Difference Between Block Cipher and Stream Cipher
Overview
Block ciphers and stream ciphers are cryptographic algorithms used to protect the confidentiality and integrity of data. They differ in their approach to encryption, with block ciphers processing data in fixed-size blocks and stream ciphers encrypting data bit by bit or byte by byte. In this blog post we will discuss about Block Cipher and Stream Cipher in details and will also find out exactly about block cipher vs stream cipher.
Prerequisite
To understand the concept of block cipher vs stream cipher, it's important to know what each of these encryption techniques is and the modes of operation associated with block ciphers.
What is a Block Cipher?
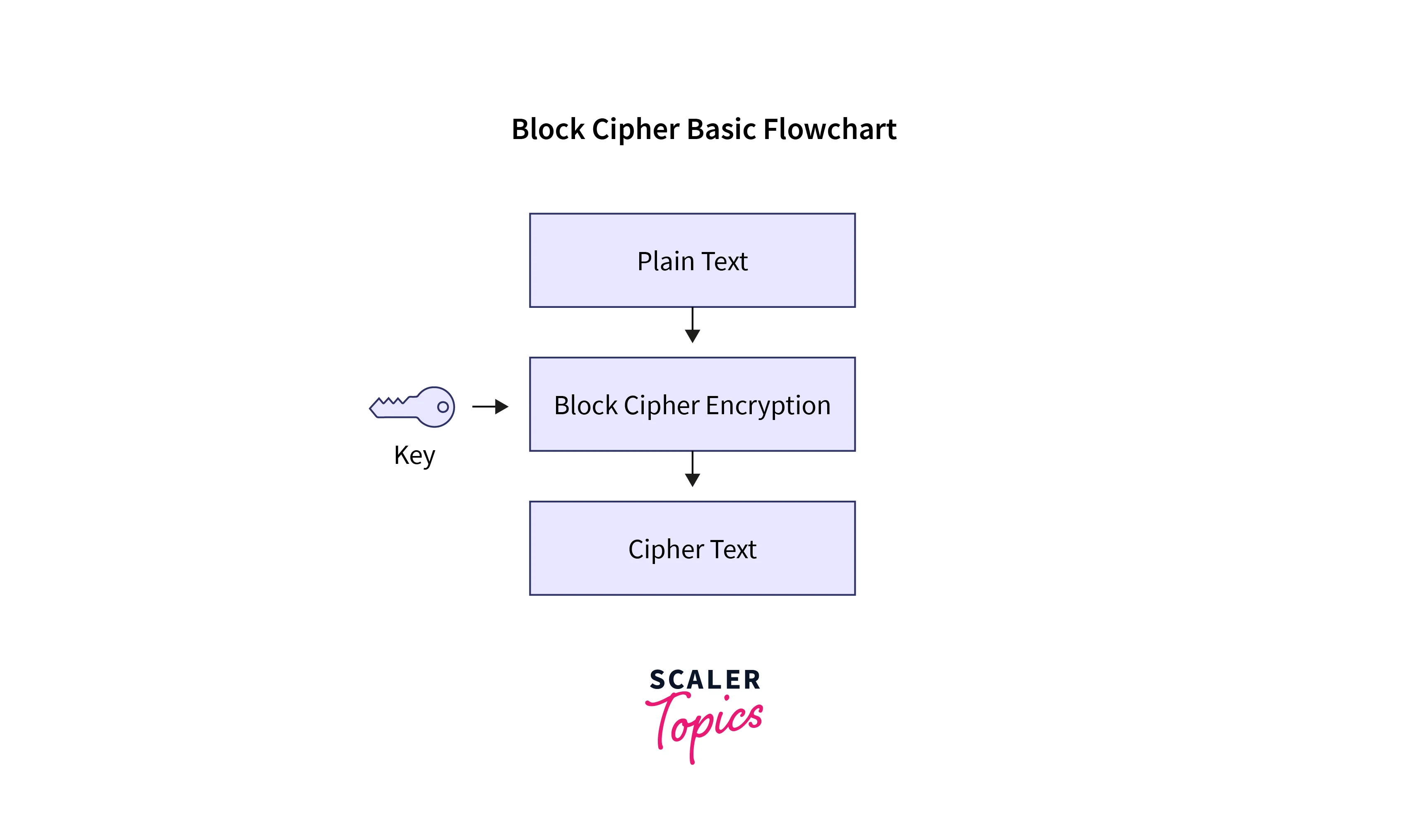
A block cipher is a symmetric-key cryptographic algorithm used to encrypt and decrypt fixed-size blocks of data. It is a fundamental component of modern cryptographic systems and is widely employed to secure data in various applications, including data storage, communication, and authentication.
Here are the key characteristics and components of a block cipher:
Symmetric-Key Cryptography: Block ciphers belong to the category of symmetric-key cryptography, where the same secret key is used for both encryption and decryption. This key must be kept confidential and shared securely between the parties involved.
Fixed Block Size: Block ciphers operate on fixed-size blocks of data. Common block sizes include 64 bits (as in DES), 128 bits (as in AES), or occasionally other sizes like 256 bits. The input plaintext is divided into these fixed-size blocks for encryption.
Substitution-Permutation Network (SPN): Block ciphers typically use a structure called a Substitution-Permutation Network, which involves a series of substitutions and permutations applied iteratively to the input data blocks. These operations are controlled by the encryption key.
Key Expansion: Block ciphers often employ a key expansion algorithm to generate a set of round keys from the original encryption key. These round keys are used in each round of the encryption and decryption processes.
Rounds: Block ciphers operate in multiple rounds, with each round consisting of a combination of substitution and permutation operations. The number of rounds depends on the specific block cipher algorithm and its key length.
Confidentiality: The primary purpose of a block cipher is to ensure the confidentiality of data. It does this by transforming plaintext blocks into ciphertext blocks using the encryption key. Decrypting the ciphertext with the same key should yield the original plaintext.
Security: The security of a block cipher relies on factors like the algorithm's mathematical properties, the key length, and the complexity of the encryption process. Block ciphers are designed to resist various cryptographic attacks, including brute-force attacks and differential cryptanalysis.
Modes of Operation: Block ciphers are typically used in conjunction with modes of operation to handle data that is larger than the block size. Modes like Electronic Code Book (ECB), Cipher Block Chaining (CBC), and others determine how multiple blocks are processed and combined to encrypt or decrypt larger datasets.
Modes of operation of a block cipher
-
Electronic Code Book (ECB) Mode: Electronic Code Book (ECB) Mode is a fundamental block cipher mode of operation in which each fixed-size block of plaintext is independently encrypted with the same key, resulting in identical plaintext blocks yielding identical ciphertext blocks. Due to this predictable behavior, it lacks security against certain attacks.
-
Cipher Block Chaining (CBC) Mode: Cipher Block Chaining (CBC) Mode is a block cipher mode in which each plaintext block is XORed with the previous ciphertext block prior to encryption, adding variability and making the cipher resistant to data patterns.
-
Cipher Feedback (CFB) Mode: It is a block cipher mode that transforms a block cipher into a stream cipher, where each ciphertext block becomes a stream of keys for encrypting the following plaintext block. It permits the encryption of individual data bits or bytes.
-
Output Feedback (OCB) Mode: Output Feedback (OFB) Mode is a mode of operation for block ciphers that converts a block cipher to a stream cipher. It generates a keystream independently of the plaintext or ciphertext and XORs the keystream with the data to produce ciphertext. This mode is typically employed for real-time data encryption and is robust against transmission errors.
-
Counter (CTR) Mode: Counter (CTR) Mode is a block cipher mode of operation used for encryption. In CTR mode, a counter value is encrypted using a block cipher to generate a keystream, which is then XORed with the plaintext to produce ciphertext. It is highly parallelizable and appropriate for both encryption and decryption of data streams, making it ideal for real-time applications and high-speed communication channels.
What is a Stream Cipher?
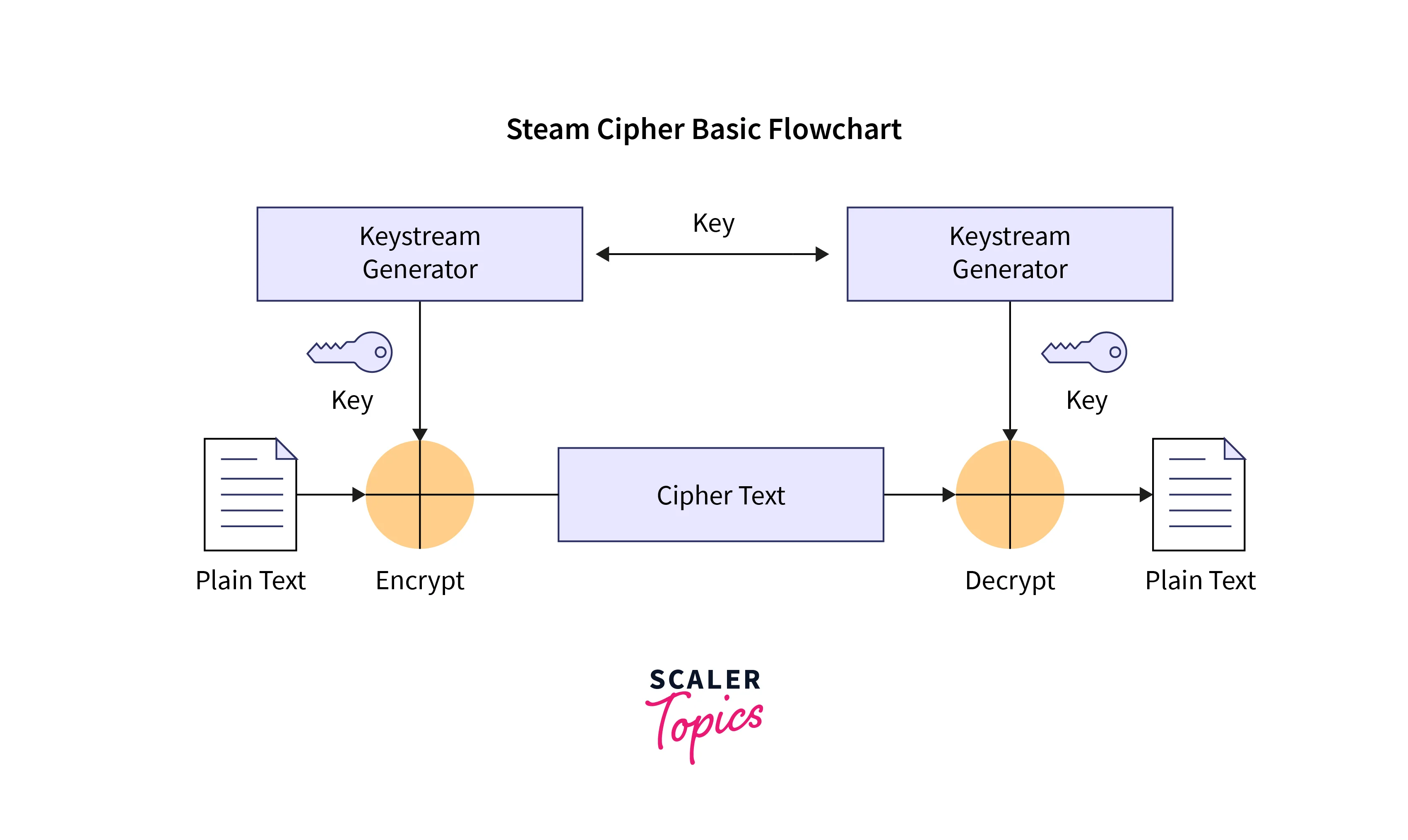
A stream cipher is a symmetric-key cryptographic algorithm used for encrypting and decrypting data bit by bit or byte by byte, typically in a continuous stream. Unlike block ciphers, which process data in fixed-size blocks, stream ciphers operate on individual units of data and are designed for real-time encryption and transmission of data streams.
Key characteristics of stream ciphers:
Symmetric-Key Cryptography: Stream ciphers, like block ciphers, rely on symmetric-key cryptography, meaning the same key is used for both encryption and decryption.
Bit-Level or Byte-Level Processing: Stream ciphers encrypt and decrypt data at the bit or byte level, making them well-suited for encrypting data streams, such as network communication, voice, or video.
Keystream Generation: Stream ciphers generate a pseudorandom keystream based on the encryption key. This keystream is then combined with the plaintext (or ciphertext during decryption) using bitwise XOR operations to produce the encrypted data.
Synchronous vs. Self-Synchronizing: Stream ciphers can be categorized as synchronous or self-synchronizing:
Synchronous Stream Ciphers: Generate the keystream solely based on the key and initialization vector (IV), and both the sender and receiver must be synchronized to use the same keystream.
Self-Synchronizing/Asynchronous Stream Ciphers: Use the previous ciphertext (or plaintext during decryption) to synchronize the keystream generation, making them more resilient to minor transmission errors.
Real-Time Applications: Stream ciphers are ideal for encrypting data streams in real-time because they do not require dividing data into fixed-size blocks, allowing for continuous encryption and decryption of varying data lengths.
Types of Stream Ciphers
-
Synchronous Stream Ciphers: Synchronous Stream Ciphers are cryptographic algorithms that generate a pseudorandom keystream based on a secret key and an initialization vector (IV). This keystream is combined with the plaintext using bitwise XOR to produce ciphertext, and both the sender and receiver must be synchronized with the same key and IV for successful encryption and decryption.
-
Self-Synchronizing/Asynchronous stream Ciphers: Self-Synchronizing/Asynchronous Stream Ciphers are cryptographic algorithms that generate a keystream based on the previous ciphertext (or plaintext during decryption), allowing them to automatically synchronize and recover from minor transmission errors without explicit use of an initialization vector (IV).
Differences between Block Cipher and Stream Cipher (Table)
| Aspect | Block Cipher | Stream Cipher |
|---|---|---|
| Data Processing | Processes fixed-size blocks of data | Processes data bit by bit or byte by byte |
| Real-time Stream Encryption | Typically not suitable for real-time streams | Well-suited for real-time stream encryption |
| Encryption Speed | Slower due to block-by-block processing | Faster, as it operates on individual bits or bytes |
| Modes of Operation | Operates in various modes like ECB, CBC, CFB, etc. | Generally does not have modes of operation |
| Error Propagation | Errors in one block affect the entire block | Errors are typically localized and don't propagate |
| Parallel Processing | Limited parallelism due to block processing | High parallelism potential for bit-level operations |
| Use Cases | Common for disk encryption, data at rest | Common for network communication, data in motion |
Conclusion
- This article defines and gives you an understanding of block cipher vs. stream cipher.
- Block ciphers process data in fixed-size blocks, while stream ciphers operate on data bit by bit or byte by byte.
- Stream ciphers are suitable for real-time encryption, while block ciphers are often used for data at rest.
- Block ciphers have various modes of operation, while stream ciphers typically do not.
- Block ciphers can suffer from error propagation, whereas stream ciphers tend to localize errors.
- Stream ciphers offer high parallelism potential for encryption of individual bits or bytes, while block ciphers are limited in parallelism due to block processing.
