Azure Security Services|Azure Security Services - Scaler Topics
Overview
Recognizing that security is paramount in the cloud, we understand the crucial need for accurate and timely Azure security information. Opting for Azure for your applications and services offers a prime benefit—access to a comprehensive set of security tools and features. These resources play a vital role in crafting secure solutions on Azure's robust platform, ensuring the confidentiality, integrity, availability, and transparent accountability of customer data.
General Azure security
A comprehensive list of Azure's security services and technologies is valuable for evaluating cloud service provider options, enabling you to:
- Assess Security Capabilities
- Compare Competing Providers
- Tailor Your Security Strategy
- Enhance Security Posture
With that in mind let's explore some Azure's security-related services in brief
1. Microsoft Defender for Cloud

Microsoft Defender for Cloud is a cloud-native platform that integrates DevSecOps for unified security management, CSPM for breach prevention, and CWPP for targeted protection across servers, containers, storage, databases, and workloads.
2. Microsoft Sentinel

Microsoft Sentinel is a scalable, cloud-native solution offering:
- SIEM (Security Information and Event Management)
- SOAR (Security Orchestration, Automation, and Response)
It offers comprehensive security analytics and threat intelligence across the enterprise.
- Attack detection
- Threat visibility
- Proactive hunting
- Threat response
3. Azure Key Vault
Azure Key Vault is a key management solution in Azure that addresses several key challenges:
-
Secrets Management:
- Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
-
Key Management:
- Create and manage encryption keys used for data encryption.
-
Certificate Management:
- Provision, manage, and deploy TLS/SSL certificates for use with Azure and internal connected resources.
4. Azure Monitor logs
Azure Monitor Logs, powered by Azure Data Explorer and using Kusto Query Language (KQL), supports interactive log analysis through Log Analytics, proactive issue identification with Log Alert Rules, visual reporting in Workbooks, dashboard creation in Azure Dashboards, integration into Azure Logic Apps workflows, utilization in PowerShell scripts or Azure Automation runbooks, retrieval via Azure Monitor Logs API, and access through Azure Monitor Query Client Libraries for various ecosystems like .NET, Go, Java, JavaScript, and Python.
5. Azure Dev/Test Labs
Azure DevTest Labs simplifies the creation and management of IaaS virtual machines (VMs) and PaaS environments in labs, offering:
- Preconfigured VMs: Labs provide bases and artifacts for VM creation.
- ARM Templates: Easily create environments, like Azure Web Apps or SharePoint farms, using Azure Resource Manager templates.
Lab functionalities:
- Lab Owners: Create preconfigured VMs with required tools and software.
- Lab Users: Claim preconfigured VMs or create and configure their own VMs and environments.
- Lab Policies: Track and control lab usage and costs.
Storage security
1. Azure Storage Service Encryption
Azure Storage automatically encrypts cloud-stored data using service-side encryption (SSE), ensuring data protection, security, and organizational standards compliance.
Key points about Azure Storage encryption:
- Uses 256-bit AES encryption, compliant with FIPS 140-2.
- Resembles BitLocker encryption on Windows.
- Enabled for all storage accounts (Resource Manager and classic), non-disabling.
- Applies universally to data types, performance/access tiers, and deployment models.
- Covers various storage resources, including block, append, page blobs, archive-tier blobs, redundancy options, and primary/secondary regions.
- Defaults to securing data without requiring code or application adjustments.
2.Client-Side encryption for blobs
The Azure Blob Storage client library for .NET enables data encryption within client applications before uploading to Azure Storage and decryption during downloads. It also offers integration with Azure Key Vault for storage account key management.
Key points:
- Supports both service-side and client-side encryption.
- For simplicity in protecting your data, Microsoft recommends using service-side encryption features in most scenarios.
3. Azure Storage shared access signatures
A shared access signature (SAS) provides secure, delegated access to storage account resources with specified control over accessible resources, permissions granted, and validity period.
There are three types of shared access signatures supported by Azure Storage:
- User Delegation SAS
- Service SAS
- Account SAS
4. Azure Storage Account Keys
An Azure storage account houses your Azure Storage data, including blobs, files, queues, and tables. It offers a globally accessible namespace over HTTP or HTTPS.
Prerequisites:
- If you lack an Azure subscription, create a free account first.
- Sign in to Azure.
To create an Azure storage account:
- Navigate to the Azure portal.
- Click "Create a resource."
- Search for "Storage account" and select it.
- Follow the prompts to configure and create your storage account.
5. Azure File shares
Azure Files provides fully managed, cross-compatible cloud-based file shares via SMB, NFS, and Azure Files REST API. Accessible by both cloud and on-premises deployments, it supports Windows, Linux, and macOS clients for SMB shares, and Linux clients for NFS shares. Azure File Sync allows caching SMB shares on Windows servers for quick access.
Common use cases for Azure Files include:
- Substitute traditional file servers with serverless Azure file shares.
- Use AD authentication for FSLogix profile containers on Azure Files in Azure Virtual Desktop.
6. Azure Storage Analytics
Azure Storage Analytics logs and metrics track storage account activity, aiding in request monitoring, usage analysis, and issue diagnosis. Enable Storage Analytics separately for each service through the Azure portal or programmatically using REST API or client libraries. Data is stored in blobs (for logs) and tables (for metrics), accessible via Blob and Table service APIs.
Database security
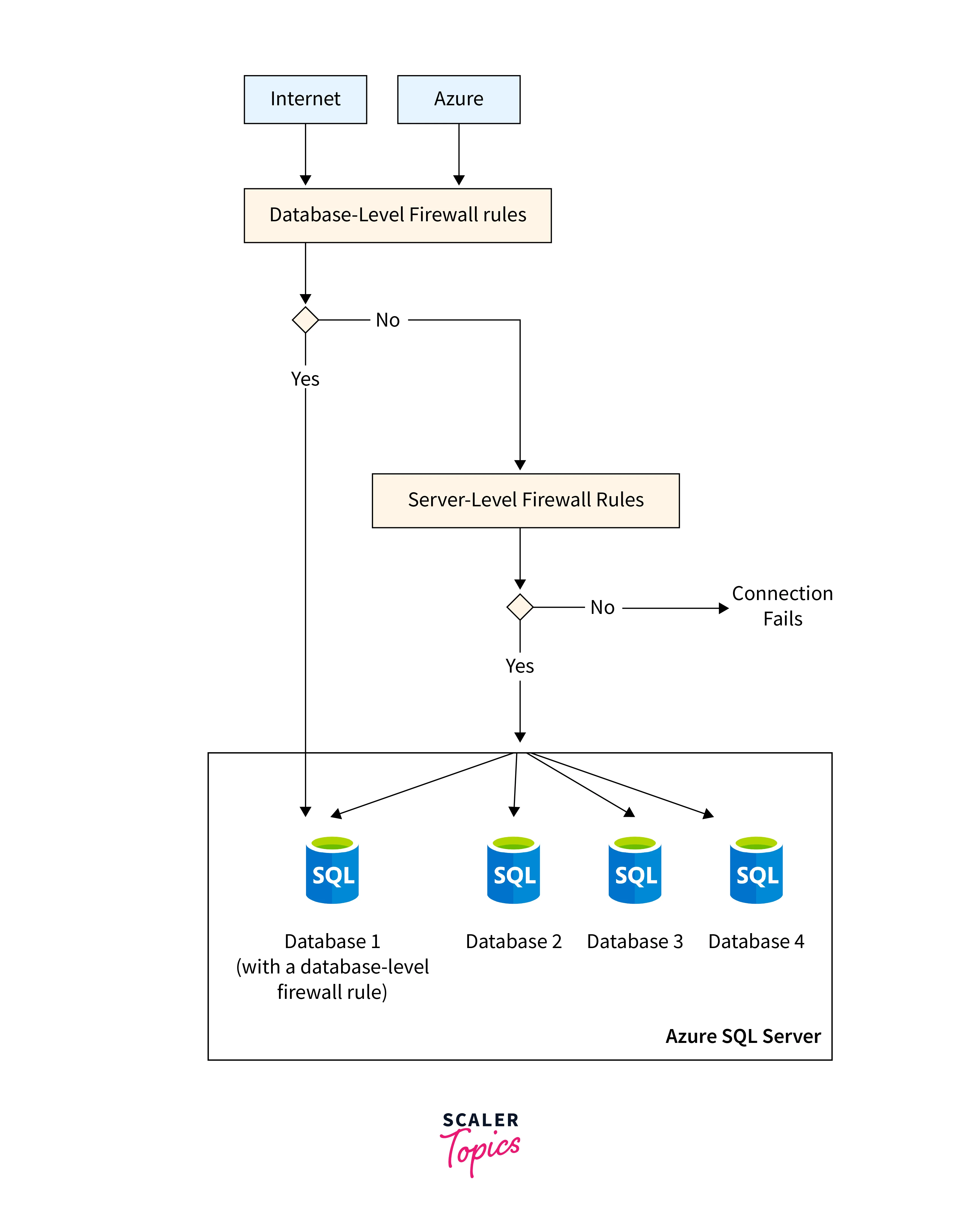
1. Azure SQL Firewall
When creating a new server in Azure SQL Database or Azure Synapse Analytics (e.g., "mysqlserver"), a server-level firewall is set up, blocking all access to the public endpoint "mysqlserver.database.windows.net."
2. Azure SQL Connection Encryption
For security purposes, SQL Database ensures access control through firewall rules that restrict connectivity based on IP addresses, authentication methods that require users to verify their identity, and authorization mechanisms that limit users to specific actions and data.
3. Azure SQL Always Encrypted
Always Encrypted, safeguards sensitive data (e.g., credit card numbers, social security numbers) in Azure SQL Database, Azure SQL Managed Instance, and SQL Server databases. It enables client applications to encrypt data without revealing keys to the Database Engine, ensuring a separation between data owners and administrators. Supporting limited confidential queries, it uses deterministic encryption and, with secure enclaves, extends capabilities for operations like pattern matching. Always Encrypted operates transparently, encrypting and decrypting data within client applications to preserve semantics and ensure data security.
4. Azure SQL transparent data encryption
Transparent Data Encryption (TDE) secures Azure SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics by encrypting data at rest without application changes. TDE is enabled by default for new Azure SQL Databases but requires manual activation for older ones. In Azure SQL Managed Instance, it's enabled at the instance level for new databases, while Azure Synapse Analytics requires manual activation.
5. Virtual network rules
Virtual network rules act as a firewall security measure to manage whether the server for your databases in Azure SQL Database and Azure Synapse Analytics accepts communications from specific subnets in virtual networks.
Identity and access management
1. Azure role-based access control
Azure Role-Based Access Control (Azure RBAC) serves as the authorization system for managing access to Azure resources. Access is provided by assigning roles to users, groups, service principals, or managed identities at a specific scope. Steps:
- Identify the needed scope
- Open the Add role assignment page
- Open the Add role assignment page
- Select who needs access
- (Optional) Add condition
- (Optional) Add condition
2. Microsoft Entra ID
Microsoft Entra ID is a cloud-based identity and access management service for employee access to external resources, including Microsoft 365, Azure Portal, and numerous SaaS applications. It also facilitates access to internal resources like corporate intranet apps and organization-specific cloud apps.
3.Azure Active Directory B2C
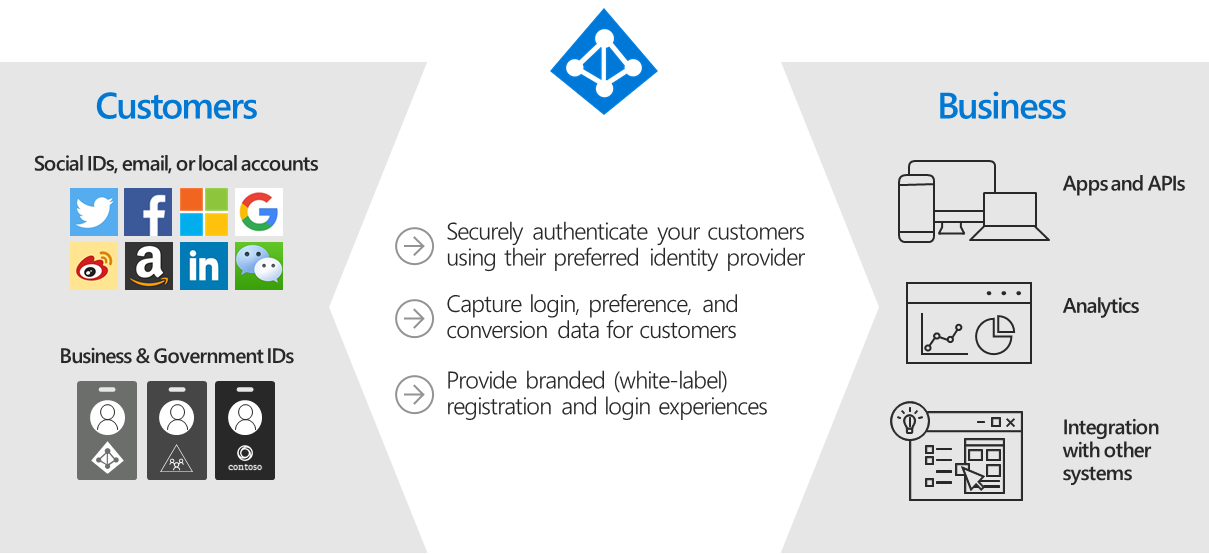 ]
Azure AD B2C is a CIAM solution for massive user support and authentication security. It manages scaling, safety, and threat handling. It's distinct from Microsoft Entra ID and enables businesses to create customer-facing apps with unrestricted user sign-up and access.
]
Azure AD B2C is a CIAM solution for massive user support and authentication security. It manages scaling, safety, and threat handling. It's distinct from Microsoft Entra ID and enables businesses to create customer-facing apps with unrestricted user sign-up and access.
Backup and disaster recovery
1. Azure Backup
Azure Backup offers straightforward, secure, and budget-friendly options for data backup and recovery in the Microsoft Azure cloud.
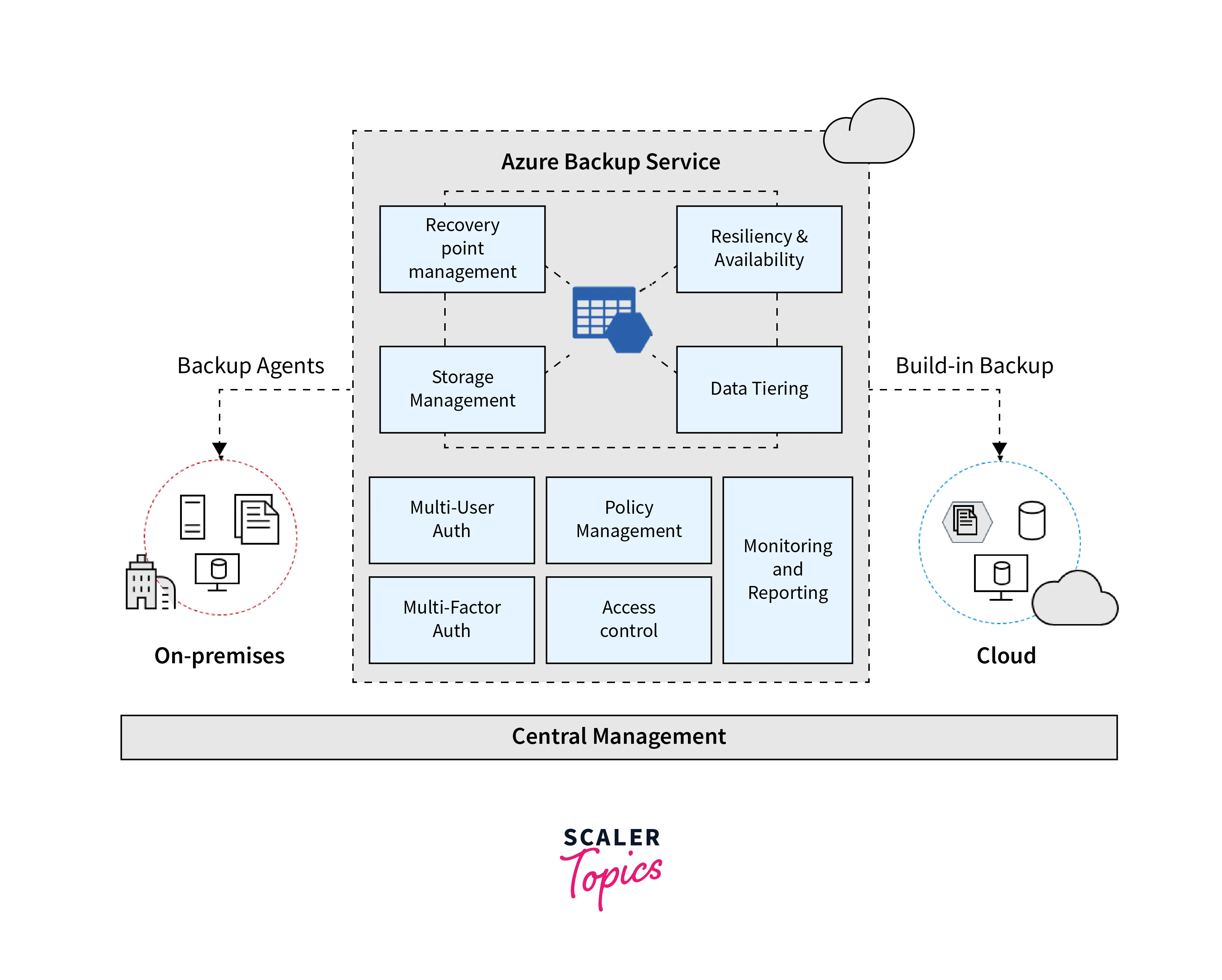
2. About Site Recovery
An online service that duplicates workloads from physical and virtual machines (VMs) at a primary site to a secondary location, ensuring service recovery in the event of a failure.
Networking
| Service | Description |
|---|---|
| Azure VPN Gateway | A network device serving as a VPN endpoint to enable cross-premises access to Azure Virtual Networks. |
| Web application firewall (WAF) | A functionality that offers centralized safeguarding of your web applications against typical exploits and vulnerabilities. |
| Azure DDoS protection | When paired with optimal application design, it offers protection against DDoS attacks. |
| Azure Load Balancer | A TCP/UDP application network load balancer. |
| Azure Traffic Manager | A DNS-based traffic load balancer. |
| Azure ExpressRoute | A capability enabling the expansion of on-premises networks into the Microsoft cloud via a private connection facilitated by a connectivity provider. |
| Azure Application Gateway | An advanced load balancer for web traffic that empowers you to oversee traffic to your web applications. |
| Virtual Network service endpoints | Furnishes secure and direct access to Azure services via an optimized route on the Azure backbone network. |
Conclusion
- The Azure Blob Storage client library for .NET allows data encryption within client applications, promoting data security.
- The built-in capabilities for azure security services are categorized into six key areas: Operations, Applications, Storage, Networking, Compute, and Identity.
- Azure Storage automatically encrypts your data using service-side encryption (SSE) when stored in the cloud
- Azure Storage Analytics logs and provides metrics for storage accounts, aiding in request tracking, usage analysis, and issue diagnosis
