Flooding is a technique of routing in computer networking, in which a sender node transmits packets via all the outgoing links. Flooding is similar to broadcasting in that it happens when sender packets are transferred without routing data to each network node attached.
Since flooding naturally utilizes each route in the network, flooding algorithms are designed to find and utilize the shortest path to transfer the packets. Flooding can also be used for D.O.S. (Denial Of Service) attacks for bringing down a network by flooding network traffic.
What is Flooding?
Flooding is a static routing technique, based on the following principle:
“When a packet reaches the router, it is transferred to all the outgoing links, except only the link that it has reached the router through.”
Flooding is used in routing protocols such as O.S.P.F. (Open Shortest Path First), peer-to-peer file transfers, systems such as Usenet, bridging, etc. Let us have a look at an example for a better understanding. Assume there is a network with 6 routers connected through transmission lines, as shown in the figure ahead.
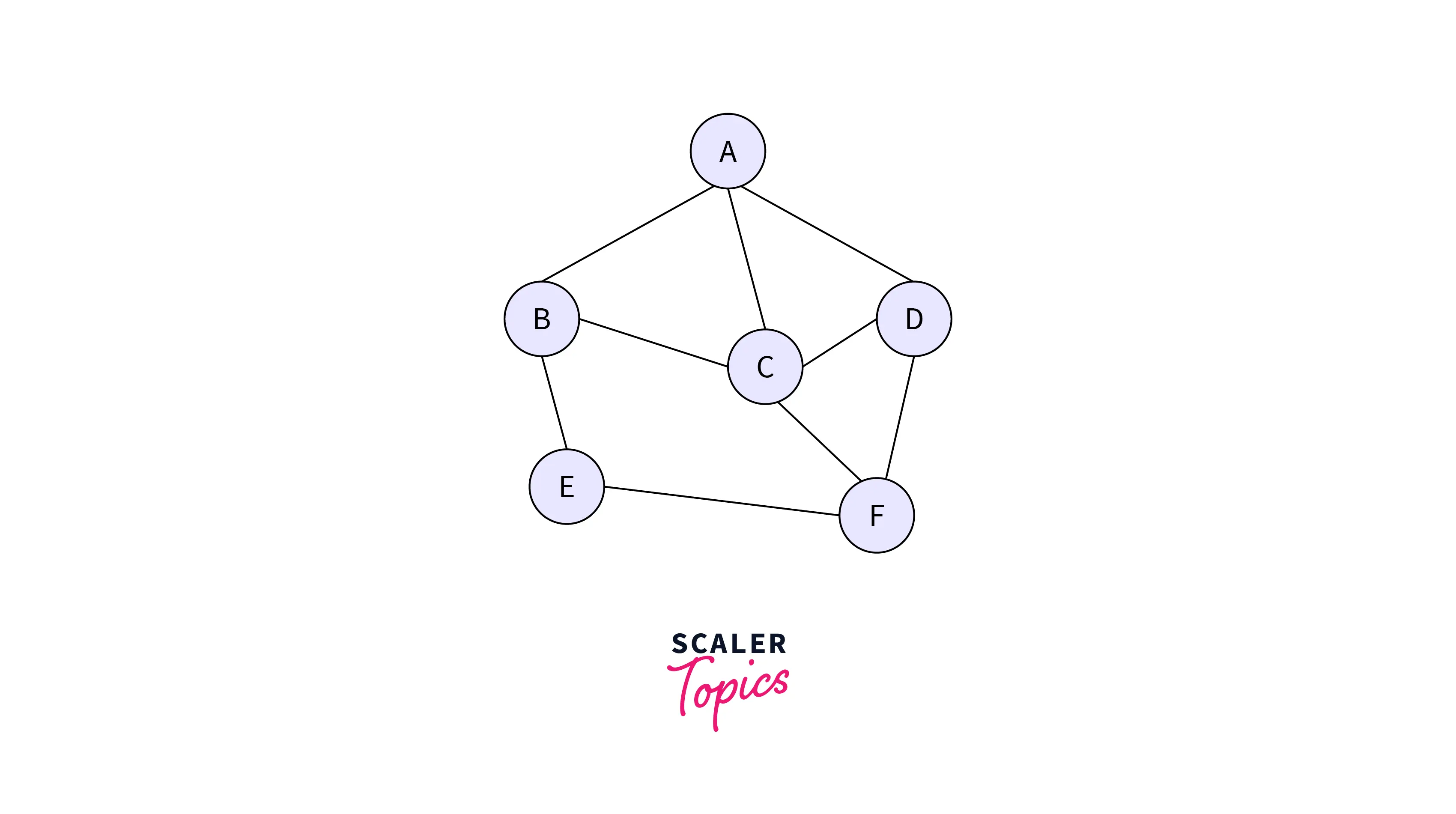
Following are the Events That Take Place in Flooding
- Any packet incoming to A is sent to D, C, and B.
- B sends this packet to E and C.
- C sends this packet to F, D, and B.
- D sends this packet to F and C.
- E sends the packet to F.
- F sends the packet to E and C.
Types of Flooding
Flooding in computer networking is usually of the following three kinds:
Uncontrolled Flooding
In uncontrolled flooding, every node distributes the packets unconditionally to all its neighbors. Broadcast storms become a catastrophe in the absence of conditional logic for the prohibition of indefinite recirculation of the same packet.
Controlled Flooding
Controlled flooding is more reliable, thanks to the two algorithms that it has:
S.N.C.F. (Sequence Number Controlled Flooding)
As each node possesses sequence numbers and memory of addresses, it sticks its very own sequence number and addresses with the packet. If a packet arrives at a node that has the packet in memory already, the node immediately drops the packet.
R.P.F. (Reverse Path Forwarding)
A node transfers a packet only in the forward direction to the next node. If the packet came from the next node, it is returned to the sender.
Selective Flooding
It is a version of flooding that only sends packets to routers in the same direction. Instead of transferring each incoming packet on every line, the routers transmit the packets on only those lines that are approximately going in the right direction.
Characteristics of Flooding
Following are some features of flooding:
- Every possible route between the source and the destination for transmission is tried in flooding.
- There always exists a minimum of one route which is the shortest.
- Any node that is connected, whether directly or indirectly, is explored.
- Flooding does not require any information related to the network, such as the costs of various paths, load conditions, topology, etc. This is why it is non-adaptive.
Advantages of Flooding
- Flooding always attempts to select the shortest path.
- Since any node connected directly or indirectly is explored, there is no probability of any node being missed out.
- Flooding is very robust. Even if several routers malfunction, the packets still find a path to their destinations.
- Flooding is quite easy to implement and set up, as a router can know only about its neighbors.
Disadvantages of Flooding
- Repetitive and unauthorized packets of data can jam a network. This could result in hampering other data packets.
- Flooding becomes inefficient in case only one destination requires the packet because flooding unconditionally transmits the data packet to all nodes.
- Flooding aids in generating an infinite number of duplicate data packets unless there exists some logic to enforce a limit upon the creation of packets.
- Flooding is expensive in terms of the bandwidth that it wastes. A message may have a single destination, yet it has to be sent to all the hosts.
- When a
D.O.S. (Denial Of Service)attack or ping flood occurs, flooding may harm the reliability of the network.
Conclusion
- Flooding is a technique of routing computer networking in which a sender node transmits packets via all the outgoing links.
- Flooding is used in routing protocols such as
O.S.P.F. (Open Shortest Path First), peer-to-peer file transfers, systems such as Usenet, bridging, etc. - Flooding is of three types: controlled, uncontrolled, and selective.
- Flooding always attempts to select the shortest path.
- Flooding is quite easy to implement and set up, as a router can know only about its neighbors.
- Repetitive and unauthorized packets of data can jam a network. This could result in hampering other data packets.
- When a
D.O.S. (Denial Of Service)attack or ping flood occurs, flooding may harm the reliability of the network.
