Create GitHub Personal Access Token
Overview
An alternative to using a password to log into GitHub while using its APIs or via the terminal or command line is to use a GitHub Personal Access Token. It is intended to access GitHub resources on your behalf. Currently, Github supports two different types of tokens : one is fine-grained tokens and another one is classic tokens.
They are mostly advised due to the increased security they provide while logging onto GitHub. The creation and application of a token for authentication are covered in this article.
Introduction to Personal Access Tokens
The GitHub personal access token is a replacement for your password for authentication. You need to input your GitHub account name in place of the username and the created personal GitHub access token in place of your password when performing Git operations such as the git push or git pull that ask for credentials before beginning the operation.
You can use your Git client to cache your token so you don't have to manually enter it each time you perform an HTTPS Git operation. Git keeps temporary credentials until they expire in memory. The token can be kept locally in a text file so that Git can read it before processing each request.
There are two types of tokens that GitHub presently supports, one is a fine-grained token and another one is a classic token. It is recommended to you use the fine-grained tokens instead of classic tokens because Fine-grained tokens have several security advantages over the classic token. There are a few factors that we need to recognize about Personal Access Tokens :
- Resources accessible by each token should be owned by a single user or an organization and only specific repositories can be accessed by each of the tokens.
- Specific rights are assigned to each token, allowing for greater manipulation than the scopes of the default access tokens.
- Every token holds some expiration date.
- Any fine-grained tokens that have access to the organization's resources may need to have the owners' consent.
- Written access to public repositories that are not controlled by you or a group to which you do not belong is only available to holders of classic tokens.
- Collaborators which are external can only use the classic token to access organization repositories in which they are collaborating.
Additionally, business owners can limit personal access token usage within their businesses. GitHub believes that deleting the tokens that have not been used for a year is a good security practice. To increase security, it is also advised that you provide your access token with an expiration date.
Let's examine why these tokens are necessary :
- They are used to authenticate GitLab features that demand a username together with your GitLab login.
- Although they resemble group access tokens and project access tokens, they are linked to users rather than groups or projects.
- When two-factor authentication (2FA) is activated, they are mostly necessary.
Steps to Generate the Personal Access Token
To create a personal access token for the repository in your GitHub account, let's proceed now. To authenticate access to the GitHub API, GitHub functions similarly to an OAuth access token.
On GitHub, you can create a token using the following methods :
-
Select developer options from your GitHub account settings.
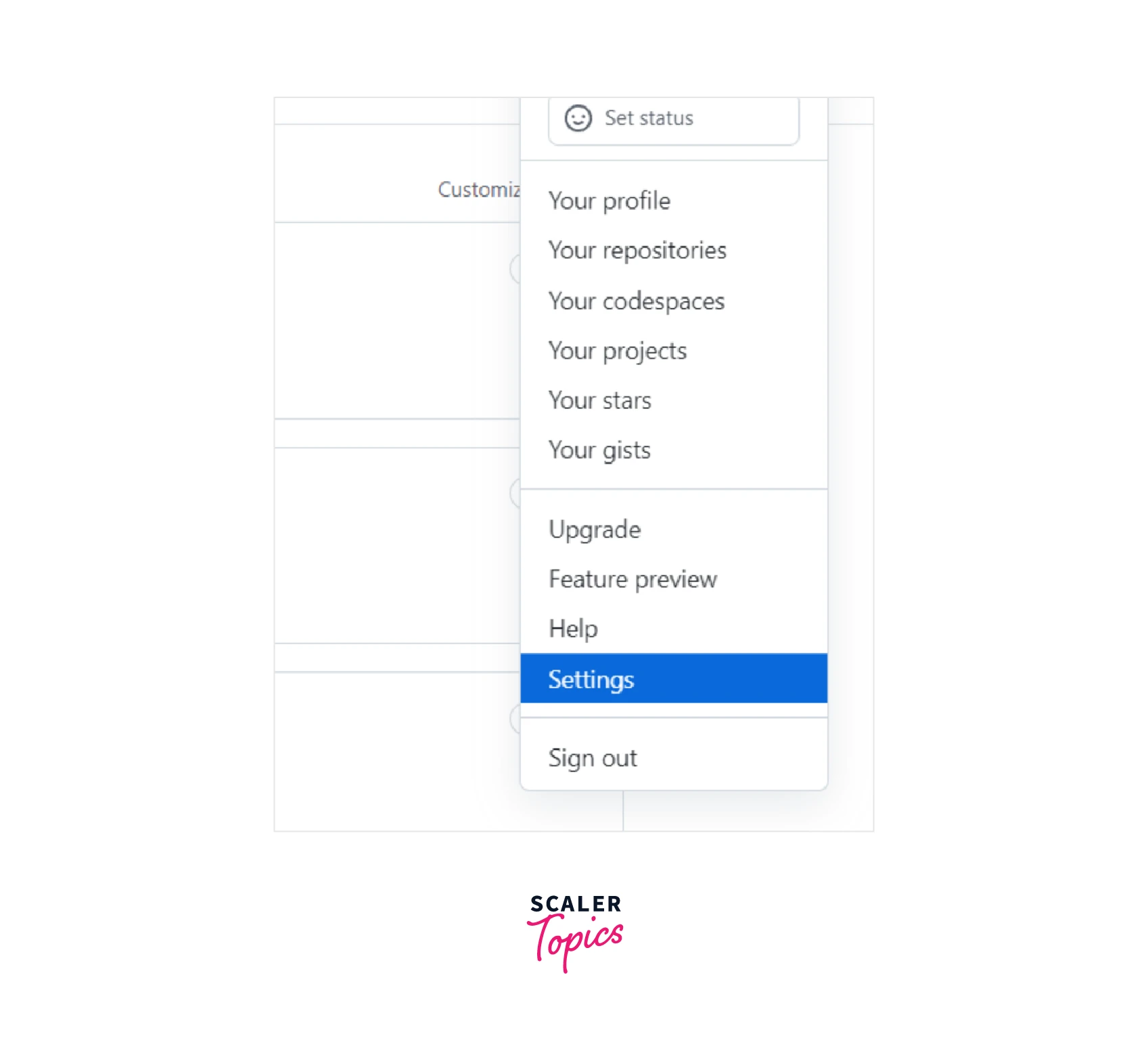
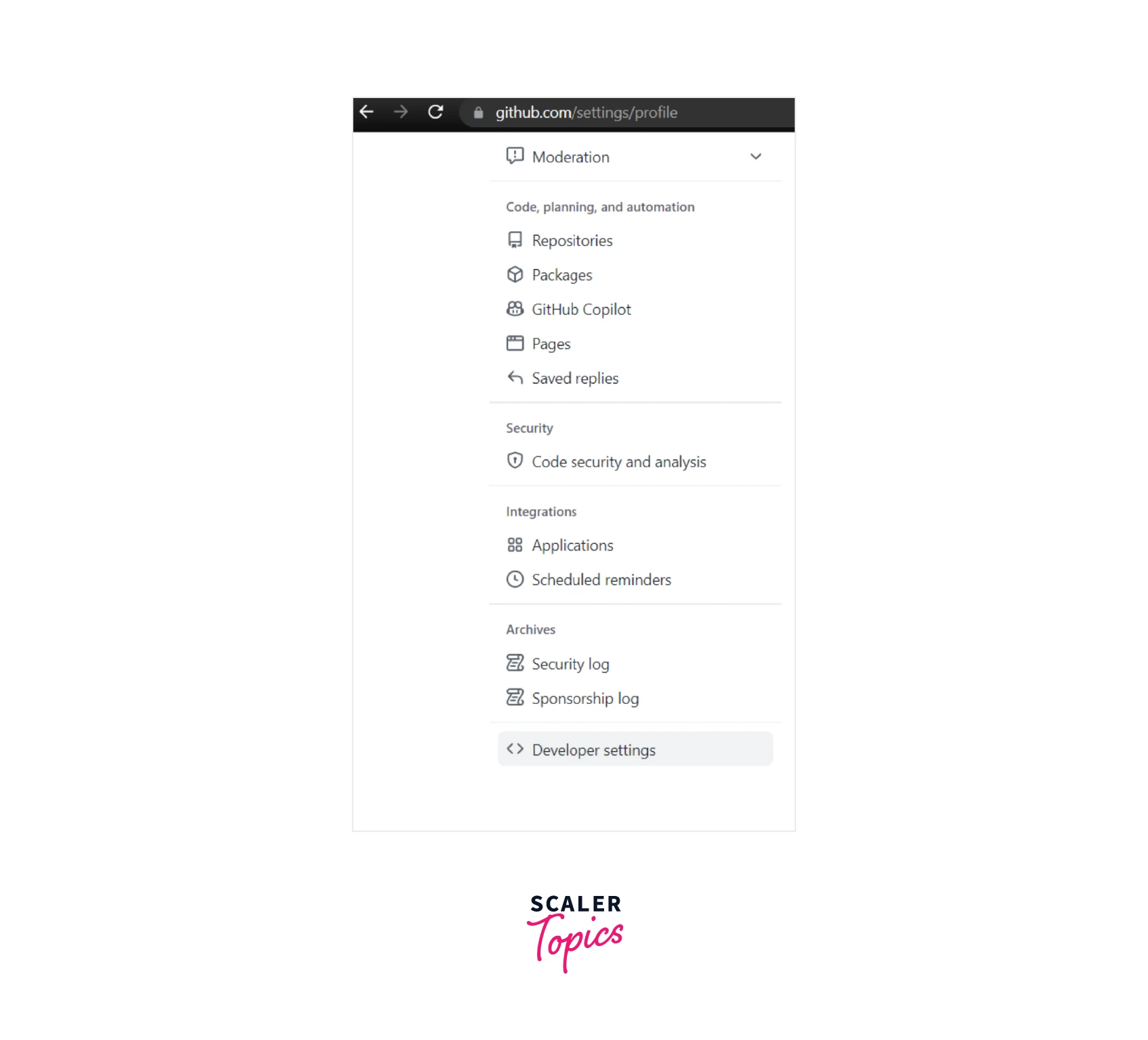
Go to the Personal Access Tokens menu, click Generate New Token, and re-enter the password if necessary.
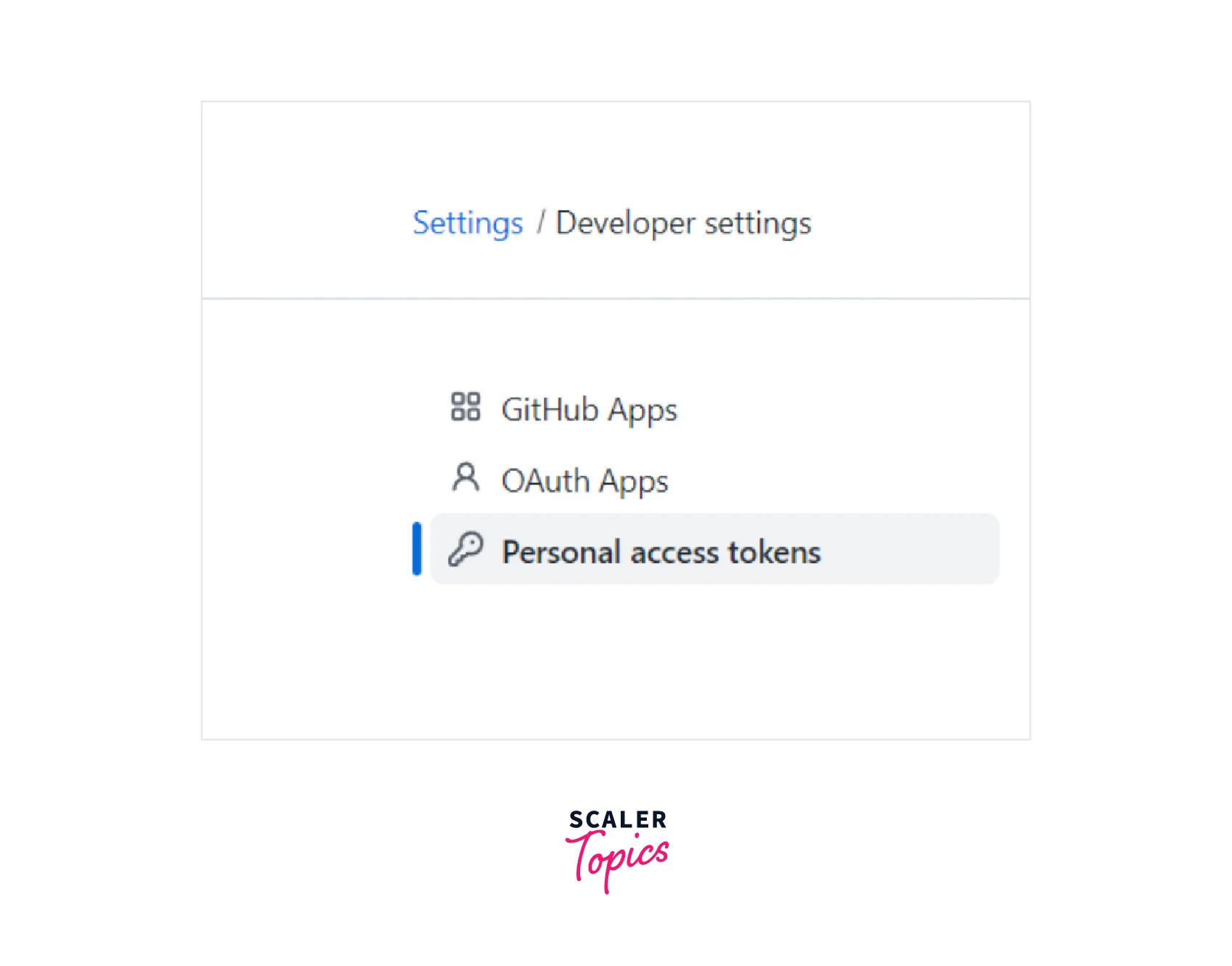
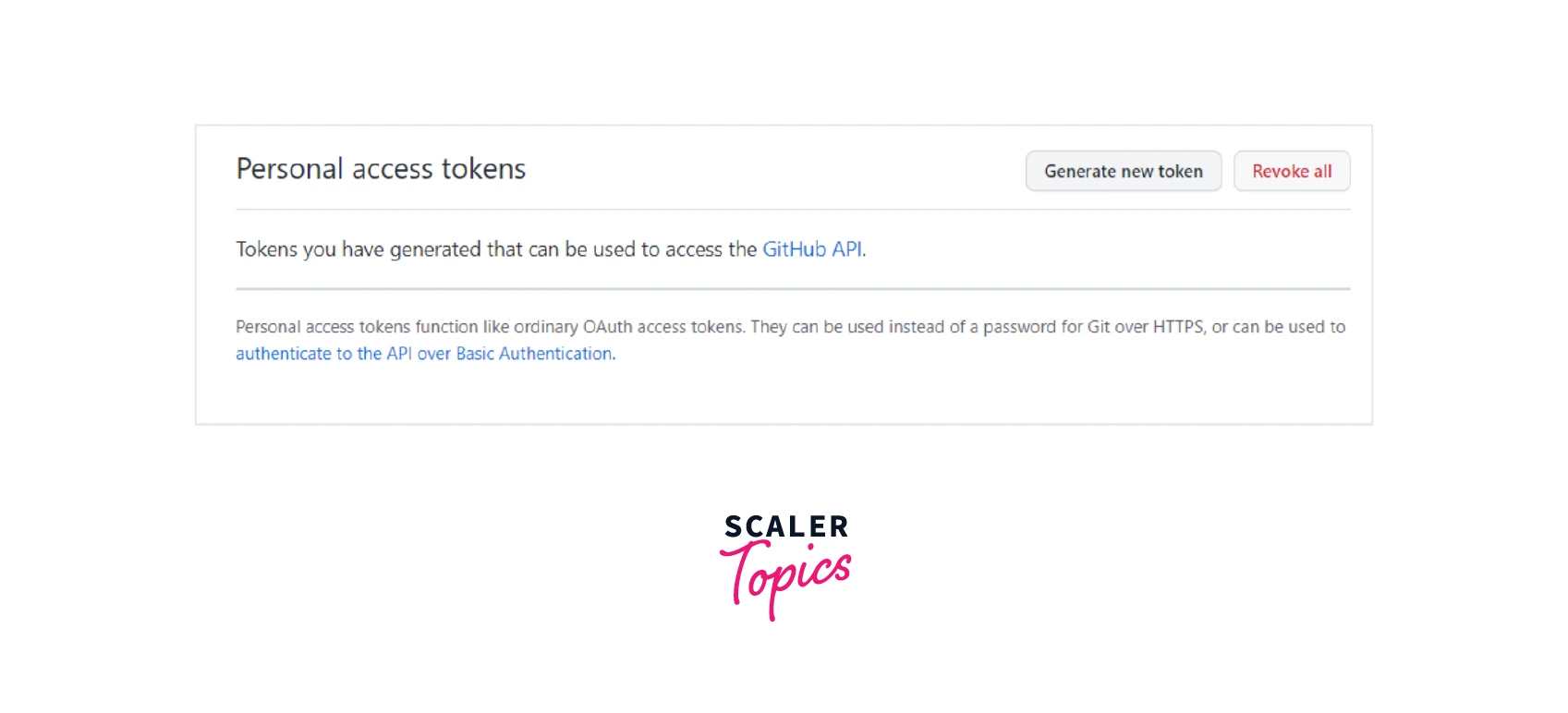
-
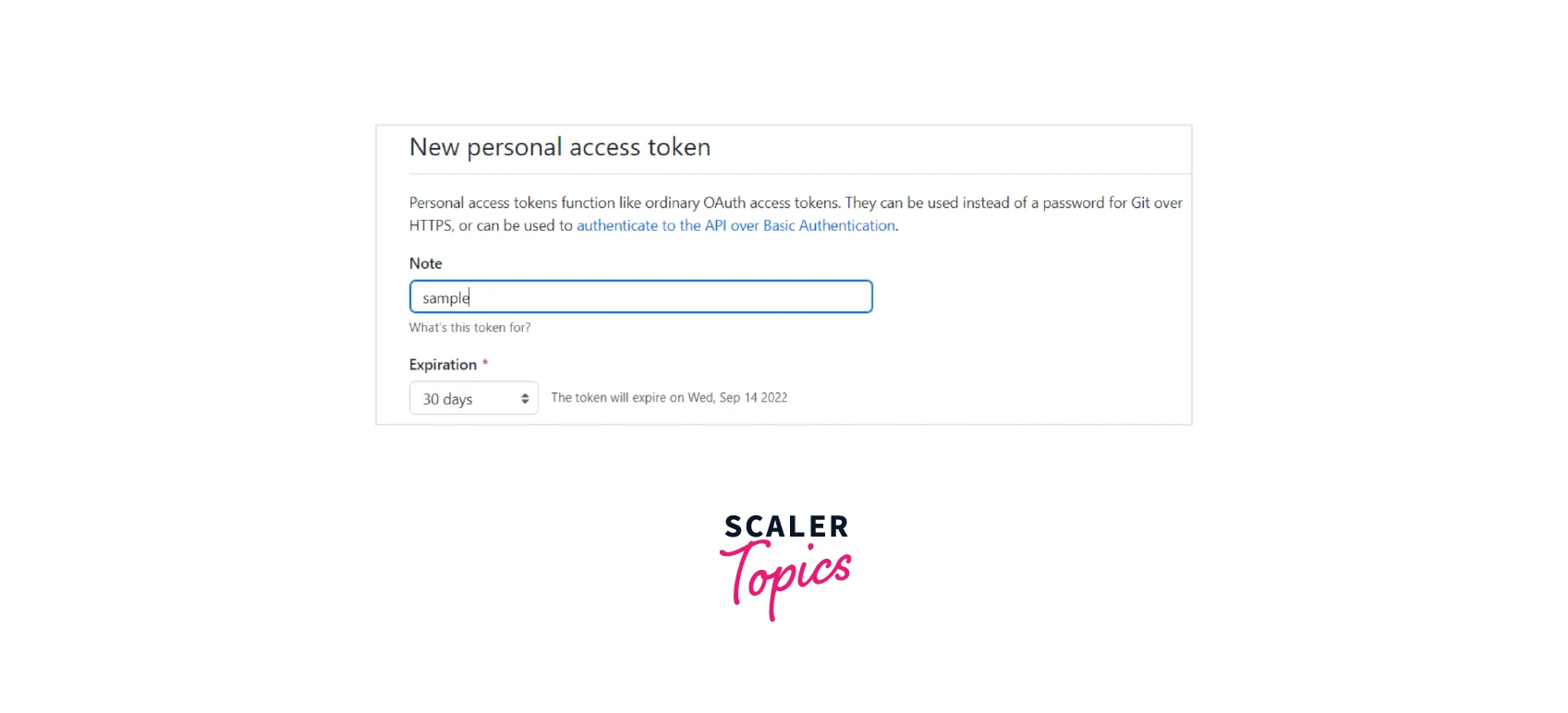
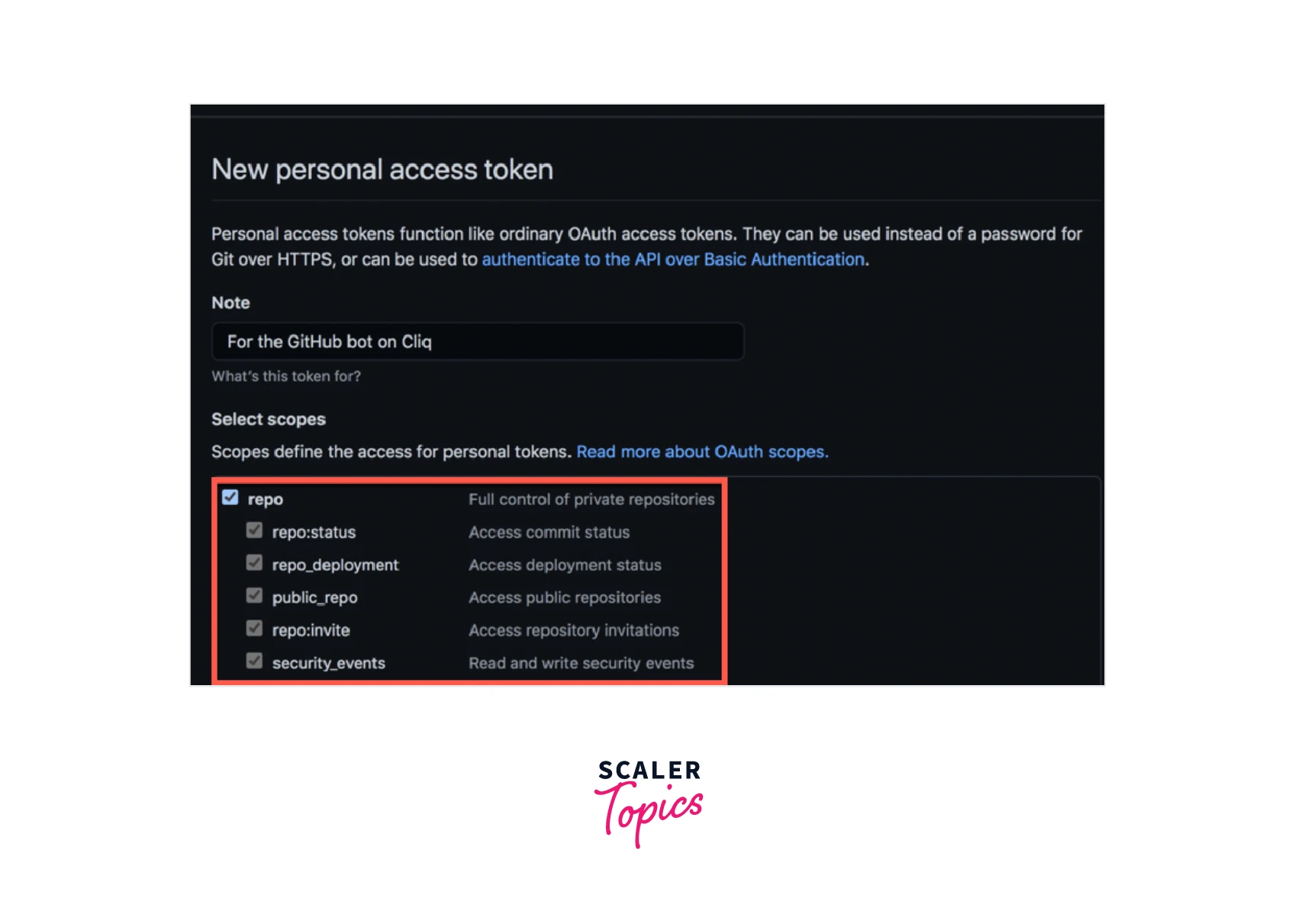
In the Note box area, enter a name for the GitHub token, and choose repo as the scope. The token is valid for all specified repository actions.
-
If you don't want the access token to expire, pick a date for its expiration or select "No expiration" to make it never expire.
-
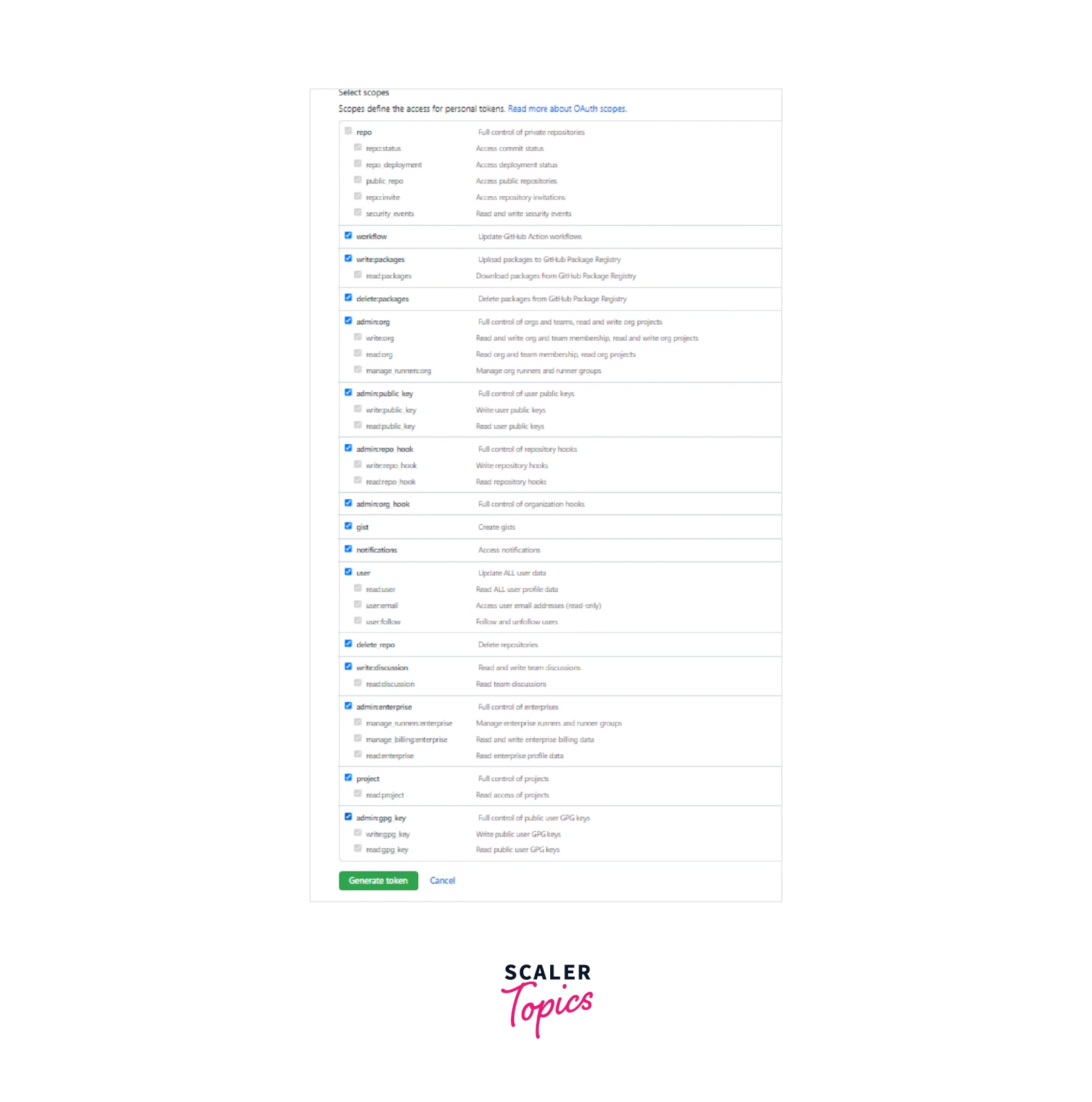
For complete access to the repository for your GitHub token, check the box next to each permission scope.
-
Click Generate Token.
-
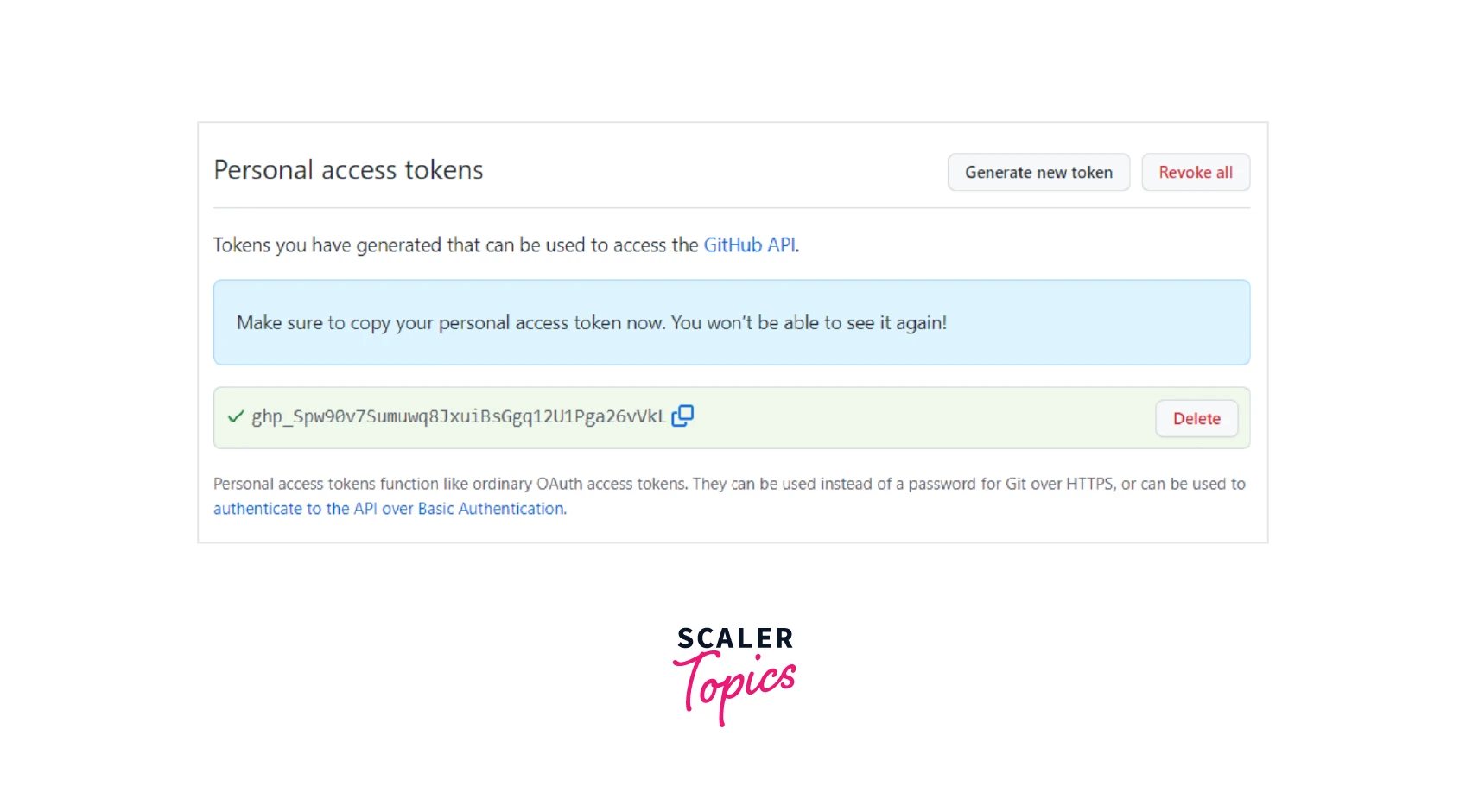
When executing HTTPS Git activities, be sure to copy your GitHub token and use it as your password.
Please take note that GitHub will only show the token once. Therefore, make sure to make a copy of the token and store it safely.
Revoke Personal Access Token
By doing the actions listed below, you can revoke your token at any time :
- Go to your avatar and click the Edit profile section in the top right corner.
- Navigate to the left side and select the Access Tokens menu.
- Next to the key, select Revoke in the Active Personal Access Tokens section.
You can also programmatically revoke the tokens as part of automation or testing. However, there is a requirement for that, and that is the ability to run a Rails console session against your GitLab instance with the necessary permissions. Type the following commands to programmatically revoke a token :
-
Start typing in the Rails console.
-
Run the command below to revoke the token from, say, example-token-string :
Using the Rails runner, the two commands mentioned above can also be condensed to a single-line shell command :
View the Last Time a Token was Used
Every 24 hours, the token's usage data is refreshed. When a token is used to perform a Git activity or to authenticate, GitLab counts it as having been utilized.
The steps listed below can be used to view the most recent use of a token :
- Click the Edit profile button next to your avatar in the top right corner.
- Select the Access Tokens menu from the left side of the screen.
- View the token's last used date and timestamp in the Active Personal Access Tokens section, which is located next to the key.
Additionally, you can view the expiration date of a token. They typically expire at midnight UTC on the date you specify.
- Every day at 1:00 UTC, GitLab checks to determine which tokens will expire during the following 7 days. Email notifications will be sent to the token holders.
- Every day at 2:00 UTC, GitLab checks to see whether the tokens are about to expire. Email notifications will be sent to the token holders.
Actions Based on the Assigned Scopes
When creating a token for a specified repo, certain rights can be granted, and those permissions can then be utilized to carry out operations according to their assigned scopes.
| Assigned Scope | Action |
|---|---|
| sudo | Once authenticated as an administrator, it grants permission to perform API actions as any user on the system. |
| api | This scope enables full read/to write access to the API, including all groups and projects, container registries, and package registries |
| read_user | This scope allows read-only access to the authenticated user's profile through the /user API endpoint. Your username, open email address, and complete name are all included in this. Additionally, under /users, read-only API endpoints are accessible. |
| read_api | All groups, projects, container registries, and package registries are accessible via this scope's read access. |
| read_repository | Private project repositories are accessible via read-only access in this scope. |
| read_registry | This scope allows read access to Container Registry images when the project is private and requires approval. It is available only when Container Registry is enabled. |
| write_repository | Private project repositories are accessible via this scope in both read and write modes. |
| write_registry | When a project is private and requires approval, this scope enables read/write access to Container Registry images. Only when Container Registry is enabled is it accessible. |
Alternatives to Personal Access Tokens
Git Credential Manager is a secure OAuth alternative to Personal Access Tokens for Git over HTTPS. Simple manual authentication using your password is another option.
Conclusion
- A GitHub Personal Access Token is an alternative way to authenticate to GitHub using API's of GitHub or via a terminal/command line instead of a password.
- It is designed to access the resources of GitHub on your behalf and presently there are two types of access tokens supported by Github, one a fine-grained token and another one a classic token.
- You can use your Git client to cache your token so you don't have to manually enter it each time you perform an HTTPS Git operation.
- To increase the security, you are advised to provide your token's expiration date.
- GitHub believes that deleting the tokens that have not been used for a year is a good security practice.
- When creating a token, certain rights can be granted, and those permissions can then be utilized to carry out operations according to their assigned scopes.
- Every 24 hours, the token's usage data is refreshed. When a token is used to perform a Git activity or to authenticate, GitLab counts it as having been utilized.
- You need to input your GitHub account name in place of the username and the created personal GitHub access token in place of your password when performing Git operations such as the git push or git pull that ask for credentials before beginning the operation.
- Git Credential Manager and Simple manual authentication using your password is a secure OAuth alternative to Personal Access Tokens for Git over HTTPS.
- Collaborators which are external can only use classic tokens to access organization repositories in which they are collaborating.
- They typically expire at midnight UTC on the date you specify.
- To authenticate access to the GitHub API, GitHub functions similarly to an OAuth access token.
