Devops Security
DevOps security, an amalgamation of development, operations, and security principles, aims to dissolve barriers between software development and IT operations. In the pursuit of faster software delivery, DevOps advocates continuous deployment, allowing development teams to release feature enhancements and bug fixes without disrupting user experiences. Despite these benefits, security concerns arise as developers leverage third-party code, which may harbor vulnerabilities. The collaborative essence of DevOps fosters closer working relationships between developers and IT teams, resulting in software releases with reduced errors. The evolution of this philosophy, exemplified by DevSecOps, integrates security seamlessly into the software development lifecycle. DevOps methodologies, emphasizing automated and incremental updates, facilitate efficient software delivery, often employing microservices within containers and running in diverse cloud environments. While DevOps processes and containerization enhance business outcomes, they introduce challenges to application security. DevSecOps addresses these complexities by ingraining security measures at every phase of the software development lifecycle, ensuring protection across the dynamic landscape of automated processes, microservices, and diverse cloud deployments.
DevOps Security Challenges
Despite its many advantages, DevOps introduces new risks and cultural shifts that create security challenges typically intractable by traditional security management solutions and practices. Traditional security management solutions and practices were not designed to support the rapid and automated delivery of software common in DevOps.
There are numerous DevOps security challenges, but some of the most important ones are as follows:
Cyber Attackers target privileged Credentials Used in DevOps
DevOps processes rely on privileged access to systems and tools, vulnerable to cyber attackers seeking unauthorised access. Attackers can access sensitive data, systems, and applications when privileged credentials are compromised.
Developers Are Focused on Velocity—Not Security
The DevOps culture values speed and agility, but this can compromise security. Developers may prioritise feature delivery over security testing, allowing attackers to exploit vulnerabilities.
Tool-centric Approaches to Secrets Management Create Security Gaps
DevOps teams frequently rely on automated tools for secret management, such as storing passwords, keys, and certificates in repositories or using centralised key management systems. However, these approaches can lead to unauthorised access and data breaches if not properly configured or managed.
Dev and Ops Incompatibilty
The cooperation of two distinct teams—development and operations—is necessary for DevOps. Unifying their procedures might be difficult because they are used to operating in silos. Roles and policies that are not clear might leave security weaknesses.
Cloud Security
The widespread use of cloud-first architecture has led to yet another difficulty. With ill-defined and hazy network borders, the cloud exposes a far larger attack surface than a conventional, on-premise deployment. With just a few mouse clicks or lines of code, almost any supplied resource may be set up to be reachable by public internet traffic.
Legacy Infrastructure
Many organisations continue to rely on difficult-to-secure and maintain legacy infrastructure. This can lead to attackers exploiting vulnerabilities to gain unauthorised access, steal data, or disrupt operations.
Recruiting
Finding and hiring skilled DevOps security professionals can take time for businesses. There is a high demand for these professionals and a need for more qualified candidates, resulting in increased competition and higher hiring costs. This can make it difficult for businesses to establish and maintain strong DevOps security teams.
What is DevSecOps?
DevSecOps is a method of approaching software development that prioritises security from the start. This means that instead of thinking of security as an afterthought, like putting a lock on a door after it's been built, security is built into every step of the development process.
This allows developers to identify and address potential security issues early rather than waiting until the end, when it may be more difficult and expensive. This method ensures that the software is as secure as possible, lowering the risk of future security breaches or other issues.
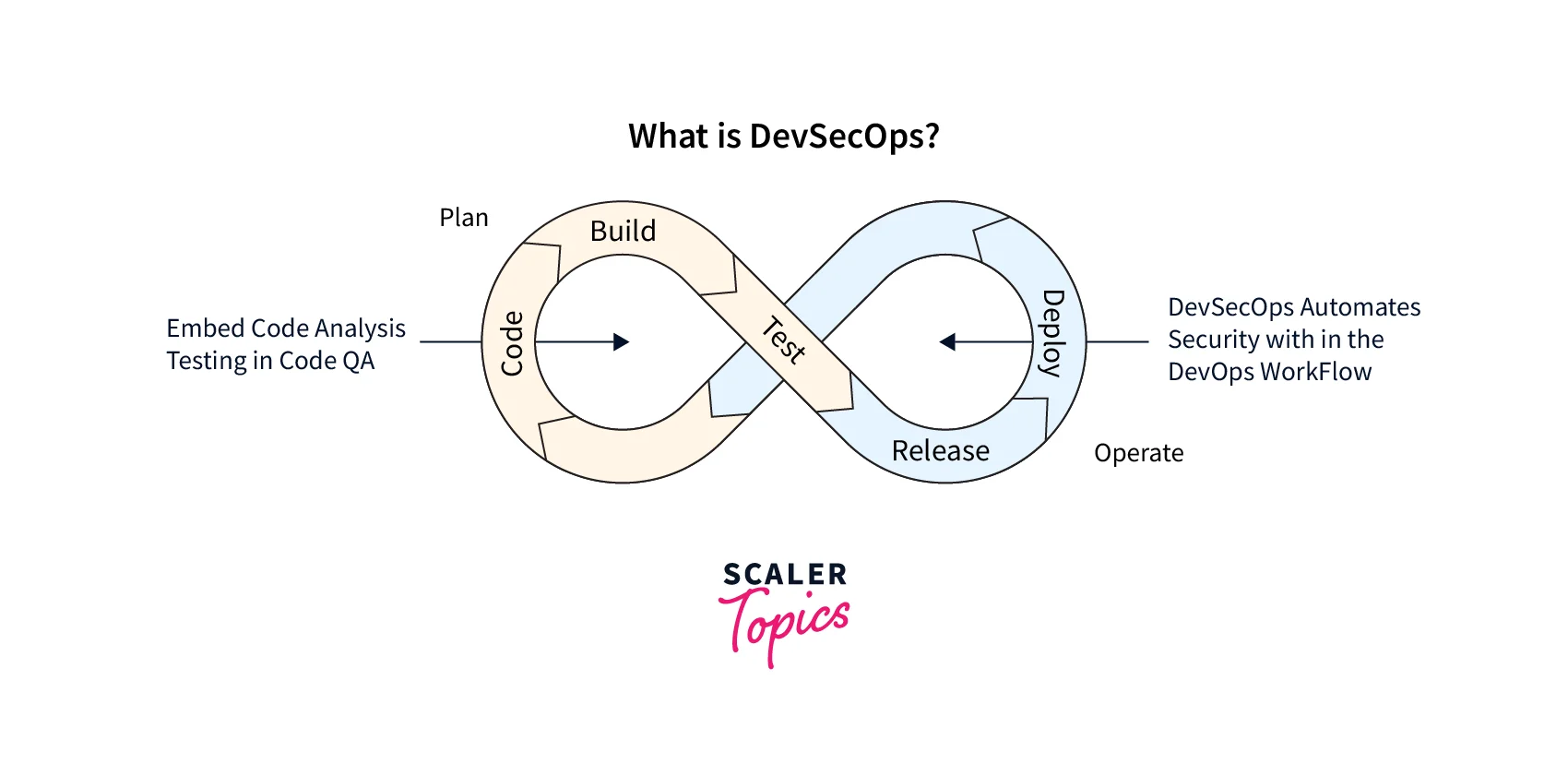
DevSecOps aims to ensure that software is secure and reliable from the start rather than addressing security issues as they arise. DevSecOps aims to reduce the likelihood of security vulnerabilities and improve software's overall security and reliability by incorporating security into the development process.
DevOps vs DevSecOps
The main distinction between DevOps and DevSecOps is that DevSecOps includes security. While DevOps focuses on team collaboration and integration, DevSecOps makes security an integral part of the development process.
Communications and Collaboration
- DevOps focuses on close collaboration between development and operations teams, emphasising breaking down silos and creating a culture of shared responsibility.
- Fostering open communication channels, forming cross-functional teams, and encouraging collaboration through shared goals and metrics are all part of this.
- DevSecOps extends this approach by involving security teams in the development process, ensuring that security is built in from the start.
Automation
- Automation is heavily used in DevOps and DevSecOps to streamline software development.
- Builds, deployments, testing, and other processes can be automated, freeing developers and operations teams to focus on higher-level tasks.
- Automation is also used in DevSecOps to enforce security policies and ensure that vulnerabilities are detected and addressed as early in the development process as possible.
Continuous Processes
- Continuous processes are emphasised in both DevOps and DevSecOps. This includes continuous integration, continuous delivery, and continuous deployment, aiming to deliver software as quickly and reliably as possible while minimising the risk of errors or failures.
- Continuous processes are achieved through the use of automation as well as a continuous improvement culture in which teams are constantly looking for ways to optimise their processes and workflows.
Here is the tabular comparison of DevOps vs DevSecOps, which briefs the differences between the two:
| DevOps | DevSecOps |
|---|---|
| Focuses on collaboration and integration between developers and operations teams | Builds on DevOps principles but with an added emphasis on security |
| Goal is to streamline the software development process and make it more efficient and reliable | Goal is to integrate security into every stage of the development process |
| Silos are broken down, and communication between teams is promoted | Security is not treated as a separate function but as an integral part of the development process |
| Continuous integration and continuous delivery (CI/CD) is a key practice | CI/CD is still a key practice, but with added security considerations |
| Automation and monitoring are important aspects | Automation and monitoring are important, with added security monitoring |
| Developers and operations teams share responsibility for quality and reliability | Developers, operations teams, and security teams share responsibility for security |
DevOps Security Best Practices
Security is a critical component of the software development process. Here are some best practices to keep in mind when incorporating security into your DevOps processes:
Embrace a DevSecOps Model
DevSecOps integrates security into the DevOps workflow, making security a team-wide responsibility. It emphasises proactive security measures over reactive ones, incorporating security into the development process.
Policy and Governance
Create security policies and governance that meet your organisation's needs, such as access control, data protection, and compliance. Ensure that everyone on the team knows and follows these policies.
Automate Your DevOps Security Processes and Tools
Automating security processes and tools can increase efficiency while decreasing the possibility of human error. Consider using automated testing tools and Continuous Integration/Continuous Deployment (CI/CD) pipelines to ensure the code is secure.
Comprehensive Discovery
Conduct a thorough discovery of all assets in your environment to identify potential security risks. This can include mapping out your network infrastructure, identifying the data types you store, and determining the location of sensitive data.
Vulnerability Management
Set up a vulnerability management process to detect and fix security flaws. This can include performing regular security assessments and penetration testing, as well as monitoring for new vulnerabilities on an ongoing basis.
Configuration Management
Implement a configuration management process to ensure that all systems and applications are securely configured. This includes tasks such as automating security configuration and enforcing configuration policies.
DevOps Secrets Management
Manage and protect secrets such as passwords, API keys, and certificates in a secure manner. Consider using a secrets management tool to ensure that secrets are properly encrypted and managed.
Privileged Access Management (PAM)
Implement PAM to control access to sensitive data and resources. Implementing multi-factor authentication, monitoring privileged access, and restricting access to those who need it are all examples of this.
Segment Networks
Use network segmentation to control the spread of security threats. Separating development and production environments, implementing firewalls, and using virtual private networks (VPNs) to secure communications are some examples.
Implement Infrastructure as Code(IaC)
IaC security is a more recent approach to cloud security, which traditionally focused on configured cloud resources once they were delivered and making sure that recurring human configuration didn't create new problems. Securing access to vital services and client data is a common theme in cloud security challenges.
Steps for Enabling DevSecOps In Your Organization
The following actions are usually taken by organisations to achieve DevOps security at scale, mitigate risks associated with privileged access, and align with DevOps culture and methods:
Instantiate security policy as a code
- Define security policies and standards that align with your organisation's goals and objectives.
- Use a version control system to manage the security policy and standards as code.
- Review and update security policies and standards regularly to address new threats and vulnerabilities.
- Automate the security policy deployment to all relevant systems as code.
Establish separation of duties
- Define the development and security teams' roles and responsibilities.
- Ensure that the development and security teams collaborate and effectively communicate.
- Implement controls to prevent developers from changing production environments without the security team's permission.
- Create a security testing and review process before deploying code to production.
Integrate security into CI/CD practices
- To automate security checks, incorporate security testing tools into the CI/CD pipeline.
- Install security gates at each pipeline stage to ensure that the code passes security checks before proceeding to the next.
- To identify security flaws early in the development cycle, use code analysis, vulnerability scanning, and penetration testing tools.
- Automate the remediation process so that issues are addressed immediately.
Take a proactive approach to security
- Conduct security risk assessments regularly to identify potential threats and vulnerabilities.
- Monitor the environment for security threats continuously and respond quickly to mitigate risks.
- Train developers and other team members to be aware of security risks and adhere to best security practices.
- Encourage a security awareness and continuous-improvement culture.
Automate security processes
- Automate security testing, vulnerability scanning, and remediation with tools and processes.
- Use automation to ensure that security policies and standards are followed throughout the organisation.
- Implement tools for continuous security monitoring and alerting.
- Use automation to generate security posture and compliance reports.
Ready to Navigate the DevOps Landscape? Enroll in DevOps Engineer Course Today and Gain the Skills to Drive Innovation and Efficiency.
Conclusion
- DevOps introduces new security challenges such as infrastructure as code, continuous integration/continuous deployment (CI/CD) pipelines, and the need for collaboration between teams.
- DevSecOps is a methodology that incorporates security practices into the DevOps process to ensure that security is built into software from the start and is maintained throughout the software development life cycle.
- DevOps focuses on faster software development and deployment. At the same time, DevSecOps adds security as an essential component of the process to ensure that security is integrated into every stage of the software development life cycle.
- DevOps Security Best Practices involve implementing security measures throughout the entire software development life cycle, such as integrating security testing into the CI/CD pipeline, using secure coding practices, conducting regular vulnerability scans, implementing access controls, and monitoring for suspicious activity.
