How To Generate a CSR (Certificate Signing Request) in Linux?
Overview
A Certificate Signing Request (CSR) consists of an encrypted text file which is encrypted using block encryption. This CSR is shared with a Certificate Authority (CA) while applying for an SSL certificate.
An SSL certificate is a digital certificate used by websites to ensure the authenticity of the origin of the website. This is necessary to make sure that the communication of a client with a website is encrypted and is being directed to the correct locations.
To generate CSR in Linux, we use the OpenSSL command line tool.
SSL Certificate Categories
SSL certificates are of two types:
-
CA authorized certificate: These certificates are issued by a Trusted Third Party entity. These digital certificates are used by servers on the internet for data encryption with the client. These certificates have a limited validity according to the plan selected by the organization owner and the owners need to get these certificates revalidated before their expiry. To obtain CA digital certificates, owners need to get their domain verified beforehand.
-
Self-signed certificates: These are the digital certificates signed by individuals using their private keys and not signed using the private keys of a trusted Certificate Authority. Local certificate authorities are used to create such SSL certificates. These are usually used for applications running on a local network and FTP servers. Self-signed certificates have a validity of one year.
Generating CSR in Linux
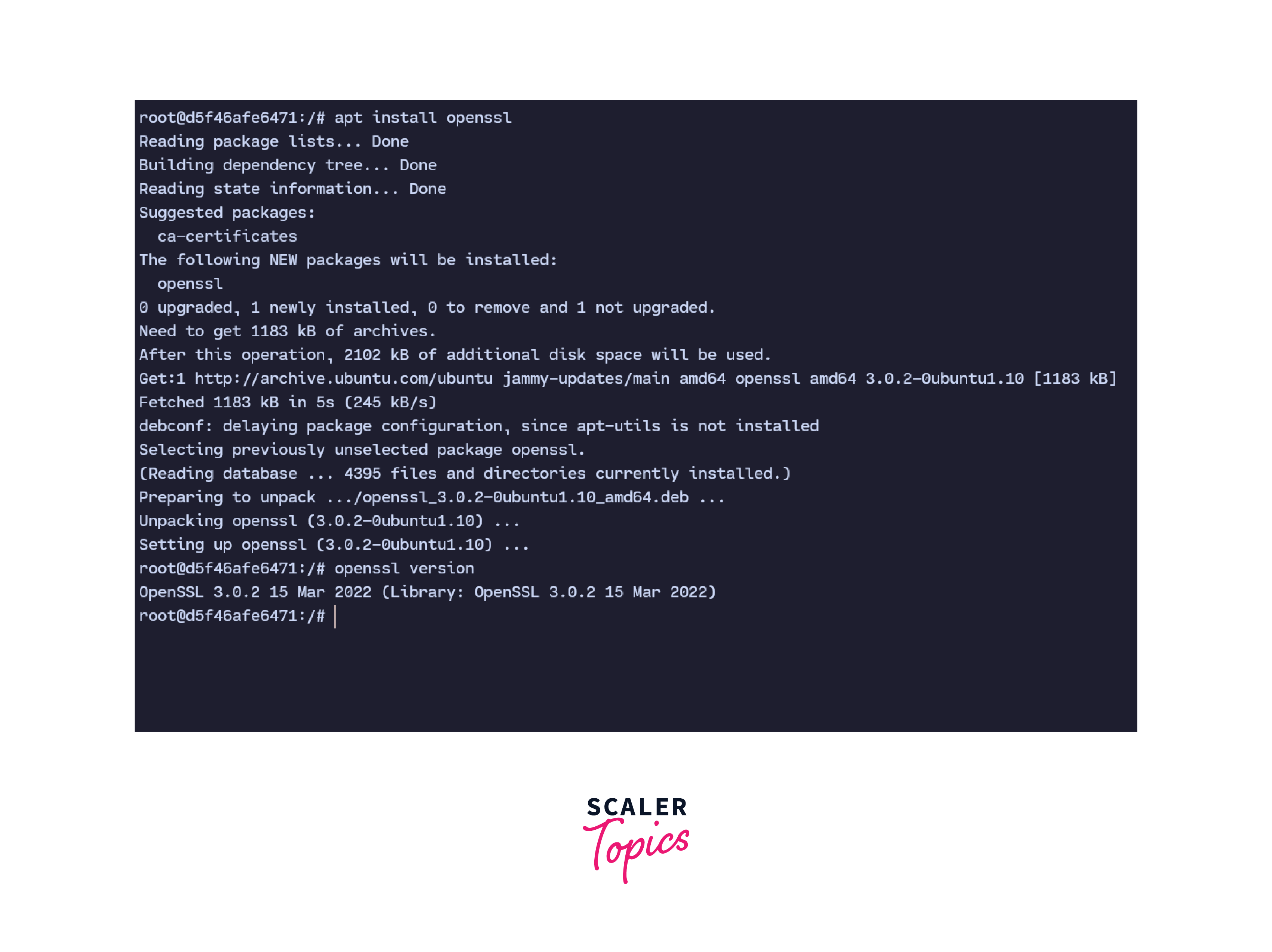
To generate CSR in Linux, we need to install the OpenSSL command line tool. OpenSSL is an open-source implementation of the SSL and TLS protocols.
To install the OpenSSL tool on Debian-based systems, we run the command:
Now, in a directory where you want to save the CSR file and the associated key files, run the command:
Breakdown of what the command does:
- genrsa: Instructs openssl to use create a key using the RSA encryption algorithm.
- -out: Name of the file in which the key will be saved.
This generates a 2048-bit private RSA key saved in the csrkey.key file.
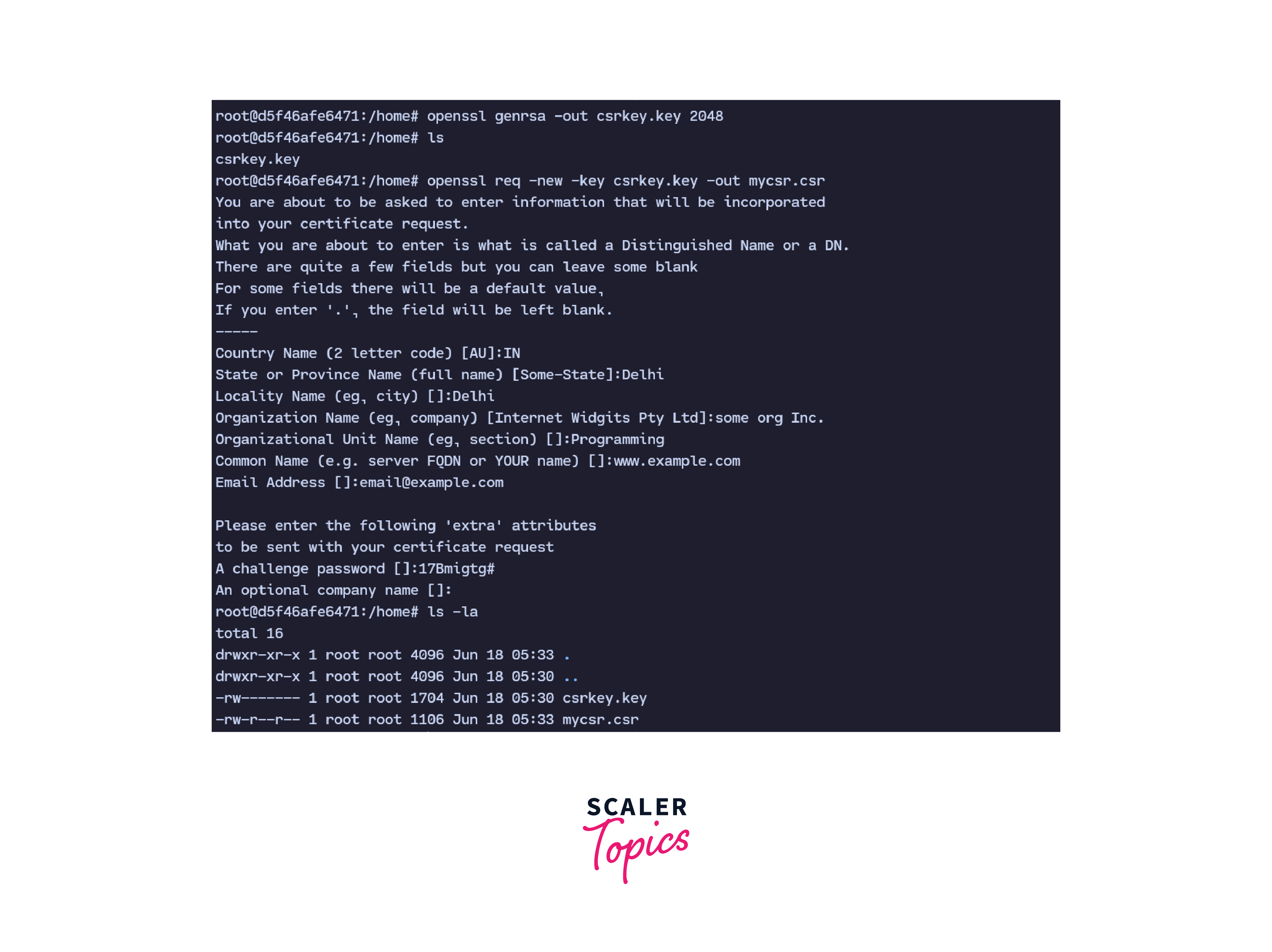
Now, to generate CSR in Linux using this private key, run the command:
Breakdown of what the previous command does:
- -new: Denotes a new request
- -key: Which key file to use
- -out: The name of the output file.
Once we run this command, it asks us for the following information:
- Country Name (2 letter code) [AU]: Name of the country where the organization is located in.
- State or Province Name (full name) [Some-State]: Full name of the state where the organization is located in.
- Locality Name (eg, city) []: The name of the city where the organization is located in.
- Organization Name (eg, company) [Internet Widgits Pty Ltd]: The name of the organization
- Organizational Unit Name (eg, section) []: The industry sector in which the organization operates.
- Common Name (e.g. server FQDN or YOUR name) []: The domain name of the organization which is purchasing the SSL certificate.
- Email Address []: Valid email address of the organization buying the SSL certificate.
Once this information is entered, this generates CSR in Linux in the current directory by the name mycsr.csr.
This CSR file is submitted to a Certificate Authority. The Certificate Authority then signs this CSR file with its private key. This signed file can then be used as a digital certificate for SSL encryption on your website.
The certificate generated with this command is private and should be kept confidential. Malicious actors can use this certificate to impersonate the identity of your organization.
Verifying a CSR file
Once we generate CSR in Linux, users should verify and validate the contents of the generated CSR file before it is sent to a Certificate Authority. This is to ensure that all the information entered for the creation of the certificate was valid and accurate.
To validate the contents of the CSR file, we run the following command:
Breakdown of the previous command:
- -text: Instructs OpenSSL to output the information from the certificate in plain text.
- -in: Points to the CSR file OpenSSL needs to read for validation.
- -noout: Instructs OpenSSL not to output the raw contents of the CSR file.
- -verify: This flag is self-explanatory. This flag instructs OpenSSL to verify the contents of the CSR file and outputs its content to plain text.

Self-signing the Certificate Using a Private key
After we generate CSR in Linux and it has been validated, it is shared with a trusted Certificate Authority like Verisign. But for testing purposes or for deploying a certificate locally, we can sign the certificate with our private key.
To self-sign a certificate, we run the following command:
Breakdown of the previous command:
- x509: The x509 is a multi-purpose subcommand used in OpenSSL for handling certificates. We can use this command to view certificate information, convert certificates to different formats, and sign the certificates.
- -in: Refers to input CSR file which will be used for signing.
- -out: Refers to the output name of the certificate that will be generated using the CSR file and the private key.
- -req: Denotes that the input is a CSR and not a certificate file.
- -signkey: The private key to be used for signing the digital certificate.
- -days: Digital certificates need to be valid for some specific number of days. This is done from a security perspective to make sure that old certificates are not used by malicious actors to impersonate your online presence. We pass in the number of days for which the certificate will stay valid.
Running this command creates the digital certificate file. This certificate can now be used to provide SSL encryption on your websites.
Conclusion
-
A Certificate Signing Request (CSR) is a block encrypted file shared with a trusted Certificate Authority (CA) to obtain an SSL certificate. This SSL certificate is used for data encryption with a website. A command line program called OpenSSL is used to generate CSR in Linux.
-
SSL certificates are of two types:
- CA-authorized certificates: These are certificates signed by a trusted Certificate Authority and are used for SSL encryption of internet-facing websites.
- Self-signed certificates: These are certificates self-signed by individuals using their private keys. These are used internally inside an organization or on an FTP server.
-
To generate CSR in Linux, we first need to install openssl. Then a private key is generated using OpenSSL and then a CSR is generated using this private key.
-
The generated CSR file and the key used to generate it are private and should be kept confidential.
-
A CSR file should be verified before being sent to a Certificate Authority to make sure the information saved inside the CSR is correct.
