Enumerating FTP with Nmap
Overview
This article aims to provide an in-depth understanding of how to use the Nmap tool to enumerate File Transfer Protocol (FTP) services. The article will cover the basics of FTP and how it works, as well as the various options and commands available in Nmap for enumerating FTP services. The article will also provide examples and step-by-step instructions for using Nmap to enumerate FTP services on a target network.
Introduction
File Transfer Protocol (FTP) is a widely used protocol for transferring files between computers on a network. Nmap, short for "Network Mapper", is a powerful network exploration and security auditing tool. In this article, we will explore how to use Nmap to enumerate FTP servers on a network. We will cover the basics of FTP and what Nmap is, and provide examples of uses of Nmap to perform basic and advanced enumeration tasks on FTP servers.
File Transfer Protocol (FTP)
File Transfer Protocol (FTP) is a standard network protocol used for the transfer of files between a client and a server over a TCP-based network, such as the Internet. FTP is a client-server protocol, meaning that a client initiates a request and a server responds to that request.
The client and server communicate through two separate channels:
- control channel
- data channel
The control channel is used for authentication, issuing commands, and sending status messages, while the data channel is used for the transfer of the actual files.
FTP is also commonly used for website maintenance and management, as it allows for the easy transfer of files between the website developer's computer and the web server. Furthermore, many operating systems, such as Windows and Linux, have built-in support for FTP which makes it easy to use.
Using Nmap to Perform Basic FTP Enumeration
FTP enumeration is the process of identifying and gathering information about an FTP server on a target network. Nmap, a powerful network exploration and security auditing tool, can be used to perform this task.
The basic command for performing an FTP enumeration with Nmap is:
This command tells Nmap to perform a version scan (-sV) on port 21, which is the default port for FTP. The [target host] can be a hostname or IP address.
Another useful option for FTP enumeration is the -A option, which enables OS detection, version detection, script scanning, and traceroute. This option can provide more detailed information about the target host and its FTP service:
Additionally, Nmap also allows users to specify a specific FTP script to run during the enumeration process. To run a specific script, the -sC option can be used. For example, to run the ftp-anon script, which checks for anonymous FTP access, the following command can be used:
These are just a few examples of the basic commands and options that can be used for FTP enumeration with Nmap. There are many other options and scripts available that can provide even more information about the target FTP service. By using Nmap, a cybersecurity professional can quickly and easily gather information about FTP services on a target network and identify any potential vulnerabilities.
Examples of Common Usage Scenarios for Basic FTP Enumeration
Examples of common usage scenarios for basic FTP enumeration with Nmap include:
- Identifying open FTP services on a target network:
This can be done by running a basic port scan (nmap -sV -p 21 [target]) on the target network, which will identify all hosts that have an open TCP port 21 (FTP). - Checking for anonymous login:
By running the nmap --script=ftp-anon [target] command, one can check if the target FTP servers allow anonymous login. - Identifying vulnerable FTP servers:
By running the nmap -sV --script=ftp-vuln-cve\* [target] command, one can identify if the target servers are vulnerable to any known FTP-related vulnerabilities. - Exporting the results of the scan:
By using the -oX or -oN options, one can export the results of the scan to an XML or normal text file respectively.
Advanced Enumeration with Nmap
Advanced enumeration with Nmap involves using more advanced options and commands to gather more detailed information about the target FTP server. This can include using Nmap's scripting engine to run specific scripts that are designed to enumerate FTP servers. Some examples of advanced enumeration techniques include:
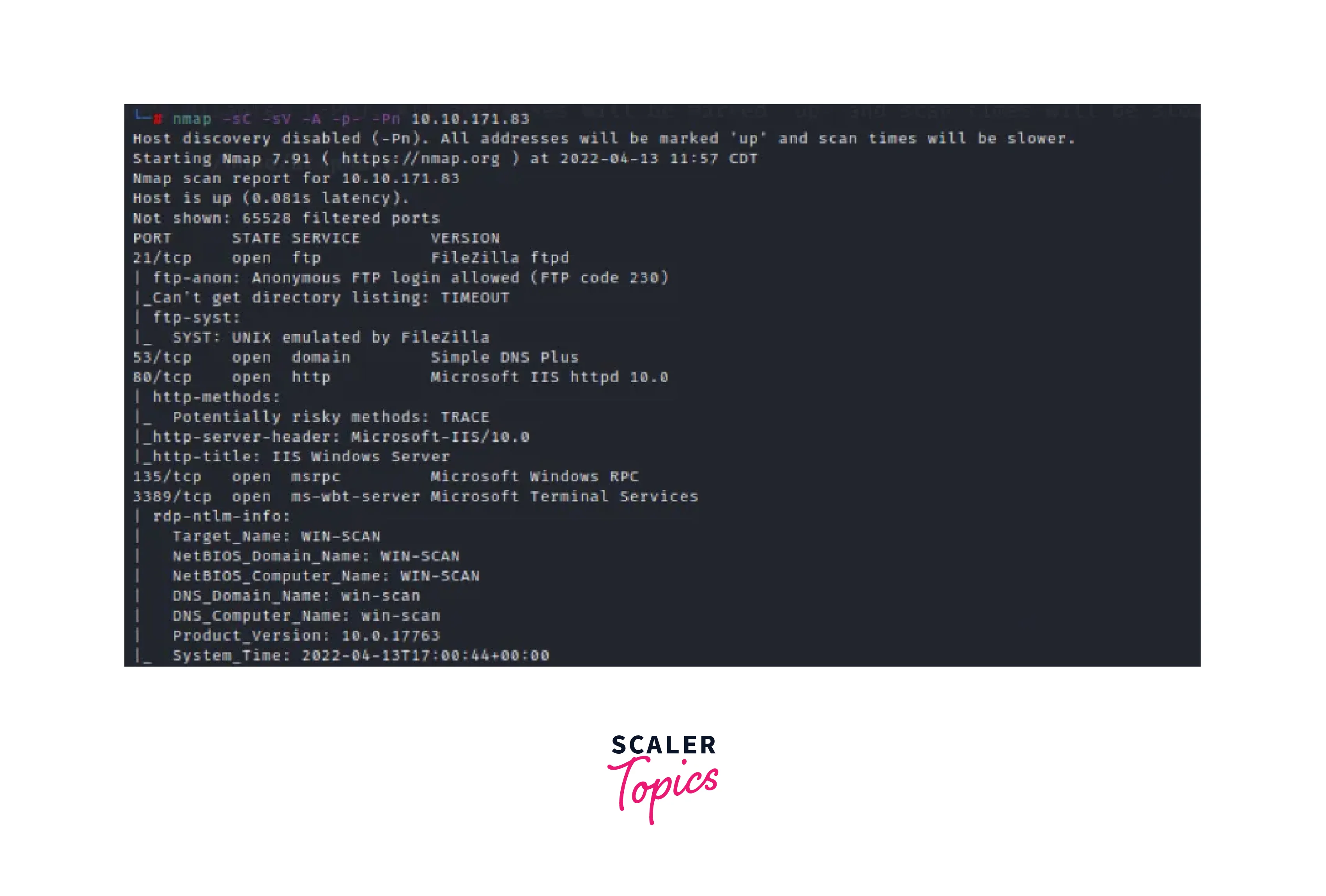
Using Nmap's version detection feature to fingerprint the specific version of the FTP server software in use. This can help identify vulnerabilities that are specific to that version of the software. Using Nmap's script engine to run scripts that are designed to enumerate specific information about the FTP server, such as the directory listing of the server or the users that are currently logged in. Using Nmap's OS detection feature to fingerprint the operating system of the target machine. This can help identify potential vulnerabilities that are specific to that operating system.
Using Nmap's service version detection feature to fingerprint the version of the FTP service running on the target machine. This can help identify vulnerabilities that are specific to that version of the service. Using Nmap's script engine to run other scripts that are designed to enumerate other services running on the target machine, such as HTTP or SMB.
Advanced Options and Commands for Enumerating FTP with Nmap
When performing basic FTP enumeration with Nmap, several common usage scenarios can be encountered. One common scenario is the need to quickly determine which hosts on a network have an FTP service running. In this case, the basic Nmap command for performing a ping sweep and port scan can be used, such as "nmap -sP 192.168.1.1-255 -p 21". This command will ping all hosts in the specified IP range and scan for open ports on port 21, which is the default port for FTP.
Another common scenario is the need to gather detailed information about the version and configuration of an FTP service. This can be accomplished by using the -sV option in Nmap, which attempts to determine the version of the service running on the target host. For example, the command "nmap -sV -p 21 192.168.1.100" will scan port 21 on host 192.168.1.100 and attempt to determine the version of the FTP service running on that host.
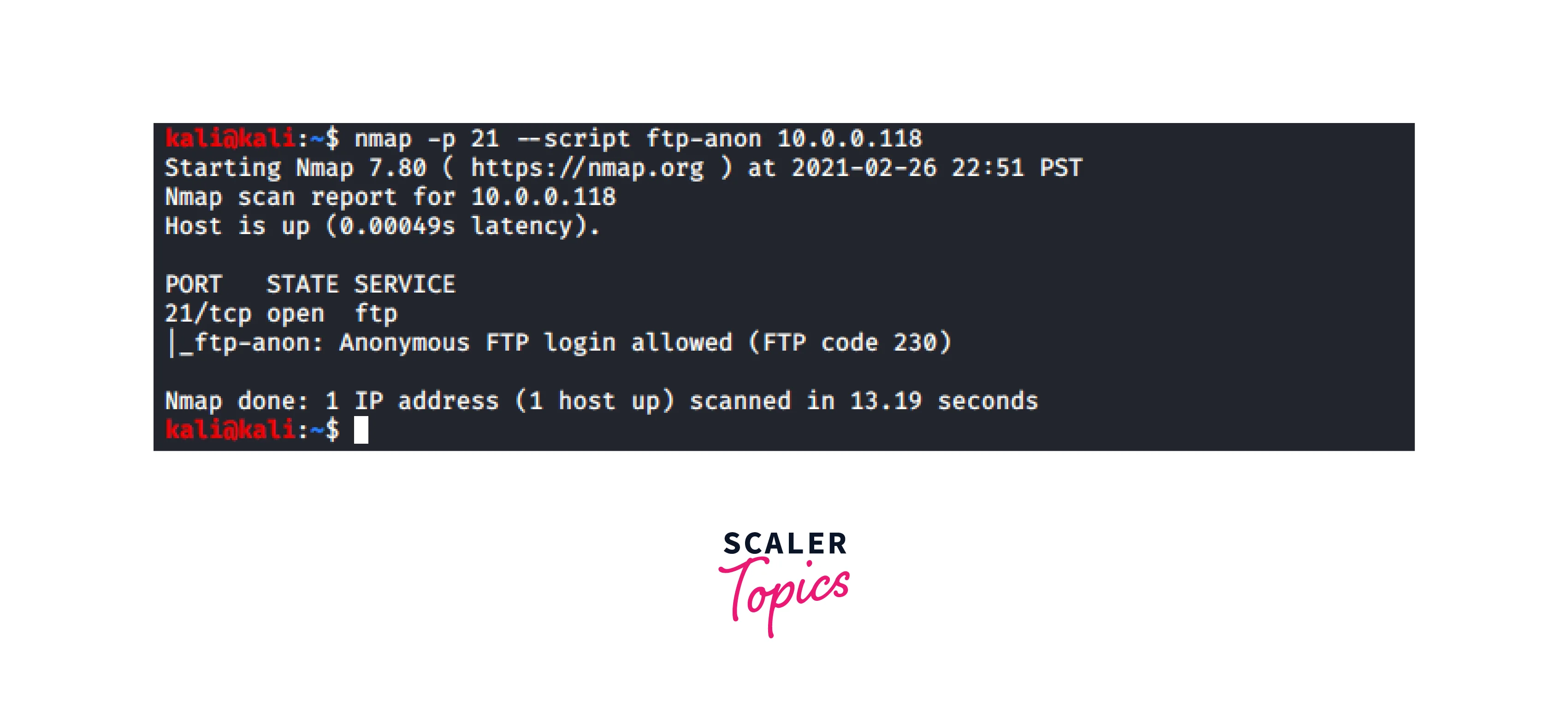
A third common usage scenario is the need to identify anonymous login access to the FTP service. This can be accomplished by using the --script ftp-anon script in Nmap, which checks for anonymous login access and reports the results. For example, the command "nmap --script ftp-anon -p 21 192.168.1.100" will scan port 21 on host 192.168.1.100 and check for anonymous login access to the FTP service.
Explanation of How to Use Nmap to Perform Advanced FTP Enumeration
Advanced enumeration with Nmap involves using more advanced options and commands to gather detailed information about the FTP services on a target network. Some of the advanced options and commands that can be used for FTP enumeration include:
- The -sV option, which can be used to determine the version of the FTP service running on a target host.
- The -A option, which can be used to enable OS detection, version detection, script scanning, and traceroute.
- The -sC option, which can be used to enable the default script scan. This can be useful for identifying vulnerabilities in the FTP service.
- The --script option, which can be used to specify a specific script or set of scripts to run against the target host. This can be useful for gathering detailed information about the FTP service, such as user accounts and file listings.
- The --script-args option, which can be used to pass arguments to the script or set of scripts being run. This can be useful for controlling the behavior of the script or set of scripts and gathering more specific information.
- The --top-ports option, which can be used to specify a specific set of ports to scan. This can be useful for narrowing down the scope of the scan and reducing the amount of time it takes to complete.
- The -p option, which can be used to specify a specific set of ports to scan. This can be useful for targeting specific FTP services or for scanning a small number of hosts.
Techniques for Customizing and Automating FTP Enumeration Using Nmap
One popular script for FTP enumeration is the ftp-anon script, which attempts to log into an FTP server anonymously and gather information about the directories and files that are available. This script can be run using the -sC flag, which tells Nmap to run the default set of scripts.
Another technique for automating FTP enumeration is to use Nmap in combination with other tools, such as Metasploit or Nessus. These tools can be used to perform further enumeration and vulnerability scanning of the target FTP service, providing a more comprehensive view of the security posture of the target network.
Examples of Advanced Usage Scenarios for Enumerating FTP with Nmap
Here are a few examples of advanced usage scenarios for enumerating FTP with Nmap:
1. Detecting and Fingerprinting FTP Servers
Nmap can be used to scan a network for open FTP ports and fingerprint the server software in use, allowing security professionals to identify potential vulnerabilities and misconfigurations. When performing an enumeration of FTP servers with Nmap, one of the first steps is to detect and fingerprint the servers. This is done by sending a series of probes and analyzing the responses to determine the type and version of the server software. Nmap includes several built-in probes for detecting and fingerprinting FTP servers, as well as the ability to use custom probes.
2. Brute-forcing FTP Login Credentials
Nmap can also be used in conjunction with other tools, such as Hydra, to perform a brute-force attack against FTP servers to identify weak login credentials. Brute-forcing FTP login credentials involve attempting to log in to an FTP server using a list of commonly used username and password combinations. This can be done using specialized tools such as "Hydra" or "Medusa" which automates the process of trying different combinations of credentials. The goal of brute-forcing is to find valid login credentials that can be used to gain access to the FTP server. This method can be used for both legitimate penetration testing and malicious activity. It is important to note that many servers have security measures in place to detect and prevent brute-force attacks, such as limiting the number of login attempts or temporarily banning IP addresses that have multiple failed login attempts.
3. FTP Bounce Attacks
Nmap can also be used to perform an FTP bounce attack. FTP bounce attacks are a type of attack that allows an attacker to indirectly connect to a target system through an intermediary FTP server. The attacker first establishes a connection with the intermediary FTP server and then sends commands to the server to connect to the target system.
This is done by using the "PORT" command in FTP, which allows the attacker to specify the IP address and port number of the target system to the intermediary server. The intermediary server then connects to the target system on behalf of the attacker. This type of attack can be used to bypass firewalls or other security measures that are in place to protect the target system. It can also be used to perform reconnaissance on the target system or to launch other types of attacks. It's important to note that not all FTP servers support FTP bounce attacks, and some may even have the ability to detect and prevent them.
4. Scanning for Anonymous FTP Access
Nmap can be used to scan a network to find open FTP servers that allow anonymous access, which can be a security concern if the server contains sensitive information. Scanning for anonymous FTP access is a technique to identify if an FTP server allows anonymous (or unauthenticated) connections. This can be done using various tools, such as Nmap, which has options to check for anonymous access. For example, the Nmap command "nmap -p 21 --script ftp-anon" can be used to scan for anonymous access on port 21 (the default port for FTP) and run the ftp-anon script to check for anonymous login.
If a server allows anonymous access, the script will return a message indicating that anonymous login is allowed and may also provide information about the file system, such as the root directory. This information can be useful to an attacker, as it can be used to identify potentially sensitive files or directories that can be accessed without authentication.
5. Detecting FTP Servers Behind Firewalls
FTP servers can be hidden behind firewalls, making them harder to detect. However, several techniques can be used to detect FTP servers that are behind firewalls. One common method is to use Nmap's "-sV" option to perform a version scan of the target network. This option sends probes to the target host to determine the version of the services running on the host. It can also identify open ports and the services running on them. Another method is to use the Nmap Scripting Engine (NSE) to run scripts that are specifically designed to detect FTP servers behind firewalls. These scripts can be used to fingerprint the FTP server and identify the version of the software running on it. Additionally, some firewall configurations may allow an FTP control connection but not the data connection, this can be detected by performing a "FTP bounce scan" which involves bouncing the data connection through a different open FTP server to connect to the target FTP server.
Techniques for Identifying Vulnerabilities
There are several techniques for identifying vulnerabilities in a system or network. Some of the most common techniques include:
- Vulnerability scanning:
This technique involves using automated tools to scan a system or network for known vulnerabilities. These tools typically check for missing patches, misconfigurations, and other issues that could be exploited by an attacker. - Penetration testing:
This technique involves simulating an attack on a system or network to identify vulnerabilities and assess the effectiveness of security controls. Penetration testing can be performed manually or with the use of automated tools. - Source code analysis:
This technique involves reviewing the source code of a software application to identify vulnerabilities that could be exploited by an attacker. This can be done manually or with the use of automated tools. - Social engineering:
This technique involves tricking individuals into revealing sensitive information or performing actions that could compromise security. Social engineering can be performed through phishing emails, phone calls, or in-person interactions. - Network traffic analysis:
This technique involves monitoring network traffic to identify unusual activity that could indicate a security incident. This can be done with the use of network security monitoring tools. - Physical security assessment:
This technique involves evaluating the physical security controls of a facility to identify vulnerabilities that could be exploited by an attacker. This can include evaluating access controls, cameras, and other physical security measures.
Conclusion
- FTP is a widely used network protocol for transferring files between computers on a network.
- Nmap is a powerful tool that can be used to enumerate various services and protocols, including FTP.
- By using Nmap, one can discover hosts and services on a computer network, scan ports, use scripting engine and vulnerability scanning, as well as output the results in different formats.
- This article has explored how to use Nmap to enumerate FTP services on a target network, covering the basics of FTP, how it works, and the various options and commands available in Nmap for enumerating FTP services.
- From basic enumeration to advanced techniques such as brute-forcing login credentials, FTP bounce attacks, and scanning for anonymous access, this article has provided a comprehensive guide on how to effectively use Nmap for FTP enumeration and vulnerability detection.
