Azure Networking Services
Overview
Azure Networking Services provide a comprehensive and reliable networking in Azure infrastructure for cloud-based applications. It offers Virtual Networks (VNETs) to isolate resources, Azure Load Balancer for distributing traffic, and Application Gateway for web traffic management. Azure VPN Gateway ensures secure connectivity to on-premises networks, while Azure ExpressRoute establishes private connections to Microsoft's data centers. Azure Traffic Manager enables global traffic distribution across regions, and Network Watcher facilitates monitoring and diagnostics. Additionally, Azure Firewall and Network Security Groups enhance security. This article highlights how Azure Networking Services empower businesses with seamless, scalable, and secure networking solutions in the cloud.
Introduction
Azure Networking Services is a comprehensive suite of cloud-based networking solutions offered by Microsoft Azure, designed to enhance the performance, security, and scalability of applications and services in the cloud. This suite includes a wide range of features, enabling organizations to build robust, interconnected networks and seamlessly connect their on-premises infrastructure to the Azure cloud environment.
Key components of Azure Networking Services include Azure Virtual Network, which allows users to create private, isolated networks in the cloud; Azure Load Balancer, facilitating efficient distribution of incoming network traffic; Azure VPN Gateway, providing secure connectivity to Azure virtual networks from on-premises locations; Azure Application Gateway, offering application-level load balancing and protection; Azure ExpressRoute, enabling private, high-bandwidth connections between Azure data centers and on-premises infrastructure, and more.
With Networking in Azure Services, businesses can achieve optimal network performance, ensure data privacy, and build flexible, hybrid cloud environments to meet their unique requirements.
What Is Azure Virtual Network?

Azure Virtual Network is a cloud-based networking service offered by Microsoft Azure. It enables users to create and manage private, isolated networks within the Azure cloud environment. With Azure Virtual Network, organizations can securely connect and control their Azure resources, such as virtual machines, databases, and applications.
Users can define custom IP address ranges, set up subnets, and establish network security groups to control inbound and outbound traffic. This allows for the segregation of resources and enhances security by implementing access control lists.
Azure Virtual Network enables connectivity between on-premises networks and Azure resources using Virtual Private Network (VPN) or Azure ExpressRoute, facilitating hybrid cloud scenarios. This makes it easier for businesses to extend their on-premises data centers to the cloud and build a seamless and secure hybrid infrastructure.
Advantages of Using Azure Virtual Network
Azure Virtual Network offers several advantages:
- Isolate and control access to resources in a private network environment, safeguarding sensitive data.
- Seamlessly extend on-premises networks to the cloud, enabling hybrid setups with secure communication.
- Easily scale network resources to meet changing demands and accommodate growing workloads.
- Built-in load balancing and traffic management ensure efficient and high-performing applications.
- Azure services can be seamlessly integrated, simplifying application deployment and management.
- Efficiently monitor and manage the network through Azure Portal for streamlined administration.
- VPN and ExpressRoute options enable secure connections between Azure and on-premises networks.
- Redundancy features provide continuous availability and reliability for critical applications.
- Pay-as-you-go pricing allows cost optimization based on actual network usage.
Elements of Azure Virtual Network
Subnets
In Azure Virtual Network, A Subnet is a logical division of the IP address space within the virtual network. It allows for better organization and management of resources by grouping them together based on their functionality or security requirements. By utilizing these subnet types, Azure Virtual Network enables administrators to design and implement secure, scalable, and efficient network architectures for their applications and services.
Private
A Private Subnet is not directly accessible from the internet and provides an additional layer of security. Resources within a private subnet can communicate with each other and other resources in the same virtual network but require Network Address Translation (NAT) or a gateway to access the internet or communicate with external networks. Private subnets are suitable for backend databases or internal services that should not be exposed to the public.
Public
A Public Subnet is associated with a public IP address and allows resources within it to have direct access to the internet. This type of subnet is commonly used for resources that need to be publicly accessible, such as web servers or application gateways.
Routing
Routing in Azure Virtual Network refers to the process of directing network traffic between different subnets and resources within the virtual network. It involves determining the best path for data packets to travel from the source to the destination in networking in Azure. Azure Virtual Network uses route tables to manage routing, allowing users to define custom routes and control traffic flow. Routing plays a vital role in establishing communication between virtual machines, gateways, and on-premises networks, ensuring efficient data transmission and connectivity within the Azure cloud environment.
Network Security Groups
Network Security Groups (NSGs) in Azure Virtual Network are essential elements for managing and controlling inbound and outbound network traffic. They act as virtual firewalls, allowing users to define rules that permit or deny communication between resources within the virtual network and with external networks. NSGs can be associated with subnets or individual network interfaces of networking in Azure, providing granular control over network traffic. By configuring NSGs, users can enhance the security posture of their Azure resources, protecting them from unauthorized access and potential threats, and ensuring a secure and reliable network environment in the Azure cloud.
How to Launch an Instance Using Azure VNet?
To launch an instance on Azure using VNet for networking in Azure, follow these simple steps:
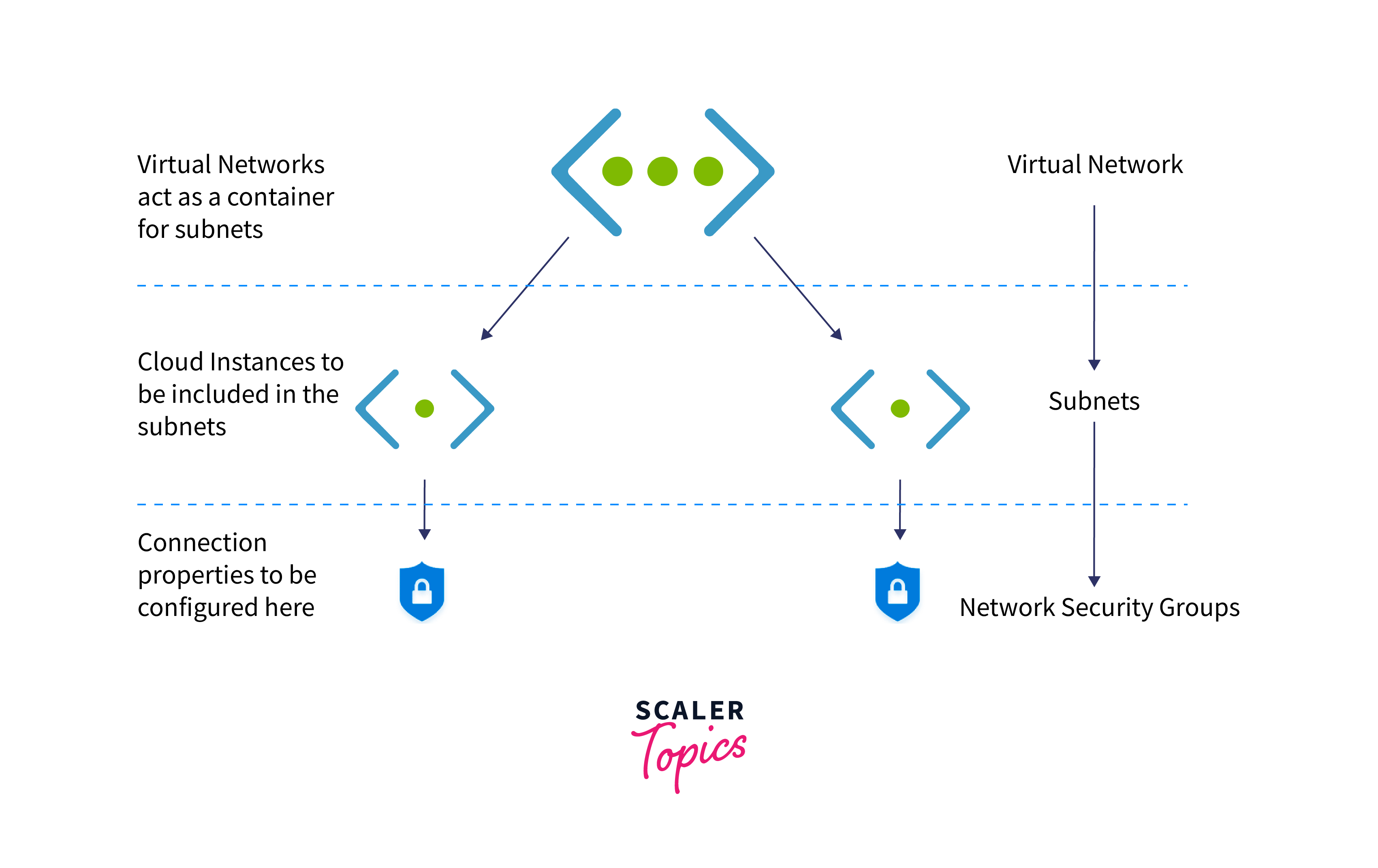
- Create Virtual Network: Begin by setting up a virtual network in Azure, defining its address space to create a private, isolated environment.
- Create Subnets: Within the virtual network, create subnets that act as segmented zones to organize and manage resources efficiently.
- Assign Subnets to Instances: Associate each instance or Virtual Machine with the appropriate subnet, ensuring they reside in the right network segment.
- Connect to Network Security Group (NSG): Secure the instances by linking them to a relevant Network Security Group, controlling inbound and outbound traffic.
- Configure NSG Properties: Fine-tune the network security settings and policies within the NSG to meet specific security requirements.
- Launch The Instance: Once the setup is complete, you can easily launch your instance on Azure, benefitting from a secure, well-structured virtual network.
A Step-By-Step Procedure of Creating Azure Virtual Machine and Virtual Network
Here's a step-by-step procedure to create an Azure Virtual Machine (VM) and Virtual Network (VNet):
Step 1: Sign in to Azure Portal
- Log in to the Azure portal using your Azure account credentials.
Step 2: Create a Virtual Network
- In the Azure portal, navigate to "Create a resource" and search for "Virtual network."
- Click on "Virtual network" and provide the necessary details like Name, Address space, and Subnet details.
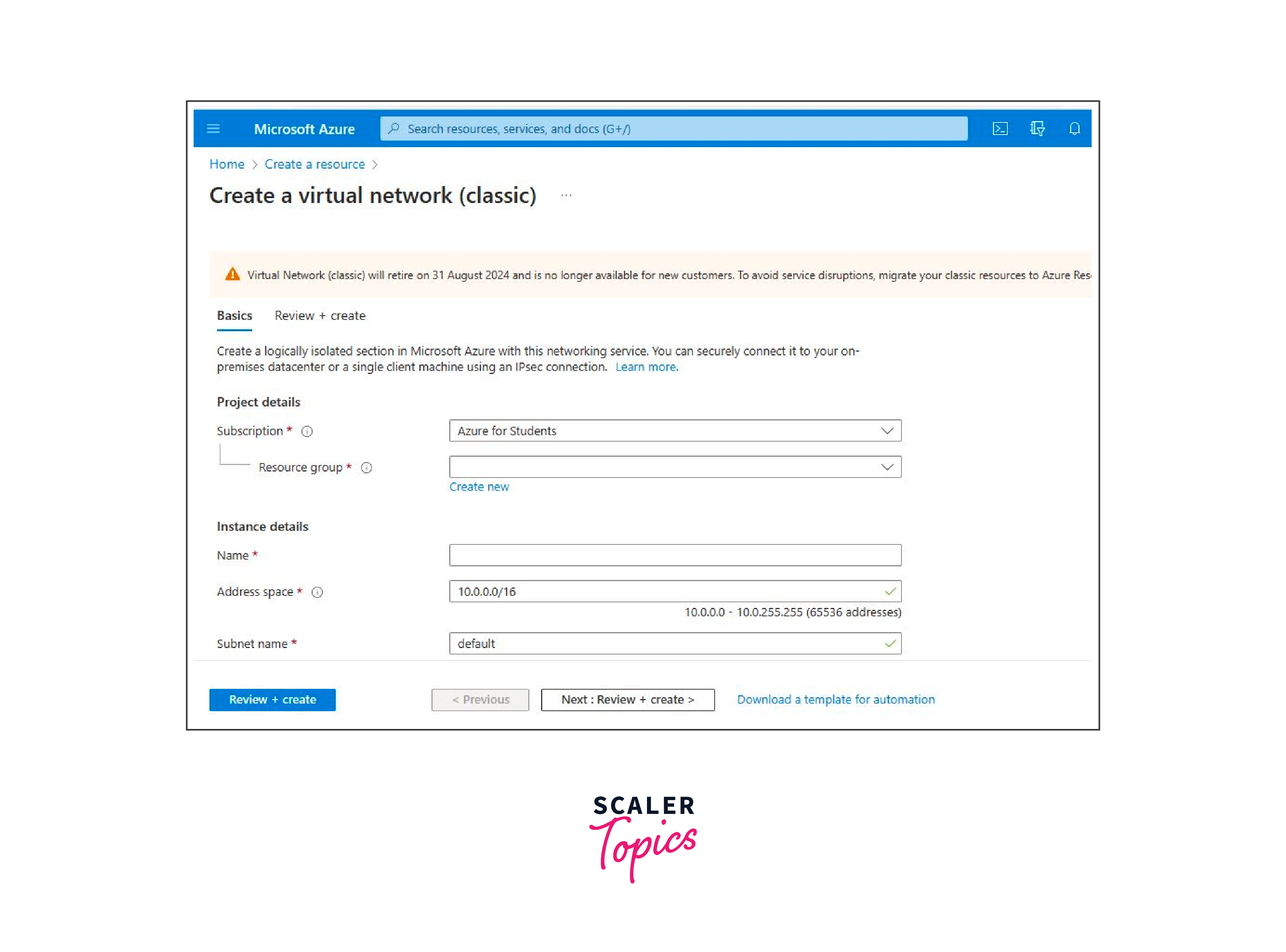
- Click "Create" to create the virtual network.
Step 3: Create a Subnet
- In the newly created virtual network, navigate to "Subnets" and click on "Add subnet."
- Provide a Name and Address range for the subnet.
- Click "OK" to create the subnet.
Step 4: Create a Virtual Machine
- In the Azure portal, navigate to "Create a resource" and search for "Virtual machine."
- Click on "Virtual machine" and provide the necessary details like Name, Region, Availability options, Image, and Size.
- Under "Configure Network," select the previously created virtual network and subnet.
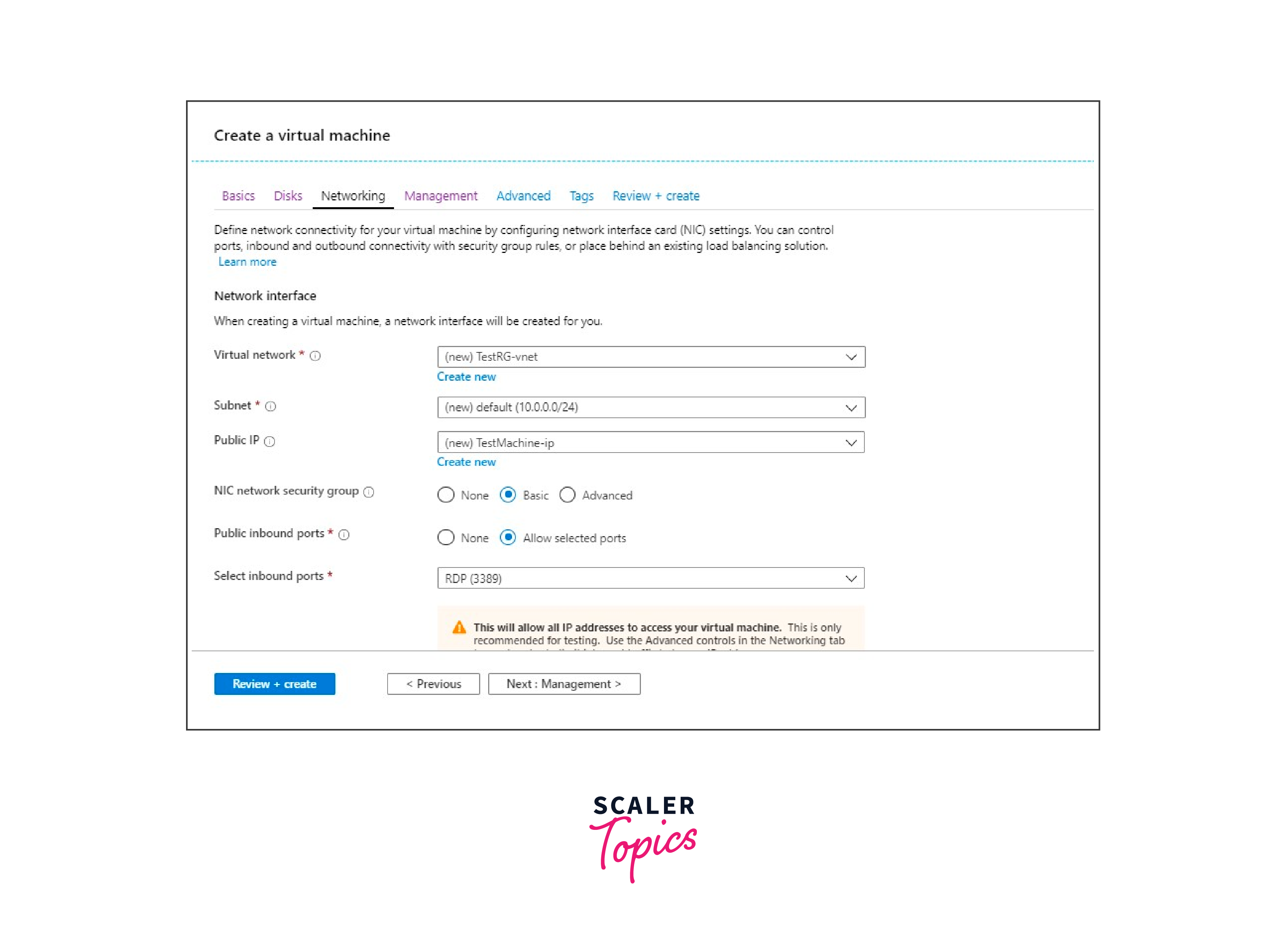
- Provide necessary authentication (username/password or SSH key) and other configurations.
- Click "Review + Create" to review the settings.
- Click "Create" to start provisioning the virtual machine.
Step 5: Connect to The Virtual Machine
- Once the virtual machine is created, navigate to the virtual machine's overview page in the Azure portal.
- Click on "Connect" to download the RDP (Remote Desktop Protocol) file for Windows VMs or The SSH command for Linux VMs.
- Use the downloaded RDP file or SSH command to connect to the virtual machine.
IP Addressing
What is an IP Address?
An IP (Internet Protocol) address is a unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It serves as an identifier and locator for devices on the network. IP addresses are essential for data routing, enabling devices to send and receive data across the internet.
There are two main versions of IP addresses:
- IPv4: This version uses a 32-bit format and is the most commonly used. IPv4 addresses are expressed in four groups of numbers separated by periods (e.g., 192.168.0.1). The total number of IPv4 addresses is limited, leading to the exhaustion of available addresses.
- IPv6: To address the scarcity of IPv4 addresses, IPv6 was introduced. It uses a 128-bit format and is expressed in eight groups of hexadecimal digits separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334). IPv6 provides a vast number of addresses, ensuring the future growth of the internet.
Private IP
A Private IP is an IP address assigned to devices within a private network, such as a local area network (LAN), that is not directly accessible from the internet. It allows devices to communicate internally while remaining hidden from external networks, enhancing security. Private IP addresses are reserved for internal use and are not routable on the internet. The most commonly used ranges for private IPs are:
- 10.0.0.0 to 10.255.255.255
- 172.16.0.0 to 172.31.255.255
- 192.168.0.0 to 192.168.255.255
These ranges provide a large pool of addresses for private networks, supporting various devices and subnets within an organization.
Public IP
A Public IP is an IP address assigned to a device or server that is directly accessible from the internet, allowing it to send and receive data across the global network. Public IPs enable communication with other internet-connected devices and services. They are unique and globally routable addresses. The range of public IP addresses is vast, as they are allocated by Internet Assigned Numbers Authority (IANA) to various Internet Service Providers (ISPs) and organizations worldwide. Public IP ranges are divided into different classes, including IPv4 and IPv6, which provide an enormous pool of addresses to accommodate the growing number of internet-connected devices and services.
What is IP Subnetting?
- IP subnetting is the process of dividing a large IP network into smaller, more manageable subnetworks called subnets.
- It involves using the subnet mask to create distinct ranges of IP addresses within the original network.
- Subnetting allows efficient utilization of IP addresses, reduces network congestion, and enhances security by segregating devices into separate logical groups.
- Devices within the same subnet can communicate directly, while communication between different subnets requires routers.
- Subnetting is a fundamental concept in IP networking and is essential for optimizing network performance, implementing security measures, and organizing IP address allocation in both local area networks (LANs) and wide area networks (WANs).
CIDR (Classless Inter Domain Routing)
- CIDR (Classless Inter-Domain Routing) is a method of IP addressing and routing that provides a more flexible and efficient allocation of IP addresses compared to the traditional classful addressing scheme.
- With CIDR, IP addresses are represented in the form of "prefix/length," where the prefix indicates the network address and the length specifies the number of bits in the subnet mask.
- This allows for variable-length subnet masks (VLSM) and finer granularity in dividing IP address space, enabling organizations to allocate addresses more precisely to match their network requirements.
- CIDR has become the standard for IP addressing and has played a crucial role in conserving IPv4 address space and facilitating the transition to IPv6.
- For Example, "192.168.1.0/24" represents a network address of "192.168.1.0" with a subnet mask of "255.255.255.0" (24 bits).
IP Address in Azure
In Networking in Azure, an IP address is a unique numerical label assigned to each resource, such as virtual machines, load balancers, and network interfaces, within the Azure cloud environment. There are two types of IP addresses in Azure:
- Public IP: Public IP addresses are used for resources accessible from the internet, enabling communication with external networks.
- Private IP: Private IP addresses are used for internal communication within an Azure Virtual Network, allowing secure interaction between resources.
IP addresses play a critical role in establishing connectivity and facilitating data exchange between Azure resources, enabling seamless access and communication within the cloud infrastructure.
IP Allocation
In Azure, "IP Allocation" refers to the process of assigning IP addresses to resources such as Virtual Machines, Load Balancers, and App Services within a virtual network. Azure provides two types of IP allocation:
- Dynamic IP Allocation: Resources receive an IP address automatically from the available pool when they are created or started. The IP address may change when the resource is restarted.
- Static IP Allocation: Resources are assigned a fixed, unchanging IP address, which remains the same even if the resource is restarted. Static IP allocation is useful for scenarios that require a consistent IP address, such as domain controllers or public-facing services.
Azure Virtual Network
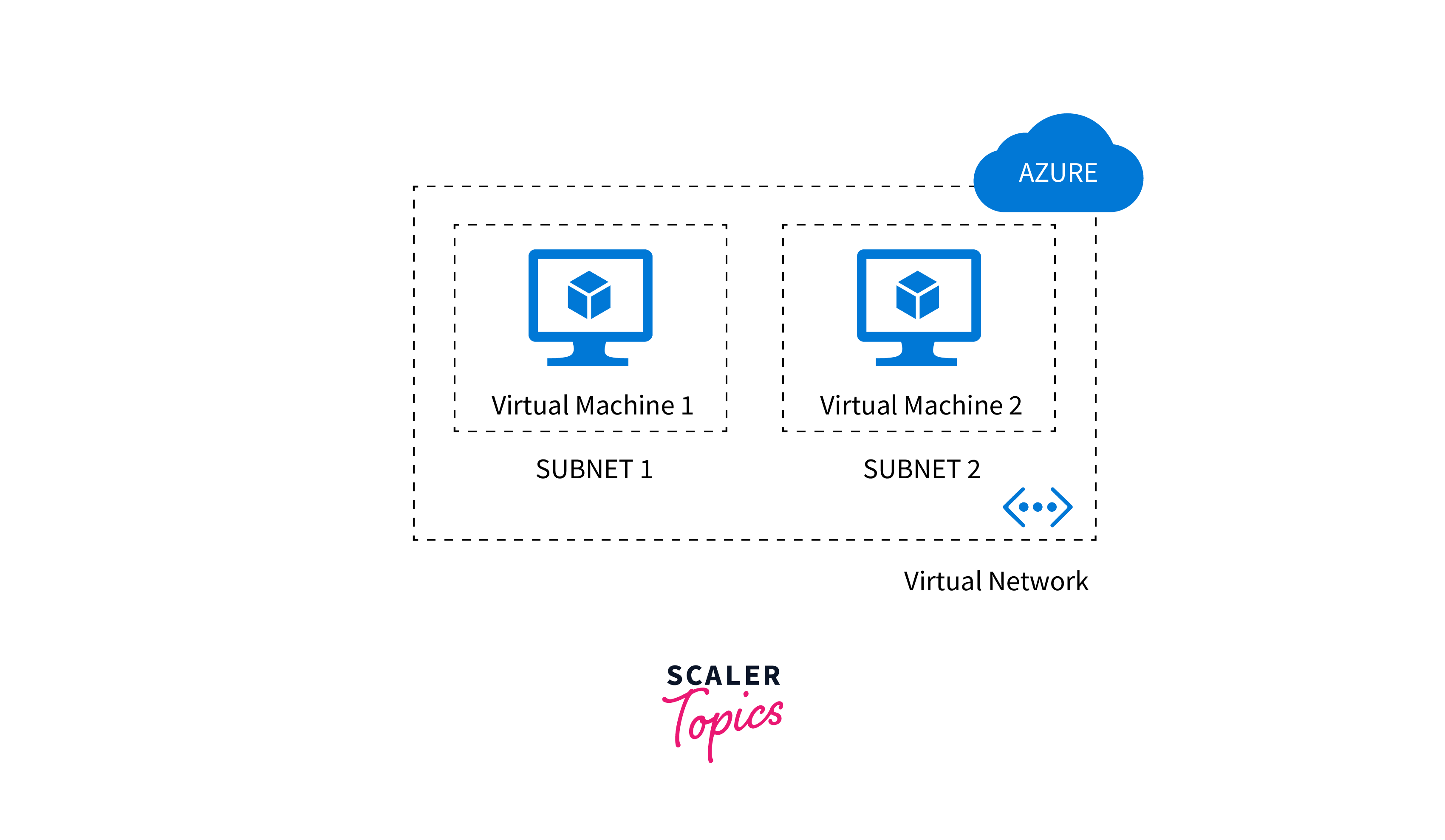
Azure Subnet
- Azure Subnet is a segmented section within an Azure Virtual Network.
- It helps organize and manage resources efficiently.
- Subnets enable secure communication between resources in the same virtual network.
- Each subnet can have its own Network Security Group (NSG) for traffic control.
- Resources within a subnet share the same IP address space defined by the virtual network.
- Subnets can be associated with Azure Virtual Machines and other services for proper network isolation.
- Azure Virtual Network allows administrators to create and manage multiple subnets to optimize network traffic and enhance security.
Azure Network Interface
- An Azure Network Interface (NIC) is a virtual network card that connects virtual machines (VMs) and other Azure resources to a Virtual Network.
- It provides connectivity, security, and network configuration to the VMs.
- NICs enable communication between VMs in the same virtual network and to external networks.
- Each NIC is associated with an IP address, MAC address, and Network Security Group (NSG) for traffic control.
- NICs can have public IP addresses for internet access or private IP addresses for internal communication.
- Azure Network Interface allows for flexible network configurations and seamless integration with Azure Virtual Machines and other services.
Network Security
Network Security Group (NSG)
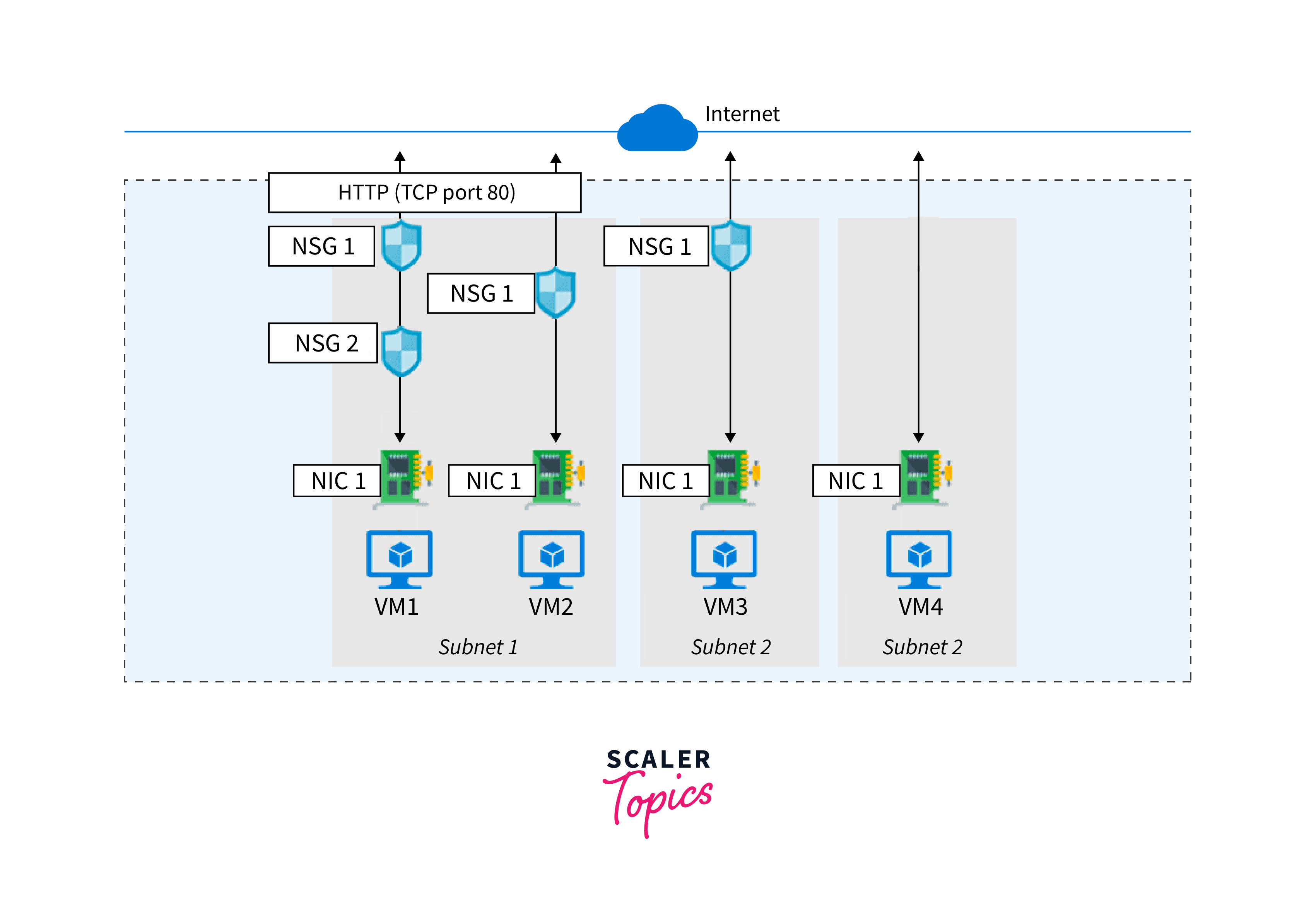
Network Security Group (NSG) in Azure is a cloud-based security feature that acts as a virtual firewall, providing granular control over inbound and outbound network traffic for Azure resources. It allows administrators to define rules that permit or deny specific traffic based on various criteria such as source IP, destination IP, protocol, and port.
Key points about NSG in Azure:
- Traffic Filtering: NSGs allow you to filter network traffic at the subnet or network interface level, providing a secure network perimeter for Azure resources.
- Rules Prioritization: Rules within an NSG are processed in a priority order, and the first matching rule determines whether traffic is allowed or denied.
- Default Rules: NSGs have default "Allow" and "Deny" rules for inbound and outbound traffic, which can be customized to align with specific security requirements.
- Inbound and Outbound Control: NSGs can control both incoming and outgoing traffic, helping prevent unauthorized access and data exfiltration.
- Port-Level Security: By defining rules for specific ports, NSGs ensure that only authorized communication is permitted on designated ports.
- Application Security: NSGs support filtering traffic based on application-specific requirements, enhancing application-level security.
- Associations: NSGs can be associated with Azure Virtual Machines, subnets, and network interfaces, allowing for flexible application of security policies.
- Logging and Monitoring: NSGs provide logging and monitoring capabilities, enabling administrators to track network traffic and security events.
- Secure Multi Tier Architectures: NSGs facilitate the creation of secure multi-tier architectures by controlling traffic flow between different application layers.
Service Endpoints
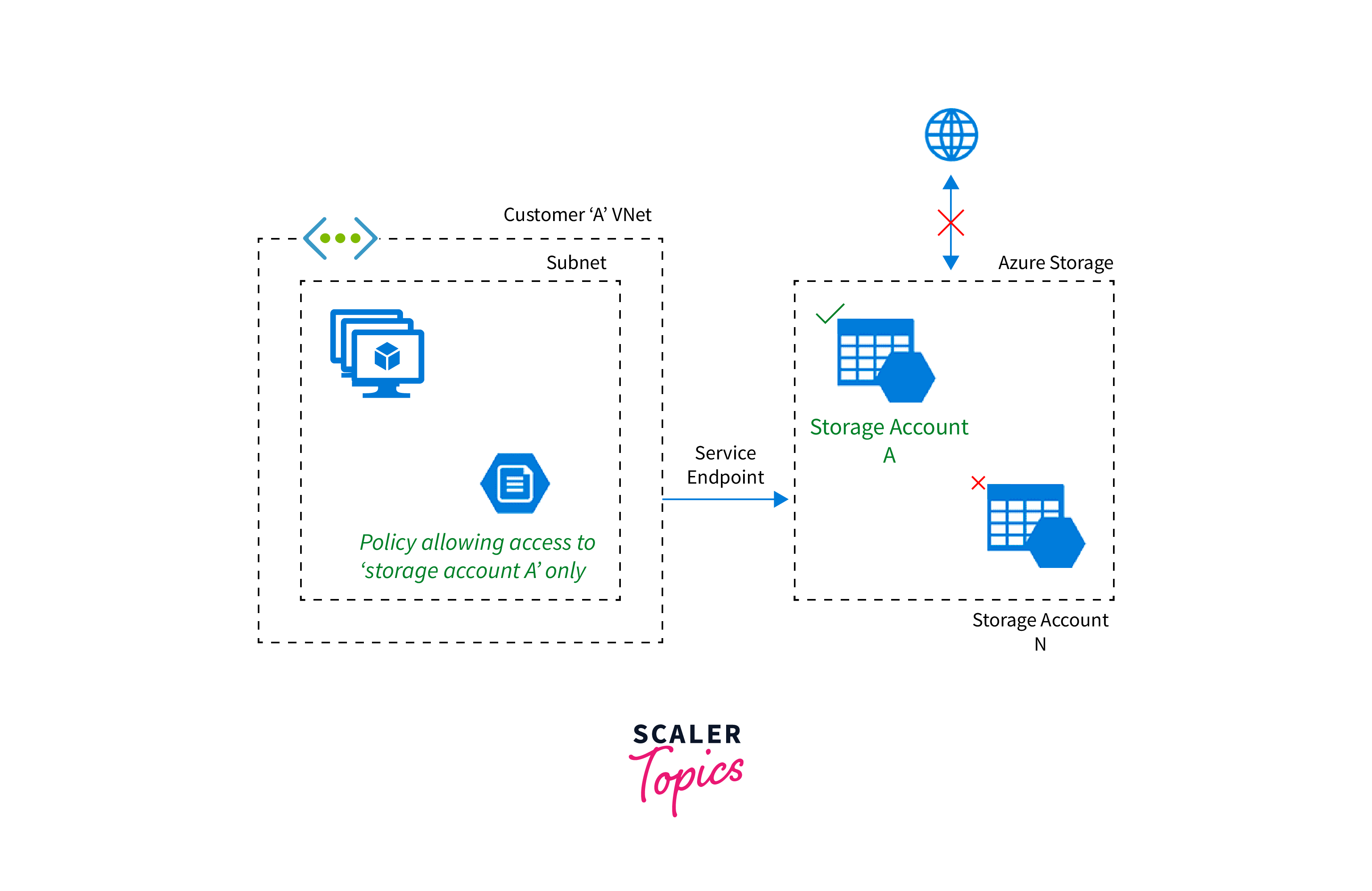
- Azure Service Endpoints allow secure access to Azure services from a Virtual Network.
- They create a direct connection between the VNet and the service without exposure to the public internet.
- Service Endpoints enhance security by reducing the attack surface and preventing data exfiltration.
- Traffic between the VNet and the service stays within the Azure backbone network, improving performance and reliability.
- Service Endpoints are available for various Azure services like Azure Storage, Azure SQL Database, and Azure Cosmos DB.
- By leveraging Service Endpoints, organizations can enhance the security and performance of their Azure services while maintaining network isolation.
Web Application Firewall (WAF)
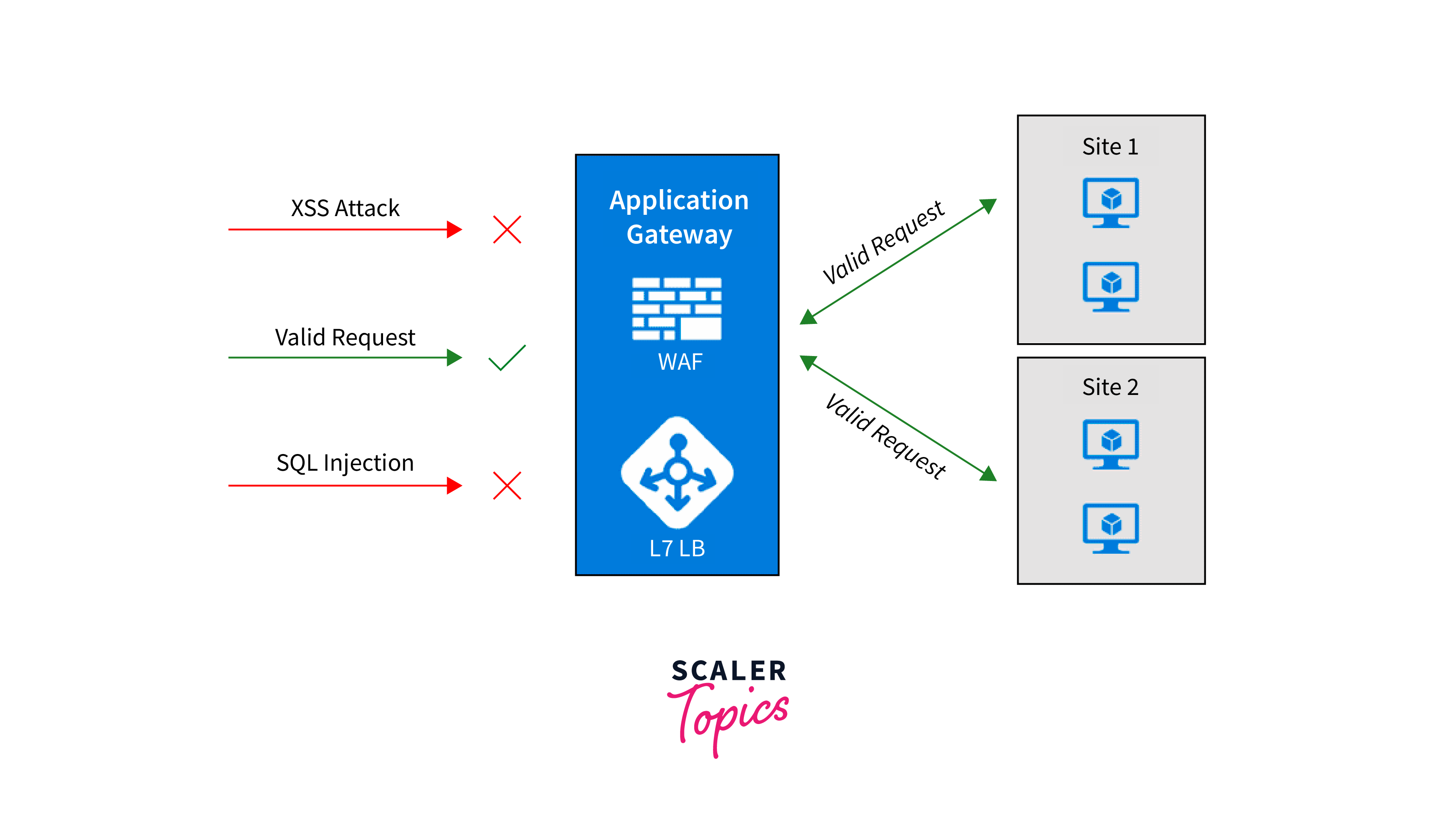
Azure Web Application Firewall (WAF) is a security feature that helps protect web applications from common web-based attacks. It acts as a reverse proxy, sitting between the client and the web application, inspecting incoming HTTP/HTTPS traffic, and filtering out malicious content and potential vulnerabilities.
Key points about Azure WAF:
- Protection Against OWASP Top 10: Azure WAF safeguards web applications against the OWASP Top 10 threats, including SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Customizable Rule Sets: WAF allows the use of custom rule sets, enabling tailored protection for specific application requirements.
- Real Time Monitoring and Reporting: WAF provides real-time monitoring and detailed reporting on web application traffic, security events, and attack attempts.
- Easy Integration: Azure WAF seamlessly integrates with Azure Application Gateway, Azure Front Door, and Azure Content Delivery Network (CDN), offering comprehensive security solutions.
- Automatic Rule Updates: Microsoft regularly updates WAF rule sets to protect against emerging threats, ensuring up-to-date security for web applications.
- Flexible Policy Enforcement: Administrators can configure WAF policies to allow, block, or log web traffic based on specified criteria.
- IP Whitelisting/Blacklisting: WAF allows the definition of IP whitelists and blacklists to control access to web applications.
- Centralized Management: WAF can be managed centrally through Azure Security Center, providing a unified view of security policies and events across multiple applications.
- Geo Filtering: Azure WAF supports filtering traffic based on geographic locations, restricting access to web applications from specific regions.
Azure Network Models
VNet Peering
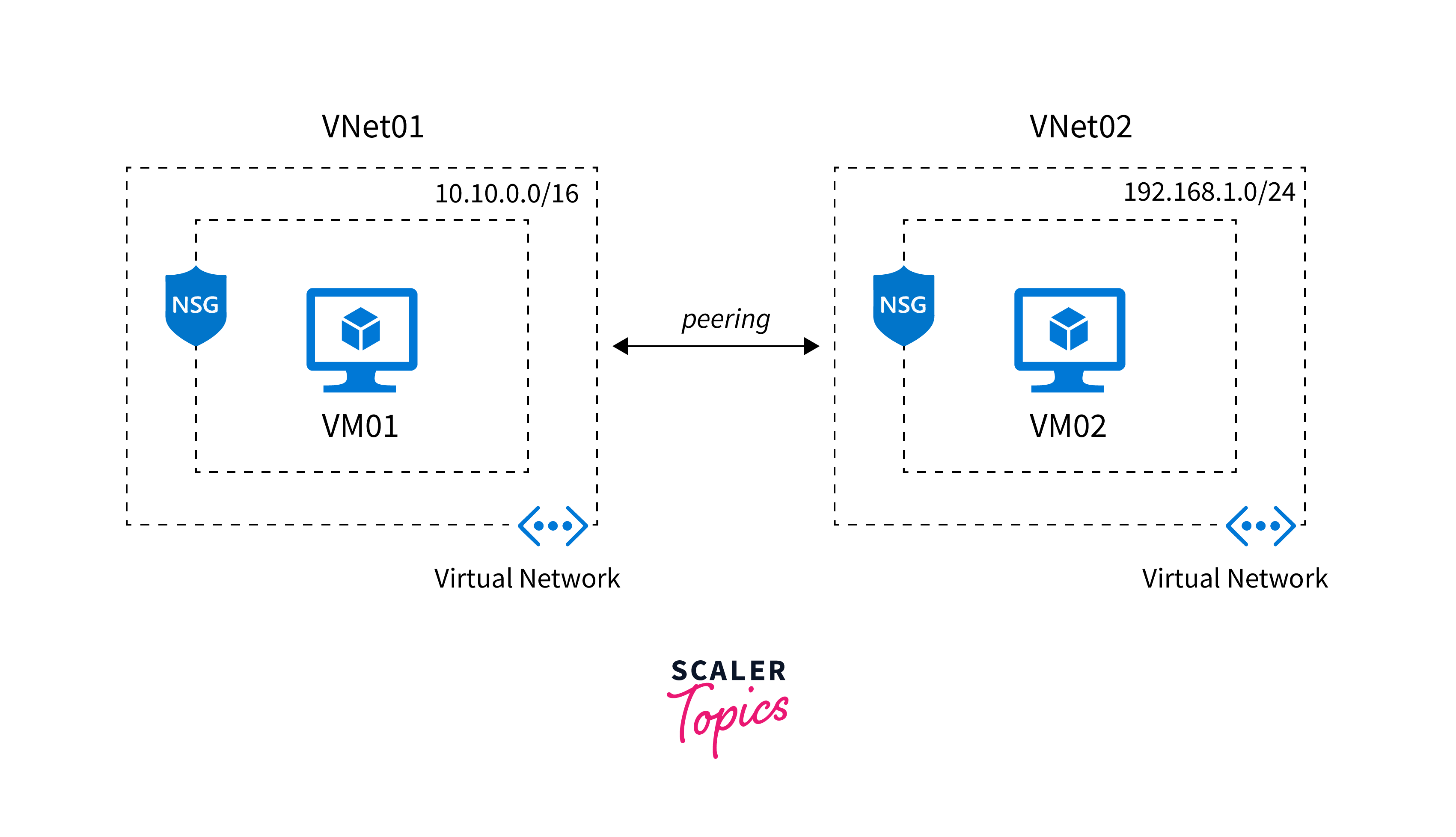
VNet Peering in Azure is a networking feature that allows secure communication between virtual networks (VNets) within the same region or across different regions. It enables resources in peered VNets to communicate as if they were part of the same network, without traversing the public internet.
There are two types of VNet Peering:
Regional VNet Peering
This type of peering connects VNets within the same Azure region. It is commonly used for interconnecting resources and services within an organization's Azure environment.
Global VNet Peering
Global peering enables VNets in different Azure regions to communicate with each other. It allows organizations to create geographically distributed architectures, facilitating cross-region data replication and disaster recovery scenarios.
Both types of VNet Peering provide low-latency, high-bandwidth connectivity, promoting resource sharing, centralized management, and application integration across Azure environments. It's essential to consider network architecture and security requirements while implementing VNet Peering to ensure optimal and secure communication between resources.
Virtual WAN (Wide Area Network)
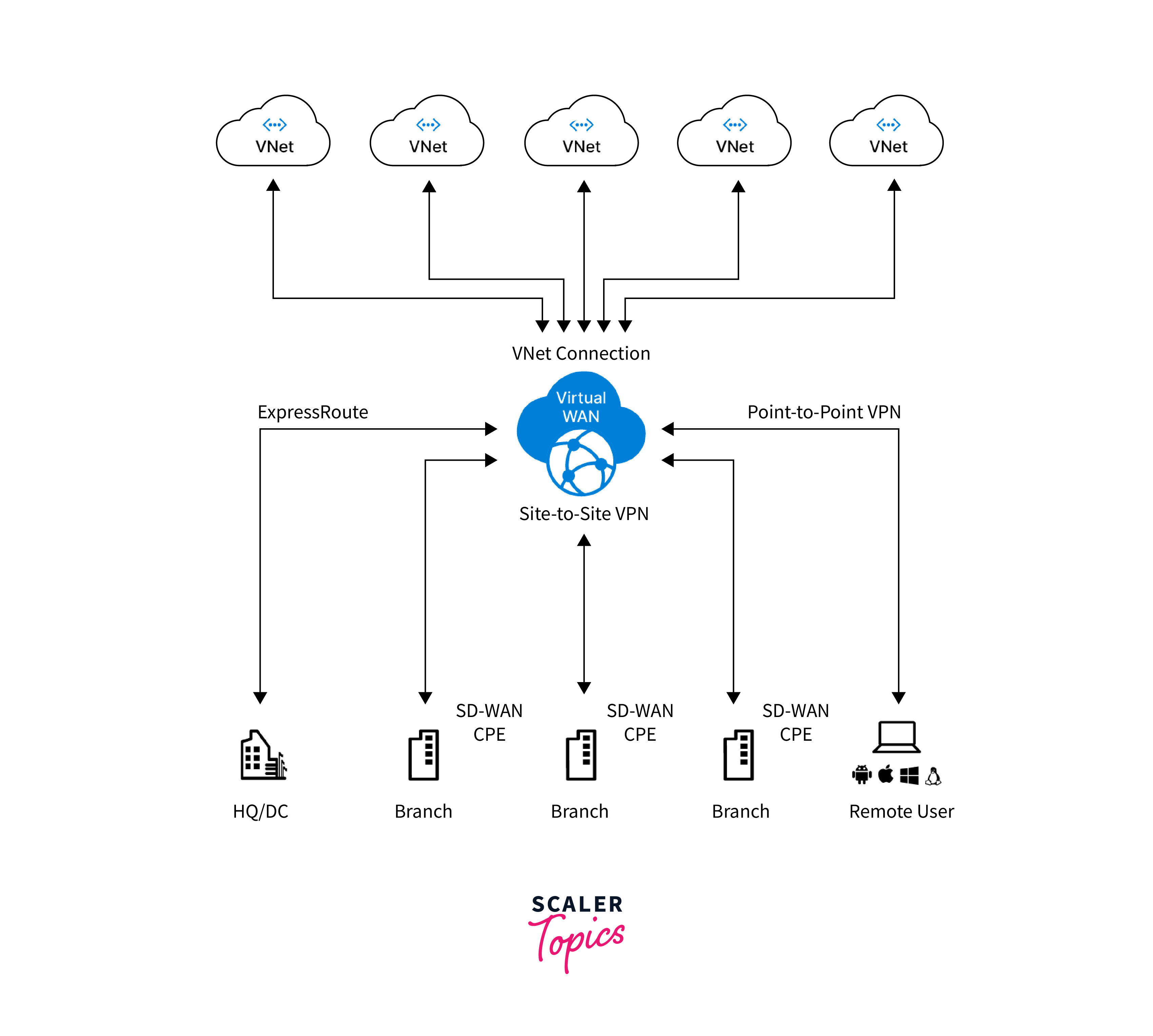
Virtual WAN (Wide Area Network) in Azure is a networking service designed to simplify and optimize connectivity for organizations with multiple branch offices and remote locations. It provides a hub-and-spoke architecture, allowing businesses to centralize network management and efficiently connect their branch locations to Azure resources.
Virtual WAN offers several key features, including automated route optimization, traffic segmentation, and secure communication through VPN and ExpressRoute connections. It leverages Microsoft's global network infrastructure to provide low-latency and high-performance connections between branch offices and Azure services.
By utilizing Virtual WAN, Organizations can improve network performance, reduce administrative overhead, and enhance security for their wide-area networking needs. Virtual WAN also provides seamless integration with other Azure services, allowing businesses to create a scalable and agile network environment tailored to their unique requirements.
More Azure Virtual Network Information
Pricing
Azure Virtual Network pricing is based on various factors like the number of Virtual Network Peering connections, data transfer (inbound and outbound), and the number of VPN and ExpressRoute gateways. There might be charges for Public IP addresses and Network Security Groups (NSGs). To know more about the pricing details you can visit Azure Virtual Network Pricing.
Protecting Resources
Protecting Resources in Azure Virtual Network (VNet) involves implementing security measures to ensure the confidentiality, integrity, and availability of data and applications within the VNet. This includes using Network Security Groups (NSGs) to control inbound and outbound traffic, deploying Azure Firewall or Network Virtual Appliances for advanced network security, and enabling Azure DDoS Protection for safeguarding against Distributed Denial of Service attacks. Additionally, implementing Virtual Private Network (VPN) or Azure ExpressRoute connections enhances network security and privacy. Regularly updating and patching virtual machines, applying identity and access management controls, and monitoring network activity are essential practices for protecting resources in Azure.
FAQs
Q. Can I modify Vnet after I created them?
A. Yes, you can modify Azure Virtual Networks (VNets) after creating them. You can change VNet address ranges, add or remove subnets, modify Network Security Groups (NSGs) rules, and update peering connections. However, some changes may require resources to be redeployed, causing temporary disruptions.
Q. Can I perform WAN optimization between VNets or a VNet and my on-premises data center? A. Yes, you can perform WAN optimization between VNets or a VNet and your on-premises data center in Azure. By utilizing Virtual WAN and Azure Virtual WAN Optimization partners, you can improve network performance, reduce latency, and enhance the efficiency of data transfer over the wide area network.
Q. What tools do I exploit to make a VNet? A. To create and manage an Azure Virtual Network (VNet), you can use various tools provided by the Azure platform:
- Azure Portal
- Azure CLI (Command-Line Interface)
- Azure PowerShell
- Azure Resource Manager (ARM) Templates
- Azure Cloud Shell
Q. What address ranges Am I able to use in my VNets? A. For optimal and secure IP address allocation in Azure, adhering to specific address ranges is recommended. RFC 1918 designates address spaces reserved for private, non-routable use, ensuring internal network privacy:
- 10.0.0.0 – 10.255.255.255 (10/8 prefix)
- 172.16.0.0 – 172.31.255.255 (172.16/12 prefix)
- 192.168.0.0 – 192.168.255.255 (192.168/16 prefix)
Azure also supports the Shared Address space specified in RFC 6598, treated as Private IP Address space:
- 100.64.0.0 – 100.127.255.255 (100.64/10 prefix)
Using other IETF-recognized private, non-routable address spaces may have unintended consequences. Moreover, certain address ranges are restricted in Azure:
- 224.0.0.0/4 (Multicast)
- 255.255.255.255/32 (Broadcast)
- 127.0.0.0/8 (Loopback)
- 169.254.0.0/16 (Link-local)
- 168.63.129.16/32 (Internal DNS)
To maintain efficient IP address management and prevent network issues, follow these guidelines when defining IP address spaces for Azure resources. By doing so, you ensure a secure and well-organized network environment in your Azure deployments.
Conclusion
- Azure Virtual Network is a cloud-based networking service that allows you to create private, isolated networks in Azure, enabling secure communication between resources and on-premises networks.
- Advantages of using Azure Virtual Network include secure and isolated network environments, seamless integration with on-premises networks, flexible IP address management, and simplified network administration in the Azure cloud environment.
- Elements of Azure Virtual Network include Subnets, IP Addressing, Network Security Groups (NSGs), Routing, Virtual Network Peering, and VPN/ExpressRoute connectivity options for secure and efficient network communication.
- An IP address is a unique numerical label assigned to devices connected to a network, enabling them to identify and communicate with each other on the internet or a private network.
- CIDR (Classless Inter-Domain Routing) is an IP addressing scheme that allows more flexible allocation of IP addresses by using variable-length subnet masks, accommodating networks of different sizes.
- Azure Subnet is a segmented portion of an Azure Virtual Network, allowing users to organize and isolate resources. Azure Network Interface is a network adapter that connects virtual machines to VNets, facilitating network communication.
- Network Security in Azure refers to the implementation of measures like Network Security Groups (NSGs), Security Endpoints and Web Application Firewalls to protect Azure resources and data from unauthorized access and cyber threats.
- VNet Peering in Azure enables secure communication between Azure Virtual Networks (VNets) across regions or within the same region, as if they were part of the same network.
- Virtual WAN in Azure is a networking service that simplifies and optimizes connectivity for branch offices and remote users, providing secure, low-latency access to Azure resources.
