Azure Virtual Machine Security
Overview
Azure Virtual Machine Security encompasses a range of measures and features to protect virtual machines on the Azure cloud platform. It includes antimalware solutions, disk encryption, hardware security modules, and backup capabilities. Azure Site Recovery enables disaster recovery, ensuring business continuity. Virtual networking features, security policy management, and compliance certifications further enhance security. Azure Confidential VMs offer an extra layer of protection for sensitive data.
What is Azure Virtual Machine Security?
Azure Virtual Machine Security refers to the set of practices and measures implemented to safeguard virtual machines (VMs) running on the Microsoft Azure cloud platform. It is essential to ensure the confidentiality, integrity, and availability of VMs and the data they host. Azure VM security encompasses a range of features and best practices designed to protect against threats, vulnerabilities, and unauthorized access. Some key aspects of Azure Virtual Machine Security include:
-
Antimalware Protection:
Azure provides built-in antimalware solutions that defend VMs against malware, viruses, and other security threats. Azure Security Center enables you to activate antimalware protection for both Windows and Linux VMs.
-
Disk Encryption:
Encrypting the data on VM disks is vital for protecting it from unauthorized access. Azure Disk Encryption uses encryption standards like BitLocker for Windows VMs and DM-Crypt for Linux VMs to ensure data confidentiality.
-
Hardware Security Modules (HSMs):
For advanced encryption and key management, Azure offers Hardware Security Modules. HSMs are tamper-resistant devices that protect cryptographic keys and operations, enhancing the security of VMs.
-
Backup and Disaster Recovery:
Azure Backup allows automated backups of VMs, including operating systems, application data, and configurations. Azure Site Recovery provides disaster recovery capabilities, replicating VMs to a secondary Azure region for business continuity.
-
Virtual Networking:
Azure's virtual networking capabilities help you isolate VMs, control network traffic, and secure communication. Features like Virtual Network, Network Security Groups (NSGs), and Azure Firewall provide network security options.
Antimalware
Azure provides built-in antimalware protection to defend your VMs against viruses, malware, and other security threats. With Azure Security Center, you can enable antimalware solutions for both Windows and Linux VMs, ensuring that your virtual machines are shielded from malicious software. Here are key points about antimalware:
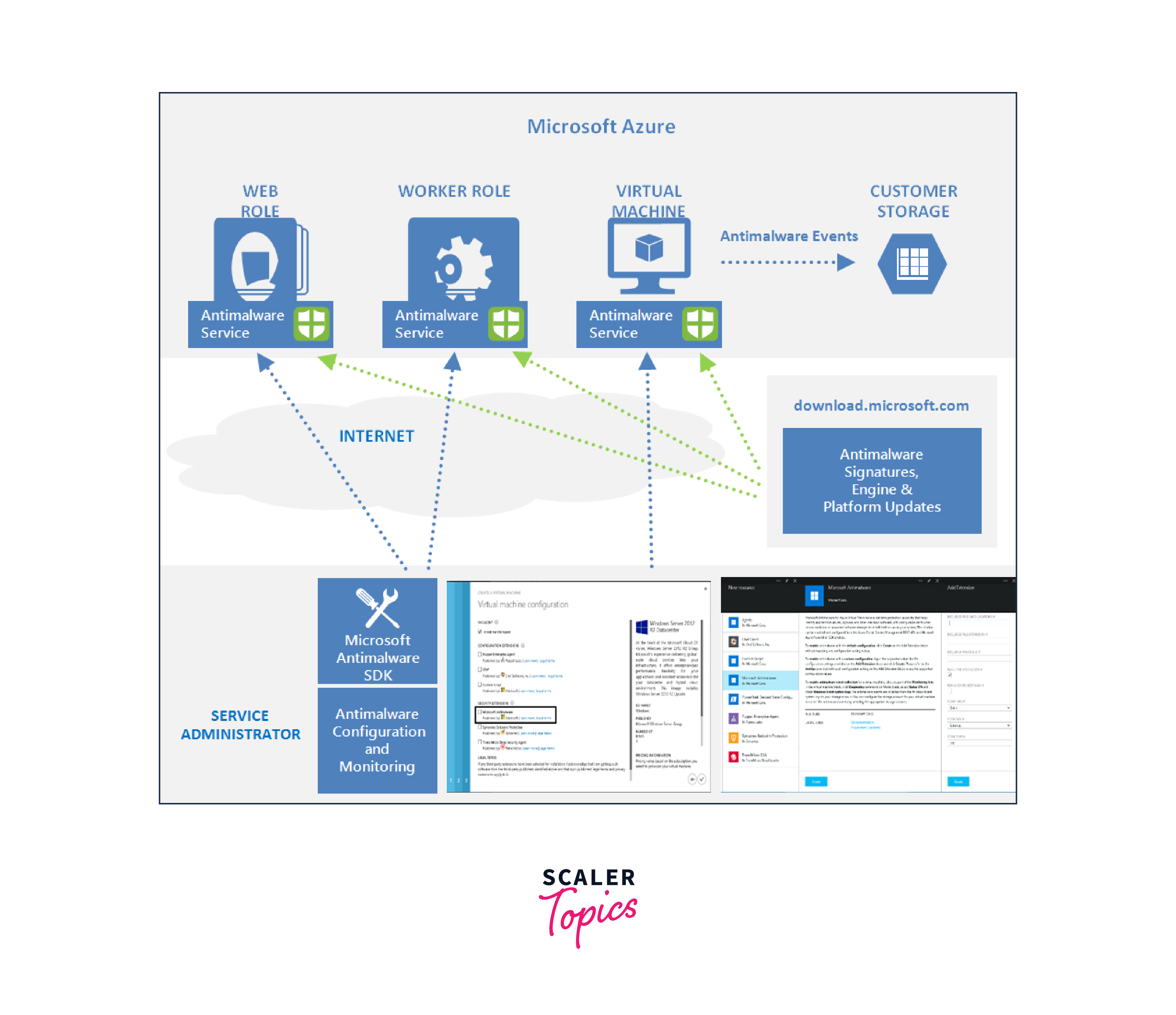
-
Detection and Prevention:
Antimalware tools are specifically designed to identify and prevent malware from infecting computers and networks. They use various techniques, such as signature-based scanning, behavioral analysis, and heuristics, to recognize and block malicious code.
-
Real-Time Protection:
Many antimalware solutions provide real-time protection by constantly monitoring system activities and incoming files. When a potential threat is detected, the software takes immediate action to quarantine or remove it.
-
Regular Updates:
Antimalware software is only effective when it's up-to-date. Malware authors continually develop new threats, so antimalware vendors regularly release updates to recognize and combat these emerging dangers.
-
Multiple Layers of Defense:
Effective security often involves multiple layers of defense. Antimalware is just one part of a comprehensive security strategy, which may also include firewalls, intrusion detection systems, and secure browsing practices.
-
User Education:
While antimalware tools are crucial, user education is equally important. Users must be aware of the risks associated with downloading files from untrusted sources, clicking on suspicious links, and opening email attachments from unknown senders.
-
Commercial and Open-Source Solutions:
Antimalware solutions are available as both commercial products and open-source projects. Commercial options often offer advanced features, technical support, and additional layers of security. Open-source alternatives provide cost-effective protection, but may require more technical expertise to implement.
Hardware Security Module
For scenarios requiring advanced encryption and key management, Azure offers Hardware Security Modules (HSMs). HSMs are tamper-resistant devices that secure cryptographic keys and operations. By using Azure Dedicated HSM, you can enhance the security of your VMs by protecting sensitive data and cryptographic keys.
Virtual Machine Disk Encryption
Encrypting the data on your Azure VM disks is essential for protecting it from unauthorized access. Azure Disk Encryption uses industry-standard BitLocker encryption for Windows VMs and DM-Crypt for Linux VMs. This feature ensures that your data remains confidential even if an unauthorized individual gains access to the underlying storage.
Virtual Machine Backup
Regular backups are an integral part of any security strategy. Azure Backup allows you to create automated backups of your VMs, including the operating system, application data, and configuration settings. These backups can be crucial for recovering your VMs and data in the event of data loss, accidental deletions, or security incidents.
Azure Site Recovery
Azure Site Recovery is a Microsoft Azure service that provides disaster recovery and business continuity solutions for on-premises and cloud-based workloads. It allows organizations to replicate and recover their applications and data in the event of planned or unplanned outages, ensuring minimal downtime and data loss. Here are key aspects of Azure Site Recovery:
-
Replication:
Azure Site Recovery enables continuous replication of on-premises physical servers, virtual machines, and Azure virtual machines to Azure data centers. This replication can be asynchronous, ensuring data is up to date in the target location.
-
Business Continuity:
In the event of a disaster or outage, Azure Site Recovery allows for a seamless failover to the replicated workloads in Azure. This ensures business continuity and minimizes downtime.
-
Supported Workloads:
It supports a wide range of workloads, including Windows and Linux virtual machines, physical servers, and VMware virtual machines.
-
Multi-VM Consistency:
Azure Site Recovery ensures the consistency of multi-tier applications by replicating all related VMs together. This helps in maintaining application integrity during failover.
Virtual Networking
Azure's virtual networking capabilities enable you to isolate your VMs, control network traffic, and secure communication between VMs. Features like Azure Virtual Network, Network Security Groups (NSGs), and Azure Firewall provide robust network security options to protect your VMs from network-based attacks.
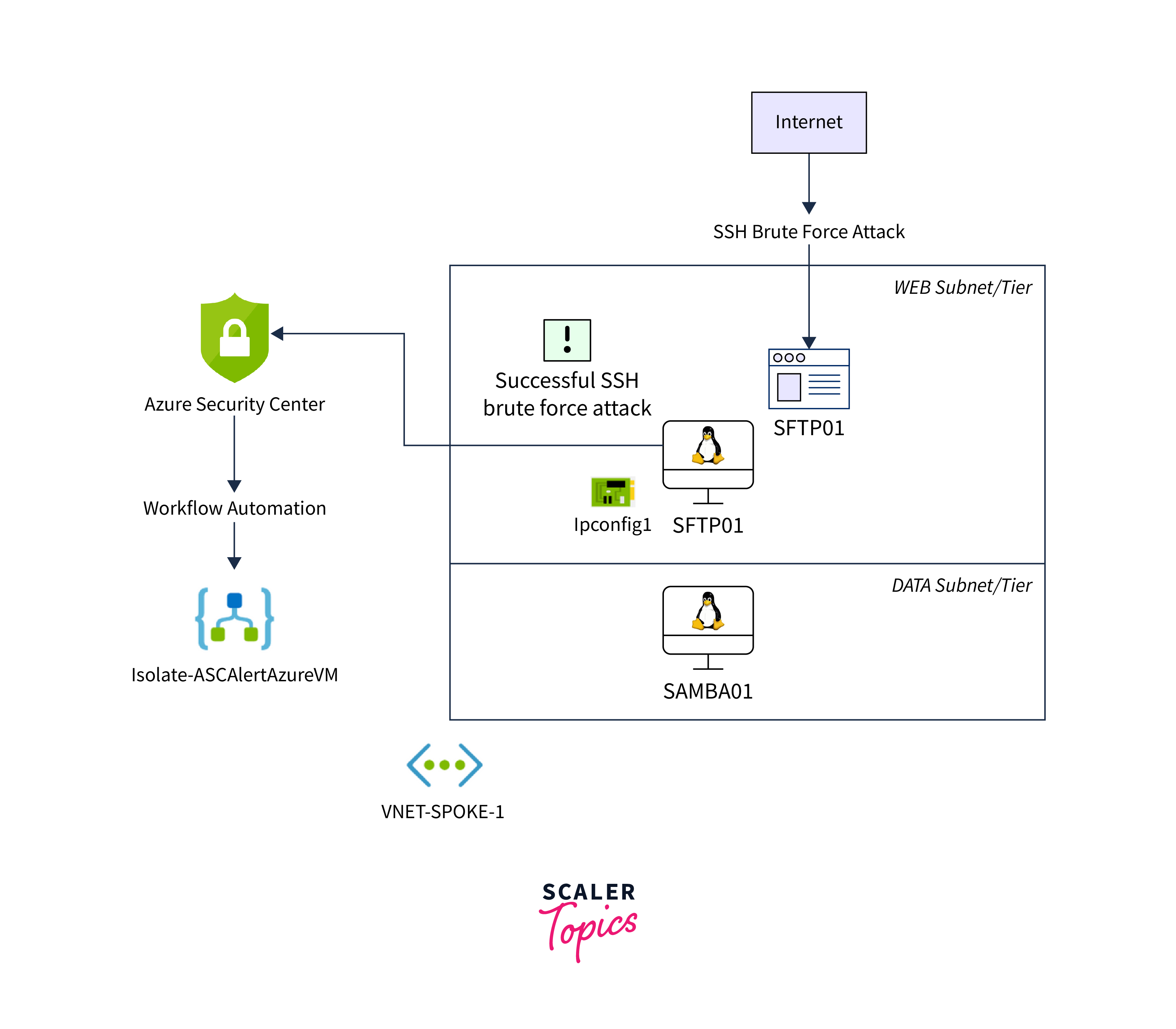
Security Policy Management and Reporting
Azure Security Center provides a centralized platform for managing security policies, detecting threats, and generating security reports. It helps you maintain compliance with security best practices and provides recommendations for enhancing the security of your VMs.
Security policy management and reporting play a critical role in compliance management and threat detection within an organization's cybersecurity framework. Let's explore how they contribute to these aspects:
Compliance Management:
-
Policy Enforcement:
Security policy management ensures that all security policies and controls are defined, implemented, and enforced consistently across an organization's IT infrastructure. This alignment with regulatory requirements and industry standards is crucial for compliance.
-
Audit Trail:
Policy management systems maintain detailed logs and records of policy changes, user access, and security events. These audit trails are essential for compliance audits, allowing organizations to demonstrate adherence to security and privacy regulations.
-
Policy Customization:
Organizations can tailor security policies to align with specific compliance frameworks such as GDPR, HIPAA, or PCI DSS. This customization ensures that security controls address the unique requirements of each regulation.
Threat Detection:
-
Baseline Creation:
Security policies establish a baseline for "normal" behavior within the network. Any deviations from this baseline can be flagged as potential security threats. Policy management systems help in defining and continuously monitoring these baselines.
-
Anomaly Detection:
Automated systems can identify unusual or suspicious activities that may signify a security breach. For instance, if a policy dictates that certain ports should never be open, any unauthorized attempts to open them can trigger alerts.
-
Event Correlation:
Policy management tools analyze security events and incidents to identify patterns or correlations that may indicate a security threat. For instance, multiple failed login attempts from different locations can be indicative of a brute force attack.
Compliance
Azure VMs adhere to a wide range of compliance standards and certifications, including GDPR, HIPAA, and ISO 27001. This compliance ensures that your VMs meet the requirements of various industries and regulatory bodies, demonstrating a commitment to data security and privacy.
Confidential Computing
Confidential computing in Azure is a security feature that provides a trusted execution environment for workloads running in the cloud. It's designed to protect sensitive data and code from unauthorized access, even from cloud administrators or the infrastructure provider, such as Microsoft Azure itself. Here are key aspects of confidential computing in Azure:
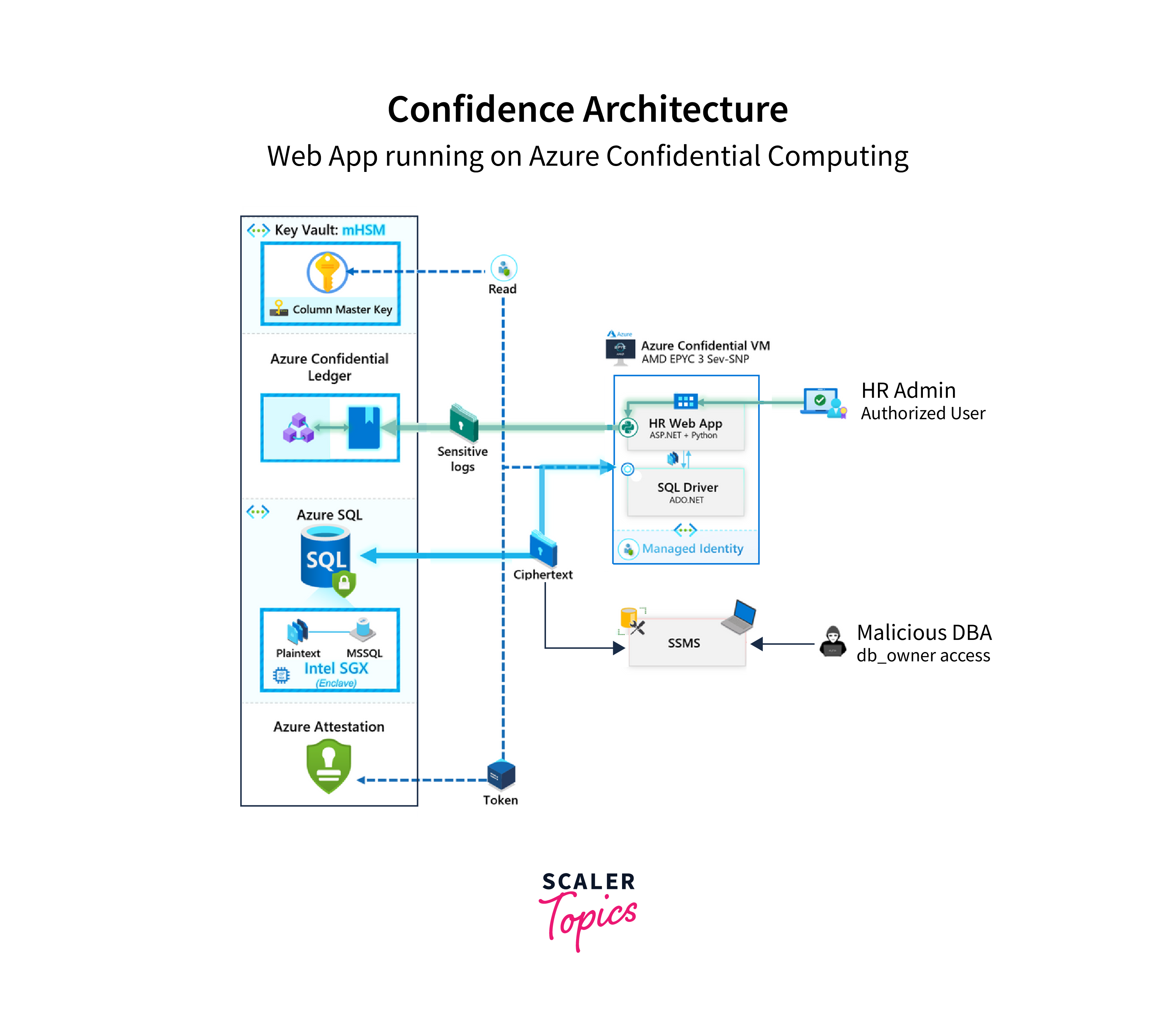
-
Enclave Technology:
At the core of confidential computing in Azure is the use of secure enclaves. These enclaves are isolated, protected areas of the CPU and memory that are shielded from the underlying infrastructure. This isolation ensures that data and code within the enclave are safe from inspection.
-
Data Protection:
Azure confidential computing is particularly important for scenarios where sensitive data, such as financial or healthcare information, needs to be processed in the cloud. With enclaves, the data is kept encrypted and confidential even during processing.
-
Code Protection:
In addition to data protection, confidential computing in Azure also safeguards the code being executed within an enclave. This means that proprietary algorithms or intellectual property can be processed securely in the cloud.
-
Intel SGX Technology:
Azure uses Intel Software Guard Extensions (SGX) technology to create these secure enclaves. SGX enables the creation of isolated, trusted execution environments where code and data can be processed securely.
-
Use Cases:
Confidential computing in Azure is useful in various industries and scenarios. For example, it can be used in healthcare for processing patient data, in financial services for protecting sensitive financial information, and in scenarios where secure data analysis is required.
Conclusion
- Azure Virtual Machine Security encompasses a comprehensive set of security features and practices to protect VMs and the data they host. These measures are essential for safeguarding your virtualized infrastructure and maintaining the integrity of your applications and data in the Azure cloud.
- Securing your Azure Virtual Machines is an ongoing process that demands careful planning and implementation of various security measures and best practices. Azure's built-in security features, such as antimalware protection, encryption, and compliance certifications, provide a strong foundation for safeguarding your VMs.
- By leveraging these tools and following security best practices, you can enhance the protection of your virtualized infrastructure and maintain the integrity of your data and applications in the Azure cloud.
