Azure Security Center
Overview
In cloud-based services, security for sensitive data and infrastructure is a major concern and Microsoft Azure provides its own Security Center, a dedicated cloud security solution that is designed to protect Azure environments from cyber threats. This article explores the core concepts of Azure Security Center with its features and best practices to ensure resilient security protection.
What is Azure Security Center?
Azure Security Center is a cloud security solution offered by Microsoft, specifically tailored for Azure environments. It serves as a centralized hub for monitoring, assessing, and enhancing the security of your cloud resources.
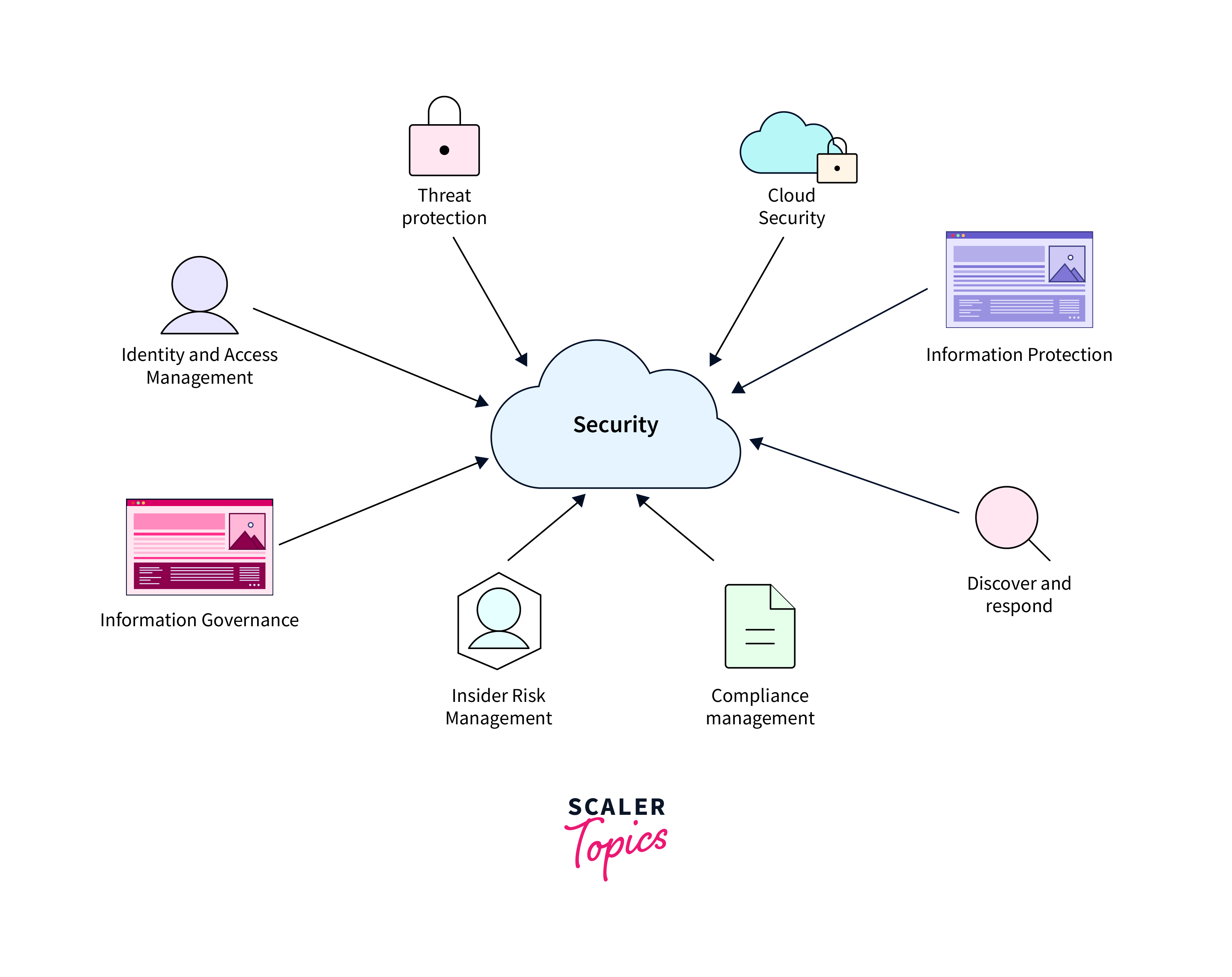
How Azure Security Works
Azure Security Center operates on a multi-layered approach to safeguarding Azure environments. It combines the power of advanced analytics, machine learning, and various services or components to provide comprehensive protection:
-
Threat Protection and Anomaly Detection: Advanced analytics and machine learning to identify suspicious activities and patterns within your Azure environment. This includes analyzing data such as logins, resource usage, and network traffic.
-
Azure Monitor and Azure Log Analytics: These services play a crucial role in the detection and response process. Azure Monitor provides a comprehensive view of your resources and applications, allowing the Security Center to detect potential threats. Azure Log Analytics, on the other hand, helps in collecting, analyzing, and correlating data from various sources, enabling a more in-depth investigation of security incidents.
-
Azure Policy and Azure Resource Health: These components ensure that your resources are configured in compliance with security best practices and industry-standard regulations. Azure Policy allows you to define and enforce security policies across your Azure environment, ensuring that resources meet specific compliance requirements. Azure Resource Health monitors the health of your resources and provides insights into their operational status.
-
Threat Intelligence Integration: Azure Security Center integrates with global threat intelligence feeds to stay updated with the latest cybersecurity threats. This ensures that the system can recognize known attack patterns and indicators of compromise.
-
Security Alerts and Incidents Management: When suspicious activities are detected, Azure Security Center generates real-time alerts. These alerts are prioritized based on severity, allowing administrators to focus on the most critical threats first. Each alert provides detailed information about the incident, including recommended actions for mitigation.
-
Just-In-Time Access and Network Security Group Recommendations: These features enhance security by reducing the attack surface. Just-in-time access allows administrators to grant temporary access to specific resources, minimizing exposure. Network Security Group Recommendations provide advice on how to configure network security groups for better protection.
Example:
Consider a scenario where a malicious actor attempts to gain unauthorized access to an organization's Azure environment.
- They may try to exploit vulnerabilities in an application running on a virtual machine.
- Azure Security Center, with its advanced threat protection capabilities, would detect this unusual activity.
- It would analyze login patterns, resource usage, and network traffic, flagging suspicious behavior.
- The system would then generate a security alert, indicating a potential threat.
- This alert would be sent to the administrator, highlighting the incident's details and providing recommended actions.
- In this case, the Security Center might suggest temporarily blocking access to the affected virtual machine, mitigating the risk of a successful cyber attack.
Features of Azure Security Center
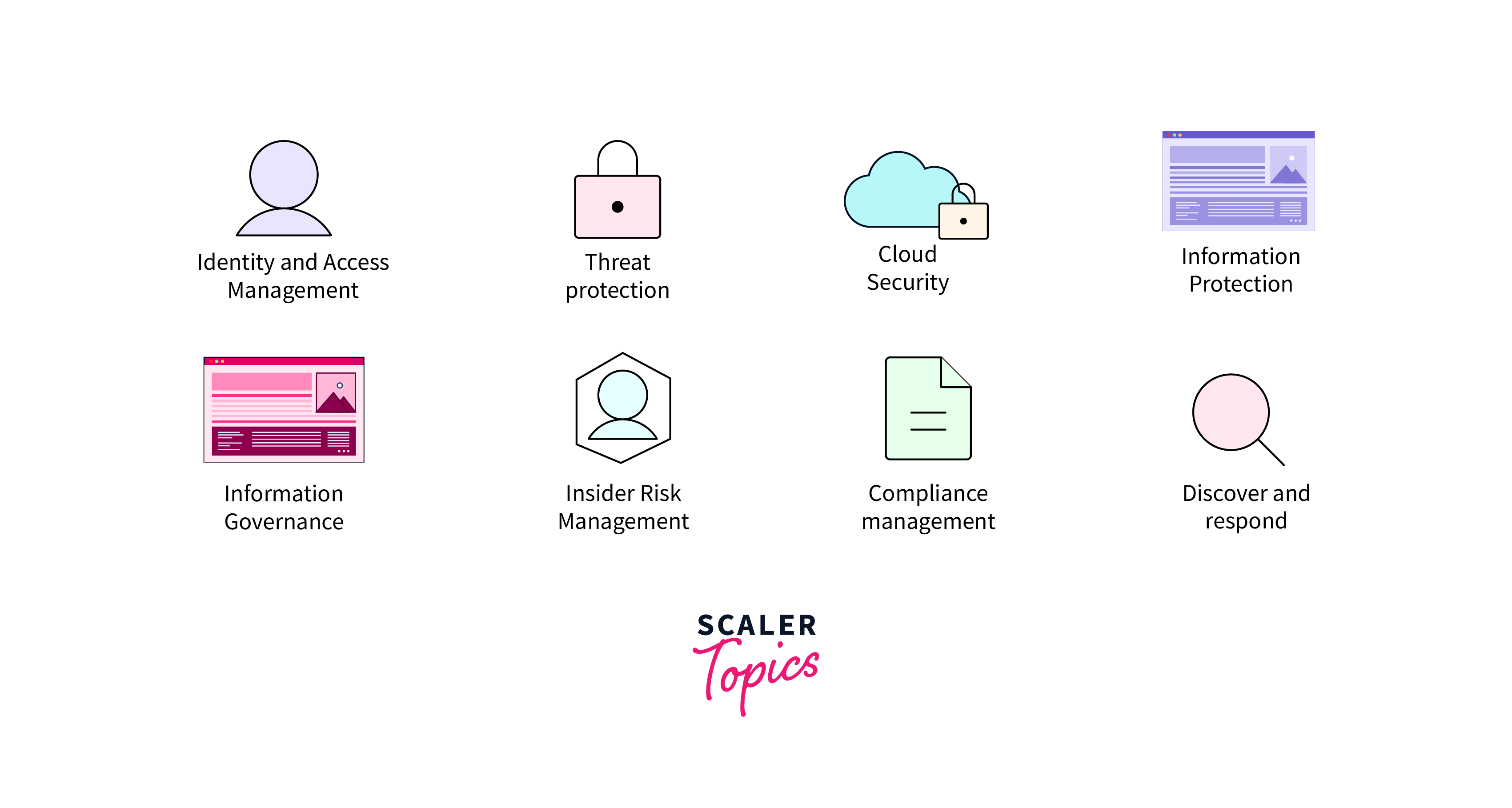
Azure Security Center is equipped with multiple powerful features:
Security Policies and Compliance
Define and enforce security policies to ensure resources adhere to industry-standard compliance regulations. This feature helps maintain a robust security posture by aligning with specific security requirements.
Threat Protection
Detect and respond to threats using advanced analytics, anomaly detection, and machine learning algorithms. This feature enables real-time threat identification and prompt mitigation.
Just-In-Time Access
Grant access to resources on-demand, reducing the attack surface and enhancing security. With Just-In-Time Access, administrators can limit access to critical resources, minimizing potential security risks.
Network Security Group Recommendations
Receive recommendations to strengthen network security configurations. This feature offers customized guidance on how to configure network security groups for better protection against cyber threats.
Threat Protection for Azure Storage and SQL Databases
Safeguard critical data assets from potential breaches. This feature provides an additional layer of security for important data stored in Azure Storage and SQL databases.
Security Alerts and Incidents
Receive real-time alerts and insights into security incidents, enabling swift response. Security Center promptly notifies administrators about potential security breaches, facilitating immediate action.
Architecture
The architecture of Azure Security Center is structured to provide security monitoring and response capabilities. At its core, Security Center consists of several key components that work in tandem to safeguard Azure environments.
- Recommendations serve as a main element that monitors risk in the Cloud Security Posture Management (CSPM) scenario. They offer actionable guidance to enhance the overall security posture of the environment.
- Alerts play a critical role in identifying and responding to security incidents. They are generated when suspicious activities or potential threats are detected within the Azure environment.
- The Continuous Export feature enables the streaming of both recommendations and alerts. This data can be directed to a chosen Log Analytics workspace, facilitating in-depth analysis and monitoring. Additionally, it offers the option to stream this information to an Event Hub, which can be integrated with third-party Security Information and Event Management (SIEM) systems for further analysis.
- Security Center can integrate with other cloud providers like AWS and GCP. This ensures a holistic security approach across multi-cloud environments. Additionally, external recommendations from third-party partners can be ingested, often transmitted via Application Program Interfaces (APIs).
- The Log Analytics Agent is instrumental in gathering security-related information from various sources. It is configured to forward this data to a designated Log Analytics workspace.
- In Linux environments, the Security Center goes a step further by creating the omsagent daemon in addition to the agent for Linux. This daemon operates under the omsagent account, which is automatically established during the agent installation process. This enhances the depth of security event monitoring for Linux-based systems.
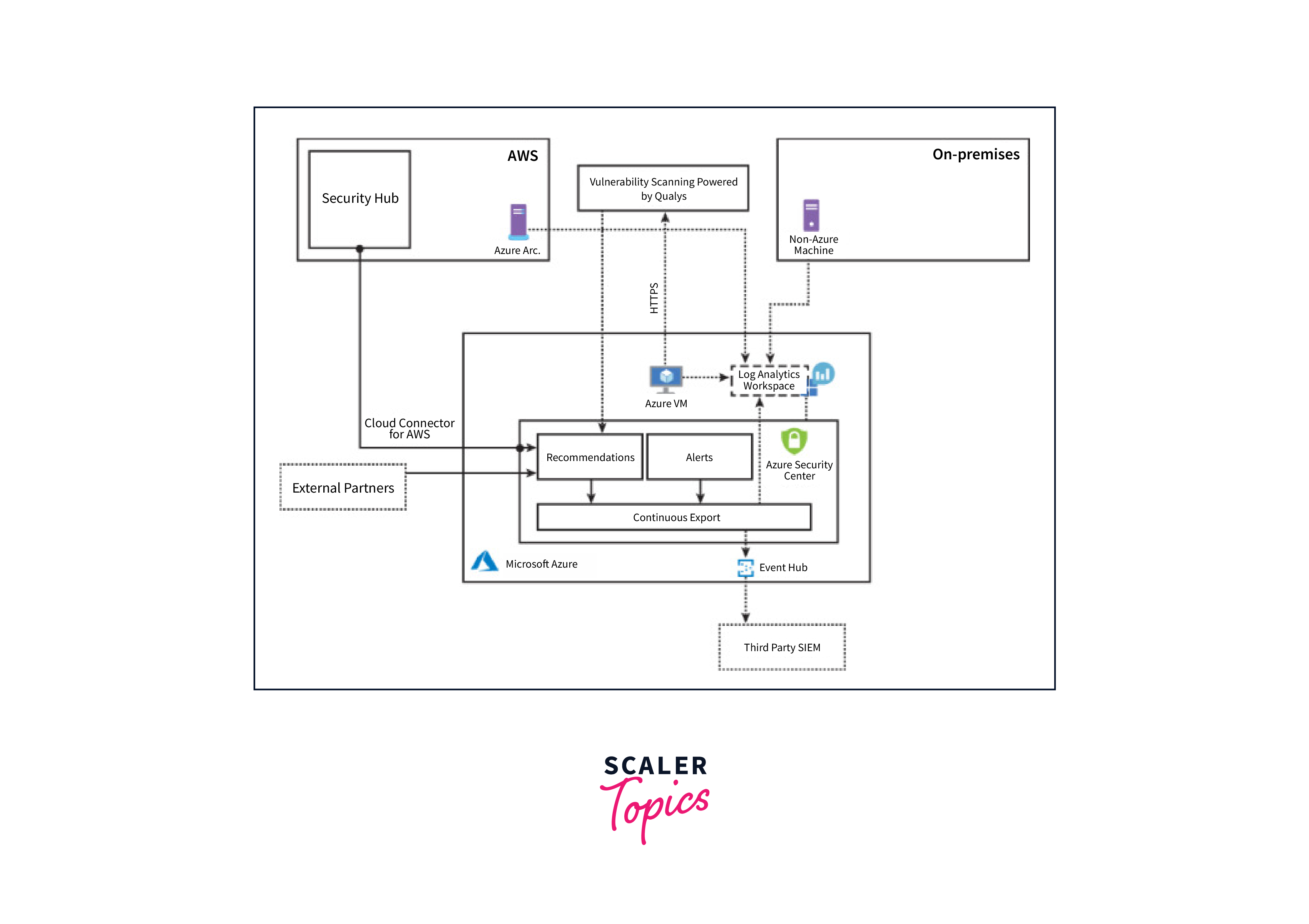
Cloud Security Posture Management (CSPM) involves continuously assessing and aligning cloud resources with industry-standard security best practices. It ensures that cloud environments are configured securely, reducing vulnerabilities to potential cyber threats.
How to Use Azure Security Center?
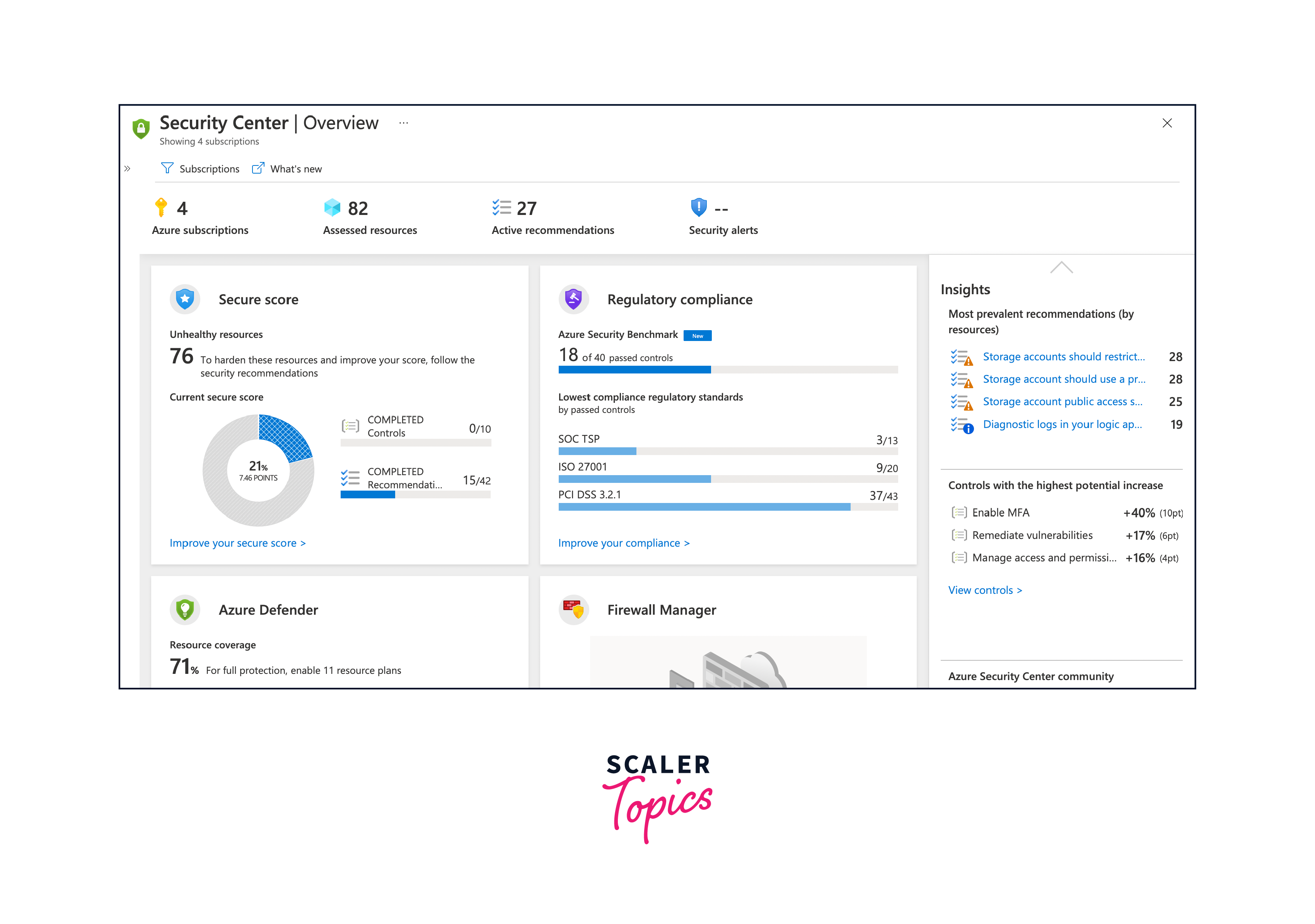
Azure Security Center can be utilized by navigating to the Azure portal and selecting Security Center from the left-hand menu. From here, you can access all information regarding the security status of your resources, configure policies, and leverage the wealth of recommendations provided to enhance your security posture.
Pricing
Azure Security Center offers both free and paid tiers. Here is a table showing the price of Azure security in India:
| Service | Description | Price |
|---|---|---|
| Azure Security Center Free Tier | Includes continuous assessment, security recommendations, and Azure Secure Score for Azure, on-premises, and hybrid resources. | Free |
| Microsoft Defender for Cloud (Beyond 30 Days) | Automatically charges apply after the first 30 days of free usage. All protected resources incur charges as per the pricing scheme. | As per Azure pricing scheme |
| Defender Cloud Security Posture Management (CSPM) | Advanced CSPM offering agentless vulnerability scanning, attack path analysis, integrated data-aware security posture, and intelligent cloud security graph. Billing is based on Server, Storage account, and Database counts. | ₹0.583/Billable resource/hour |
| Microsoft Defender for Servers Plan 1 | Provides advanced threat protection for servers. | ₹0.560/Server/hour |
| Microsoft Defender for Servers Plan 2 | Offers extended capabilities for server security. | ₹1.665/Server/hour |
| Microsoft Defender for Containers | Delivers threat protection for container environments. | ₹0.7832/vCore/hour |
| Microsoft Defender for SQL on Azure-connected databases | Provides advanced security for SQL databases on Azure. | ₹1.711/Instance/hour |
| Microsoft Defender for SQL outside Azure | Extends SQL database security outside Azure. | ₹1.249/vCore/hour |
| Microsoft Defender for MySQL | Ensures security for MySQL databases. | ₹1,248.432/Instance/month |
| Microsoft Defender for PostgreSQL | Provides security for PostgreSQL databases. | ₹1,248.432/Instance/month |
| Microsoft Defender for MariaDB | Offers security for MariaDB databases. | ₹1.682/Instance/hour |
| Microsoft Defender for Azure Cosmos DB | Provides security for Azure Cosmos DB resources. | ₹0.0999 per 100 RU/S/hour |
| Microsoft Defender for Storage | Ensures security for storage accounts. | ₹1.1153 per storage account/hour |
| Malware Scanning (add-on to Defender for Storage) | Offers malware scanning for storage data. | ₹12.485/GB of data scanned |
| Microsoft Defender for App Service | Provides advanced threat protection for App Service instances. | ₹1.665/Instance/hour |
| Microsoft Defender for Key Vault | Offers security for Key Vault resources. | ₹20.66/Vault/month |
| Microsoft Defender for Resource Manager | Ensures security for Resource Manager. | ₹419.23/Subscription/month |
Pricing for Microsoft Defender in the cloud after 30 days depends on the number of resources and the price fixed on each resource.
Azure Security Best Practices
- Implement Multi-Factor Authentication (MFA): Provides stronger security for user login and critical operations by using multiple authentication mechanisms.
- Regularly Monitor and Analyze Security Alerts: Stay vigilant for any unusual activities and respond promptly to potential threats.
- Keep Systems and Software Updated: Ensure that all Azure resources are running the latest security patches and updates.
- Encrypt Sensitive Data: Utilize tools like Azure Disk Encryption and Azure Storage Service Encryption, to protect sensitive data at rest and in transit.
- Role-Based Access Control (RBAC): Implementing the principle of least privilege ensures that individuals only have access to the resources necessary for their role.
Advantages
- Azure Security Center provides end-to-end security for Azure, on-premises, and hybrid environments, ensuring a unified defense against cyber threats. Users can track their security posture through Azure Secure Score, which provides a quantifiable measure of how well security practices are implemented.
- By integrating with Azure Defender, organizations gain advanced threat protection, further enhancing their security posture against evolving cyber threats and provide them advanced security capabilities, including agentless vulnerability scanning, which helps identify and remediate vulnerabilities without the need for additional software installation.
- Azure Security Center conducts attack path analysis to identify potential routes that attackers could use to infiltrate resources, enabling organizations to implement necessary safeguards. It also assists in meeting compliance requirements by providing security policies and recommendations aligned with industry-standard compliance regulations.
- Security Center delivers real-time alerts for suspicious activities and by implementing Just-In-Time access, organizations can reduce the attack surface by granting temporary access to resources only when needed, minimizing security risks.
FAQs
Q. How does Azure Security Center benefit my organization's security posture?
A. Azure Security Center provides comprehensive security solutions, offering end-to-end protection across Azure, on-premises, and hybrid environments, ensuring a unified defense against cyber threats.
Q. Can I customize security policies in Azure Security Center to align with our specific compliance requirements? A. Yes, Azure Security Center allows organizations to define and enforce custom security policies, ensuring alignment with industry-standard compliance regulations.
Q. How does Just-In-Time access in Azure Security Center enhance security? A. Just-In-Time access reduces the attack surface by granting temporary access to resources only when needed, minimizing security risks and providing an extra layer of protection.
Conclusion
- Azure Security Center is Microsoft's dedicated cloud security solution for Azure environments. It serves as a centralized hub for monitoring, assessing, and enhancing the security of Azure resources.
- It employs advanced analytics, machine learning, and global threat intelligence for real-time threat detection.
- Features of Azure Security Center include security policies, threat protection, just-in-time access, network security recommendations, and more.
- It integrates with Azure Monitor, Log Analytics, Azure Policy, and Azure Resource Health for comprehensive threat detection and response.
- We can access the Azure security center through the Azure portal, review security recommendations, manage policies, and respond to alerts.
- Offers both free and paid tiers based on the number of monitored resources.
- Azure security best practices include implementing multi-factor authentication, regular monitoring of security alerts, and keeping systems updated.
- Advantages include protection, real-time insights, and scalability for Azure environments.
- Provides advanced capabilities like vulnerability scanning and attack path analysis, with billing based on specific resources.
