Hunting for Subdomains
Overview
The article provides an in-depth look into the world of subdomain hunting and the various tools that are available for conducting these types of assessments. The article covers popular subdomain hunting tools such as Sublist3r, Amass, Nmap, Knock, and Assetfinder and explains the features, benefits, and limitations of each tool.
The article also covers how to set up and configure each tool, including the technical details of system requirements, installation process, and commands used to run subdomain hunts. The article also explains how to analyze and interpret the results of subdomain hunting tests, including the types of information that can be gathered, and how to identify potential vulnerabilities.
Introduction
Hunting for subdomains is an essential aspect of website security and vulnerability assessment. With the increasing usage of subdomains for various purposes such as hosting applications, providing customer service, or creating landing pages, it becomes important to identify and assess the security of each subdomain. By discovering subdomains, one can gain a deeper understanding of the target website and its infrastructure, allowing for a more comprehensive security assessment.
The process of hunting for subdomains involves several techniques such as using automated tools, searching publicly available information, and monitoring the target website for changes. This helps to uncover hidden subdomains that may not be easily accessible and can also provide insight into the organization's network structure. The information obtained through hunting for subdomains can be used to find vulnerabilities and fix them before they are exploited by malicious actors.
Hunting for subdomains is a crucial task for both cybersecurity professionals and website owners. While the former can use it to identify security weaknesses and potential threats, the latter can use it to assess the efficiency of their website structure and identify opportunities for improvement. With the ever-evolving cyber security landscape, hunting for subdomains has become an essential part of website management and is a critical aspect of protecting against cyber-attacks and data breaches.
Explanation of What Subdomains are and Why They are Important in the Context of Cybersecurity
Subdomains serve as an extension of a main domain and are typically used to separate different sections or functionalities of a website. For example, a website may have a subdomain dedicated to customer support, while another may be used for e-commerce transactions. This allows organizations to structure their websites in a way that makes sense for their users, while also making it easier to manage the different components of their websites.
The use of subdomains also provides benefits in terms of search engine optimization (SEO), as it allows for greater control over the URLs used to access the different sections of a website. This makes it easier for search engines to index and categorizes the content on a website, improving its visibility in search results.
However, subdomains can also introduce security risks if not properly secured. For example, if an attacker can compromise a subdomain, they can potentially gain access to sensitive information, such as customer data, financial information, or internal communications. This is why organizations need to monitor their subdomains and ensure that they are protected with appropriate security measures, such as encryption and access controls.
In addition to the risks posed by malicious actors, subdomains can also be vulnerable to internal security threats, such as accidental data loss or exposure due to misconfigurations. This is why it is important to have a comprehensive security plan in place that covers all subdomains and the applications and services they host.
Subdomains are an important component of website organization and structure, and can provide many benefits in terms of user experience and search engine optimization. However, they also introduce potential security risks that must be addressed through monitoring and security measures. Organizations should take a proactive approach to subdomain security to minimize the risk of data breaches and protect their sensitive information.
Brief Overview of the Purpose and Function of Subdomain Hunting
The purpose and function of subdomain hunting include:
- The purpose of subdomain hunting is to gain a better understanding of a website's infrastructure and its associated subdomains. This information can then be used to assess the security of the website and identify potential vulnerabilities that could be exploited by malicious actors. By discovering subdomains, security professionals can also identify any misconfigurations that could expose sensitive information and data.
- The function of subdomain hunting is to identify all the subdomains associated with a website and gather information about each subdomain, including its purpose, hosting location, and associated applications or services. This information can then be used to identify security risks and vulnerabilities, as well as to assess the overall security posture of the website.
- Subdomain hunting is typically performed using a combination of automated tools and manual methods, such as searching publicly available information and monitoring the target website for changes. The information obtained from subdomain hunting can then be used to prioritize security assessments and make informed decisions about how best to protect the website from potential threats.
Understanding Subdomain Hunting Tools
Subdomain hunting tools are software programs designed to automate the process of discovering and cataloging subdomains associated with a target website. These tools use various methods to search for subdomains, including brute-force techniques, domain name service (DNS) enumeration, and data scraping from public sources.
One of the primary benefits of using subdomain hunting tools is the ability to quickly and efficiently gather information about a website's infrastructure. This information can be used to assess security risks, prioritize security assessments, and make informed decisions about how best to protect the website from potential threats.
There are several different types of subdomain hunting tools available, each offering different features and capabilities. Some tools focus solely on subdomain discovery, while others offer more advanced features, such as the ability to assess the security of discovered subdomains and identify potential vulnerabilities. When selecting a subdomain hunting tool, it is important to consider several factors, including the accuracy of the results, the speed of the tool, and its ease of use. Additionally, organizations consider the cost of the tool, as well as any associated licensing or maintenance fees.
Subdomain hunting tools are an essential aspect of website security and vulnerability assessment. By automating the process of discovering and cataloging subdomains, these tools help security professionals quickly and efficiently assess the security posture of a website and identify potential security risks. When selecting a subdomain hunting tool, it is important to consider the accuracy, speed, and cost of the tool, as well as its ease of use and other features.
Overview of Popular Subdomain Hunting Tools Such as Sublist3r, Amass, and Other Similar Tools
Subdomain hunting is an important aspect of website security and vulnerability assessment, and there are several popular tools available to automate this process. Some of the most popular subdomain-hunting tools include:
-
Sublist3r:
Sublist3r is a well-established subdomain hunting tool that is widely used by security professionals around the world. It offers a fast and efficient method of searching for subdomains, making it an ideal tool for security assessments. Sublist3r uses a combination of techniques to search for subdomains, including brute-force techniques, DNS enumeration, and data scraping from public sources.One of the key benefits of Sublist3r is its accuracy. The tool uses a comprehensive database of subdomains, which is constantly updated to ensure that the results are accurate and up-to-date. This makes Sublist3r a valuable tool for security professionals who need to make informed decisions about website security and vulnerability assessment. The tool has a simple and intuitive user interface, making it accessible to users of all levels of technical expertise. This makes it an ideal tool for security professionals who need to gather information quickly and efficiently.
-
Amass:
Amass is a cutting-edge subdomain hunting tool that offers a range of advanced features and capabilities. Unlike other subdomain hunting tools, Amass is designed to go beyond just discovering subdomains and offer a comprehensive security assessment. This makes it a valuable tool for security professionals who require in-depth information about a website's infrastructure.The tool can collect information such as IP addresses, server names, and other relevant details about each subdomain. Another feature of Amass is its ability to assess the security of discovered subdomains. The tool can identify potential vulnerabilities and security risks, such as weak passwords, unpatched software, and other issues that could leave a website vulnerable to attack.
-
Nmap:
Nmap is a multi-functional tool that is commonly used for network mapping and security assessments. While Nmap is primarily used for network mapping, it can also be used for subdomain hunting. Nmap uses various techniques, such as port scanning, to identify active subdomains and gather information about them.Nmap is a powerful tool that can be used in conjunction with other tools to gather comprehensive information about a website's infrastructure. For example, Nmap can be used to identify active subdomains and then used in combination with other tools, such as vulnerability scanners, to assess the security of the website. Nmap uses various techniques, such as port scanning, to identify active subdomains, ensuring that the results are accurate and up-to-date.
-
Knock:
Knock is a straightforward subdomain discovery tool that is designed to provide quick and accurate results. The tool uses a brute-force technique to search for subdomains, which involves systematically trying different combinations of subdomains until a match is found. This makes Knock a fast and efficient tool for security professionals who need to gather information about subdomains quickly. The tool has a straightforward and easy-to-use interface, making it accessible to users of all levels of technical expertise. This makes it an ideal tool for security professionals who need to gather information quickly and don't have the time or technical expertise to use more complex tools. Another advantage of Knock is its speed. The tool uses a brute-force technique to search for subdomains, which can produce quick results. This makes it an ideal tool for security professionals who need to gather information quickly and efficiently. -
Assetfinder:
Assetfinder is a popular subdomain hunting tool that is designed for security professionals who need to gather information quickly and efficiently. The tool uses various methods, including DNS enumeration, to gather information about subdomains, making it an accurate and reliable tool for security assessments. Assetfinder tool has a simple interface, making it accessible to users of all levels of technical expertise. This makes it an ideal tool for security professionals who need to gather information quickly and don't have the time or technical expertise to use more complex tools. The tool uses various methods, including DNS enumeration, to gather information about subdomains, making it a fast and efficient tool for security professionals who need to gather information quickly. In addition, Assetfinder is a lightweight tool.
There are several popular subdomain hunting tools available, each offering different features and capabilities. When selecting a subdomain hunting tool, it is important to consider the accuracy, speed, and ease of use of the tool, as well as its cost and any associated licensing or maintenance fees.
Setting Up and Configuring Subdomain Hunting Tools
Setting up and configuring subdomain hunting tools can be a critical step in ensuring the accuracy and efficiency of subdomain hunting. Several factors need to be considered when setting up and configuring these tools, including the tool's requirements, the target website, and the user's technical expertise. In this section, we will see the setting up and configuration setting for Sublist3r.
- Assess system requirements:
To ensure that Sublist3r runs smoothly on the system, it is important to assess the system requirements. This includes checking the operating system compatibility and minimum memory requirements. Sublist3r is compatible with Windows, MacOS, and Linux operating systems and requires at least 1 GB of memory. Additionally, it is recommended to have the latest version of Python installed on the system. Sublist3r is written in Python and requires version 2.7 or higher to function properly. - Gather information about the target website:
Before setting up Sublist3r, it is important to gather relevant information about the target website. This information includes the domain name and IP address of the target website, which can help Sublist3r to more accurately identify subdomains. It is also important to understand the structure of the target website and its hosting environment. This information can be gathered using tools such as Whois, nslookup, and traceroute. - Download and install Sublist3r:
Sublist3r can be downloaded from its official website or other sources, such as GitHub. Once downloaded, Sublist3r can be installed by following the instructions provided in the installation guide. The installation process involves extracting the files from the archive and moving them to the desired location on the system. - Configure Sublist3r:
Sublist3r can be configured by editing its configuration file, which is usually located in the installation directory. The configuration file allows the user to set the target domain, set the number of threads, and specify the wordlist used for brute-forcing. The configuration file can also be used to specify additional options, such as the maximum number of results to display and the type of subdomains to include. It is important to carefully configure the tool to ensure that it operates optimally and produces accurate results. - Test Sublist3r:
Once Sublist3r is installed and configured, it is important to test the tool to ensure that it is functioning correctly. This can be done by running Sublist3r against a test website and checking the results to ensure that all subdomains are accurately identified. If any errors or issues are encountered during the testing process, it is important to troubleshoot and resolve them before using the tool in a real-world scenario.
Running a Subdomain Hunt
These are the basic steps and commands used to run a subdomain hunt using Sublist3r, Amass, and Knock. It is important to remember that different tools may have different options and commands, so it is important to consult the documentation of each tool before using it.
Running a Subdomain Hunt Using Sublist3r
-
Installation:
To run a subdomain hunt using Sublist3r, the tool must first be installed. This can be done using pip, which is a package manager for Python. To install Sublist3r using pip, the command pip install sublist3r should be entered in the terminal. -
Usage:
To run a subdomain hunt using Sublist3r, the target domain must be entered as an argument in the terminal. The command sublist3r -d [target domain] can be used for this purpose. -
Options:
Sublist3r offers several options that can be used to customize the subdomain hunt. For example, the option -t [number of threads] can be used to specify the number of threads that will be used to search for subdomains. By default, Sublist3r uses 10 threads. -
Output:
The output of the subdomain hunt will be displayed in the terminal and will include a list of all the subdomains discovered. The output can be saved to a file using the option -o [output file name].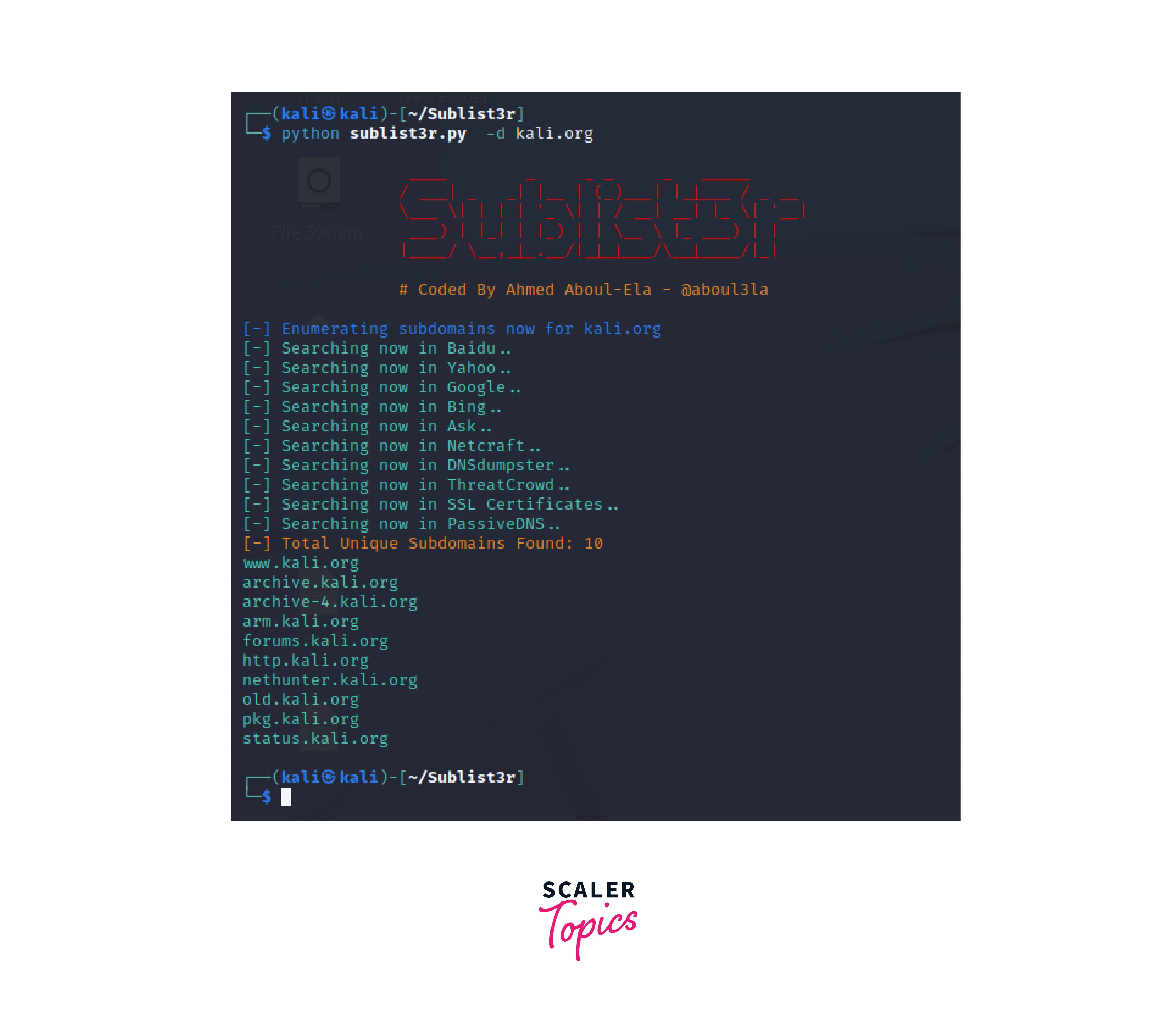
Running a Subdomain Hunt Using Amass
-
Installation:
To run a subdomain hunt using Amass, the tool must first be installed. This can be done using Go, which is a programming language. To install Amass using go, the command go get -u github.com/OWASP/Amass should be entered in the terminal. To install using snap in Linux we use the command snap install amass -
Usage:
To run a subdomain hunt using Amass, the target domain must be entered as an argument in the terminal. The command amass enum -d [target domain] can be used for this purpose. -
Options:
Amass offers several options that can be used to customize the subdomain hunt. For example, the option -o [output file name] can be used to save the output of the subdomain hunt to a file. -
Output:
The output of the subdomain hunt will be displayed in the terminal and will include a list of all the subdomains discovered, as well as information about each subdomain such as its IP address, DNS records, and links to any associated websites.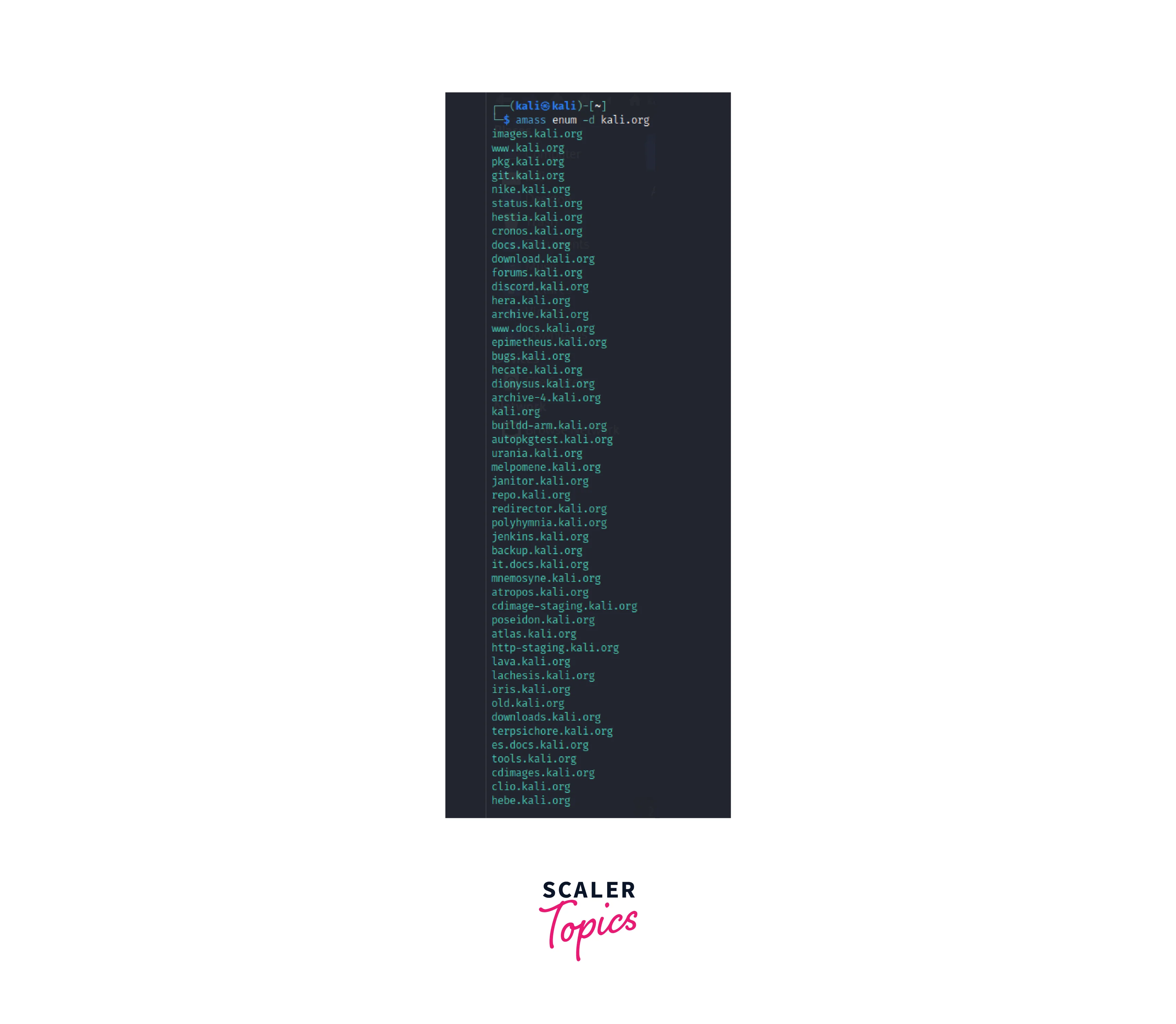 // This shows amass subdomains result
// This shows amass subdomains result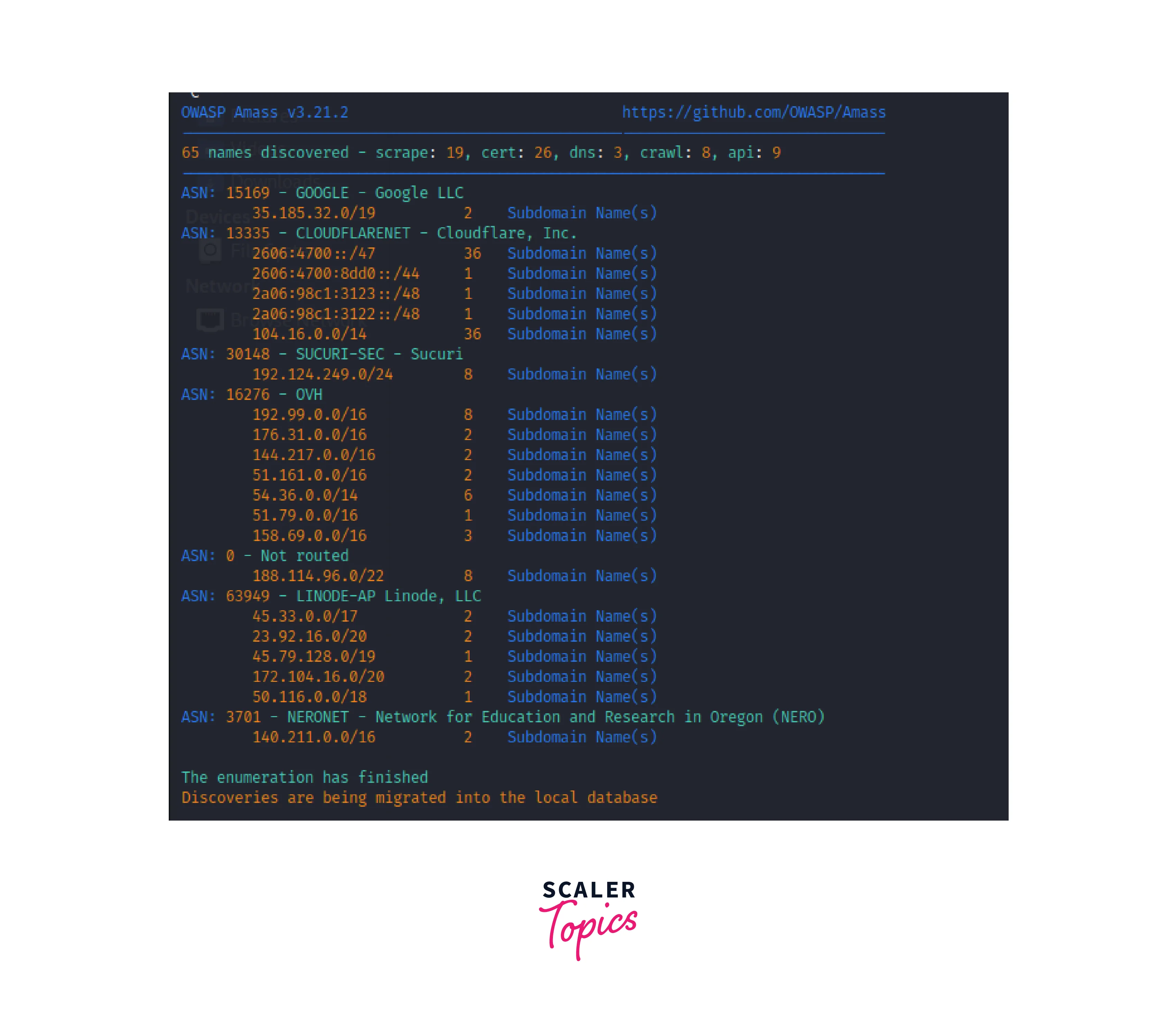 // This image shows the result report generated by amass
// This image shows the result report generated by amass
Running a Subdomain Hunt Using Knock
-
Install Knock:
Before running a subdomain hunt using Knock, it must be installed on the system. This can be done by cloning the repository from GitHub or downloading the package from the website. -
Setting up the command line:
Knock can be run from the command line. To run the subdomain hunt, the target domain name must be specified as an argument. -
Running the hunt:
The subdomain hunt can be started by executing the following command: ./knockpy.py <target domain> -
Analysing the results:
Knock will return a list of subdomains that have been found. This information can be used to identify potential vulnerabilities and assess the security of the target website.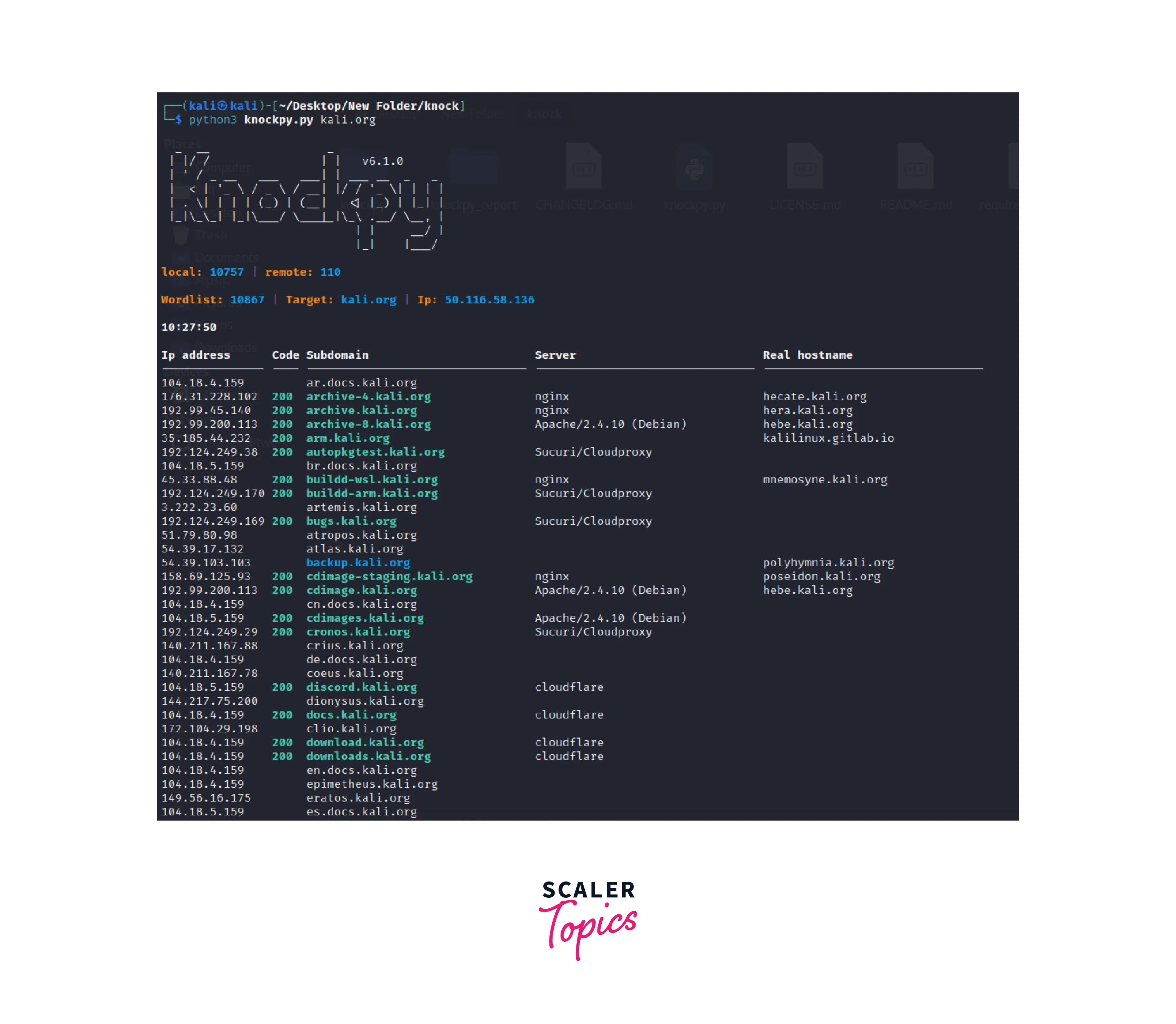 // This shows the knockpy subdomains' result
// This shows the knockpy subdomains' result
Analysing and Interpreting Results
Analysing and interpreting the results of a subdomain hunting test can be a complex process, as the results can vary depending on the tool used and the scope of the test. However, regardless of the tool used, several key steps can be followed to analyze and interpret the results of a subdomain hunting test.
-
The first step in analyzing the results of a subdomain hunting test is to review the list of subdomains that have been discovered. This list should be reviewed to identify any subdomains that have been discovered that are unexpected or seem suspicious. Any subdomains that are identified as suspicious should be further investigated to determine if they pose a security threat.
-
The next step in analyzing the results of a subdomain hunting test is to assess the security of the discovered subdomains. This can be done by looking for potential vulnerabilities, such as open ports or weak credentials, that may make the subdomains more susceptible to attack. Any subdomains that are identified as being vulnerable should be further investigated to determine if they pose a significant security threat.
-
Finally, it is important to interpret the results of a subdomain hunting test in the context of the organization's overall security posture. This may involve comparing the results of the test with the organization's current security practices, identifying any areas where the organization may be exposed to risk, and developing a plan to address these risks.
For example, if a subdomain hunting test performed using Sublist3r discovers a subdomain that is vulnerable to SQL injection, this may indicate that the organization's web applications are not being properly protected against this type of attack. In this case, the organization may need to take steps to better secure its web applications to mitigate the risk of a successful SQL injection attack.
Conclusion
- Subdomain hunting is an important aspect of website security and is used to gather information about a website's infrastructure and potential vulnerabilities.
- Popular subdomain-hunting tools include Sublist3r, Amass, Nmap, Knock, and Assetfinder. Each of these tools offers different features and capabilities, but all are designed to provide comprehensive information about a website's subdomains.
- The process of running a subdomain hunt involves setting up the tool, running the command, and analyzing the results. The results of a subdomain hunt can reveal important information about a website's infrastructure and potential vulnerabilities, which can be used to improve security.
- Subdomain hunting is a crucial aspect of website security, as subdomains can often be used to launch attacks or access sensitive information.
- According to a study, over 50% of all subdomains are vulnerable to attack, making subdomain hunting an important step in securing a website.
