What Is Data Encryption?
Overview
Data encryption is converting simple plaintext, which is humanly readable, into cipher text. This way, the data is now coded in a non-human readable format. Even if this data is exposed to any potential threat or exposed to malicious activities, the fraud needs first to decrypt it, and then only could this data be completely exposed. It is often seen that decoding or decrypting the text is possible by authorized users.
Introduction
Vast amounts of data containing sensitive information are precisely handled, managed, and carefully stored online these days, either in the cloud or over other connected servers. It is only possible for businesses to conduct or users to work with the involvement of their sensitive data transmitted and stored by the various similar networked computer systems across organizations.
With digitalization and data migrating towards the cloud comes the threat of the risk of the exposure of sensitive data to fraudsters. Data encryption algorithms offer a unique and secure way to protect this sensitive data. With data encryption, the plaintext (often the user's sensitive data like email, address, blood group, etc.) is encrypted or written in language that is scrambled to allow only the correct and authorized user to view that information. This not only offers data security to the users who have their personal information stored in the cloud but also offer users to seamlessly and securely send, receive, and store data on a mobile, such as one connected to the IoT.
Individuals and organizations are leveraging data encryption security and the technologies around it to protect their user information thatis being sent to and fro between the server and browser. This information includes all from personal information to payment details. Data encryption software, widely popular as the cipher or the data encryption algorithm, is being implemented for developing the encryption scheme which theoretically breaks the data with large amounts of computing power.
What is Encryption?
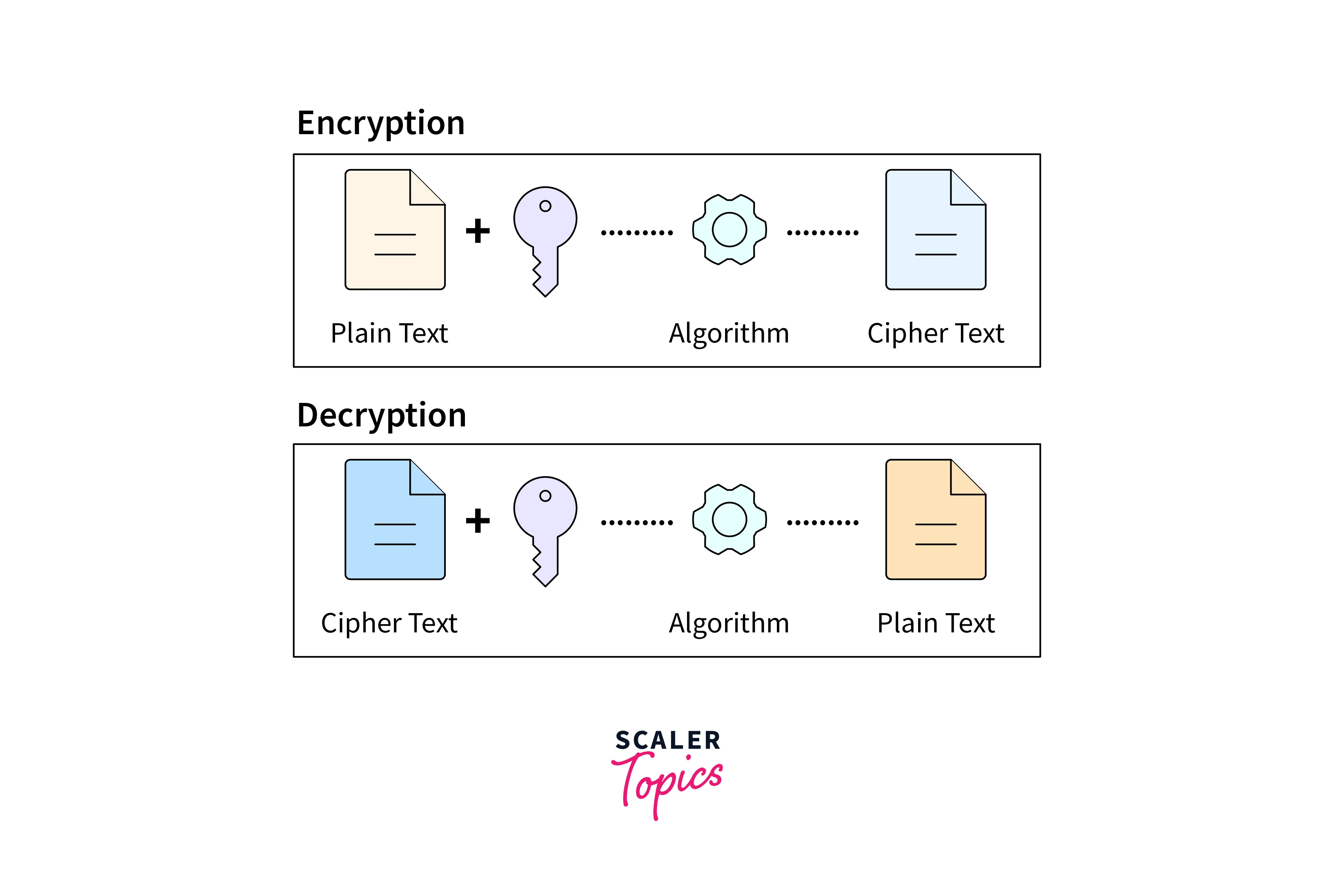
We can define encryption as the process of converting the data from its human-readable format into the encoded ciphered format. Users can only read the encrypted data once they are fully authorized to decrypt it and get the human-readable formatted data out of it. Encryption is considered to be the basic building block of data and cyber security. Data encryption is the simplest and most important way that makes sure that a computer system's information is not stolen or read by others who want to only jeopardize the security for malicious activities.
Encrypted data is often scrambled and unreadable without permission until the user accessing sensitive information is appropriately authorized to decrypt. Encryption prevents the data from being stolen or misused, as the hacker cannot fetch it in plaintext format. This encrypted and encoded ciphertext is used to protect sensitive information from being leaked and exposed even if it comes in contact with a potential threat. The data needs to be decrypted where the decryption key is considered the secret to protect the data from being secure against unauthorized access. The data is stored in a safe and protected system, where it gets encrypted before sending, offering safety, while the other sanctioned misapplication is not showing the same level of protection.
Protecting your Data
As data increases, the risk associated with exposure to it also increases. Protect the data. Various techniques and technologies are available these days. But the most common and convenient way of protecting your data is by encrypting the data. Data encryption is converting the simple plaintext, which is human-readable, into a cipher text. This way, the data is now coded in a non-human readable format. Even if this data is exposed to any potential threat or exposed to malicious activities, the fraud needs first to decrypt it, and then only could this data be completely exposed. The Data Encryption process includes preserving crucial customer data and offers confidentiality by transforming the data as encoded ciphertext. This ciphertext could only be decoded via the distinct decryption key produced only at the time of encrypting the data with authorized access or before this process.
It is often seen that decoding or decrypting the text is possible by authorized users. But this doesn't mean that technology can decrypt the text. With data encryption, users can deter any malicious or negligent bodies from accessing their private and sensitive data. The use of intercepted data in the data encryption process is what makes it even more challenging to expose sensitive data. Therefore, it is considered a crucial way of defense in the field of cybersecurity. The data encryption algorithms, also known as Data encryption software, are implemented to develop the encryption scheme, which theoretically could only get broken when vast amounts of computing power are utilized. It's also seen that data integrity is maintained with encryption, and almost everything on the internet needs to be encrypted at some stage.
Data encryption holds its application in various industries such as finance, data protection in classified government intel, individual personal credit card, or online transactions. Data encryption finds its usage during data storage or transmission. It is implemented with other authentication services, ensuring that the keys are only offered to or utilized by authorized users. Data that gets encrypted is often referred to as ciphertext, while the one that is not encrypted is called plaintext.
Why is data encryption so important?
As data becomes more accessible, available, and desirable to attackers, protecting it becomes more and more crucial. Organizations need to protect their customer's data and face data protection regulation requirements that typically require the implementation of data encryption. All the standard infrastructures considered to be watching the data, still the possibility of the data getting exposed must be regarded as. There also is the chance of data exposure and compromise, but by encrypting the data, your data is still protected at some level and offers security.
Along with enhanced security, data encryption offers protection of privacy, protection of data integrity, along with preventing unauthorized access to anyone and everyone. Furthermore, data encryption unwanted or misleading modifications to the data are also contained and help the data hold its origin and authenticity.
Types of data encryption: asymmetric vs. symmetric
Data encryption is a way of protecting your meaningful data. This can be done in two different ways, either with an asymmetric key or with a symmetric key mentioned below.
- Symmetric Data Encryption
- Asymmetric Data Encryption
Let us dive deep to learn about both.
Asymmetric Encryption Methods
With the asymmetric encryption methods via the help of the asymmetric encryption keys, two different keys are utilized that are private and public. These keys are mathematically linked together. The keys are asymmetric as these keys are essentially large numbers paired together and are not even identical. Hence, they are known as asymmetric encryption keys. Here, the owner owns the private key, while the different public keys can either be shared among the other authorized recipients or made available for the larger public. With the help of cryptography methods, the keys are employed for data encryption as well as for decryption of data. And in this way, the keys would not be easily accessed by the public as they won't be unable to read or decode them. Popularly, this is known as the "public-key" encryption majorly implemented for internet security protocols. The word "asymmetric encryption" describes this encryption type.
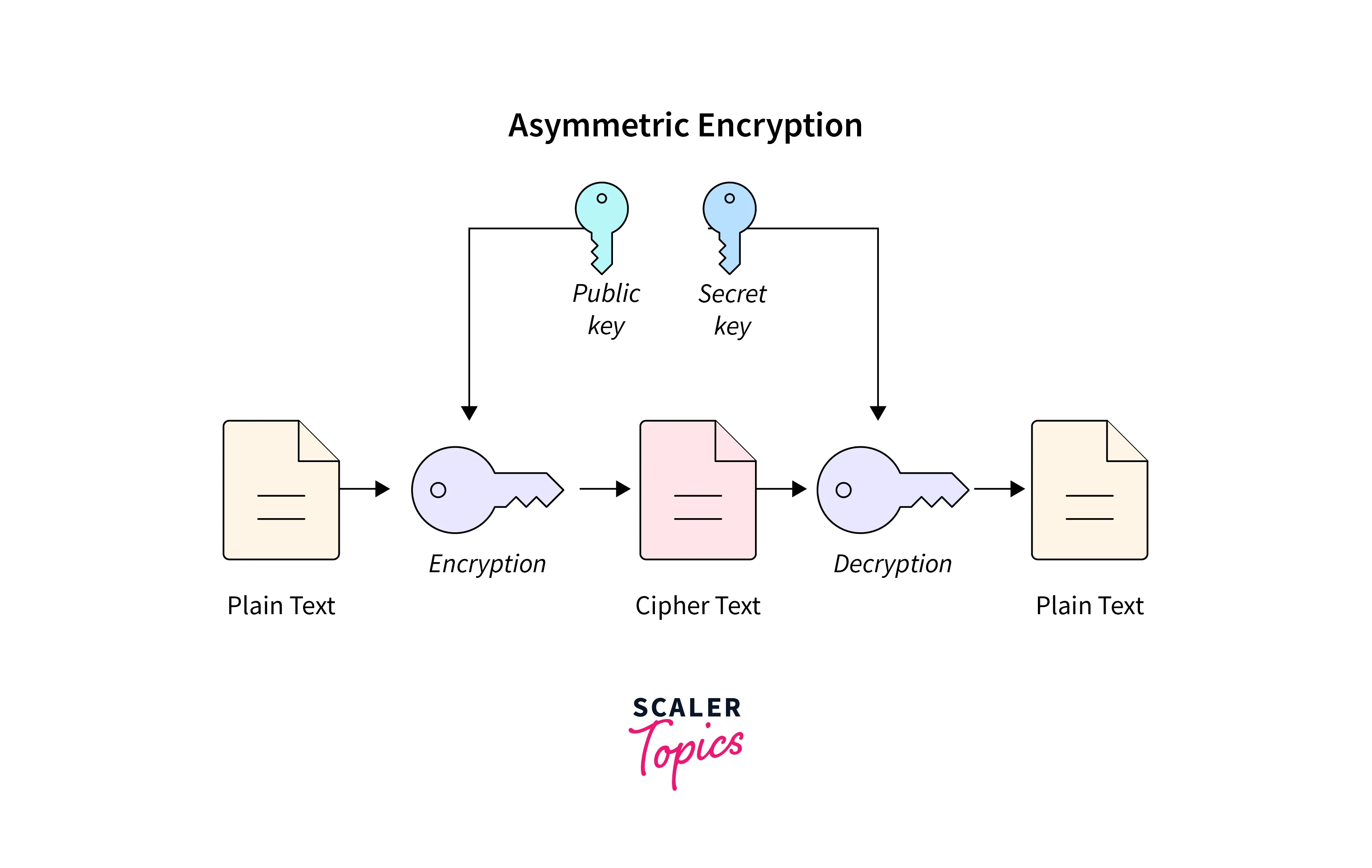
Symmetric Encryption Methods
The symmetric encryption method, via the help of symmetric encryption keys, is what is known as private key encryption. The symmetric encryption key is utilized for encoding the same key used to decode. This makes it a perfect set of keys for individual users and highly closed systems. In other cases, the keys must be sent separately to the receiver. This opens up potential risks, too, if the key gets compromised. This interception could be via any third party, like a hacker. It is seen that symmetric data encryption is much faster compared to the asymmetric method. More strategies should be implemented in the cryptography algorithms, for the data encryption and decryption processes. This process implements the algorithms that involve the processing of the unique key. The unique key is kept secure as it could only be exposed to the system or person validated by completing the authentication for decoding the message to read the key. This entire approach is called "symmetric data encryption" in the network encryption field.

Benefits of Data Encryption
With this section of the article, we should highlight the critical benefits of data encryption.
As more organizations are moving towards digitizing their process and systems to hybrid or multi-cloud environments, there has been much talk about public cloud security. Protecting the data here is critical for integrity, as customer trust could not be risked.
Various cloud service providers (CSPs) are learning and adapting ways by which they can offer protection for the data being stored in the cloud and are yet responsible for providing the security of the cloud. But it's the customers' responsibility for safety in the cloud, precisely when data security is concerned.
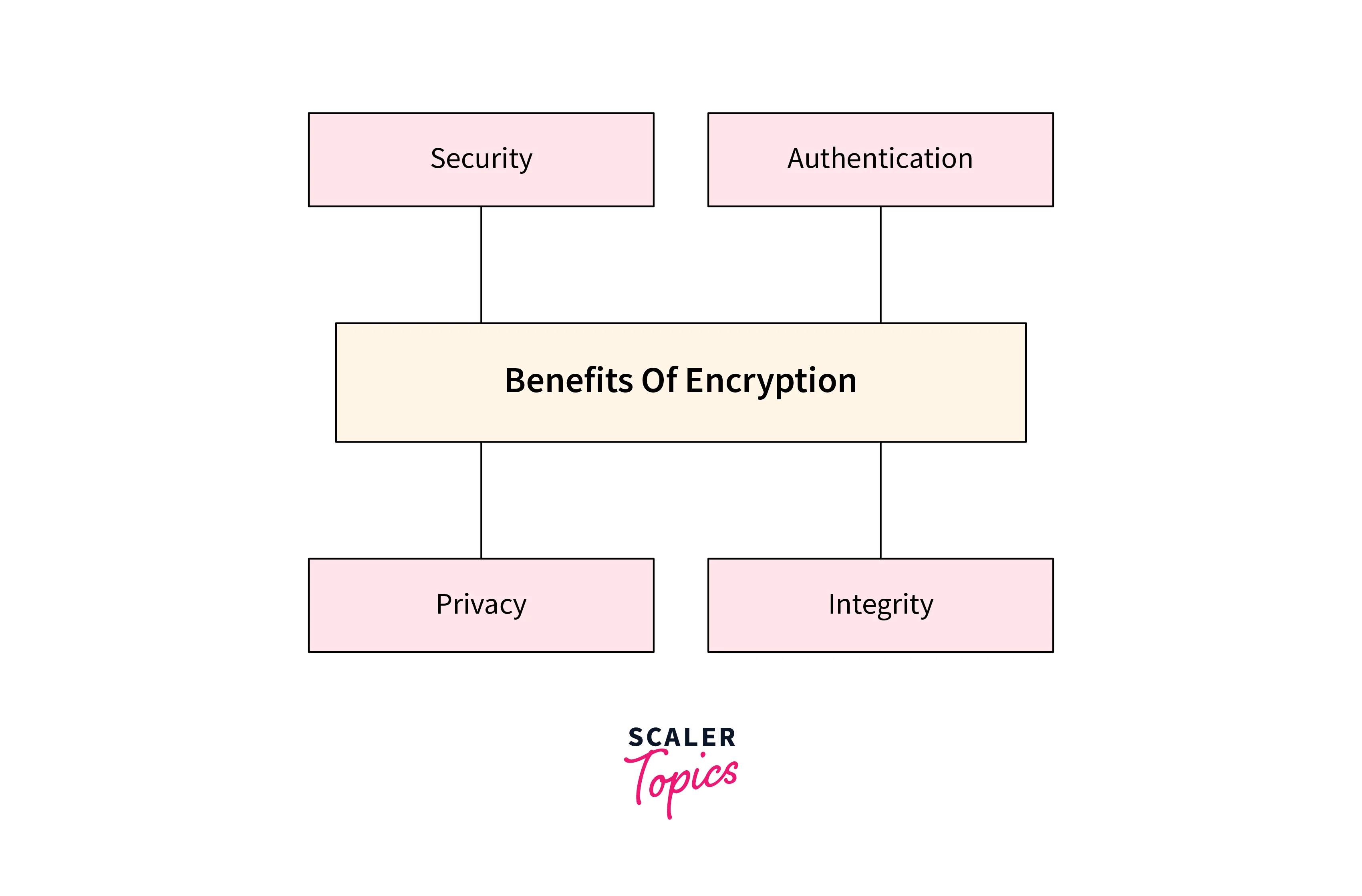
Prominent robust data encryption must offer the following prime benefits to its users and shall also provide the critical management solutions as stated below:
- Data integrity is supported by encrypting the data. It is often seen that various business initiatives are compromised due to poor data quality. Data integrity is of utmost importance for any business to support and call for smarter decisions against threats and data corruption.
- For on-premise and cloud data encryption keys, the lifecycle process must be automated.
- A self-contained fully centralized management console to offer utmost data encryption intact with the other data encryption key policies as well as configurations.
- For help with compliance, the role along with group-based access controls together with the audit logging must be adhered to.
- Data encryption offers trust and gives a competitive edge to the organization over others. For people who protect sensitive data, along with those who are trusting for their data, data encryption provides reliable security.
- The intellectual property must follow data encryption. The data at rest must adhere to the digital rights management systems for data encryption. The intellectual property must be protected and avoid any reverse engineering or unauthorized usage of the already copyrighted material.
- For on-premise and cloud-based data, encryption must be provided at the file, database, and application levels.
- Various devices could be utilized for following the data encryption tools as well as technologies enabling policies such as working from home and giving more power to e-commerce.
Data Encryption Solutions
Protecting the data, be it at rest or while the critical data is in transit, is crucial for any organization dealing with millions of records of customer data. Various data encryption solutions are widely available. Ranging from data encryption software to cloud-based data encryption models are popular and implemented based on whether the data that needs to be protected is generally data at rest or in transit.
Understanding data at rest is crucial to information that is not actively transmitting from one device to another or even not moving from one network to another. These kinds of data are generally stored on a hard drive, flash drive, or laptop or sometimes even archived distinctly. As the data is under specific hardware, having the device's own set of security features helps to restrict unusual access and hence is much safer and less vulnerable. It doesn't mean it can't be stolen or misused. It's seen that data at rest generally contains more valuable data, which makes it even more appealing as a target for fraudsters.
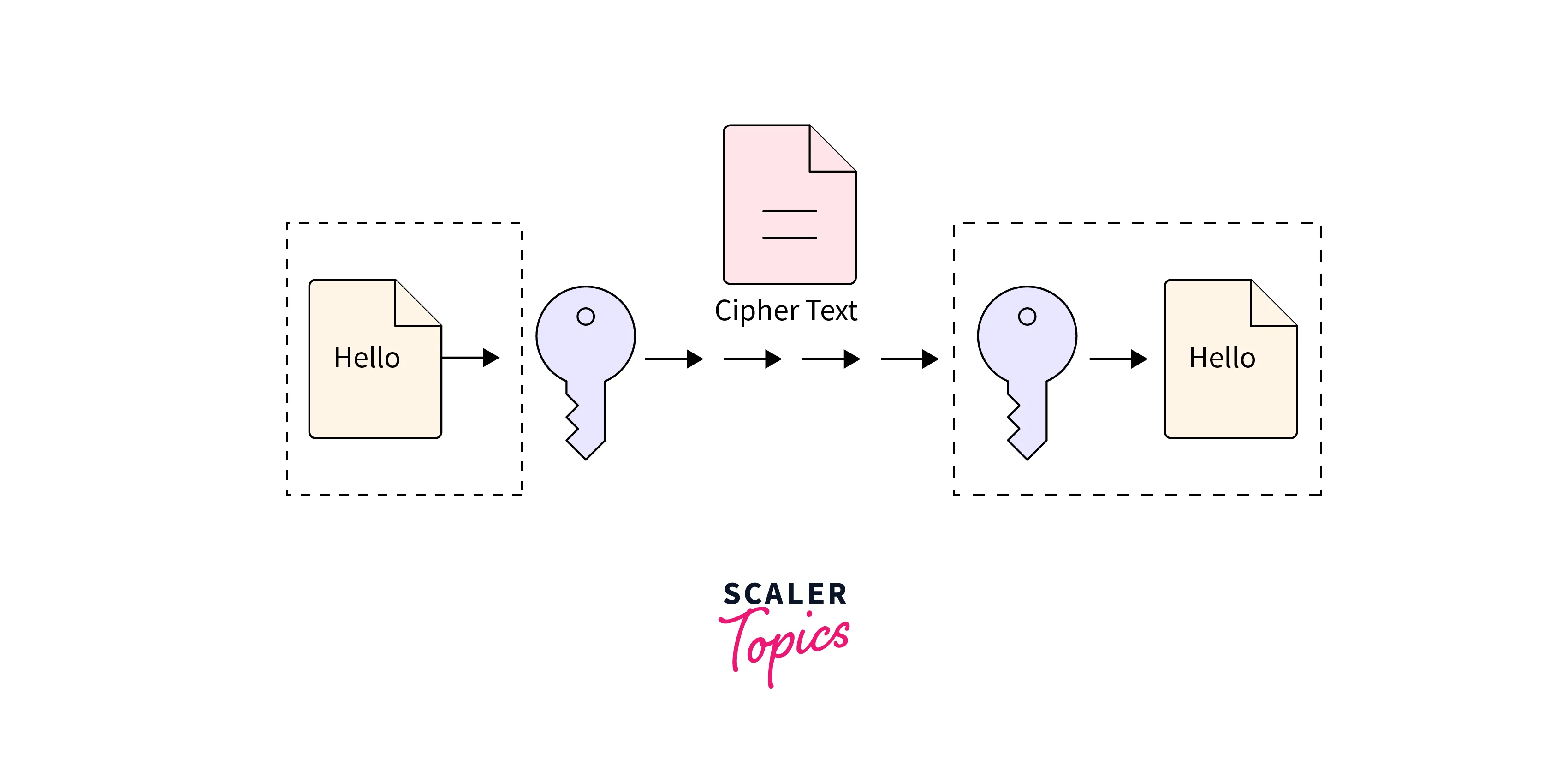
While data in transit is defined as data being carried over and currently in the migration phase from one point to another, this transit can be over a private network or the internet. While the data is in transit, it is highly vulnerable to attack and data leaks. This arises from the weaknesses seen in data transfer techniques in the transition mode. However, with end-to-end encryption techniques, the data is encrypted while in the transmission phase, which offers relief and lets the data remain private even if on the verge of interception.
While data encryption sitting at rest is less risky for any kind of data theft like stolen devices or getting lost, unintentional sharing of passwords, or accidental granting of permission by randomly increasing the time for accessing the crucial information along with offering the time required to discover ransomware attacks, data loss, remotely erasing of specific data, or even change of credentials, by preventing data loss along with data protection, data encryption helps to tackle the increased business challenges like employees using removable media or any external pen drives, website applications. When such a thing happens, the business usually loses control over crucial data.
Hence, data encryption solutions are not only essential but a critical component for best data loss prevention. Moreover, it helps prevent hackers from ingesting any malware or stealing cloud data, web applications, and external or removable devices.
It's also essential to capture the fact that protecting the data is also to ensure it is not misused, even if it mistakenly falls into the wrong hands. Hence, a data encryption solution is crucial.
- Data at rest could be configured to enable the applications that access the data stored can decrypt it.
- While the data in transit are more troublesome from an admin perspective, it is critical to make sure both the data encryption and decryption abilities are for both senders and recipients.
We define a data encryption solution as the critical software system employing the algorithms for data encryption that shall eventually protect the sensitive data, integrated with other management tools for monitoring and deploying the data encryption across the company. With the help of data encryption solutions, users get tools helping them with crucial management where the keys, passwords, and other data needed to encrypt the data access are available to authorized users. Depending on the specific policies, these could be modified (revoked, changed). Various other technologies that organizations have adopted along with the other traditional security products are prevention against any intrusion, firewalls, and role-based access control systems, which in turn help avoid data breaches.
Hence, when the fraud attackers successfully breach the network, the data encryption software inevitably provides the last defense against the exposure and theft of sensitive data. Organizations can implement data encryption tools and various government and industry regulations, like protecting the consumer's privacy and financial data. Also, the specific stiff penalty is an integral part of non-compliance. Data encryption is a vital way of producing data encryption that protects the organization, if any, such as a data breach or a laptop stolen.
Conclusion
- The asymmetric encryption methods via the help of the asymmetric encryption keys, two different keys are utilized that are private and public. These keys are mathematically linked together.
- Data encryption algorithms offer a unique and secure way to protect this sensitive data. With data encryption, the plaintext (often the user's sensitive data like email, address, blood group, etc.) is encrypted or written in language that is scrambled to allow only the correct and authorized user to view that information.
- Data encryption offers trust and gives a competitive edge to the organization over others. For people who protect sensitive data, along with those who are trusting for their data, data encryption provides reliable security.
- The symmetric encryption method, via the help of symmetric encryption keys, is what is known as private key encryption. The symmetric encryption key is utilized for encoding the same key used to decode.
- Encrypted data is often scrambled and unreadable without permission until the user accessing sensitive information is appropriately authorized to decrypt.
