Kubernetes Secrets Management
Overview
Kubernetes Secrets Management involves securely storing and managing sensitive information, such as passwords and API tokens, used by applications. Secrets are stored separately from application code and configuration, encrypted at rest, and can be injected into pods as environment variables or mounted as files, ensuring data security and separation of concerns within containerized environments.
Understanding Kubernetes Secrets
Kubernetes Secrets is a way to securely manage sensitive information, such as passwords, tokens, and certificates, within Kubernetes clusters. They are designed to keep this sensitive data separate from application code and configuration, reducing the risk of exposure.
Explanation of what Kubernetes Secrets are and how they work.
Secrets work by storing sensitive information in a Kubernetes cluster and providing controlled access to that information to the pods that require it. The data stored in secrets is base64-encoded, which adds a basic level of obfuscation, although it's important to note that this encoding is not a secure encryption method.
Secrets can be used in two primary ways within Kubernetes:
- Environment Variables: Secrets can be injected into pods as environment variables. This allows applications running in the pods to access the sensitive information as environment variables, without directly exposing the data in the application code.
- Volumes: Secrets can also be mounted as files in pods. This approach enables applications to read the sensitive data from files, again avoiding direct exposure in the application code.
Kubernetes provides a level of security for secrets by encrypting them at rest in the etcd data store, which is the key-value store used by Kubernetes to store configuration data. However, it's important to note that secrets do not provide an extremely high level of security, especially against determined attackers with access to the cluster. For more robust security needs, external solutions like HashiCorp Vault or other Key Management Systems (KMS) may be considered.
Types of Secret
In Kubernetes, there are several types of secrets available for different use cases. Each type serves a specific purpose when it comes to managing sensitive information within your cluster. Here are the main types of secrets:
| Secret Type | Purpose and Use Case |
|---|---|
| Opaque Secrets | Store arbitrary key-value pairs (e.g., passwords, tokens) |
| Service Account Tokens | Authenticate pods to the Kubernetes API server |
| Docker Registry Secrets | Store credentials for private Docker image registries |
| TLS Secrets | Store TLS certificates and private keys for secure communication |
| SSH Secrets | Store SSH keys for authentication to external resources |
| Custom Secrets | User-defined secret types for specialized use cases |
Best Practices for Secrets Management in Kubernetes
Effective secrets management in Kubernetes is crucial for maintaining the security and integrity of your applications. Here are some best practices to consider:
- Use Kubernetes Secrets: Utilize the built-in Kubernetes Secret resource to store sensitive data. Avoid hardcoding sensitive information directly in your application code or configuration.
- Limit Access: Follow the principle of least privilege. Grant only the necessary permissions to access and manipulate secrets. Use Kubernetes RBAC (Role-Based Access Control) to restrict access to secrets.
- Sensitive Data Encryption: Ensure that sensitive data stored in secrets is properly encrypted. Kubernetes automatically encrypts secrets at rest in the etcd datastore, but consider encrypting the data before storing it as well.
- Regularly Rotate Secrets: Implement a routine for rotating secrets, such as passwords and tokens. Kubernetes provides the ability to update secrets without modifying pods.
- External Secrets Management: For more robust security needs, consider using external solutions like HashiCorp Vault or cloud-native Key Management Systems (KMS) to manage and distribute secrets centrally.
- Monitor and Audit: Regularly audit access to secrets and monitor for unusual activity. Kubernetes provides audit logs that can help you track who accessed or modified secrets.
- Avoid Hardcoding Secrets in YAML: When deploying manifests, avoid hardcoding sensitive information directly in YAML files. Use environment variables or ConfigMaps to inject secrets into the deployment process.
Creating and Managing Kubernetes Secrets
Let's learn to create and manage Kubernetes Secrets.
Step-by-step guide to creating and managing secrets using kubectl.
Step 1: Create a Secret
- Open a terminal window.
- Create a secret. The generic type is used for storing key-value pairs.
This command creates a secret named my-secrets with two key-value pairs: API_KEY and DATABASE_PASSWORD.

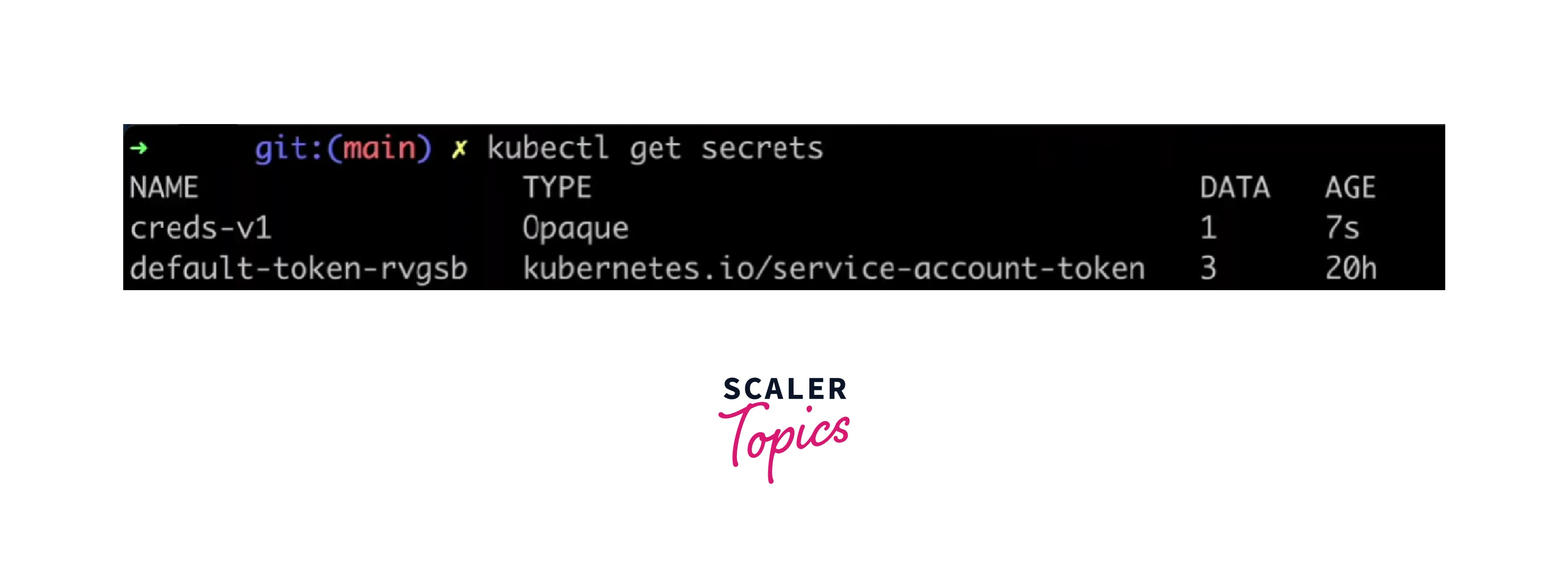
Step 2: View the Created Secret
Verify that the secret is created using:
This will display information about the secret, including its name, type, and age.
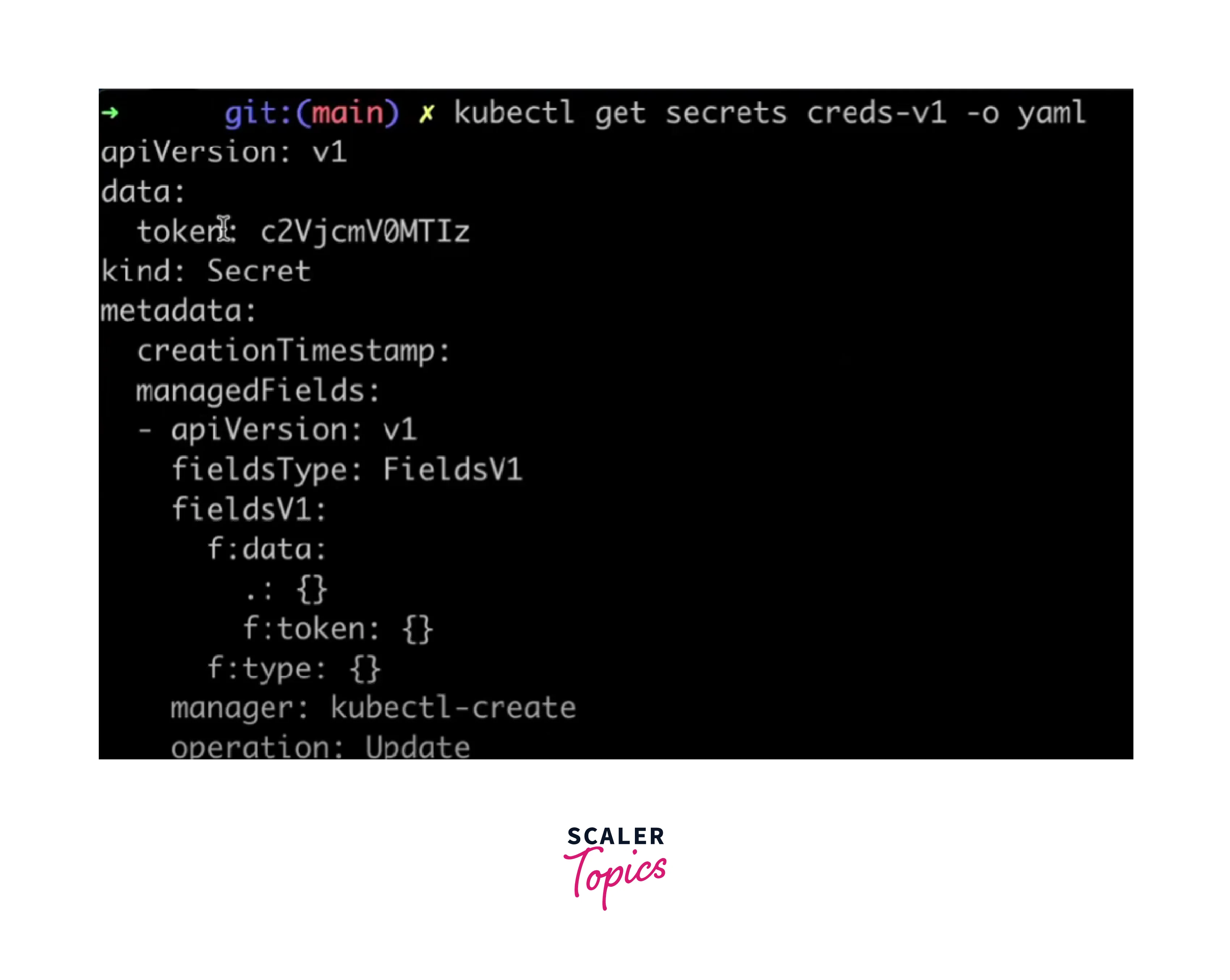
Step 3: View Secret Data
To view the decoded data within the secret, use the kubectl get secret command with the -o yaml flag:
Step 4: Access Secret Data
To access the decoded secret data, you can use base64 decoding with the token of your secret.

Step 5: Update a Secret
To update a secret, you can use the kubectl edit secret command:
This will open the secret in the default text editor. Make the necessary changes. On saving the file, Kubernetes will automatically update the secret.
Step 6: Delete a Secret
To delete a secret, use the kubectl delete secret command:
Confirm the deletion when prompted.
Step 7: Using Secrets in Pods
When creating pods that need access to the secrets, you can reference the secret's keys as environment variables or volumes. Here's an example pod configuration:
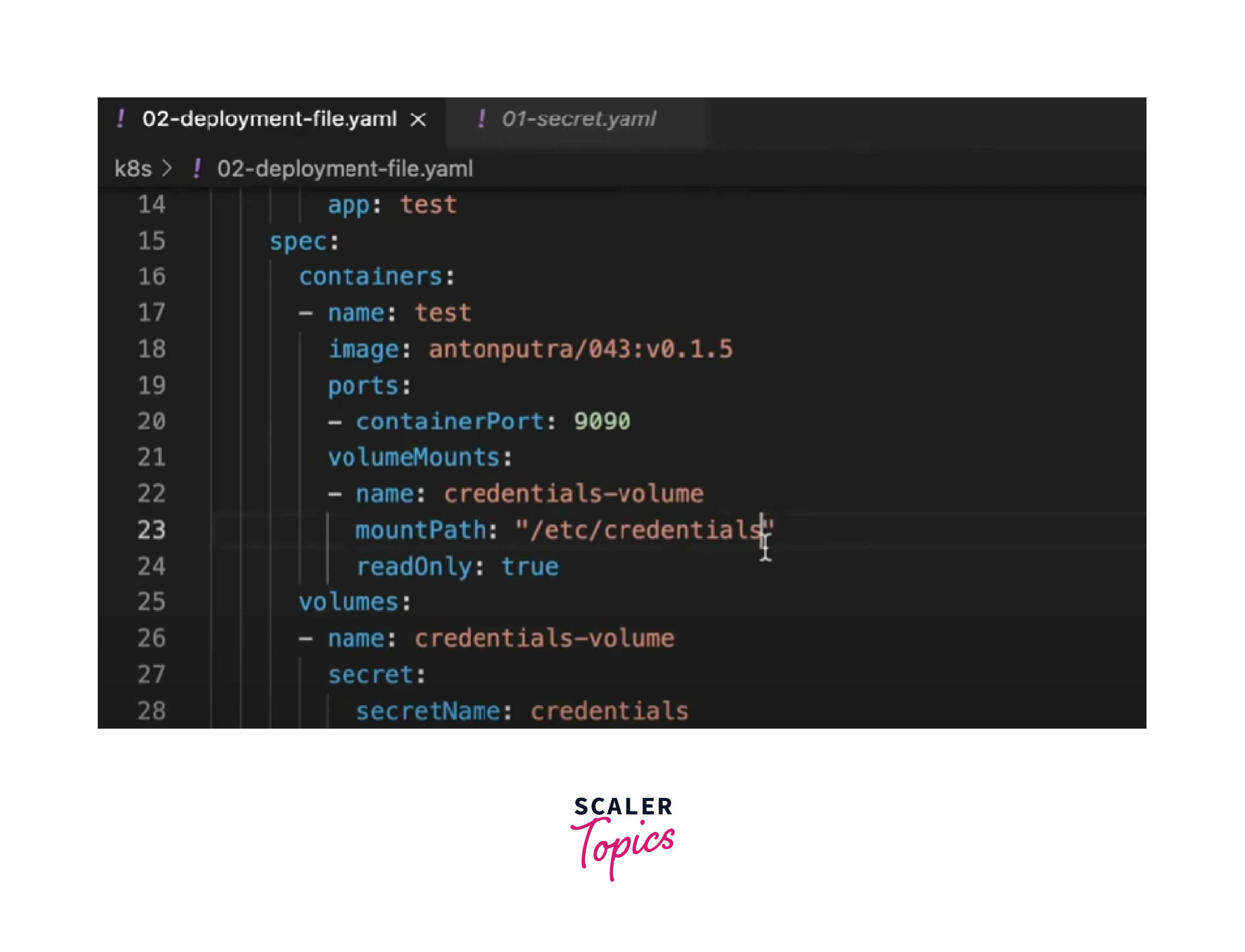
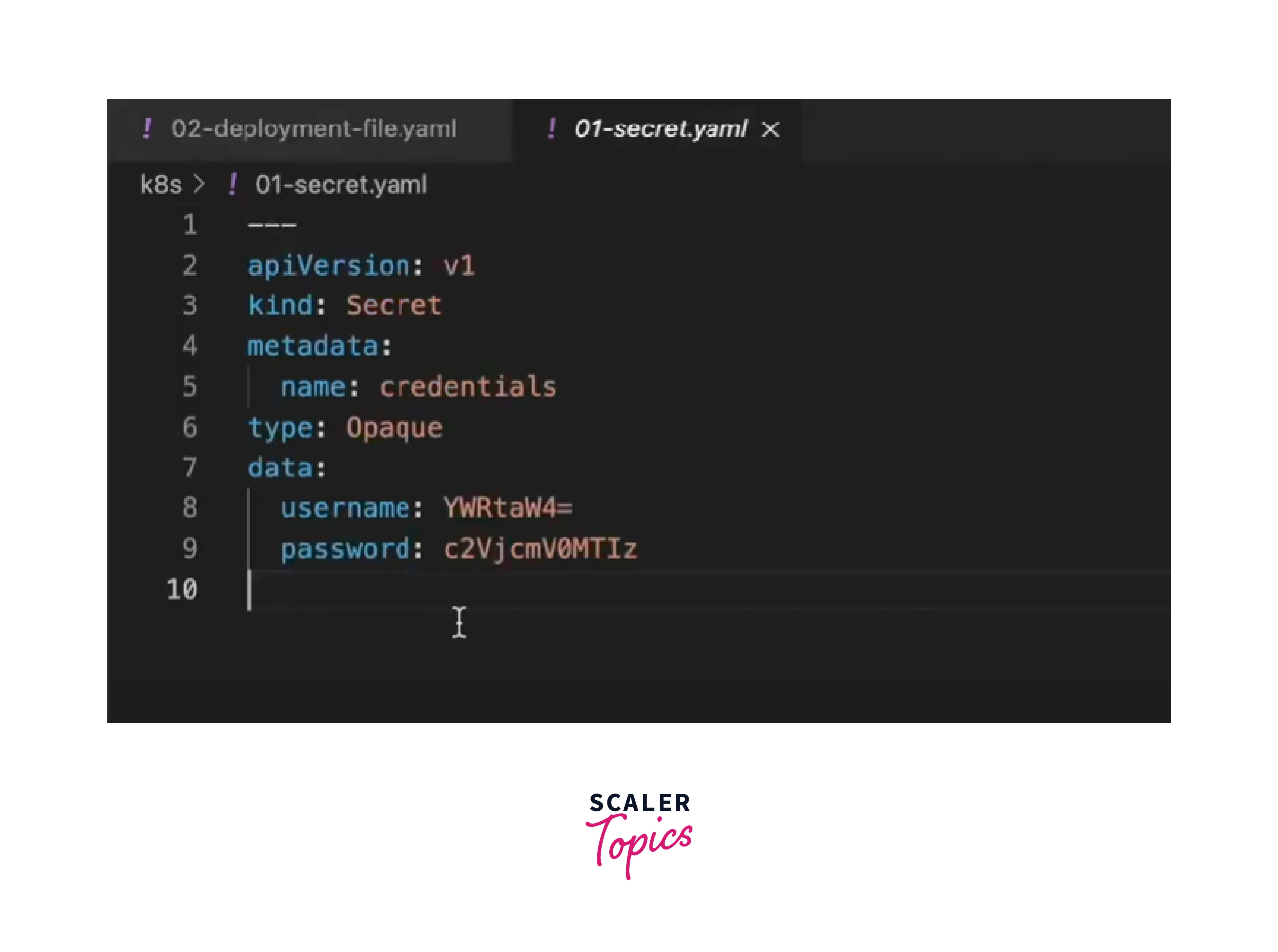
On running the kubectl apply command the deployment gets created with the secrets.
Integrating External Secrets Management Systems
Integrating external secrets management systems, such as HashiCorp Vault or cloud-native Key Management Services (KMS), can significantly enhance your secrets management practices by providing advanced security, centralization, and more comprehensive management capabilities. Here's a general guide on how to integrate such systems into your Kubernetes environment:
- Choose System: Select a suitable external secrets management solution like HashiCorp Vault or cloud-native Key Management Services (KMS).
- Setup: Install and configure the chosen system, ensuring authentication, policies, and access controls.
- Migrate Secrets: Transition existing secrets to the external system and start storing new secrets there.
- Integration: Connect the external system with Kubernetes using plugins or secrets controllers like "kube-secrets" or "secrets-store-csi-driver".
- Rotation and Updates: Utilize external system features for secret rotation, versioning, and centralized updates.
- Access Controls: Implement RBAC for both Kubernetes and the external system to ensure secure access.
- Monitoring: Leverage external system's monitoring and auditing tools for tracking secret access and changes.
- Testing: Rigorously test the integration to verify proper functionality and application access.
- Documentation: Provide clear documentation and training to teams using the integrated solution.
Secrets Rotation and Lifecycle Management
Secrets rotation and lifecycle management are critical aspects of maintaining the security and integrity of your applications. Properly managing secrets throughout their lifecycle helps prevent unauthorized access and reduces the risk of security breaches. Here's a guide on secrets rotation and lifecycle management:
1. Define a Rotation Policy:
Determine how frequently your secrets need to be rotated. Factors such as the sensitivity of the data, iindustryregulations,` and security best practices should guide your policy.
2. Automate Rotation:
Automate the rotation process as much as possible. Manual rotation can introduce human error and delays. Utilize tools or scripts that facilitate automatic secret rotation according to your defined policy.
3. Pre-Rotation Steps:
Before rotating a secret, perform these steps:
- Generate New Secret: Create a new secret with updated credentials or sensitive information.
- Update Applications: Make sure your applications are aware of the upcoming rotation. Update their configurations or environment variables to reflect the new secret.
- Testing: Test the updated applications in a controlled environment to ensure they work properly with the new secret.
4. Rotate Secrets:
When it's time to rotate secrets:
- Update the Secret: Update the existing secret with the new credentials or data. This can be done using kubectl edit secret or similar commands.
- Update Applications: Ensure that all applications using the old secret are updated to use the new secret.
5. Post-Rotation Steps:
After rotating a secret:
- Revoke Old Secret Access: Invalidate or revoke access to the old secret to prevent any lingering unauthorized access.
- Monitoring: Monitor application behavior and logs after rotation to catch any potential issues.
Auditing and Monitoring Secrets Access
Auditing and monitoring secrets access are essential aspects of maintaining the security and compliance of your applications and infrastructure. Here's a guide on how to audit and monitor secrets access using Kubernetes and kubectl:
- Enable Kubernetes Audit Logging: Enable Kubernetes audit logging to capture relevant events, including secret access. This involves configuring the Kubernetes API server to generate audit logs.
- Monitor Audit Logs: Use tools like kubectl and log aggregators to monitor and analyze the audit logs. Look for events related to ssecretaccess, modifications, and other relevant activities.
- Set Up Alerts: Configure alerts based on specific audit log events related to secrets. This can help you promptly identify unauthorized or suspicious activities.
- Use kubectl for Auditing: You can use kubectl to query audit logs and gain insights into secrets access:
- To retrieve audit logs, use: kubectl get events --field-selector type=Audit
- To filter logs for secrets-related activities, use: kubectl get events --field-selector type=Audit grep -E 'Secret|ConfigMap|SecretKeyRef'
- Implement Centralized Logging: Consider using a centralized logging solution to aggregate and analyze audit logs from multiple Kubernetes clusters. Popular tools include Fluentd, Elasticsearch, and Kibana (EFK) stack.
- Log Customization: Configure Kubernetes audit policy to capture specific events related to secrets. You can customize the audit policy to focus on secret access and modifications.
- Access Monitoring: Monitor access to secrets using tools like kubectl and audit logs. Regularly review who has accessed secrets and when.
- Automation: Automate the process of analyzing audit logs and generating alerts. Use scripts or tools that can detect patterns of unauthorized secret access.
- Compliance Reporting: Audit logs can be used to generate compliance reports, demonstrating that you're adhering to security policies and regulatory requirements.
Securing Containerized Applications with Kubernetes Secrets
Securing containerized applications with Kubernetes Secrets offers several benefits and is essential to maintaining the overall security and confidentiality of your applications.
Imagine you have a microservices-based application that relies on a database for storing and retrieving data. To ensure security, you're using Kubernetes to orchestrate your containers. Here's how securing containerized applications with Kubernetes Secrets could play out in this scenario:
- Database Credentials: Your application needs credentials to access the database. Instead of hardcoding these credentials into your application's configuration files, you create a Kubernetes Secret to store the database username and password securely.
- Secret Creation: You create a Secret named "db-credentials" containing the database username and password. The data is base64 encoded for storage.
- Pod Configuration: In your application's pod configuration, you reference the "db-credentials" Secret, injecting the database credentials as environment variables into the container.
- Pod Deployment: When you deploy your application pod, Kubernetes securely injects the environment variables with the database credentials from the Secret.
- Access Control: You configure Role-Based Access Control (RBAC) to ensure that only the relevant pods or services have access to the "db-credentials" Secret.
- Rotation: If you need to update the database credentials due to security reasons, you can update the Secret without modifying your application code. Kubernetes handles the injection of the updated credentials during the next pod deployment.
- Auditing: Kubernetes provides auditing capabilities, allowing you to track who accessed or modified the Secret, helping with compliance and security monitoring.
Deployment to the Green Pipeline
Let's walk through a scenario where you deploy an application using Kubernetes Secrets and demonstrate how the secrets are consumed within the application. In this example, we'll consider a simple web application that requires API keys for authentication.
Demonstrating how secrets are consumed within applications.
Deploying a Web Application with Secrets:
- Create a Secret: Assume you have an API key that the web application needs for authentication. You want to store this API key securely using a Kubernetes Secret.
- Deploy the Application: Next, you'll deploy the web application using the Kubernetes Deployment manifest. In this deployment, you'll reference the secret and consume the API key as an environment variable.
- Access the Secret Within the Application: Inside your web application code, you'll access the API key through the environment variable.
-
Deploy the Application: Apply the Deployment manifest using kubectl apply -f deployment.yaml. Kubernetes will create the necessary resources, including the Deployment and the Secret.
-
Accessing the Web Application: When the application pod starts, Kubernetes injects the API key from the api-secret Secret as an environment variable into the container. The application code accesses this environment variable to authenticate with the external API.
Third-party Tools and Plugins for Secrets Management
Several third-party tools and plugins can enhance secrets management in Kubernetes beyond the built-in Secrets functionality. These tools provide additional features such as encryption, rotation, access controls, and auditing. Here are some popular options:
- HashiCorp Vault: Vault is a highly popular secret management tool that can be integrated with Kubernetes. It provides a centralized platform for secret storage, encryption, dynamic secret generation, and access management. Vault supports various authentication methods and fine-grained access control policies.
- Bitnami Sealed Secrets: Sealed Secrets is a project that extends Kubernetes Secrets by encrypting them with a public key. Encrypted secrets are stored in the cluster, and only the controller with the private key can decrypt and create Secrets. This allows secrets to be safely stored in version control systems.
- AWS Secrets Manager: If you're running Kubernetes in AWS, AWS Secrets Manager can be integrated to manage secrets. It provides secure storage, automatic rotation, and access policies for secrets. The AWS Secrets Manager Injector can be used to inject secrets into pods.
- Google Cloud Secret Manager: Similarly, Google Cloud Secret Manager is designed for storing and managing secrets in Google Cloud. It integrates well with Kubernetes clusters running on Google Cloud Platform.
- Azure Key Vault: If you're using Azure, Azure Key Vault can be integrated with Kubernetes to securely manage keys, certificates, and secrets. It offers features like automatic key rotation and hardware-based security.
- EnvKey: EnvKey provides a convenient way to manage environment variables and secrets across various platforms, including Kubernetes. It supports automatic rotation and ensures that only authorized services have access to secrets.
- Sops: Sops is a tool that can be used to encrypt secrets stored in configuration files. It integrates well with Kubernetes and can encrypt secrets before they are committed to version control, providing an added layer of security.
- Mozilla SOPS: Similar to Sops, Mozilla SOPS is a command-line utility that can be used to manage encrypted files, including Kubernetes manifests containing secrets.
Challenges and Limitations
While Kubernetes Secrets offer a convenient way to manage sensitive data, they also come with certain challenges and limitations that you should be aware of:
Challenges:
- Base64 Encoding: Kubernetes Secrets store data in base64-encoded format. While this provides a basic level of obfuscation, it's not a secure encryption method. Sensitive data should be encrypted before being stored in Secrets.
- Limited Access Control: Kubernetes Secrets use Role-Based Access Control (RBAC) to manage access, but they lack more granular access controls. This can lead to situations where multiple pods or users have access to the same secret even if they only need specific parts of it.
- Rotation Complexity: Rotating Secrets, especially when done manually, can be complex and error-prone. Automated solutions are required for regular and secure rotation.
- Secrets in Memory: Once Secrets are injected into containers as environment variables or mounted files, they remain in memory for the lifetime of the container. This could be a security concern if containers are compromised.
- Secret Management at Scale: As the number of secrets and applications grows, managing them manually can become challenging. External secret management solutions like HashiCorp Vault can help address this challenge.
Limitations:
- No Built-in Encryption: Kubernetes Secrets don't natively provide encryption for the stored data. If you need encryption at rest, you must configure it at the Kubernetes cluster level.
- Lack of Secret Versioning: Secrets are updated by deleting and recreating them, which can lead to issues if multiple versions of a secret are required for rolling updates or debugging.
- Limited Auditing: While Kubernetes provides some basic audit logging, there might be limitations in tracking changes or access to Secrets.
- Cluster-wide Scope: Secrets are stored at the cluster level, and there's no built-in namespace-specific separation. This can potentially lead to accidental access to Secrets across namespaces. Moreover, namespace isolation primarily helps with organizational separation and avoids naming conflicts. However, Secrets are still accessible by all pods within the same namespace, so it's not a security boundary on its own. Proper access control mechanisms are needed to ensure that only authorized pods within the namespace can access the Secrets.
- Limited Secret Size: The maximum size for a single Secret is 1 MiB, which might not be sufficient for storing large files or complex data structures.
- No Dynamic Secret Retrieval: Kubernetes Secrets are static; they don't offer built-in mechanisms for dynamic secret retrieval from external sources like HashiCorp Vault does.
- Immutable After Creation: Once a Secret is created, its content cannot be updated directly. You need to delete and recreate it, which can affect running applications.
- Limited Data Types: Secrets support only string data, which might not cover all use cases (e.g., binary data).
Addressing common challenges in secrets management with Kubernetes.
Addressing common challenges in secrets management with Kubernetes requires careful planning, adherence to best practices, and sometimes the use of external tools. Here's how you can address the challenges mentioned above:
- Base64 Encoding: Use encryption before storing sensitive data in Secrets. This adds an extra layer of security and ensures that even if someone gains access to the encoded data, they won't be able to easily decipher it.
- Limited Access Control: Implement Role-Based Access Control (RBAC) carefully. Create different service accounts for different applications or pods, and grant them access only to the Secrets they require. Consider using more advanced RBAC features, like Pod Security Policies or Network Policies, to further restrict access.
- Rotation Complexity: Implement automated secret rotation using tools like HashiCorp Vault or third-party solutions. Automating the rotation process reduces the chances of human error and ensures a consistent approach.
- Secrets in Memory: Implement additional security measures like runtime security tools, memory protection mechanisms, and regular security audits to minimize the risk of sensitive data exposure from memory.
- Secret Management at Scale: Consider using external secret management solutions like HashiCorp Vault or specialized Kubernetes operators like Sealed Secrets. These tools are designed to handle secret management at scale and offer more advanced features.
- Lack of Encryption at Rest: Configure encryption at rest for your Kubernetes cluster's data store (e.g., etcd) to ensure that the stored secrets are encrypted. This provides an additional layer of protection beyond Kubernetes Secrets.
- Limited Auditing: Utilize Kubernetes audit logging and monitoring tools to keep track of changes to Secrets and access to them. You can also integrate external logging and monitoring solutions for more comprehensive auditing capabilities.
- Cluster-wide Scope: When creating Secrets, use namespaces to keep them isolated and accessible only to the appropriate resources within that namespace. Avoid using default namespaces and manage access controls effectively.
- Limited Secret Size: If you need to store large files or data structures, consider using external solutions like HashiCorp Vault, which offers more flexibility in storing and managing data of varying sizes.
- No Dynamic Secret Retrieval: Integrate an external secret management tool like HashiCorp Vault, which provides dynamic secret generation and retrieval capabilities. This ensures secrets are generated on the fly and minimizes the exposure window.
- Immutable After Creation: Plan for secret updates by using proper versioning. Consider using external tools that allow for dynamic secret updates without disrupting running applications.
- Limited Data Types: If you need to store binary data or complex structures, consider using ConfigMaps for those cases, and use Kubernetes Secrets specifically for storing sensitive string-based data.
Conclusion
- Kubernetes Secrets are used to securely manage sensitive information (e.g., passwords, tokens) within Kubernetes clusters.
- They keep sensitive data separate from application code and configuration to minimize exposure risk.
- External tools like HashiCorp Vault, AWS Secrets Manager, etc., offer advanced features for secrets management.
- These tools provide encryption, rotation, access controls, and auditing beyond built-in Kubernetes capabilities.
- Secrets can be created using different types: Opaque, Service Account Tokens, Docker Registry, TLS, SSH, and custom secrets.
