What is Kerberos and How Does Kerberos Work?
Overview
To secure and protect the user's credentials, Kerberos was designed. It keeps the passwords out of insecure networks, even after the user's identities have been verified. This ensures security. Kerberos offers a centralized authentication server that functions by authenticating the credential/ ticket. Sessions of the authorized users to the servers and vice versa.
Introduction
With Kerberos, users can securely log in to their confidential accounts without worrying if anything could be hacked. Kerberos offers a centralized authentication server that functions by authenticating the credential/ ticket. Sessions of the authorized users to the servers and vice versa. As part of the Kerberos Authentication, it is the database and the server that is utilized for the client authentication. A third-party server popularly known as KDC or Kerberos Key Distribution Center (KDC) is run by Kerberos. Every user, along with the service over the network, is known as the principal in the Kerberos environment.
What is Kerberos?
While entering your credentials to log in to specific sites, have you wondered how magically you get authenticated and get access to the file servers, email servers, and other resources?
Kerberos runs in the background and protects your credentials from getting accidentally leaked or hacked.

To secure and protect the user's credentials, Kerberos was designed. It keeps the passwords out of insecure networks, even after the user's identities have been verified. This ensures security. Kerberos offers a centralized authentication server that functions by authenticating the credential/ ticket. Sessions of the authorized users to the servers and vice versa. Kerberos works as an authentication protocol for the various end-users/client and applications.
Developed in the 1980s at MIT, the name Kerberos originally refers to the three-headed dog named Hades who guarded hell according to Greek mythology. Later Microfost also leveraged this protocol and refined it for inclusion in Windows 2000. Since then, Kerberos has worked as an open-source protocol.
How does Kerberos Work?
For many organizations, Kerberos is proving to be the number one choice when it comes to offering a credible security solution. But does it do that? Let us explore more how Kerberos authentication works to provide security.
Kerberos implements what is widely popular as symmetric key cryptography along with its vital distribution center (KDC) for authenticating and validating the correct user's identities.
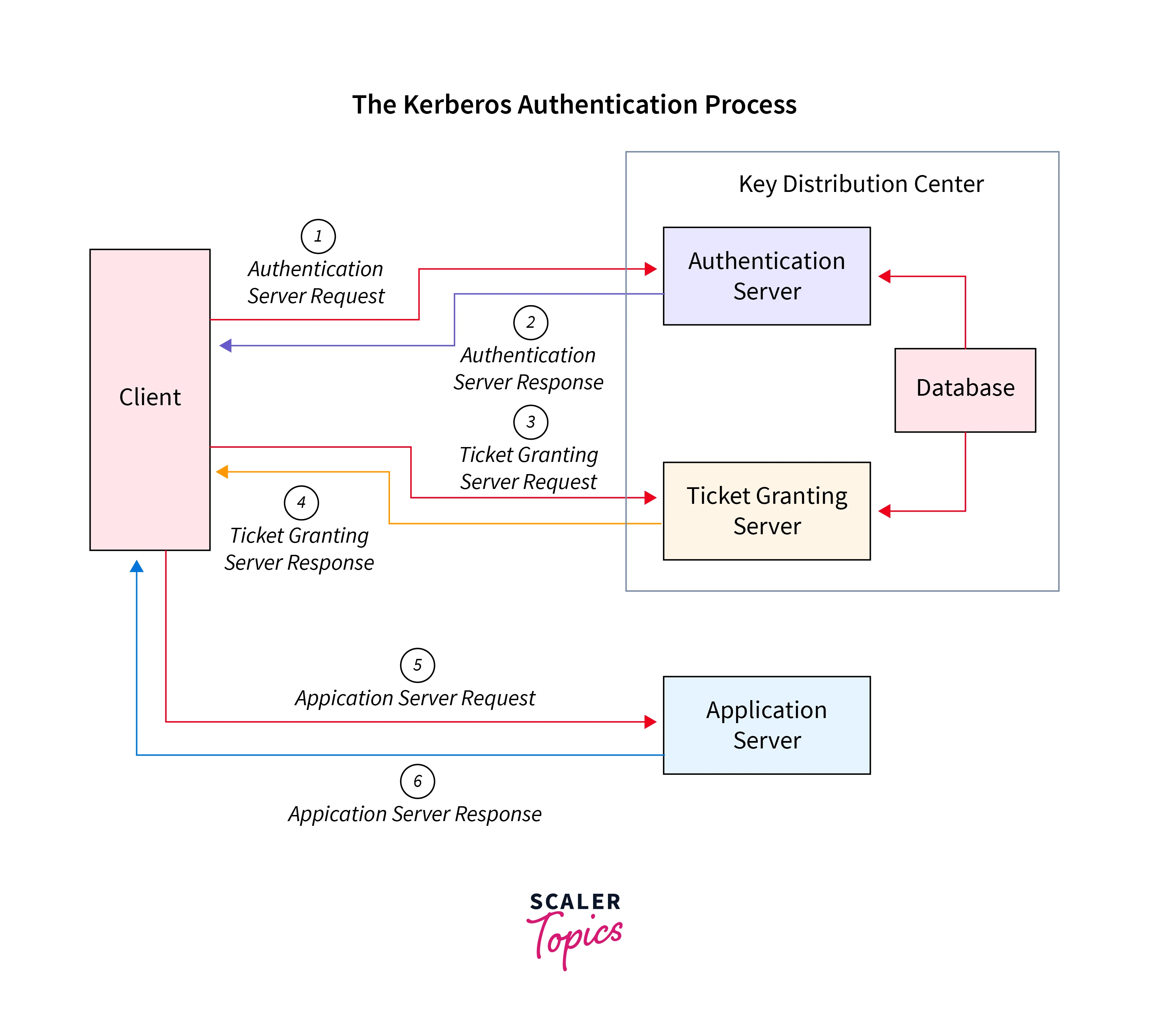
Three critical aspects are required in the Key distribution center:
- First, the ticket-granting server (TGS) shall connect the user to the service server (SS).
- Second, for storing the password and identification related to the verified users, the Kerberos database is used.
- Third, for offering initial authentication, an authentication server (AS) is required.
While Kerberos authenticates the identity of the users, it stores the defined ticket created for each session over the client's device. A Kerberos-aware service sees for this session ticket instead of the password. It is in the Kerberos environment where the entire process of authentication takes place. In this environment, a KDC gets authorized to authenticate all three components that are service, host, or the user.
The entire process around Kerberos authentication involves the core components as discussed below:
- Starting, it is the client that initiates the service request on the user's behalf
- Then it's with the server that shall be hosting the service which is needed to access that is retired by the user.
- The authentication client is performed by the Authentication Server. Once successful, the client receives the ticket-granting ticket (TGT) or something similar to a user authentication token that ensures that the client is correctly authenticated.
- The Key Distribution Center contains three components, namely: the Authentication Server, the Ticket Granting Service, along with the Kerberos database.
- Also, the service tickets are issued by the ticket-granting service.
What is Kerberos Used for?
You can find the implementation of Kerberos authentication in most places in this digital world. However, it gets its primary usage in security systems which are highly dependent on reliable auditing along with authentication features.
-
Various security where Kerberos is utilized and implemented are:
- Posix authentication
- Active Directory
- NFS
- Samba
-
Kerberos authentication also finds its implementation in alternative authentication systems with SSH, POP, and SMTP.
What does Kerberos Authentication Protocol do?
So far, we have learned how Kerebors works and what it is utilized for. Let us explore in the actin of the article what is it that the Kerberos authentication protocol does.
Previously it was MIT that developed the Kerberos authentication protocol for its project called Athena. The name that Kerberos gets is from Greek Mythology, where the three-headed dog of Hades was considered to guard hell.
This name was selected as the Kerberos authentication protocols represent all three:
- Client/ End User.
- Application Server/ Network Resource
- Key Distribution Center
Key Distribution Center:
The Key Distribution Center own the liberty to grant ticket in the Kerberos. To prove their identities, various hosts are allowed. Also, the developer who is intended for the Kerberos' authentication has access. This also means that they can support authorizations.
By the three components mentioned above, Kereberos can authenticate the trusted host authentication over the untrusted networks. It makes sure that the network resources are only accessed by authorized users. Also, it offers AAA security. Here, the AAA stands for Authentication, Authorization, and Accounting.
Previously it was developed to only authenticate the MIT developer who was working on a project for the required systems securely. But since then, Kerberos has found its implementation in various places. It now helps to authorize the users too. When many systems or applications were transferred unencrypted passwords, Kerberos came into play, enabling security to this transfer. They ensured that hackers get denied if they tried to access any of the passwords.
Hence, the Kerberos authentication development was out of necessity. The people who designed Kereberos were B.C. Neuman, S.P. Miller, J.I. Schiller and J.H. Saltzer.
Advantages of Using Kerberos Authentication
While we so far studied what is Kerberos authentication and how it works. Let us quickly consolidate the key benefits offered by the Kerberos authentication to secure and protect your cybersecurity setup by implementing the same.
- Effective Access Control: Kerberos authentication allows its users with a single key point to help it keep a defined track of logins as well as security policy enforcement.
- Session Key Tickets are Active for a limited period: Every Kerberos session critical ticket, when generated, is active until its expiry date. This ticket has a timestamp, the entire data, and the duration until it remains valid and can authenticate. All this is entirely controlled by the administrator.
- Mutual Authentication: In the Kerberos authentication, we can see mutual authentication. With both, service systems and end-users both can authenticate each other.
- Authentication can be reused: It is seen that the authentication via the Kerberos authentication is reusable, reliable as well as durable. With the Kerberos authentication, each end-user gets verified via the system only once. Now until the session key ticket is active, that is, before its expiration date. The end user could easily enter their personal information for authentication and authorization purposes.
- Security Measure is Diverse, Secure, and Strong: The diverse security protocols employed by Kerberos authentication are cryptography, various secret keys, or authorization via a third party. This helps to create a strong, protected, and secure defense. All the remote access keys are encrypted, and it is made sure that the passwords don't get sent over the networks.
Kerberos Objects Concepts and Terms
The purpose of Kerberos authentication revolves around password management. So that no passwords get transmitted over the network, Kerberos endures this security. The passwords are instantly discarded and are not left over in the client systems once it is utilized. While storage is concerned, no passwords should be present in plain text format. And each session must utilize one password. In addition, there is a centralized server where all the information related to the authentication information is stored.
This implies three points, as stated below:
- An administrator can restrict access from a centralized server for any client.
- All the services can be accessed via a single-user password.
- There are fewer complications in protecting the user information as only one server needs to be secured.
- For the Kerberos authentication, all the entities, once prompted, must authenticate each other upon prompt.
Kerberos Crucial Terms
Various entities are utilizing the Kerberos protocols stated below:
- The Kerberos Principals: It represents a distinct ID that is allotted to the ticket. It is more or less similar to a user ID for many users. Kerberos uses any one of the following information to identify a principal:
- For users: Via the username, while for hosts, Kereberod looks for the word host. For services, the Kerberos looks for the word principal as its the name of the service.
- An optional identifier is also used for finding the defined hostname
- One can find the Kerberos name explicitly defined in which the Kerberos server is operating.
- The Kerberos Application Servers: This provides access to the resource end-users.
- Kerberos KDC: With the Kerberos Key Distribution Center, access is offered to the resources, like terminal emulation as well as remote computing.
- The Kerberos Database: Users can find every principal recorded over the database. This database works as a centralized repository. Defined client identification is also captured under the Kerberos Database, along with their access.
- The Kerberos Authentication Service: Under the Kerberos Authentication Service, the Ticket Granting Ticket (TGT) is granted to the clients.
- The Kerberos Ticket Granting Service: In the Kerberos Ticket Granting Service, depending on the TGT, the authentication is granted.
- Once the authentication is granted, an authentication ticket is presented to the user. The client can implement the authentication ticket to get the tickets for allowing the application service.
The Core Components of Kerberos
The core components of the Kerberos Authentication workflow are described below:
- Client: For initiating any communication for the service requests, the client acts for the user.
- Server: For any service a user wants to access, the server helps with the same and hosts the service.
- Authentication Server (AS): The client authentication is done by the Authentication Server. Once the authentication is successful, the Authentication Server issues the client with a ticket known as the Ticket Granting Ticket. It is this TGT that makes sure that the other servers are aware that the client accessing it is already authenticated.
- Key Distribution Center (KDC): In the Kerberos environment, the authentication server is made up of three parts named A database, the Ticket Granting Server (TGS), along with the Authentication Server (AS). All these parts exist as a single server named the Key Distribution Center
- Ticket Granting Server (TGS): The TGS is an application server that offers service tickets is its service.
How to do Kerberos Authentication Protocols Work?
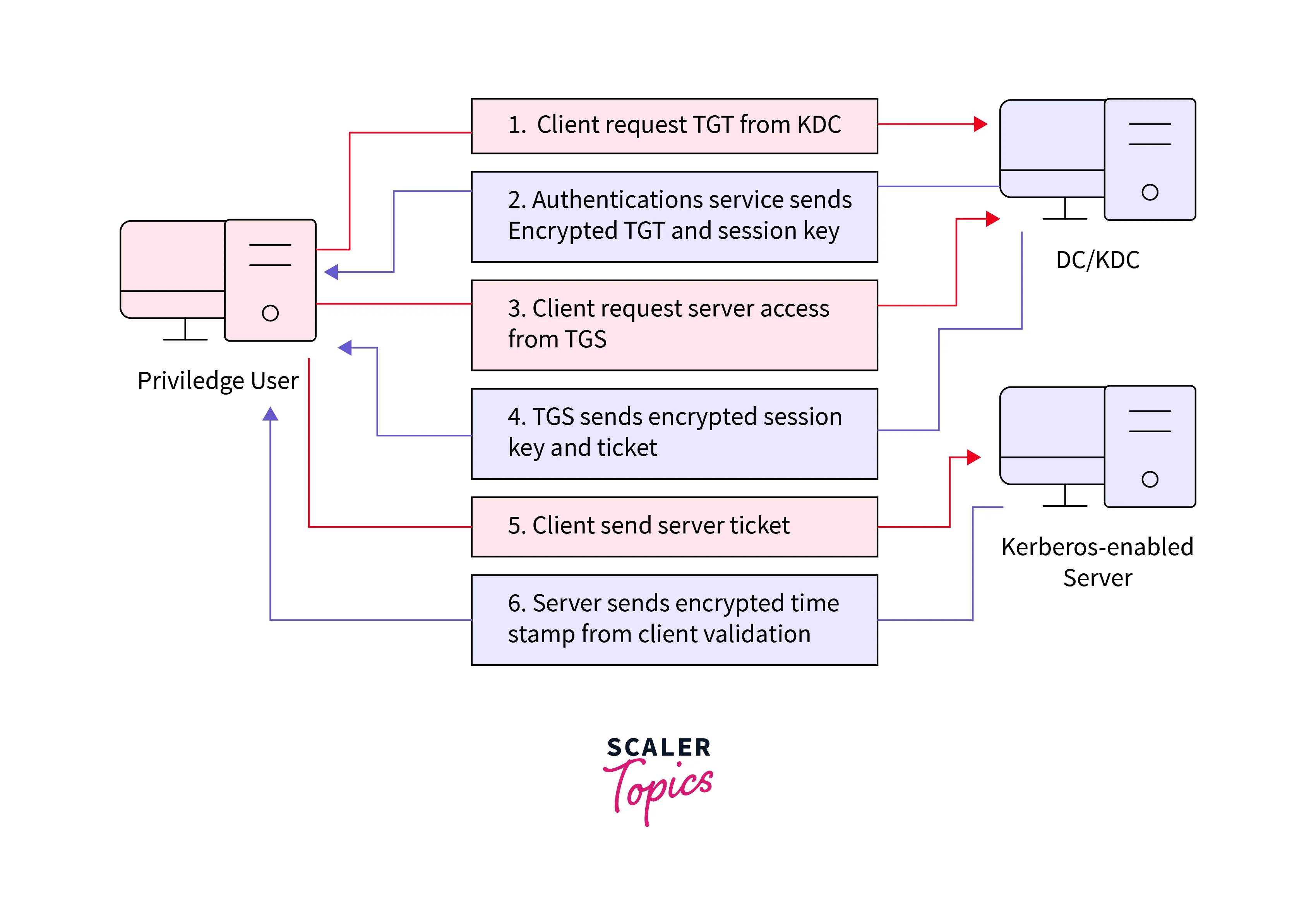
Let us explore and learn how Kerberos Authentication Protocols Works:
- The Authentication Server Request is the first step that takes place. Here, the end users start the entire process of Kerberos Authentication Protocols by raising a request for authentication from the KDC. Mostly, the authentication request occurs as plain text.
- Then, once the request is raised successfully, the Authentication Server initiates the response. The KDC processes the TGT along with the session key. This key is generated when the end user already exists in the database. But the authentication fails when the KDC recognizes that the end user's details are not available in the database.
- The end user needs to ask for the service ticket via the Service Ticket Request. The service ticket can be generated with the earlier TGT via the KDC.
- In response, the KDC now makes a Service Ticket Response. It sends the encrypted ticket that contains the session key. To decrypt the service ticket, the end users could start implementing the session key earlier sent via the KDC.
- Now, the Application Server Request is triggered. The end users start by requesting the application server to allow the usage of the service ticket. In response, the application server grants permission and authenticates the client. This step is known as the Application Server Response. Here, a ticket is sent that shall allow access to that specific service.
- Once done, this service ticket which was accessed stays until its expiration. Also, the users can make use of the same service ticket until it expires. Usually, 600 minutes is the default lifetime granted via the Kerberos ticket.
The entire process discussed above is shown below:
Kerberos vs Other Network Authentication Protocols
Till now, we have been studying Kerberos authentication. But since the invention of Kerberos authentication, there have been many other Network Authentication Protocols that help to secure the end users' credentials and more.
Below we have discussed the three most widely popular Network Authentication Protocols alongside Kerebeors:
- Kerberos vs. Microsoft New Technology LAN Manager (NTLM)
- Kerberos vs. Lightweight Directory Access Protocol (LDAP)
- Kerberos vs. Remote Authentication Dial-in User Service (RADIUS)
Kerberos vs. Microsoft New Technology LAN Manager (NTLM)
- Microsoft's New Technology LAN Manager ( widely popular as NTLM) was invented by Microsoft. NTLM is said to be the first technology implemented by Windows.
- From the 2000 version of Windows, almost all the editions of Windows have implemented Kerberos somewhere or the other.
- Additionally, NTLM implements a challenge-response authentication where the entire process revolves around end users knowing the correct answer.
- In this challenge-response authentication, the server questions, and the process is authenticated if the end users correctly answer.
Kerberos vs. Lightweight Directory Access Protocol (LDAP)
- Another well-known Network Authentication Protocol is Lightweight Directory Access Protocol.
- Abbreviated as LDAP, users can implement LDAP to maintain information about its end users.
- End users can also see that Kerberos and LDAP authentication are available on a single network.
- LDAP also offers an authorization service, while one can channel the authentication with Kerberos.
Kerberos vs. Remote Authentication Dial-in User Service (RADIUS)
- Remote Authentication Dial-in User Service, also famous as RADIUS, is another well-known Network Authentication Protocol.
- With RADIUS, End users can remotely access Internet Service Providers. It serves the purpose of approving and allowing the end users to dial in.
- Whereas the other network services implement it for accounting and authentication with its integration with Kerberos.
Tabular comparison between the three networks:
| Kerberos | Microsoft New Technology LAN Manager (NTLM) | Lightweight Directory Access Protocol (LDAP) | Remote Authentication Dial-in User Service (RADIUS) |
|---|---|---|---|
| From the 2000 version of Windows, Kerberos is implemented. | First technology implemented by Windows | Maintain information about its end users | End users can remotely access Internet Service Providers |
| End users look for Kerberos and other authentication over a single network. | Implements a challenge-response authentication | End users can also see that both Kerberos and LDAP authentication are available on a single network. | Serves the purpose of approving and allowing the end users to dial in. |
| Other network services implement Kerberos in integration with it. | The server questions, and if the end users correctly answer the process is authenticated. | Offers an authorization service | Other network services implement it for accounting as well as authentication |
How Secure is Kerberos?
As studied, many other protocols and security measures have been invented after Kerberos. But the question is if that leads to Kerberos authentication being insignificant or less secure. Well, it is not.
Kerberos still finds its application in the backend processes of various security protocols and is still considered entirely secure by different security practitioners globally. Furthermore, Kerberos authentication secures user data with its strong encryption.
Below are a few ways discovered by security researchers to hamper Kerberos.
- Pass-the-key attack: Hackers could impersonate the end users via their credentials.
- Pass-the-ticket attack: Hackers could implement tickets while the KDC is sending the ongoing session ticket.
- Golden ticket attack: Hackers have also found a way to implement threats via the Windows domain controllers for creating the end user's credentials.
Can Kerberos be Hacked?
We know that Kerberos is offering users a great way to secure and protect crucial and sensitive information. Along with its implementation for so long, Kerberos is a widely popular tool as well. Unfortunately, this also attracts various potential threats that might be trying to find a way to get through the protocol and use the user's private credentials for malicious activity.
Can we say Kerberos is at risk of being hacked?
Let us find out with this section of the article.
- As we know, with technological advancement, their chance to attempt fraud and security violations is also increasing significantly. Be it any leading security protocol, or Kerberos authentication, nothing is 100 percent secure in today's world. Hackers can still find tier ways to decode and invade the protection.
- But as Kerberos authentication has been around for a while, the trust gained is significant. It still could be seen implemented in the backend processes of various security protocols. Although hackers are advancing too, they still can find ways to forge tickets, make attempts to log in to private accounts, or even with malware, their attempt to downgrade the encryption continues.
- Irrespective of all this, Kerberos' authentication is still relevant as the security access protocol. The flexibility in the protocol boosts the chance to try more robust encryption algorithms. This way, more ways to mitigate threats could be combatted and help to educate users with best practices to stay secure and protected.
Is Kerberos Still Relevant?
With the advancement in technology, security also has been advanced. While Kerberos is still being implemented as the backend for various security protocols, is it still relevant in this age of digitalization?
Let us find out with this section of the article.
- Kerberos might be with us for a long, but that does not take away its originality and importance. It's still relevant. It has worked as an effective security protocol, even though various cyber attacks have cracked it. Powered with solid encryption, Kerberos authentication protects with authentication for tickets and passwords.
- Kerberos authentication is here to stay, and no immediate alternative replacements are seen in the future. Most security advancements are protecting tickets and passwords or helping users provide various methods for securely validating their identity.
- In all these security technologies, Kerberos authentication plays the backend technology. It works as an effective, suitable, and solid solution for connected workplaces as SSO, helping the users prove their identity for validations to access various applications or systems by one verification.
Conclusion
- To secure and protect the user's credentials, Kerberos was designed. It keeps the passwords out of insecure networks, even after verifying the user's identities.
- Kerberos ensures security, offering a centralized authentication server that functions by authenticating the credential/ ticket.
- Kerberos authentication is here to stay, and no immediate alternative replacements are seen in the future. The majority of security advancements are protecting tickets and passwords or helping users to provide various methods for validating their identity securely.
- Hackers can still find tier ways to decode and invade the protection. But as Kerberos authentication has been around for a while, the trust gained is significant.
- Kerberos could be seen implemented in the backend processes of various security protocols.
- In the Kerberos environment, the authentication server comprises three parts named A database, the Ticket Granting Server (TGS), and the Authentication Server (AS).
