How to Give Root Privileges to a User in Linux?
Overview
Are you a Linux user who wants to grant root privileges to another user? Perhaps you have a team member named scaler_topics who needs elevated access to perform administrative tasks on your Linux system.
Linux offers various ways to grant root privileges, allowing them to execute administrative commands and access critical system files. By granting root privileges, you delegate a significant amount of power and responsibility to the user, so it's crucial to understand the implications and proceed cautiously.
In this article, we will explore step-by-step methods of how to give root privileges to a user in Linux. Additionally, we will acquire the knowledge of confirming the user's possession of root privileges. Let's get started, shall we?
Using usermod to Add Root Group
To provide root privileges to a specific user, such as scaler-topics, an effective technique involves utilizing the usermod command. The usermod command allows you to modify user account details, including group membership. To add root privileges to the user, you can add them to the root group using the usermod command.
Here's how to give root privileges to a user in Linux using the usermod command:
- Open a terminal on your Linux system.
- Execute the following command to add the user scaler_topics to the root group:
The -aG flag adds the user to the root group without removing them from other groups they belong to.
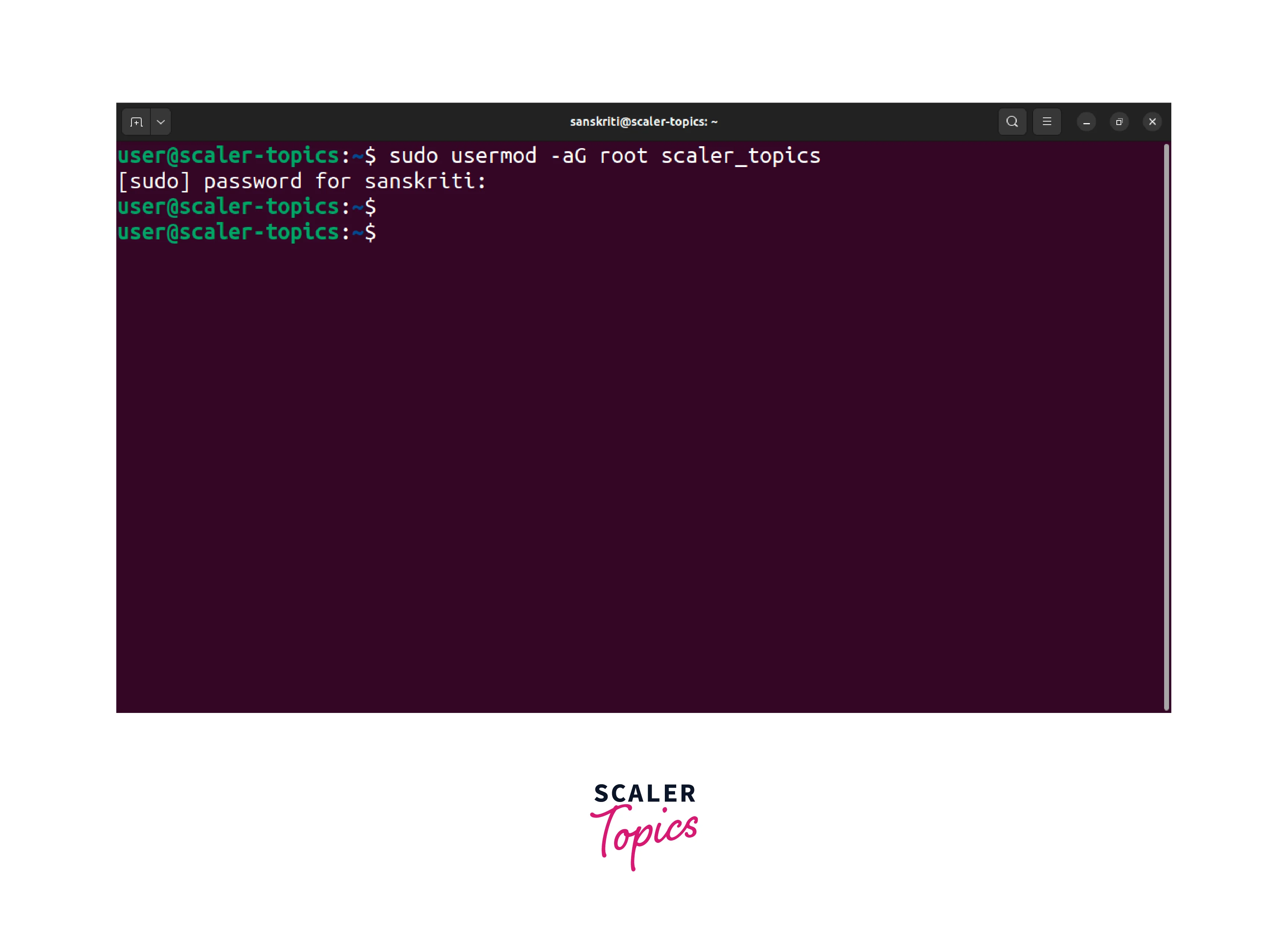
- Once the command executes successfully, the user scaler_topics will have root privileges. Now, they can run administrative commands using the "sudo" command.
- To verify the user scaler_topics now has root privileges, open a terminal and execute the following command:
This command will display the groups the user scaler_topics is a part of. Check if the output contains the root group.
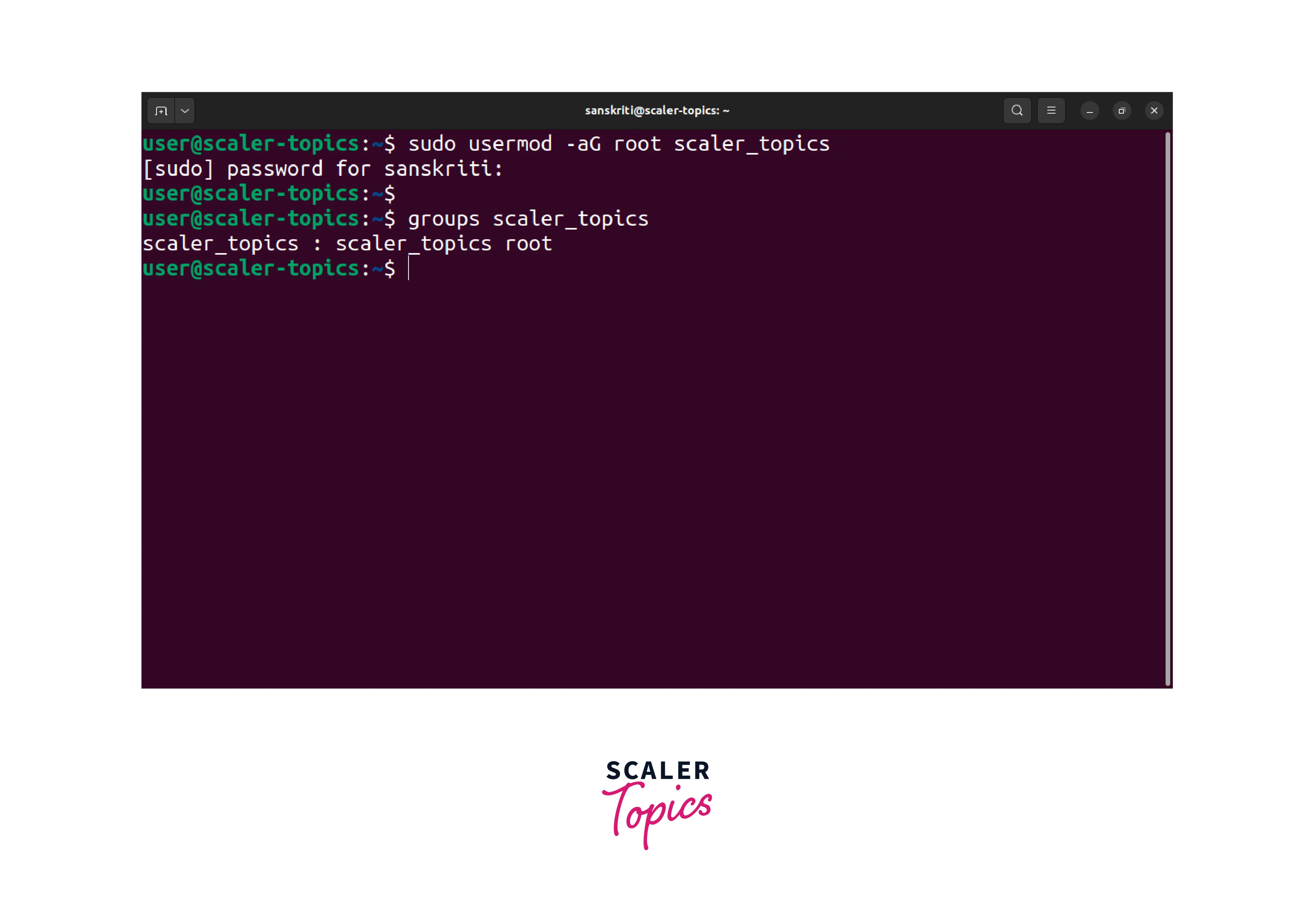 As you can see above, the root group is listed, which means the user scaler_topics has been successfully granted root privileges.
As you can see above, the root group is listed, which means the user scaler_topics has been successfully granted root privileges.
useradd Command to Add Root Group
Another method to learn how to give root privileges to a user in Linux, named scaler_topics, involves using the useradd command with appropriate options. This method creates a new user account and assigns it to the root group during the user creation.
Here's a step-by-step guide:
- Open a terminal and run the following command to create a user scaler_topics and assign them to the root group:
The -ou option sets the user ID (UID) to 0. The -g option sets the primary group ID (GID) to 0. The value 0 of the UID and GID corresponds to the root user and the root group.
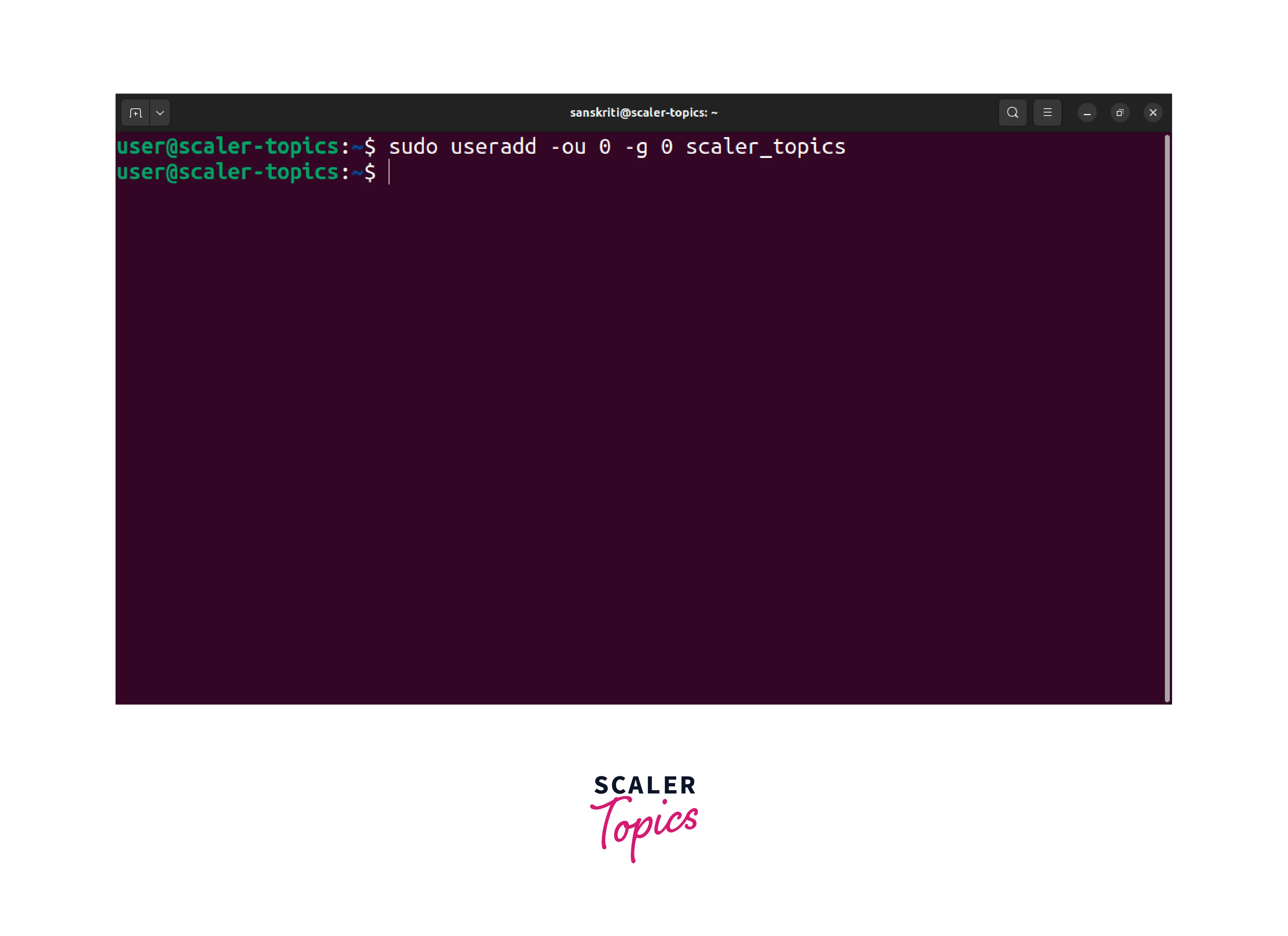
- The execution of this command will result in the user account scaler_topics creation with root privileges.
- To confirm the successful assignment of root privileges to the user scaler-topics using the useradd method, you can open a terminal and execute the provided command:
This command will display the user ID (UID) and group ID (GID) information for the user scaler_topics. Check if the UID and GID values are both set to 0.
 As you can see that both values are 0, which means the user scaler_topics has root privileges.
As you can see that both values are 0, which means the user scaler_topics has root privileges.
Now that you have learned how to give root privileges to a user in Linux using the useradd command, you can confidently manage user access on your system.
If you want to delete the user created using the useradd command, refer to this link for instructions on removing the user safely.
:::
Editing /etc/passwd File to Give Root Privileges to a User in Linux
Alternatively, you can manually edit the /etc/password file and grant root privileges to the user *scaler_topics*. The /etc/passwd` file stores essential user account information, including the UID, GID, and the user's assigned shell.
By following the below instructions on how to give root privileges to a user in Linux, namely scaler_topics, you can securely delegate administrative tasks:
- Open a terminal on your Linux system.
- Execute the following command to open the /etc/passwd file in a text editor:
This command opens the file using the nano text editor with root privileges.
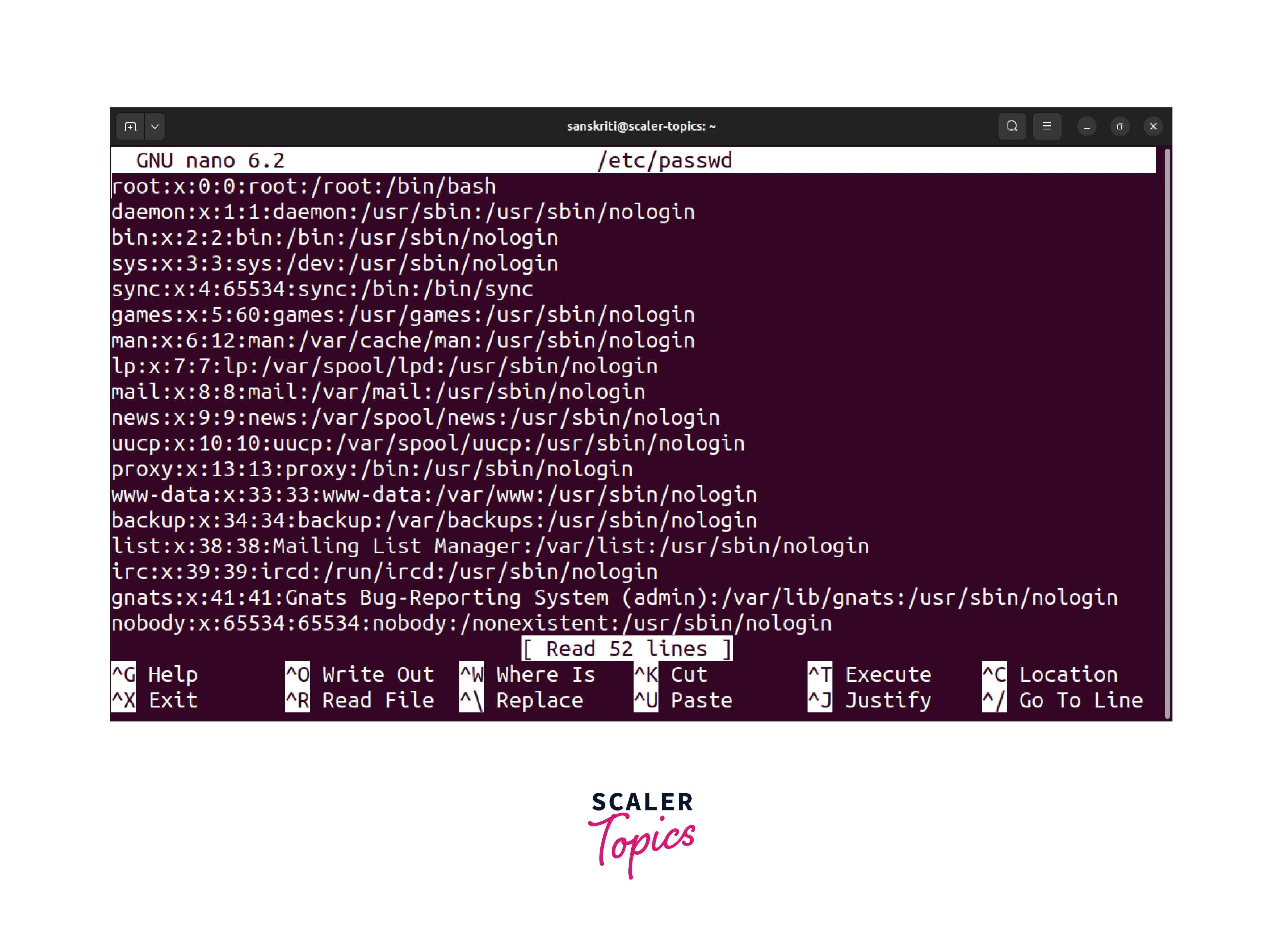
- Locate the line that corresponds to the user scaler_topics.
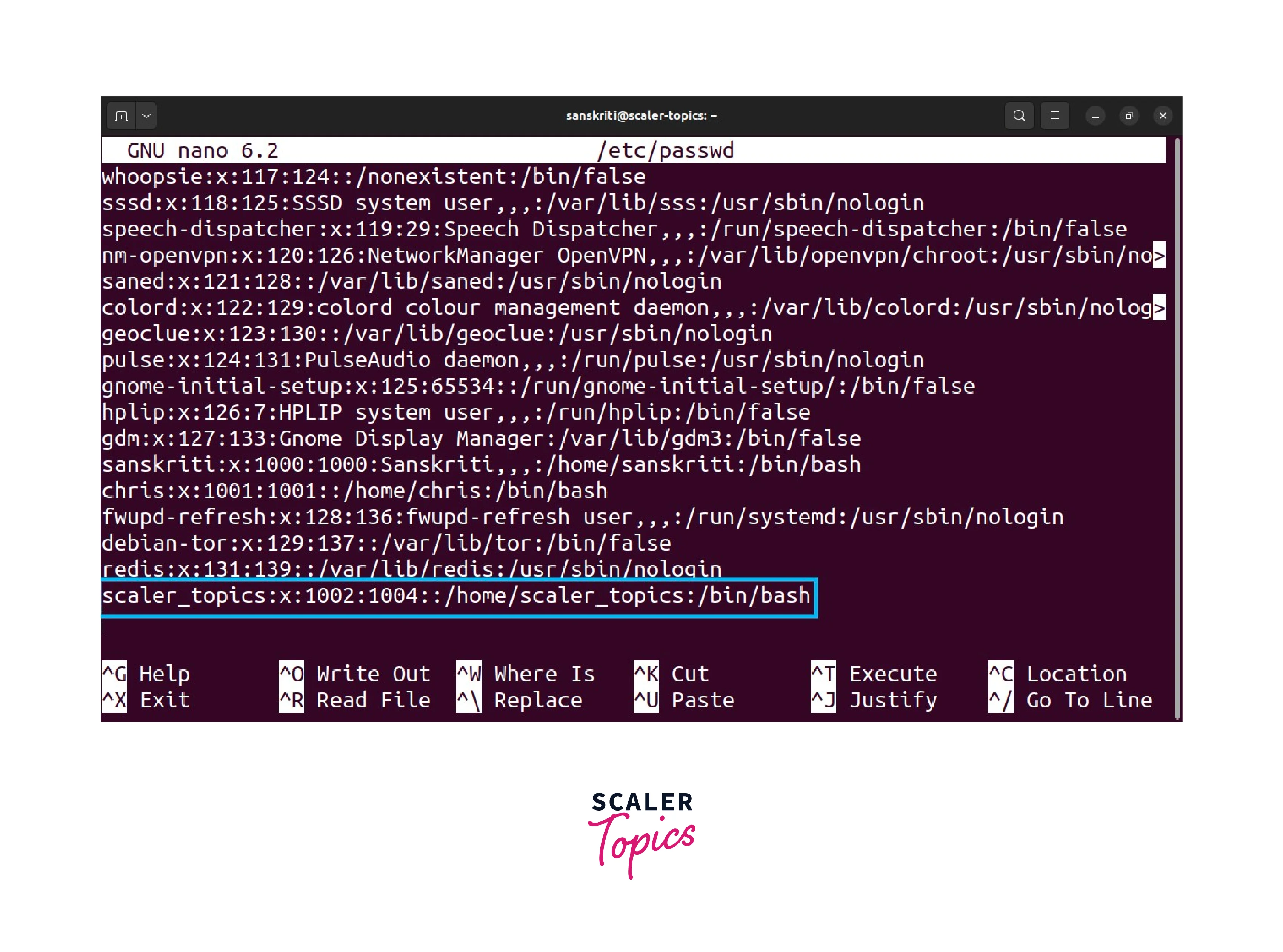
- Edit the line, specifically the user's UID and GID, to set them to 0.
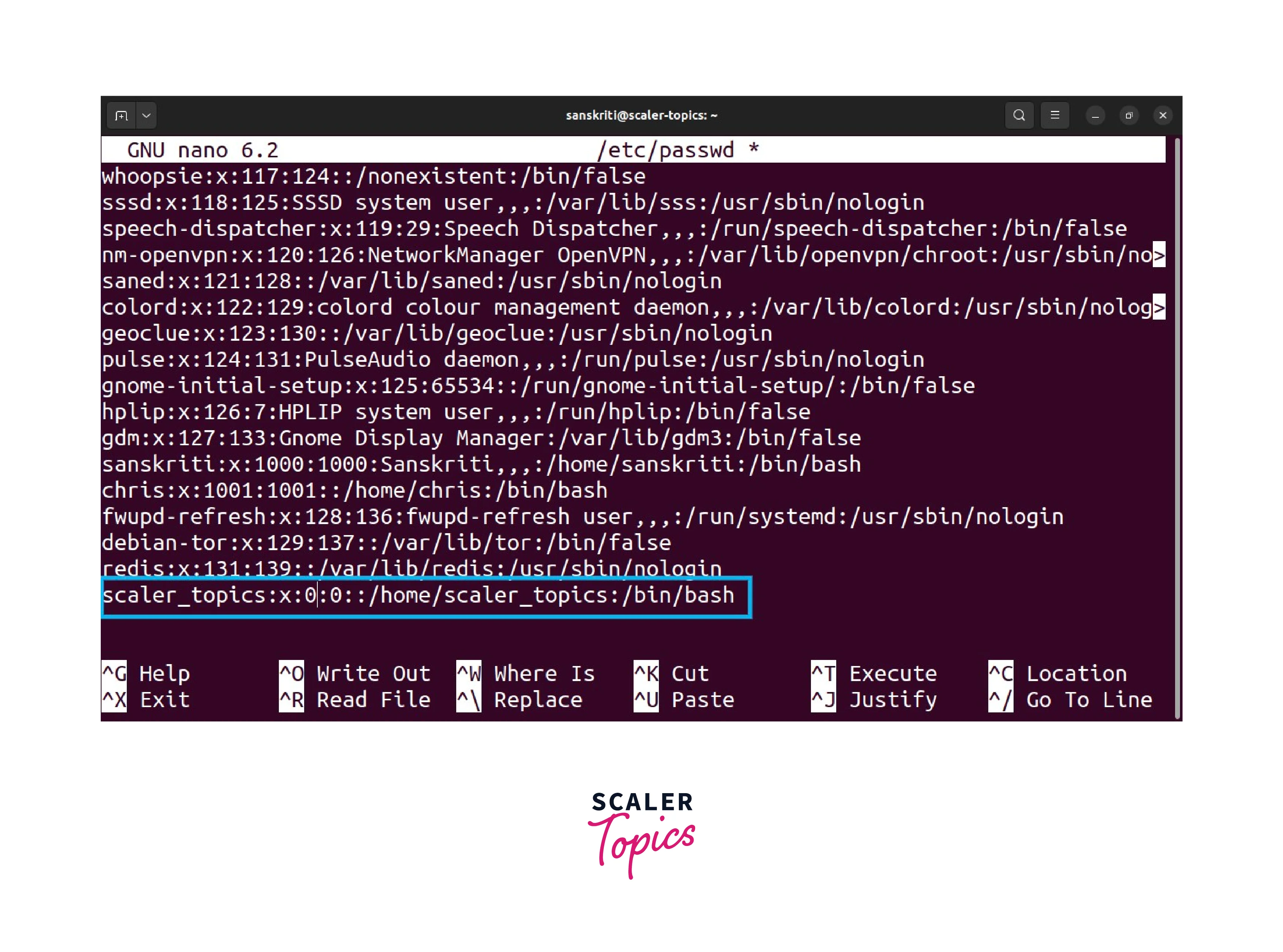
- Save the changes and exit the text editor.

- The user scaler_topics will now have root privileges.
:::
Setting a Sudo User
Using the sudo command is a common practice in Linux to grant temporary root privileges to specific users. By configuring a user as a sudoer, they can execute commands as the root user while providing their password.
Here's another method of how to give root privileges to a user in Linux to set up a user a sudo user :
- Open a terminal on your Linux system.
- Execute the following command to edit the sudoers file using the visudo command:
This command opens the sudoers file in the default text editor.
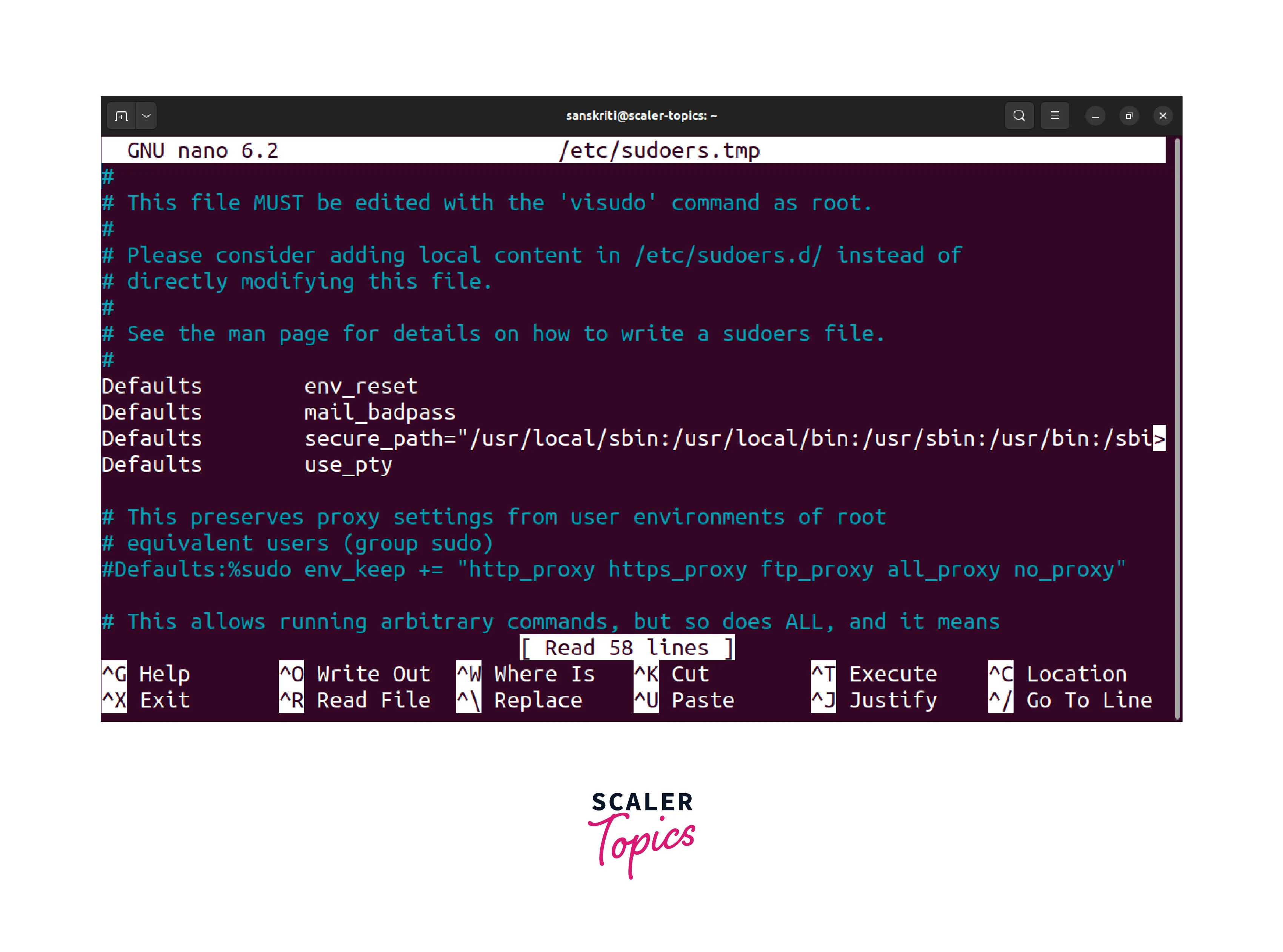
- Scroll down to the relevant section in the sudoers file.
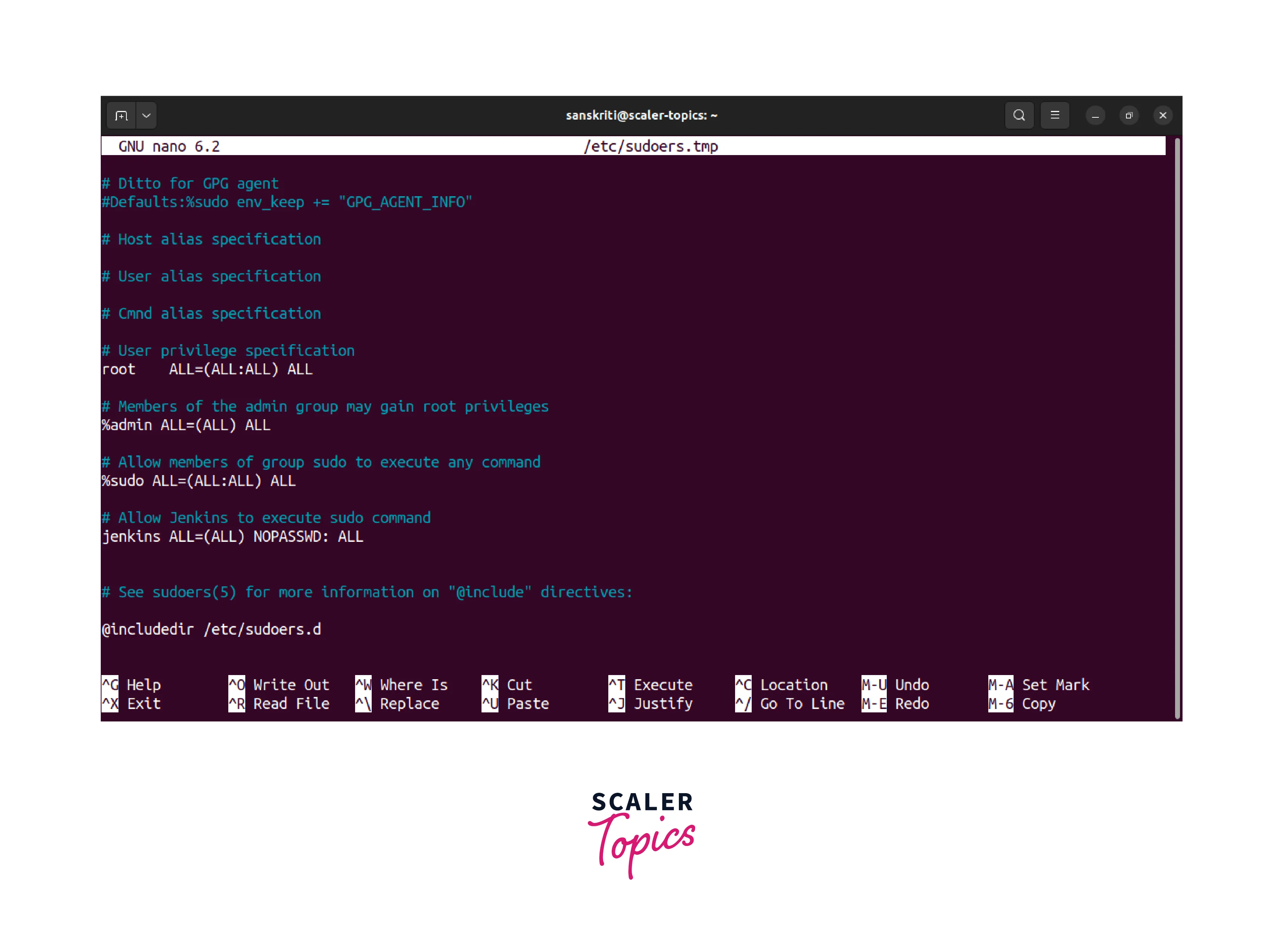
- Add the following entry to grant root privileges to the user named scaler_topics:
scaler_topics ALL=(ALL:ALL) ALL Using this line, the specified user scaler_topics is granted full root privileges, enabling them to execute any command as any user on any host.
Using this line, the specified user scaler_topics is granted full root privileges, enabling them to execute any command as any user on any host. - Save the changes to the sudoers file and exit the text editor.
- The user scaler_topics will now have root privileges on the system.
By following these instructions on how to give root privileges to a user in Linux, you can securely delegate administrative tasks. Choose the method that suits your requirements and proceed with caution to ensure the security and stability of your system. Happy administering!
FAQs
Now let's address some frequently asked questions related to how to give root privileges to a user in Linux.
Q. Can I give root privileges to multiple users simultaneously?
A. Yes, you can grant root privileges to multiple users simultaneously. Follow the steps mentioned above for each user you want to give root access to.
Q. How can I remove root privileges from a user?
A. To remove root privileges from a user, you can use the deluser command with appropriate options. Execute sudo deluser username root to remove the user from the root group.
Q. Is it recommended to give root privileges to regular users?
A. While it is good to know how to give root privileges to a user in Linux, granting these privileges to regular users is generally not recommended unless necessary. It is best practice to follow the principle of least privilege and only give root access to trusted administrators.
Q. Are there any risks associated with granting root privileges to a user?
A. Yes, granting root privileges to a user comes with risks. It gives them control over the whole system, which can be dangerous if misused. It is vital to grant root privileges to trusted users only and exercise caution when performing administrative tasks.
Q. How can I verify if a user has root privileges?
A. You can use the sudo -l -U <username> command to check the sudo privileges of a specific user. It will display the allowed commands and access level for that user. If the output of this command does not display any errors and instead provides output, it means that the specified user (<username>) has some level of sudo privileges. The result will typically list the allowed commands the user can execute with elevated privileges.
:::
Conclusion
In this article, we have explored different methods on how to give root privileges to a user in Linux. Here are the key takeaways from this article:
- The usermod command adds users to the root group and provides root privileges. It allows you to modify user account details, including group membership.
- The useradd command with appropriate options can create a new user account and assign it to the root group during user creation, effectively granting root privileges.
- Manually editing the /etc/passwd file modifies the user's UID and GID, granting them root privileges. However, exercise caution when editing system files manually.
- Setting up a user as a sudo user by configuring the sudoers file allows them to execute commands with temporary root privileges, providing a more controlled approach.
When granting root privileges, it is vital to adhere to the principle of least privilege, granting these privileges only to trusted users who require them for specific tasks. Regular users generally do not need root access for their day-to-day activities.
