How to Check Open Ports in Linux?
In the domain of computer networking, open ports serve as essential gateways for communication between devices and services. Whether troubleshooting network connectivity or enhancing system security, knowing how to check open ports is crucial. This article explores various methods to accomplish this task in Linux, equipping you with the knowledge and tools needed to monitor and manage network connections effectively. From understanding network ports to practical techniques using command-line tools like netstat, ss, lsof, nmap, and netcat, you'll gain the expertise to navigate the landscape of open port checking confidently. Let's demystify the process of checking open ports in Linux together!
What are Network Ports?
A port is a communication endpoint used in computer networking that identifies a particular process or service on a Linux system. Ports allow multiple applications to run simultaneously on a single system, each using a different port to send and receive data. Ports are essential for establishing network connections and enabling communication between different devices over a network.
In Linux, ports are identified by numbers ranging from to . These numbers are divided into three ranges:
- Well-known ports: Ports in the range 0-1023 are reserved for well-known services. These ports are standardized and assigned to specific protocols or services. For example, port is commonly used for HTTP (Hypertext Transfer Protocol) traffic.
- Registered ports: Ports in the range 1024-49151 are known as registered ports. They can be used by user applications or software services that are not part of the operating system's standard services.
- Dynamic or private ports: Ports in the range 49152-65535 are dynamic or private ports. Client applications typically use these ports for temporary connections and are not assigned to specific services.
Understanding network ports is crucial when troubleshooting network connectivity issues or securing a Linux system.
Examples of Important Ports
The following are examples of some important ports and the services they are commonly associated with:
- Port : Secure Shell (SSH) for secure remote access to a Linux system.
- Port : HTTP for web traffic.
- Port : HTTPS for secure web traffic.
- Port : Simple Mail Transfer Protocol (SMTP) for email transmission.
- Port : Domain Name System (DNS) for translating domain names to IP addresses.
- Port : File Transfer Protocol (FTP) for file transfer.
- Port : MySQL database server.
- Port : Microsoft SQL Server.
- Port : Remote Desktop Protocol (RDP) for remote desktop access.
- Port : OpenVPN for secure virtual private network (VPN) connections.
These are just a few examples, and many more ports are used for various services and protocols.
List Open Ports and Protocols using /etc/services File
The /etc/services file on a Linux system provides a list of well-known ports and the protocols associated with them. You can view the contents of this file to get information about common ports and their corresponding services.
To check open ports using the /etc/services file, follow these steps:
-
Open a terminal on your Linux system.
-
Type the following command to view the file:
Command:
-
The output will display the contents of the /etc/services file, showing port numbers, protocol names, and service names.
Snippet of the output:

You can use this information to identify the ports used by specific services on your Linux system. However, this method only provides information about well-known ports and their protocols and does not show the currently open ports on your system.
List Open Ports with Netstat
Netstat is a command-line tool used for network monitoring and troubleshooting in Linux. It also allows you to check open ports on your system.
To use netstat to list open ports, follow these steps:
- Open a terminal on your Linux system.
- Type the following command:
Command:
The options used in this command have the following meanings:
- -t: Shows TCP (Transmission Control Protocol) ports.
- -u: Shows UDP (User Datagram Protocol) ports.
- -l: Displays listening ports.
- -n: Shows port numbers instead of resolving them to service names.
Output of the netstat command: The output will display a list of open ports along with the corresponding protocols (TCP or UDP) and the process or service using each port. You can identify open ports by looking for the LISTEN state.
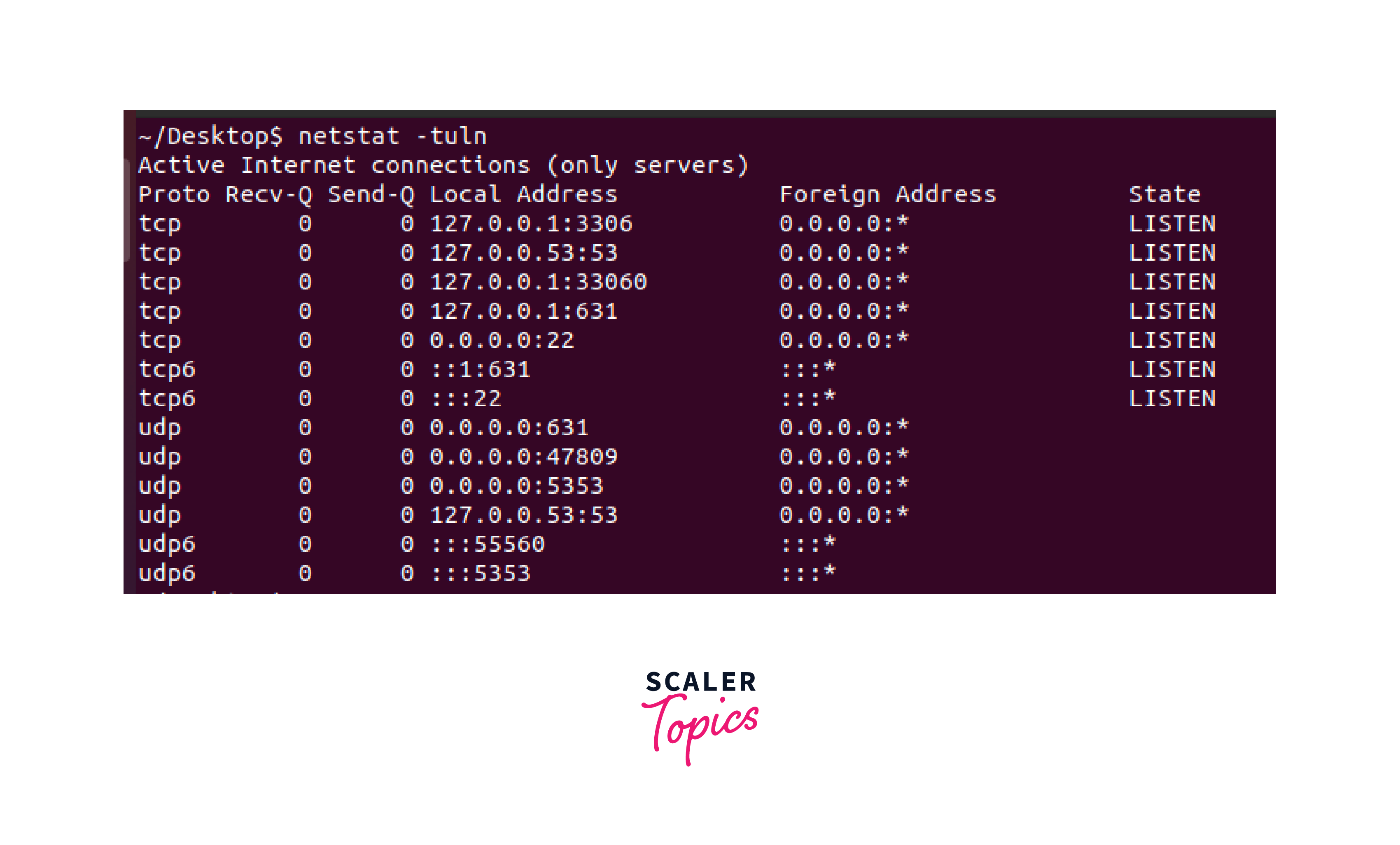
Let's examine important parameters in the output:
- TCP Connections: The system has TCP connections in the LISTEN state. These connections are listening on specific IP addresses and ports:
- 127.0.0.1:631: local address 127.0.0.1, port 631
- 0.0.0.0:22: all network interfaces (0.0.0.0), port 22
- 127.0.0.1:33060: local address 127.0.0.1, port 33060
- 127.0.0.1:3306: local address 127.0.0.1, port 3306
- 127.0.0.53:53: local address 127.0.0.53, port 53
- ::1:631: IPv6 loopback address ::1, port 631
- :::22: all IPv6 addresses (::), port 22
- UDP Connections: The system has UDP connections. These connections are not in the LISTEN state, indicating they are not actively listening. They are bound to specific IP addresses and ports:
- 0.0.0.0:5353: all network interfaces (0.0.0.0), port 5353
- 0.0.0.0:38865: all network interfaces (0.0.0.0), port 38865
- 127.0.0.53:53: local address 127.0.0.53, port 53
- 0.0.0.0:631: all network interfaces (0.0.0.0), port 631
- :::43850: all IPv6 addresses (::), port 43850
- :::5353: all IPv6 addresses (::), port 5353
Check Open Ports Locally
Sometimes, you may only want to check open ports on the local system. In such cases, you can use the loopback IP address (127.0.0.1) to test for open ports locally.
To check open ports locally using the loopback address, follow these steps:
- Open a terminal on your Linux system.
- Type the following command:
Command:
Output of the netstat + grep command: This command filters the output of netstat to show only the open ports associated with the loopback address.
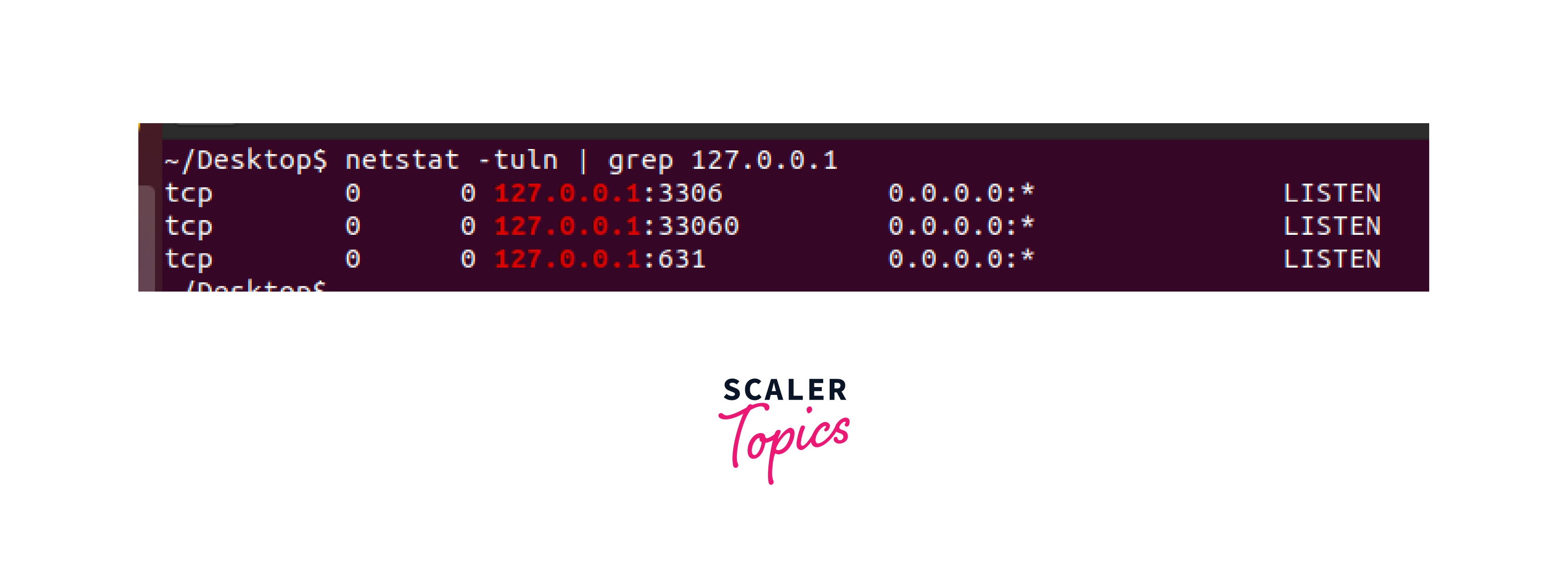
TCP Connections:
- The system has TCP connections in the LISTEN state.
- The connections are established on specific local addresses and ports:
- 127.0.0.1:631: This TCP connection is listening on the local address 127.0.0.1 and port 631.
- 127.0.0.1:33060: This TCP connection is listening on the local address 127.0.0.1 and port 33060.
- 127.0.0.1:3306: This TCP connection is listening on the local address 127.0.0.1 and port 3306.
List open ports with ss
SS (Socket Statistics) is another command-line tool available in Linux for displaying information about network sockets. It provides more detailed and up-to-date information compared to netstat.
To list open ports using ss, follow these steps:
- Open a terminal on your Linux system.
- Type the following command:
Command:
The options used in this command are similar to netstat and have the same meanings:
- -t: Shows TCP ports.
- -u: Shows UDP ports.
- -l: Displays listening ports.
- -n: Shows port numbers instead of resolving them to service names.
Output of the ss command: The output shows a list of open ports with their associated protocols (TCP or UDP) and the process or service using each port.

- UDP Connections: There are several UDP connections in the UNCONN state. They are associated with different local addresses and ports, including 0.0.0.0:5353, 0.0.0.0:50655, 127.0.0.53%lo:53, 0.0.0.0:631, [::]:5353, and [::]:46315. The peer addresses are represented as 0.0.0.0:* and [::]:*.
- TCP Connections: There are several TCP connections in the LISTEN state. They are associated with different local addresses and ports, including 127.0.0.1:3306, 127.0.0.53%lo:53, 0.0.0.0:22, 127.0.0.1:631, 127.0.0.1:33060, [::]:22, and [::1]:631. The peer addresses are represented as 0.0.0.0:* and [::]:*.
List open ports with lsof
LSOF (List Open Files) is a powerful command-line tool that can also be used to check open ports on a Linux system. It provides information about files and processes currently open by the system.
To list open ports using lsof, follow these steps:
- Open a terminal on your Linux system.
- Type the following command:
Command:
The options used in this command have the following meanings:
- -i: Filters the output to show only internet-related files.
- -P: Prevents port number resolution to service names.
- -n: Shows port numbers instead of resolving them to host names.
- grep LISTEN: Filters the output to show only listening ports.
Output of the lsof command: The output displays the open ports in a readable format, including the process ID (PID) and the process name or service associated with each port.

Here's a brief text explanation:
- systemd-r: This process, owned by the systemresolve user, has file descriptor (FD) 13u and uses IPv4 protocol. It listens on local address 127.0.0.53:53 for TCP connections.
- cupsd: There are two instances of the cupsd process. The first instance, owned by the root user, has file descriptor (FD) 6u and uses IPv6 protocol. It listens on the local address [::1]:631 for TCP connections. The second instance, also owned by root, has file descriptor (FD) 7u and uses IPv4 protocol. It listens on the local address 127.0.0.1:631 for TCP connections.
- sshd: This process, owned by the root user, has two file descriptors (FD), one for IPv4 and another for IPv6 connections. It listens on the wildcard address (*) and port 22 for both IPv4 and IPv6 TCP connections.
- myself: There are two instances of the mysqld process, both owned by the mysql user. The first instance has file descriptor (FD) 31u and uses IPv4 protocol. It listens on the local address 127.0.0.1:33060 for TCP connections. The second instance has file descriptor (FD) 34u and uses the IPv4 protocol. It listens on the local address 127.0.0.1:3306 for TCP connections.
List open ports with nmap
A network can be scanned using the powerful open-source network scanning tool Nmap to find hosts and services. We can also use it to check open ports on a Linux system.
To list open ports using nmap, follow these steps:
- Install nmap on your Linux system if it is not already installed. To install it, use your Linux distribution package manager. For example, on Ubuntu, you can run the following command:
Command:
- Open a terminal on your Linux system.
- Type the following command: Command:
This command instructs nmap to scan all ports on the local system.
The output will display a list of open ports along with their associated services and protocols.
Output of the nmap command:
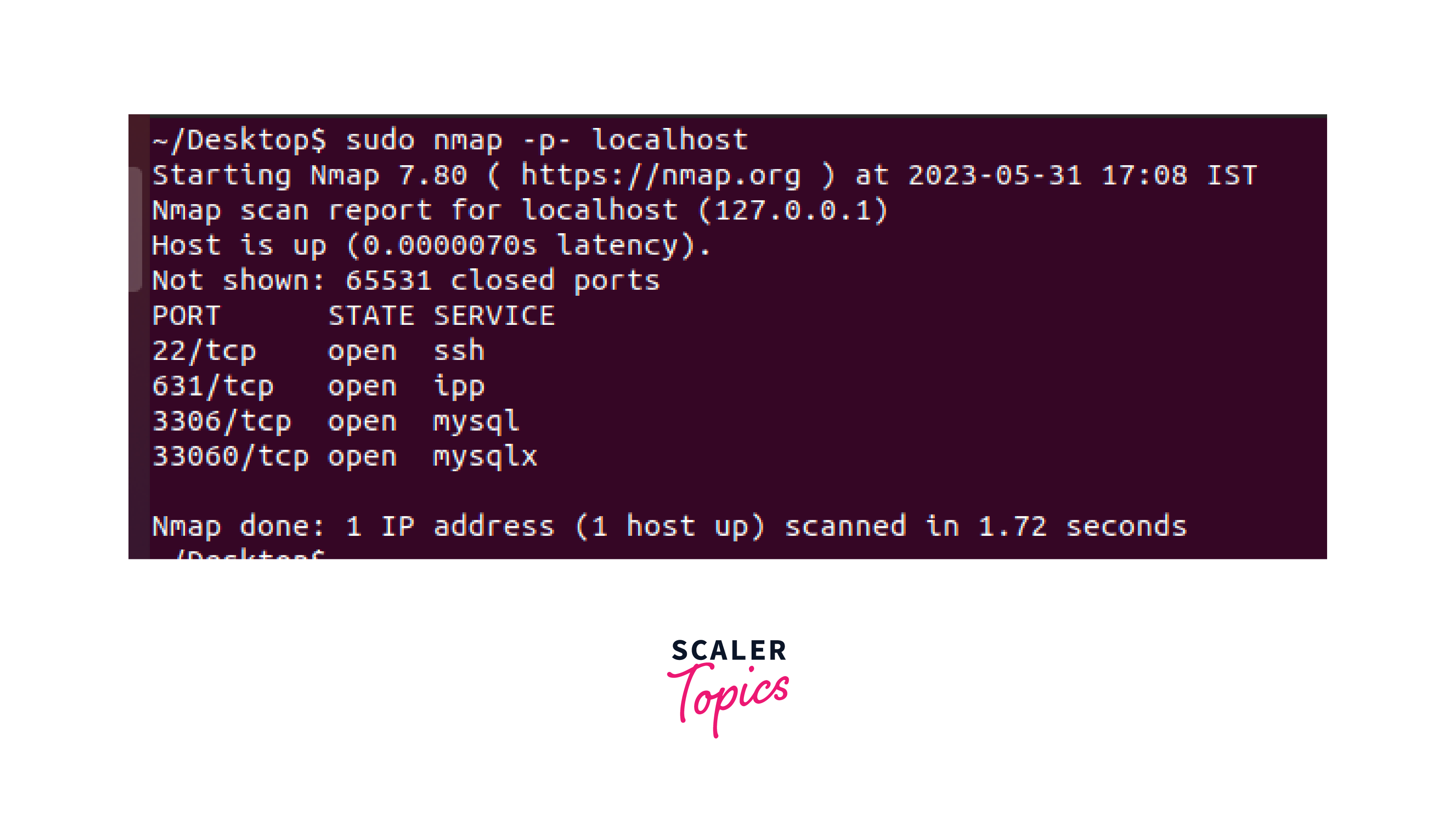
Here's a very short explanation:
- The scan revealed four open ports: port 22 is open for SSH, port 631 is open for IPP (Internet Printing Protocol), port 3306 is open for MySQL, and port 33060 is open for MySQLX.
- The scan did not show the details of the 65531 closed ports on the local host.
- The Nmap scan was completed in 1.15 seconds, scanning one IP address with one host being up.
List open ports with netcat
Netcat, also known as nc, is a versatile command-line tool for network communication in Linux. It can be used to establish connections, send and receive data, and also check open ports.
To list open ports using netcat, follow these steps:
- Open a terminal on your Linux system.
- Type the following command:
Command:
This command uses netcat to scan all ports (1-65535) on the local system.
The output will show the open ports with a successful connection message.
Using GUI Tools to Check Open Ports
While command-line tools are commonly used to check open ports in Linux, graphical user interface (GUI) tools are also available that provide a more intuitive and visual approach. These GUI tools can be particularly helpful for users who prefer a graphical interface or those who are new to the command line. Here are a few examples:
-
Gufw: Gufw is a user-friendly graphical interface for the Uncomplicated Firewall (UFW) in Ubuntu and other Debian-based distributions. It allows you to easily configure firewall rules, including opening and closing specific ports. By accessing the GUI, you can view a list of open ports and their associated rules, making monitoring and managing your system's network connections convenient.
-
FirewallD: FirewallD is a dynamic firewall management tool available in various Linux distributions, including CentOS, Fedora, and openSUSE. It provides both a command-line interface and a GUI tool called firewall-config. With firewall-config, you can easily visualize and manage firewall rules, including allowing or blocking specific ports. It offers a comprehensive overview of open ports and simplifies the process of checking and configuring them.
Checking Open Ports with System Monitoring Tools
In addition to dedicated port scanning tools and command-line utilities, you can also leverage system monitoring tools to check open ports in Linux. Here are a few examples:
-
htop: htop is an interactive process viewer that offers an enhanced alternative to the traditional top command. In htop, you can navigate through processes and monitor system resources. To check open ports, launch htop in the terminal and press F4 or select Setup from the menu. Then, type LISTEN in the Filter field to display only processes with open listening ports. This allows you to identify the processes associated with open ports.
-
Gnome System Monitor: Gnome System Monitor is a graphical tool available in GNOME-based Linux distributions. It provides a comprehensive overview of system resources, including network connections. Launch Gnome System Monitor, navigate to the Processes or Network tab, and look for processes or connections in the Listening state. This will show you the open ports and the associated processes or services.
-
Nagios: Nagios is a powerful and extensible monitoring system widely used for network and system monitoring. It offers various plugins and modules to monitor network services, including open ports. By configuring Nagios and its associated plugins, you can set up checks to monitor the availability and responsiveness of specific ports on your Linux system.
Understanding Firewall Configuration
When checking open ports in Linux, it's important to consider the role of firewall configurations. Firewalls act as a protective barrier between your system and the network, controlling incoming and outgoing network traffic.
Linux systems commonly use firewall solutions like iptables or nftables. These firewall configurations can restrict access to specific ports or block incoming connections altogether. It's essential to understand how firewall rules can affect the visibility of open ports.
To check open ports accurately, you need to ensure that the firewall allows the desired connections. Here are some key points to consider:
-
Firewall Rules: Review the active firewall rules to determine if any restrictions or blocks are in place. Use the appropriate command-line tools for your firewall configuration, such as iptables or nft, to list the active rules.
-
Allow Incoming Connections: If you intend to check open ports from external systems, ensure that the firewall permits incoming connections to the ports you wish to check. Adjust the firewall rules accordingly to allow traffic to those ports.
-
Temporary Rule Adjustments: Sometimes, you may temporarily modify the firewall rules to allow all incoming connections for testing purposes. However, exercise caution when making such changes and remember to revert them to their original state once testing is complete.
Conclusion
- Checking open ports in Linux is essential for network troubleshooting, security auditing, and monitoring network services.
- In this article, we explored various methods to check open ports in Linux, including using the /etc/services file, netstat, ss, lsof, nmap, and netcat.
- Each method provides different levels of information and can be useful in different scenarios.
- By understanding how to check open ports, you can better manage network connections and ensure the security and stability of your Linux system.
