Network Interface In Azure
Overview
Azure offers a wide range of robust cloud services that empower organizations to scale, innovate, and deploy solutions globally. Network Interface is a crucial element in communication and orchestrating connections within the Azure ecosystem. We will explore the features, configurations, and steps to create a Network Interface In Azure.
What is Azure Network Interface
Azure Network Interface is a network interface card (NIC) that connects a VM to a VNet. Think of it as the gateway that allows a VM to communicate with other resources in a network. It plays an important role in managing the flow of data to and from a Virtual Machine, ensuring seamless connectivity within the Azure environment.
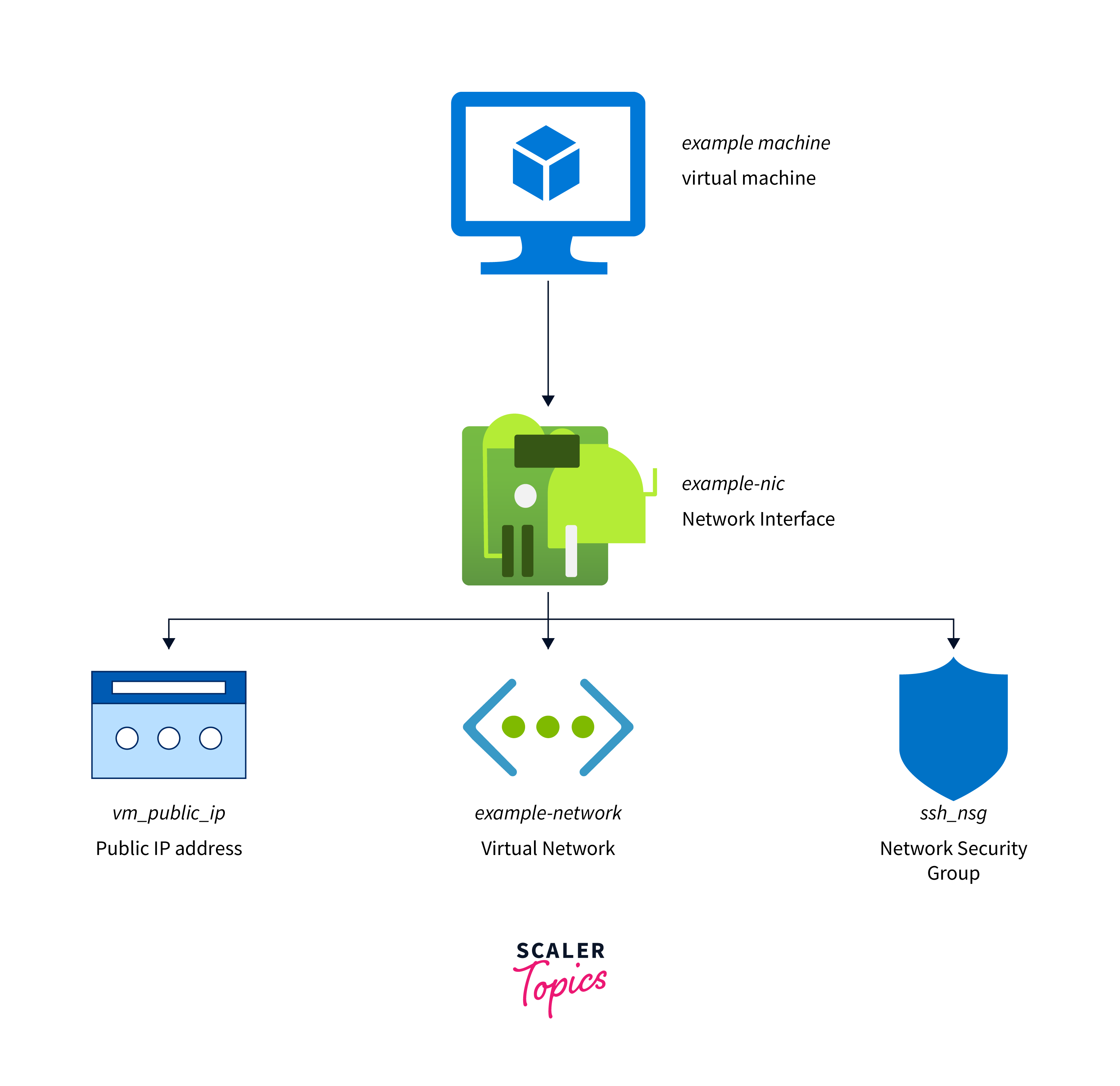
The Network Interface's Configuration
The configuration of a Network Interface in Azure involves a set of parameters that instruct how it communicates within the Azure environment. Each aspect plays an important role in shaping the behaviour and security of network traffic.
Vnets & Subnets
A VNet is a logically isolated section of the Azure network, while Subnets are subdivisions within a VNet.
Features:
- Logical isolation or different VNets act as separate, independent networks, offering enhanced security and control.
- Scaled up or down to accommodate changing workloads.
- Foundational structure for implementing NSGs, providing a structured environment to define and enforce network security policies.
Configuration Options: Define the IP address ranges for both the VNet and its associated Subnets. This ensures that resources within the VNet can communicate with each other. For scenarios requiring communication between VNets, configuration options like VNet Peering or Virtual Network Gateways can be used.
IP Configuration
Each Network Interface is assigned one or more IP configurations. These configurations include private IP addresses, associated public IP addresses (if required), and network security group (NSG) settings.
Features:
- Allows the assignment of both public and private IP addresses.
- IP addresses can be dynamically assigned by Azure or set statically to ensure consistency.
- Load balancing enables traffic distribution across multiple resources for enhanced performance and availability.
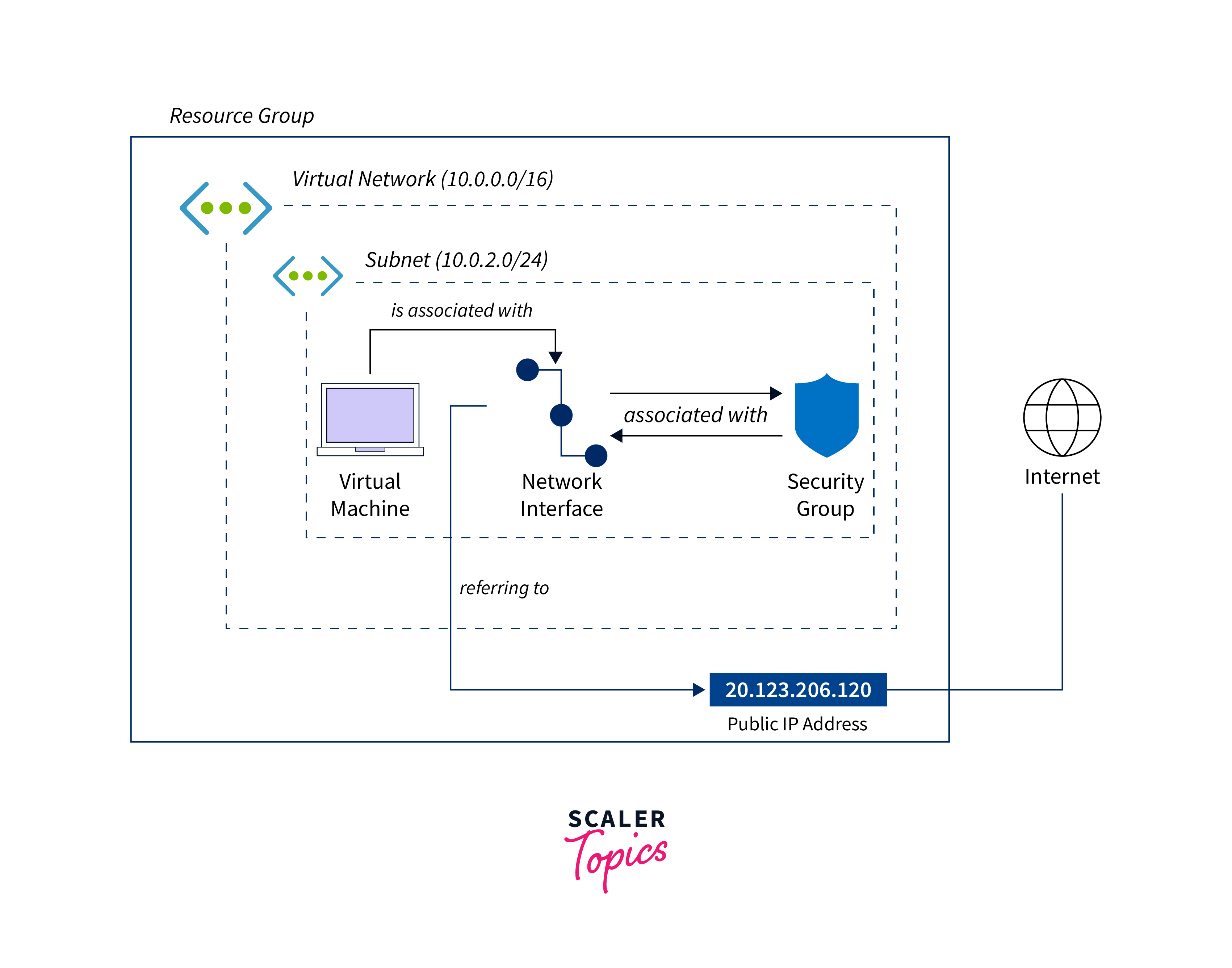
Configuration Options: Choice between dynamic and static assignment can be made in the Configuration section of the resource. Within a VNet, navigate to the specific Subnet > Settings > IP Configurations. Here, you can add or modify private IP configurations.
NSG & Routes
Network Security Groups (NSGs) act as virtual firewalls, controlling inbound and outbound traffic to a Network Interface. Additionally, routes define the path that network traffic takes, ensuring it reaches its destination efficiently.
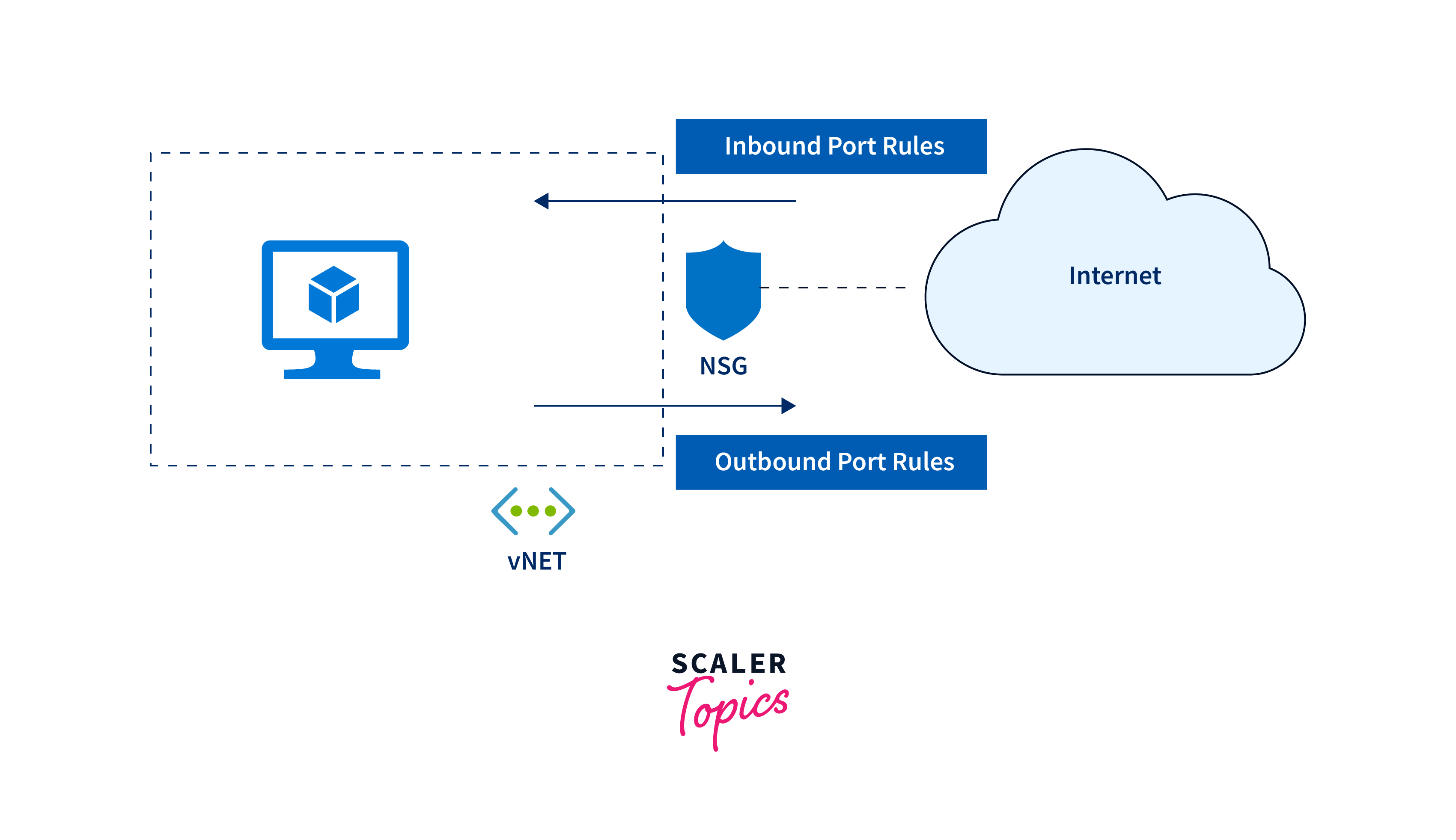
Features:
- Creation of ACLs that define inbound and outbound traffic rules.
- Filter traffic based on the source, destination, and protocol.
- Work with route tables to ensure that traffic is directed as intended.
Configuration Options: Within the NSG settings, navigate to Inbound security rulesorOutbound security rules and add rules based on the desired criteria (source, destination, port, etc.). NSG can be associated with a VNet by Subnets > select the Subnet > Associate > choose the NSG.
IP Forwarding
IP Forwarding is a crucial feature that allows a Virtual Machine to act as a network router. This capability is especially valuable in scenarios where complex network architectures or load-balancing configurations are required.
Features:
- Essential in load balancing configurations, allowing a VM to efficiently distribute traffic across multiple resources.
- Seamless communication between Azure and on-premises environments.
Configuration Options: In the desired VM > Settings > Networking > select the network interface > IP configurations > toggle IP forwarding to Enabled. Define custom routes within the route tables to ensure that traffic is directed appropriately when IP Forwarding is enabled.
DNS Servers
Domain Name System (DNS) servers are essential for translating human-readable domain names into IP addresses. Configuring DNS servers for a Network Interface ensures that it can seamlessly communicate with resources both within and outside the Azure environment.
Features:
- Translate human-readable domain names into IP addresses.
- Use of custom DNS servers, providing flexibility in DNS resolution for business requirements.
- High availability and redundancy, ensuring that DNS services remain accessible and reliable.
Security Considerations
Data security is a critical aspect of monitoring. Here are some key security considerations when dealing with monitoring data and logs:
- Ensure data privacy and compliance with regulations, such as GDPR or HIPAA. Employ data masking, encryption, and access controls to protect sensitive data within logs.
- Implement robust access controls and authentication mechanisms to restrict access to monitoring data.
- Data transmitted between monitoring components or stored in log files should be encrypted to protect it from interception and tampering using encryption techniques (e.g., AES-256).
- Implement intrusion detection systems (IDS) to identify unauthorized access attempts to monitoring components. Implement anomaly detection algorithms to flag unusual or suspicious activities.
IP Addresses
Public IP Addressing
- Public IP addresses provide a direct connection to the internet.
- They are essential when a Virtual Machine needs to be accessed from the outside world.
- Azure allows for dynamic or static assignment of public IP addresses, depending on the specific requirements of the deployment.
Private IP Addressing
- Private IP addresses are used for internal communication within the Azure network.
- They are assigned from a reserved address space and are not routable over the internet.
- This ensures that communication remains confined within the Azure environment, ensuring security.
Hostname Resolution
Hostname resolution is the process of translating human-readable hostnames into IP addresses. Consider a scenario where a user attempts to access a website, say www.scalar.com.
- When the user enters this domain name into their browser, the system initiates a request to find the corresponding IP address.
- The system first checks its local DNS cache.
- If there's no cached record, the system contacts a DNS resolver. This resolver is often provided by the user's Internet Service Provider (ISP).
- The resolver queries the root DNS servers, asking for the location of the authoritative DNS server for .com domains. Once located, it queries this authoritative server for the IP address of www.scalar.com, which is also cached locally for future reference.
- The system establishes a connection to the web server hosting www.scalar.com.
Internal DNS Hostname Resolution (for VMs)
Azure provides a built-in DNS service that allows VMs to resolve hostnames to their respective IP addresses within a VNet. This internal DNS resolution ensures smooth communication between resources, eliminating the need for manual IP address management.
Consider a scenario where multiple VMs coexist within a VNet. Each VM is assigned a unique hostname for easy identification, such as web-server-1 or database-instance. When one VM needs to communicate with another, it utilizes the DNS service provided by Azure. This is possible as Azure's internal DNS service maintains a record of all VMs and their corresponding private IP addresses within a VNet.
Configure Multiple NICs and IP Addresses for a VM
Follow these steps to set up multiple NICs and IP addresses for a VM:
-
On the home page of azue portal, search and select Network interfaces through the search bar on the top.
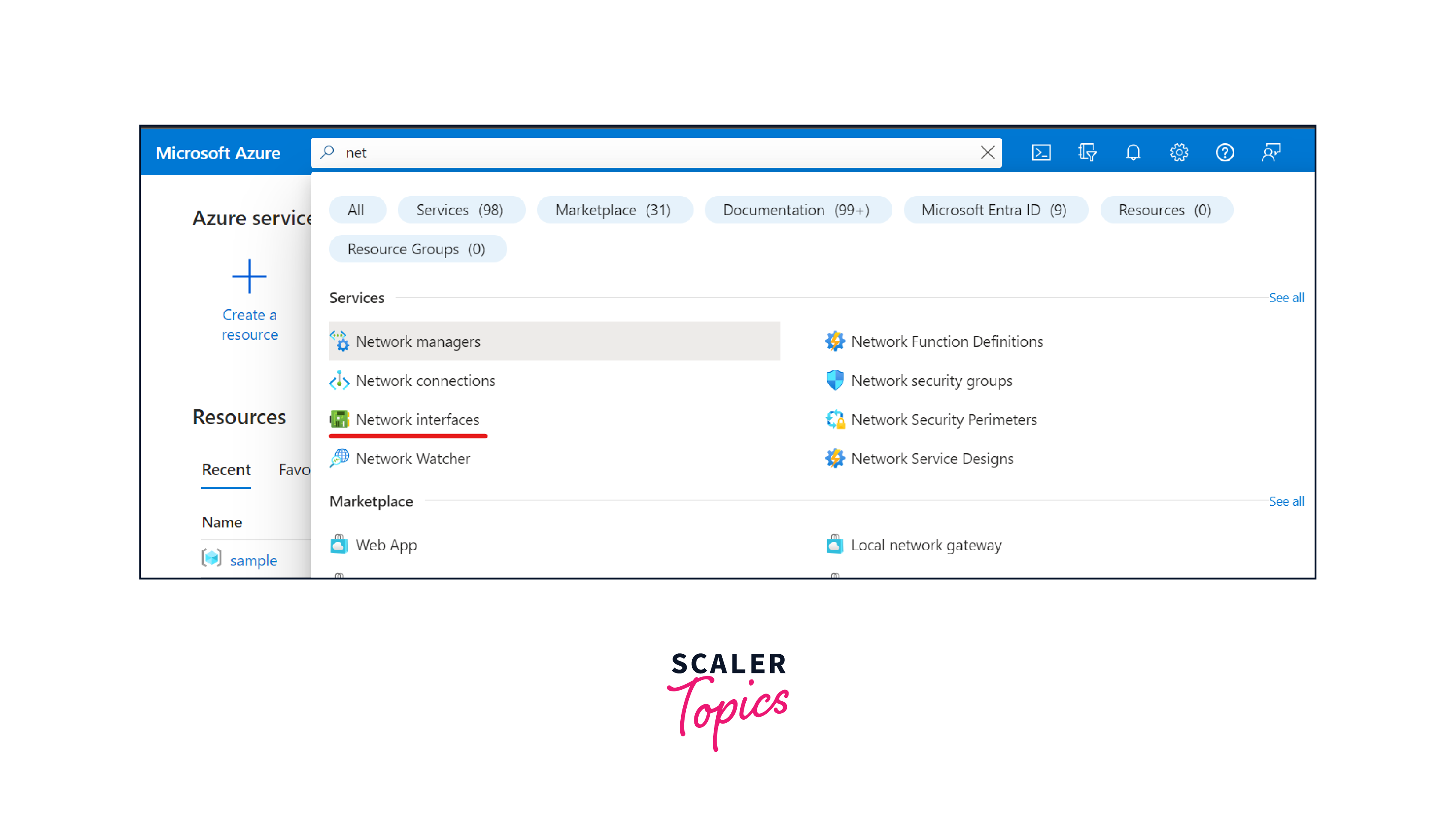
-
Click on the Create network interface button to create a new NIC.
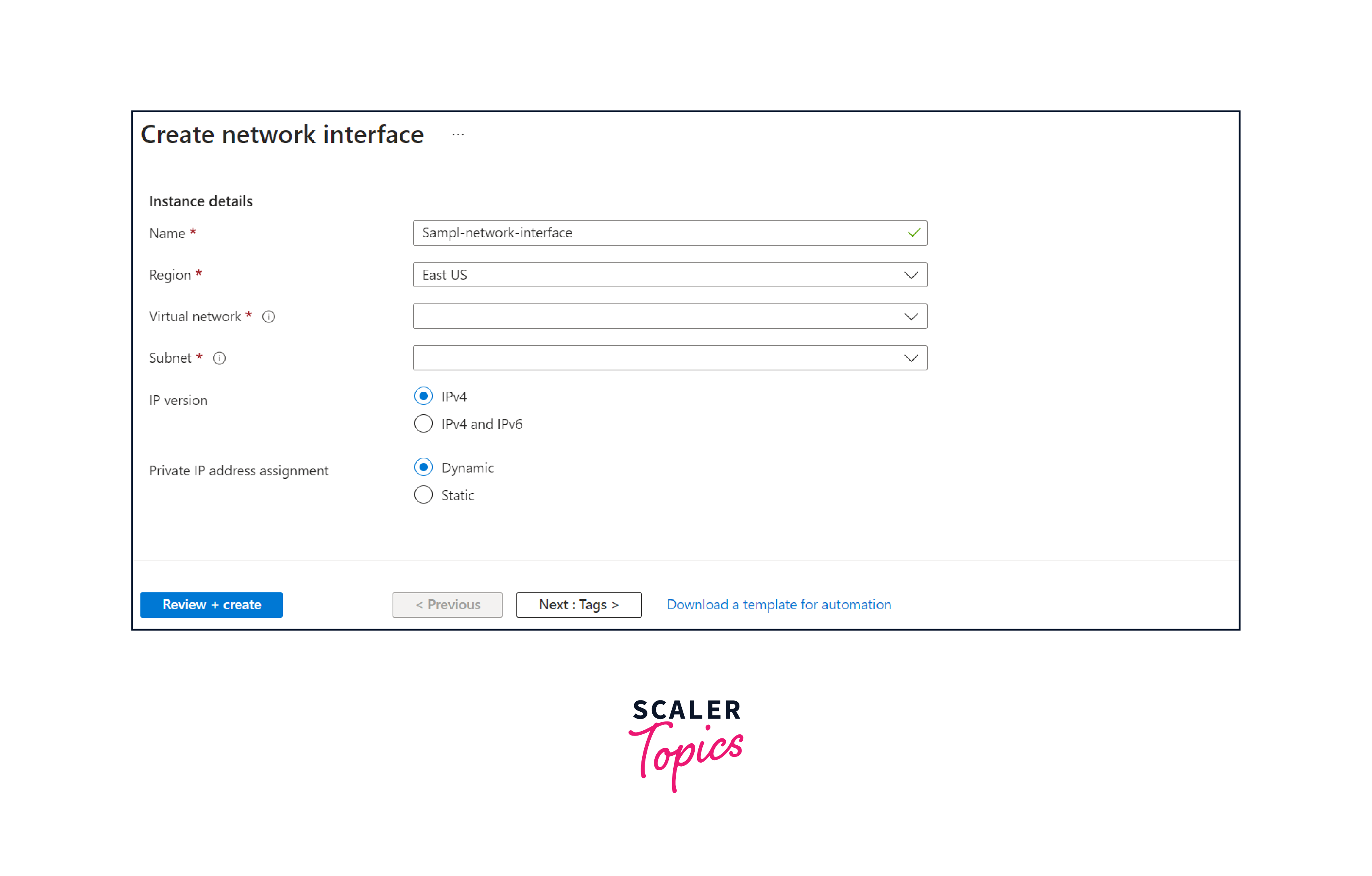
- In the Create network interface page, provide the necessary details:
- Name: Enter a descriptive name for the NIC.
- Virtual network: Choose the VNet associated with the VM.
- Subnet: Select an existing subnet or create a new one.
- Public IP: Choose whether to assign a public IP address. This is optional and depends on your specific requirements.
- Security group: Assign a Network Security Group if needed.
- IP forwarding: Enable this if you intend to use the VM as a network router.
- Click Create to finish creating the new NIC. This will take you back to the VM's Network interfaces page.
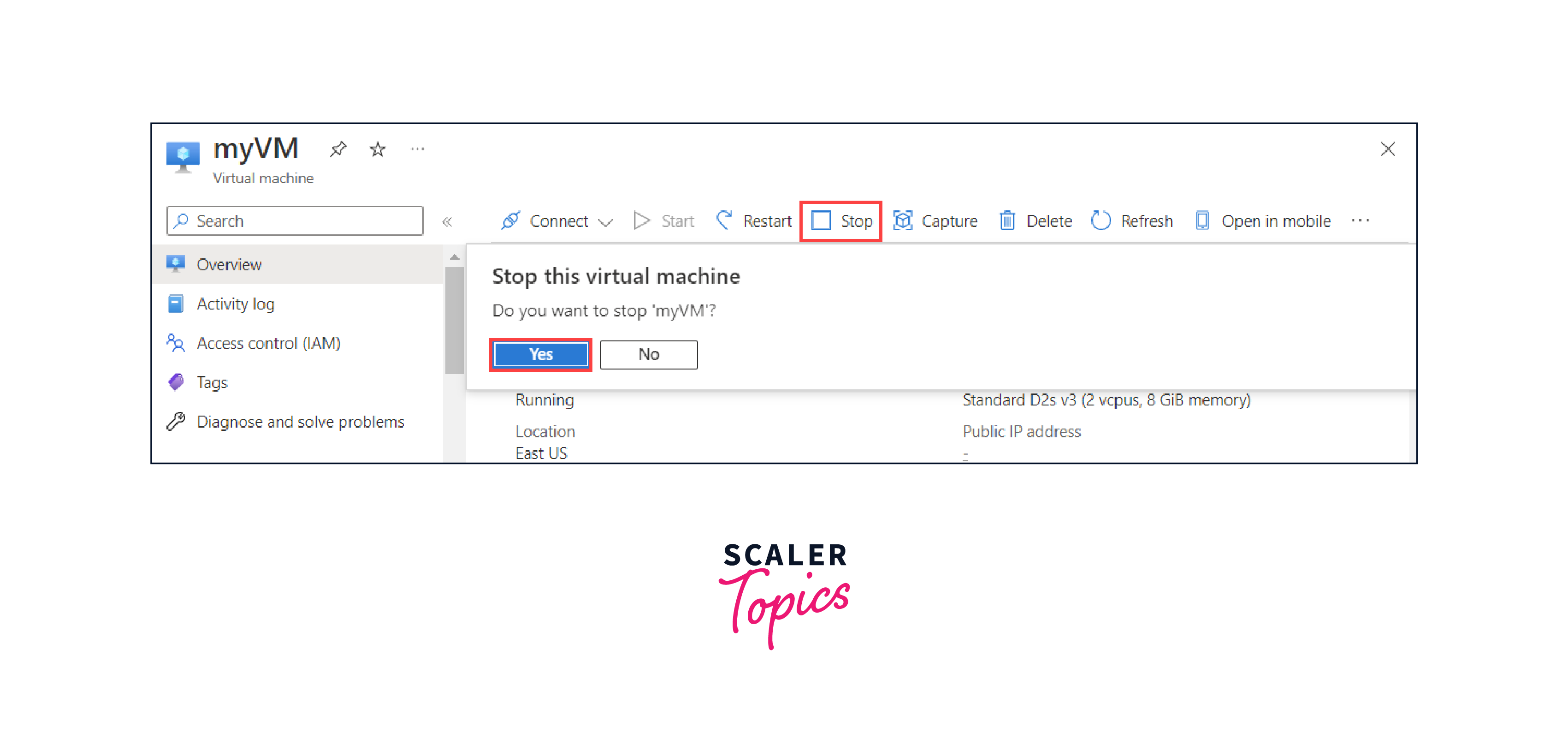
- In the Azure Portal, locate and select Virtual machines from the left-hand menu.
- Click on the VM to which you want to add multiple NICs and IP addresses and stop the VM.
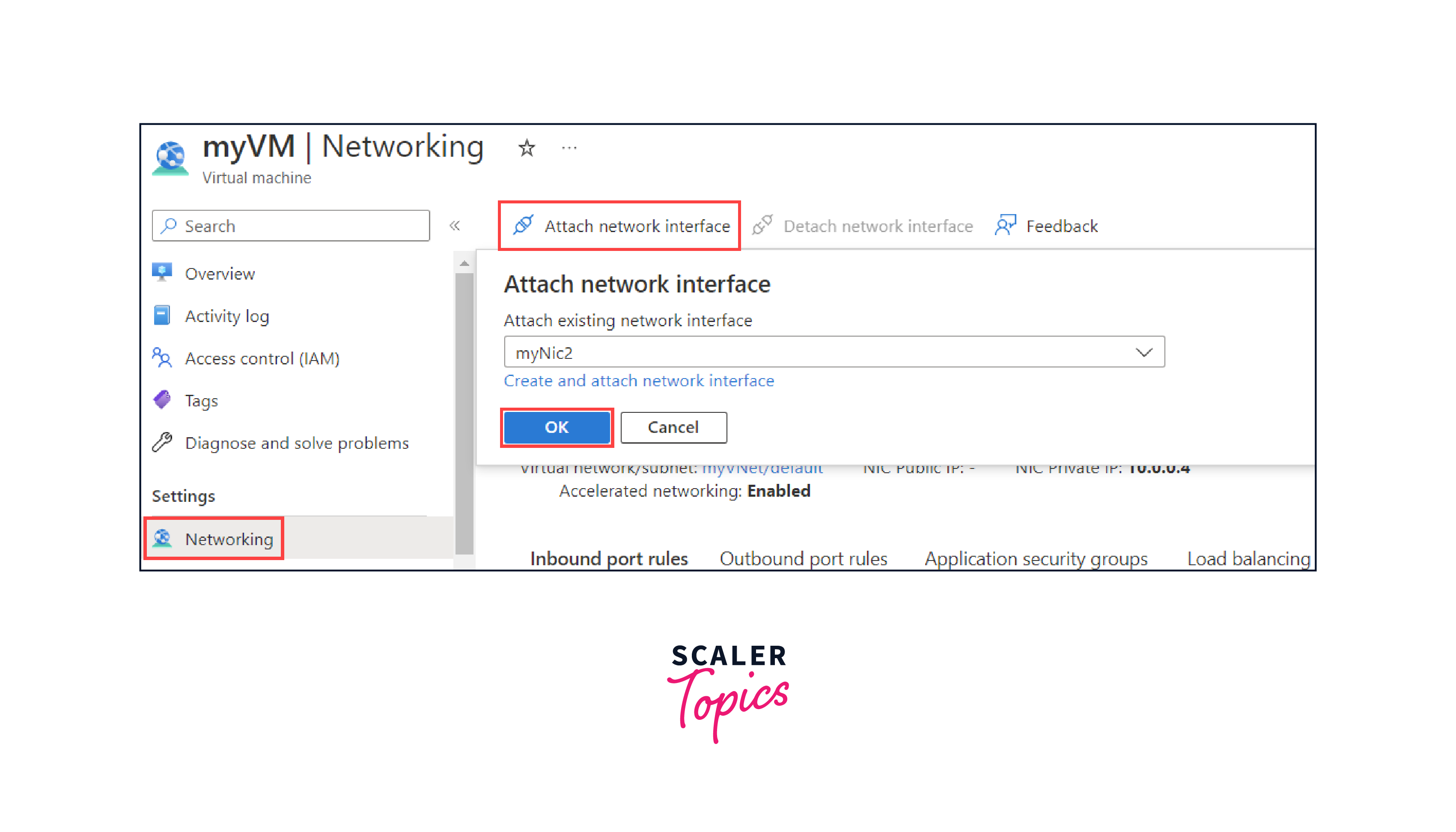
- Go to the Networking setting and click the Attach network interface button. Then select the newly created NIC from the list.
- In the NIC overview pane, select IP configurations from the left-hand menu.
- Click on the existing IP configuration or add a new one, and associate it with the appropriate VM and NIC.

- Once all the NICs and IP addresses are added, go back to the VM's Networking settings to ensure that all the NICs are listed.
- Restart the VM to apply the changes.
Conclusion
- Azure Network Interface serves as a linchpin in Azure's network architecture, acting as a vital conduit between Virtual Machines (VMs) and Virtual Networks (VNets). This seamless connectivity is important for ensuring uninterrupted communication between resources, forming the backbone of any Azure-based infrastructure.
- VNets, with their isolation capabilities, provide a secure environment for resources to operate within. Subnets further refine this structure, allowing for organized segmentation based on function or department. This not only enhances security but also aids in efficient resource management.
- The flexibility provided by IP Configuration is invaluable. It allows for the assignment of both public and private IP addresses, ensuring that resources can communicate over the internet or within a private network. This feature is particularly critical for applications that require dynamic scalability.
- Network Security Groups (NSGs) and Routes work in concert to secure network traffic and define optimal data paths. NSGs act as virtual firewalls, controlling inbound and outbound traffic while routes ensure that traffic flows efficiently.
- The capability of IP Forwarding empowers Virtual Machines to operate as network routers. This functionality is invaluable for organizations with complex network topologies or those employing load-balancing configurations.
