What is Attack Vector and Attack Surface?
Overview
In the ever-evolving world of cybersecurity, safeguarding sensitive information and systems has become an imperative task. The rise of advanced cyber threats has necessitated the adoption of comprehensive security measures, one of which is the zero-trust security model. This approach emphasizes the need to validate every user and device attempting to access a network. A critical aspect of zero trust security is understanding the concepts of attack vectors and attack surfaces. These two elements play a pivotal role in identifying vulnerabilities and devising robust security strategies.
What Is An Attack Vector?
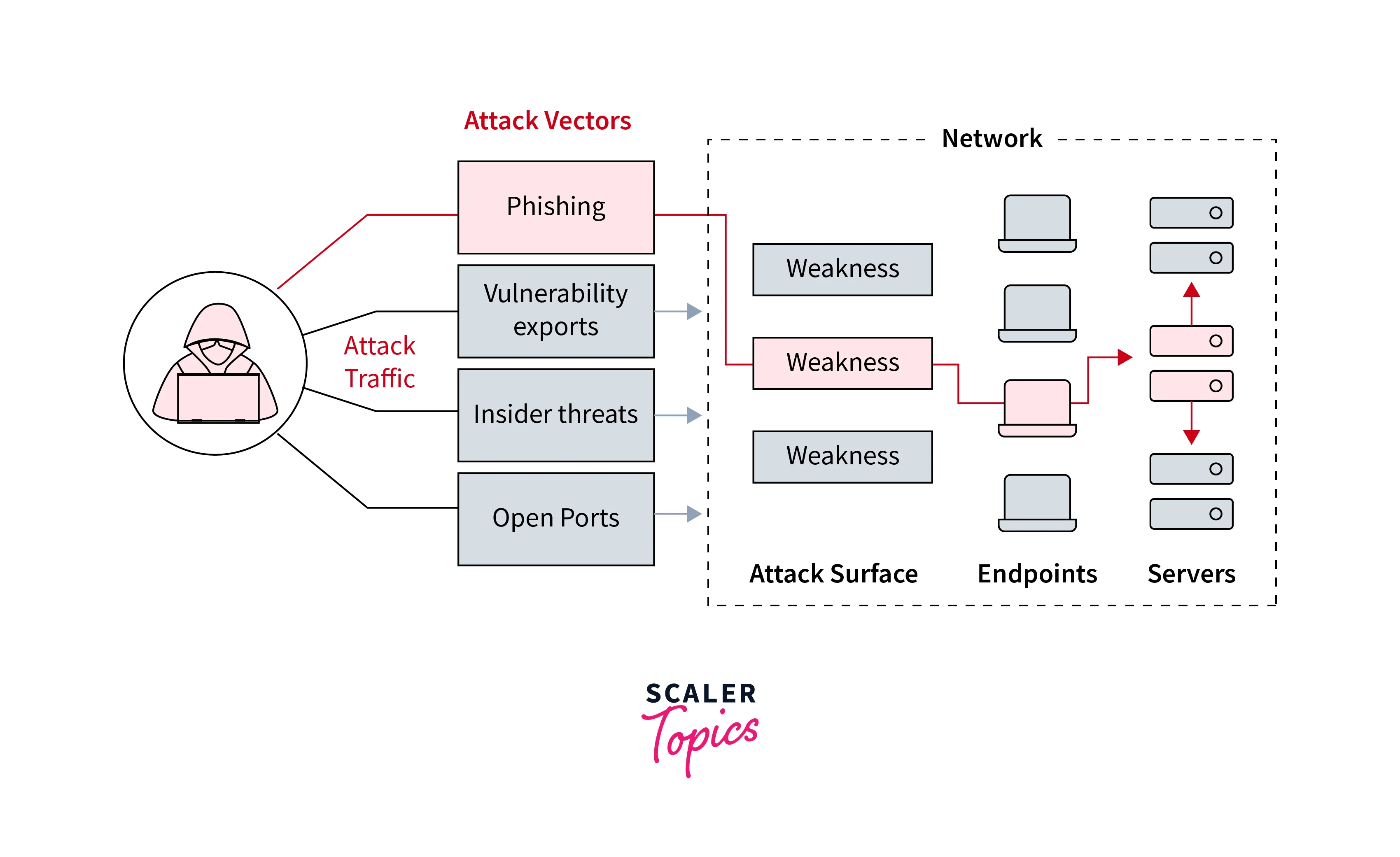
An attack vector is essentially the method or means by which a cyber attacker gains access to a system or network. It is a pathway through which an intruder exploits a vulnerability to compromise security. Attack vectors are diverse and can range from software vulnerabilities to human errors. Understanding these vectors is crucial for effective cybersecurity.
Some Most Common Attack Vectors
Attack vectors can be categorized into several types, each with its own characteristics and mechanisms. Here are some of the most common attack vectors:
-
Phishing Attacks: Phishing attacks involve sending deceptive emails, messages, or websites that appear legitimate to trick users into revealing sensitive information, such as login credentials or personal data. These attacks can exploit human error or lack of awareness.
-
Malware: Malware, short for malicious software, encompasses various types like viruses, worms, Trojans, and ransomware. Attackers use these programs to gain unauthorized access, steal data, or cause damage to systems.
-
Brute Force Attacks: In brute force attacks, attackers systematically attempt different combinations of usernames and passwords until they find the correct credentials to access a system or account.
-
Social Engineering: Social engineering attacks manipulate human psychology to deceive individuals into divulging confidential information. Techniques include pretexting, baiting, and tailgating.
-
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: DoS attacks overload a system's resources, rendering it unavailable. DDoS attacks amplify this by using multiple compromised devices to flood the target system, making it impossible for legitimate users to access.
-
Ransomware: Ransomware attacks involve encrypting data and demanding a ransom for decryption. Attackers often exploit phishing or software vulnerabilities. Proper backups, system updates, and user training are essential for protection.
-
Misconfigured Systems: Misconfigured systems result from unintended or incorrect settings, creating vulnerabilities for attackers. Regular security audits and automated tools help detect and mitigate misconfigurations.
-
Unpatched Systems: Unpatched systems have not received security updates, making them vulnerable to known vulnerabilities. Robust patch management processes are crucial for keeping systems up-to-date and secure.
-
Compromised Credentials: Compromised credentials give attackers legitimate access to systems and data. Strong password policies, multi-factor authentication, and user account monitoring are essential for protection.
-
Phishing: Phishing attacks not only exploit human psychology but also serve as an attack surface. Compromised accounts from phishing can lead to further exploitation. Security awareness training, email filtering, and user vigilance are critical to reducing this attack surface.
What Is An Attack Surface?
An attack surface refers to the sum of all potential points of vulnerability in a system, network, or application. It represents the exposure or risk that an organization faces concerning unauthorized access, data breaches, and other cyber threats. By understanding the attack surface, organizations can better protect themselves by reducing the number of potential entry points for attackers.
Some Most Common Attack Surfaces
-
Network Perimeter: The traditional network perimeter, traditionally defended by firewalls, has evolved and expanded significantly in recent years. This expansion is primarily driven by the rise of remote work and the widespread adoption of cloud services. In the past, organizations primarily focused on securing their internal networks from external threats. However, the modern business landscape has extended this perimeter to include external-facing servers, network devices, and gateways.
-
Web Applications: Websites and web applications are often exposed to the internet, making them prime targets for attackers. Vulnerabilities in these applications can lead to data breaches and unauthorized access.
-
Endpoints: Endpoints, including laptops, desktops, and mobile devices, are common entry points for attackers. Security vulnerabilities in these devices can result in data theft or system compromise.
-
Third-Party Services: Many organizations rely on third-party services, which can introduce security risks if they have access to an organization's data or network. Integration with third parties must be carefully managed to minimize risks.
-
Cloud Services: Cloud computing has become an essential part of many organizations' infrastructures. Attack surfaces in the cloud include cloud instances, storage, and management interfaces.
-
Human Factor: Employees, contractors, and partners can inadvertently create attack surfaces by falling victim to social engineering attacks, misconfiguring systems, or mishandling sensitive information.
-
Physical Access Points: Physical access points like data centers and server rooms can be exploited by unauthorized individuals. Proper security measures, including access controls and employee training, are vital for securing these areas.
-
Insider Threats: Malicious insiders or unintentional employee errors can create a substantial attack surface. User behavior monitoring, stringent access controls, and training are essential to mitigate this threat.
-
Mobile Devices: The use of mobile devices for work introduces a new attack surface. Attackers target mobile devices with malware and phishing. Mobile device management (MDM), encryption, and security policies help reduce these risks.
-
Internet of Things (IoT) Devices: IoT devices often lack robust security, making them vulnerable to compromise. Segmenting IoT devices and applying security updates are crucial to minimize this attack surface.
Difference Between Attack Vector And Attack Surface
| Aspect | Attack Vector | Attack Surface |
|---|---|---|
| Definition | The method or means by which an attacker gains access to a system or network. | The sum of all potential points of vulnerability in a system, network, or application. |
| Nature | It is the pathway used by an attacker to exploit a vulnerability in the system. | It is the overall exposure or risk an organization faces concerning unauthorized access and cyber threats. |
| Examples | Phishing, malware, exploiting software vulnerabilities, brute force attacks, social engineering | Network perimeter, web applications, endpoints, third-party services, cloud services, human factors. |
| Focus | Focused on the specific method of intrusion. | Focused on identifying and reducing potential entry points or risks. |
Security Against Attack Vectors And Attack Surfaces
Security against both attack vectors and attack surfaces is essential in building a robust cybersecurity strategy, especially within the framework of a zero-trust security model. Here are some key considerations for protecting against these threats:
-
Zero Trust Principles: Implement the zero trust security model, which assumes that no entity, whether inside or outside the network, can be trusted by default. Zero trust enforces strict identity verification, access controls, and monitoring of all network traffic.
-
Regular Patching and Updates: Keep software, applications, and systems up-to-date to mitigate vulnerabilities. Attackers often exploit known weaknesses that have not been patched.
-
User Training and Awareness: Educate employees and users about the dangers of social engineering and phishing attacks. A well-informed workforce is less likely to fall victim to such attacks.
-
Endpoint Security: Employ strong endpoint security solutions that include antivirus, intrusion detection, and monitoring to protect against malware and other threats.
-
Web Application Security: Implement secure coding practices and use web application firewalls to defend against web application attacks. Regular security testing and code reviews are essential.
-
Network Security: Secure the network perimeter with firewalls, intrusion detection systems, and intrusion prevention systems. Segment networks to limit lateral movement for attackers.
-
Cloud Security: Embrace cloud security best practices, including proper configuration, access control, and monitoring in cloud environments.
-
Third-Party Risk Management: Assess and manage the security of third-party services and vendors. Ensure they follow the same security standards as your organization.
-
Incident Response Planning: Develop a comprehensive incident response plan to react swiftly to security breaches. Regularly test the plan to ensure readiness.
-
Continuous Monitoring: Continuously monitor network traffic and system logs for anomalies and potential threats. Early detection can prevent attacks from escalating.
Conclusion
- In a world where cyber threats are constantly evolving, a proactive and layered security approach is essential.
- Understanding the concepts of attack vectors and attack surfaces is crucial for organizations looking to implement a zero-trust security model effectively.
- Attack vectors represent the various means by which attackers gain access to systems and networks.
- They can be as simple as a phishing email or as sophisticated as exploiting software vulnerabilities.
- Mitigating these vectors requires a combination of user education, secure coding practices, and robust security solutions.
- Attack surfaces encompass all the potential vulnerabilities and entry points within an organization's infrastructure.
