What is a Firewall in Cyber Security?
A firewall is a protective barrier between a trusted internal network and untrusted external networks, such as the Internet. It monitors and controls incoming and outgoing network traffic based on predetermined security rules, establishing a secure environment for data transmission. The OSI model consists of seven layers, each responsible for specific functions in network communication and the firewalls operate at the network layer (Layer 3) and the transport layer (Layer 4). We will explore the different security actions performed by firewalls at these layers in this article.
Role of Firewalls in Cyber Security
The major task of a firewall in cybersecurity is centered around preventing unauthorized access, which leads to the following roles:
- Firewall controls and regulates incoming and outgoing network traffic using access control policies.
- Firewalls continuously monitor network traffic, analyzing data packets and adapting to emerging threats and evolving attack techniques.
- Prevents unauthorized access to a network by blocking suspicious or malicious incoming traffic.
- Protecting the network from various cyber threats that target network vulnerabilities and also prevent malware or viruses in the network.
- Performs network segmentation to prevent threats from spreading across the entire network.
- Keep track of the state of active connections by utilizing stateful inspection.
Types of Firewalls in Cyber Security
Firewalls come in various types, each serving specific purposes in enhancing cybersecurity measures.
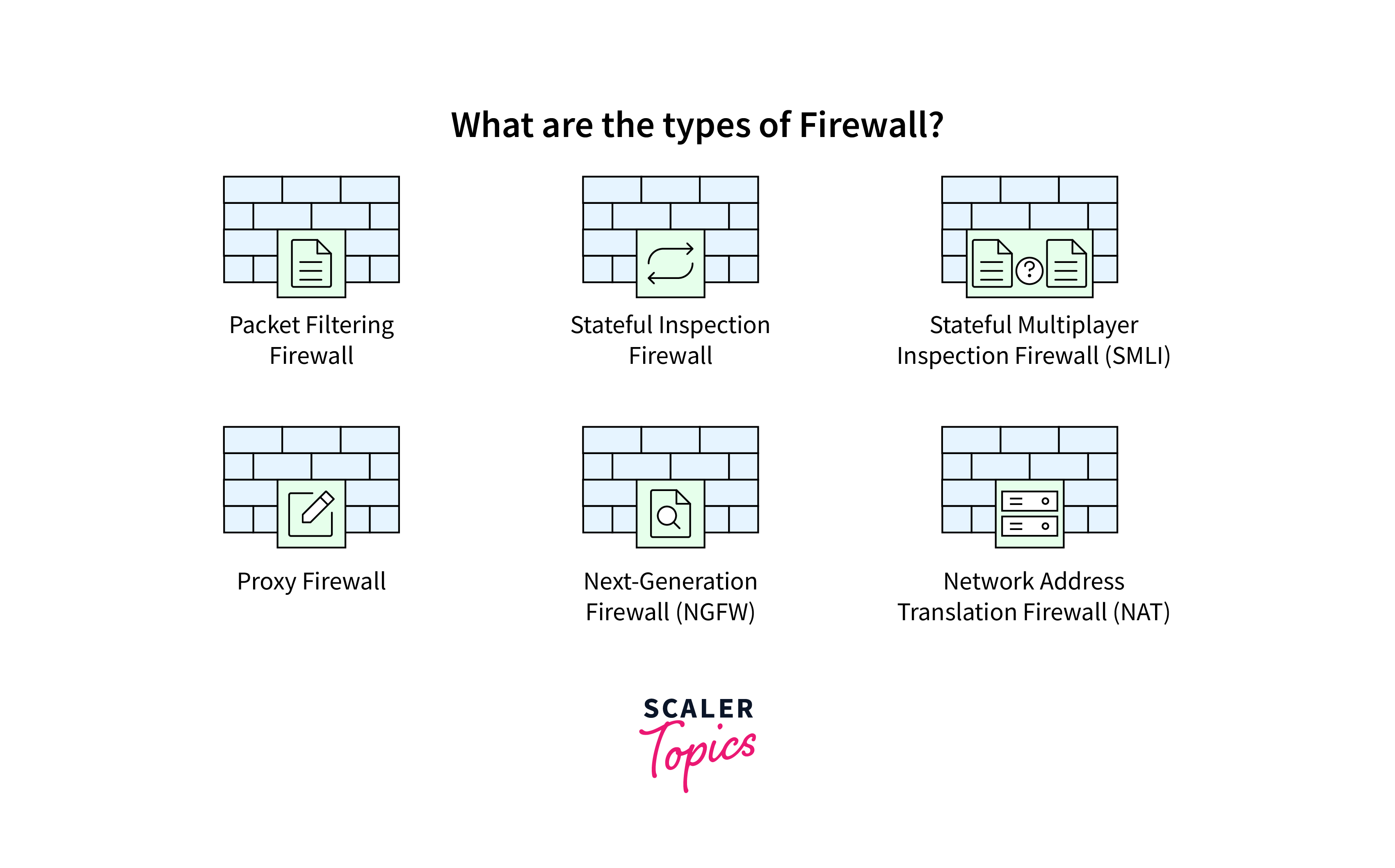
Packet Filtering
A packet is a fundamental unit of data in network communication. It contains information such as source and destination IP addresses, port numbers, and the actual data payload being transmitted.
Several vulnerabilities associated with packets include spoofing, eavesdropping, and packet injection in which attackers can manipulate packet headers, intercept unencrypted packets, and inject malicious packets.
A Packet Filtering Firewall operates at the network layer (Layer 3) of the OSI model and is designed to evaluate each packet to determine whether it should be allowed or denied entry into the network based on predetermined rules.

Features:
- Packet filtering firewalls inspect packet headers to filter based on source and destination IP addresses.
- By analyzing port numbers in packet headers, the firewall controls access to specific services running on devices.
Limitations:
While effective for basic security, packet filtering has limitations. It may struggle with more sophisticated attacks that manipulate packet content or exploit vulnerabilities by disguising malicious payloads within seemingly harmless packets.
Proxy Service Firewall
A proxy is an intermediary server that acts as a gateway between client devices and the internet. It creates indirect connections, allowing clients to access resources without directly communicating with the target server.
Proxies introduce potential vulnerabilities related to data interception, authentication issues, and trust concerns. Proxy can inspect the information passing through them and when not configured securely, can become points of vulnerability.
A Proxy Service Firewall is a security mechanism that utilizes proxy servers to control and secure communication between internal networks and external entities. This type of firewall operates at the application layer (Layer 7) of the OSI model.
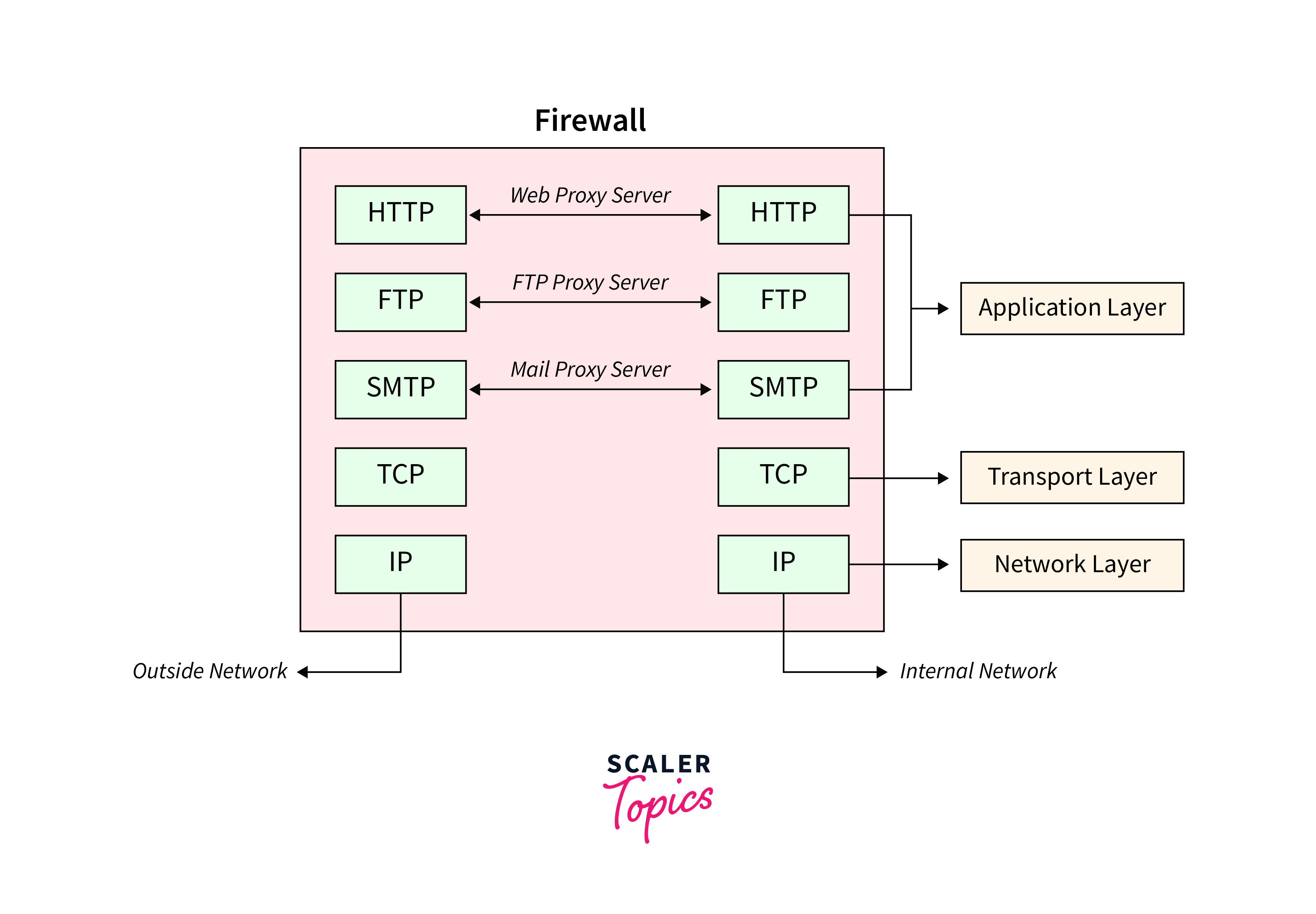
Key Features:
- Proxies in firewall services can mask the identity of internal users.
- Proxy service firewalls often include content filtering capabilities.
- Proxy servers can cache frequently requested content, reducing the load on external servers.
Limitations:
If the proxy server fails or becomes a target of an attack, it can disrupt the entire network's communication with external resources. Additionally, the implementation of proxy services may introduce resource overhead, impacting network latency and performance.
Stateful Inspection Firewall
Statefulness refers to the ability of a firewall, to keep track of the state of active connections. Unlike stateless inspection, which evaluates individual packets independently, stateful inspection maintains awareness of the context.
Vulnerabilities:
The stateful inspection process can be resource-intensive, potentially impacting the firewall's performance under heavy network traffic.
A Stateful Inspection Firewall is a security mechanism that monitors the state of active connections, allowing it to make context-aware decisions about allowing or blocking data packets. This type of firewall operates at the network layer (Layer 3) and transport layer (Layer 4) of the OSI model.
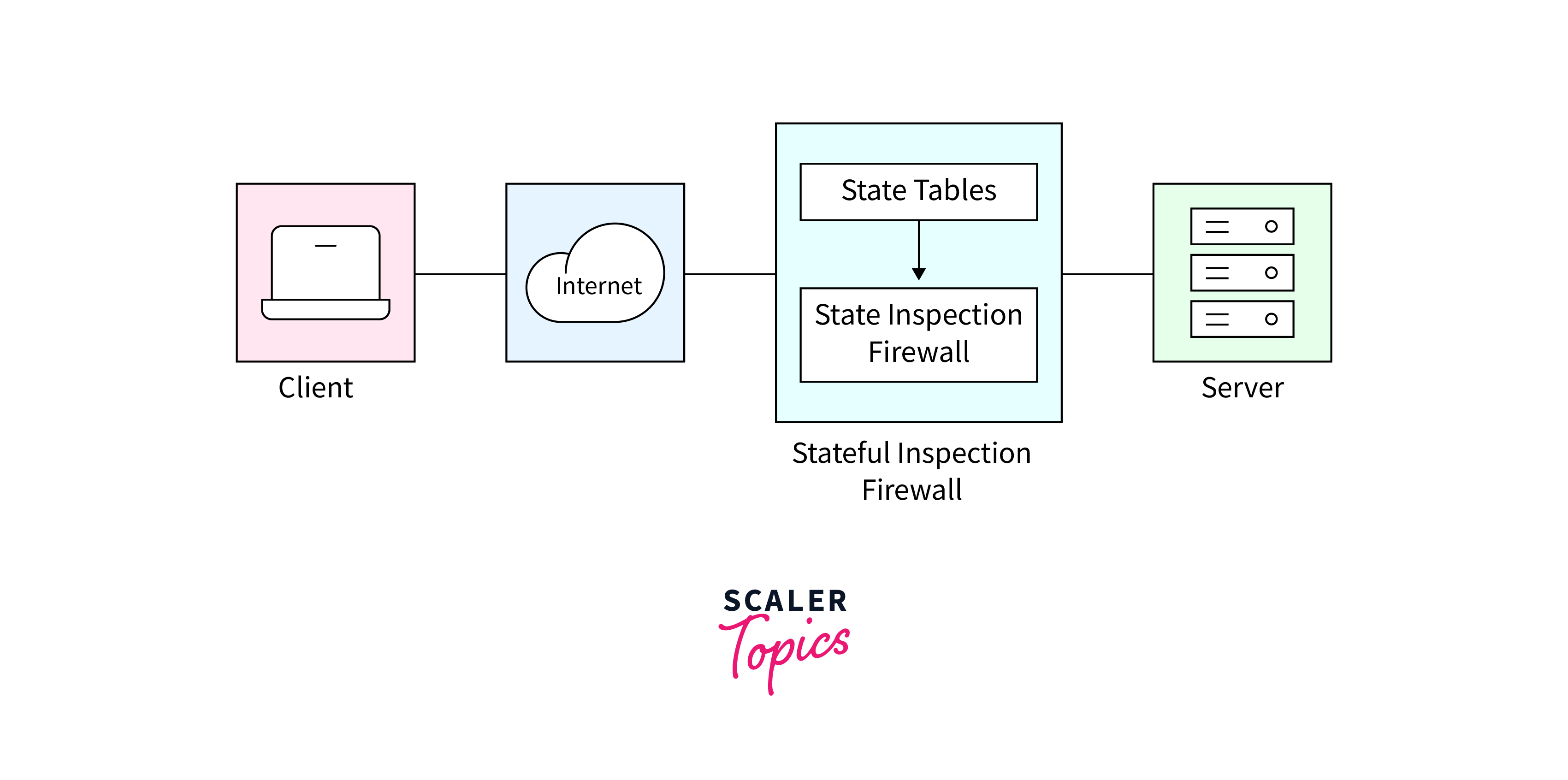
Key Features:
- Stateful inspection allows the firewall to understand the state of active connections, differentiating between legitimate and potentially harmful traffic.
- The firewall can dynamically adapt its rules based on the changing state of connections, providing a more flexible and adaptive security approach.
Limitations:
Stateful inspection can consume significant resources, potentially impacting the firewall's performance under high traffic loads. The increased awareness of connection states adds complexity to the configuration and maintenance of stateful inspection firewalls.
Next-Generation Firewall (NGFW)
A Next-Generation Firewall (NGFW) is a security solution that combines traditional firewall capabilities with advanced features like intrusion prevention, deep packet inspection, and application awareness.
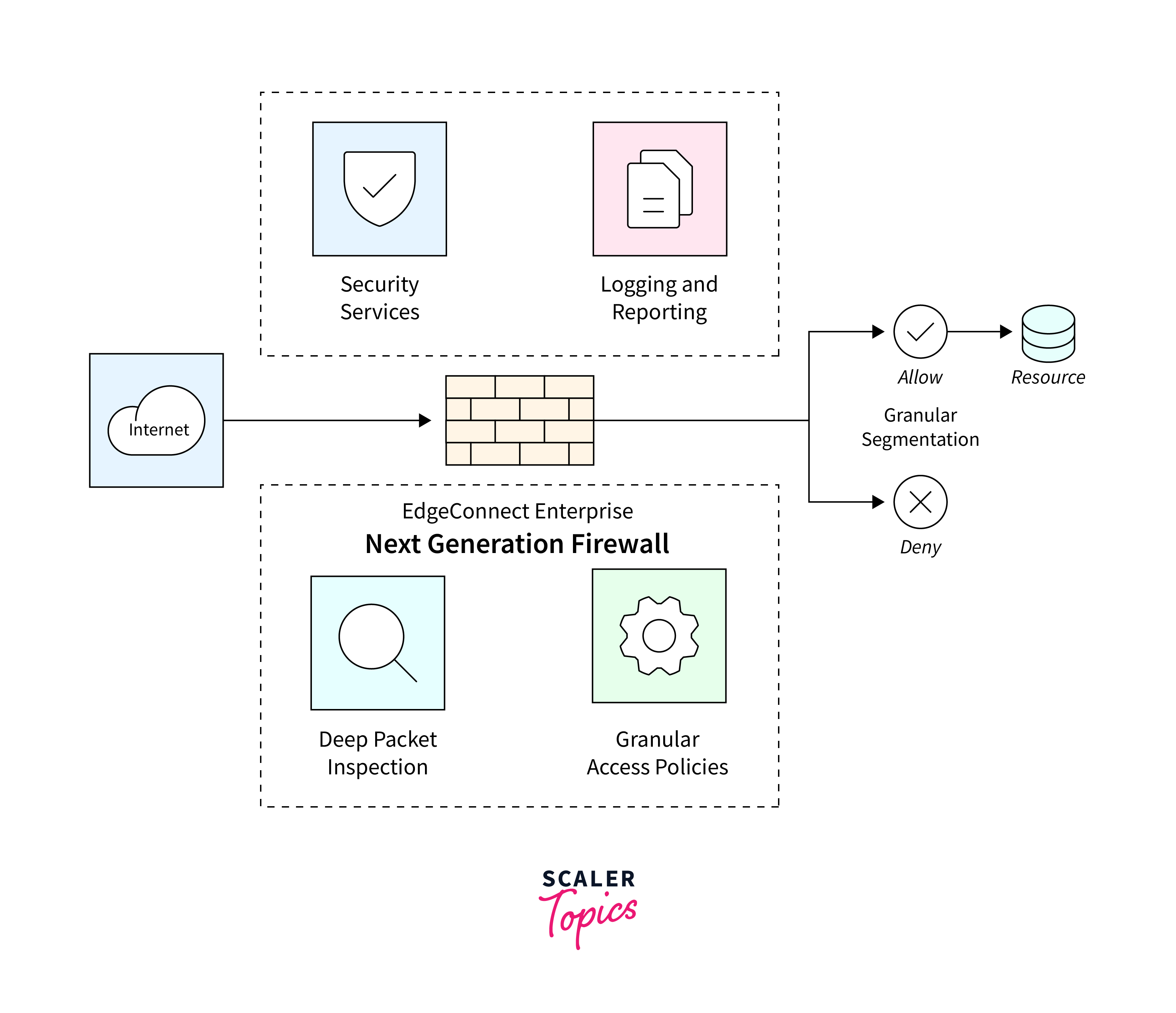
Key Features:
- NGFWs conduct deep packet inspection to analyze the content of data packets.
- NGFWs integrate intrusion prevention systems (IPS) to proactively identify and thwart potential cyber threat
- NGFWs are aware of specific applications and can enforce policies based on the application that is being used.
Limitations:
Despite advanced features, NGFWs may face challenges in detecting sophisticated attack techniques, as attackers continually evolve to bypass security measures.
Segmentation
Network segmentation involves dividing a larger network into smaller, isolated segments to enhance security by restricting unauthorized access and containing potential security incidents.
Practical Application:
Imagine a corporate network that houses various departments like finance, research and development. Without segmentation, if a cyber threat gains access to one part of the network, it could compromise the entire infrastructure. However, by implementing network segmentation, the organization can isolate these departments into separate segments.
Improving Security:
- Segmentation ensures that users only have access to the resources necessary for their specific roles.
- Sensitive information, such as financial records or intellectual property, can be isolated within specific segments.
Intrusion Detection System (IDS) & Intrusion Prevention System (IPS)
Intrusion Detection System (IDS)
An Intrusion Detection System (IDS) monitors and analyze the network or system activities for any signs of unauthorized access, security policy violations, or abnormal behavior. The two types of IDS are:
-
Signature-Based IDS:
Utilizes predefined patterns or signatures of known threats to identify malicious activities.
-
Anomaly-Based IDS:
Establishes a identifier of normal behavior and flags any deviation from this baseline as potentially suspicious.
Intrusion Prevention System (IPS)
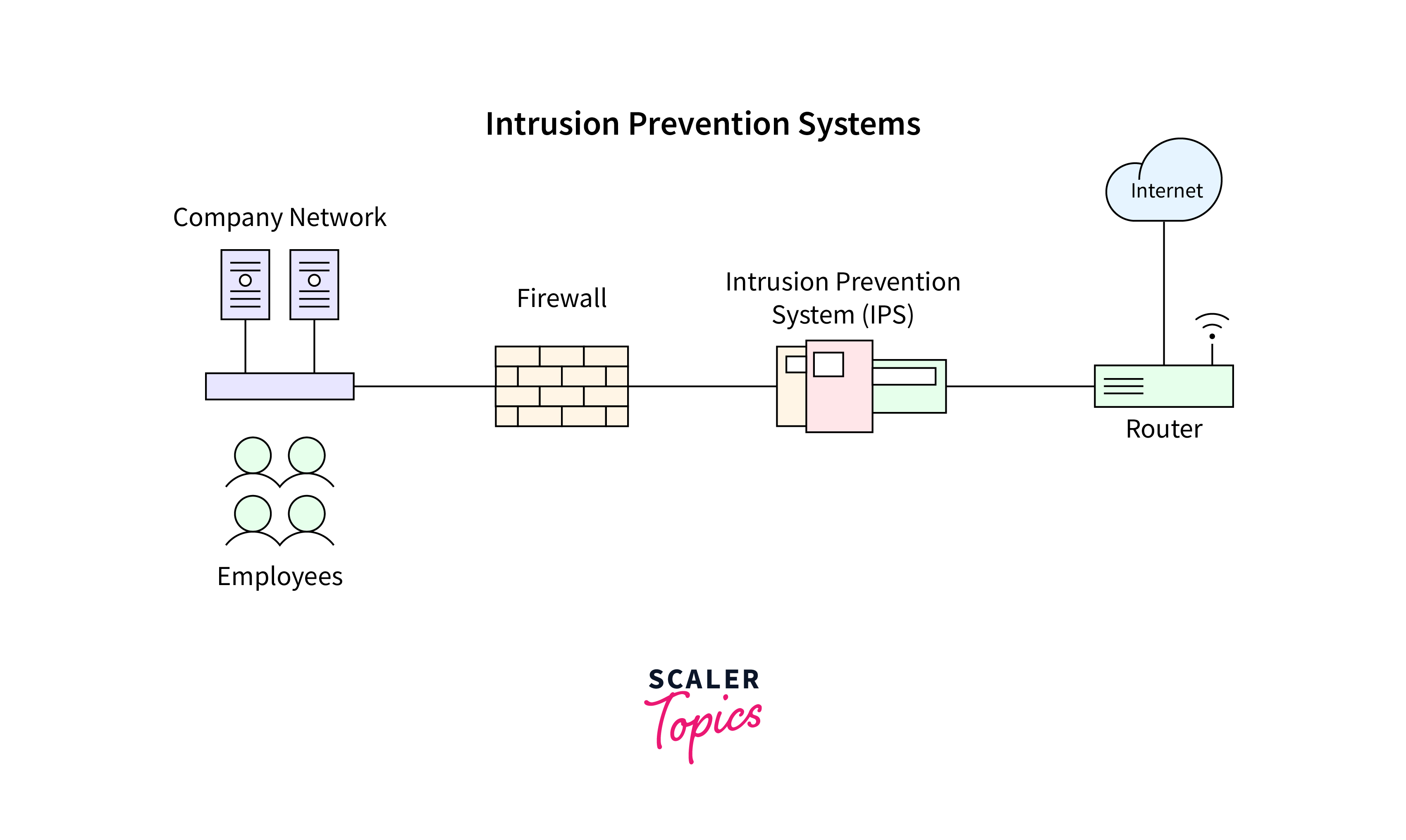
An Intrusion Prevention System (IPS) builds upon the capabilities of an IDS but, instead of just identifying and alerting, an IPS is empowered to take immediate action to prevent or mitigate the impact of detected threats. The key features of IPS are:
- IPS systems can actively perform real-time blocking of suspicious traffic including preventing certain types of packets.
- IPS conducts deep packet inspection to analyze the content and context of data packets. This allows it to identify and block malicious payloads and behaviors.
- IPS systems can adapt their security measures based on the evolving threat landscape.
Content and Application Filtering
Content and Application Filtering is a cybersecurity strategy that involves monitoring, controlling, and restricting access to specific content or applications on a network.
Content Filtering
Content filtering involves analyzing web content, emails, or other forms of communication to identify and control access to specific types of information. This can include blocking malicious websites, restricting access to inappropriate content, or preventing the download of harmful files.
Application Filtering
Application filtering focuses on controlling the use of specific applications or services on a network. This includes regulating access to social media platforms, messaging apps, or other applications that may pose security or productivity risks.
Applications
- Many organizations implement content and application filtering restricting access to non-work-related websites to enhance productivity and mitigate security risks.
- Schools and universities often use content filtering to ensure a safe online environment for students. This includes blocking access to inappropriate content.
- Public Wi-Fi providers utilize content and application filtering to manage network resources, hence preventing illegal downloads or access to malicious websites.
Web Application Firewall (WAF)
Most web applications are protected using the Web Application Firewall (WAF) which is specifically designed for web security. Unlike traditional firewalls that focus on network traffic, a WAF specifically targets the application layer (Layer 7) of the OSI model. Its primary purpose is to analyze and filter HTTP traffic between a web application and the internet.
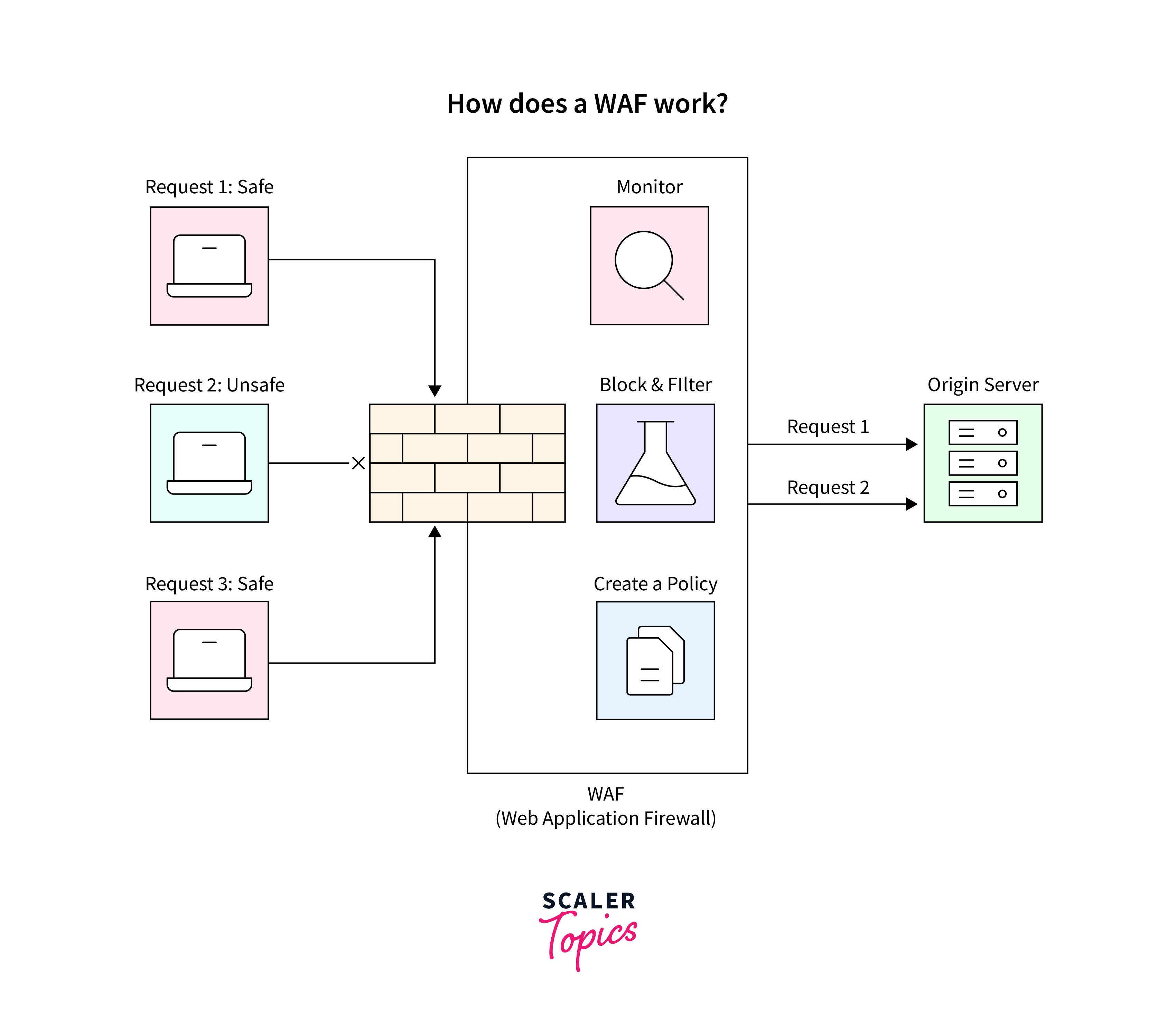
Key Functions
- WAFs are designed to safeguard web applications from a wide range of attacks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and other common web-based exploits.
- WAFs use signature-based detection to identify known attack patterns. These signatures, similar to those used in antivirus solutions, help the WAF recognize and block known malicious patterns.
- WAFs often include features to protect user sessions and prevent session-based attacks.
Best Practices for Firewalls in Cyber Security
- Keep firewalls up to date by applying regular software updates and security patches. This ensures that the firewall can effectively protect against emerging cyber threats.
- Implement granular rule configurations to specify which traffic is allowed or blocked based on source and destination IP addresses, port numbers, and protocols.
- Implement network segmentation to divide the network into isolated segments. This limits the impact of a enhancing overall network security.
- Set up monitoring and logging capabilities to track network traffic and detect any unusual or suspicious activities.
- Implement a multi-layered security approach by combining firewalls with other cybersecurity measures such as intrusion detection and prevention systems.
Conclusion
- Firewalls are crucial components of cybersecurity, acting as protective barriers between trusted internal networks and untrusted external networks. They operate at the network and transport layers, using various techniques to regulate traffic flow.
- Firewalls encompass various types, including Packet Filtering, Proxy Service, Stateful Inspection, Next-Generation (NGFW), and Web Application Firewalls (WAF), each designed for specific security needs and functionalities.
- Network segmentation involves dividing a large network into isolated segments, enhancing security by isolating different segments, and limiting the impact of potential breaches.
- Intrusion Detection Systems (IDS) monitor and alert administrators to potential security incidents, while Intrusion Prevention Systems (IPS) actively prevent or mitigate threats.
- Content and Application Filtering helps control access to specific content and applications, improving security in various settings, including corporate networks and public Wi-Fi.
- Web Application Firewalls (WAF) focus on protecting web applications from a range of cyber threats, operating at the application layer and using features like signature-based protection and behavioral analysis.
- Best practices for firewalls include regular updates, granular rule configuration, network segmentation, monitoring, and implementing a multi-layered defense strategy.
