File Locking in Linux
Overview
Maintaining file integrity and ensuring data is not lost or corrupted is important in any system. Whether it's a single-user system or a multi-user Linux system, understanding the working of the file locking mechanisms is essential for maintaining the stability and security of file operations. File locking in Linux plays a critical role in ensuring data integrity, preventing race conditions, and controlling access to files in both single-user and multi-user environments. This article explains the concepts of locks in Linux with their types and introduces tools for inspecting locks in the system, and also demonstrates the usage of the flock command for coordination between processes.
Introduction
In Linux, locks are mechanisms used to coordinate and control access to shared resources, such as files. Locks ensure that only one process can access a shared resource at a time, preventing conflicts, data corruption, and race conditions.
Linux provides various tools and commands to inspect and manage locks in the system. We will explore them in the upcoming sections of the article. By implementing locks effectively, Linux ensures proper synchronization and coordination among processes, maintaining the integrity of shared resources and ensuring secure system operations.
The Interceding Update Problem
The Interceding Update Problem, also known as the race condition, is a situation that arises when two or more processes attempt to update a shared resource concurrently without proper synchronization or locks. This problem can lead to unpredictable and incorrect results, data corruption, and system instability.
Let us understand the Interceding Update Problem with a simple example. Consider a scenario where two processes, Process A and Process B, is attempting to update the same file at the same time.
Process A reads the current value of a counter from the file, let's say it is 10. It plans to increment the counter by 1 and write the updated value back to the file. At the same time, Process B also reads the current value of the counter, which is still 10. It plans to decrement the counter by 1 and write the updated value back to the file.
Since both processes are executing concurrently, the following events may occur:
- Process A reads the value 10 from the file.
- Process B reads the value 10 from the file.
- Process A increments the value to 11 and writes it back to the file.
- Process B decrements the value to 9 and writes it back to the file.
In this case, the final value of the counter should ideally be 10, but due to the lack of proper synchronization and coordination between the processes, the result is incorrect. The counter ends up with a value of 9 instead.
A similar example in the real world will be two users A and B, retrieving or retrieving and depositing money to the bank at the same time. The final amount at the bank should not depend on the order of the action but on the action only. This may lead to loss of money which should be prevented at all costs.
To prevent this problem, we must implement appropriate file-locking techniques, such as advisory or mandatory locking, to ensure data integrity and prevent race conditions. Let us explore more on the locking mechanisms.
File Locking in Linux
Linux offers two types of file-locking mechanisms:
Advisory Locking
- Advisory locking is a file-locking mechanism in Linux that relies on the cooperation of processes.
- It allows processes to voluntarily request locks on files, indicating that the process will be reading or modifying the files.
- Advisory locking is useful in situations where processes are designed to cooperate.
- In advisory locking, there are two types of locks,
- Shared locks
- Exclusive locks
- A process can get either one of these locks. Multiple processes can acquire shared locks simultaneously, allowing them to read the file concurrently.
- However, only one process can hold an exclusive lock at a given time, ensuring exclusive write access to the file.
The advisory locks are advisory, meaning that processes can access the file even though they do not respect or check for existing locks. It is the responsibility of the processes to check for locks and act accordingly.
If a process attempts to acquire a lock on a file that is already locked by another process, it can choose to wait, try again later, or handle the situation based on the specific requirements of the application.
Mandatory Locking
- Mandatory locking, also known as file locking enforcement, is a more rigid form of file locking in Linux, where locks are enforced at the kernel level.
- Unlike advisory locking, mandatory locking forces the locking mechanism regardless of the process's cooperation. It ensures that processes cannot access a locked file without concerning the locking rules.
- When a process acquires a lock on a file, the operating system prevents other processes from performing conflicting operations until the lock is released.
- This mechanism provides a higher level of security and control over file access but requires careful implementation and configuration.
In contrast to advisory locking, mandatory locking does not rely on the cooperation of processes. It guarantees that the locking rules are consistently enforced, even if processes attempt to bypass or ignore the locks.
Inspect All Locks in a System
Inspecting all locks in a Linux system is useful for understanding the current lock status, identifying potential conflicts, and resolving any issues related to file locking.
Linux provides several commands and resources to inspect locks in the system. Let's explore two commonly used methods: the lslocks command and the /proc/locks file.
The lslocks Command
The lslocks command is a powerful tool that allows users to inspect all active locks in the system. It provides an overview of the locks, their types, associated processes, and the files they are locked on.
To use the lslocks command, open a terminal and execute it with appropriate privileges
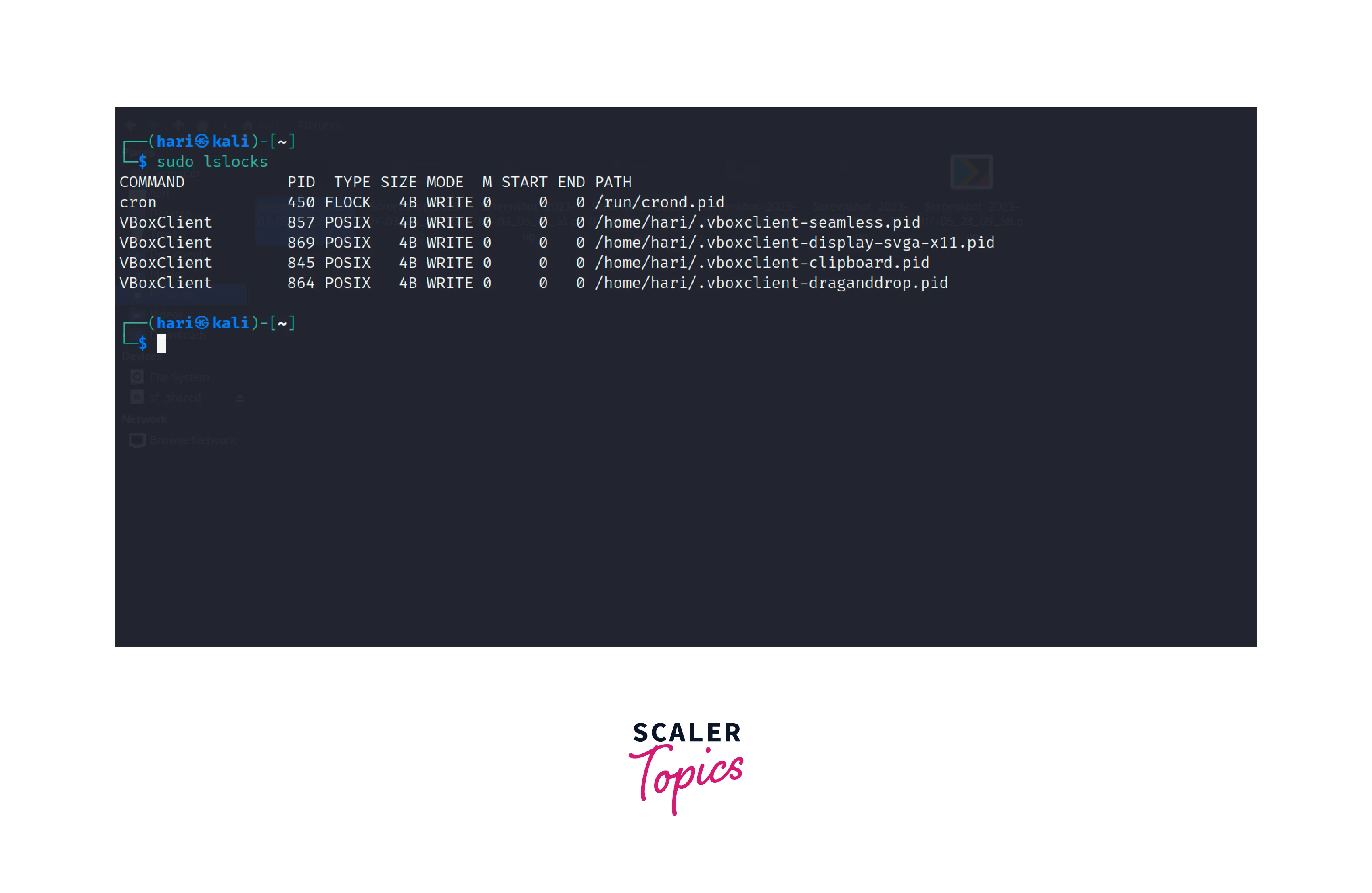
Running this command displays a list of active locks, including information such as the PID (Process ID) of the locking process, the type of lock (shared or exclusive), the inode number of the locked file, and the file path.
/proc/locks
Another method to inspect locks in a Linux system is by examining the /proc/locks file.
- Procfs (process file system) is a special virtual file system in Linux that allows users and processes to access and retrieve runtime information about the system and running processes.
- The procfs is mounted on the /proc director and contains system information such as such as CPU and memory usage, and network statistics, including the /proc/locks file, which provides details about active locks in the system.
To access the information in the /proc/locks file, we can use an editor like vim, or nano or print the data using command-line utilities such as cat or less.
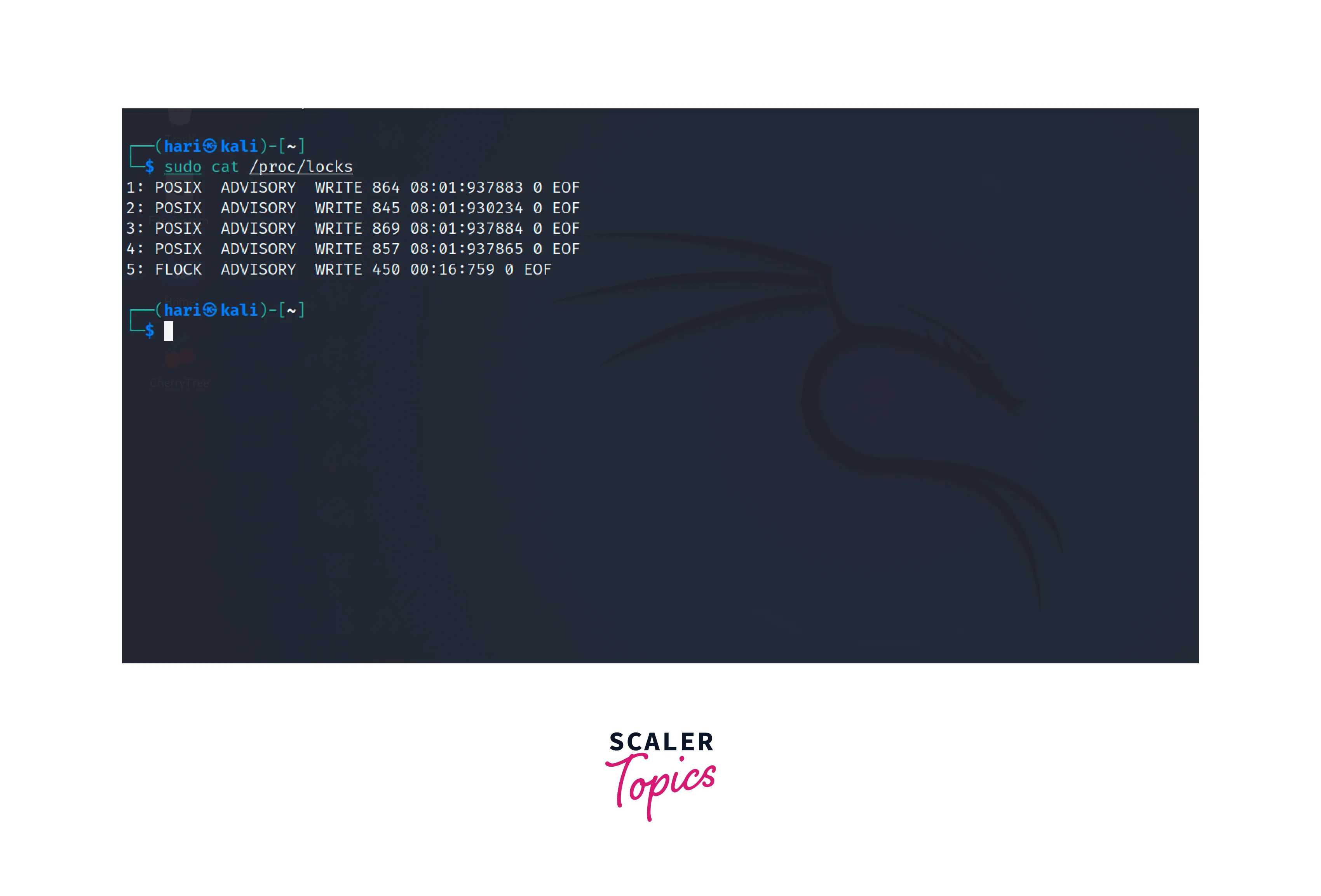
The output of the above commands shows a structured representation of active locks, including the PID, type of lock, device number, inode number, file type, and other relevant details.
Introduction to flock Command
The flock command in Linux provides advisory file-locking capabilities. It allows processes to acquire exclusive or shared locks on files. Let's explore the syntax of the flock command and demonstrate its usage with both non-cooperative and cooperative processes.
The basic syntax of the flock command is as follows,
- [options] refers to any additional flags or options that can be used with the flock command, such as -s for a shared lock or -x for an exclusive lock.
- [file] specifies the path to the file on which the lock should be acquired.
- [command] represents the command or script that should be executed while holding the lock.
The following command attempts to acquire an exclusive lock on the file specified by file.lock. If another process already holds the lock, the flock command will wait until the lock is released before executing the specified command.
The following command is used to acquire a shared lock,
Multiple processes can acquire shared locks simultaneously, allowing them to read the file concurrently.
Now, let's demonstrate the usage of the flock command with non-cooperative and cooperative processes:
Demonstration of the flock with Non-Cooperative Processes
To understand the usage of flock with non-cooperative processes, let's consider a scenario where two independent processes, Process A and Process B attempt to access a shared file concurrently without respecting locks. We use bash scripts to access the same file and will also use the flock command to enforce exclusive access to the file.
Process A attempts to acquire an exclusive lock on data.txt using the flock command,
In this script, the flock command tries to acquire an exclusive lock (-x) on the file data.txt. The -w 10 option specifies a waiting time of 10 seconds if the lock is not immediately available. The 200 file descriptor is used to represent the lock.
Similarly, Process B attempts to acquire an exclusive lock on data.txt using the flock command,
Now, let us name both the scripts as a.sh and b.sh and simulate the execution of these processes. We'll assume that both scripts are executed simultaneously.
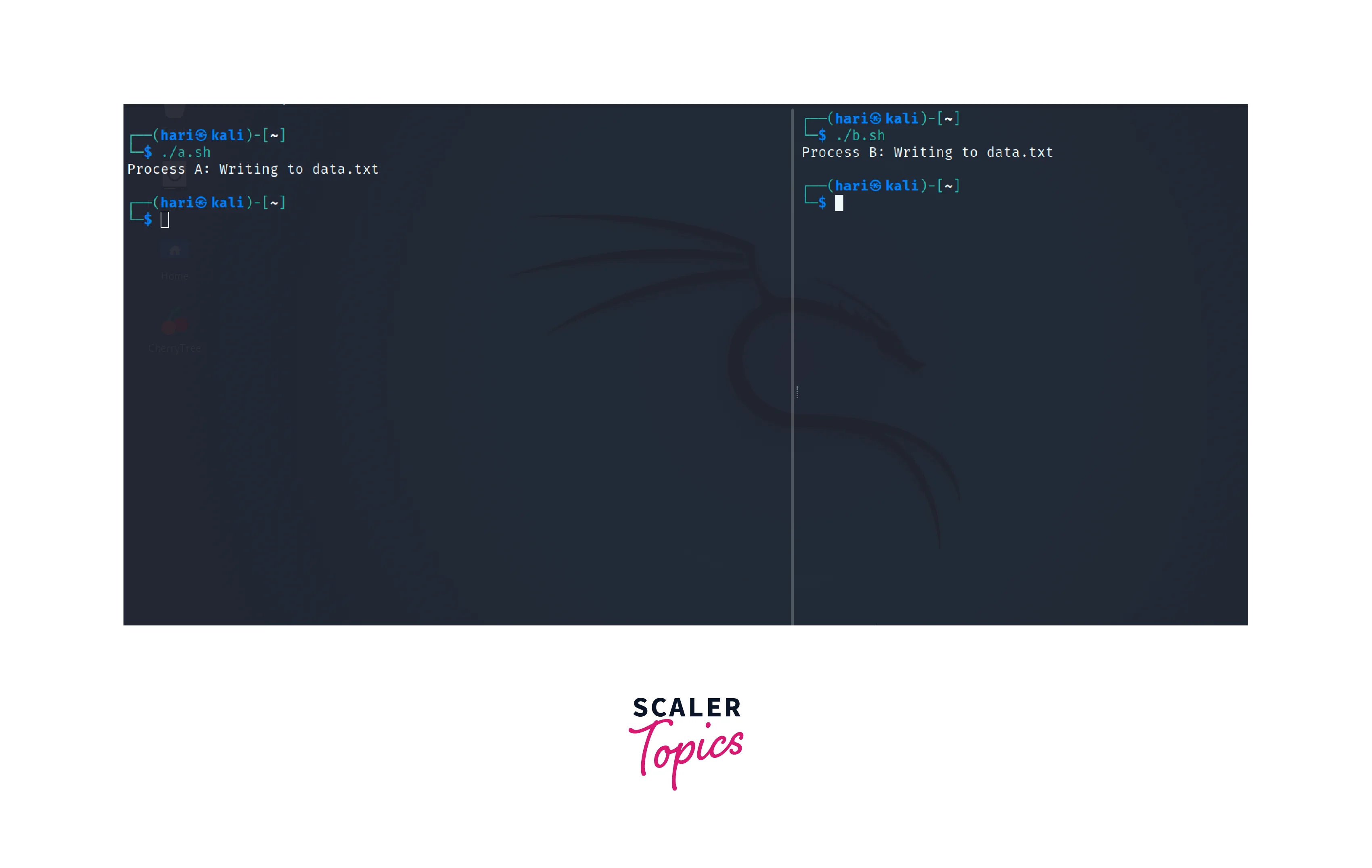
Initially, both processes start executing concurrently and attempt to acquire the lock on data.txt. Since the file is not locked by any process initially, any one of the processes will successfully acquire the lock and proceed to execute its critical sections.
Let us consider that Process A successfully acquires the lock first and enters its critical section, writing its content to data.txt. While Process A is still executing, Process B tries to acquire the lock but finds it unavailable. As per the -w 10 option, Process B waits for 10 seconds for the lock to become available.
After Process A releases the lock, Process B immediately acquires it and enters its critical section, writing its content to "data.txt". Since flock ensures exclusive access, only one process can hold the lock at a time, preventing conflicts and ensuring data integrity.
Demonstration of the flock with Cooperative Processes
To demonstrate the usage of flock with cooperative processes, let's consider a scenario where multiple processes such as Process A, Process B, and Process C need to read a shared file called data.txt concurrently while ensuring synchronization. We'll also use theflock command to acquire shared access to the file.
Process A attempts to acquire a shared lock on data.txt using the flock command and the following script,
In this script, the flock command attempts to acquire a shared lock (-s) on the file data.txt. The -w 10 option specifies a waiting time of 10 seconds if the lock is not immediately available. The 200 file descriptor is used to represent the lock in successive cases.
Similarly, Process B and Process C also attempt to acquire shared locks on data.txt using flock in scripts,
Initially, all three processes start executing concurrently, and let us consider that, Process A acquires the lock and enters its critical section, reading the contents of data.txt. At the same time, Process B and Process C also acquire the shared lock, allowing them to execute their critical sections concurrently.

By using shared locks, multiple processes can read the contents of the file simultaneously without conflicts. The shared lock ensures allows multiple processes to hold shared locks and read the file concurrently.
Conclusion
- File locking in Linux is crucial for maintaining data integrity and concurrency.
- Advisory locking is a voluntary mechanism where processes request locks on files to indicate exclusive modification or reading intentions.
- Mandatory locking enforces the locking mechanism regardless of process cooperation, ensuring strict adherence to locking rules.
- The lslocks command and the /proc/locks file provide a comprehensive overview of active locks in the system, allowing administrators to identify conflicts and take appropriate actions.
- The flock command enables advisory file locking, allowing processes to acquire exclusive or shared locks on files for coordination and synchronization.
- Non-cooperative processes may not check for locks, but the flock command can still prevent them from accessing a locked file.
- Cooperative processes respect and check for locks, coordinating their actions based on the lock status.
- Understanding and implementing file locking mechanisms in Linux enhances data security, prevents conflicts, and ensures stable file operations.
