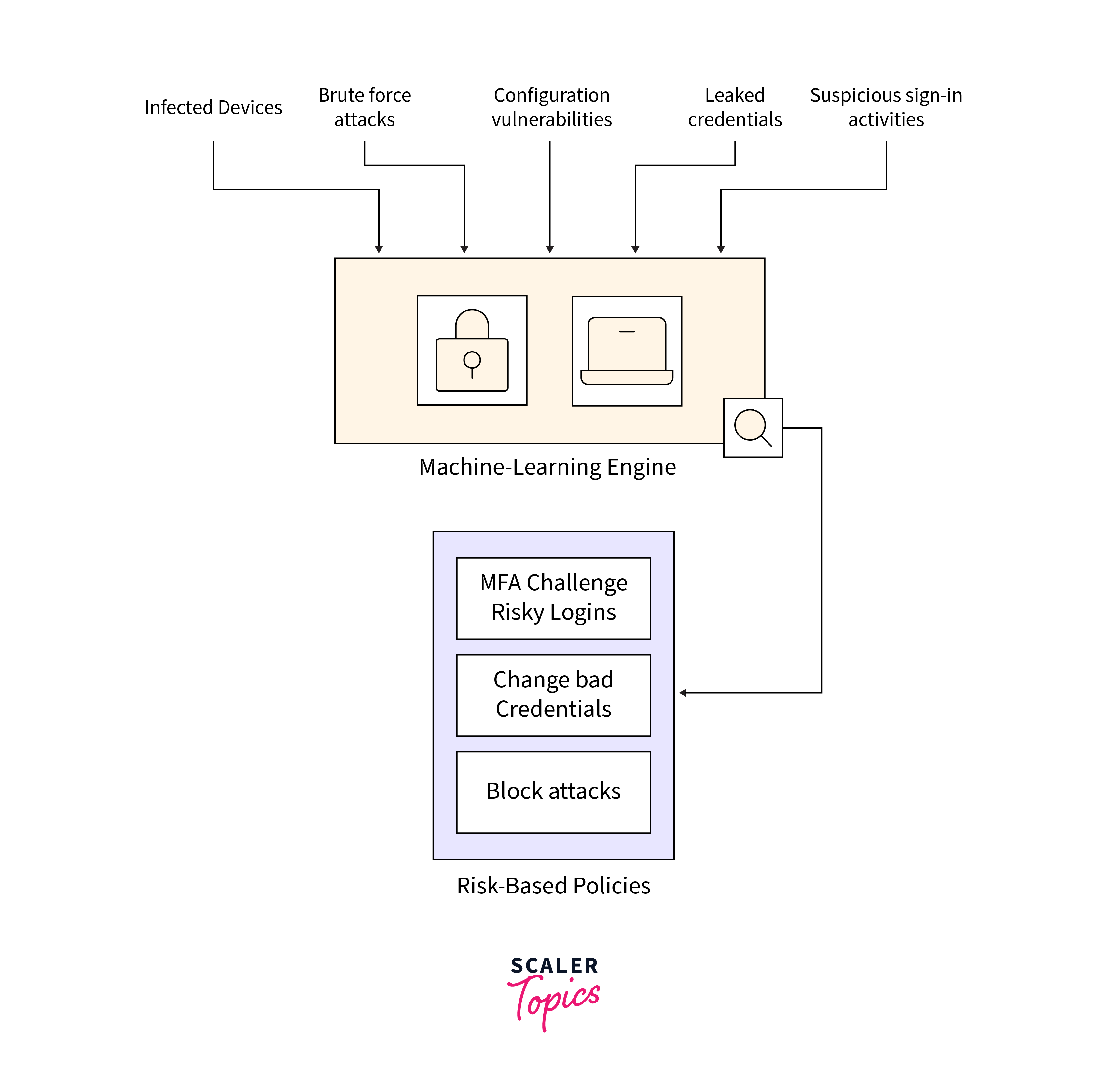
Utilizing adaptive machine learning algorithms and heuristics, Identity Protection actively identifies anomalies and risk detections that may signal a compromised identity. This information is then used to generate reports and alerts, enabling timely investigation and appropriate remediation measures.
Key Capabilities:
-
Risk Detection Types:
Microsoft Entra ID identifies six distinct risk detection types, enhancing the precision of threat identification. -
User Risk Level Calculation:
Calculates user risk levels, providing a clear assessment of potential vulnerabilities. -
Custom Recommendations:
It offers recommendations for overall security posture by pinpointing specific areas that require attention. -
Investigation Support:
Identity Protection facilitates thorough investigations by sending notifications for risk detections, providing contextual information for a deeper understanding, and offering workflows to track progress. -
Risk-Based Policies:
Organizations can configure risk-based policies that automatically respond to identified issues once a specified risk threshold is reached. -
Account Security:
The feature enables the blocking or securing of risky user accounts, and can also mandate users to register for multi-factor authentication, adding an extra layer of protection.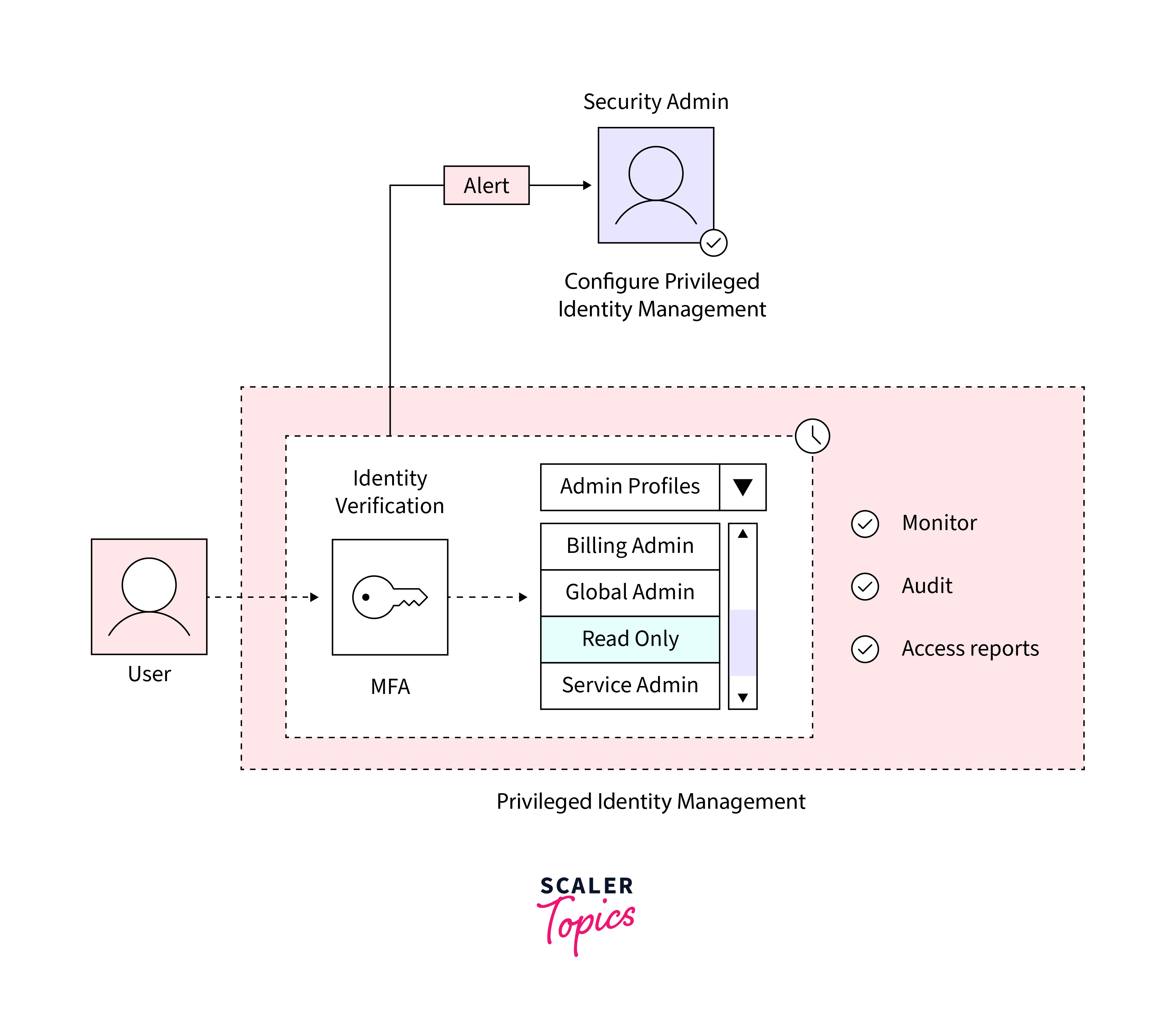
-
Microsoft Entra Privileged Identity Management (PIM) is used to effectively manage, control, and monitor access privileges within their ecosystem.
-
This feature extends its reach to resources not only within Microsoft Entra ID but also across other essential Microsoft online services like Microsoft 365 and Intune.
-
PIM offers a range of functionalities aimed at enhancing security and oversight.
-
It provides real-time alerts and detailed reports concerning Microsoft Entra administrators and Just-In-Time (JIT) administrative access to critical services.
Azure Monitor Logs
Azure Monitor logs are designed to oversee and safeguard both on-premises and cloud infrastructures, ensuring their efficient management and protection.
- Azure Monitor logs, in tandem with Microsoft Defender for Cloud, offer a comprehensive perspective into an organization's IT security posture.
- It provides pre-configured search queries targeting noteworthy issues, providing invaluable insight into the security status of computers within the network.
- This feature allows users to access event logs from the previous 24 hours, 7 days, or any other custom-defined time frame, ensuring that critical information is always at hand.
- Azure Monitor logs facilitate a quick assessment of the overall security posture within the context of IT operations.
Insight and Analytics
-
The Azure Monitor logs repository serves as the centralized hub for collecting data from various connected sources.
-
Users can configure data sources and integrate solutions into their subscriptions, each creating distinct record types with their own set of properties.
-
The Azure portal serves as the primary interface for interaction with Azure Monitor logs.
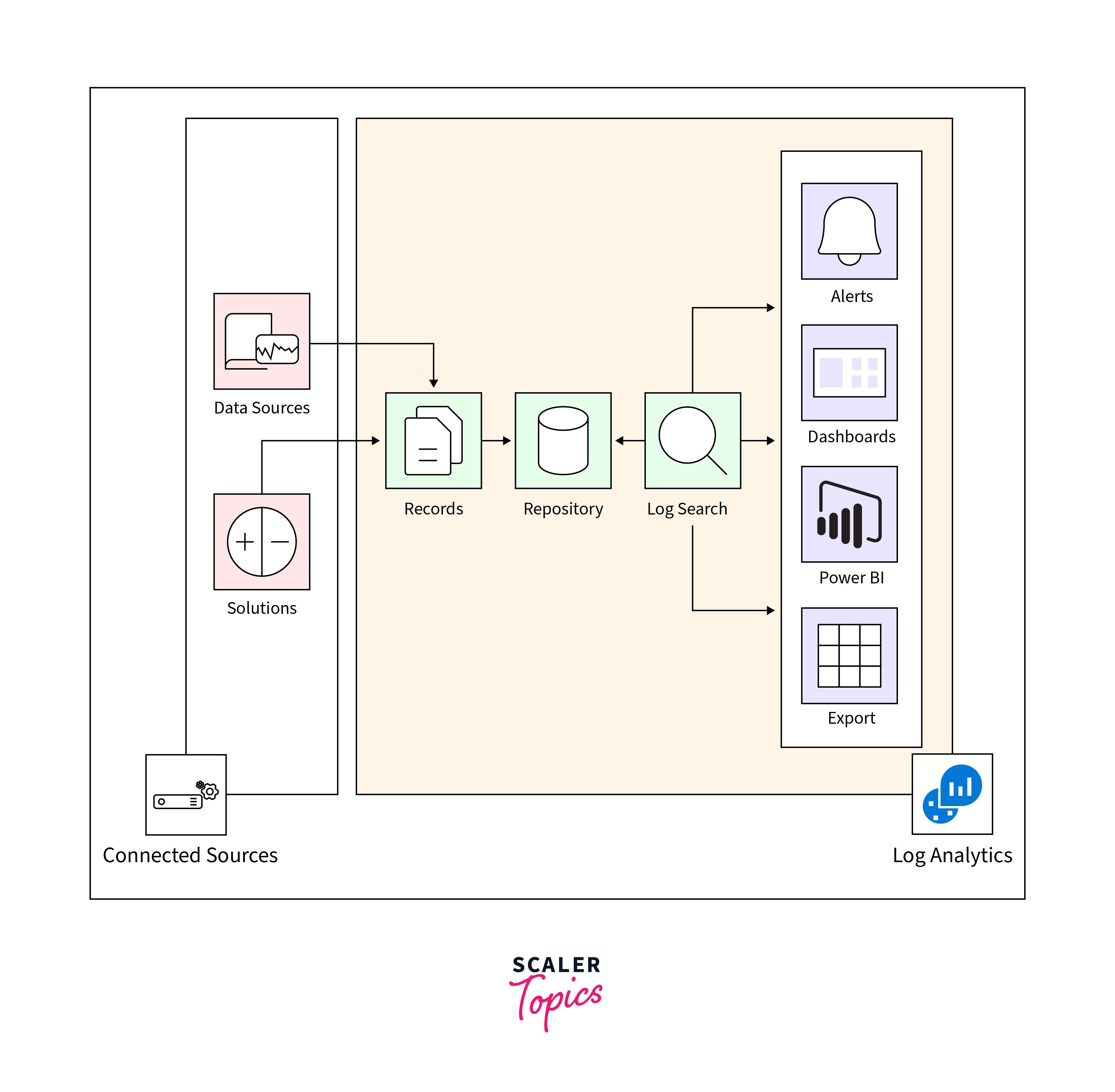
Users can engage in log searches, construct queries to dissect collected data, or customize dashboards to present graphical representations of critical information.
We can also automate alerting and control of security:
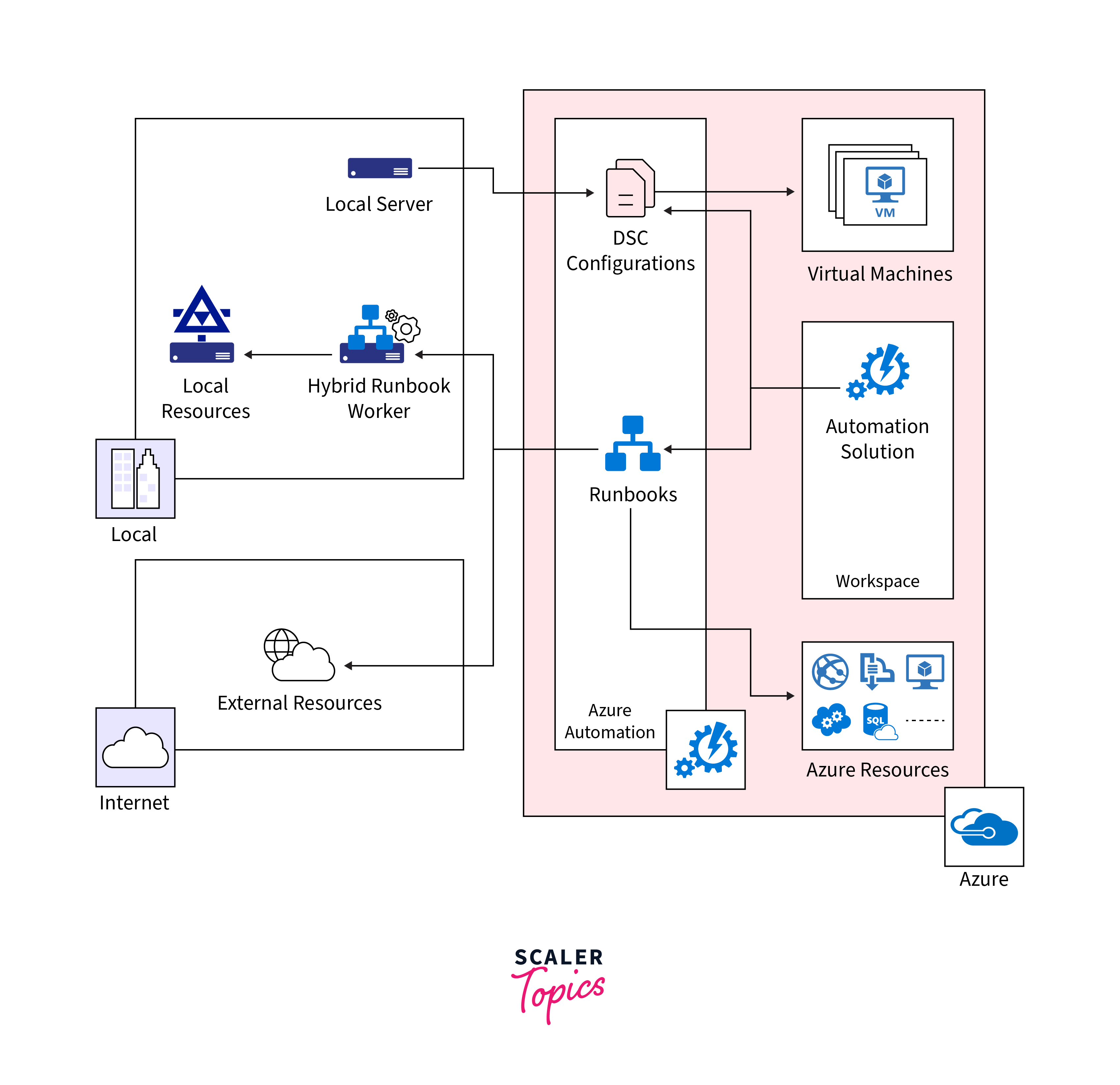
- Azure Automation takes automation to the next level with PowerShell, executed either in the cloud or on local servers.
- This capability enables the automation of administrative processes, providing extensive configuration management through PowerShell Desired State Configuration (DSC).
- Users can create and manage DSC resources hosted in Azure, applying them to both cloud and on-premises systems.
- This ensures that configurations are automatically enforced or reports are generated to highlight any drifts from established security policies, thereby maintaining a secure and compliant infrastructure.
Microsoft Defender for Cloud
-
Microsoft Defender for Cloud is a robust security solution designed to safeguard hybrid cloud environments and provide recommendations to address identified vulnerabilities.
-
These recommendations are based on the Microsoft cloud security benchmark, a set of Azure-specific best practices derived from widely recognized compliance frameworks.
-
By enabling Defender for Cloud's enhanced security features, organizations benefit from intelligent protection across Azure, hybrid, and multi-cloud resources.
-
Microsoft provides a workload protection dashboard, offering visibility and control over integrated cloud workload protection features. This includes capabilities from various Microsoft Defender plans.
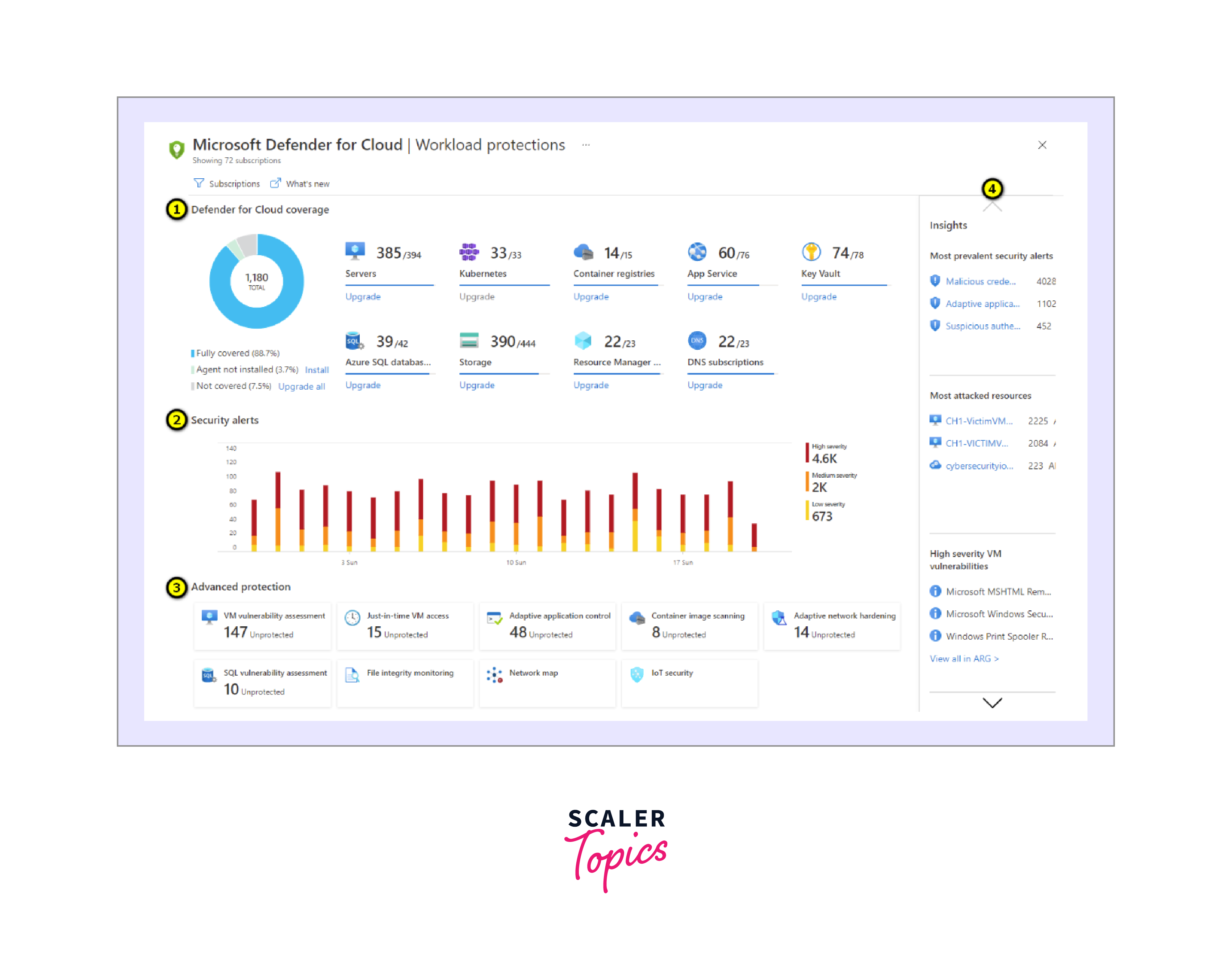
Microsoft's security researchers actively monitor global threat intelligence and maintain a rich dataset, ensuring Defender for Cloud can update its detection algorithms to address evolving threats and detect new attack patterns and trends.
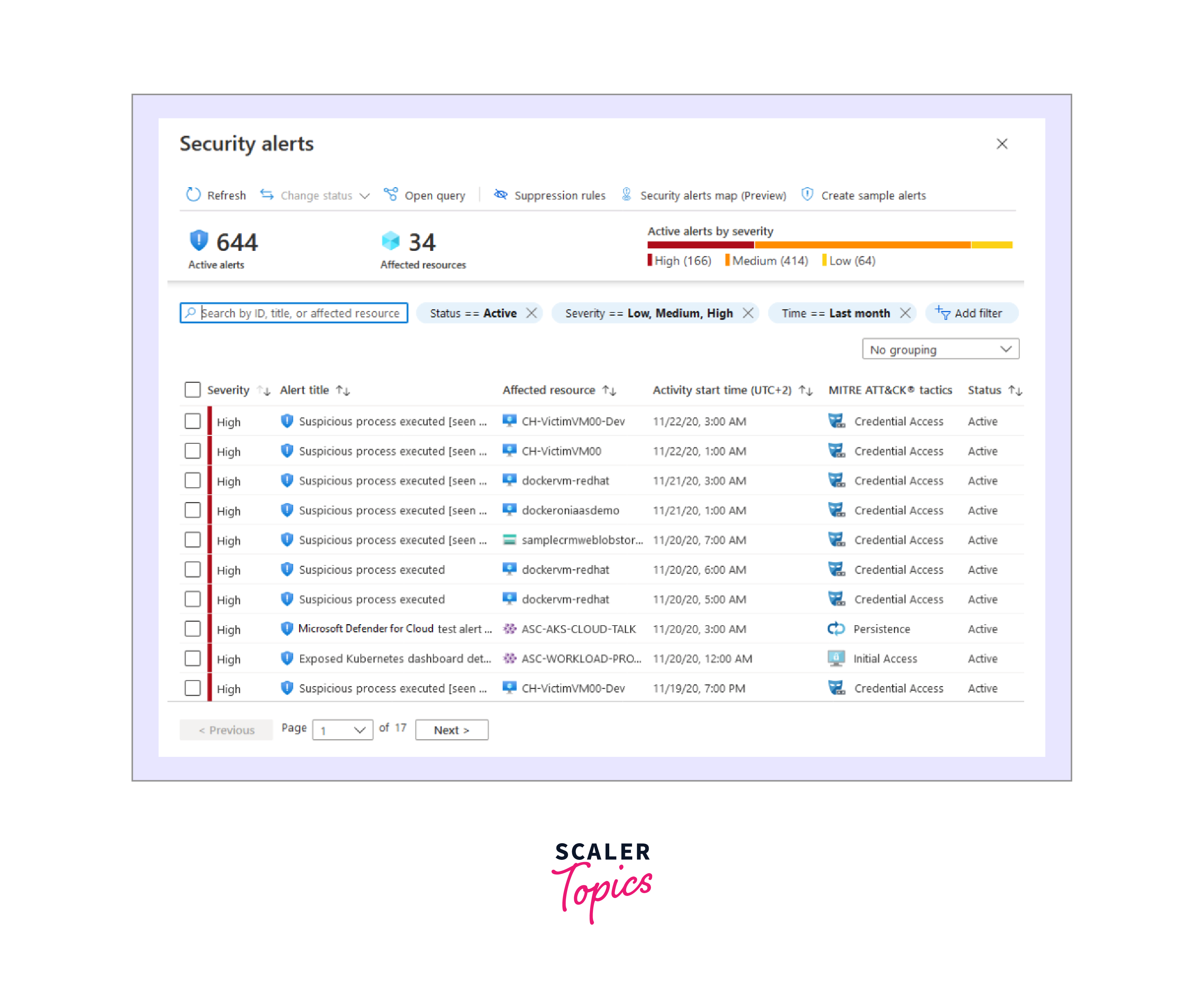
- Defender for Cloud automatically gathers security information from various sources, analyzing and correlating it to identify potential threats.
- It uses big data and machine learning technologies to evaluate events across the entire cloud, detecting threats that would be otherwise challenging to identify.
- It also uses behavioral analytics to identify compromised resources based on the analysis of various logs.
- It also utilizes anomaly detection and continuous threat intelligence monitoring, focusing on baselines specific to an organization's deployments.
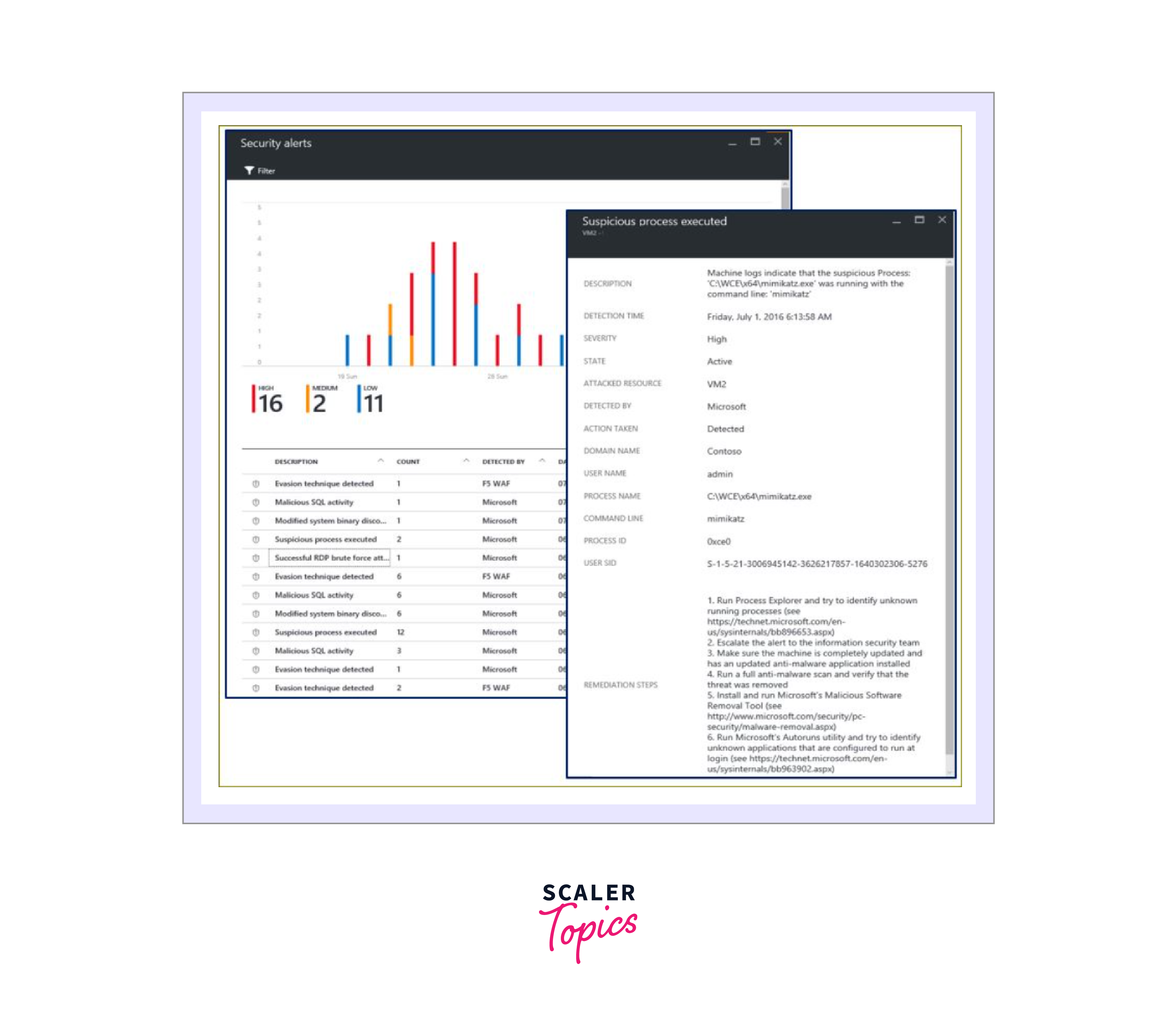
Microsoft also offers a complementary solution called Microsoft Defender for Storage. This Azure-native layer of security intelligence provides contextual security alerts for storage accounts, leveraging advanced threat detection capabilities and Microsoft Threat Intelligence data.
Threat Protection Features: Other Azure Services
Virtual Machines: Microsoft Antimalware
Microsoft Antimalware for Azure is a self-sufficient solution designed to operate in the background, ensuring continuous security for applications and tenant environments without human intervention.
Features:
- Monitors activities on cloud services and virtual machines to promptly detect and block malware execution.
- Conducts periodic targeted scans to identify actively running programs that may be malware.
- Automatically takes action upon detecting malware, including deleting or quarantining malicious files and cleaning up registry entries.
Azure SQL Database Threat Detection
Azure SQL Database Threat Detection is an integral security intelligence feature within Azure SQL Database, tirelessly working to identify anomalous activities and potential threats to the database.
Features:
- Security officers or designated administrators receive immediate notifications about in-depth details of the suspicious activity and recommendations for mitigation.
- Detection Methodologies:
- Deterministic Detection:
Identifies suspicious patterns in SQL client queries based on known attacks, offering high detection accuracy. - Behavioral Detection:
Detects abnormal behavior in the database by analyzing the most recent 30 days of activity, providing a dynamic approach to threat identification.
- Deterministic Detection:
Application Gateway Web Application Firewall
Application Gateway Web Application Firewall (WAF) provides enhanced protection to web applications against common web vulnerabilities. Protects web applications without modifying the back-end code, supports multiple web applications simultaneously, and provides real-time reports through application gateway WAF logs.
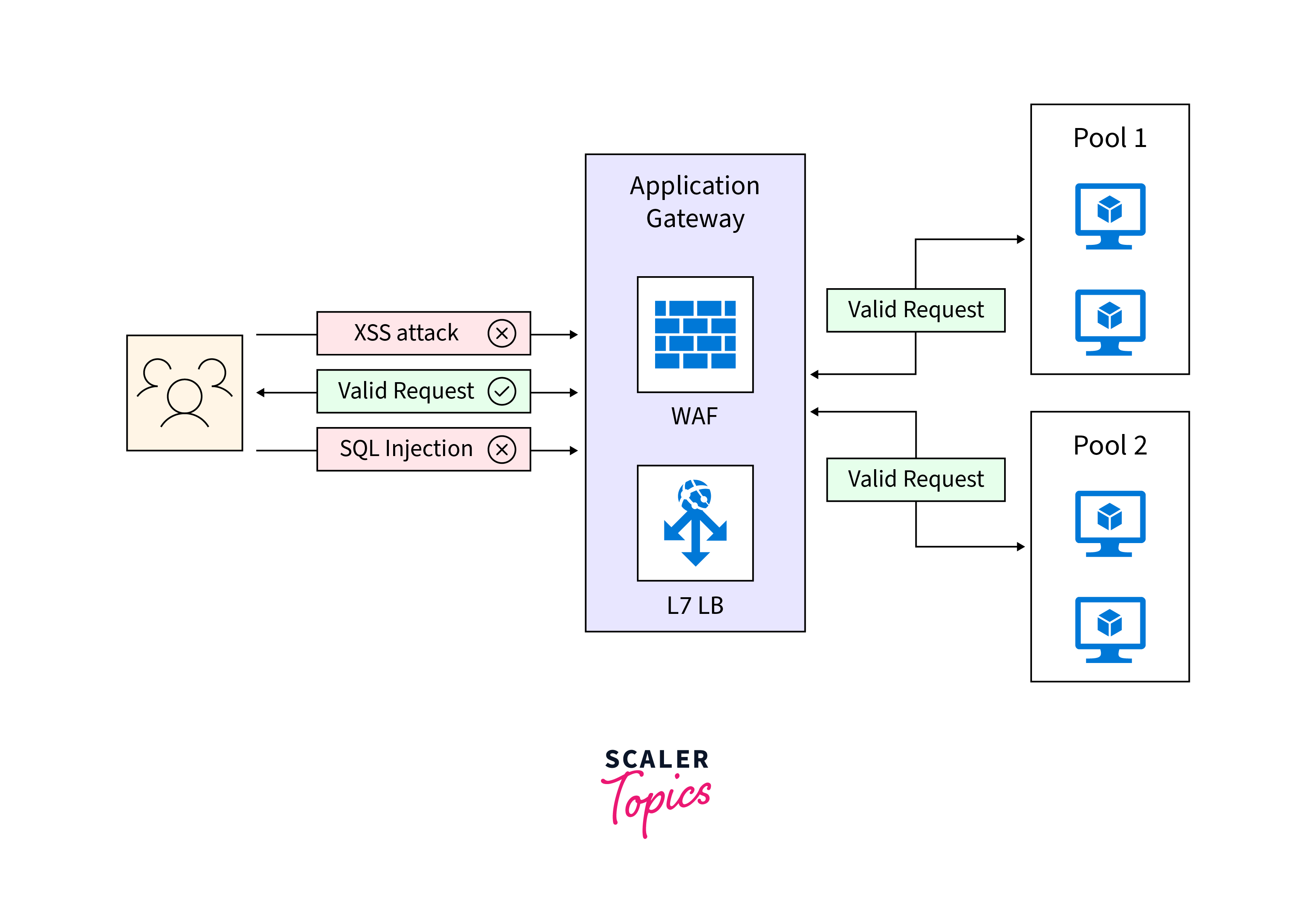
The protections include:
- SQL Injection and cross-site scripting Protection.
- Defense Against Common Web Attacks.
- HTTP Protocol Violations and Anomalies Protection.
- Prevention Against Bots, Crawlers, and Scanners.
- Detection of Application Misconfigurations.
Defender for Cloud Apps
Defender for Cloud Apps offers tools for organizations transitioning to cloud applications.
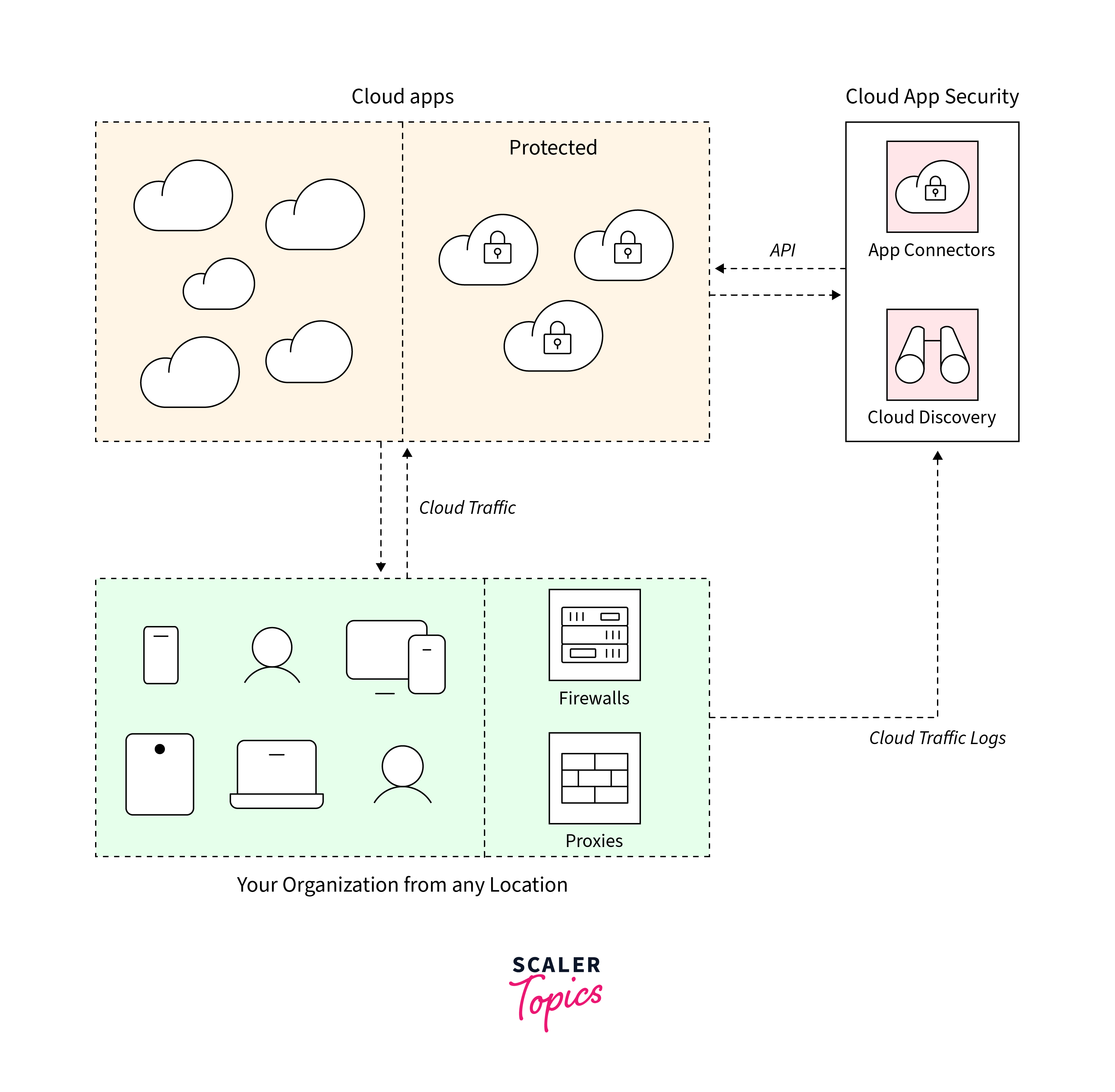
Capabilities:
- Discover:
Provides visibility into apps, activities, users, data, and files in the cloud environment. - Investigate:
Employs cloud forensics tools for in-depth analysis of risky apps, users, and files, generating reports for ongoing monitoring. - Control:
Mitigates risk by setting policies and alerts to govern network cloud traffic, facilitating migration to sanctioned cloud app alternatives. - Protect:
Enables sanctioning or prohibition of applications, enforces data loss prevention, controls permissions, and sharing, and offers custom reporting and alerts.
Third-party Threat Protection Capabilities Through the Azure Marketplace
Azure Marketplace provides the Web Application Firewall tool which inspects inbound web traffic, efficiently blocking various threats including SQL injections, cross-site scripting, malware uploads, and application-level DDoS attacks. This provides the following benefits:
- Defends against a range of threats, from SQL injections to malware uploads, bolstering application security.
- Empowers administrators with granular access control policies for authentication, authorization, and accounting (AAA).
- Scans outbound traffic for sensitive data, providing options to mask or block unauthorized dissemination.
- Enhances web application content delivery through caching, compression, and other optimization techniques.
Conclusion
- Azure ATP is a comprehensive security solution designed to safeguard cloud infrastructures against various cyber threats.
- Microsoft Entra ID Protection is a feature of Azure ATP that offers a detailed overview of risk detections and potential vulnerabilities impacting an organization’s identities.
- It uses adaptive machine learning algorithms to detect anomalies and potential compromises in identities, generating reports and alerts for timely action.
- Microsoft Defender for Cloud complements Azure ATP by continuously assessing connected resources and providing detailed security recommendations based on the Microsoft Cloud security benchmark.
- Azure Monitor logs serve as a cloud-based IT management solution, offering holistic security and compliance insights, and enabling streamlined security and compliance audit processes.
- Third-party threat protection capabilities available through Azure Marketplace, such as Web Application Firewall, provide additional layers of defense against a range of cyber threats.
- Azure SQL Database Threat Detection is a security intelligence feature built into Azure SQL Database, identifying potential threats and providing immediate notifications to administrators.
- Defender for Cloud Apps is a critical component of the Microsoft Cloud Security stack, offering tools to uncover shadow IT, assess risks, enforce policies, investigate activities, and stop threats.
