Setting up and managing firewalls (iptables)
Overview
Firewalls are an essential aspect of any network security infrastructure. They help protect computers and other devices from unauthorized access, malware, and other network threats. In this article, we will discuss how to set up and manage Linux Firewall, specifically iptables.
Introduction to Linux Firewall
A firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on established security rules. It acts as a barrier between a trusted network and an untrusted network, mainly from the internet source. A firewall helps prevent unauthorized access, malware infections, and other security breaches.
How Does Linux Firewall Work?
The Linux Firewall, also known as iptables, is a network security tool that filters and manages incoming and outgoing traffic based on predefined rules. It works by examining packets of data passing through the system and determining whether to accept or reject them based on the configured firewall rules.
If a packet matches a rule, it is processed according to that rule's action. For example, if the rule specifies that the packet should be accepted, the firewall allows the packet to pass through. If the rule specifies that the packet should be rejected, the firewall discards the packet and sends a rejection message to the sender.
Additionally, users have the provision to create customized chains and rules as per their requirement to control and filter specific types of traffic. This flexible customization makes Linux Firewall a very advanced and capable tool for network security.
How Do Iptables Work?
Iptables is a command-line tool for configuring the Linux kernel's built-in firewall, which is responsible for filtering network traffic and enforcing security policies. Iptables work by processing network packets and applying a set of predefined rules to determine whether to accept, reject, or modify the packet's contents.
Iptables use a set of chains to organize the rules that it applies to incoming and outgoing traffic. There are three default chains: INPUT, OUTPUT, and FORWARD.
Further in this article, we will learn about chains and its types. Let’s follow.
Chains

Chains are the most important part of the Linux firewall (iptables). Chains is responsible for allowing users to organize and manage a set of rules that control network traffic. There are three default chains in Iptables: INPUT, OUTPUT, and FORWARD, each type has a different capability and functionality. Let’s understand them more vividly.
Input Chain
This chain handles incoming traffic intended for the local system. Rules in the INPUT chain are applied to packets before they are processed by any other chain. The INPUT chain is used to apply security policies, such as blocking packets from specific IP addresses or protocols, or allowing certain traffic based on port numbers.
Output Chain
The OUTPUT chain handles outgoing traffic generated by the local system. Rules in the OUTPUT chain are applied to packets after they have been processed by any other chain. The OUTPUT chain can be used to control which packets are allowed to leave the system, such as blocking packets from certain ports or limiting the bandwidth available for certain protocols.
Forward Chain
This one handles packets that are being forwarded through the system, such as when acting as a router. Rules in the FORWARD chain are applied to packets that are not intended for the local system. The FORWARD chain can be used to control which packets are allowed to pass through the system, such as blocking packets from certain IP addresses or protocols, or limiting the bandwidth available for certain types of traffic.
Customized chain
In addition to the default chains, users can also create their own customized chains, which can be used to create rules and simplify management. Customized chains can be used to group rules that apply to a specific type of traffic, such as HTTP or FTP, or to implement more complex security policies.
Next, we will learn about different policies in iptables.
Different Policies
Policies in general mean a set of rules. In Iptables, policies refer to the same general meaning of a set of rules that define how incoming and outgoing network traffic is handled by the firewall. The most common policies in Iptables include the default policy and the specific chain policies.
The default policy specifies the action to take for packets that do not match any rules in a particular chain. This policy can be set to ACCEPT, DROP, or REJECT, depending on the security requirements of the system. The specific chain policies are used to define the behavior of traffic passing through a particular chain as discussed in the earlier part of the article.
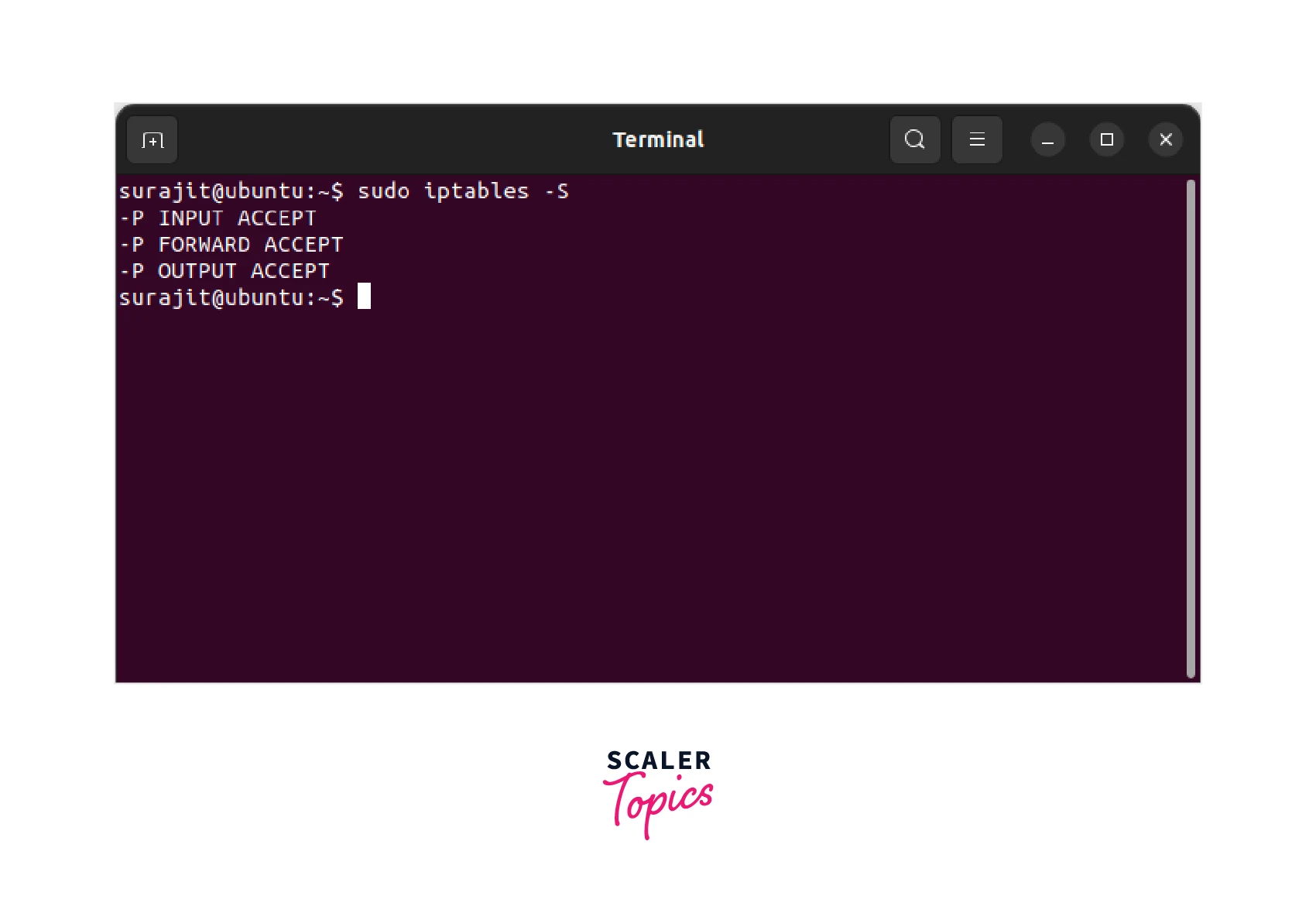
These policies can be customized based on specific security policies or network requirements. We will discuss the set of rules in detail further in the article while understanding the setting up of rules in iptables.
How to Configure and Install Firewall Iptables in Ubuntu?
Now, we will figure out the exact steps to follow for installing and configuring iptables in Ubuntu.
Step 1:
Open a terminal and update the package repository using the following command:
Step 2:
Install iptables using the following command:
Step 3:
Check the status of iptables using the following command:
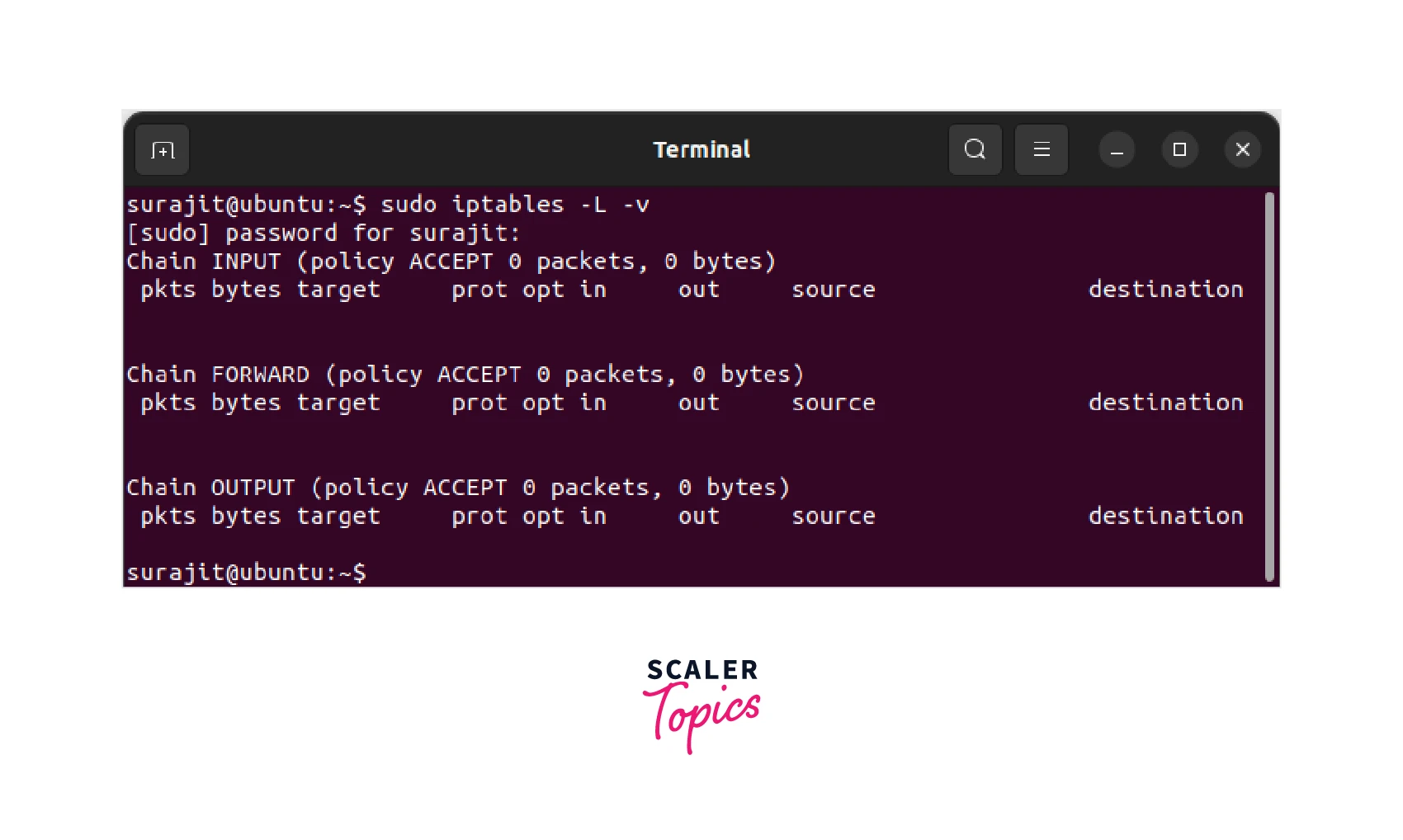
Step 4:
Once iptables is installed, enter the following command to check the current firewall rules:
After checking the firewall rules we found that by default, all traffic is allowed, so we need to set up our firewall rules.
Further in the article, we will learn to set up rules for the iptables installed in the system.
Making Your First Iptables Rule
Now, we will learn how to create the first rule in Linux firewall(iptables) with practical examples.
Step 1:
First of all we need to check the current rules of the firewall. This will help you understand what traffic is currently allowed or blocked on your system. To do this, open a terminal window and run the below-mentioned command:
This command will list all the current rules in iptables as we have seen earlier.
Step 2:
Now that you have an idea of what rules are currently in place, let's create a new rule. In this example, we will be creating a rule to allow incoming SSH traffic to be called as a web page in simple language.
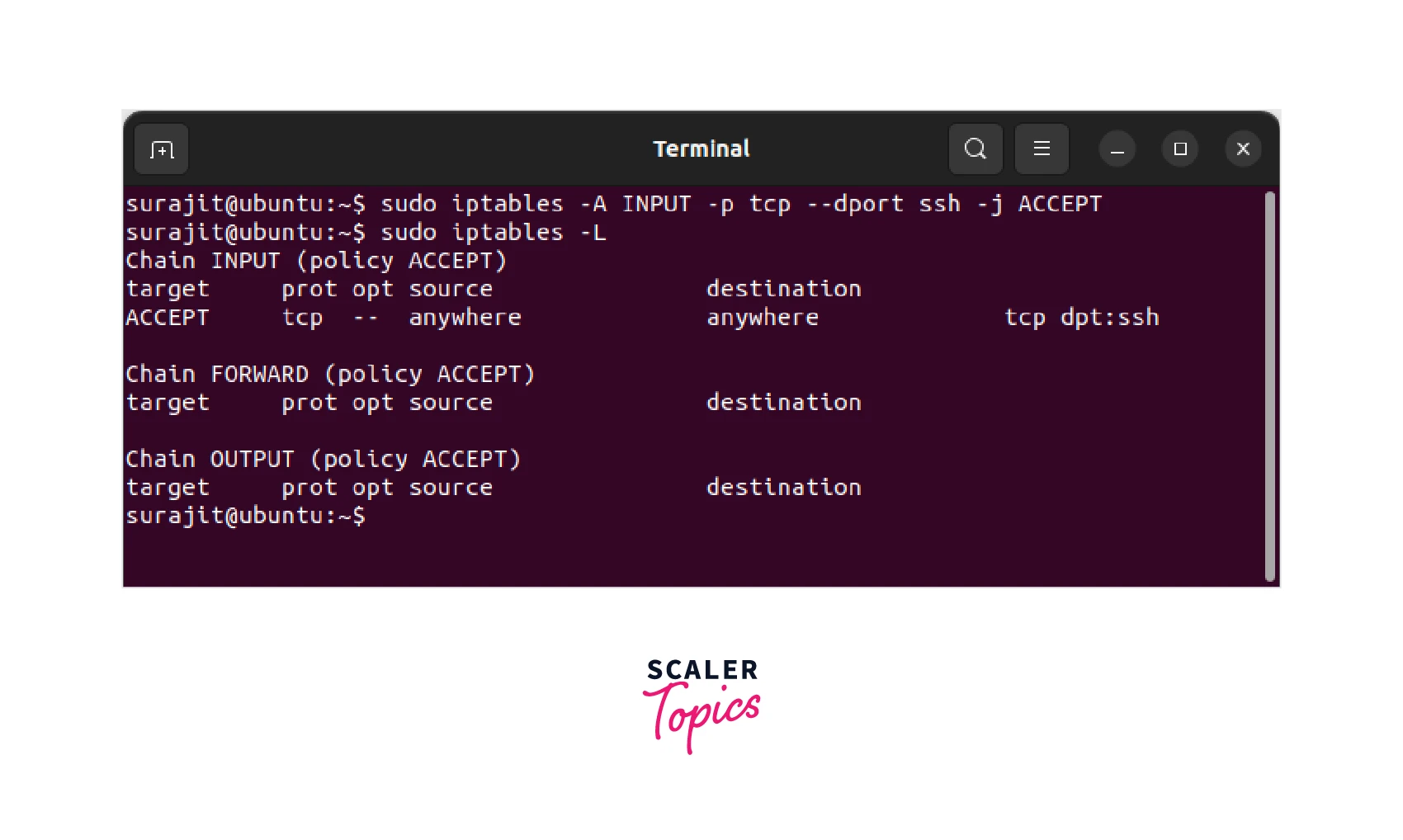
Let's break down this command for a better understanding.
- sudo : Run the command as the root user
- iptables : The command we are running
- -A INPUT : Append the new rule to the INPUT chain (which is responsible for incoming traffic)
- -p tcp : Specify the protocol (in this case, TCP)
- --dport ssh : Specify the destination port (in this case, port 22 for SSH)
- -j ACCEPT : If the traffic matches the rule, accept it
Step 3:
After we have created a new rule, we need to save it so it remains after rebooting the system. To do this, we will use the iptables-save command.
This command mentioned above saves the current iptables rules to a file called rules.v4 in the /etc/iptables/ directory.
Step 4:
Verifying the new rule is important. To verify that the new rule has been added successfully, run the following command:
This will list all the current rules in iptables, including the new rule that was just added.
Once the command confirms that the rule is saved, You have successfully created your first rule in iptables. You need to be very careful while making changes to your firewall rules, as they can have a significant impact on your system's security.
DROP Rule
Drop rule creation in iptables is a rule to block all traffic from a specific source or to a specific destination. Now, we will go through the steps to create a Drop rule in iptables and will also understand the specifications of the options used in the command.
It is always recommended to check the current rule in iptables before applying any changes to it by using the below-mentioned command:
Creating a Drop rule in iptables Linux firewall.
Step 1:
To create a Drop rule in iptables, we use the -j DROP as the target. This below-mentioned example is of a Drop rule that blocks all traffic from a specific IP address.
Let's break down this command to understand the specifications of the options used:
- sudo : Run the command as the root user
- iptables : The command we are running
- -A INPUT : Append the new rule to the INPUT chain (which is responsible for incoming traffic)
- -s 192.168.1.100 : Specify the source IP address that we want to block
- -j DROP: If the traffic matches the rule, drop it
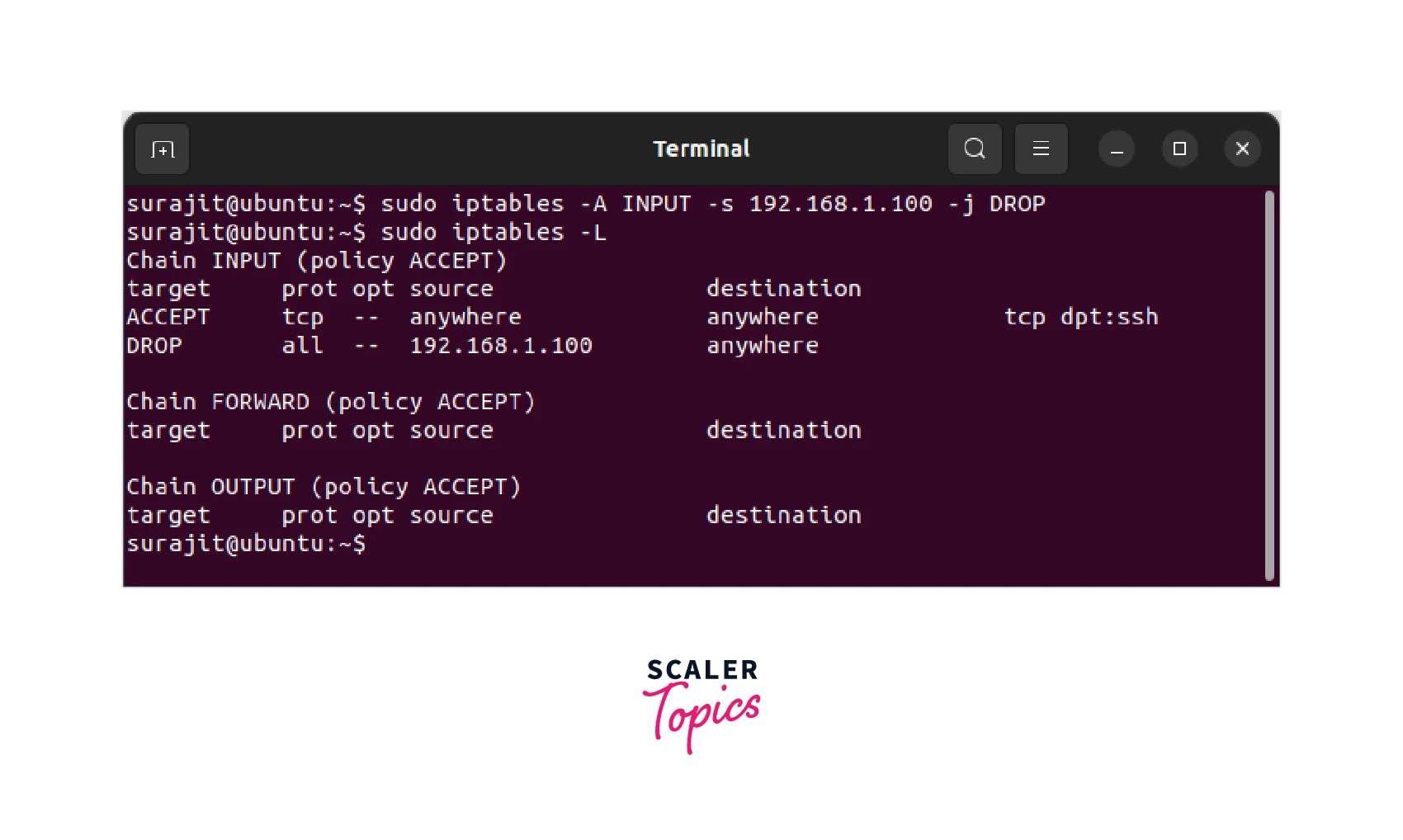
Step 2:
Now, after the creation of the new rule, we need to save it so that it remains across reboots. To do this, we will use the iptables-save command.
This command saves the current iptables rules to a file called rules.v4 in the /etc/iptables/ directory.
ACCEPT Rule
Creation of an ACCEPT rule in iptables means allowing specific traffic to pass through your firewall. We will demonstrate the same practice for better understanding.
Step 1:
Creating an ACCEPT Rule in iptables. We use the -j ACCEPT as a target. The below-mentioned example allows incoming HTTP traffic.
Let's break down this command to understand the specifications of the options used:
- sudo : Run the command as the root user
- iptables : The command we are running
- -A INPUT : Append the new rule to the INPUT chain (which is responsible for incoming traffic)
- -p tcp : Specify the protocol (in this case, TCP)
- --dport 80 : Specify the destination port (in this case, port 80 for HTTP)
- -j ACCEPT : If the traffic matches the rule, accept it
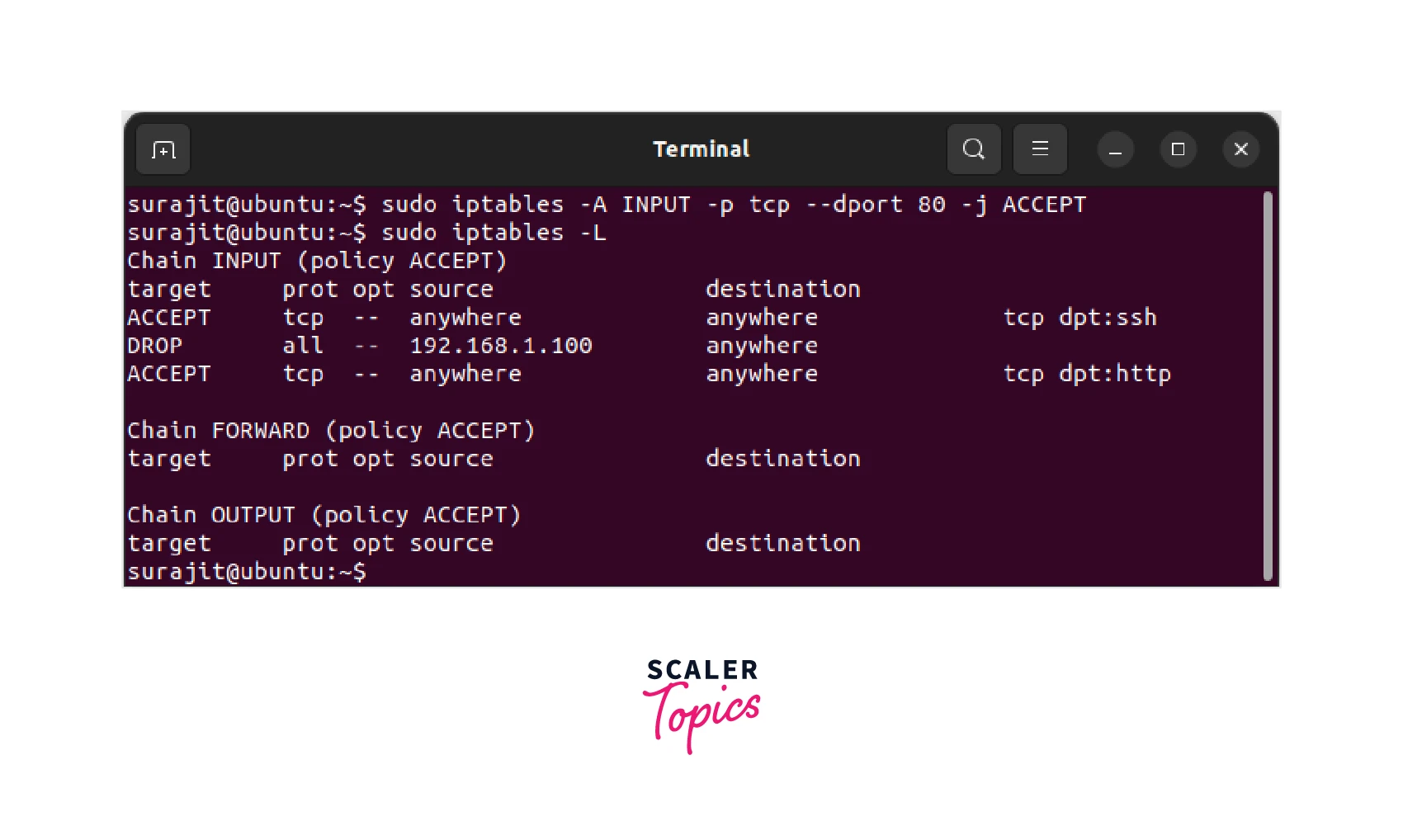
Step 2:
Now, after the creation of the new rule, we need to save it so it remains across reboots. For doing this, we will use the iptables-save command as mentioned below.
This command saves the current iptables rules to a file called rules.v4 in the /etc/iptables/ directory. That is how you can create an Accept rule in the Linux firewall.
Removing a Rule Through the Iptable
If you are looking to remove a rule from the iptables, you need to know the chain, protocol, source/destination IP address, and port number of the rule.
Step 1:
As usual for that we will have to check the currently applied rules in the iptables.
This will help you identify the rule and find all the information of the rule you want to remove.
To do this, use the below-mentioned command.
Step 2:
To remove the rule, use the iptables -D command, followed by the chain name and the rule details. As an example, to remove a rule that blocks incoming traffic on port 22 (SSH), use the below-mentioned command:
Let's break down this command to understand the specifications of the options used.
- sudo : Run the command as the root user
- iptables : The command we are running
- -D INPUT : Delete a rule from the INPUT chain
- -p tcp : Specifies the protocol (in this case, TCP)
- --dport 22 : Specifies the destination port (in this case, port 22 for SSH)
- -j DROP : Specifies the target of the rule (in this case, DROP)
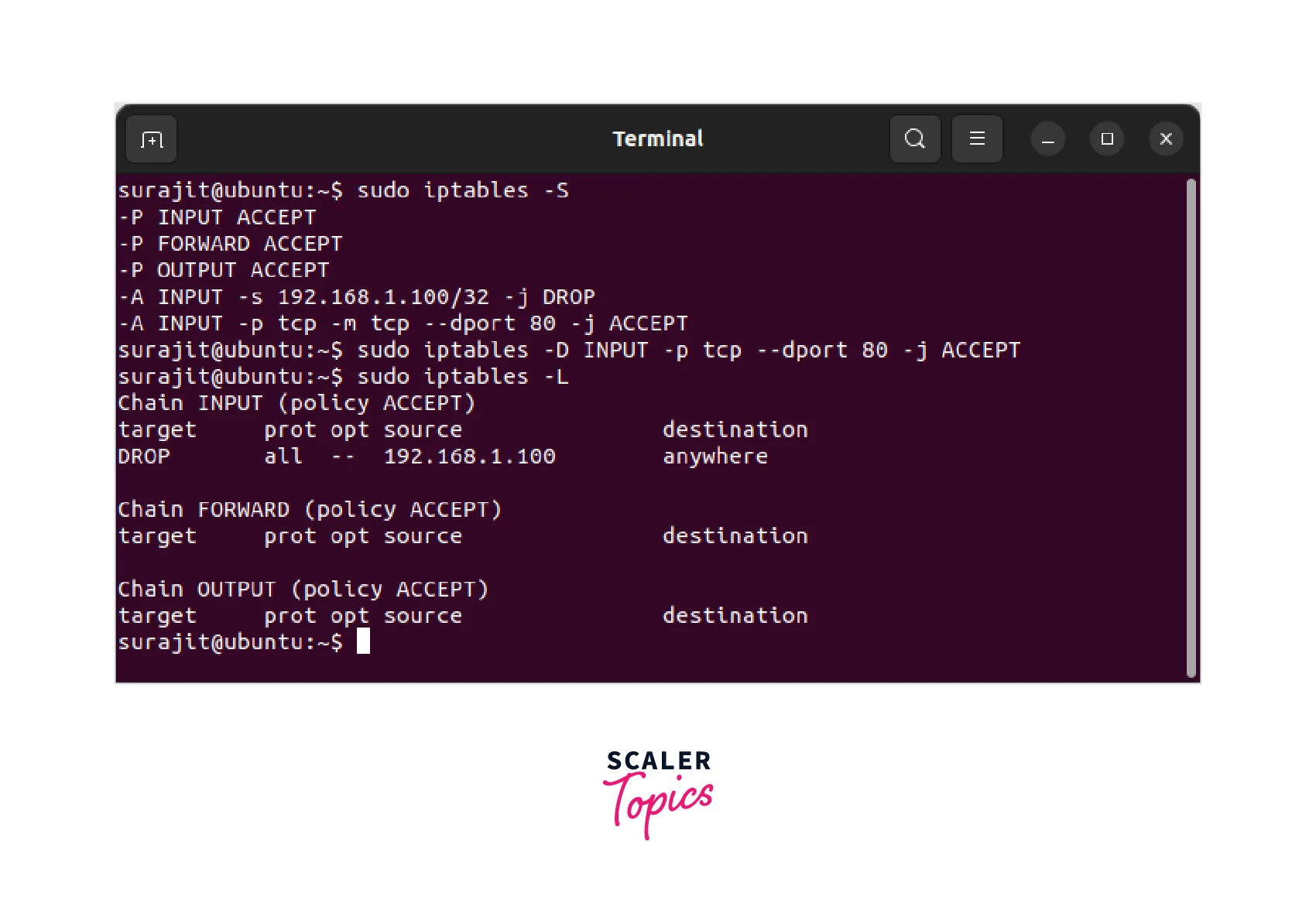
After removing the rule, save the updated iptables rules so that the rule remains across reboots.
Saving Your Configuration
We have already discussed the procedure to save newly created rules in the iptables. However, let’s understand saving the configuration in Linux Firewall iptables exclusively.
After making changes to the iptables rules, it's important to save the configuration to ensure that the changes remain after a system reboot. There are few different ways to save the iptables configuration, depending on the Linux distribution you are using.
For Debian/Ubuntu systems, you can use the iptables-persistent package to save the iptables configuration.
We need to start with installing the iptables-persistent package. To do so, we need to run the below-mentioned command:
During the installation, you will be prompted to save the current iptables rules. You need to choose "Yes" to save the rules.
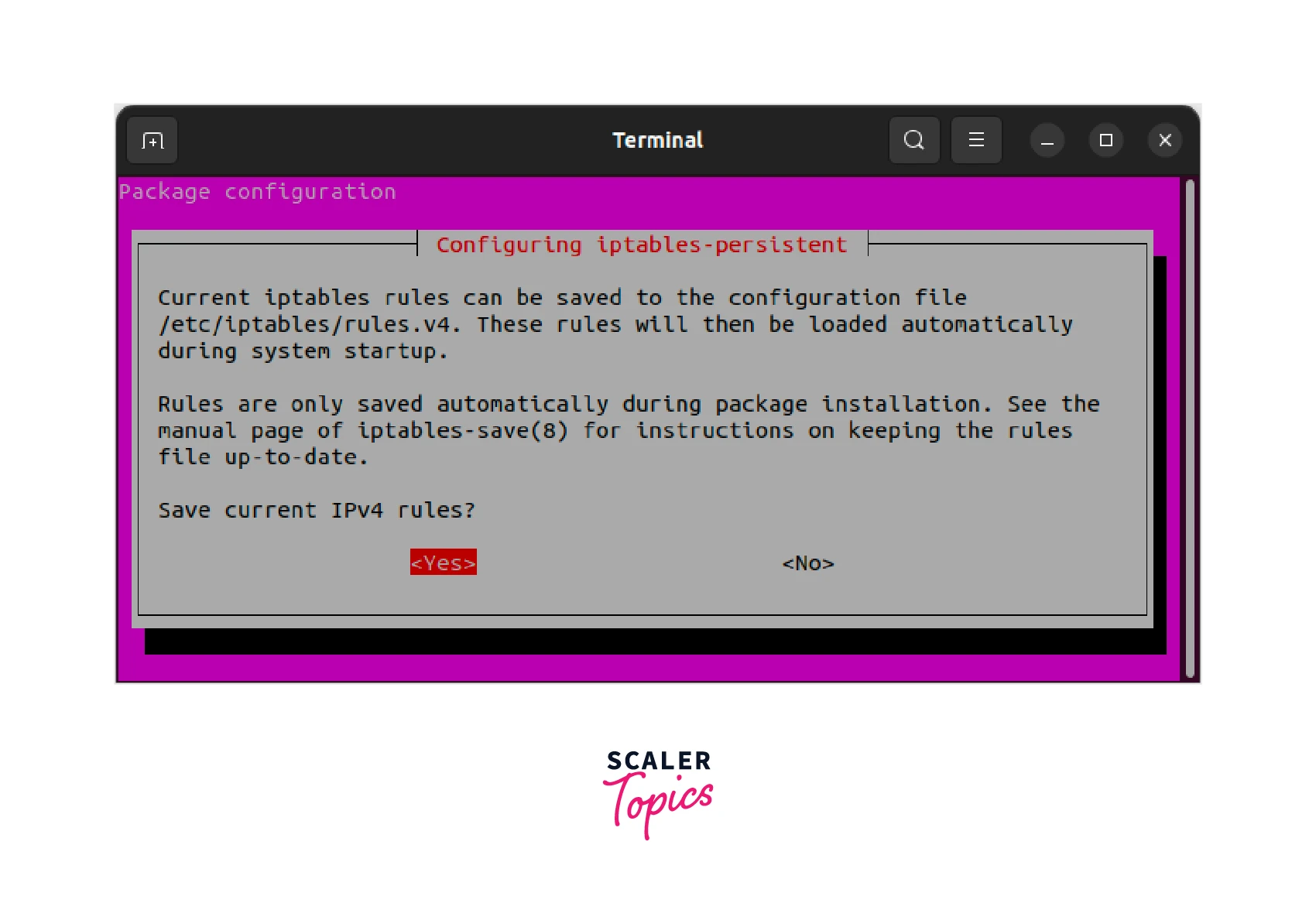
If you are looking to save the iptables rules manually without using the iptables-persistent package, then you need to use the iptables-save command for saving the current rules to a file.
This command mentioned above saves the current iptables rules to a file called rules.v4 in the /etc/iptables/ directory.
Note: On some Linux distributions, you might need to create the directory "/etc/iptables/ directory" first.
Some situations may arrive where you might need to restore the iptables rules. r restoring the saved iptables rules, use the below-mentioned iptables-restore command.
This command loads the saved iptables rules from the rules.v4 file.
So that’s it, by using the above-mentioned commands you can save a new rule in the iptables Linux firewall.
Conclusion
- Firewalls are important for network security.
- Linux has a built-in firewall tool called
- Iptables work by creating rules that define how the firewall should handle network traffic
- Users can configure and manage iptables by setting up chains and policies, creating rules, and removing rules.
- It is important to save and apply iptables configurations to ensure the firewall is working properly.
