Securing Kubernetes Cluster
Overview
Kubernetes is an open-source container orchestration platform that automates the deployment, scaling, and management of containerized applications. A Kubernetes cluster is a collection of interconnected physical or virtual machines (nodes) that work together to manage and run containerized applications. The cluster provides a powerful framework for automating various tasks associated with managing and scaling applications, allowing organizations to focus on building and delivering software.
Best Practices to Secure Kubernetes Clusters
Securing a Kubernetes cluster is of paramount importance to ensure the confidentiality, integrity, and availability of your applications and data. Here's an overview of best practices to secure your Kubernetes cluster:
1. Use the Latest Version: Always keep your security in Kubernetes cluster up to date with the latest version. Newer versions often include security patches and enhancements.
2. Cluster Configuration:
- Minimize Attack Surface: Disable or remove any unnecessary components, plugins, or APIs from the cluster that you do not need.
- Secure Communication: Ensure that all communication within the cluster and with external entities is encrypted using TLS/SSL.
- Network Policies: Implement network policies to control traffic between pods and namespaces.
3. Authentication and Authorization:
- RBAC (Role-Based Access Control): Use RBAC to control who can access and modify resources within the security in kubernetes cluster.
- Multi-Factor Authentication (MFA): Enforce MFA for security in kubernetes cluster access.
- Service Accounts: Limit permissions granted to service accounts and avoid using default service accounts.
4. Secure Images:
- Image Vulnerability Scanning: Use container image vulnerability scanning tools to identify and remediate vulnerabilities in your container images.
- Image Signing: Sign your container images to ensure their integrity.
5. Secret Management:
- Use Kubernetes Secrets: Store sensitive information like API keys, passwords, and certificates in Kubernetes Secrets rather than hardcoding them in configurations.
- Secret Encryption: Encrypt the etcd datastore to secure stored secrets.
6. Pod Security Policies: Implement Pod Security Policies to define security standards for your pods, restricting their capabilities and access to the host system.
7. Network Security:
- Network Policies: Implement Kubernetes Network Policies to control traffic flow between pods and namespaces.
- Firewalls and Network Segmentation: Use firewalls and network segmentation to restrict access to your security in kubernetes cluster from unauthorized networks.
8. API Server Access Control:
- API Server Authorization Mode: Choose RBAC or other authorization modes that best fit your security in kubernetes cluster requirements.
- API Server Hardening: Implement rate limiting, request filtering, and other controls on the API server to prevent abuse.
9. Logging and Monitoring:
- Audit Logging: Enable audit logging to keep track of API requests and changes made to the cluster.
- Monitoring: Employ monitoring tools to track the health and performance of your cluster. Detect and respond to anomalies.
10. Regular Backups: Backup your cluster's etcd data regularly. This allows you to restore the cluster to a known-good state in case of issues.
11. Updates and Patching:
- Regular Updates: Keep your Kubernetes components, operating systems, and applications updated with the latest security patches.
- Regular Security Audits: Conduct security audits to identify vulnerabilities and weaknesses in your cluster.
12. Disaster Recovery Planning: Develop a comprehensive disaster recovery plan outlining steps to take in case of security breaches or other critical incidents.
13. Education and Training: Continuously educate your team about security in kubernetes best practices and keep them updated about the latest security threats and mitigation techniques.
Access Controlling to Kubernetes API
Access control to the Kubernetes API is crucial to prevent unauthorized access and ensure the security of your cluster. *Security in Kubernetes provides several mechanisms for controlling access to its API server:
i. RBAC (Role-Based Access Control): RBAC allows you to define roles, role bindings, and cluster roles to control what actions users and service accounts can perform on cluster resources. You define rules specifying which API groups, verbs, resources, and namespaces a role or role binding can access.
ii. ABAC (Attribute-Based Access Control): ABAC allows you to define access policies based on attributes, such as the user's name or group. However, RBAC is generally recommended over ABAC due to its finer-grained control.
iii. Webhooks: Security in Kubernetes allows you to integrate external authentication and authorization systems through admission control webhooks. This enables custom logic for access control decisions.
iv. Service Account Tokens: Security in Kubernetes automatically creates service account tokens for pods to authenticate with the API server. These tokens can be used to restrict API access by associating RBAC roles with service accounts.
v. OIDC (OpenID Connect): Security in Kubernetes supports OIDC for authentication, allowing users to log in using their existing identity provider. RBAC can then be used to control access based on their identity.
Access Controlling to Kubelet
The Kubelet is the primary agent that runs on each node and interacts with the control plane to manage containers. Access control to the Kubelet is essential to prevent unauthorized access and manipulation of containers on nodes.
- Kubelet TLS Bootstrap: Kubelet uses a client certificate for authentication. Kubernetes supports a certificate-based bootstrap process for Kubelets, ensuring they have the necessary credentials to authenticate with the control plane.
- Kubelet Authentication: Kubelets authenticate with the control plane using the Kubelet client certificate. You can configure authentication tokens or client certificates for Kubelets to prevent unauthorized access.
- Kubelet Authorization: Kubelets are authorized to perform specific actions based on the roles assigned to them. This can be enforced using RBAC, which controls the actions a Kubelet can take on pods and nodes.
- Node Authorization: Node authorization refers to controlling which nodes are allowed to join the cluster. It involves configuring the --authorization-mode flag for the API server.
- Kubelet API Access: Limit access to Kubelet's API server endpoint using network policies or firewalls. The Kubelet's API server provides information about the node and its containers.
- Secure Communication: Ensure that communication between Kubelets and the control plane is secure using TLS/SSL encryption.
Controlling Workload Capabilities
In Kubernetes, controlling the capabilities of workloads (containers within pods) is crucial to limit their access to host resources and enhance security. By default, containers in pods have a certain level of privilege that allows them to interact with the underlying host system. However, these privileges can be restricted to minimize the potential impact of security breaches.
i. Privilege Escalation and Capabilities:
- Privilege Escalation: This occurs when a container inside a pod gains more privileges than initially assigned. It can be dangerous if a compromised container escalates its privileges to affect the host or other containers.
- Capabilities: Linux capabilities are distinct privileges that can be granted to processes. By default, containers have a set of capabilities, but you can drop unnecessary capabilities to reduce attack vectors.
ii. Best Practices:
- Use Minimal Privileges: Always follow the principle of least privilege. Containers should only have the capabilities and privileges required to perform their intended tasks.
- Drop Unnecessary Capabilities: Use Kubernetes Pod Security Policies or PodSecurity admission controllers to drop unnecessary capabilities from containers.
- Restrict Privilege Escalation: Set allowPrivilegeEscalation: false in PodSecurityPolicy to prevent privilege escalation.
- Avoid Running as Root: Whenever possible, run containers with non-root users to reduce the potential impact of any security vulnerabilities.
Protection of Cluster Components from Compromise
Protecting cluster components is crucial to prevent unauthorized access and data breaches that can result from compromised components.
i. Cluster Components:
- Control Plane Components: Protect the control plane components, such as the API server, etc., scheduler, and controller manager, from unauthorized access.
- Kubelet: Ensure the Kubelet on each node is secure and not susceptible to unauthorized manipulation.
ii. Best Practices:
- Use Network Policies: Implement network policies to control traffic to and from cluster components.
- Restrict Access: Limit access to control plane components using firewall rules, network segmentation, and proper access controls.
- Secure etcd: Implement encryption and authentication for etcd. Limit access to etcd endpoints.
- Regular Updates: Keep all cluster components up to date with the latest security patches.
- Hardened Images: Use security-focused base images for control plane components and nodes.
- Monitor for anomalies: Set up monitoring and auditing to detect any unusual activities or unauthorized access attempts.
iii. Compartmentalization and Defense in Depth:
- Compartmentalization: Separate different components of the cluster to contain breaches. Use network policies and segmentation to isolate sensitive components.
- Defense in Depth: Implement multiple layers of security controls to prevent single points of failure. Combine authentication, authorization, encryption, and monitoring.
Major Kubernetes Security Issues and Concerns
Kubernetes, like any complex system, has potential security issues and concerns that need to be addressed.
1. Inadequate Access Control: Misconfigured or insufficient access controls can lead to unauthorized access and data breaches.
2. Vulnerable Images: Using container images with known vulnerabilities can expose the cluster to attacks.
3. Privilege Escalation: Containers gaining more privileges than necessary can lead to compromise.
4. Insecure Configurations: Incorrectly configured pods, services, and network policies can open security gaps.
5. Exposed Dashboard: Leaving the Kubernetes dashboard accessible without proper authentication can be risky.
6. Compromised Nodes: If nodes are compromised, attackers can potentially access sensitive data.
7. Insecure APIs: Weak API security can lead to unauthorized access and data leaks.
8. Unencrypted Communication: Lack of encryption between components can result in data exposure.
9. Security: inadequately secured, etc., can compromise sensitive data.
10. Lack of Updates: Failing to apply security patches promptly can expose vulnerabilities.
RBAC and Network Policies
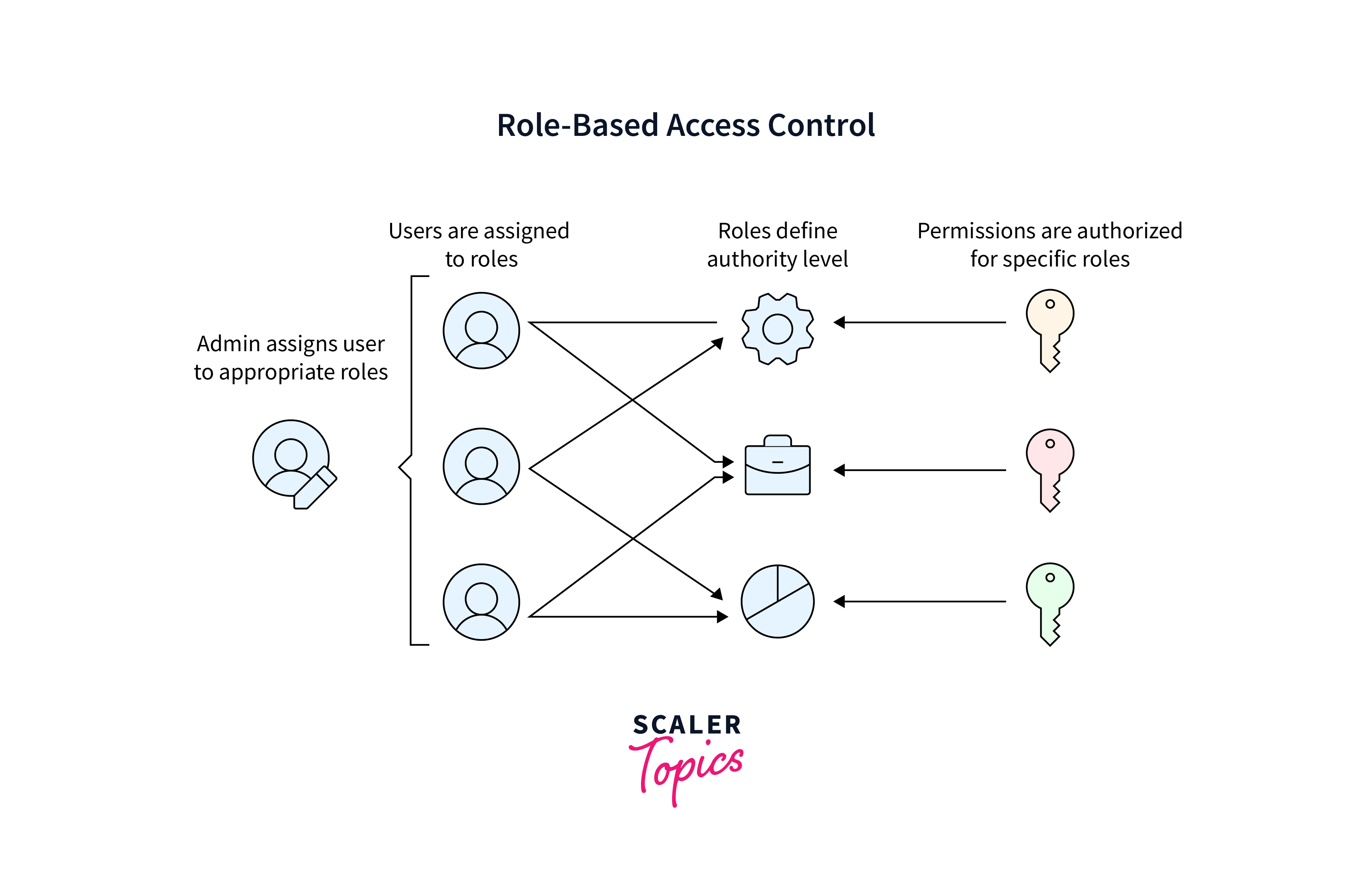
RBAC is a powerful mechanism in Kubernetes that enables fine-grained control over who can access and manipulate resources within a cluster. It helps in enforcing the principle of least privilege, ensuring that users, service accounts, and groups have only the necessary permissions to perform their tasks.
Components of RBAC:
i. Roles and Cluster Roles:
- Roles: Define permissions within a specific namespace. For example, you can create a role that allows reading pods in a particular namespace.
- Cluster Roles: Define permissions across the entire cluster. For instance, you can create a ClusterRole that allows managing nodes.
ii. RoleBindings and ClusterRoleBindings:
- RoleBindings: Associate users, groups, or service accounts with Roles within a namespace.
- ClusterRoleBindings: Associate users, groups, or service accounts with ClusterRoles across the entire cluster.
Example RBAC Configuration:
In this example, the role named "pod-reader" allows getting and listing pods in the "my-namespace" namespace.
Network Policies:
Network policies in Kubernetes control the flow of network traffic to and from pods. They are used to enforce communication rules between pods, enhancing security by segmenting application components.
Components of Network Policies:
i. Policy Types:
- Ingress: Kubernetes network policies generally use "Ingress" for controlling incoming traffic to pods.
- Egress: Kubernetes network policies generally use "Egress" for controlling outgoing traffic from pods.
ii. Selectors:
You use labels to select pods to which the network policy rules apply. For example, you can create a network policy that allows only specific pods to receive traffic.
iii. Rules:
Network policies consist of a set of rules that specify what traffic is allowed or denied based on source pods, namespaces, and ports.
Example Network Policy Configuration:
In this example, the network policy named "allow-nginx" allows incoming traffic from pods labeled with "role: db" to pods labeled with "app: nginx" on port 80.
Use Cases:
- RBAC is used to control API access and actions on resources within the cluster.
- Network policies are used to control communication between pods, allowing only authorized connections. They do not provide encryption or authentication for the communication between pods. They focus on controlling which pods can communicate with each other based on labels and selectors.
Benefits:
- RBAC provides a structured approach to controlling user and application access.
- Network policies enhance microsegmentation, reducing the attack surface and potential lateral movement of threats.
FAQs
Q1. Can Kubernetes run without network policies?
A. Yes, Kubernetes can run without network policies, but implementing them enhances security by controlling communication between pods.
Q2. What's the difference between a role and a cluster role in RBAC?
A. A role grants permissions within a specific namespace, while a cluster role grants permissions across the entire cluster.
Q3. Why is securing etcd important in Kubernetes?
A. etcd stores cluster configuration and state data. Insecure, etc., can expose sensitive information and compromise the entire cluster.
Conclusion
- Kubernetes security is crucial to protecting applications and data.
- Access control, image security, network policies, and secure configurations are key areas.
- RBAC limits user access, while network policies control communication.
- Regular updates and monitoring help maintain a secure cluster.
