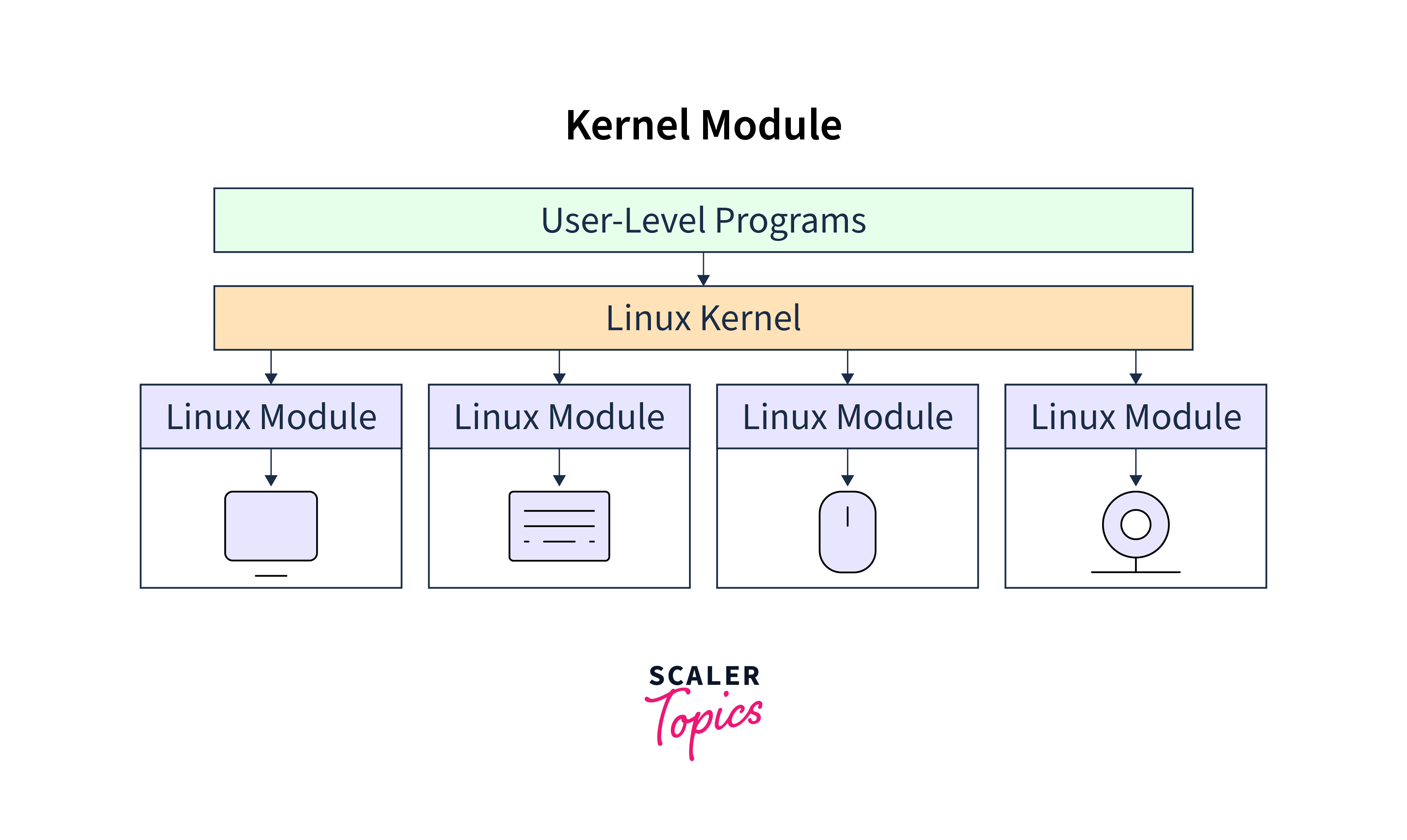
What is a Kernel Module in Linux?
A Linux kernel module is a fragment of code that can be dynamically loaded into the Linux kernel without requiring a reboot. It is intended to extend the functionality of the kernel, permitting the inclusion of new features or support for various hardware devices or file systems.
Kernel modules enable the addition or removal of code from the kernel without requiring recompilation or modification of the entire kernel. As they permit the addition of device drivers on demand, they are particularly useful for supporting hardware that was not available when the kernel was compiled.
Supporting new network cards, adding file system support, supplying device drivers for peripherals, implementing security features, and enabling additional kernel functionality are common use cases for kernel modules.
Typically, kernel modules are stored in distinct files with the extension ".ko" and are loaded into the kernel using the "insmod" or "modprobe" commands. Once loaded, the module becomes an integral component of the operating kernel and can interact with other system components.
Kernel modules provide the Linux kernel with flexibility and modularity, allowing it to be customized and adapted to various hardware configurations and software requirements. They provide a method for extending the kernel's capabilities without requiring a complete system reboot, making Linux a highly versatile and adaptable operating system.
Kernel Modules Subdirectories
Linux kernel modules are organized into subdirectories based on their purpose or category. These subdirectories provide a structured way to manage and organize kernel modules. The main subdirectories for kernel modules are typically found under the /lib/modules/
kernel: This directory contains core kernel modules, including fundamental functions such as process management, memory management, and system calls.
drivers: The drivers' directory is further divided into various subdirectories, each representing a different category of hardware drivers. For example, you may find subdirectories like a net for network drivers, sound for audio drivers, USB for USB drivers, and so on.
fs: This directory contains file system modules. Each file system, such as ext4, NTFS, or FAT, may have its subdirectory here.
net: The net directory contains network-related modules, including protocols, device drivers, and network stack components.
crypto: This directory holds cryptographic modules that provide encryption, decryption, hashing, and other cryptographic operations.
sound: Sound-related modules, such as sound card drivers, mixer controls, and audio frameworks, are located in this directory.
video: The video directory contains modules related to video and graphics, including graphics card drivers, frame buffer drivers, and video-related utilities.
These are just a few examples of the subdirectories commonly found within the /lib/modules/
Example of Linux Kernel Module
Here are some examples of kernel modules with brief explanations of their functionalities:
ext4: The ext4 module is responsible for providing support for the ext4 file system in the Linux kernel. It enables the kernel to read, write, and manipulate ext4 file systems, which are widely used in many Linux distributions. This module allows for efficient and reliable storage and retrieval of files on disk.
usb-storage: The usb-storage module enables the kernel to handle USB mass storage devices such as USB flash drives, external hard drives, and memory card readers. It allows the kernel to recognize and communicate with these devices, making them accessible as block devices. This module enables users to read and write data to USB storage devices seamlessly.
iwlwifi: The iwlwifi module provides support for Intel Wireless WiFi Link adapters. It allows the kernel to communicate with and control Intel Wi-Fi adapters, enabling wireless networking capabilities. This module handles tasks such as scanning for available networks, connecting to wireless networks, and transmitting/receiving data over Wi-Fi.
snd_hda_intel: The snd_hda_intel module is responsible for supporting Intel High Definition Audio (HDA) controllers. It provides audio capabilities for Intel-based systems, allowing the kernel to manage sound playback and recording. This module handles tasks such as audio input/output, mixing, and processing, enabling sound functionality on Intel systems.
nvidia: The nvidia module is specific to systems with NVIDIA graphics cards. It provides the necessary support for NVIDIA GPUs, allowing the kernel to interact with the graphics hardware. This module handles tasks such as initializing the GPU, managing display output, and providing hardware acceleration capabilities for graphics-intensive applications.
These are just a few examples of kernel modules, and there are many more available for various hardware devices, file systems, network protocols, and other functionalities.
Now, Let's check out an example of a simple kernel module that prints a message when it is loaded and unloaded:
Explanation of each component present in the above code.
-
This code is a simple example of a kernel module written in C for the Linux kernel. Let's go through the code and understand its different parts:
-
These lines include necessary header files for kernel module development, which provide various functions, types, and macros used in the module.
-
These macros define the licensing, authorship, and description of the module. In this case, the module is licensed under the GPL (GNU General Public License), and you should replace "Your Name" with your actual name.
-
This function is the module's initialization routine. It is called when the module is loaded into the kernel using the insmod command. The __init macro indicates that this function is only used during module initialization and will be discarded from memory after that. In this example, it simply prints a message using the printk function, which sends the message to the kernel log with the KERN_INFO log level.
-
This function is the module's exit routine, which is called when the module is unloaded from the kernel using the rmmod command. Similarly to the initialization routine, the __exit macro indicates that this function is only used during module exit and will be discarded from memory after that. It also prints a message using printk.
-
These lines register the module's initialization and exit functions with the kernel. The module_init macro specifies the initialization function to be called when the module is loaded, and the module_exit macro specifies the exit function to be called when the module is unloaded.
This code defines a simple kernel module that prints messages to the kernel log during initialization and exit. It serves as a basic example to demonstrate the structure and flow of a kernel module.
We will also find out how to compile the above-given code later in this article.
Working with Linux Kernel Module
Working with Linux kernel modules involves several steps, including developing the module, compiling it, loading it into the kernel, interacting with the module, and unloading it when no longer needed. Here's a general overview of the process:
Develop the Kernel Module:
Write the code for the kernel module in the programming language supported by the kernel, typically C. The module code should implement the desired functionality, such as device drivers, file systems, or additional kernel features. Ensure that the necessary header files are included and that required functions are implemented.
Create a Makefile:
Create a Makefile to automate the compilation process. The Makefile should specify the necessary compilation flags and dependencies. This file helps simplify the compilation process and ensures that the module is built correctly.
Compile the Module:
Use the Makefile or manually compile the module code using the appropriate compiler. The compilation command should link against the kernel's headers and libraries. For example:
Load the Module:
Load the compiled module into the kernel using the insmod command or a similar utility. For example:
Interact with the Module:
Once the module is loaded, you can interact with it as desired. This may involve using special device files created by the module, configuring its behavior, or triggering specific functionality.
Check Kernel Logs:
Monitor the kernel logs using the dmesg command to view any log messages or debugging output generated by the module. This can help diagnose issues or understand the module's behavior.
Unload the Module:
When you no longer need the module, you can unload it from the kernel using the rmmod command. For example:
During the development process, you may make changes to the module code, recompile it, reload it into the kernel, and repeat the testing or debugging steps.
It's important to note that working with kernel modules requires administrative privileges (sudo) as loading and unloading modules directly affect the kernel's functionality. Additionally, it's crucial to carefully test and validate kernel modules before using them in a production environment to ensure system stability and security.
Listing Currently-Loaded Modules
To list the currently loaded modules in a Linux system, you can use the lsmod command.
Open a terminal and run the following command:
The output will display a list of currently loaded kernel modules. Each line represents a single module and provides information such as the module name, size, dependencies, and the number of other modules using it.
An example of what the output will look like in a Linux Kernel Module List:
In the example above, the nvidia, snd_hda_intel, iwlwifi, usb_storage, and ext4 modules are currently loaded.
Compiling a Kernel Module
Compiling a kernel module involves ensuring that the necessary headers and build environment are set up correctly and then using the appropriate compilation commands. Here's a general outline of the process:
Install Kernel Headers:
Make sure that the kernel headers matching your running kernel version are installed. These headers contain the necessary header files and build infrastructure for compiling kernel modules. On many Linux distributions, you can install the headers using the package manager. For example, on Ubuntu or Debian, you can run:
Create the Module Source Code:
Write your kernel module source code in a file with a .c extension. The code should include the required headers and implement the desired functionality.
Create a Makefile:
Create a Makefile to specify the build instructions for the kernel module. The Makefile should include the necessary compilation flags, dependencies, and the target module name. Here's a simple example of a Makefile for a kernel module:
Compile the Module:
Open a terminal and navigate to the directory containing your module source code and the Makefile. Run the make command to build the module:
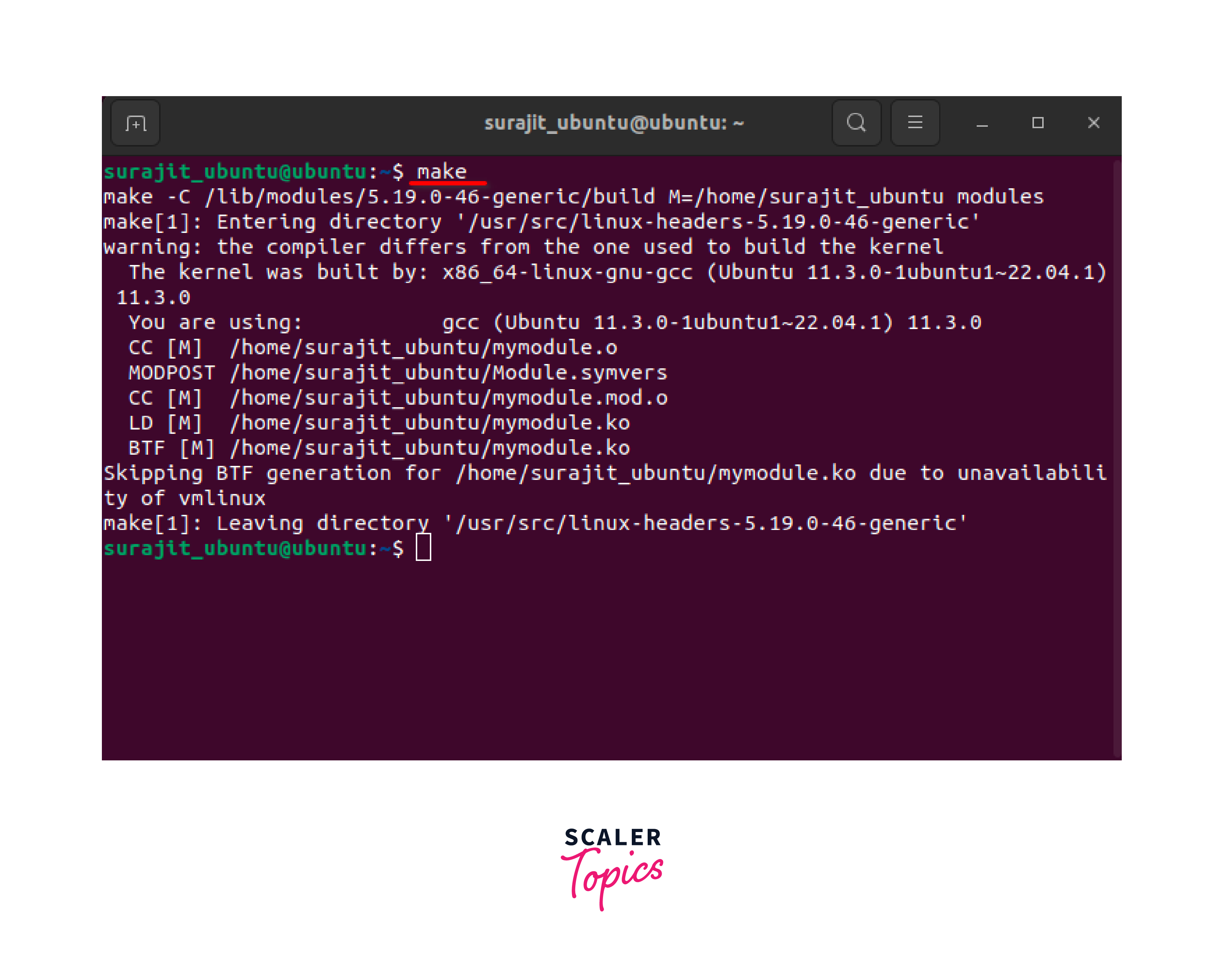
This command uses the Makefile to compile the module. It invokes the kernel build system (kbuild) and compiles the module source code into an object file (.ko).
Verify the Compilation:
After the compilation process completes successfully, you should see the module object file (e.g., mymodule.ko) in the current directory. This indicates that the module has been compiled successfully.
Load and Test the Module:
You can load the compiled module into the kernel using the insmod command and test its functionality. Make sure you have the necessary permissions to load the module (typically, you'll need to run the command as root using sudo).
Clean Up:
If you want to clean up the compiled object files and intermediate build artifacts, you can use the clean target in the Makefile:
This command removes the compiled object files and restores the directory to its original state.
Loading and Unloading a Kernel Module
Loading and unloading a kernel module involves adding or removing the module from the running kernel. Here's an overview of the process:
Loading a Kernel Module
Compile the Kernel Module:
Ensure that you have compiled the kernel module using the instructions provided in the previous response.
Load the Module:
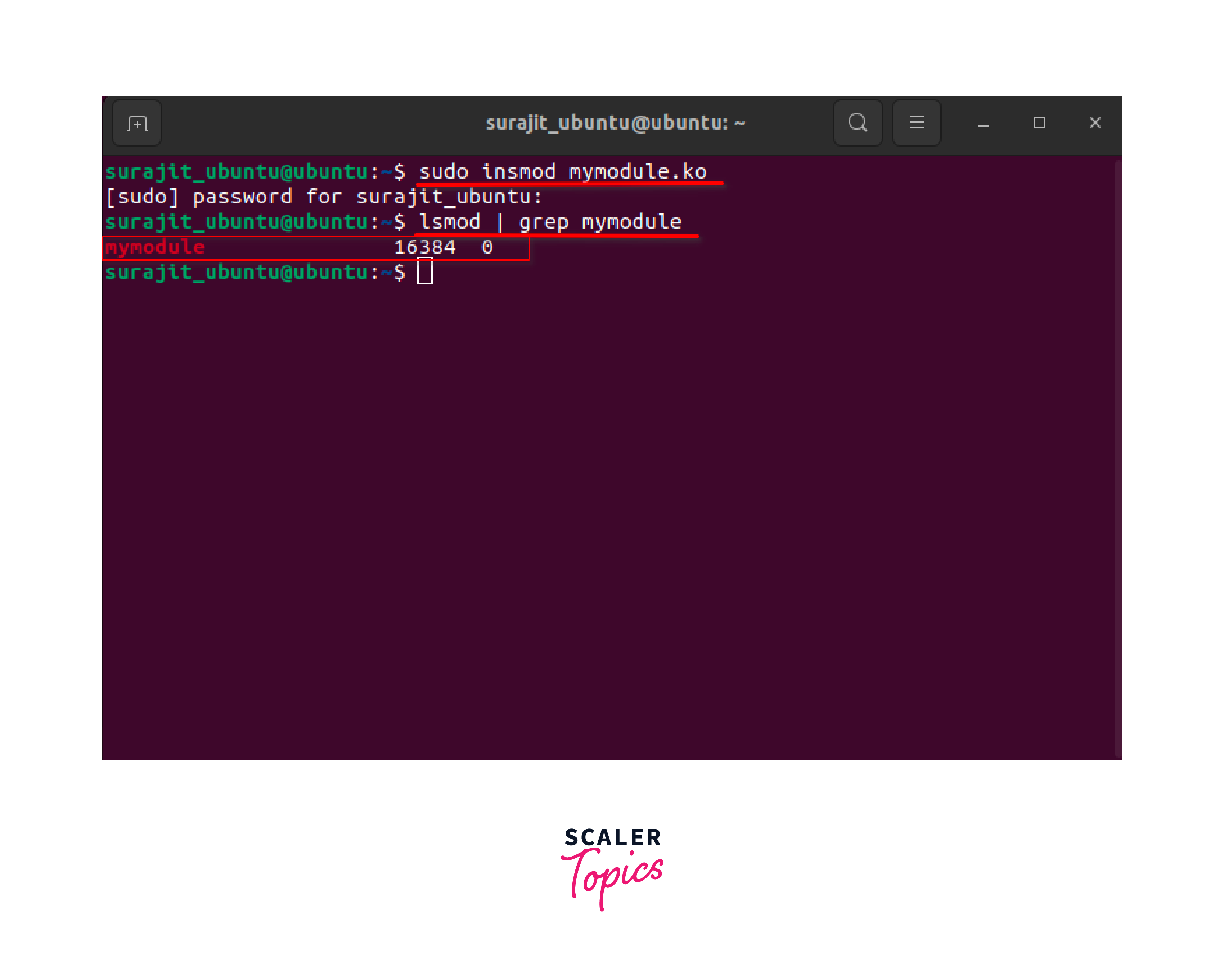
Open a terminal and use the insmod command (or a similar utility) to load the module into the kernel. You will typically need administrative privileges to load a module. For example:
The insmod command loads the module specified by the .ko file into the kernel. The module's initialization function will be executed.
Verify the Module is Loaded:
To confirm that the module has been loaded successfully, you can use the lsmod command to list the currently loaded modules. Ensure that your module appears in the list.
Interact with the Module:
Once the module is loaded, you can interact with it based on its functionality. This may involve using special device files created by the module, configuring its behavior, or triggering specific actions.
Unloading a Kernel Module
Unload the Module:
To unload a loaded kernel module, you can use the rmmod command (or an equivalent utility). Again, administrative privileges may be required.
For example:
The rmmod command removes the specified module from the kernel. The module's exit function will be executed.
Verify the Module is Unloaded:
You can use the lsmod command to verify that the module has been unloaded. Ensure that your module no longer appears in the list of loaded modules.
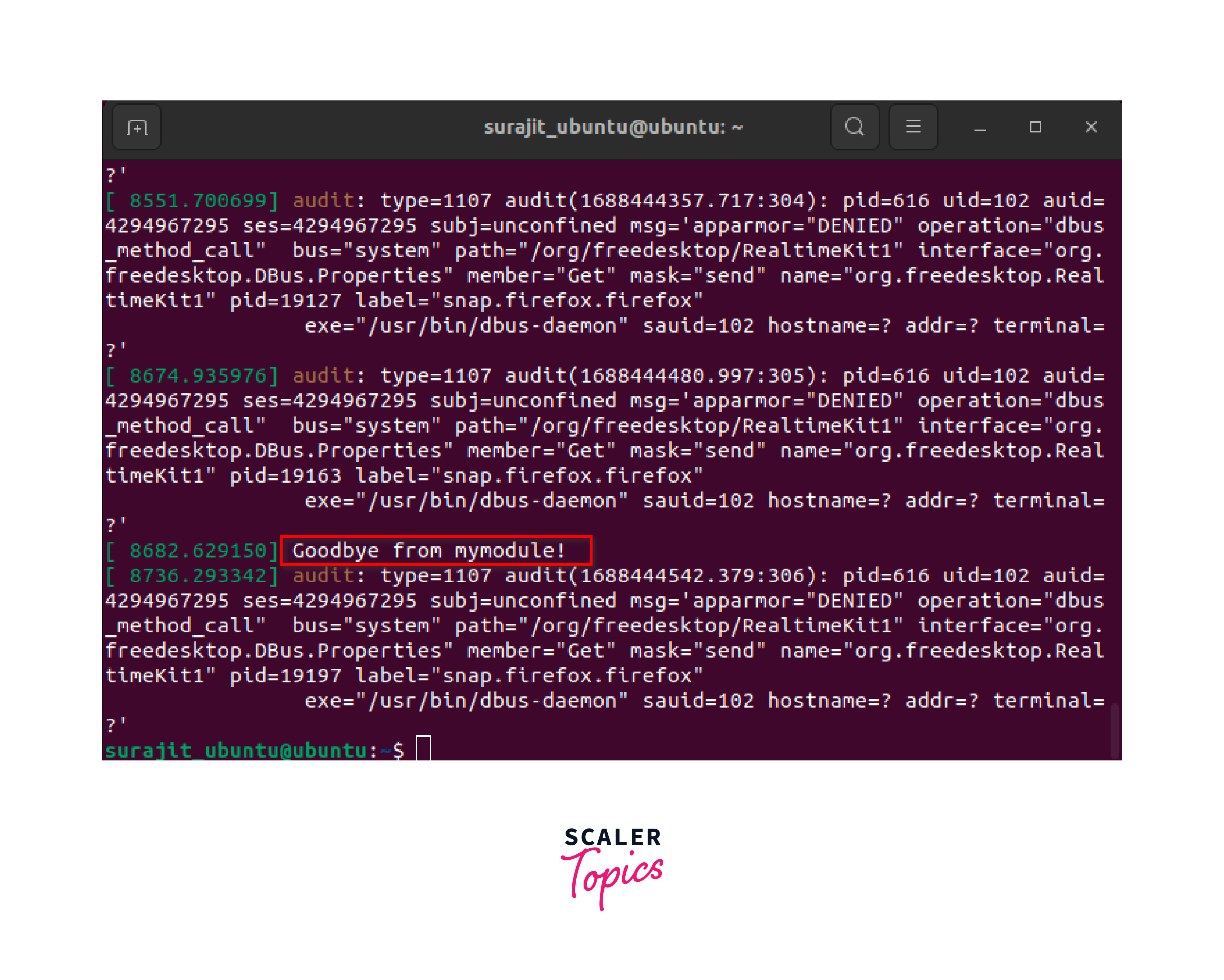
It's important to note that unloading a module should be done with caution, as it can affect the stability and functionality of the system. Ensure that you have taken any necessary precautions and understand the implications of unloading a particular module before doing so.
Debugging a Kernel Module
Debugging a kernel module can be a challenging task due to the unique environment and constraints of kernel development. However, there are several techniques and tools available to assist in debugging kernel modules. Here are some common approaches:
Print Debugging Messages:
Insert debug print statements at key points in your module's code using the printk function. These messages can provide valuable information about the module's execution flow and variable values. You can view the printed messages in the kernel log using tools like dmesg or journalctl. For example:
Kernel Debugger (KDB):
KDB is a built-in kernel debugger that allows you to pause the kernel's execution, inspect data structures, and execute commands. You can trigger a kernel breakpoint by adding the __asm__("int3") instruction in your code. Once the kernel hits the breakpoint, you can use commands provided by KDB to examine variables, backtrace the execution stack, and more.
Kernel Probes:
Kernel probes, such as kprobes and uprobes, allow you to dynamically insert breakpoints at specific locations in the kernel code without modifying the original source. This technique can be useful for tracing the execution of specific functions or system calls. Tools like perf and systemtap provide support for kernel probing.
Dynamic Kernel Debugging (KDB/KGDB):
KGDB is a kernel extension that allows remote debugging of a running kernel using a remote GDB debugger. It enables you to set breakpoints, inspect variables, and step through the kernel code. This approach requires additional configuration and setup but offers powerful debugging capabilities.
Kernel Oops Reports:
If your module triggers a kernel crash (known as an "oops"), the kernel generates an error report containing valuable information about the cause of the crash. You can retrieve this information from the kernel log or by analyzing kernel crash dump files. Tools like crash or kdump can assist in analyzing kernel crash dumps.
Static Code Analysis:
Static code analysis tools, such as sparse or cppcheck, can help identify potential coding issues and vulnerabilities in your kernel module's source code. These tools can detect common programming mistakes and provide suggestions for improvements.
Remember to thoroughly test and validate your module in a controlled environment before deploying it on production systems. Kernel debugging requires careful attention and expertise, as any misstep can lead to system instability or crashes. It's essential to have a solid understanding of kernel internals and debugging techniques to effectively debug kernel modules.
Signing Kernel Modules for Secure Boot
Signing kernel modules is an important step when working with Secure Boot-enabled systems. Secure Boot is a feature that ensures only signed and trusted code can be loaded during the boot process, including kernel modules. To sign kernel modules, you'll need to generate and manage cryptographic keys and certificates. Here's a general outline of the process:
Generate a Key Pair:
The first step is to generate a cryptographic key pair: a private key and a corresponding public key. The private key will be used to sign the kernel modules, while the public key will be embedded in the system firmware to verify the module signatures during boot. You can use tools like openssl to generate the key pair. For example:
Configure the Build System:
If you're building kernel modules from source code, you'll need to configure the build system to use the signing keys. The build system typically provides options to specify the path to the signing keys or specify the key details in a configuration file. Refer to the documentation or build system instructions for the specific method used in your environment.
Sign the Kernel Modules:
After configuring the build system, rebuild the kernel modules to generate signed versions. The build process will use the private key to sign each module during compilation. The exact commands or options to sign the modules will depend on the build system or specific module build process. Ensure that the signed modules are generated in the correct location.
Enroll the Public Key:
To ensure that the system can verify the module signatures during boot, you need to enroll the public key in the system firmware. The exact method for enrolling the key will depend on the system firmware or bootloader used. This step is usually performed during the Secure Boot configuration process. Consult the system documentation or firmware/bootloader documentation for instructions on enrolling the public key.
Enable Secure Boot:
Once the public key is enrolled, enable Secure Boot in the system firmware or bootloader settings. This ensures that only signed modules are loaded during the boot process.
By following these steps, you can sign your kernel modules and ensure they are loaded in Secure Boot-enabled systems without triggering security warnings or boot failures. It's important to carefully manage your private key and ensure it remains secure, as it is critical for maintaining the integrity of your signed modules.
Advantages of Linux Kernel Module
Linux kernel modules offer several advantages, making them a powerful tool for extending the functionality of the Linux kernel.
Let's look at some of the key advantages of using kernel modules:
Dynamic Loading and Unloading:
Kernel modules can be dynamically loaded and unloaded into the running kernel without requiring a system reboot. This flexibility allows for easy addition, removal, and updating of functionality without disrupting the entire system. It enables modular system configurations, efficient resource utilization, and the ability to hot-plug devices or features.
Kernel Space Access:
Kernel modules have direct access to kernel internals and services. They can interact with and modify the kernel's data structures, functions, and device drivers, allowing for deep integration and customization. This access makes kernel modules suitable for implementing device drivers, file systems, network protocols, and other kernel-level functionality.
Memory and Performance Optimization:
Kernel modules can be designed to load on demand, minimizing memory usage and improving system performance. By dynamically loading only the necessary modules, system resources can be allocated efficiently. Additionally, kernel modules can be optimized for specific hardware or use cases, providing better performance compared to generic kernel configurations.
Customizability and Flexibility:
Kernel modules offer great flexibility in tailoring the kernel to specific needs. Users can select and load only the required modules, reducing the kernel's overall size and complexity. This customization enables fine-grained control over system features, hardware support, and security options, resulting in lean and efficient configurations.
Code Reusability and Maintenance:
Kernel modules promote code reusability and modular software design. Developers can build reusable modules that provide specific functionalities, which can be shared and reused across different projects or distributions. This approach simplifies code maintenance, bug fixes, and feature updates, as changes can be made to a module without affecting the entire kernel.
Security and Stability:
Kernel modules can enhance system security and stability by providing isolation between modules and the core kernel. Faults or bugs in a module are less likely to affect the entire kernel, minimizing the risk of system crashes or vulnerabilities. Additionally, modules can be loaded with specific security measures, such as module signing, to ensure the integrity and authenticity of the code.
Linux kernel modules offer a flexible and efficient mechanism for extending the functionality of the Linux kernel. They enable customization, modular design, dynamic loading, and targeted optimizations, resulting in a versatile and powerful operating system.
Conclusion
-
Linux kernel modules are loadable kernel code that can be dynamically added or removed from the running kernel.
-
Kernel modules offer several advantages, including dynamic loading and unloading, direct access to kernel internals, memory and performance optimization, customizability, code reusability, and improved security and stability.
-
Compiling a kernel module involves setting up the necessary headers and build environment, creating the module source code, and using a Makefile to specify the build instructions.
-
Loading a kernel module involves using the insmod command to add the module to the kernel while unloading a module can be done with the rmmod command.
-
Debugging a kernel module can be challenging, but techniques such as printing debug messages, using kernel debuggers like KDB or KGDB, employing kernel probes, analyzing kernel oops reports, and conducting static code analysis can be helpful.
-
When working with Secure Boot-enabled systems, signing kernel modules using cryptographic keys and certificates is necessary to ensure module integrity. The signing process involves generating a key pair, configuring the build system, signing the modules, enrolling the public key in the system firmware, and enabling Secure Boot.
-
Linux kernel modules provide a flexible and efficient mechanism for extending the functionality of the Linux kernel. They offer customizability, code modularity, dynamic loading, and targeted optimizations, making the Linux operating system versatile and powerful.
-
Understanding and working with kernel modules is valuable for kernel developers, device driver writers, system administrators, and anyone interested in exploring the inner workings of the Linux kernel.
