Azure Bastion Host
Overview
Azure Bastion is a fully managed service in Microsoft Azure that provides secure and convenient remote access to virtual machines (VMs) through the Azure Portal. It eliminates the need for exposing VMs to the public internet, enhances security with multi-factor authentication, and offers seamless RDP and SSH access from a web browser, simplifying remote administration while reducing the attack surface and operational complexities.
What is Azure Bastion?
Azure Bastion simplifies and enhances remote connectivity to virtual machines (VMs) by providing secure and seamless RDP and SSH access through the Azure Portal. It eliminates the need for a public IP address, RDP/SSH client configurations, and jump boxes, enhancing security and convenience for managing VMs in Azure. Think of it as a bridge that securely connects you to your VMs in the cloud.
Key Features
Azure Bastion provides several key features for secure remote access to virtual machines (VMs) in the Azure cloud:
- Secure Remote Connectivity:
Azure Bastion offers secure RDP and SSH connectivity to VMs directly from the Azure Portal. It eliminates the need for exposing VMs to the public internet, reducing attack surfaces and enhancing security. - No Public IP Required:
With Azure Bastion, there's no need to assign public IP addresses to individual VMs, which helps improve security by reducing exposure to the internet. - One-Click Access:
Users can initiate remote connections to VMs with a single click within the Azure Portal, streamlining the access process. This user-friendly approach simplifies remote management tasks. - No Public SSH Keys Required:
Users don't need to store or manage public SSH keys for secure access, simplifying the access process. - Multi-Factor Authentication (MFA):
Azure Bastion supports multi-factor authentication for an additional layer of security, requiring users to provide multiple proofs of identity. - Network Security Groups (NSGs):
Network Security Groups can be applied to Bastion Subnets, allowing fine-grained control over network traffic to and from Azure Bastion. - Private and Isolated Connectivity:
Azure Bastion leverages Virtual Network (VNet) peering and private IP addressing, ensuring private and isolated connectivity to VMs.
Benefits
Azure Bastion provides several benefits for managing and securing remote access to virtual machines (VMs in Azure):
- Enhanced Security:
Azure Bastion eliminates the need to expose virtual machines to the public internet. Instead, it provides a secure and hardened gateway to access your VMs over the Azure network, reducing the attack surface. - Simplified Remote Access:
Users can connect to virtual machines from anywhere using just a web browser. There's no need for a VPN client or complex network configurations, simplifying remote access for administrators and users. - Multi-Factor Authentication:
Azure Bastion supports multi-factor authentication (MFA), adding an extra layer of security to user logins and reducing the risk of unauthorized access. - Seamless Integration:
Bastion is tightly integrated with the Azure Portal, offering a consistent and user-friendly interface for managing virtual machines and accessing them through a single location. - No Public IP Addresses:
You can eliminate the use of public IP addresses for virtual machines, reducing exposure to potential attacks and helping maintain a more secure network architecture. - Auditing and Logging:
Bastion provides detailed audit and logging capabilities, making it easier to monitor and track remote access activities for compliance and security purposes. - Time and Cost Savings:
By simplifying remote access, reducing the need for VPNs or third-party solutions, and lowering the attack surface, Azure Bastion can save time and reduce operational costs.
Architecture of Azure Bastion
The architecture of Azure Bastion is designed to provide secure and convenient remote access to Azure virtual machines (VMs) while minimizing exposure to the public internet.
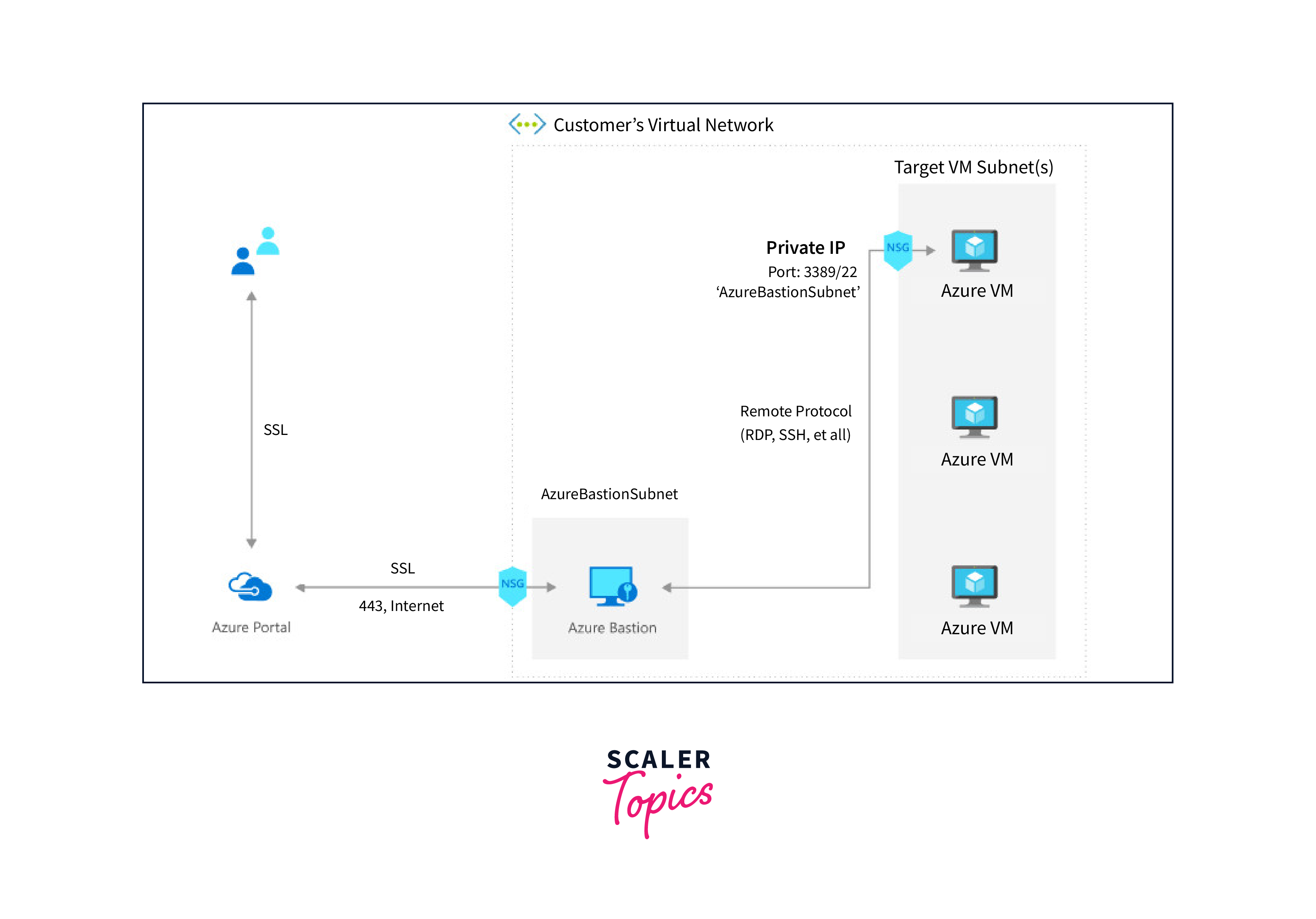
The connectivity with Azure Bastion works as follows:
- You initiate a connection by accessing the Azure management portal via HTTPS using any web browser.
- Within the portal, you select the virtual machine you want to connect to.
- The Azure portal establishes a connection to the Azure Bastion service using the private IP address on port 443.
- Once the connection is established, you receive a new session within your web browser. From this session, you can securely access the desktop of the selected virtual machine and any other VMs within your network using RDP or SSH protocols.
This process ensures secure, browser-based access to your virtual machines without exposing them to the public internet, enhancing both accessibility and security.
What is Host Scaling?
Azure Bastion offers host scaling, a feature that allows you to control the number of hosts (volumes) to manage the capacity of RDP/SSH connections that Azure Bastion can support. By increasing the number of hosts, you can enhance Azure Bastion's capacity to handle more traffic, accommodating a larger number of RDP and SSH connections. Conversely, reducing the number of hosts can limit the number of supported connections.
Azure Bastion Use Cases
Azure Bastion serves as a secure and convenient way to remotely access virtual machines in Azure. Here are some common use cases for Azure Bastion:
- Secure Remote Access:
Azure Bastion provides a secure way to remotely access virtual machines in your Azure environment using RDP or SSH over SSL/TLS encryption. It eliminates the need to expose virtual machines to the public internet, enhancing security. - Remote Management:
IT administrators and support teams can use Azure Bastion to manage and troubleshoot virtual machines without the need for a VPN connection. This simplifies remote management tasks. - Zero Public IP:
Azure Bastion eliminates the requirement for assigning public IP addresses to virtual machines. This helps in reducing the attack surface and managing IP address allocations. - Multi-VM Connectivity:
It allows you to connect to multiple virtual machines within the same virtual network without the need for separate public IP addresses or complex network configurations.
Pricing
Azure Bastion has pricing based on the usage of the service.
- Standard SKU Pricing:
$0.095 per hour per Bastion host: This covers the deployment of a Bastion host, and it allows for an unlimited number of connections. Note that the price is based on the provisioned Bastion host, not the number of connections. - Data transfer charges:
Data transfer out of Azure Bastion is subject to standard data transfer rates. - Preview SKU Pricing:
During the preview phase, Azure Bastion is offered at a reduced price of $0.0375 per hour per Bastion host.
Configuration
Configuring Azure Bastion involves several steps to set up the service. Here's a high-level overview of the configuration process for Azure Bastion:
-
Prerequisites:
- Ensure you have an Azure subscription. You'll need appropriate permissions to create and configure resources.
- Determine the Azure Virtual Network in which you want to deploy Azure Bastion.
-
Create an Azure Bastion Service:
- In the Azure Portal, navigate to the Azure Bastion service, and create a new Azure Bastion instance.
-
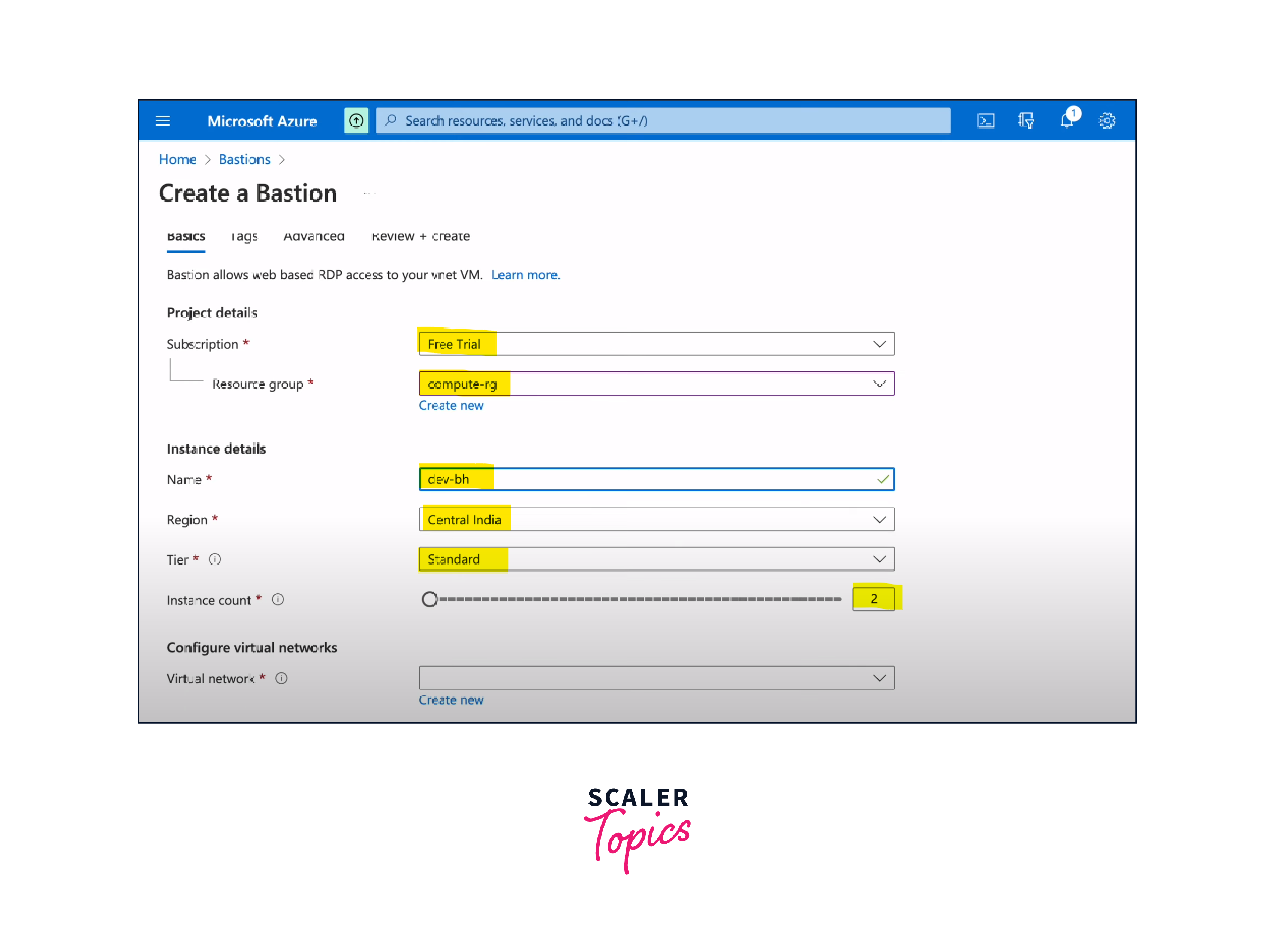
Basic Configuration:
- Provide a name for the Azure Bastion instance.
- Choose the Virtual Network in which you want to deploy Azure Bastion.
- Configure the subnet within the selected Virtual Network for Azure Bastion.
-
Public IP Address:
- Azure Bastion requires a public IP address. You can create a new one or use an existing one.
- Configure the name for the public IP address and other settings as needed.
-
Review + Create:
- Review your settings to ensure they are accurate.
- Click "Create" to provision the Azure Bastion service.
Connecting to VM
After you've successfully configured Azure Bastion, you can connect to virtual machines securely. Here's how you can do it:
-
Navigate to Azure Bastion:
In the Azure Portal, navigate to the Azure Bastion service you've created. -
Select a Virtual Machine:
From the Azure Bastion service, select the virtual machine you want to connect to. -
Initiate Connection:
Click on the "Connect" button to initiate the connection.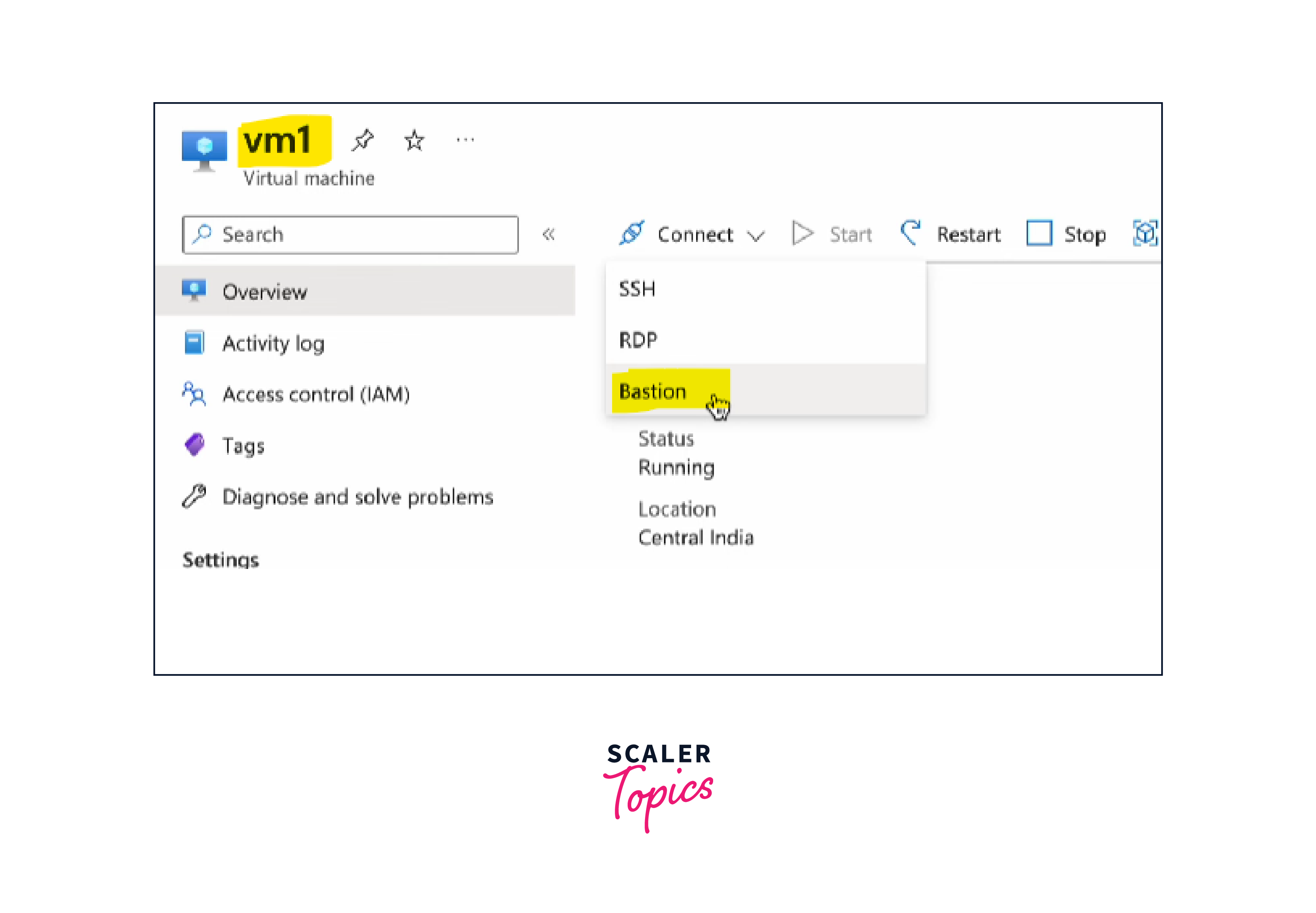
-
Authenticate:
You'll be prompted to provide your Azure Active Directory (Azure AD) credentials for authentication.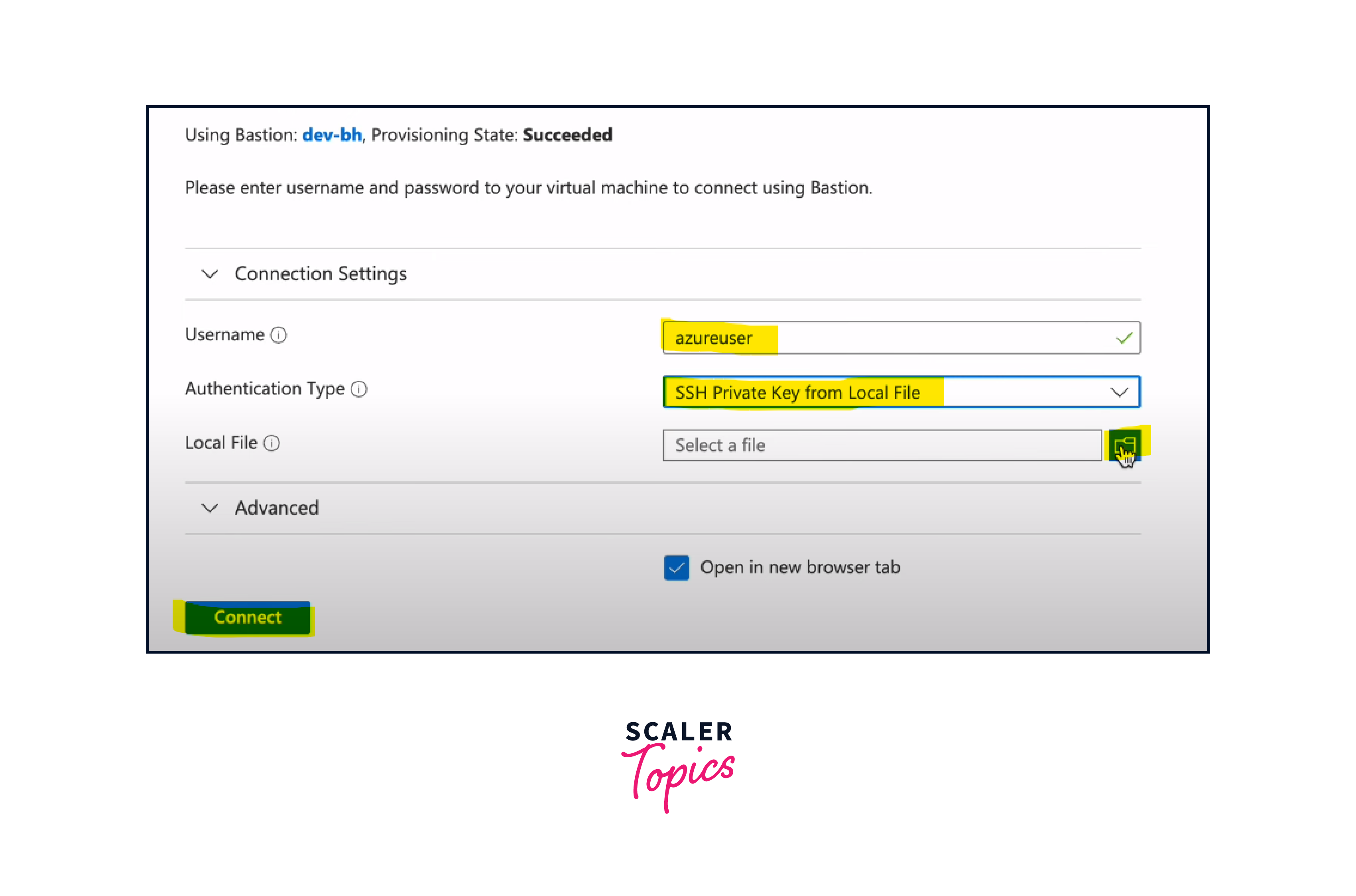
-
Secure Access:
Once authenticated, you'll gain secure access to the virtual machine through your browser. The RDP or SSH session is established through Azure Bastion.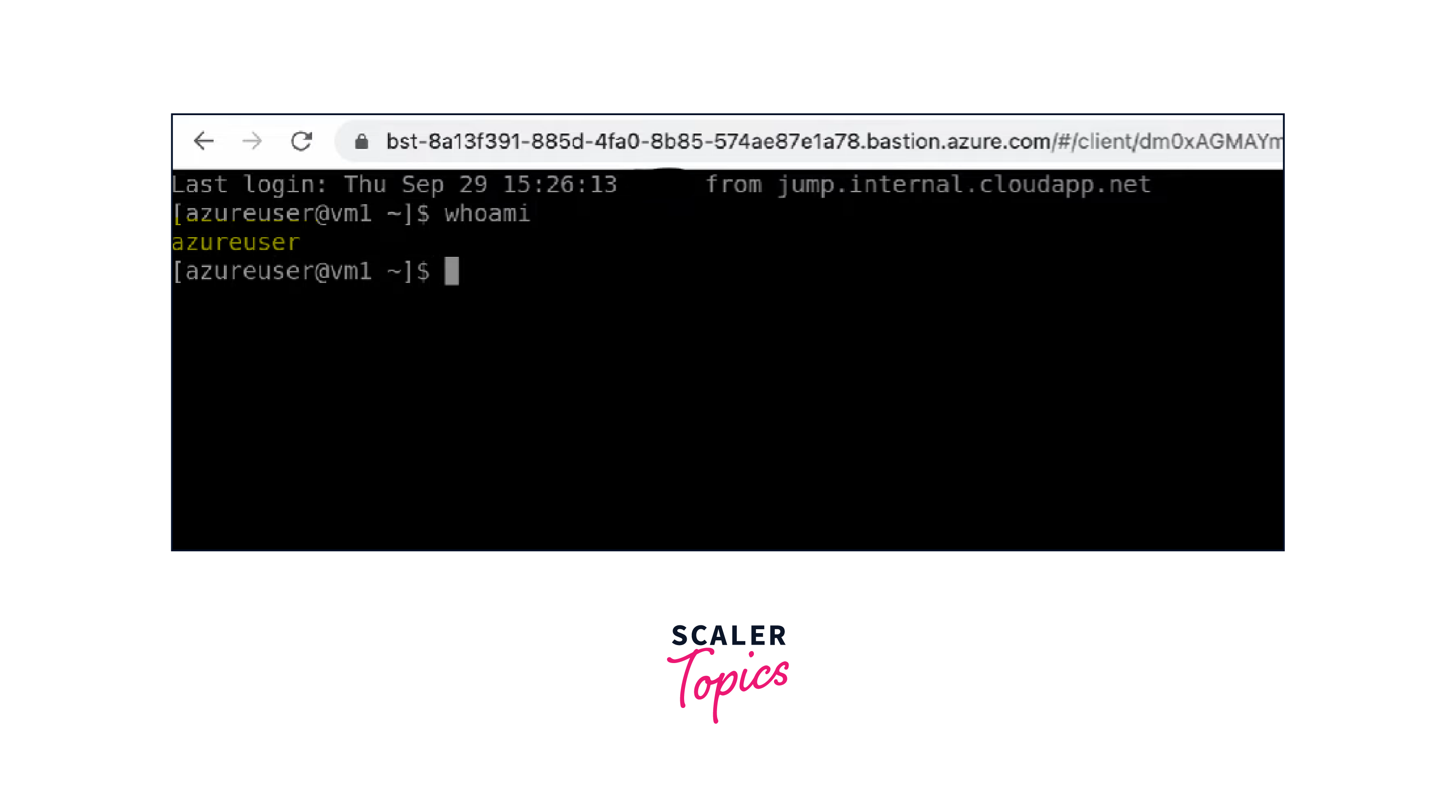
-
Access Control and Network Security Groups (NSGs):
You can further enhance security by configuring Network Security Groups (NSGs) to control traffic to and from Azure Bastion and your virtual machines. -
Log Out:
After you've finished your session, it's essential to log out and close the connection.
FAQs
Q. What is Azure Bastion used for?
A. Azure Bastion is used for secure remote access to Azure Virtual Machines through the Azure Portal, providing RDP and SSH access without exposing VMs to the public internet.
Q. How does Azure Bastion enhance security compared to traditional methods?
A. Azure Bastion offers secure, browser-based access that eliminates the need to open RDP or SSH ports. It leverages Azure AD for authentication and enforces multi-factor authentication (MFA) for added security.
Q. Is Azure Bastion available for all Azure VM sizes and SKUs?
A. Azure Bastion is available for most Windows and Linux VM sizes and SKUs, making it a versatile solution for accessing a wide range of virtual machines.
Conclusion
- Azure Bastion is a fully managed service that provides secure and seamless remote access to Azure Virtual Machines via the Azure Portal.
- Azure Bastion's architecture involves connecting to the Azure management portal, which then establishes a secure connection to the Azure Bastion service over HTTPS, allowing users to access VMs via RDP or SSH.
- Host scaling in Azure Bastion Standard SKU allows configuring the number of hosts to control the supported RDP/SSH connections, with support for up to 50 hosts.
- Azure Bastion is used for secure remote access to Azure VMs, enabling secure administration, troubleshooting, and maintenance tasks without exposing VMs to the public internet.
