Ping, TCP, UDP, Three-Way Handshake (What are these and how do they work)
Overview
Network protocols play a significant role in providing security for both data at rest and in transit. All the network protocols follow the TCP/IP model. The TCP, UDP, HTTPS, FTP, etc., are well-known protocols that help in transmitting & receiving data securely across the globe. Also, concepts like ping & three-way handshakes play a critical role in networking, data transmission, and security. In this article, we will learn about what is ping, TCP, UDP, three-way handshake, etc.
What is Ping in Cybersecurity?
Ping or Packet Internet Groper is an internet program and a method that determines the communication latency or verifies a particular IP by sending a request packet. Using this program, the users can specify the time required for data traversal from one network point to another.
The ping method also helps diagnose whether the host computer or the user can reach the destination or whether the host computer is operating appropriately or not.
In cybersecurity, hackers also use this ping method to check whether they are getting a response back from the host or not. If they get a response, it determines that the host whom the hacker has pinged is live. Some well-known ping-based attacks are:
-
Ping flood: Ping flood is a simple denial of service-like attack where the attacker tries to flood the victim's network system with multiple pings or ICMP echo requests. The attackers understand the network's capability to respond & accordingly send more ping requests. The network usually tries to reply with an equal number of reply packets. It tires the network's outgoing and incoming support by consuming unnecessary bandwidth.
-
Ping of Death (PoD): It is a type of cyber attack where the attacker tries to ping multiple times to crash, freeze, or destabilize the victim's system. They use the ping program to customize oversized packets and send them to the victim through simple ping command. PoD attacks often target conventional weaknesses that are still relevant and vulnerable in some ways. We call it ping of death because the attacker's motive is to stop or crash the functionality of the network or system to end (as the system ceases to work). Now, that we have understood what is Ping, let's understand it with a real-world example.
Relating Ping with a Real-World Example
We can use the ping command to utilize the ping program and its methods to check whether the host computer is live or not. Open up the command prompt and type in the "ping" or "ping /?" command.
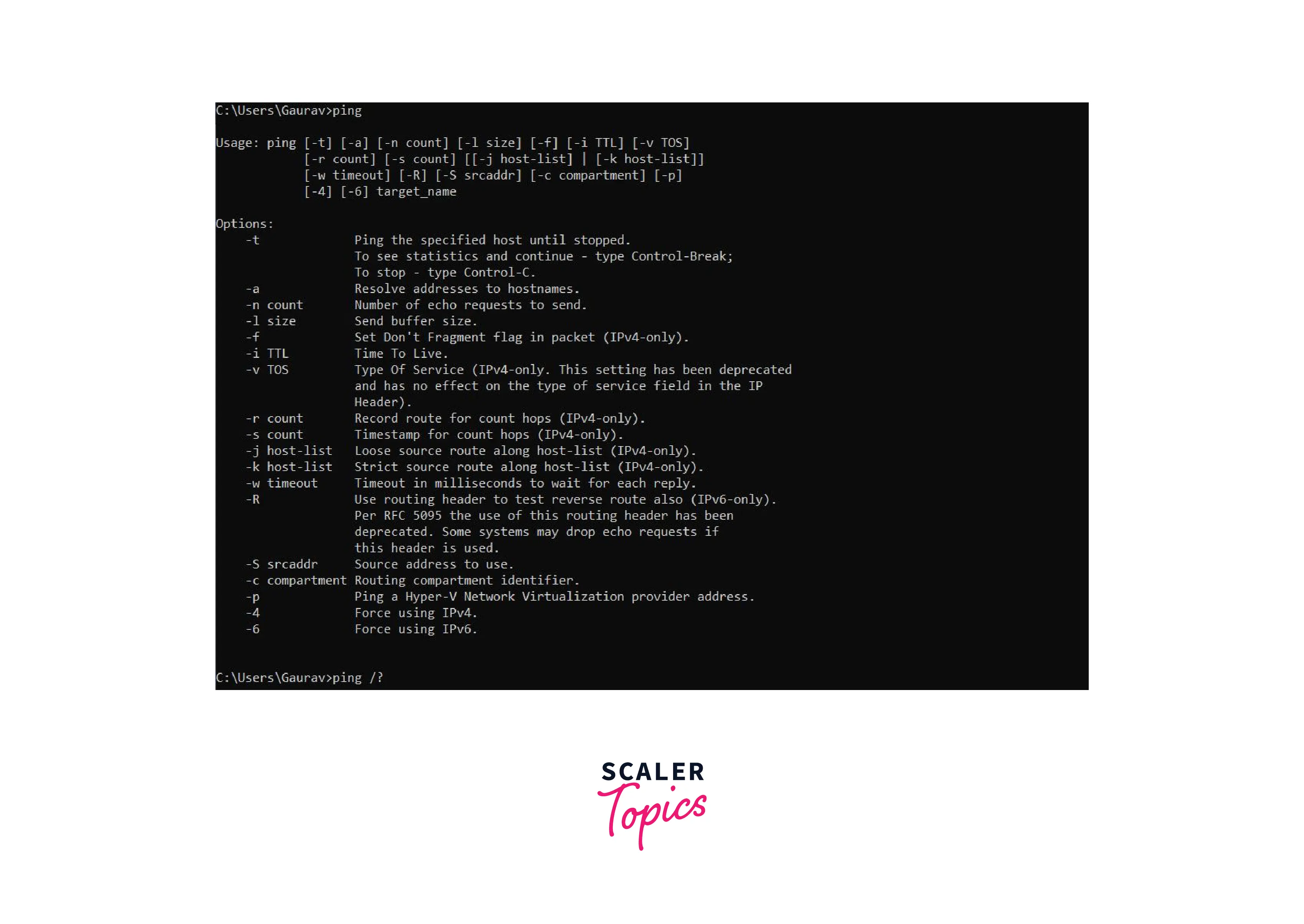
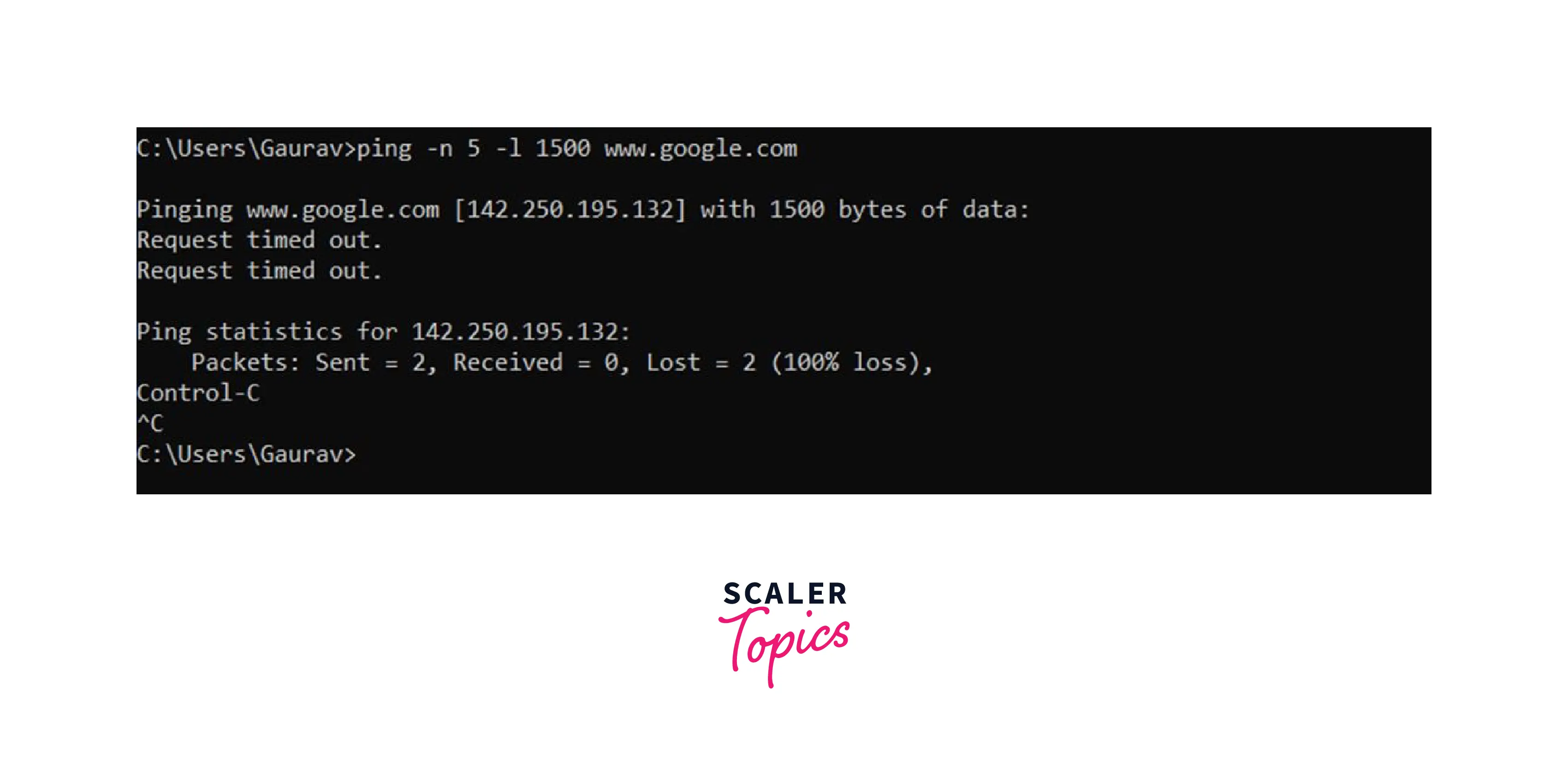
It will list all the options and attributes one can use with the ping command. We can also use the ping technique to ping various websites and domains. Here is an example:
ping -n 5 -l 1500 www.google.com or ping www.google.com
What is the ICMP Protocol?
Every layer of the OSI model uses different protocols to perform distinct tasks. The Internet Control Message Protocol (ICMP) is a network layer protocol that performs diagnostics on network communication issues. The ping service uses this protocol to send echo requests to get a response from the destination IP address that it pings.
The ICMP protocols also determine whether the data packets go to the correct destination at the right time or not. As soon as the network receives an ICMP echo request, it tries to respond with an ICMP echo reply immediately to show its presence. ICMP is useful when the data packet is too large and dropped by the router.
At that moment, the router will send an ICMP packet with a message to the source system for the data. Apart from this functionality, we can leverage the ICMP protocol to perform multiple pings and utilities like traceroute in networking. The ping, as discussed above, will verify the existence of a particular IP address. The traceroute utility will list all the routing paths or hops between two internet devices (source and destination).
Know more about ICMP protocol in this guide here.
What are TCP, UDP, and Three-Way Handshake?
TCP and UDP protocols alongside the three-way handshake are the foundational protocols working in the background of all network transmissions. Let's learn in detail about what each of them is and how they are necessary for network communication.
TCP:
Transmission Control Protocol (TCP) is a standard communication protocol defined by the Internet Engineering Task Force (IETF). It is one of the primary protocols of the Transmission Control Protocol/Internet Protocol (TCP/IP) suite. The TCP protocol works between the network layer and the application layer. The Transmission Control Protocol (TCP) works with the Internet Protocol (IP) to determine how different systems within the network can send and receive packets. It is a reliable and connection-oriented protocol. The TCP performs the following tasks:
- Decides how to break the data packets into several parts to deliver them over the network
- Send and receive data packets over the network layer
- Manages transmission flow control
- Managing of retransmission of data packets that are lost or garbled
- Checks for error-free data transmission
- Acknowledge data packets that receive
To learn more about the Transmission Control Protocol (TCP), check out this guide.
UDP:
User Datagram Protocol (UDP) is another popular communication protocol that works as a part of the Internet Protocol suite. Unlike TCP, it is not reliable and is a connectionless protocol. Applications that want to transmit data or set connections in low latency with loss-tolerating support prefer UDP. Also, in case of time-sensitive data transmission situations like DNS transmission or video playback, the UDP speeds up the communications by not establishing a link before transferring the data. Some key characteristics of UDP are:
- It is a stateless protocol. There is no acknowledgment of mechanisms associated with the UDP.
- Data transmission is fast.
- Each UDP segment gets handled independently. Thus, each segment takes a different route to transmit the data packets and reach the destination.
- UDP gets preferred where latency is a concern.
- Applications where real-time error correction is not required or any app serving a massive client base can prefer UDP over TCP.
To learn more about the User Datagram Protocol, check out this guide.
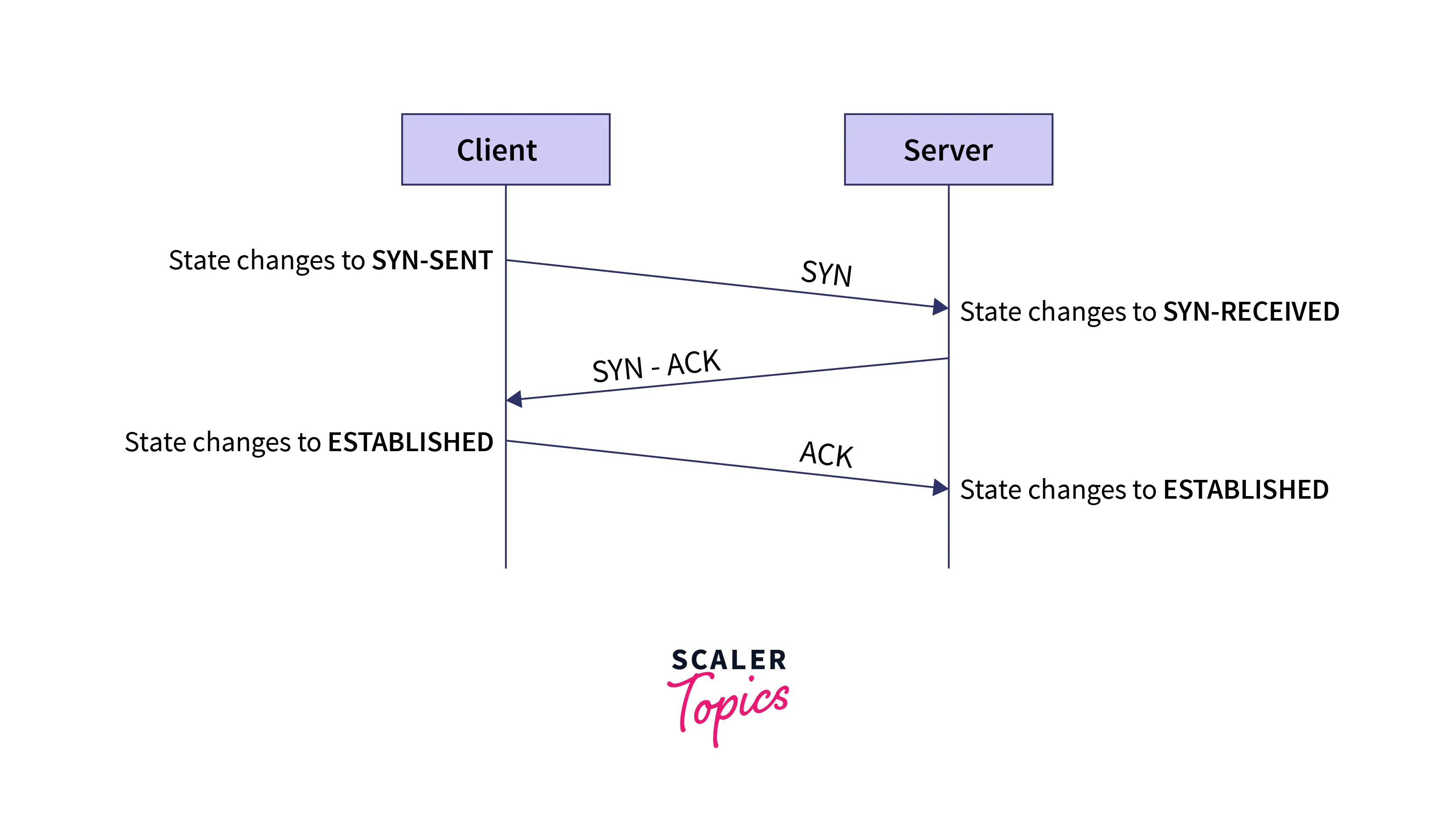
The Three-way handshake:
All TCP/IP network communication uses the three-way handshake process to establish a proper connection between the local client and the server. It is a three-step process requiring both the client and the server to synchronize and exchange acknowledgment data packets before actually transmitting the data.
A three-way handshake is also known as a TCP handshake or SYN-SYN-ACK because its design allows us to initiate, arrange, and separate TCP socket connections for simultaneous use. This method permits us to transfer data through multiple TCP socket connections in either direction concurrently. Attackers often use this technique to ping and wait for a response. If the response arrives from particular TCP sockets, it means the port is live, and if that port has any vulnerability, attackers can use it to exploit a system.
To learn more about the three-way handshake, check out this guide.
Conclusion
- In this article, we have gathered insight into the ping method and how hackers use it for ping flood and ping of death (PoD) attacks.
- Then we explore real-life pinging by using the ping command to ping google.com.
- Next, we encountered the ICMP protocol and situations where we employ ICMP protocol.
- Lastly, we discussed what TCP and UDP protocols are and what a three-way handshake is.
