Kubernetes Pod Security Policies
Overview
This article takes you through Kubernetes Pod Security Policies (PSPs) systematically. It covers the essentials, of setting up security, crafting customized policies, utilizing defaults, testing, managing exceptions, monitoring, and adopting best practices. Explore how Pod Security Policies enhance the safety of your Kubernetes-based container applications.
Understanding Kubernetes Pod Security Policies
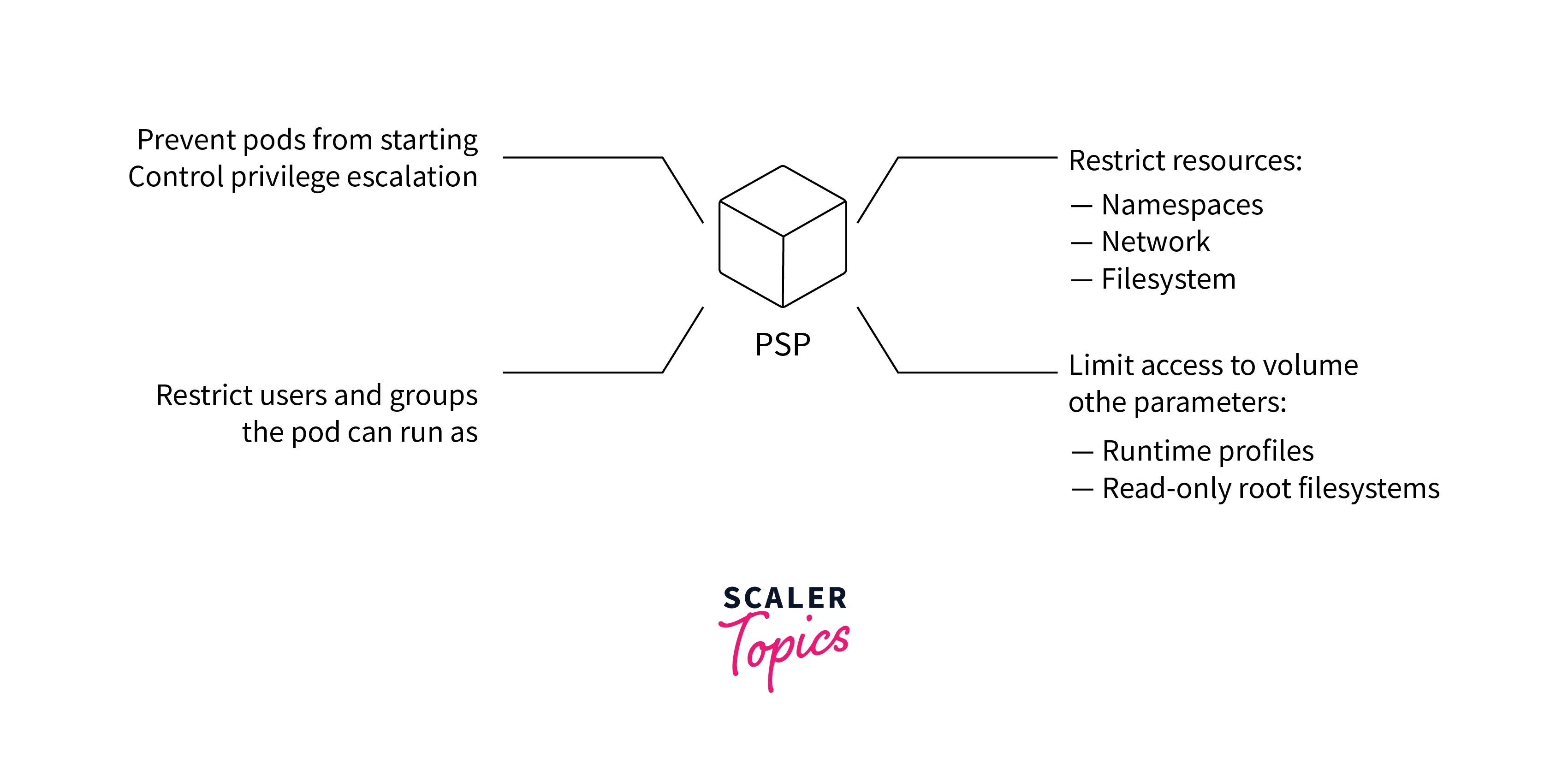
In essence, Kubernetes Pod Security Policies act as a security gatekeeper, governing the configuration and behavior of Pods within a Kubernetes cluster. Think of them as a way to define the rules of engagement for your containers. For instance, a Kubernetes administrator can utilize Kubernetes Pod Security Policies to enforce access only from specific IP ranges, restrict the number of concurrent users for a given service, or grant access to custom resources based on roles, groups, and even version control repositories such as Git or Mercurial.
Kubernetes Pod Security Policies are inherently tied to Kubernetes' pod security layer, providing a strategic layer of protection. They can seamlessly integrate with the Kubernetes CLI or be added as a plugin to the open-source toolset, augmenting the security features of the platform.
Upon the deployment of a Kubernetes cluster, the Kubernetes Pod Security Policies associated with the constituent pods are registered within a proprietary LDAP registry embedded in the cluster itself. This registry serves as a repository for Kubernetes Pod Security Policy definitions, allowing for streamlined access control.
It's noteworthy that Kubernetes handles the registration of Kubernetes Pod Security Policies automatically during cluster initiation. This orchestration eliminates much of the manual setup required. However, in scenarios involving specialized services like Pod-Xchange, manual Kubernetes Pod Security Policy registration might be necessary.
As a new cluster kicks off, Kubernetes undertakes the automatic registration of Kubernetes Pod Security Policies across all pods. This orchestration is overseen by the kubelet, a critical system daemon operating on the respective node of each pod. This process is facilitated by a straightforward registerDnsDaemon DSL command.
For instance, consider the following command:
This registration prompts the pod to validate and issue certificates as needed, fostering a secure and controlled environment. More advanced setups can involve DNS records that mandate Kubernetes Pod Security Policy registration prior to usage.
Once Kubernetes Pod Security Policy registration is established, configuration becomes possible via pod metadata within its designated namespace. Here's a glimpse of how a Kubernetes Pod Security Policy might be configured:
It's essential to mention that Kubernetes automatically replaces the existing security policy with the updated one. However, the old policy can still be accessed using the previous certificate.
Considering scenarios where clusters might cease operation or misconfigured resources render you offline, Kubernetes employs a unique update and installation approach known as re-hosting. This involves creating a new cluster instance within AWS using ECS services from the initial deployment. While re-hosts simplify resource deployment, they introduce complexities related to compatibility and security, particularly the potential for unauthorized access.
This concludes our exploration of the core concepts underlying Kubernetes Pod Security Policies. In the subsequent sections of this article, we'll delve into enabling, configuring, and creating these policies, demonstrating best practices and considerations for effective policy management.
Enabling and Configuring Pod Security Policies
Kubernetes has revolutionized the way applications are deployed and managed, offering a dynamic and scalable environment for modern software development. However, with the increased flexibility and complexity, security considerations have become paramount. Enter Kubernetes Pod Security Policies, a vital tool for enforcing security measures within a Kubernetes cluster.
Enabling Pod Security Policies
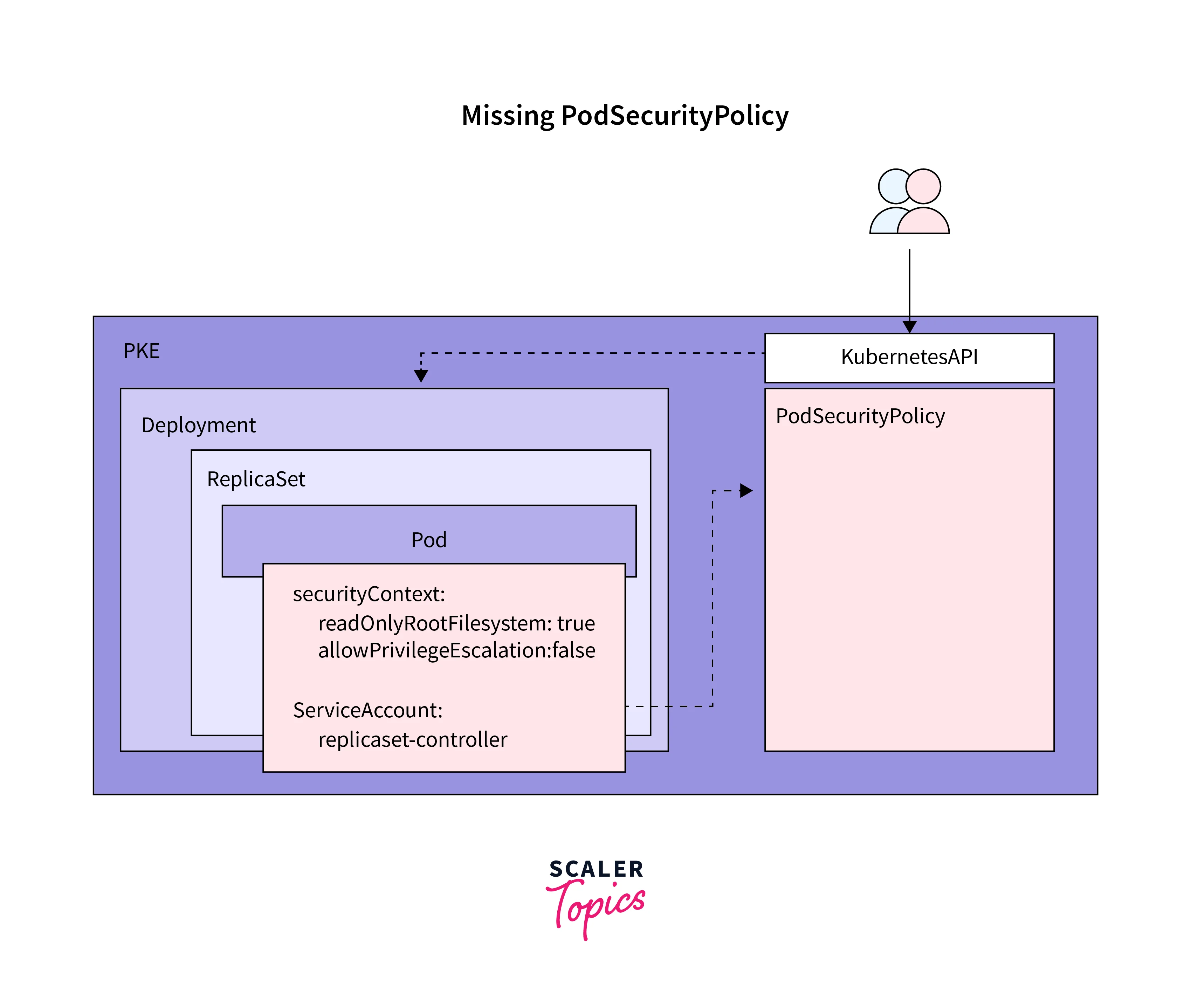
By default, Kubernetes does not enforce any Pod Security Policies, allowing Pods to be created without restrictions. To enable Pod Security Policies, you need to follow these steps:
-
Enable the Admission Controller: Kubernetes leverages an admission controller to validate and mutate admission requests. To enable Pod Security Policies, you need to ensure that the PodSecurityPolicy admission controller is added to the admission control configuration.
-
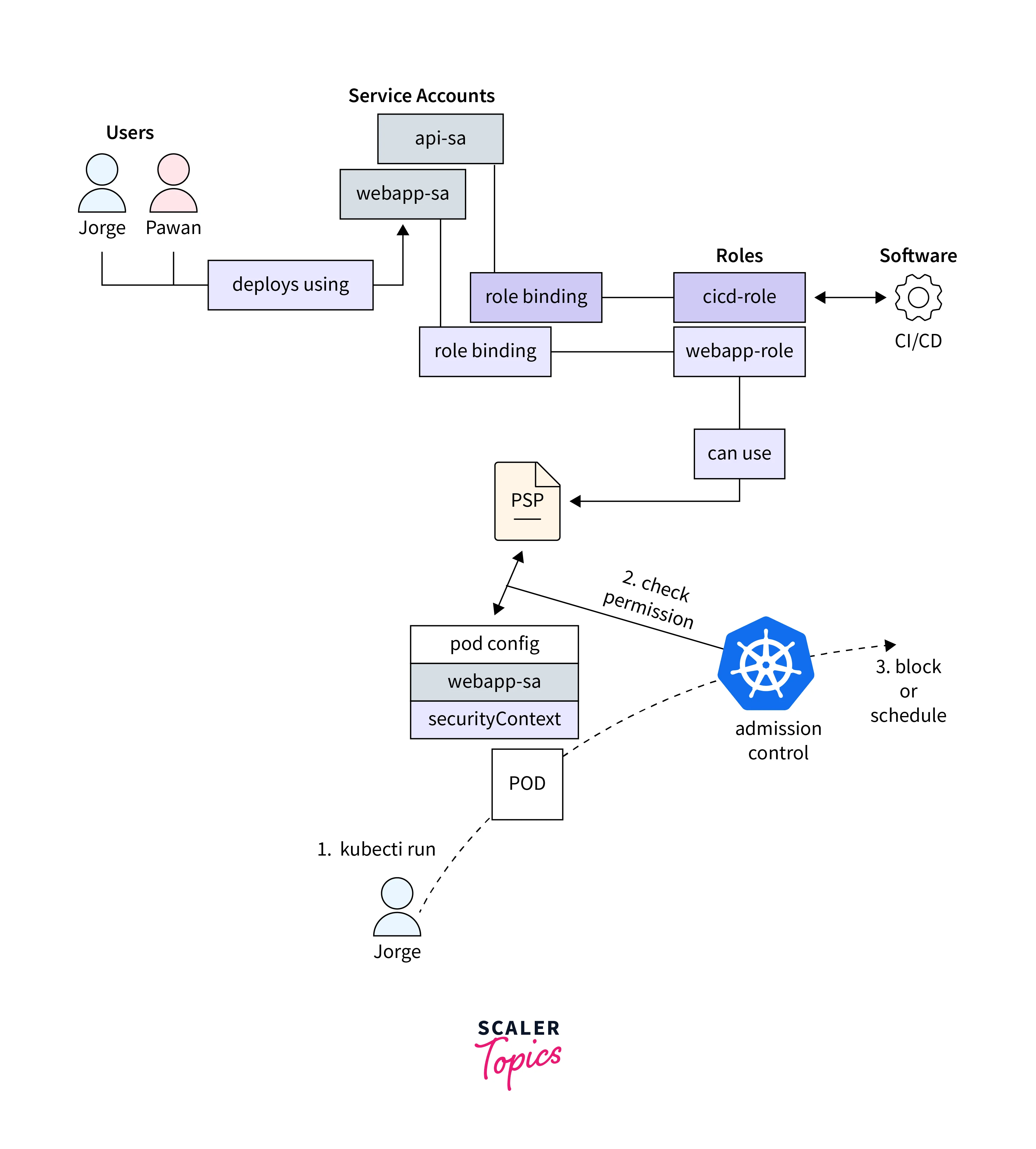
Creating the Required Role and RoleBinding: You'll need to create a Role and a RoleBinding that grants the necessary permissions to users or service accounts. These permissions allow them to use Pod Security Policies. Here's an example of creating a Role and RoleBinding:
-
Enforce the Admission Control Policy: Once the admission controller is enabled and the required roles are set up, you can enforce the admission control policy by creating Pod Security Policy objects.
Configuring Pod Security Policies
Configuring Pod Security Policies involves defining the security constraints that Pods must adhere to. Here are the key aspects to consider:
- Privilege Escalation: This setting restricts the privilege escalation within containers. You can disallow privilege escalation by setting the allowPrivilegeEscalation field to false.
- Capabilities: Kubernetes allows fine-grained control over the capabilities a container can have. You can drop certain capabilities that are not required by your application, minimizing potential attack vectors.
- Volume Types: Specify which volume types are allowed. By limiting the types of volumes Pods can use, you can prevent potential vulnerabilities, such as hostPath volumes that might grant access to sensitive data on the node.
- Host Namespace and Network Policies: Restricting access to the host's namespace and network policies enhances isolation and prevents unauthorized communication between Pods and nodes.
- Seccomp and AppArmor Profiles: Utilize Seccomp profiles and AppArmor profiles to restrict the system calls a container can make and enforce application-specific security policies.
- User and Group IDs: Define the allowed user and group IDs for containers, preventing the use of root users and enforcing the principle of least privilege.
Benefits of Configuration
Proper configuration of Pod Security Policies offers several advantages:
- Reduced Attack Surface: By enforcing specific security measures, you shrink the potential avenues that attackers can exploit.
- Consistent Security: Configuration settings are applied uniformly across all Pods, ensuring a consistent security posture.
- Compliance: Pod Security Policies help meet regulatory compliance standards by enforcing security best practices.
- Enhanced Reliability: Properly configured Pods are less likely to experience unexpected behaviors or disruptions due to security vulnerabilities.
By enforcing security measures and maintaining a consistent security posture, you create a more resilient and secure Kubernetes environment. In the next section, we will delve into the process of creating custom Pod Security Policies tailored to your application's requirements.
Creating Pod Security policies
Creating Pod Security Policies in Kubernetes involves defining a set of rules that specify the security requirements for Pods within the cluster. These policies serve as guidelines for ensuring that Pods adhere to specific security configurations, reducing the risk of potential security breaches and vulnerabilities.
Defining a Pod Security Policy
To create a Pod Security Policy, you need to define a set of constraints that control various aspects of a Pod's configuration, such as the use of privileged containers, host namespaces, and capabilities. Let's explore some key elements and examples of how these constraints can be implemented.
Privileged Containers
A privileged container has more access to the host system and can potentially compromise security. To restrict the use of privileged containers, you can define a policy like this:
Capabilities and Seccomp Profiles: Capabilities grant different levels of access to the kernel. By restricting capabilities, you can minimize the attack surface. Here's an example:
Volume Types and Host Paths: You can limit the types of volumes a Pod can use and restrict access to host paths:
Applying the Policy
Once you define the Pod Security Policy, you need to ensure that it's applied to the cluster. This involves creating a ClusterRole and a ClusterRoleBinding, granting permissions to the policy.
Example:
Using Pod Templates:
After applying the policy, you can use it in your Pod templates by specifying the securityContext section with the desired constraints. Here's an example:
In this example, the Pod uses the defined security context to ensure proper security settings.
Using Default Pod Security Policies
In Kubernetes, security is a paramount concern. As organizations deploy containerized applications, the need to ensure the robustness of their security mechanisms becomes increasingly critical. Kubernetes Pod Security Policies offer a robust solution to enforce security measures, and among them, the utilization of default policies provides a foundational layer of protection.
Understanding Default Pod Security Policies
Default Pod Security Policies are predefined sets of security constraints that Kubernetes clusters offer out of the box. These policies are designed to establish a baseline level of security for Pods without requiring manual configuration. They serve as a protective shield, ensuring that even if Pod configurations are not explicitly defined, they still adhere to certain security standards. By using these default policies, organizations can rapidly bolster the security of their deployments without exhaustive configuration efforts.
Default Pod Security Policies play a pivotal role in maintaining a secure Kubernetes environment. They address the challenges of enforcing security at scale by providing a standardized framework that aligns with industry best practices. These policies restrict the capabilities of Pods, reducing the attack surface and preventing them from running with excessive privileges. This is crucial in preventing potentially malicious or erroneous code from exploiting vulnerabilities.
Benefits of Utilizing Default Policies
Implementing default Pod Security Policies offers several compelling benefits. Firstly, it ensures a consistent security posture across all Pods in a cluster, irrespective of the application. This uniformity is crucial for maintaining compliance and reducing the chances of misconfigurations that could lead to security breaches. Secondly, default policies provide an excellent starting point for organizations unfamiliar with security configurations, helping them establish a strong baseline.
Enhanced Defense Against Common Threats
- Kubernetes Pod Security Policies defend against various common threats.
- Restrictions on Pod access to host filesystems prevent attacks aiming to manipulate or extract sensitive host data.
- Processes within Pods are barred from directly accessing specific devices or engaging with the host network.
- Such measures minimize attackers' ability for lateral movement within the system.
Customization and Overrides
- Default Pod Security Policies offer a robust foundation but aren't inflexible constraints.
- Kubernetes allows cluster administrators to customize or create exceptions in these policies.
- Customization ensures a balance between security and operational efficiency.
- Flexibility prevents excessive disruption to application functionality.
Testing and Validating Pod Security Policies
Ensuring the effectiveness of Kubernetes Pod Security Policies (PSPs) is essential to maintaining a secure containerized environment. As PSPs play a crucial role in safeguarding applications against potential vulnerabilities, testing and validating these policies becomes paramount. In this section, we'll explore the importance of testing PSPs, various testing techniques, and best practices to validate the policies effectively.
Importance of Testing Kubernetes Pod Security Policies
Testing PSPs is akin to putting on a pair of virtual gloves before handling fragile cargo. It is a proactive measure to identify any gaps, misconfigurations, or unintended consequences that might compromise the security posture of the Kubernetes cluster.
Testing Techniques for Kubernetes Pod Security Policies
-
Static Analysis:
This technique involves reviewing the PSP configurations without executing them. By analyzing the settings, administrators can identify issues such as overly permissive settings, missing constraints, or conflicting rules. Static analysis tools can provide insights into potential vulnerabilities before the policies are enforced.
-
Dynamic Testing:
Unlike static analysis, dynamic testing involves applying the PSPs and observing their impact on running Pods. This technique requires caution, as improperly configured policies could disrupt applications. By creating test Pods with varying configurations and security contexts, administrators can assess whether the policies correctly allow or deny expected actions.
-
Penetration Testing:
Similar to ethical hacking, penetration testing involves deliberately attempting to breach the security boundaries defined by PSPs. This approach helps uncover potential weaknesses that malicious actors might exploit. By simulating real-world attack scenarios, administrators can gain insights into the effectiveness of their policies.
Best Practices for Validating Kubernetes Pod Security Policies
-
Use a Test Cluster:
Before applying PSPs to a production environment, set up a separate test cluster. This allows you to evaluate the policies' impact without risking disruptions to critical workloads.
-
Gradual Rollout:
Implement the PSPs gradually, starting with non-critical workloads. Monitor these Pods closely to ensure that the policies do not cause unintended issues. Once you're confident in the policies' behavior, extend their coverage to more critical applications.
-
Collaborative Testing:
Involve multiple stakeholders, including security teams, application developers, and cluster administrators, in the testing process. Diverse perspectives can help identify potential blind spots and ensure comprehensive testing.
Managing Exceptions and PodTemplate
In some scenarios, you might encounter situations where certain Pods need to deviate from the standard security policies due to specific application requirements. Kubernetes Pod Security Policies offer a solution to address such exceptions without compromising the overall security of the cluster.
To manage exceptions effectively, you can utilize the PodTemplate field within your Pod Security Policies. This feature allows you to define exceptions or overrides for specific Pods that need different security settings. Here's a simplified example to illustrate how this works:
Let's say you have a Pod Security Policy that enforces that all Pods must not run as the root user and must not use host namespaces. However, you have a legacy application that requires running as the root user. Instead of relaxing the policy for all Pods, you can create an exception using the PodTemplate field:
In this example, the exception-pod-policy defines an exception to allow privileged Pods and custom SELinux labels. The legacy-app-pod then uses this exception policy, allowing the legacy application to run as the root user and use specific host paths.
Auditing and Monitoring Pod Security Policies
Ensuring the effectiveness of your Pod Security Policies requires ongoing auditing and monitoring. Regular audits help identify potential policy violations, misconfigurations, or vulnerabilities in your deployed Pods.
Kubernetes provides tools and practices to assist with auditing and monitoring Pod Security Policies:
-
Policy Violation Reports:
Kubernetes generates reports when Pods violate security policies. These reports can be accessed through various means, such as Kubernetes Events or specialized auditing tools. It's essential to monitor these reports to detect and address policy violations promptly.
-
Third-Party Tools:
There are third-party tools and plugins available that can help streamline the process of auditing and monitoring Pod Security Policies. These tools often provide more advanced reporting, visualization, and alerting capabilities.
-
Logging and Alerting:
Integrate Kubernetes logs with centralized logging solutions to gain visibility into security events and policy violations. Set up alerts to receive notifications when policy violations occur, enabling quick responses.
By auditing and monitoring your Pod Security Policies, you can maintain a proactive security posture, respond to incidents promptly, and ensure that your Kubernetes environment remains secure and compliant with your organization's policies.
Best Practices for Pod Security Policies
Kubernetes Pod Security Policies (PSPs) play a crucial role in safeguarding containerized applications within a Kubernetes cluster. Employing best practices when implementing and managing PSPs is essential to maintain a strong security posture and protect your workloads from potential threats. In this section, we'll explore key best practices to consider when working with PSPs.
Start with a Risk Assessment
Before defining Pod Security Policies, conduct a thorough risk assessment of your applications and their dependencies. Identify potential vulnerabilities and attack vectors. This assessment will guide you in determining the appropriate security constraints to apply within your PSPs.
Implement Least Privilege Principle
Follow the principle of least privilege when crafting PSPs. Limit the capabilities and permissions of containers to only what is necessary for their intended functionality. Restricting unnecessary access minimizes the potential impact of security breaches.
For example, consider the following:
Implement Network Policies
Complement PSPs with Kubernetes Network Policies to control network access between Pods. This limits communication to only authorized sources, reducing the potential for lateral movement by attackers.
Testing and Validation
Thoroughly test PSPs before enforcing them in production. Utilize staging or test clusters to validate the impact of PSPs on your applications. This helps avoid unexpected disruptions and ensures that your policies work as intended.
Monitor and Audit Regularly
Implement monitoring and auditing mechanisms to track PSP violations and potential security incidents. Tools like Kubernetes' audit logs can provide valuable insights into policy violations and help you detect and respond to security breaches.
Consider Namespace Isolation
Isolate workloads into separate namespaces and apply specific PSPs based on workload requirements. This approach allows for customized security policies tailored to the needs of different applications.
Stay Informed
Stay updated on Kubernetes security best practices and changes in the PSP landscape. Engage with the Kubernetes community and security experts to ensure you're following the latest recommendations.
Kubernetes Pod Security Policies are a cornerstone of securing your containerized applications. By following these best practices, you can create a robust security foundation that guards against potential threats, reduces vulnerabilities, and ensures the integrity of your Kubernetes environment.
Limitations and Future Developments
-
Complex Configuration:
Despite their benefits, implementing Kubernetes Pod Security Policies can be challenging due to their complex configuration process. Administrators need to carefully balance security requirements with application functionality, potentially leading to a steep learning curve.
-
Granularity:
While Pod Security Policies enhance security, they can sometimes lack granularity. Fine-tuning policies for different types of workloads might be challenging, as policies are typically applied cluster-wide.
-
Compatibility:
As Kubernetes evolves, Pod Security Policies might face compatibility issues with newer versions or features. Ensuring that policies remain effective across updates requires ongoing monitoring and adaptation.
-
Limited Coverage:
Kubernetes Pod Security Policies primarily focus on the security aspects of Pods. However, containerized applications encompass more than just Pods, including networking and storage configurations, which might not be fully covered.
-
Future Developments:
The Kubernetes community recognizes these limitations and is actively working on improvements. The "PodSecurity" project, part of the Kubernetes Enhancement Proposals (KEP) process, aims to provide a more flexible and customizable approach to container security.
-
Admission Controllers:
Kubernetes is moving towards using Admission Controllers, such as the "PodSecurity Admission" controller, to offer more dynamic and versatile security enforcement. This evolution promises better integration and extensibility for security policies.
-
Third-party Solutions:
While Kubernetes Pod Security Policies address core security concerns, third-party solutions and tools are emerging to complement and extend their functionality. These solutions offer specialized features and might cater to specific use cases.
Conclusion
- Kubernetes Pod Security Policies bolster app security through standardized configurations.
- Admins gain control for consistent security in dynamic Kubernetes setups.
- Best practices are streamlined, minimizing misconfiguration risks.
- Evolving policies, like "PodSecurity," promise more flexibility ahead.
- Striking a balance: Security meets functionality in policy implementation.
- Embracing Pod Security Policies strengthens Kubernetes' secure ecosystem.
