Azure Container Registry
Introduction
In the ever-evolving landscape of cloud computing, containerization has emerged as a powerful tool for developers and IT professionals alike. Azure Container Registry (ACR) stands as a key player in this ecosystem, providing a seamless and efficient solution for managing container images. Let's delve into the world of Azure Container Registry, exploring its key concepts, features, use cases, best practices, and pricing tiers.
What is Azure Container Registry
 Azure Container Registry is a fully managed private registry service offered by Microsoft Azure. It serves as a central hub for storing, managing, and deploying container images in a secure and scalable manner. ACR enables organizations to streamline their container workflows, ensuring reliable and fast access to containerized applications.
Azure Container Registry is a fully managed private registry service offered by Microsoft Azure. It serves as a central hub for storing, managing, and deploying container images in a secure and scalable manner. ACR enables organizations to streamline their container workflows, ensuring reliable and fast access to containerized applications.
A cloud-based solution for managed, private registries built on Docker Registry 2.0 is called Azure Container Registry (ACR). It may be used to manage and store Docker images and artifacts in private by setting up and maintaining Docker container registries in the Azure cloud.
Existing pipelines for developing and deploying container-based applications can be integrated with ACR. Azure Container Registry Tasks can be used to produce a container image in Azure. With triggers like base-image updates and source code commits, you may fully automate your builds or create images on demand.
Key Concepts
Key features of Azure Container Registry include:

- Private Registry: ACR provides a private registry for storing container images. This ensures that only authorized users and systems have access to the stored images, enhancing the security of containerized applications.
- Integration with Azure Services: ACR seamlessly integrates with other Azure services, facilitating the deployment of containerized applications on Azure Kubernetes Service (AKS) or Azure Container Instances (ACI). This integration promotes a cohesive and efficient cloud-native development environment.
- Geo-replication: ACR supports the replication of container images across multiple Azure regions. This feature improves the availability and performance of containerized applications by allowing users to deploy from a geographically closer registry.
- Role-Based Access Control (RBAC): ACR incorporates RBAC to manage access and permissions for different users and groups. This ensures that only authorized individuals can push, pull, or manage container images within the registry.
- Webhooks: ACR supports webhooks, enabling automation and integration with continuous integration and continuous deployment (CI/CD) pipelines. Webhooks can trigger events such as image pushes, allowing for automated workflows based on changes to the container images.
- Scalability: With Azure Container Registry, users can scale their container image storage and retrieval needs based on demand. This scalability is crucial for organizations with dynamic workloads and evolving containerized applications.
Overall, Azure Container Registry simplifies the management of container images in the cloud, supporting secure and efficient containerized application deployment. It is a valuable tool for organizations adopting containerization and orchestrating containerized workloads in Azure environments.
Features
Network Security with Virtual Network Service Endpoints:
ACR supports Virtual Network Service Endpoints, allowing users to secure their container registry by restricting access to a specific virtual network or set of IP addresses. This enhances network security and reduces the exposure of the registry to the public internet.
- Azure CLI and Azure PowerShell Support: ACR is accessible and manageable through the Azure Command-Line Interface (CLI) and Azure PowerShell. This provides flexibility for users who prefer scripting and automation for managing their container registry.
- Audit Logging: ACR provides detailed audit logs, allowing users to track and monitor registry activities. Audit logging is crucial for compliance, troubleshooting, and gaining insights into user interactions with the registry.
- Token Authentication for Docker CLI: ACR supports token authentication, allowing users to authenticate with the Docker CLI using Azure Active Directory tokens. This enhances security by providing an alternative to basic authentication methods.
- Custom Roles: ACR allows users to define custom roles with specific permissions, providing a more granular level of access control. This feature is beneficial for organizations with unique security and access requirements.
- Retention Policies: ACR allows users to define retention policies for images, automatically cleaning up older or unused images. This helps optimize storage space and ensures that only relevant images are retained in the registry.
- some of the azure resgistry elements are shown below:
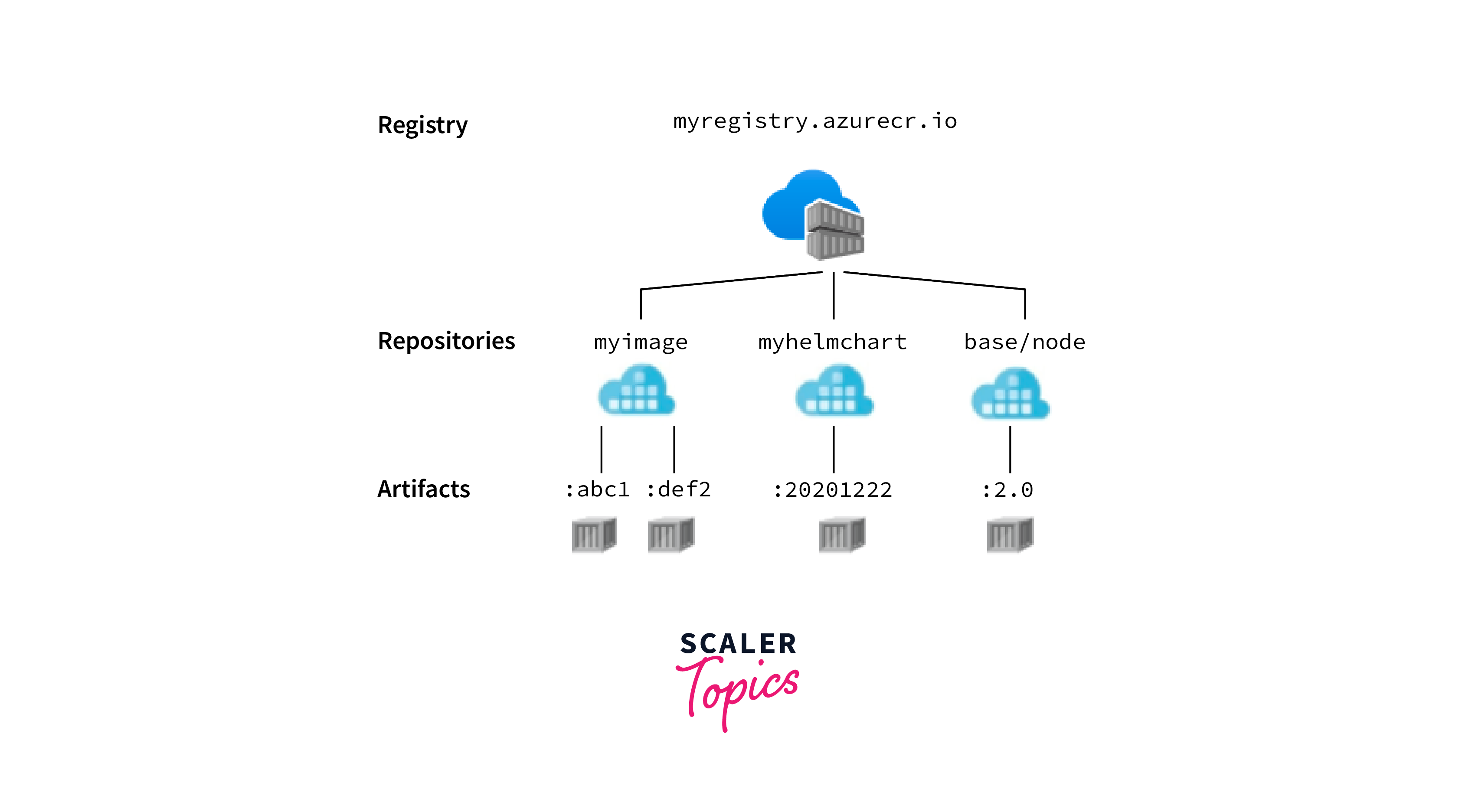
Use cases & Best Practices
Use Cases
Microservices Architecture:
ACR is well-suited for organizations adopting a microservices architecture. It allows for the efficient storage and management of container images, supporting the development and deployment of individual microservices independently.
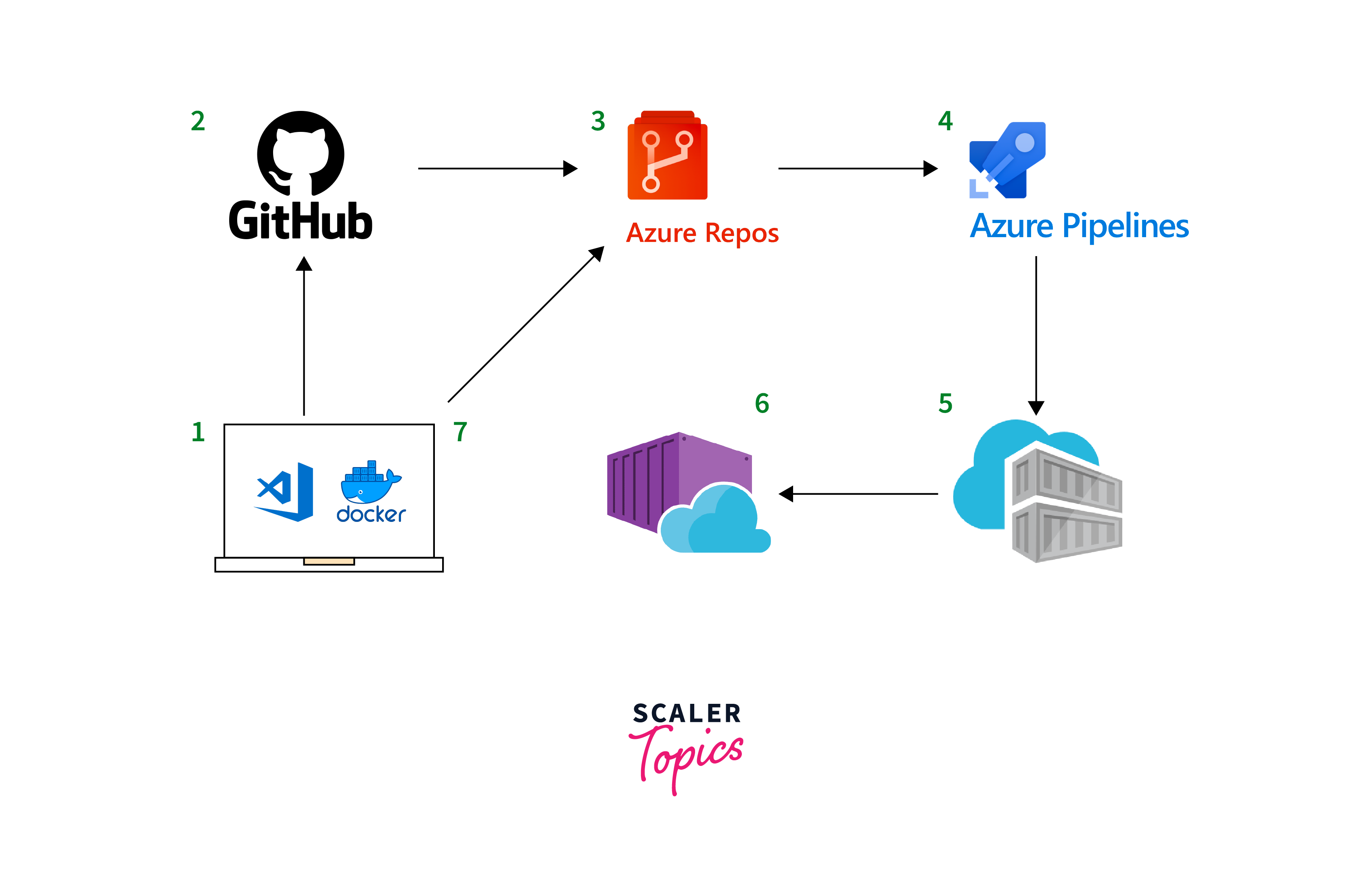
Continuous Integration and Continuous Deployment (CI/CD):
ACR integrates seamlessly with CI/CD pipelines, enabling automated image builds, tests, and deployments. This use case streamlines the development process, facilitating rapid and reliable application delivery.
Secure Image Distribution:
ACR provides a private registry, making it an ideal solution for securely distributing container images within an organization. This is crucial for maintaining the confidentiality of proprietary applications and ensuring regulatory compliance.
Hybrid Cloud Deployments:
Organizations with hybrid cloud setups, combining on-premises infrastructure with cloud resources, can use ACR for managing container images across both environments. This flexibility simplifies the deployment of applications in hybrid scenarios.
Best Practices
Content Trust and Image Scanning:
Enable content trust to verify the integrity and authenticity of container images. Additionally, regularly scan container images for vulnerabilities using integrated scanning tools to address security concerns.
Versioning and Tagging:
Adopt a consistent versioning strategy for container images using tags. This practice facilitates tracking and deployment of specific versions, making it easier to manage and roll back updates.
Logging and Monitoring:
Enable and review audit logs to monitor registry activities. Integrate ACR with Azure Monitor to gain insights into performance, troubleshoot issues, and plan for capacity.
Network Security:
Enhance network security by configuring Virtual Network Service Endpoints to restrict access to ACR from specific virtual networks or IP addresses. This helps prevent unauthorized access to the registry.
Pricing and Tiers:
ACR offers different pricing tiers to accommodate various needs:
-
Basic: Standard features with basic storage and data transfer capabilities. It is cost-free.
-
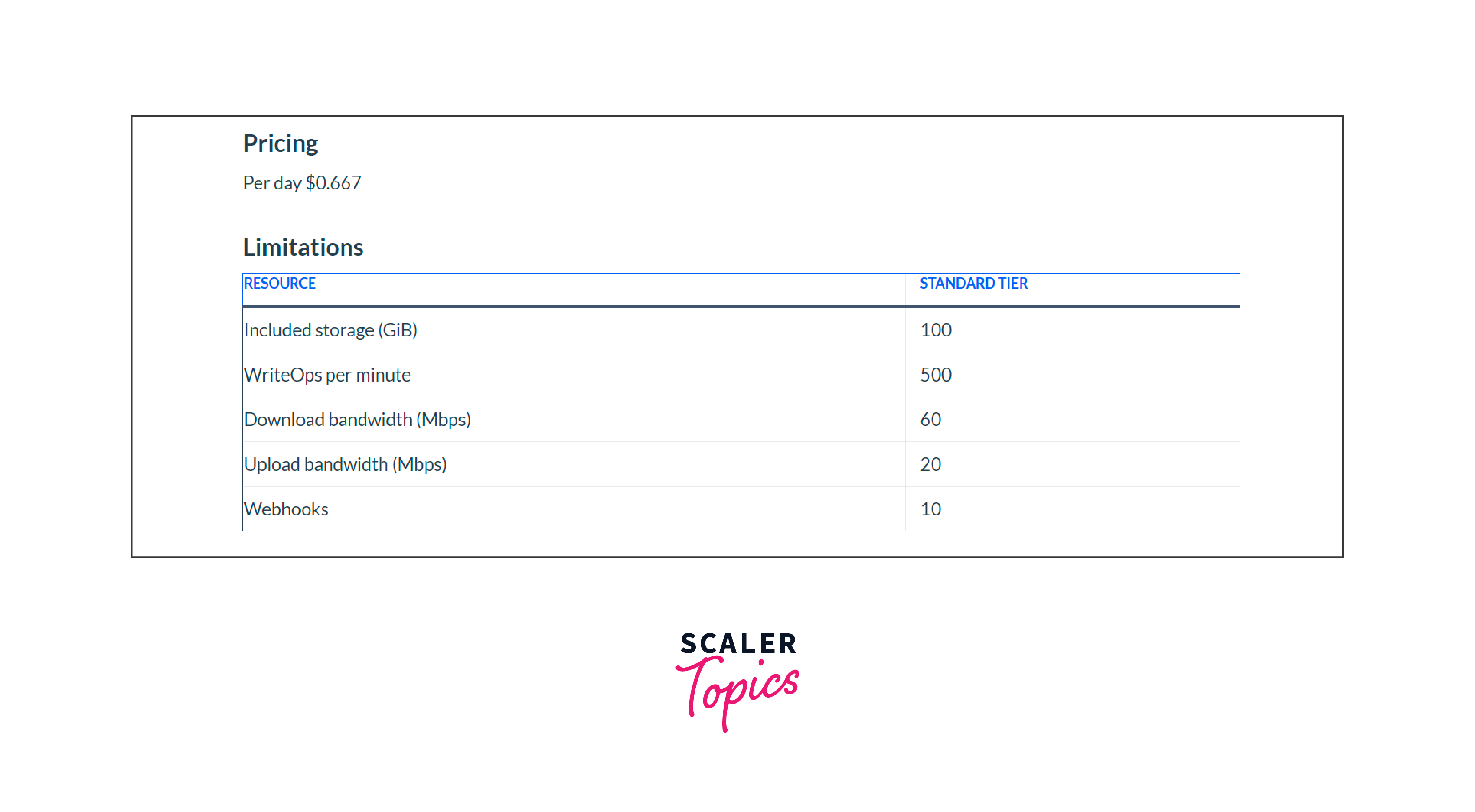
Standard: Enhanced features including geo-replication and increased storage capacity.
-
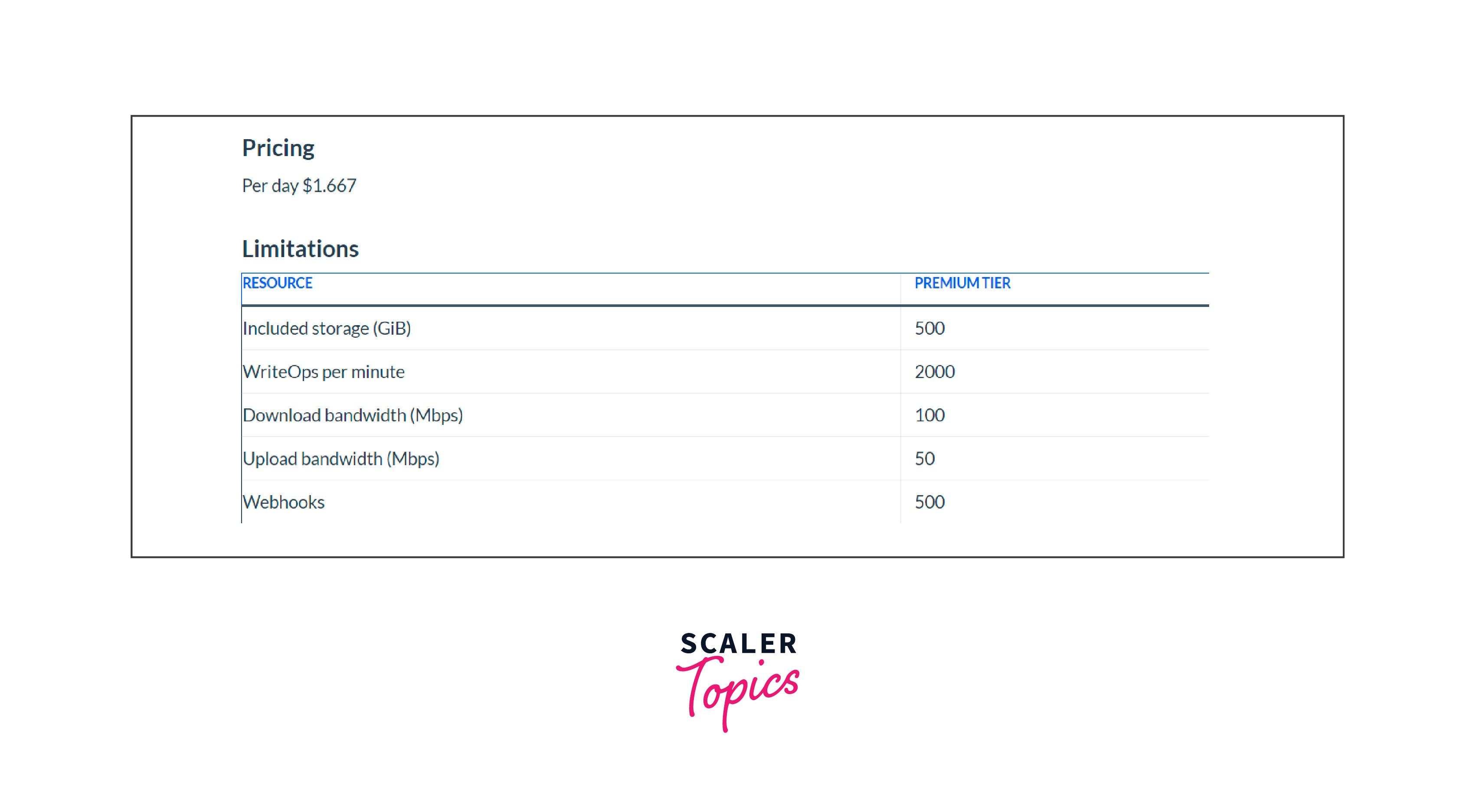
Premium: Designed for high-performance scenarios, with premium storage and additional concurrency.
Setting Up Azure Container Registry
Setting up Azure Container Registry (ACR) is a straightforward process, and the reference you provided offers a comprehensive guide on getting started. Below is a summarized step-by-step process based on the provided reference using the Azure portal and Azure CLI:
Step 1: Sign in to the Azure Portal
- Navigate to the Azure Portal.
- Sign in with your Azure account.
Step 2: Create a Resource Group (if needed)
- A resource group is a logical container for resources deployed in Azure.
- Create a new resource group or use an existing one based on your organization's structure.
Step 3: Create an Azure Container Registry
- In the Azure portal, navigate to "Create a resource."
- Search for "Container Registry" and select it from the results.
- Click "Create."
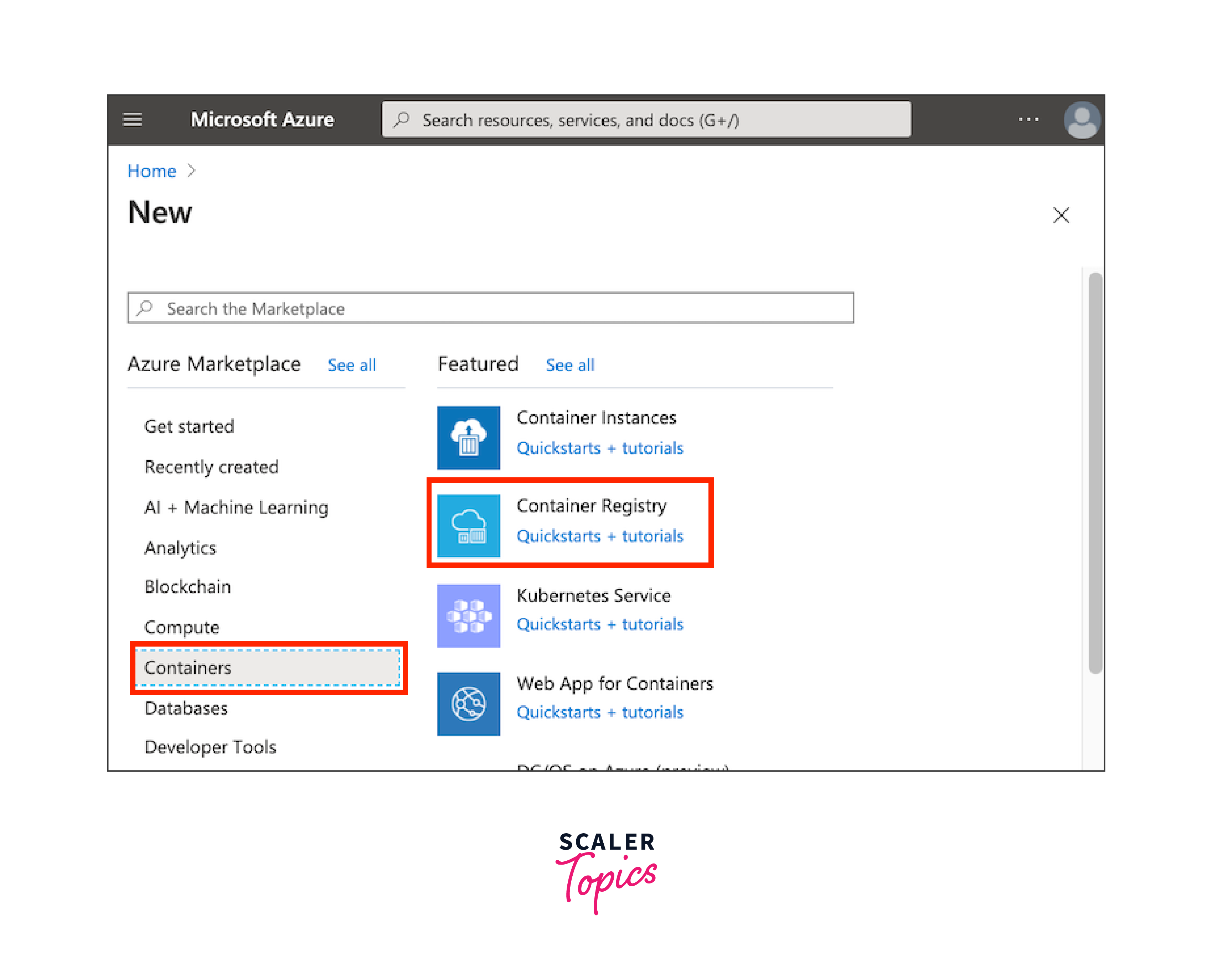
-
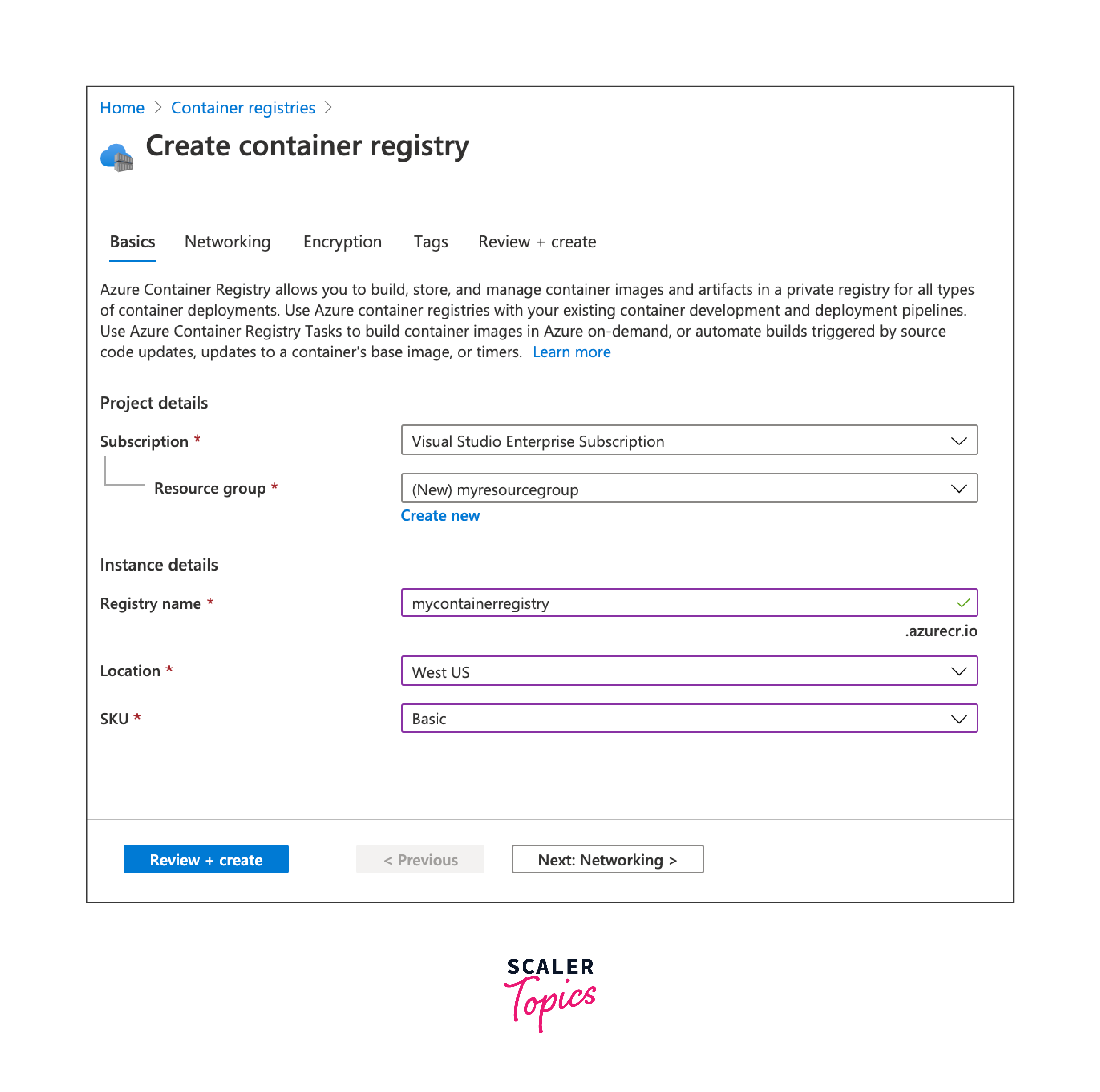
Fill in the required information:
- Subscription: Select your Azure subscription.
- Resource Group: Choose the resource group you created or use an existing one.
- Registry Name: Enter a unique name for your ACR.
- Region: Choose the Azure region for your registry.
- SKU: Select the desired pricing tier (e.g., Basic, Standard, or Premium).
- Admin User: Choose whether to enable or disable admin user access.
-
Click "Review + Create" and then "Create" to deploy the ACR.
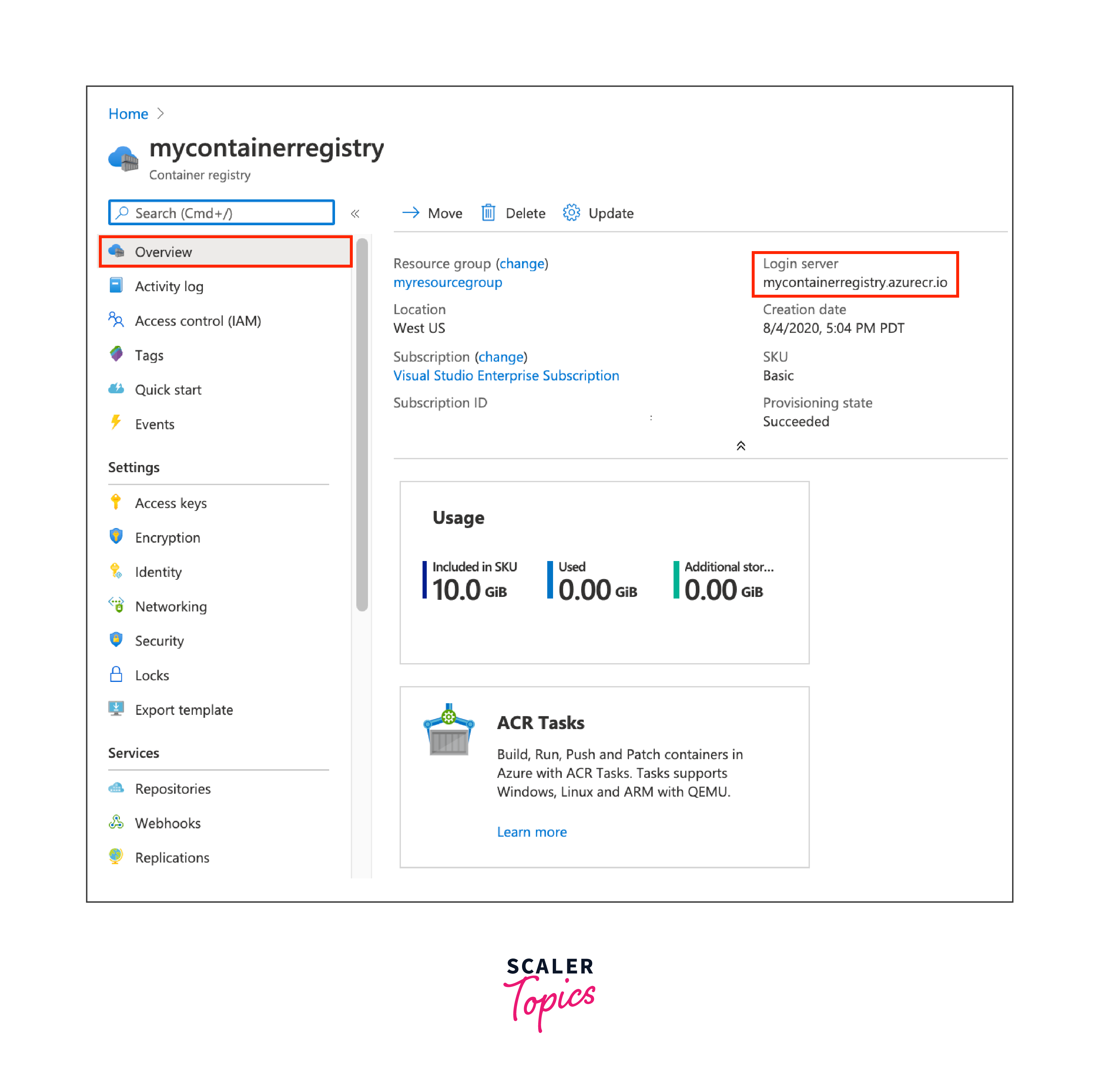
Step 4: Access and Authenticate to ACR
- After deployment, navigate to your ACR in the Azure portal.
- Click on the "Access keys" under "Settings."
- Note down the "Login server," "Username," and one of the "Passwords."
Step 5: Install Docker (if not already installed)
- If you don't have Docker installed, follow the instructions in the reference to install Docker.
Step 6: Log in to ACR using Docker
- Open a terminal or command prompt.
- Run the following command, replacing <registry-name>, <username>, and <password> with your ACR details:
Step 7: Build and Push a Docker Image Follow the instructions in the reference to create a simple Dockerfile.
- Build the Docker image:
- Push the image to ACR:
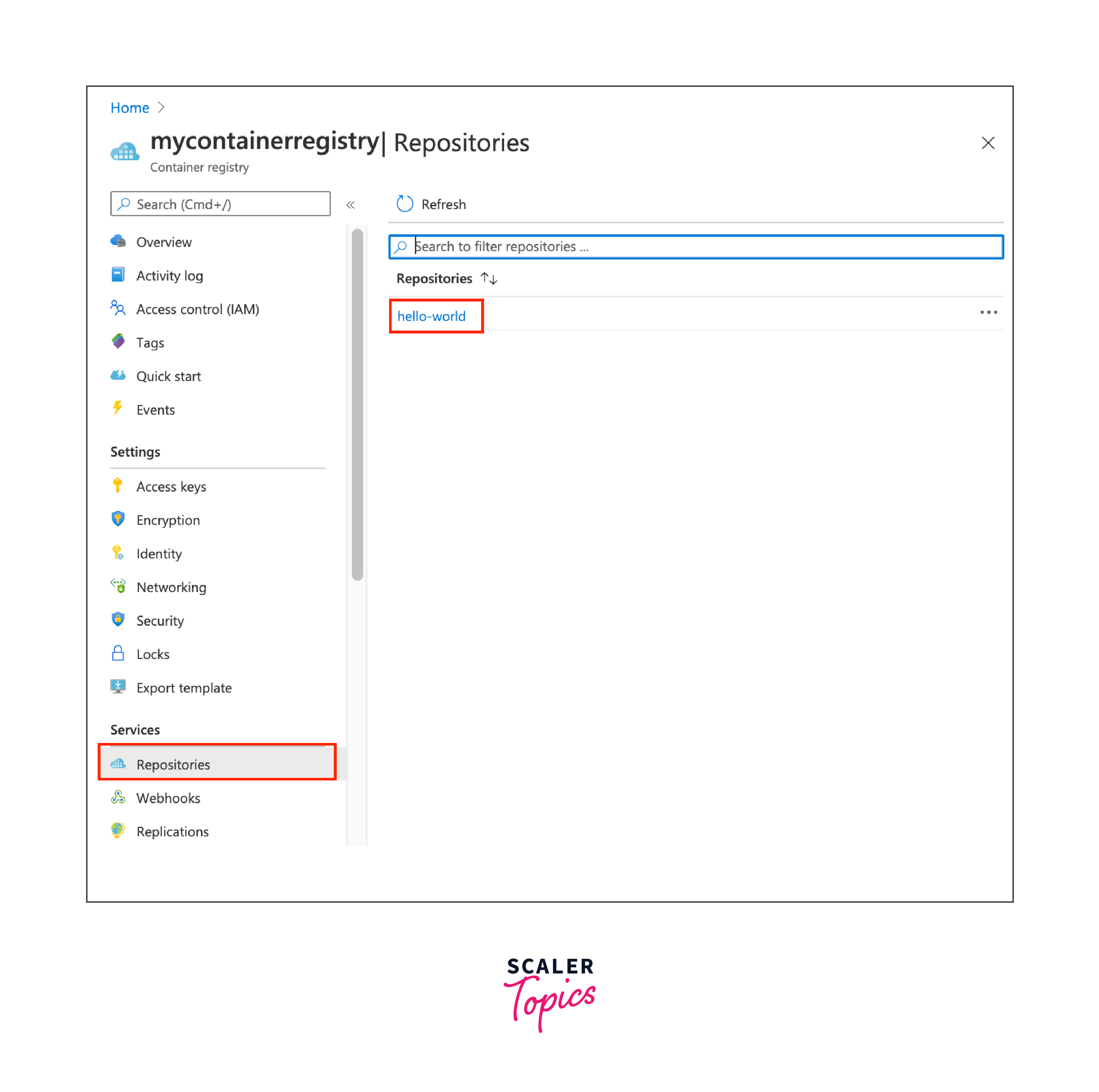
Step 8: Verify Image in ACR
- Go back to the Azure portal, navigate to your ACR, and click on "Repositories" under "Services." You should see the repository and image you pushed.
- Finally cleaning the resources:
Conclusion
- Azure Container Registry ensures secure and private management of Docker container images, prioritizing confidentiality.
- Seamlessly integrates with Azure services, facilitating streamlined deployment on Azure Kubernetes Service (AKS) and Azure Container Instances (ACI).
- Geo-replication enables global distribution of container images, optimizing deployment by providing access from closer regions.
- Webhooks support automation, integrating with CI/CD pipelines for continuous integration and deployment, promoting efficient DevOps practices.
- Role-Based Access Control (RBAC) offers fine-grained access management, enhancing security through limited user privileges.
- ACR's scalability accommodates varying workloads, with diagnostic tools and Azure Monitor integration ensuring efficient registry management and monitoring.
- Content trust, vulnerability scanning, and network security features contribute to a robust security posture for containerized applications.
