Azure Compute Services
Overview
Azure Compute Service is a cloud computing platform by Microsoft Azure, providing scalable and flexible solutions for running applications and workloads. It offers various services, including Virtual Machines (VMs) for running Windows or Linux-based applications, Azure Functions for serverless computing, and Azure App Service for hosting web and mobile apps. Azure Kubernetes Service (AKS) enables containerized application deployment, while Azure Batch manages large-scale parallel and high-performance computing tasks. Azure Compute Service empowers developers and organizations to build, deploy, and manage applications with ease, ensuring high availability, performance, and cost-efficiency in the cloud environment.
Prerequisites
To make the most of Azure Compute services and effectively utilize the cloud computing capabilities, there are certain prerequisites and considerations that users should be aware of:
- Azure Subscription:
Users must have an active Azure subscription to access Azure Compute services. Azure offers a range of subscription options, including free trial subscriptions for exploration and testing. - Understanding of Cloud Computing:
A basic understanding of cloud computing concepts, such as virtualization, scalability, and resource provisioning, is beneficial. Familiarity with cloud service models (IaaS, PaaS, SaaS) and cloud deployment models (public, private, hybrid) can help users make informed decisions while using Azure Compute. - Networking Knowledge:
Knowledge of networking principles, such as virtual networks, subnets, IP addressing, and security groups, is essential for setting up and managing virtual machines and other compute resources in Azure. - Operating Systems:
Depending on the specific compute service chosen, familiarity with Windows and/or Linux operating systems can be advantageous for configuring and managing virtual machines and containers. - Resource Management and Security:
Understanding resource groups, access controls, and RBAC (Role-Based Access Control) in Azure is crucial for effective resource management and securing compute resources. - Monitoring and Logging:
Knowledge of Azure monitoring and logging services enables users to track the performance and health of their compute resources effectively. - Azure Portal and Azure CLI:
Familiarity with the Azure portal (web-based user interface) and Azure CLI (Command-Line Interface) simplifies resource provisioning, management, and automation tasks. - Automation and Scripting:
Proficiency in scripting languages like PowerShell, Bash, or Python can be beneficial for automating deployment and management tasks. - Application Architecture:
Understanding the architecture and components of the applications to be deployed on Azure Compute services helps in selecting the appropriate service and optimizing resource utilization. - Budget and Cost Management:
Being mindful of costs and budgeting is crucial, especially when using pay-as-you-go or consumption-based pricing models. Understanding pricing options, cost management tools, and resource utilization patterns can lead to cost optimization.
Azure Compute Options
Azure offers a diverse range of compute options to cater to different application workloads and scenarios. Each option provides unique features and capabilities, empowering users to choose the most suitable option for their specific needs:
Certainly! Let's expand the comparison table to include more Azure compute services. Here are additional services: Azure Batch, Azure Container Instances, and Azure Logic Apps.
| Azure Compute Service | Key Features | Use Cases |
|---|---|---|
| Azure Virtual Machines | - Scalable virtualization with full control over OS and software | - Hosting applications and services in a customizable, isolated environment |
| - Support for Windows and Linux VMs with various sizes | - Running Windows or Linux-based applications and workloads with specific OS requirements | |
| - Persistent storage with managed disks | - Development and testing environments for applications before deployment | |
| - Integration with Azure networking | - High-performance computing tasks with specific hardware requirements | |
| Azure Functions | - Event-driven serverless compute with pay-as-you-go pricing | - Building small, stateless, and event-driven functions for quick, short-lived tasks |
| - Supports multiple programming languages | - Automation and workflows that require no server management | |
| - Easily integrates with other Azure services and third-party services | - Scalable backend for mobile and web applications | |
| - Automatic scaling and triggers based on events | - Real-time data processing and analytics | |
| Azure App Service | - Platform-as-a-Service (PaaS) offering for web and mobile apps | - Creating and deploying web applications, APIs, and mobile app backends |
| - Supports multiple programming languages | - Continuous deployment and integration for web applications | |
| - Integrated with Azure DevOps and Visual Studio | - Mobile app hosting and backend development | |
| - Managed infrastructure with automatic patching and updates | - Easy integration with Azure SQL Database and other Azure services for seamless development and deployment of applications | |
| Azure Kubernetes Service (AKS) | - Managed Kubernetes container orchestration service | - Deploying, managing, and scaling containerized applications |
| - Automatic updates and scaling for worker nodes | - Microservices architecture and application modernization | |
| - Integrates with Azure Monitor and Azure Active Directory | - High availability and fault tolerance for applications | |
| - Supports deploying Helm charts and Azure Dev Spaces for development and testing | - CI/CD workflows for containerized applications | |
| Azure Batch | - High-performance computing for large-scale parallel and batch workloads | - Rendering and transcoding of multimedia files |
| - Automatic scaling and resource management | - Genome sequencing and other scientific computations | |
| - Integrates with Azure Virtual Machines, Docker, and other services | - Distributed data processing and analytics | |
| Azure Container Instances | - Easily run containers without managing underlying infrastructure | - Rapid deployment and testing of containerized applications |
| - Quick scaling and automatic OS updates | - Short-lived, burstable workloads | |
| - Supports Linux and Windows containers | - Microservices testing and development | |
| Azure Logic Apps | - Low-code workflow automation service | - Integration of various apps and services through connectors |
| - Pre-built templates and visual designer for creating workflows | - Real-time data synchronization and event-driven workflows | |
| - Integration with Azure services, SaaS applications, and on-premises systems | - Notification and alerting systems | |
| - Event-driven execution based on triggers | - Business process automation | |
| Azure Security Center | - Threat detection and prevention | - Monitoring and securing cloud resources |
| - Security policy management | - Identifying and responding to security threats | |
| - Vulnerability assessment and management | - Compliance management and reporting | |
| - Advanced threat protection | - Continuous security monitoring and assessment | |
| - Regulatory compliance tracking | - Securing hybrid environments | |
| - Security recommendations and best practices | - Incident investigation and response | |
| Azure Active Directory | - Identity and access management | - Single sign-on (SSO) for applications |
| (Azure AD) | - Multi-factor authentication (MFA) | - User and group management |
| - Conditional access policies | - Secure remote access | |
| - Identity protection and risk assessment | - Application and API authorization | |
| - Seamless integration with SaaS applications | - B2B and B2C identity scenarios | |
| - Hybrid identity management | - Security and compliance reporting | |
| Azure Key Vault | - Securely store and manage keys, secrets, and certificates | - Storing encryption keys and secrets |
| - Centralized key management | - Protecting sensitive information | |
| - Hardware security module (HSM) integration | - Azure Disk Encryption and VM encryption | |
| - Role-based access control | - Securely accessing and distributing secrets | |
| - Auditing and logging | - Integrating with applications and services | |
| - Key rotation and versioning | - Compliance with security standards and policies |
| Azure Virtual Desktop: | |
|---|---|
| Definition | Cloud-based service by Microsoft Azure for creating virtualized desktops and applications in the cloud. |
| Key Benefits | |
| Cost-Efficiency | Reduce hardware and maintenance costs. |
| Scalability | Quickly scale up/down virtual desktops and applications. |
| Security | Robust security features, data encryption, compliance certifications. |
| Ease of Management | Centralized management through Azure Portal. |
| Access Anywhere | Access from various devices and locations. |
| Compatibility | Support for a wide range of applications and legacy software. |
| Windows 10 Multi-Session | Multiple users share a single Windows 10 virtual machine. |
| Use Cases | |
| Remote Work | Enable secure remote work scenarios. |
| Bring Your Own Device (BYOD) | Deliver virtual desktops to personal devices while maintaining security. |
| Business Continuity | Ensure work continuity during unexpected events. |
| Software Development and Testing | Provision virtual machines for development and testing purposes. |
| Temporary or Seasonal Workers | Provide virtual desktop access for temporary workers. |
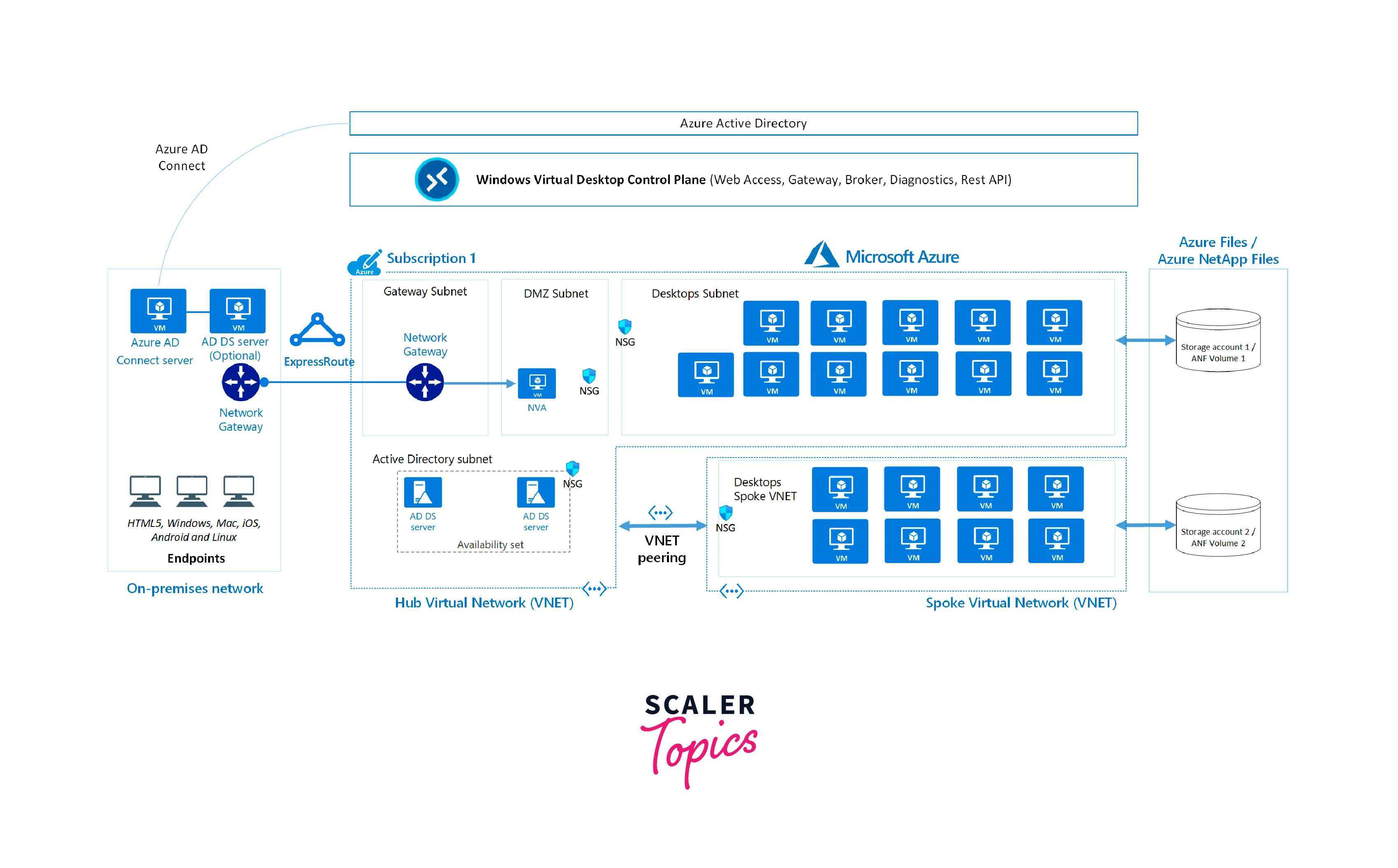
How Azure Virtual Desktop Enables Virtualized Desktops and Applications:
- Virtual Machine Management:
Azure Virtual Desktop allows organizations to create and manage virtual machines that host the desktops and applications. These virtual machines run on Azure infrastructure, providing the necessary computing power and resources. - Image Management:
Administrators can create customized virtual machine images with pre-installed applications and configurations. These images can be used to deploy multiple virtual desktops quickly and consistently. - Session Virtualization:
With Windows 10 Multi-Session, multiple users can share a single virtual machine, making efficient use of resources while providing individual user experiences. - RemoteApp:
Azure Virtual Desktop supports RemoteApp, which allows applications to be virtualized and delivered to end-users directly, without presenting an entire desktop. - Gateway and Client Access:
Azure Virtual Desktop provides a Gateway service that handles secure connections from the internet to the virtual desktops and applications. Users can access their virtual resources through the Azure Virtual Desktop client or HTML5 web client.
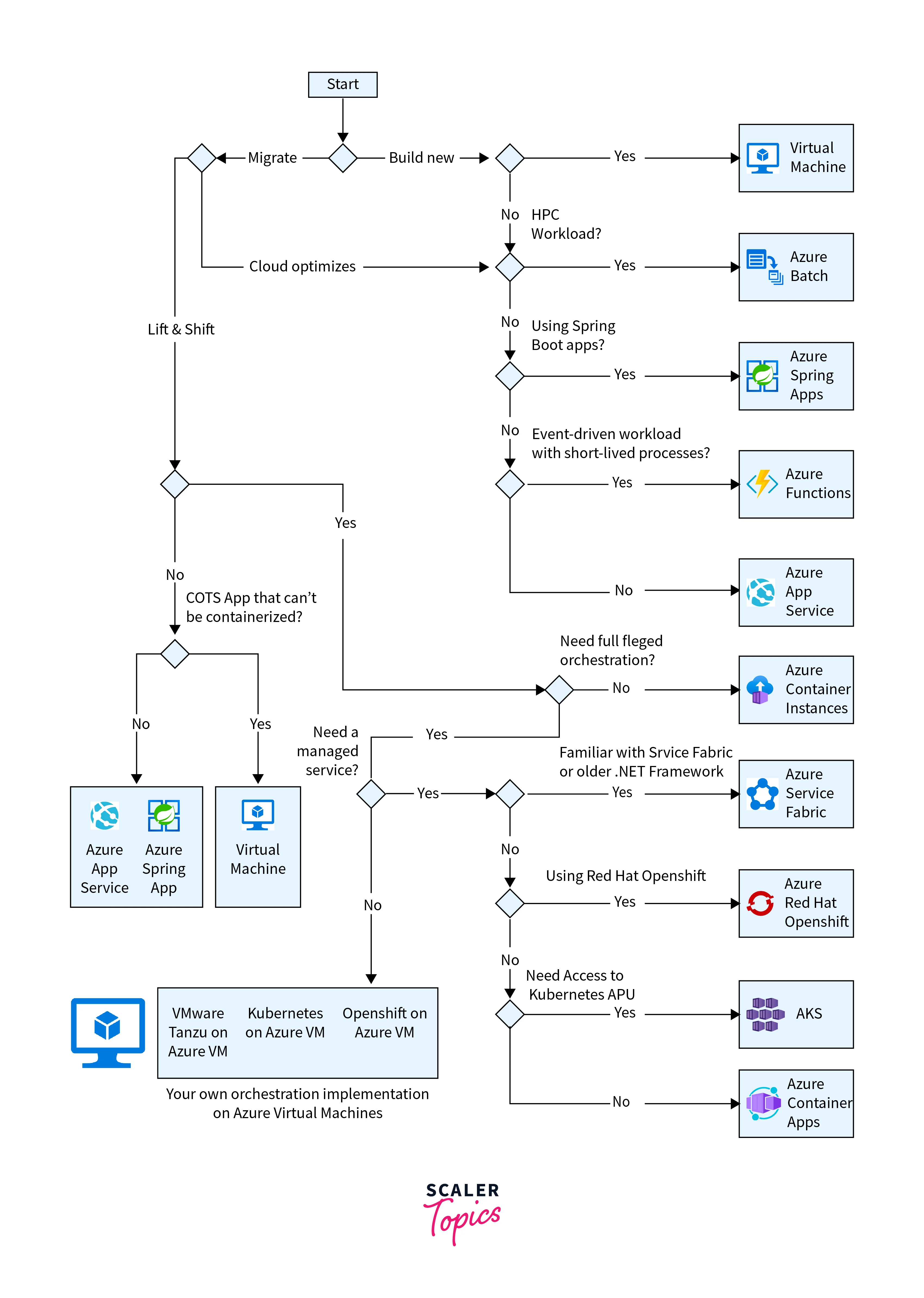
Three Key Services Are Associated with Azure Compute Service
Azure Security Center
Azure Security Center is a cloud security solution provided by Microsoft Azure that helps organizations strengthen their security posture and protect their cloud resources from threats and vulnerabilities. It serves as a central hub for monitoring, managing, and responding to security-related issues across Azure resources. Azure Security Center offers a range of features and capabilities designed to enhance cloud security and enable proactive threat detection and remediation.
Key features of Azure Security Center include:
- Security Policy Management:
Azure Security Center allows organizations to define and enforce security policies to ensure compliance with industry standards and regulatory requirements. Users can create custom security policies or use built-in policies tailored to specific frameworks, such as Azure CIS (Center for Internet Security) benchmarks or GDPR (General Data Protection Regulation) compliance. - Continuous Security Assessment:
The service continuously assesses the security of Azure resources, including virtual machines, databases, storage accounts, and more. It identifies security misconfigurations, vulnerabilities, and potential threats, providing actionable recommendations to remediate issues and improve overall security. - Threat Detection and Monitoring:
Azure Security Center employs advanced analytics and machine learning to detect suspicious activities and potential threats in real-time. It can identify indicators of compromise and abnormal behaviors, helping organizations proactively respond to security incidents.
Active Directory
Active Directory (AD) is a directory service developed by Microsoft that provides centralized management and authentication services for Windows-based network environments. It serves as a critical component of the Microsoft Windows Server operating system and is widely used in enterprise environments to efficiently manage user accounts, resources, and security policies.
Key features and functionalities of Active Directory include:
- User Authentication and Single Sign-On (SSO):
Active Directory allows users to log in to the network using their unique credentials (username and password). Once authenticated, users can access various resources, applications, and services without the need to provide credentials repeatedly, thanks to Single Sign-On (SSO) functionality. - User and Group Management:
AD enables administrators to create, manage, and organize user accounts and groups in a hierarchical structure. Grouping users simplifies the assignment of permissions and access rights to network resources, promoting effective resource management. - Domain Services:
Active Directory operates in a domain-based model, where each domain represents a logical group of network resources and users. Domains provide a boundary for security and administrative purposes and allow for delegation of administrative tasks.
Key Vault
Key Vault is a secure and centralized cloud service provided by Microsoft Azure that enables users to safeguard, manage, and control access to cryptographic keys, secrets, and certificates used in cloud applications and services. It serves as a dedicated repository for managing sensitive information, allowing organizations to store and access cryptographic keys and secrets securely. Key Vault plays a crucial role in enhancing the security of cloud applications and data by providing a robust and scalable solution for managing cryptographic materials.
Key features and functionalities of Azure Key Vault include:
- Key Management:
Key Vault allows users to create, import, and manage cryptographic keys used for encryption, decryption, and digital signatures. It supports various types of keys, including software-protected keys and Hardware Security Module (HSM)-backed keys for enhanced security. - Secret Management:
Key Vault enables the secure storage and retrieval of secrets, such as connection strings, passwords, API keys, and other sensitive information. Secrets are encrypted at rest and can be rotated periodically to minimize security risks. - Certificate Management:
Key Vault allows users to store and manage X.509 certificates used for SSL/TLS termination, code signing, and authentication. It supports automated certificate renewal, simplifying the management of certificates with shorter lifetimes.
Conclusion
- Azure Key Vault is a secure cloud service for managing cryptographic keys, secrets, and certificates in Azure.
- It provides key management functionalities, supporting various types of keys and Hardware Security Module (HSM)-backed keys.
- Key Vault offers secure secret storage and retrieval, enabling the management of sensitive information like passwords and API keys.
- It facilitates the management of X.509 certificates for SSL/TLS termination and code signing.
- Key Vault integrates with Azure RBAC for fine-grained access control and provides monitoring and auditing capabilities.
- With its seamless integration with Azure services and client libraries, Key Vault enhances the security and compliance of cloud applications.
