Azure Storage Monitoring
Overview
Azure Storage Monitoring allows you to track the performance and health of your Azure Storage resources. It provides insights into metrics like request rates, latency, and capacity utilization, helping you optimize storage efficiency and detect issues early. You can use Azure Monitor and Azure Storage Metrics to configure alerts and gain visibility into the performance and availability of your storage accounts.
What is Azure Monitor?
Azure Monitor is a comprehensive monitoring and management service provided by Microsoft Azure. It allows you to collect, analyze, and act on telemetry data from various Azure resources and applications. Azure Monitor provides insights into the performance, health, and availability of your resources, enabling you to detect and diagnose issues, set up alerts, and gain visibility into your applications and infrastructure. It supports various data sources, including metrics, logs, and traces, and offers a centralized platform for monitoring and managing your Azure environment.
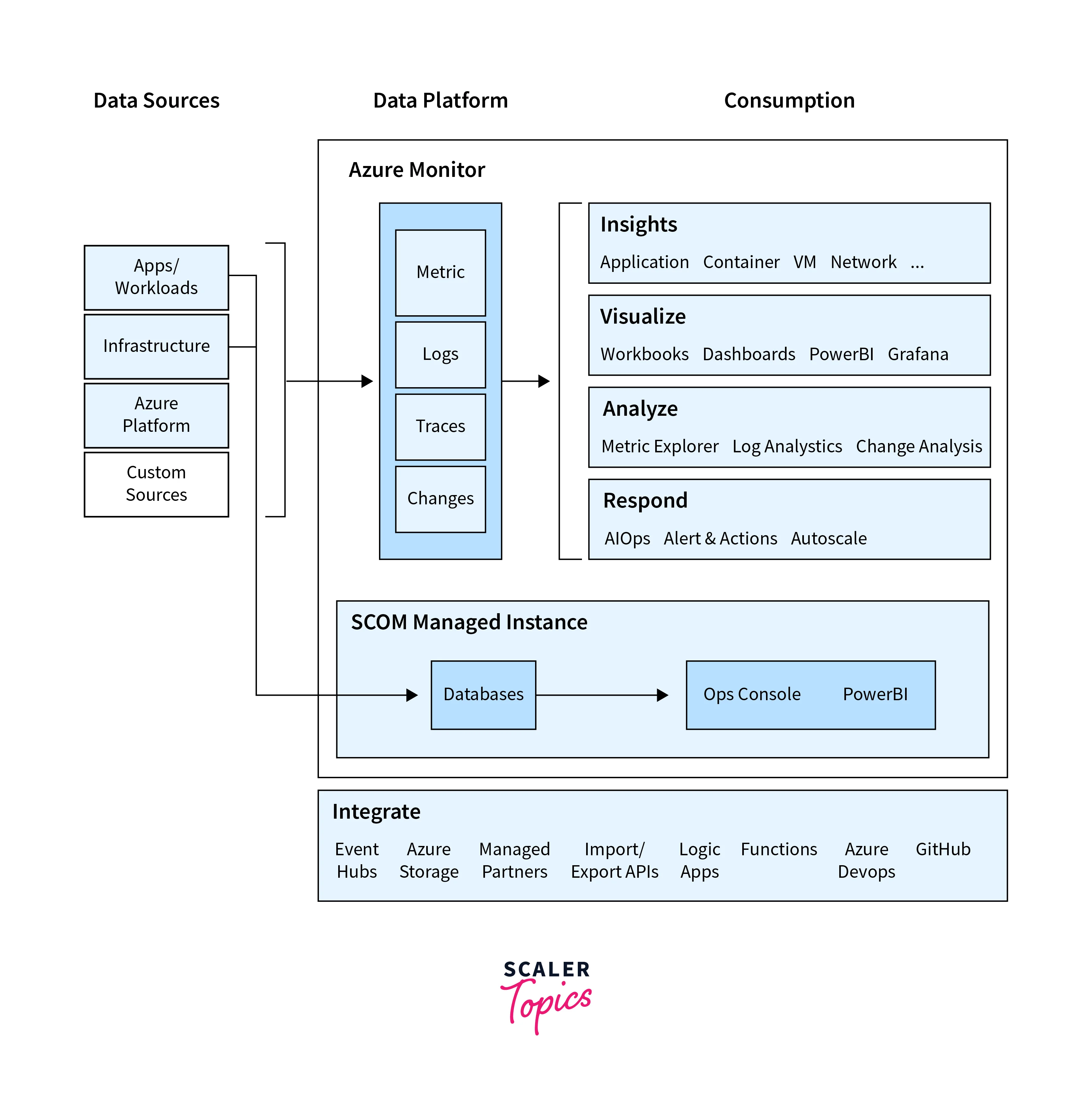
Monitoring data
Monitoring data in Azure Storage Monitoring specifically refers to the information and metrics collected and analyzed within the context of Azure Storage services. Here are some key points related to monitoring data in Azure Storage:
- Metrics: Azure Storage Monitoring captures various performance metrics such as request rates, latency, ingress/egress data, and capacity utilization for your Azure Storage accounts.
- Logs: It also records logs related to activities and events within your Azure Storage accounts, including audit and diagnostic logs.
- Retention: Azure Storage Monitoring allows you to specify the retention period for these metrics and logs to meet your compliance and auditing requirements.
- Analysis: You can analyze this monitoring data to gain insights into the behavior and performance of your Azure Storage resources, helping you optimize and troubleshoot.
Collection and routing
"Collection and routing" refer to the processes involved in gathering telemetry data and sending it to the appropriate destination for analysis and storage. Here are key points related to collection and routing:
- Data Collection: Collection involves gathering telemetry data from various sources, such as virtual machines, applications, network devices, and cloud services. This data includes metrics, logs, and traces.
- Agents and Data Collectors: Agents and data collectors, often installed on the monitored resources, are responsible for collecting telemetry data. For example, the Azure Monitor agent collects data from Azure resources and virtual machines.
- Routing: Once collected, data needs to be routed to its destination. This may involve sending data to different storage solutions, analytics tools, or dashboards for further processing and analysis.
- Data Sources: Collection and routing can handle data from diverse sources, including infrastructure, applications, databases, and services.
- Aggregation: Data may be aggregated or consolidated before routing to reduce the volume of data and make it more manageable for analysis.
Destination limitations
"Destination limitations" in the context of monitoring and telemetry data refer to the constraints and restrictions that apply to the location or system where you send or store your collected telemetry data. These limitations can vary based on the specific monitoring and data storage solutions you are using. Here are some common examples:
- Storage Capacity: The destination may have limitations on the amount of data it can store. You may need to manage data retention policies to stay within storage capacity limits.
- Data Retention Period: Some destinations have restrictions on how long they can retain data. You may need to comply with data retention policies and ensure you don't store data beyond the allowed timeframe.
- Data Throughput: Destinations may have limitations on the rate at which data can be ingested. You may need to ensure that your data collection and routing processes do not exceed these throughput limits.
- Cost Constraints: Depending on your subscription or service plan, there may be cost constraints associated with sending data to certain destinations. Be aware of pricing models and cost considerations.
- Data Formats: Some destinations may support only specific data formats or require data to be transformed into a particular format before ingestion.
- Access Control: Ensure that you have the necessary permissions and access control in place to send data to the destination. This includes authentication and authorization requirements.
Analyzing metrics
In Azure Storage Monitoring, metrics analysis refers to the process of examining and making sense of the performance and health data, referred to as metrics, collected from your Azure Storage resources. These metrics provide valuable insights into how your storage resources are functioning. Here's what metrics analysis entails:
- Metric Selection: Choose the specific metrics you want to analyze. Azure Storage offers a range of metrics, including request rates, response times, ingress and egress data, and more.
- Time Range Selection: Set the time range for the data you wish to analyze. You can look at real-time data, historical data, or specify a custom time period.
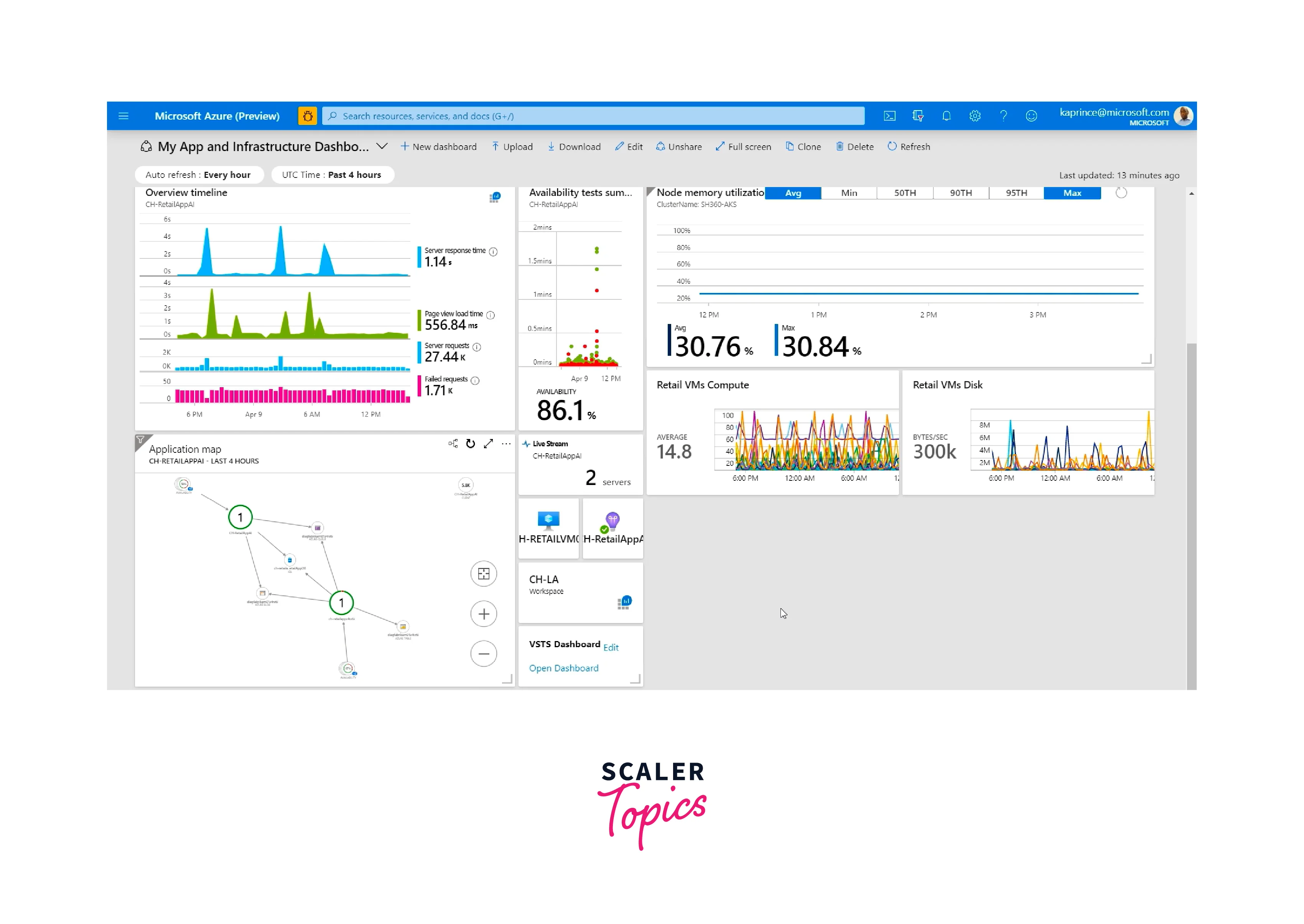
- Visualization: Utilize charts and graphs to visualize the selected metrics. This graphical representation helps in quickly identifying trends, patterns, and anomalies.
- Aggregation: Metrics can be aggregated over different time intervals (e.g., hourly, daily) to provide a high-level view of your storage performance.
- Historical Analysis: Analyze historical data to identify long-term trends, seasonality, and recurring patterns in your storage performance.
Analyzing logs
Analyzing logs involves examining textual records of events and activities to gain insights, troubleshoot issues, and improve the performance and security of systems, applications, or resources. Here's how to effectively analyze logs:
- Collect Relevant Logs: Ensure that you are collecting the logs that are relevant to your objectives. Logs can include application logs, system logs, security logs, and more.
- Centralized Logging: Store logs centrally in a dedicated location or logging service for easy access and analysis. Azure offers solutions like Azure Monitor and Azure Log Analytics for this purpose.
- Data Ingestion: Ingest log data from various sources, including servers, applications, cloud services, and network devices, into your logging platform.
- Search and Query: Use powerful search and query languages (e.g., Kusto Query Language in Azure Log Analytics) to retrieve specific log entries and filter data based on keywords, timeframes, or custom criteria.
- Visualize Log Data: Create visual representations of log data using charts, graphs, and dashboards to identify trends, anomalies, and patterns.
- Correlation: Correlate log entries from different sources to identify relationships between events and gain a comprehensive view of system behavior.
Alerts
In the context of monitoring and managing systems, applications, and resources, "alerts" refer to notifications or warnings that are triggered based on predefined conditions or thresholds. Alerts are a crucial component of proactive monitoring and incident management.
- Thresholds: Alerts are typically triggered when specific metrics, measurements, or events cross predefined thresholds. For example, you can set an alert to notify you when CPU utilization exceeds 90%.
- Conditions: Alerts can be based on various conditions, such as a specific value, a rate of change, or a combination of multiple conditions. This allows you to fine-tune when alerts are triggered.
- Notification Channels: Alerts can be sent to various notification channels, such as email, SMS, pager, mobile apps, or integration with incident management systems like Microsoft Teams, Slack, or other collaboration tools.
- Severity Levels: Alerts are often categorized by severity levels (e.g., critical, warning, informational) to prioritize responses and actions.
Security Considerations
Security considerations related to monitoring data and logs in Azure are crucial to maintaining a robust and compliant data security posture. Here are some key points to keep in mind:
- Data Encryption: Ensure that all data and logs collected by Azure monitoring tools are encrypted both in transit and at rest. Utilize Azure's encryption capabilities, such as Azure Disk Encryption and Azure Storage Service Encryption, to safeguard your data.
- Data Retention and Purging: Define data retention policies to manage log data effectively. Regularly review and purge logs that are no longer needed to minimize the risk of exposure in case of unauthorized access.
- Audit Logging: Enable audit logging for monitoring activities within your Azure environment. This ensures that any changes to access controls or configurations are recorded and can be reviewed for security and compliance purposes.
- Monitoring Alerts: Implement alerts to notify you of any unusual or suspicious activities in your monitoring data and logs. Proactive monitoring can help identify and mitigate security incidents in real-time.
Conclusion
- Azure Monitor is Microsoft Azure's comprehensive monitoring and management service for tracking the performance, health, and security of Azure resources.
- Monitoring data refers to the information collected and analyzed from various sources to gain insights into the performance, health, and status of systems, applications, or resources.
- Collection and routing involve the processes of gathering telemetry data from various sources and sending it to the appropriate destination for analysis and storage.
- Destination limitations are constraints and restrictions that apply to the location or system where telemetry data is sent, affecting storage capacity, data retention, and other factors.
- Analyzing metrics entails examining numerical measurements to gain insights into the performance, health, and behavior of systems, applications, or resources.
- Analyzing logs involves examining textual records of events to gain insights, troubleshoot issues, and improve the performance and security of systems or applications.
- Alerts are notifications triggered based on predefined conditions or thresholds, crucial for proactive monitoring and incident management in IT operations.
