What is AWS Bastion Host?
Overview
A bastion host in AWS is a hardened, secure server used as a gateway for SSH or RDP access to private instances within a Virtual Private Cloud (VPC). It acts as a controlled entry point, enhancing network security by reducing direct access to sensitive resources and allowing administrators to manage instances more securely.
Bastion Host in AWS
A Bastion Host, also known as a Jump Host or Jump Server, is a special-purpose computer on a network that is designed and configured to provide a secure entry point into a private network, often to manage and access other machines within that network. It acts as a gateway that controls and monitors access to other systems within the network, adding a layer of security.
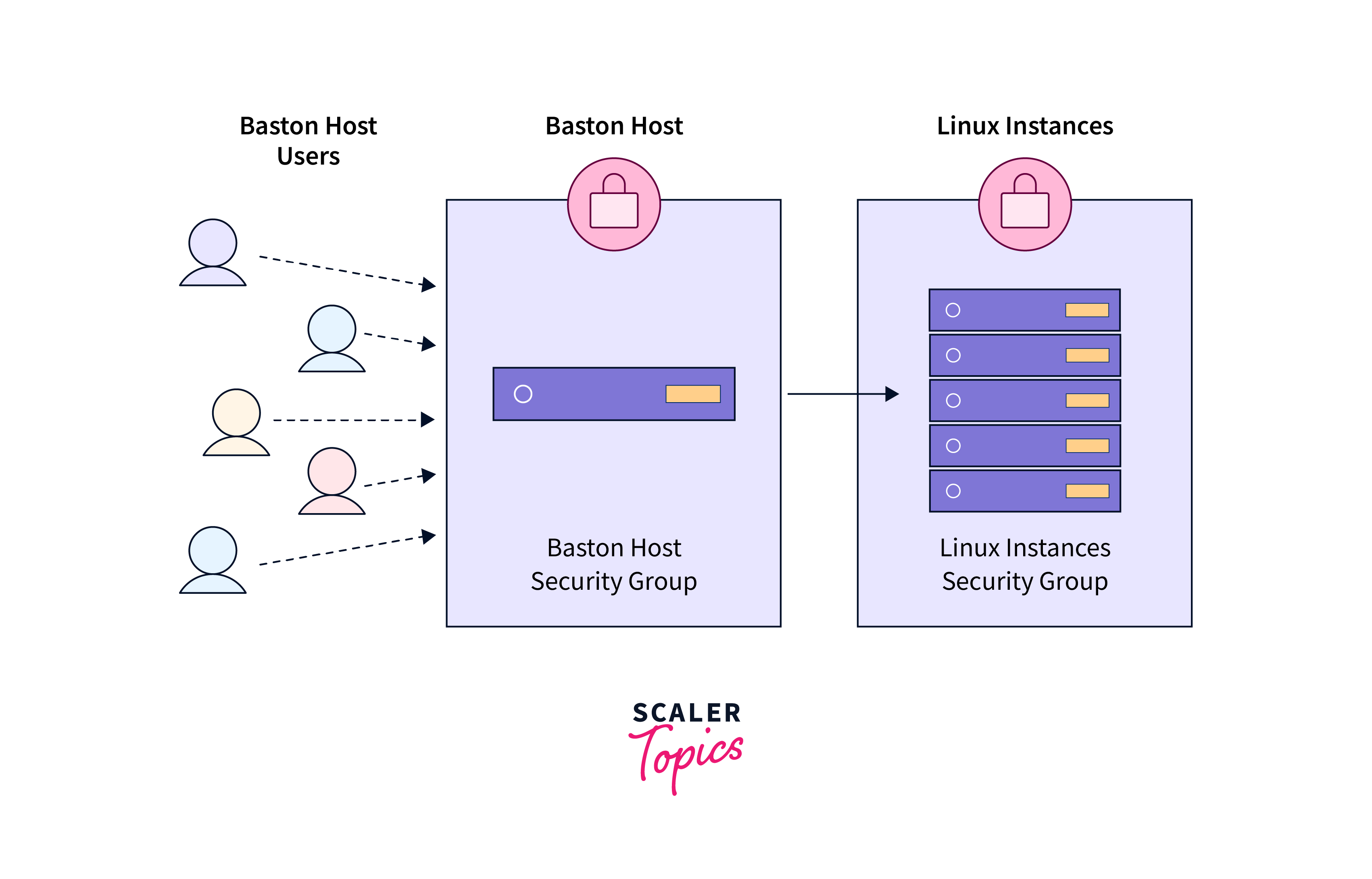
The primary purpose of a Bastion Host is to minimize the exposure of the internal network to potential security threats that might arise from direct external access. Instead of allowing direct access to sensitive systems, users connect to the Bastion Host first, and then, from there, they can initiate connections to other machines within the private network. This adds an extra layer of security and control, as the Bastion Host can be more rigorously monitored, maintained, and secured than every individual system within the internal network.
How Bastion Host Works?
Let's look into how a Bastion Host works:
Secure Entry Point:
The Bastion Host is deployed in the network perimeter and has a public IP address. It serves as the initial point of entry for users or administrators who need to access the internal network remotely.
Authentication and Authorization:
To access the internal network, users must authenticate themselves to the Bastion Host using strong credentials, such as usernames and passwords, SSH keys, or multi-factor authentication.
Secure Protocols:
The Bastion Host is configured to support secure communication protocols like SSH (Secure Shell) or RDP (Remote Desktop Protocol). These protocols encrypt the data transmitted between the user's device and the Bastion Host, ensuring data confidentiality.
Network Segmentation:
The internal network is often divided into segments or zones, each containing specific types of resources. The Bastion Host might have access to only certain segments, limiting the impact of a security breach.
Intermediate Access:
After successfully authenticating with the Bastion Host, users gain access to it. From there, they can use the Bastion Host as an intermediary to access other systems within the internal network.
Access Control Lists (ACLs):
Access control lists are configured to allow specific users or groups to connect to the Bastion Host. This adds an extra layer of control over who can access the internal network.
Logging and Monitoring:
All activities, commands executed, and connections made through the Bastion Host are logged and monitored. This creates an audit trail for security analysis and helps detect any suspicious behavior.
Firewall Rules:
The Bastion Host is typically equipped with firewall rules that control which internal resources users can connect to. These rules restrict unauthorized access and limit potential lateral movement within the internal network.
Hardened Security:
The Bastion Host is built and maintained with security best practices, including regular updates, patches, and configurations to minimize vulnerabilities.
Temporary Access:
Users usually have temporary access to the internal network through the Bastion Host. Once their tasks are complete, they disconnect from the Bastion Host, reducing the window of exposure.
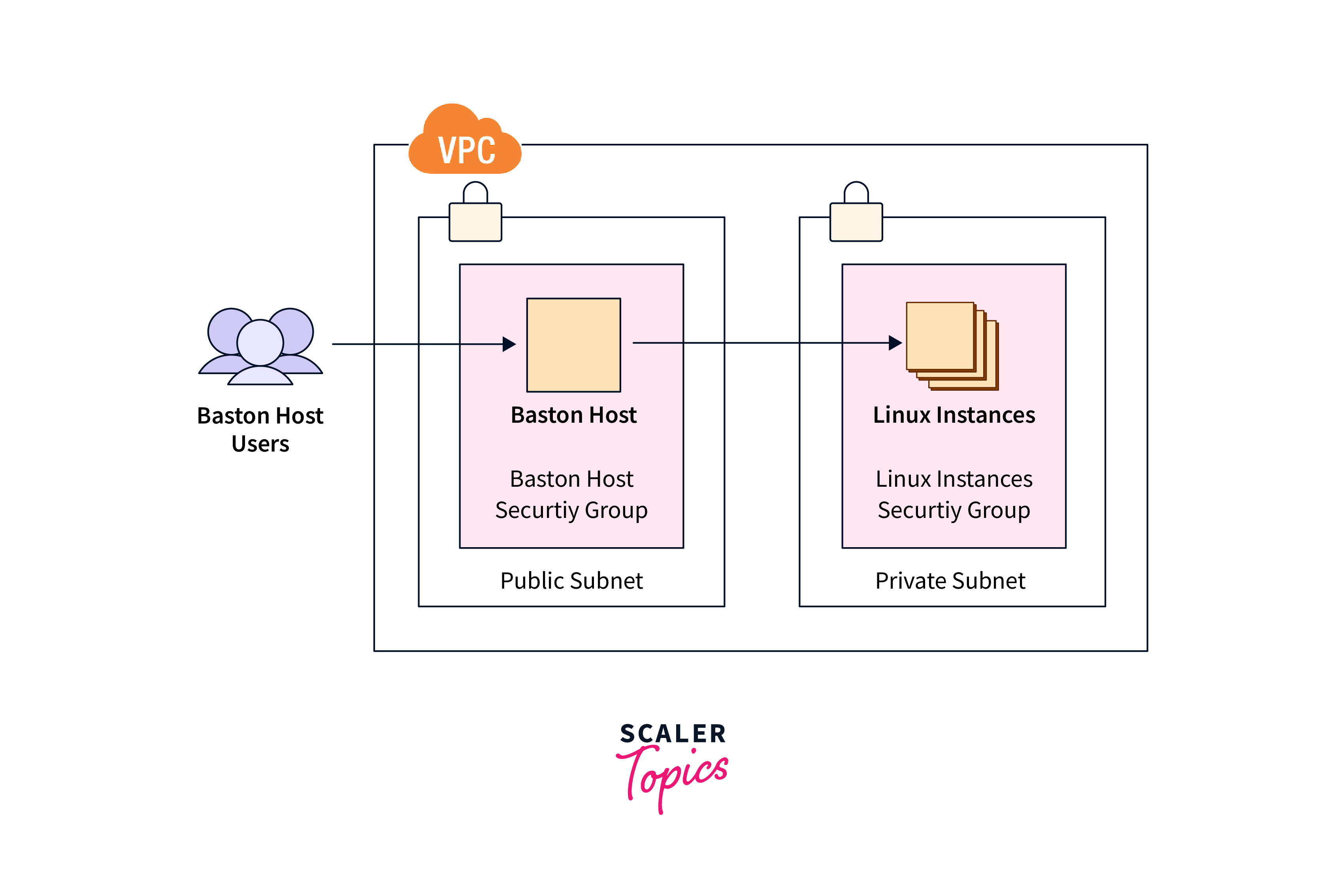
Bastion Host Best Practice
Deploying a Bastion Host involves several best practices to ensure its effectiveness in enhancing security and managing remote access. Here are some key Bastion Host best practices:
Isolation:
Place the Bastion Host in a separate subnet or network zone, isolated from the internal network and sensitive resources. This limits potential lateral movement if the Bastion Host is compromised.
Minimal Software:
Keep the Bastion Host's software and services minimal. Only install necessary applications, reducing the scope of attack and potential vulnerabilities.
Secure Configuration:
Configure the Bastion Host with secure settings, disabling unnecessary services and implementing strong authentication mechanisms.
Multi-Factor Authentication (MFA):
Enforce the use of multi-factor authentication for accessing the Bastion Host.
SSH Key-Based Authentication:
Use SSH key-based authentication instead of passwords for SSH access to the Bastion Host.
Access Control Lists (ACLs):
Implement strict access control lists to specify which IP addresses or ranges are allowed to connect to the Bastion Host.
Just-In-Time Access:
Implement just-in-time access controls, allowing users to connect to the Bastion Host only when needed and for a limited time.
Session Recording:
Enable session recording on the Bastion Host to keep a record of user activities. This aids in audits, compliance, and incident response.
Strong Password Policies:
If using password authentication, enforce strong password policies to prevent brute-force attacks.
Firewall Rules:
Use firewall rules on the Bastion Host to restrict outgoing connections and limit the types of traffic that can leave the Bastion subnet.
Logging and Monitoring:
Implement robust logging and monitoring mechanisms on the Bastion Host to detect and respond to any suspicious activities.
Conclusion
- A bastion host is a security-focused server used as an intermediary to control and secure access to internal network resources from external users or administrators.
- A bastion host works by serving as a single point of entry, controlling and monitoring access to internal systems, typically using strong authentication methods and strict access policies.
- Bastion Host Best Practices:
- Minimal Software: Keep the bastion host's software minimal to reduce attack surface.
- Access Control: Implement strong authentication methods and access controls.
- Isolation: Isolate the bastion host from the internal network.
- Logging and Monitoring: Log and monitor all access to the bastion host extensively.
- Regular Patching: Keep the bastion host updated with security patches.
- Multi-Factor Authentication (MFA): Enforce MFA for bastion host access.
- Firewall Rules: Implement strict firewall rules to allow only necessary traffic.
- Regular Auditing: Conduct regular security audits and assessments.
